Safety Management System

Employee Benefits Pay Vacation Ppt PowerPoint Presentation Infographic Template Shapes
This is a employee benefits pay vacation ppt powerpoint presentation infographic template shapes. This is a eight stage process. The stages in this process are employee benefit, health insurance, social security, achievement award, management.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF
Mentioned slide shows information about ISO 25010 2011 software quality model. Here the model is defined into eight stages namely functional suitability, reliability, performance efficiency, operability, security, compatibility, maintainability and transferability. Find highly impressive Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Key Principles Associated With Google AI Portrait PDF
This slide showcases major principles which are associated with research and development of Google AI. It provides details about be socially beneficial, built and tested for safety, preventing reinforcing of unfair bias and accountability. Create an editable Key Principles Associated With Google AI Portrait PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Key Principles Associated With Google AI Portrait PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Essential Features Provided By Saas Program Ppt PowerPoint Presentation File Outline PDF
The following slide highlights the essential features provided by saas platform illustrating key headings which includes cost efficiency, scalability, reliability and security. Persuade your audience using this essential features provided by saas program ppt powerpoint presentation file outline pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cost efficiency, scalability, reliability, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
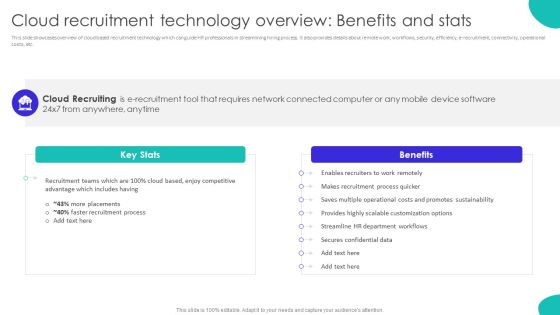
Improving Technology Based Cloud Recruitment Technology Overview Benefits And Stats Slides PDF
This slide showcases overview of cloud based recruitment technology which can guide HR professionals in streamlining hiring process. It also provides details about remote work, workflows, security, efficiency, e-recruitment, connectivity, operational costs, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Improving Technology Based Cloud Recruitment Technology Overview Benefits And Stats Slides PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Big Data Template 2 Ppt PowerPoint Presentation Portfolio Model
This is a impact of big data template 2 ppt powerpoint presentation portfolio model. This is a four stage process. The stages in this process are healthcare, science, security, business.

Risk Categories Ppt PowerPoint Presentation Styles Background Image
This is a risk categories ppt powerpoint presentation styles background image. This is a six stage process. The stages in this process are product design, design, tools, security, environment.

Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Mobile Phone Generations 1G To 5G Key Features And Disadvantages Of 5Th Generation Technology Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Deploying AML Transaction Monitoring Major Roles And Responsibilities Of Financial Microsoft PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. The Deploying AML Transaction Monitoring Major Roles And Responsibilities Of Financial Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Protection And Privacy Issues In Cloud Technology Rules PDF
The following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Persuade your audience using this Protection And Privacy Issues In Cloud Technology Rules PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Absence Of Control, Saas Security, Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5S Methodology For Conducting Kaizen Process Ppt PowerPoint Presentation File Inspiration PDF
This slide covers the 5S methodology for conducting kaizen event which includes sort, set in order, shine, standardize and sustain that are helpful in improving the team efficiency, removing obstacles, arranging items, organizing training, regular audits, preventing defects, etc. Persuade your audience using this 5S Methodology For Conducting Kaizen Process Ppt PowerPoint Presentation File Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Eliminating Unnecessary, Reduces Distraction, Enhances Safety, Organizing Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
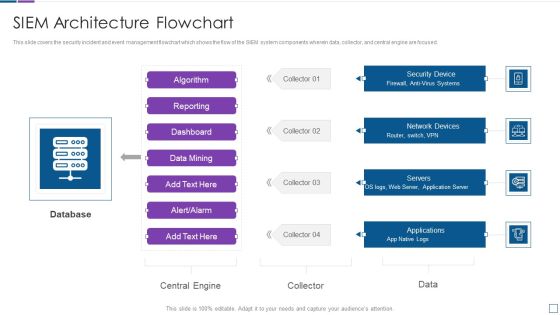
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
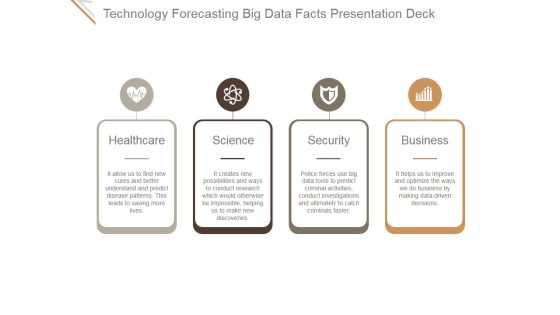
Technology Forecasting Big Data Facts Ppt PowerPoint Presentation Clipart
This is a technology forecasting big data facts ppt powerpoint presentation clipart. This is a four stage process. The stages in this process are healthcare, science, security, business.
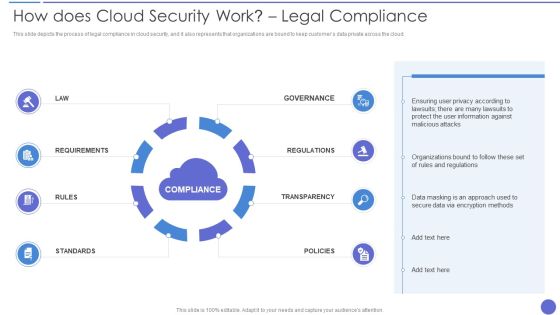
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
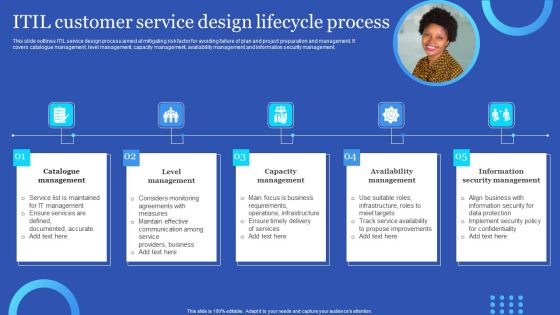
ITIL Customer Service Design Lifecycle Process Information PDF
This slide outlines ITIL service design process aimed at mitigating risk factor for avoiding failure of plan and project preparation and management. It covers catalogue management, level management, capacity management, availability management and information security management. Persuade your audience using this ITIL Customer Service Design Lifecycle Process Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Availability Management, Information Security Management, Capacity Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Executing Advance Data Analytics At Workspace Addressing Service Provider Vendor Formats PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a executing advance data analytics at workspace addressing service provider vendor formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fault management, performance management, configuration management, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
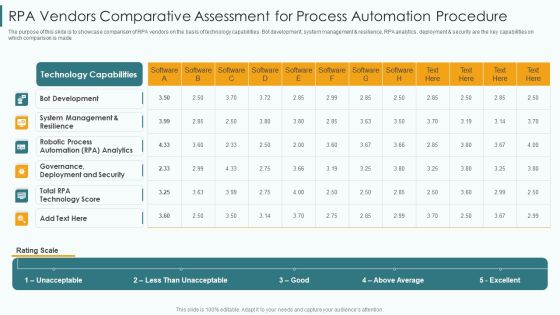
RPA Vendors Comparative Assessment For Process Automation Procedure Portrait PDF
The purpose of this slide is to showcase comparison of RPA vendors on the basis of technology capabilities. Bot development, system management and resilience, RPA analytics, deployment and security are the key capabilities on which comparison is made. Showcasing this set of slides titled rpa vendors comparative assessment for process automation procedure portrait pdf. The topics addressed in these templates are deployment, security, management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
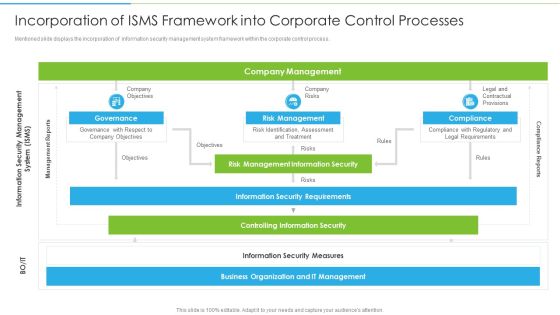
Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process. This is a Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Company Objectives, Company Management, Company Risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
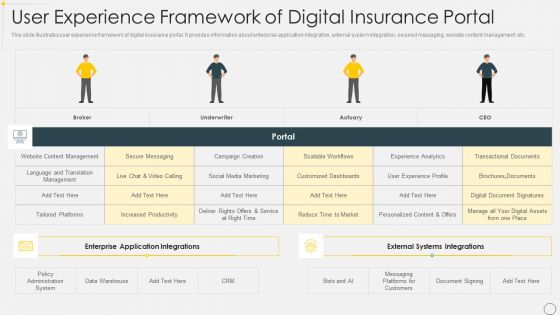
User Experience Framework Of Digital Insurance Portal Brochure PDF
This slide illustrates user experience framework of digital insurance portal. It provides information about enterprise application integration, external system integration, secured messaging, website content management, etc. Showcasing this set of slides titled User Experience Framework Of Digital Insurance Portal Brochure PDF. The topics addressed in these templates are Management, Customized Dashboards, Policy Administration System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Backup Security Mechanism For Business Leaders Infographics PDF
This slide showcases organization data backup policy that includes data type, backup frequency, onsite, offsite retention and comments. The data covered is related to server operating system, workforce records and ERP system database.Showcasing this set of slides titled Data Backup Security Mechanism For Business Leaders Infographics PDF. The topics addressed in these templates are Operating Systems, Workforce Records, Employee Home Directories. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Evolving BI Infrastructure Determine Overview Of Established Security Centre Slides PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting evolving bi infrastructure determine overview of established security centre slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, internal systems, backup, functional business units. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
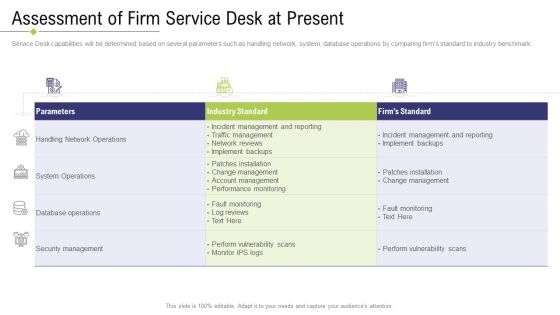
Technology Facility Maintenance And Provider Assessment Of Firm Service Desk At Present Brochure PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver an awe inspiring pitch with this creative technology facility maintenance and provider assessment of firm service desk at present brochure pdf bundle. Topics like system operations, security management, performance monitoring, network reviews, database operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
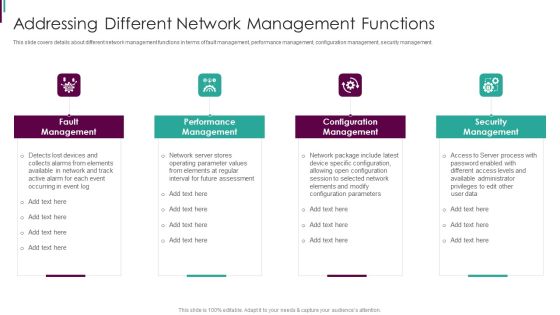
Developing Business Analytics Framework Addressing Different Network Information PDF
This slide covers details about different network management functions in terms of fault management, performance management, configuration management, security management. This is a Developing Business Analytics Framework Addressing Different Network Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Fault Management , Performance Management, Configuration Management You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
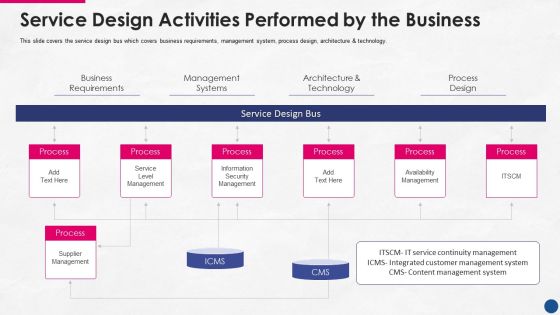
Incorporating Platform Business Model In The Organization Service Design Activities Performed By The Business Inspiration PDF
This slide covers the service design bus which covers business requirements, management system, process design, architecture and technology. Deliver and pitch your topic in the best possible manner with this incorporating platform business model in the organization service design activities performed by the business inspiration pdf. Use them to share invaluable insights on service level management, information security management, availability management, supplier management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Application Of AI For Database Access Governance Summary PDF
This slide represents the applications of artificial intelligence systems for data access governance. The purpose of this slide is to demonstrate the AI application in secure data access. The use cases include threat detection and prediction, system configuration, adaptability, data interpretation, and predictive forecasting. Presenting Application Of AI For Database Access Governance Summary PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prediction, System Configuration, Adaptability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF bundle. Topics like Security And Monitoring, Recognize Services, Supporting Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Architecture Of Cloud Security Authorization Cloud Computing Security IT Ppt Model Sample PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative architecture of cloud security authorization cloud computing security it ppt model sample pdf bundle. Topics like monitoring, security, authorization, services, data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
File Lock Security Vector Icon Ppt PowerPoint Presentation Infographics Model
This is a file lock security vector icon ppt powerpoint presentation infographics model. This is a one stage process. The stages in this process are computer software, operating system, open source.
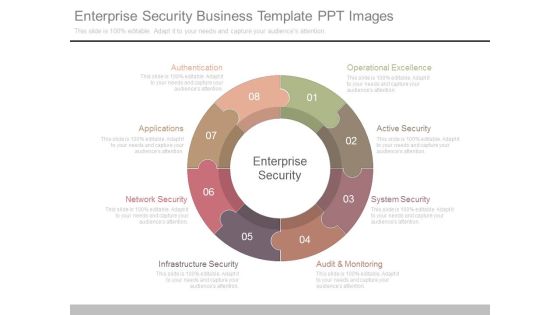
Enterprise Security Business Template Ppt Images
This is a enterprise security business template ppt images. This is a eight stage process. The stages in this process are enterprise security, authentication, applications, network security, infrastructure security, audit and monitoring, system security, active security, operational excellence.

Benefits Of RDBMS Summary PDF
This slide covers the advantages of RDBMS relational database management system for managing data. The purpose of this template is to define the features as well as uses of RDBMS. It includes details related to data integrity, scalability, security, etc.Persuade your audience using this v. This PPT design covers Six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Integrity, Scalability, Simplicity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Security Ppt Diagram Example Ppt Presentation
This is a computer security ppt diagram example ppt presentation. This is a eight stage process. The stages in this process are application guard, antivirus, passwords, firewall, attack detection, system guard, file lock, process quarantine.

Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
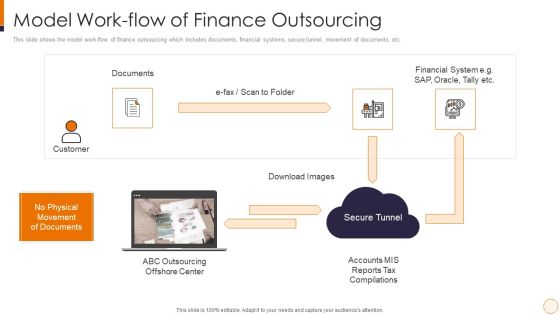
SME And Startups Financing Services Model Work Flow Of Finance Outsourcing Information PDF
This slide shows the model work-flow of finance outsourcing which includes documents, financial systems, secure tunnel, movement of documents, etc. This is a sme and startups financing services model work flow of finance outsourcing information pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial system, secure tunnel, documents, customer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda For Information Security Ppt Professional Good PDF
This is a agenda for information security ppt professional good pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, systems, data, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Market Opportunity Forecasts Example Presentation Visual Aids
This is a market opportunity forecasts example presentation visual aids. This is a eight stage process. The stages in this process are security audit, system integration, consoling training, solution architecture, analysis, account based intelligence, tools, models and forecasting.
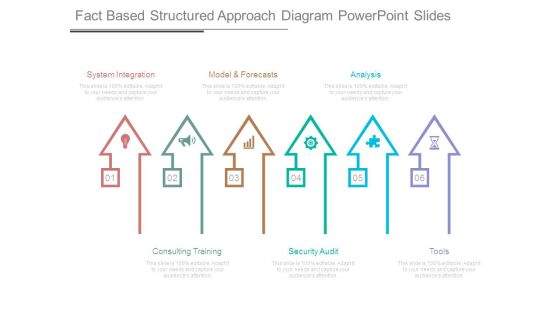
Fact Based Structured Approach Diagram Powerpoint Slides
This is a fact based structured approach diagram powerpoint slides. This is a six stage process. The stages in this process are system integration, model and forecasts, analysis, consulting training, security audit, tools.
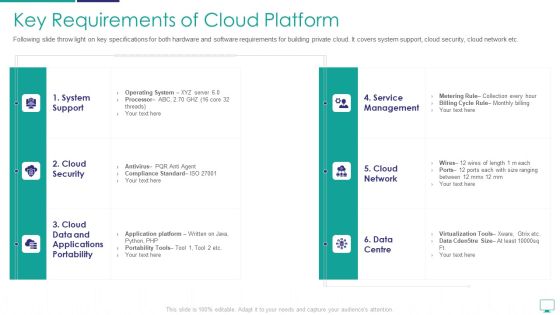
Key Requirements Of Cloud Platform Information PDF
Following slide throw light on key specifications for both hardware and software requirements for building private cloud. It covers system support, cloud security, cloud network etc. Deliver an awe inspiring pitch with this creative key requirements of cloud platform information pdf bundle. Topics like operating system, application platform, compliance standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
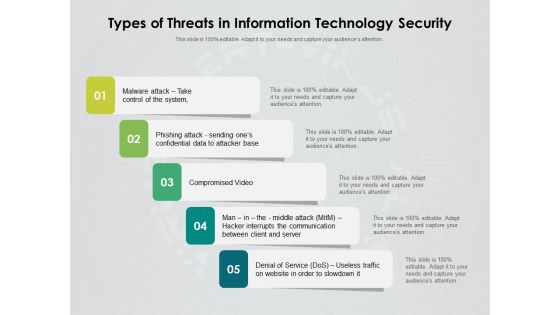
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
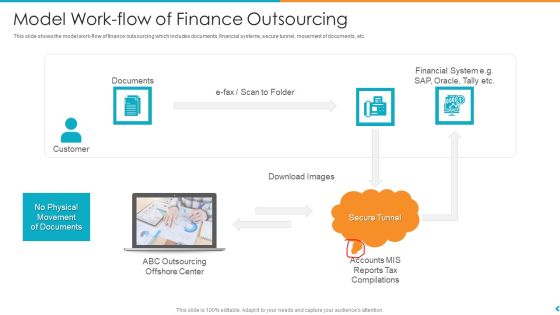
Fund Outsourcing Upgrade Efficiency Efficacy Fund Function Model Work Flow Of Finance Outsourcing Ppt File Template
This slide shows the model work-flow of finance outsourcing which includes documents, financial systems, secure tunnel, movement of documents, etc. This is a fund outsourcing upgrade efficiency efficacy fund function model work flow of finance outsourcing ppt file template template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like documents, financial systems, secure tunnel, movement of documents. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Due Diligence In Amalgamation And Acquisition IT Landscape Evaluation Infographics PDF
Following slide illustrates IT landscape evaluation of target company. Points covered in evaluation are proprietary technology, data and analytics, security and compliance, infrastructure, organization and process, business systems. This is a Due Diligence In Amalgamation And Acquisition IT Landscape Evaluation Infographics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Systems, Proprietary Technology, Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Overview Of Grey Hat Hackers Ppt Infographics Pictures PDF
This slide depicts the grey hat hackers and how they first hack any system, computer, software, or network and then ask for permission. This is a overview of grey hat hackers ppt infographics pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Information Protection Methodologies For Organizational Facilities Demonstration PDF
This slide covers business security methodologies for organizational facilities which are security plan documentation, access control, installing surveillance system and reinforce data security.Presenting Business Information Protection Methodologies For Organizational Facilities Demonstration PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Plan Documentation, Implement Access, Surveillance System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Security Incident Handling Determining Roles And Responsibilities For Risk Handling Mockup PDF
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Determining Roles And Responsibilities For Risk Handling Icons PDF
Presenting this set of slides with name cyber security implementation framework determining roles and responsibilities for risk handling icons pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
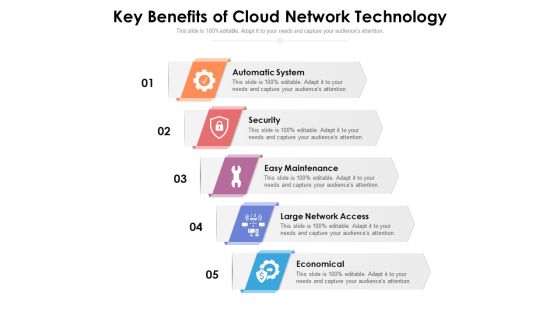
Key Benefits Of Cloud Network Technology Ppt PowerPoint Presentation Show Good PDF
Presenting this set of slides with name key benefits of cloud network technology ppt powerpoint presentation show good pdf. This is a five stage process. The stages in this process are automatic system, security, easy maintenance, large network access, economical. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Security Checklist Security Patches And Updates Summary PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting Cloud Security Checklist Security Patches And Updates Summary PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security Patches, Measures, Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security For Your Organization Determining Roles And Responsibilities For Risk Handling Ppt Outline Example PDF
Presenting this set of slides with name cyber security for your organization determining roles and responsibilities for risk handling ppt outline example pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management, executive, line management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
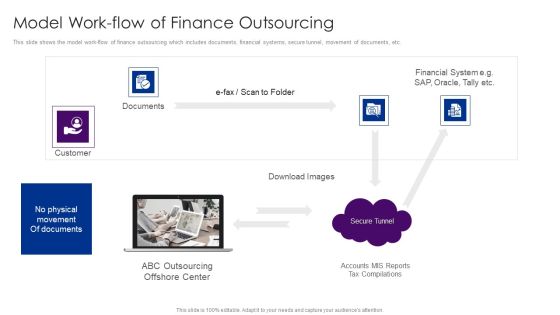
Outsourcing Financial Accounting Solutions For Company Model Work Flow Of Finance Outsourcing Topics PDF
This slide shows the model work-flow of finance outsourcing which includes documents, financial systems, secure tunnel, movement of documents, etc.Deliver an awe inspiring pitch with this creative outsourcing financial accounting solutions for company model work flow of finance outsourcing topics pdf bundle. Topics like download images, movement of documents, financial system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Summary Of Audit And Review Team Findings By Severity Download PDF
This slide summarizes inspection findings by severity of an organization by audit team. It includes findings like attack surface, account security, hardened system, patching etc.Showcasing this set of slides titled Summary Of Audit And Review Team Findings By Severity Download PDF. The topics addressed in these templates are System Hardening, Data Protection, Account Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Governance Icon Ppt PowerPoint Presentation Layouts Rules
This is a security governance icon ppt powerpoint presentation layouts rules. This is a four stage process. The stages in this process are risk management icon, governance icon, compliance icon.

 Home
Home