Safety Management Strategy Ppt

Information Privacy IT Importance Of Data Privacy Professional PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. Presenting information privacy it importance of data privacy professional pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like importance of data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Bring Your Own Device Security Policy Check In Organizations Icon Summary PDF
Persuade your audience using this Bring Your Own Device Security Policy Check In Organizations Icon Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Bring Your Own, Device Security Policy, Check Organizations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Detection Response, Attack Surface, Current Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer Simulation Human Thinking Role Of Cognitive Computing Technology In Financial Services Diagrams PDF
This slide provides information regarding role of cognitive computing technology in financial services by handling numerous customer queries and loan management. Presenting Computer Simulation Human Thinking Role Of Cognitive Computing Technology In Financial Services Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Background, Concerns, Solution, Virtual Agents, Bank Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Blockchain Business Methodology For Business Security Icon Clipart PDF
Persuade your audience using this Blockchain Business Methodology For Business Security Icon Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Business Methodology, Business Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Terrorism Assault Employee Access Control Protocols Diagrams PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated.This is a cyber terrorism assault employee access control protocols diagrams pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distributed Denial Of Service DDOS As Cyber Terrorism Tool You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security Monitoring, Internal Systems, Steering Committee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
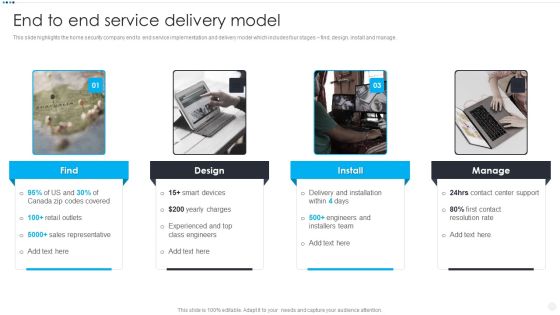
Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage. Presenting Smart Home Security Solutions Company Profile End To End Service Delivery Model Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Delivery And Installation, Contact Center Support, Contact Resolution Rate, Engineers And Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage.Presenting Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sales Representative, Experienced Engineers, Engineers Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Business Analytics Framework Determine Overview Of Established Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Developing Business Analytics Framework Determine Overview Of Established Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Command And Control, Incident Response, Threat Intelligence You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
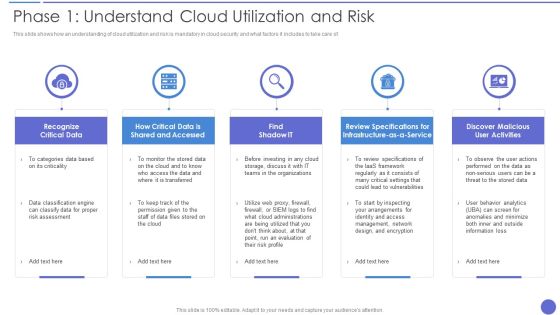
Phase 1 Understand Cloud Utilization And Risk Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. This is a Phase 1 Understand Cloud Utilization And Risk Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Recognize Critical Data, Risk Assessment, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Employee Training Schedule For New CRM System Microsoft PDF
This slide covers the workforce training plan for new CRM software. It includes training details such as session, trainer, trainees, mode, duration, and cost. Presenting Employee Training Schedule For New CRM System Microsoft PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like System Configuration, Lead Management, Data Security . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CIO Role In Digital Evolution Basic IT Professional Skills Required For Digital Transformation Microsoft PDF
This slide shows the major skills that are possessed by an IT professional such as Machine Learning, Data Analysis, DevOps, Mobility Management, Digital Marketing, Data and Digital Security, Digital Literacy etc. Presenting CIO Role In Digital Evolution Basic IT Professional Skills Required For Digital Transformation Microsoft PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Digital Literacy, Data Analysis, Machine Learning. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.This is a Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disaster, Environmental Control Failures, Deliberate Software Attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
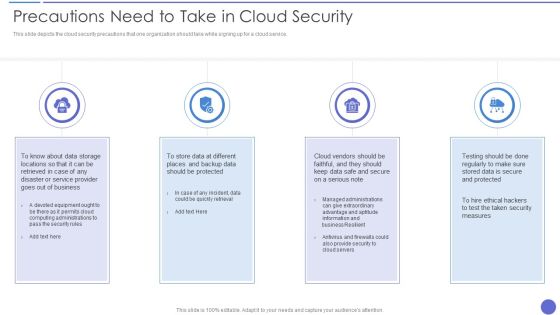
Precautions Need To Take In Cloud Security Template PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. This is a Precautions Need To Take In Cloud Security Template PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Measures, Business Resilient, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
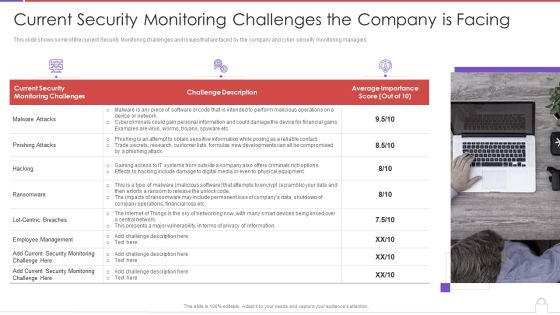
Methods To Develop Advanced Current Security Monitoring Challenges The Company Is Facing Professional PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a methods to develop advanced current security monitoring challenges the company is facing professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current security, monitoring challenges, challenge description, average importance score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Key Portrait PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a continuous development evaluation plan eliminate cyber attacks current security monitoring key portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware attacks, pnishing attacks, ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Initiatives To Produce Effective Concept For Logistic Firm Risks Involved In Technology Formats PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies or Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this initiatives to produce effective concept for logistic firm risks involved in technology formats pdf. Use them to share invaluable insights on connectivity risk, cyber security risk, inventory management risk, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
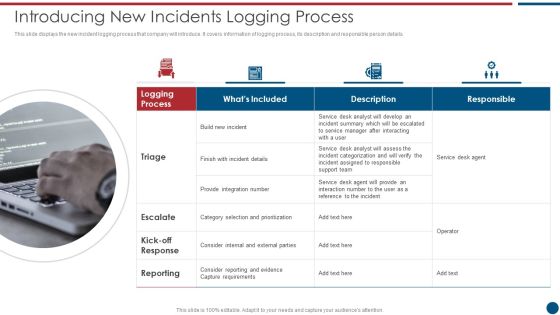
Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. This is a Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Desk, Support Team, Provide Integration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Properties Of Blockchain And Distributed Ledger Technology Mockup PDF
Following slide exhibits blockchain technology properties which shows the complete overview of this technology. Programmable, secure, anonymous, time-stamped, verification and transparency are the core properties covered in this slide. Persuade your audience using this Key Properties Of Blockchain And Distributed Ledger Technology Mockup PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Technology, Individually Encrypted, Kept Anonymous. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment How Does Cloud Security Work Formats PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Security Assessment How Does Cloud Security Work Formats PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Information Against, Transparency, Regulations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
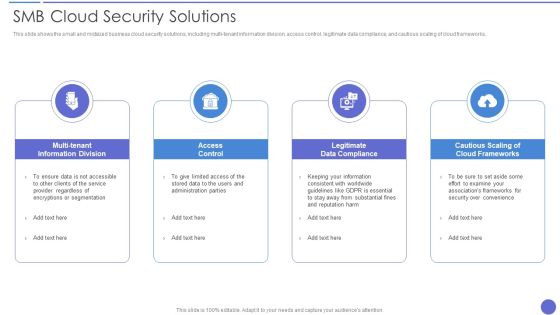
Smb Cloud Security Solutions Download PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. This is a Smb Cloud Security Solutions Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Legitimate Data Compliance, Cloud Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
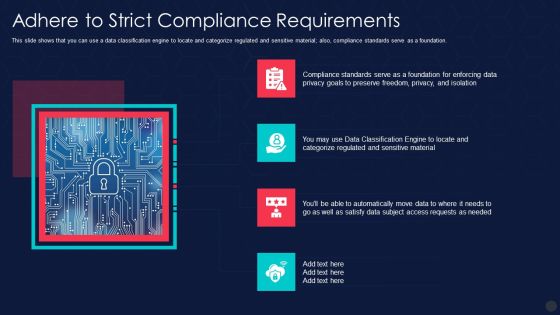
Information Privacy IT Adhere To Strict Compliance Requirements Slides PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. Presenting information privacy it adhere to strict compliance requirements slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like adhere to strict compliance requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Awareness Training Program Challenges Rules PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Presenting Security Awareness Training Program Challenges Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Outdated Content, Burden On Administrators, Employee Participation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. This is a Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Leadership, Evaluation Direction, Change Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Administrative Regulation Obtain The Right Financing For Your Business Investor Pictures PDF
This is a administrative regulation obtain the right financing for your business investor pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like pledge some future earnings, attract angel investor, secure sba loan, raise money family and friends, get microloan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
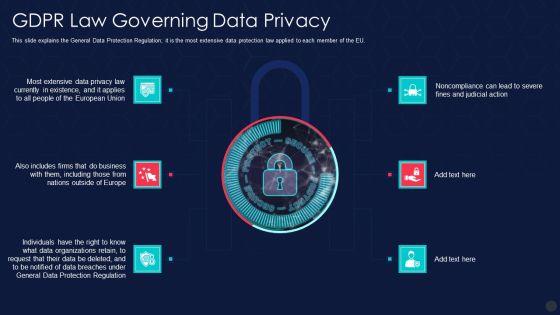
Information Privacy IT Gdpr Law Governing Data Privacy Ideas PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Presenting information privacy it gdpr law governing data privacy ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like gdpr law governing data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc.This is a Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Become A Dependable, Identify C Level Team Members, Make Monthly Reports You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
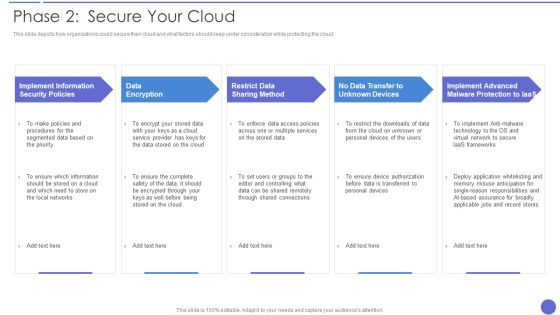
Phase 2 Secure Your Cloud Clipart PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Presenting Phase 2 Secure Your Cloud Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Encryption, Restrict Data Sharing Method, Implement Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Docsend Capital Raising Pitch Deck Revenue Model Pictures PDF
This slide depicts DocSends revenue model which includes corporate branding, team control, data and API access, etc.Presenting Docsend Capital Raising Pitch Deck Revenue Model Pictures PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Advances Security, Corporate Branding, Team Control In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Privacy IT Monitor And Detect Abnormal Activity On Sensitive Data Structure PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Presenting information privacy it monitor and detect abnormal activity on sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like monitor and detect abnormal activity on sensitive data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. This is a IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Better Threat Detection, Faster Containment, Improve Productivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Presenting IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Threat Modeling, Penetration Testing, Bug Bounty. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
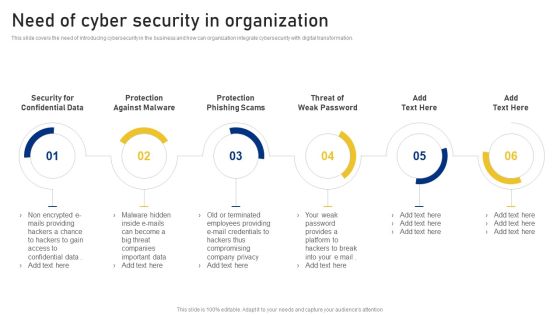
Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Privacy IT Purpose Limitation Principle Of Gdpr Law Topics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Presenting information privacy it purpose limitation principle of gdpr law topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like rpose limitation principle of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. This is a IT Security Automation Tools Integration Security Orchestration Automation And Response Layer Structure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Investigation, Findings, Remediation, Visualization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. This is a New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Applicable, Enforcement, Develop Good. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps To Ensure Robotic Process Automated Security Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a Steps To Ensure Robotic Process Automated Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Protect Log Respectability, Empower Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Outlook Of Social Engineering Attack Brochure PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. This is a Outlook Of Social Engineering Attack Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Engineering Attack, Employees Return, Randomly Selected. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
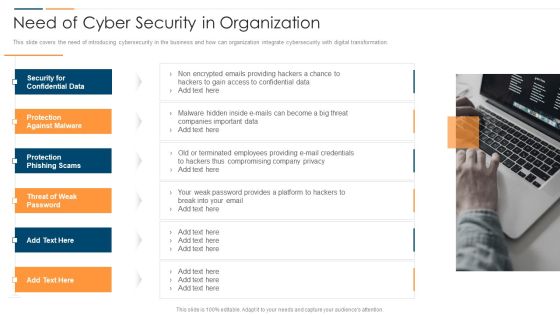
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Processing Services Delivery The Next Generation Operating Model After Implementing Ai Pictures PDF
This slide represents the next generation operating model after implementing AI in the organization and how it would increase the productivity and profit. This is a Data Processing Services Delivery The Next Generation Operating Model After Implementing Ai Pictures PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Sales Reports, Cyber Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

International Organization Standardization 270001 Risk Assessment Worksheet Information PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm. This is a international organization standardization 270001 risk assessment worksheet information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk encountered, vulnerability, asset and consequences. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

AIOPS Implementation Artificial Intelligence For IT Operations In Financial Services Portrait PDF
This slide represents the application of AIOps in financial service that includes defending against complex cybercrimes, analyzing past customer information, data security and regulatory compliance, and so on. Presenting AIOPS Implementation Artificial Intelligence For IT Operations In Financial Services Portrait PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Customer Expectations, Mobile And Digital Banking, Business Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Purpose Of IT Threats Response Playbook Professional PDF
This is a Purpose Of IT Threats Response Playbook Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Standardized Cybersecurity, Future Security, Appropriate Manner. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certified Information Systems Security Collection Of Information Technology Certifications Download PDF
This slide covers CISSP certification details such as what is the CISSP how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting certified information systems security collection of information technology certifications download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like information systems, network security, information network, organization, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Conducting Monetary Inclusion Stakeholders Expectation From Our MFS Ecosystem Clipart PDF
This slide shows various stakeholders expectations from the mobile financial service ecosystem. Stakeholders covered in the table are consumer, employees, mobile network operators, micro finance institutions, agents and regulator. This is a Conducting Monetary Inclusion Stakeholders Expectation From Our MFS Ecosystem Clipart PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Transaction Security, Commission Transactions, Reduce Money. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home