Safety Management Strategy Ppt
Security For Cloud Based Systems Management Icon For IT Project Rules PDF
Persuade your audience using this Security For Cloud Based Systems Management Icon For IT Project Rules PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Management, IT Project. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Payment Service Payment Security And Fraud Management Solutions End Structure PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. This is a online payment service payment security and fraud management solutions end structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like market basket analysis, optimization, geolocation analysis, customer velocity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Training And Building Role Competencies Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, competencies required. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essential Elements To Be Included In A Security Management Plan Slides PDF
Presenting Essential elements to be included in a security management plan slides pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like program management, preparedness, recovery, training, response. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Portrait PDF
Presenting security management plan steps in detail data backup and data loss recovery plan portrait pdf to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like outline business continuity, recovery infrastructure, inventory of the business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Professional PDF
This is a security management plan steps in detail data backup and data loss recovery plan professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security tools, categories of application, data backup frequency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Guidelines To Create An Advanced Security Management Plan 30 60 90 Days Plan Rules PDF
Presenting guidelines to create an advanced security management plan 30 60 90 days plan rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Guidelines To Create An Advanced Security Management Plan Post It Notes Professional PDF
Presenting guidelines to create an advanced security management plan post it notes professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail System Maintenance And Monitoring Sample PDF
Presenting security management plan steps in detail system maintenance and monitoring sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like corrective maintenance, adaptive maintenance, perfective maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF
Presenting Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Current Scenario, Determine Current, Determine Various. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Construction Engineering And Industrial Facility Management Interdependence Resiliency And Security Graphics PDF
This is a construction engineering and industrial facility management interdependence resiliency and security graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Demonstration PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan. Presenting Security management plan steps in detail data backup and data loss recovery plan demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security management plan steps in detail - data backup and data loss recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Customer Relationship Management Software Integration Guide CRM Slide Professional PDF
Presenting Table Of Contents Customer Relationship Management Software Integration Guide CRM Slide Professional PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Organization Details, Customizing Account, Enabling Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Website Programming IT Benefits Of Content Management System In Web Technology Formats PDF
This slide represents the benefits of using a Content Management System in the organization, and it provides features such as on-page SEO, teams collaboration, template making, security, and analytics. This is a website programming it benefits of content management system in web technology formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like seo, collaboration, templates, security, analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cios Value Optimization Addressing Hyperconverged Infrastructure For Data Centre Management Introduction PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. Presenting Cios Value Optimization Addressing Hyperconverged Infrastructure For Data Centre Management Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Agility Simplicity, Multi Cloud Support Data, Protection Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Implement Cloud Collaboration Key Features And Benefits Of Cloud Project Management Clipart PDF
The following slide depicts major features and benefits of cloud based project management. It provides details about reliability, integration, collaboration, secure backup, free monthly trials, remote team support, etc. This is a How To Implement Cloud Collaboration Key Features And Benefits Of Cloud Project Management Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reliability Integration, High Collaboration, Secure Backup. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Healthcare Applications Benefits Of Using Healthcare Data Management Mobile App Clipart PDF
This slide shows the benefits of using healthcare data management mobile app. This includes various benefits of the application to the providers and the customers such as easily availability of health-related information, secure connection, customization, etc. This is a Digital Healthcare Applications Benefits Of Using Healthcare Data Management Mobile App Clipart PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Health Related Information, Secure Connection, Intuitive Interface. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Presenting Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Human Error, Natural Disaster, Deliberate Software Attacks, Environmental Control Failures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
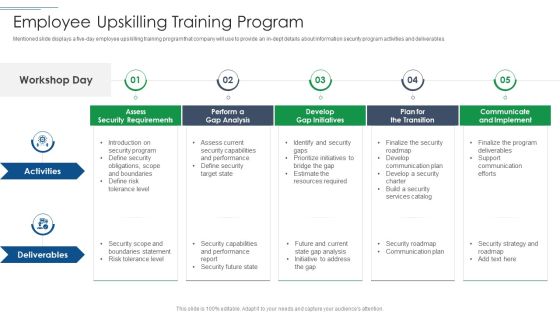
IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. This is a IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Develop Gap Initiatives, Communicate And Implement, Assess Security Requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. Presenting Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Tracking Products, Securing Operations, Managing Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.This is a Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Categorization, Incident Resolution, Incident Prioritization You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
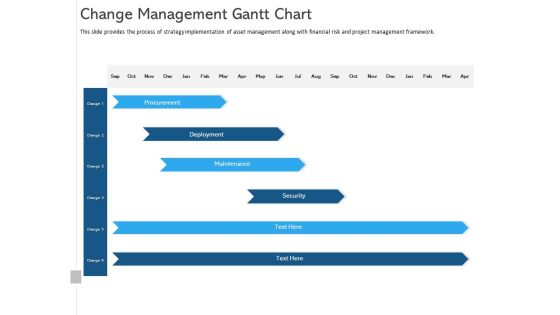
ALM Optimizing The Profit Generated By Your Assets Change Management Gantt Chart Themes PDF
This slide provides the process of strategy implementation of asset management along with financial risk and project management framework. Deliver and pitch your topic in the best possible manner with this alm optimizing the profit generated by your assets change management gantt chart themes pdf. Use them to share invaluable insights on procurement, deployment, maintenance, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
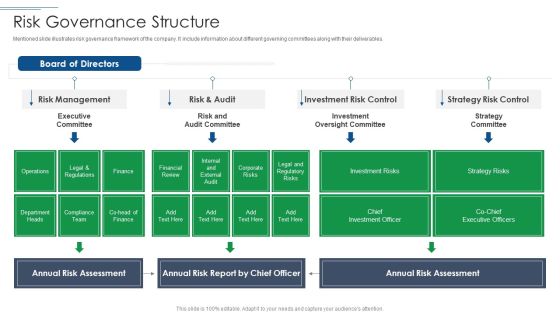
IT Security Risk Management Approach Introduction Risk Governance Structure Mockup PDF
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Risk Governance Structure Mockup PDF. Use them to share invaluable insights on Risk Management, Investment Risk Control, Strategy Risk Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Devops Configuration Management IT Determine Additional Roles Pivotal For Successful Devops Contd Topics PDF
This slide provides information regarding the additional roles considered as pivotal for successful DevOps in terms of software tester developer, security engineer and experience assurance professional. This is a devops configuration management it determine additional roles pivotal for successful devops contd topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like software tester, security engineer, experience assurance professional. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Big Data Architect Tool Selection For Big Data Management Icons PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.This is a Big Data Architect Tool Selection For Big Data Management Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Businesses Frequently, Straight Forward, Either Providing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Techniques To Enhance New Product Management Efficiency Emerging Trends Shaping Inspiration PDF
This slide describes the emerging trends shaping the product development future such as data driven development, digital product ecosystem, distributed teams, security awareness, etc. Presenting best techniques to enhance new product management efficiency emerging trends shaping inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data driven development, digital product ecosystem, distributed teams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Devops Configuration Management IT Addressing Various Trends Associated To Devops Implementation Mockup PDF
This slide provides information regarding various trends associated to DevOps implementation in terms of DevOps automation, using serverless architecture, etc. Presenting devops configuration management it addressing various trends associated to devops implementation mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like devops automation, serverless architecture, embedded security. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Objectives Of Implementing Identify And Access Management Technique Clipart PDF
This slide shows business goals that can be achieved by identification and access management strategy by systematically implementing concerned business activities. It include objectives such as security system, business verticals integration , etc. Showcasing this set of slides titled Business Objectives Of Implementing Identify And Access Management Technique Clipart PDF. The topics addressed in these templates are Business Activities, Impact, Objective. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF. Use them to share invaluable insights on Accidental Intentional, Unauthorized, Critical Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Timeline Showcasing Risk Assessment Process For Construction Project Management Rules PDF
This slide showcases timeline for construction project risk assessment which helps prevent on site accidents and increase employee safety. It provides information regarding identification of risk, evaluate risk impact, develop risk mitigation strategies and monitor construction project performance. Pitch your topic with ease and precision using this Timeline Showcasing Risk Assessment Process For Construction Project Management Rules PDF. This layout presents information on Identification Of Risk, Evaluate Risk Impact, Develop Risk Mitigation Strategies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
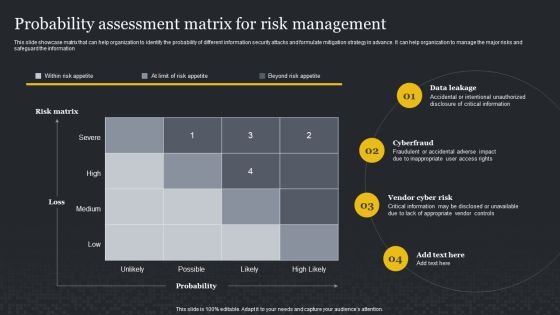
Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Slidegeeks is here to make your presentations a breeze with Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

New Shopper Imperatives To Determine Consumer Preferences Buyers Preference Management Playbook Clipart PDF
This slide provides information regarding new shopper imperatives catered to manage consumer preferences in term of certainty, flexibility, safety, trust, transparency. All imperatives are assessed based on priority of shopper. Deliver an awe inspiring pitch with this creative New Shopper Imperatives To Determine Consumer Preferences Buyers Preference Management Playbook Clipart PDF bundle. Topics like Fulfillment Method, Environmental Consciousness, Manufacturing Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ultimate Guide To Effective Change Management Process Maslow Hierarchy Of Human Needs Pictures PDF
This slide indicates the pyramid for the Maslow hierarchy of needs for individuals. It covers basic needs such as physiological, safety, and security and social needs such as love and belonging, esteem, and self actualization. Also, social media strategy is execution is depicted. This is a ultimate guide to effective change management process maslow hierarchy of human needs pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like existence, structure, community building, personal branding, monetization and optimization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Services Analysis For IT Security Risk Management Company Mockup PDF
The following slide explains various services provided by cybersecurity risk management company. It further includes details such as capability assessment, regulatory response and compliance, etc. Presenting Key Services Analysis For IT Security Risk Management Company Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Capability Assessments, Risk Management, Regulatory Response And Compliance, Strategy And Program Design. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
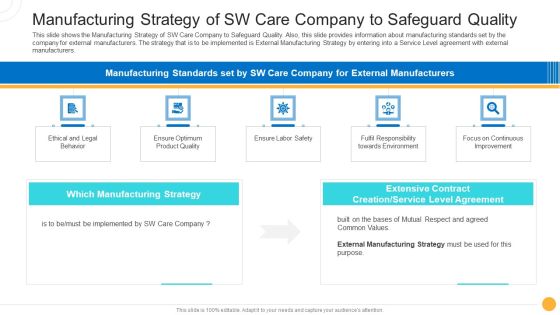
Drug Indicator Extension In A Pharmaceuticals Company Manufacturing Strategy Of SW Care Company To Safeguard Quality Brochure PDF
This slide shows the Manufacturing Strategy of SW Care Company to Safeguard Quality. Also, this slide provides information about manufacturing standards set by the company for external manufacturers. The strategy that is to be implemented is External Manufacturing Strategy by entering into a Service Level agreement with external manufacturers. Presenting drug indicator extension in a pharmaceuticals company manufacturing strategy of sw care company to safeguard quality brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like ethical and legal behavior, optimum product quality, labor safety, responsibility environment, continuous improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
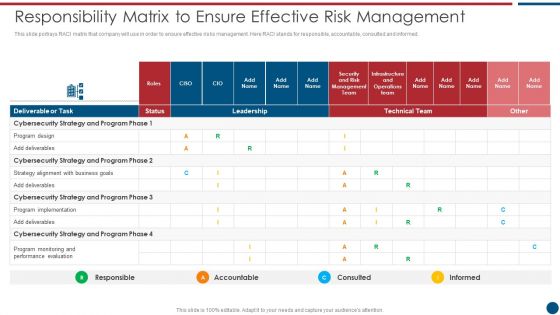
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Reasons For Executing Identify And Access Management Technique Mockup PDF
This slide shows major reasons to execute IAM strategy in organization to ease complexity of management and reducing IT costs. It include reasons such as improved security system, simplifies information sharing and usability sue , etc. Persuade your audience using this Business Reasons For Executing Identify And Access Management Technique Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security System, Information Sharing, Usability Ease. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
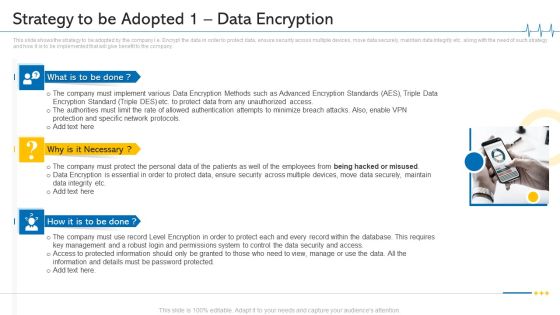
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 1 Data Encryption Microsoft PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting minimize cloud risks medical care business case competition strategy to be adopted 1 data encryption microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protection And Specific Network Protocols, Protect Data, Permissions System, Key Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
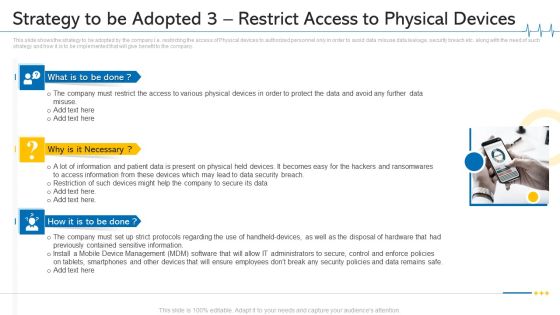
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 3 Restrict Access To Physical Devices Ideas PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. This is a minimize cloud risks medical care business case competition strategy to be adopted 3 restrict access to physical devices ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mobile device management, data security breach, physical devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Diversified Profitable Portfolio Training Plan For Portfolio Management Team Sample PDF
This slide represents training program plan for portfolio management team. It covers capital market and securities analyst, investment management, advance portfolio management etc. Deliver an awe inspiring pitch with this creative Diversified Profitable Portfolio Training Plan For Portfolio Management Team Sample PDF bundle. Topics like Investment Management, Advanced Portfolio Management, Financial Modeling And Valuation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Guidelines To Create An Advanced Security Management Plan Table Of Contents Pictures PDF
Deliver an awe inspiring pitch with this creative guidelines to create an advanced security management plan table of contents pictures pdf bundle. Topics like essential elements, security management challenges, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Essential Elements To Be Included In A Security Management Plan Pictures PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager.Deliver and pitch your topic in the best possible manner with this essential elements to be included in a security management plan pictures pdf. Use them to share invaluable insights on program management, preparedness, response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Service Graphics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security risk assessment worksheet service graphics pdf. Use them to share invaluable insights on monetary loss, reputation loss, loss of customer confidence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
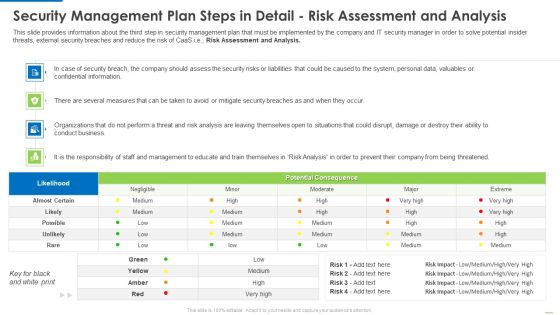
Security Management Plan Steps In Detail Risk Assessment And Analysis Diagrams PDF
Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis diagrams pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF. Use them to share invaluable insights on Identification Assess, Protecting Safeguarding, Detect Threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
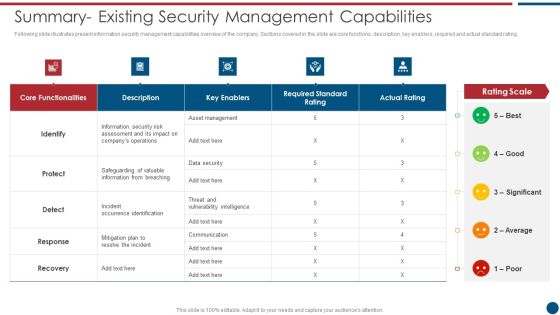
Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
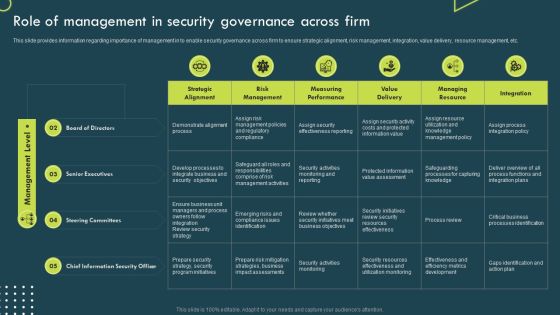
Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF bundle. Topics like Between Failures, Times Attackers, Management Programme can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
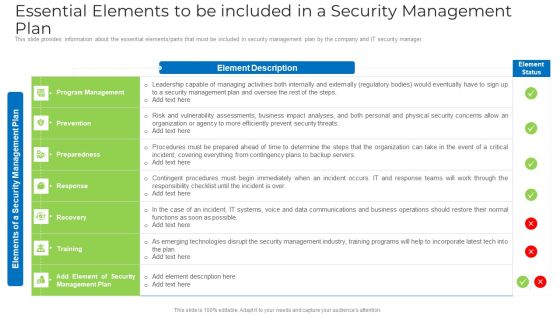
Essential Elements To Be Included In A Security Management Plan Elements PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan elements pdf bundle. Topics like risk, organization, security, systems, data communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Threat Management Action Plan Level Information PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF Use them to share invaluable insights on Assessing Information Security, Safeguarding Valuable, Vulnerability Intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. Explore a selection of the finest Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF. Use them to share invaluable insights on Sprint Report, Product Report, Delivery Method and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Risk Assessment And Analysis Introduction PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver an awe inspiring pitch with this creative security management plan steps in detail risk assessment and analysis introduction pdf bundle. Topics like information, system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home