AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Safety Dashboard
Safety Dashboard

Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF
This slide represents the difference between ITIL v2 and ITIL v3, based on focus, approach, security management, number of processes, and functions.The Comparison Between ITIL V2 And ITIL V3 IT Service Management Framework Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Characteristics Of Software As A Service Saas Pictures PDF
Deliver an awe inspiring pitch with this creative mesh computing technology hybrid private public iaas paas saas workplan characteristics of software as a service saas pictures pdf bundle. Topics like high availability, elastic infrastructure, data security, application security, automated provisioning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Data Security Software Mode Of Communication For Company Online Database Security Proposal Inspiration PDF
Presenting this set of slides with name best data security software mode of communication for company online database security proposal inspiration pdf. The topics discussed in these slides are communicate medium, description. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Your Investment For Company Online Database Security Proposal Slides PDF
Presenting this set of slides with name best data security software your investment for company online database security proposal slides pdf. The topics discussed in these slides are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
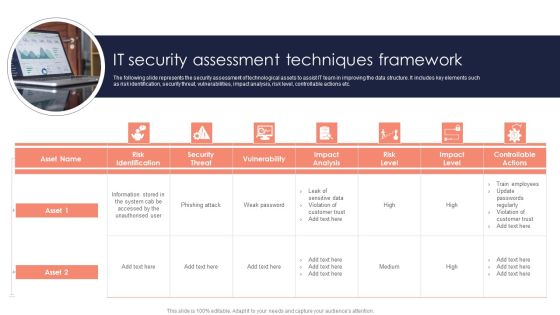
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Threat Report Ppt PowerPoint Presentation Background Cpb Pdf
Presenting this set of slides with name security threat report ppt powerpoint presentation background cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like security threat report to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Information Systems Security And Risk Management Plan Comparison Rules PDF
This graph chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Find highly impressive Information Systems Security And Risk Management Plan Comparison Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Information Systems Security And Risk Management Plan Comparison Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Business Diagrams Templates Umbrella And Symbol PowerPoint Ppt Backgrounds For Slides
We present our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides.Download and present our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Present our Business PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Use our Internet PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Present our Computer PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team.Use these PowerPoint slides for presentations relating to 3d, Access, Business, Close, Computer, Concept, Connection, Data, Digital, Firewall, Global, Guard, Information, Internet, Laptop, Light, Metal, Network, Office, Online, Pc, Personal, Privacy, Protection, Render, Safe, Secure, Security, Shield, Sign, Silver, Steel, Success, Support, Symbol, Technology, Umbrella, Virus, Web. The prominent colors used in the PowerPoint template are Blue, White, Gray. Use our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides will get their audience's attention. We assure you our Digital PowerPoint templates and PPT Slides will get their audience's attention. Use our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Customers tell us our Data PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our business diagrams templates umbrella and symbol PowerPoint PPT backgrounds for slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. PowerPoint presentation experts tell us our Digital PowerPoint templates and PPT Slides will make you look like a winner.

Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Presenting Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Human Error, Natural Disaster, Deliberate Software Attacks, Environmental Control Failures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Recent Global Security Market Trends Behavior Marketing Ppt PowerPoint Presentation Model Slideshow
This is a recent global security market trends behavior marketing ppt powerpoint presentation model slideshow. This is a six stage process. The stages in this process are business, management, marketing.

Data And Customer Analysis Company Outline ESG Highlights Structure PDF
This slide highlights the Nielsen Environmental, Social, and Governance which includes changes in data privacy and security policies, and donation to non-profit organizations Want to ace your presentation in front of a live audience Our Data And Customer Analysis Company Outline ESG Highlights Structure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Data Warehousing IT What Is Cloud Data Warehouse Ppt Styles Background Designs PDF
This slide depicts what a cloud data warehouse is and how it can store data from many data sources and is scalable as per the organizational needs. Deliver and pitch your topic in the best possible manner with this data warehousing it what is cloud data warehouse ppt styles background designs pdf. Use them to share invaluable insights on scalability, reliability, flexibility, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Enabling Data Security Risk Management Action Plan Ppt Slides Icon PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative enabling data security risk management action plan ppt slides icon pdf bundle. Topics like risk, security, information, measures, analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Data Security Software Cover Letter For Company Online Database Security Proposal Designs PDF
Presenting this set of slides with name best data security software cover letter for company online database security proposal designs pdf. This is a one stage process. The stages in this process are cover letter, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Roadmap For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software roadmap for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are roadmap, company, online database security, 2016 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Timeline For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software timeline for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are timeline, company, online database security, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Virtual WAN Architecture Working Of Software Defined Wide Area Network SD WAN Elements PDF
This slide outlines the working of a software-defined wide area network, including the basic sd wan operation. the purpose of this slide is to demonstrate how sd wan works to secure the virtual assets and intellectual property of an organization the main components include branch site, dynamic multipath optimization, etc. There are so many reasons you need a Virtual WAN Architecture Working Of Software Defined Wide Area Network SD WAN Elements PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
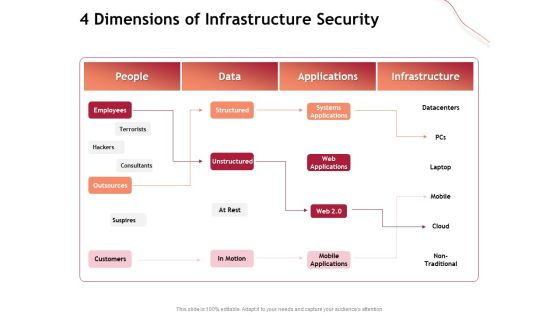
Performance Measuement Of Infrastructure Project 4 Dimensions Of Infrastructure Security Infographics PDF
Presenting this set of slides with name performance measuement of infrastructure project 4 dimensions of infrastructure security infographics pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Management Ppt Diagram Powerpoint Layout
This is a data management ppt diagram powerpoint layout. This is a five stage process. The stages in this process are security service, organizational skills, business skills, backup and recovery, performance tuning.
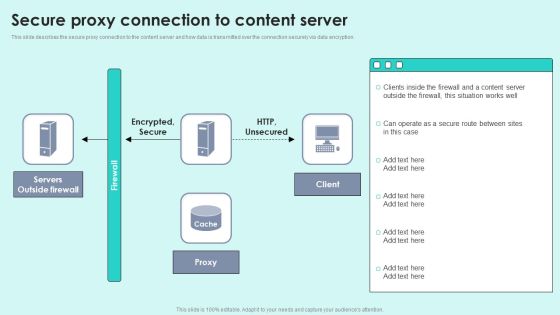
Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Data Security Software Process Flow For Company Online Database Security Elements PDF
Presenting this set of slides with name best data security software process flow for company online database security elements pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, maintain and train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Timeframe For Company Online Database Security Proposal Topics PDF
Presenting this set of slides with name best data security software timeframe for company online database security proposal topics pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Information And Event Management Logging Process Structure PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Data Security Software Next Steps For Company Online Database Security Infographics PDF
Presenting this set of slides with name best data security software next steps for company online database security infographics pdf. This is a two stage process. The stages in this process are discuss the desired changes, accept the proposal, once we get the notification of your proposal acceptance, we will send you the separate copy of the signed contract for your record. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Artificiel Intelligence Components Template Data Ppt PowerPoint Presentation Outline Graphic Images
Presenting this set of slides with name artificiel intelligence components template data ppt powerpoint presentation outline graphic images. This is a three stage process. The stages in this process are technology, marketing, planning, business, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Impact Analysis Implementing Cybersecurity Framework Ppt Model Background PDF
Presenting this set of slides with name cyber security for your organization impact analysis implementing cybersecurity framework ppt model background pdf. This is a one stage process. The stages in this process are csf metric, controls met, trend, target, current, state, performance . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Classification Of Business Data With Restricted Sensitive And Public Ppt PowerPoint Presentation Infographics Icon PDF
Presenting this set of slides with name classification of business data with restricted sensitive and public ppt powerpoint presentation infographics icon pdf. This is a three stage process. The stages in this process are public, sensitive, restricted, levels. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
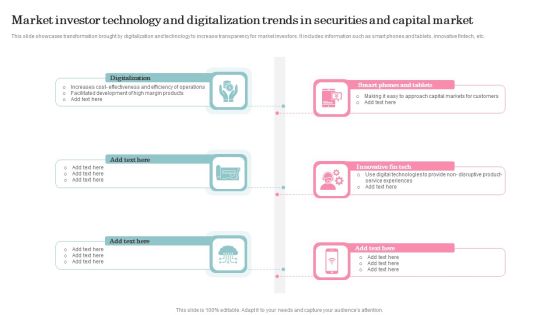
Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF
This slide showcases transformation brought by digitalization and technology to increase transparency for market investors. It includes information such as smart phones and tablets, innovative fintech, etc. Presenting Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF to dispense important information. This template comprises Six stages. It also presents valuable insights into the topics including Digitalization, Innovative Fin Tech. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Services Best Practices Marketing Plan Agenda Need Of Cloud Services In Your Business Demonstration PDF
Presenting cloud services best practices marketing plan agenda need of cloud services in your business demonstration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like operating, costs, growth, data security, flexibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Data Security Software Table Of Contents Introduction PDF
Presenting this set of slides with name best data security software table of contents introduction pdf. The topics discussed in these slides are project context and objectives, our process, your investment, company overview, our past experience, statement of work and contract, next steps. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Services Best Practices Marketing Plan Agenda Determine Your Cloud Journey With Us Data Template PDF
Presenting cloud services best practices marketing plan agenda determine your cloud journey with us data template pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data center, cloud strategy, management, secure, modernize. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Architect Trade Cyber Security Data Ppt PowerPoint Presentation Gallery Layouts
This is a architect trade cyber security data ppt powerpoint presentation gallery layouts. This is a four stage process. The stages in this process are architect trade, cyber security data.
Stock Photo 3d Folders With Key And Lock PowerPoint Slide
Concept of data security has been displayed in this power point image template with suitable graphics. This image contains the graphics of 3d folders and key with lock. Use this PPT image for your data related presentations.
Types Data Security Ppt PowerPoint Presentation Styles Objects Cpb
This is a types data security ppt powerpoint presentation styles objects cpb. This is a ten stage process. The stages in this process are types data security.
Business Diagram Folders In Circular Flow Presentation Template
Our above slide contains graphics of data folders in circular flow. It helps to display concepts like data storage and exchange of information. Use this diagram to impart more clarity to data and to create more sound impact on viewers.

Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Present Concerns Impeding Cybersecurity Clipart PDF
Presenting this set of slides with name cyber security implementation framework present concerns impeding cybersecurity clipart pdf. The topics discussed in these slides are data breaches and records exposed, reported financial losses due to increase cybercrimes, financial losses, cybercrimes incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Security Management Tool Assessment Matrix Microsoft PDF
This slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Persuade your audience using this Data Security Management Tool Assessment Matrix Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Intelligence, Advanced Data Governance, Secure Score. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Cloud Based Email Security Market Industry Trends Ppt Professional Example PDF
Presenting this set of slides with name global cloud based email security market industry trends ppt professional example pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF
This slide covers the grid specifying data risk faced and its mitigation plan. The purpose of this template is to analyze the risk incurred and plans implemented to overcome the same. It also includes elements such as impact, likelihood, metric, threshold, etc.Showcasing this set of slides titled Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF. The topics addressed in these templates are Data Distribution, Secure Computation, Verifiable Computation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CRM Implementation Strategy Securing Our Data With CRM Summary PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a CRM Implementation Strategy Securing Our Data With CRM Summary PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Communication Protection, Restrict Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Big Data Ppt PowerPoint Presentation Background Image
This is a impact of big data ppt powerpoint presentation background image. This is a four stage process. The stages in this process are healthcare, science, security, business.

Topics That Fall Under The Umbrella Of Cloud Security Cloud Computing Security IT Ppt Model Example Introduction PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. Presenting topics that fall under the umbrella of cloud security cloud computing security it ppt model example introduction pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data centre security, threat prevention, access control, threat detection, threat mitigation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Benefits Of Using Healthcare Data Management Mobile App Demonstration PDF
This slide shows the benefits of using healthcare data management mobile app. This includes various benefits of the application to the providers and the customers such as easily availability of health-related information, secure connection, customization, etc.Deliver an awe inspiring pitch with this creative Benefits Of Using Healthcare Data Management Mobile App Demonstration PDF bundle. Topics like Related Information, Secure Connection, Intuitive Interface can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Gallery Example
This is a recent global security market trends behavior ppt powerpoint presentation gallery example. This is a six stage process. The stages in this process are marketing, business, management.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Pictures Shapes
This is a recent global security market trends behavior ppt powerpoint presentation pictures shapes. This is a six stage process. The stages in this process are business, management, marketing.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Professional Picture
This is a recent global security market trends behavior ppt powerpoint presentation professional picture. This is a six stage process. The stages in this process are business, management, marketing.

Latest Trends Of Devops It Determine Different Trends Associated To Devops Industry Option Devops Summary PDF
This slide provides information regarding different DevOps industry trends such as focus on modular approach in building system, reduced deployment time to production, etc. This is a latest trends of devops it determine devops market trends with cagr and market share graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like devops enhance modular approach in building system, devops limits deployment time to production, devsecops implementing security to devops process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Risk Management Model For Data Security Structure PDF
This is a Agenda For Risk Management Model For Data Security Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Effectively Managing, Organizational Risks Arising, Threats And Vulnerabilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Program Icon For Protecting Client Data Ideas PDF
Persuade your audience using this IT Security Program Icon For Protecting Client Data Ideas PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including It Security, Program Icon, Protecting Client Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
