Roadmap Safety

Cloud Intelligence Framework For Application Consumption Developing An Intelligent Infrastructure Diagrams PDF
The slide provides the details about three phases Automation and Orchestration Service Orientation and intelligence of developing an intelligent infrastructure. Presenting cloud intelligence framework for application consumption developing an intelligent infrastructure diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, business processes, technologies and application, service orientation, automation orchestration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
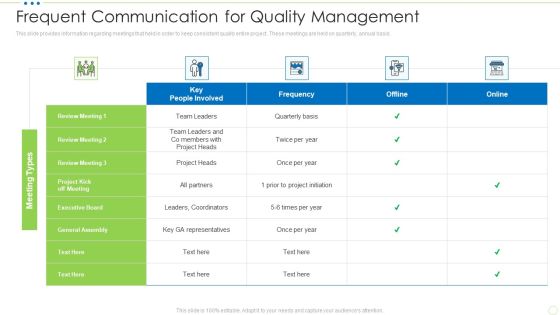
Frequent Communication For Quality Management Food Security Excellence Ppt Portfolio Deck PDF
This slide provides information regarding meetings that held in order to keep consistent quality entire project. These meetings are held on quarterly, annual basis. Deliver and pitch your topic in the best possible manner with this frequent communication for quality management food security excellence ppt portfolio deck pdf. Use them to share invaluable insights on executive board, general assembly, coordinators, project initiation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Quality Check Register Maintenance Food Security Excellence Ppt Outline Shapes PDF
This slide provides information regarding the food quality check register that is to be maintained in order to keep track of quality improvement. The details regarding the quality method used, reviewer, approver is reported. Deliver an awe inspiring pitch with this creative quality check register maintenance food security excellence ppt outline shapes pdf bundle. Topics like quality check register maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Addressing Food Processing Quality Standards Food Security Excellence Ppt Icon Example PDF
This slide provides information regarding the food processing quality standards that are defined in order to manage overall food quality. Deliver an awe inspiring pitch with this creative addressing food processing quality standards food security excellence ppt icon example pdf bundle. Topics like performance, effectiveness, dimensions compliance, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Developing Firm Security Strategy Plan Evaluating Financial Practices In Firm Icons PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an awe inspiring pitch with this creative developing firm security strategy plan evaluating financial practices in firm icons pdf bundle. Topics like evaluating financial practices in firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
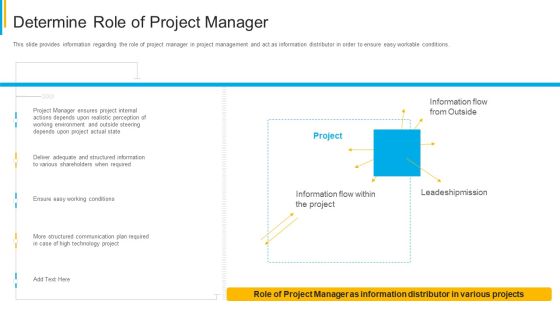
Project Security Administration IT Determine Role Of Project Manager Clipart PDF
This slide provides information regarding the role of project manager in project management and act as information distributor in order to ensure easy workable conditions. Deliver an awe inspiring pitch with this creative project security administration it determine role of project manager clipart pdf bundle. Topics like technology, communication, plan, leadeshipmission, environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
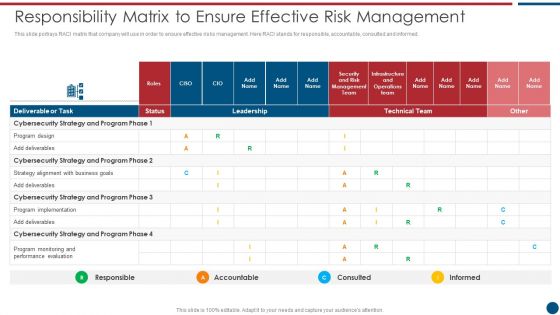
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Storage For Cloud Data Migration Ppt Slides Portrait PDF
This slide represents the use case of cloud storage service in cloud data migration by describing its benefits such as affordability, reliability, availability, and durability. Presenting cloud storage for cloud data migration ppt slides portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, data, services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Why Us For Cloud Storage Ppt Infographic Template Graphics Pictures PDF
This slide describes why organizations choose cloud storage firm as their cloud storage service provider by describing their features that are better than other providers.This is a why us for cloud storage ppt infographic template graphics pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure, applications, implementing, services, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Website Defacements Ddos Template PDF
This slide represents the other attacks carried out by Russia on Ukraine, such as website defacement, distributed denial-of-service attacks, and website clones. This is a russian cyber attacks on ukraine it website defacements ddos template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ukraine Cyberwarfare Website Defacements Ddos Attacks And Website Clones Structure Pdf
This slide represents the other attacks carried out by Russia on Ukraine, such as website defacement, distributed denial of service attacks, and website clones. This is a ukraine cyberwarfare website defacements ddos attacks and website clones structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like the ministry of foreign affairs, the ukrainian parliament, and the security service of ukraine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Content Delivery Network Edge Server Features Of Content Delivery Network Infographics PDF
This slide explains the features of content delivery networks such as protection against DDoS protection, HTTPS services, analytics, etc. Presenting Content Delivery Network Edge Server Features Of Content Delivery Network Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Measures, Advanced Security, Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Rebuild CIBIL To Prevent Bankruptcy Information PDF
This slide showcases ways to rebuild credit information bureau India limited score to overcome bankruptcy . It includes reviewing CIBIL reports regularly , not closing the amounts , applying for a secure credit card , avoid visiting credit repair service etc. Persuade your audience using this Strategies To Rebuild CIBIL To Prevent Bankruptcy Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information, Payments, Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Data Applications In E Commerce Sector Information PDF
The following slide highlights applications of big data in ecommerce to enhance online shopping experience. It covers use cases such as supply chain management, product recommendation, customer service, secure payments, target advertising, and demand forecasting. Presenting Computer Data Applications In E Commerce Sector Information PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Logistics Management, Customer Service, Pricing Optimization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Methods To Develop Major Reasons For Poor Security Monitoring In The Company Information PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver and pitch your topic in the best possible manner with this methods to develop major reasons for poor security monitoring in the company information pdf. Use them to share invaluable insights on improper security maintenance, evolving software, high end software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Role Of Management In Effective Governance Mobile Device Security Management Background PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver and pitch your topic in the best possible manner with this Role Of Management In Effective Governance Mobile Device Security Management Background PDF. Use them to share invaluable insights on Senior Executives, Steering Committees, Effectiveness Reporting and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
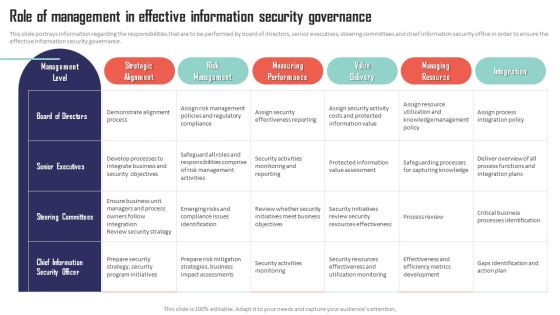
Mobile Device Management Role Of Management In Effective Information Security Microsoft PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Mobile Device Management Role Of Management In Effective Information Security Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Intelligent Infrastructure Determine Capabilities Enabling Intelligent Infrastructure Contd Elements PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. This is a Intelligent Infrastructure Determine Capabilities Enabling Intelligent Infrastructure Contd Elements PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Configuration Automation, Devices And Desktops, Infrastructure Services Analysis, Proactive Analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CRM Software Deployment Journey Implementation Steps Introduction For Identifying Introduction PDF
This slide covers the process of determining the CRM users and creating their roles and profiles in order to maintain data security. Slidegeeks has constructed CRM Software Deployment Journey Implementation Steps Introduction For Identifying Introduction PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
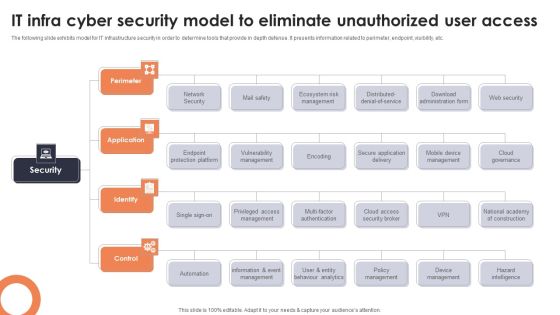
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Digital Transformation Of Consumer Emerging Technological Trends For Banking Company Topics PDF
This slide shows the latest technological trends which should be adopted by the ABC Bank which includes cyber security, upgraded ATMs, Chatbot, Artificial Intelligence etc. Presenting Digital Transformation Of Consumer Emerging Technological Trends For Banking Company Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Cyber Security, Upgraded ATMs, Cloud Computing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

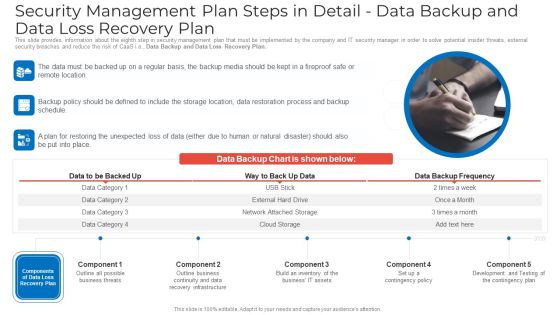
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Demonstration PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan. Presenting Security management plan steps in detail data backup and data loss recovery plan demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security management plan steps in detail - data backup and data loss recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

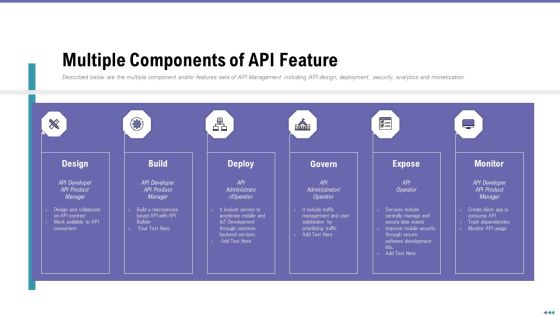
API Outline Multiple Components Of API Feature Ppt Diagram Templates PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. This is a api outline multiple components of api feature ppt diagram templates pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like design, build, deploy, govern, expose. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

API Administration Solution Multiple Components Of API Feature Ppt Professional Influencers PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. This is a api administration solution multiple components of api feature ppt professional influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like design, build, deploy, govern, expose. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Market Viewpoint Application Programming Interface Governance Multiple Components Of API Feature Topics PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. This is a market viewpoint application programming interface governance multiple components of api feature topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like design, build, deploy, govern, expose. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

API Management Market Multiple Components Of API Feature Portrait PDF
Described below are the multiple component and or features sets of API Management including API design, deployment, security, analytics and monetization. Presenting api management market multiple components of api feature portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like govern, monitor, expose, deploy, build, design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Airtable Capital Funding Pitch Deck Our Solution Microsoft PDF
This slide covers key solutions offered by cloud based software company. It involves solutions such as transform workflows with AI, build on flexible data model and offers data security and compliance. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Airtable Capital Funding Pitch Deck Our Solution Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

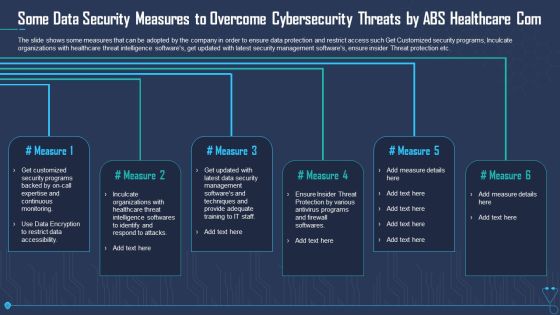
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
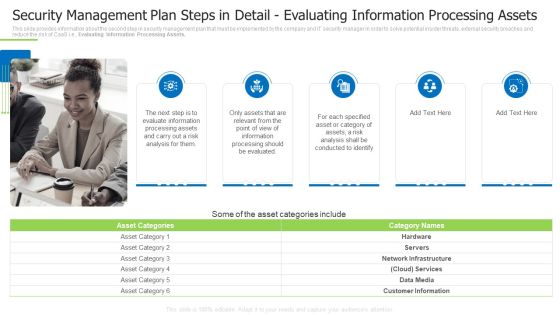
Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
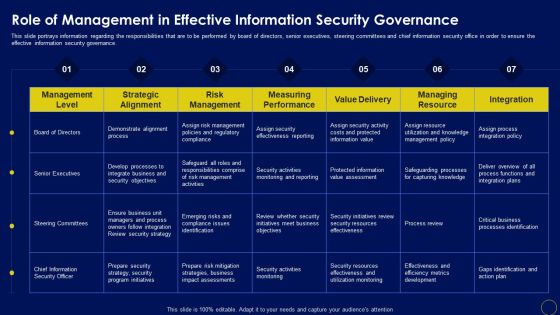
Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
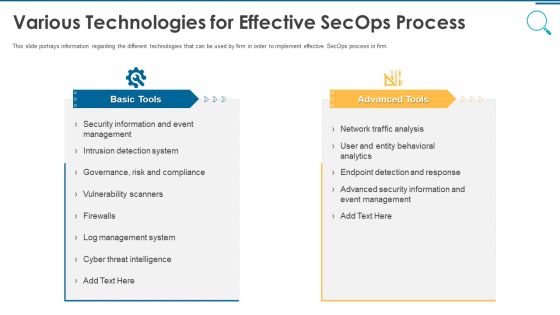
Information And Technology Security Operations Various Technologies For Effective Secops Process Infographics PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a information and technology security operations various technologies for effective secops process infographics pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Security Solutions Various Technologies For Effective Secops Process Designs PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a organizational security solutions various technologies for effective secops process designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
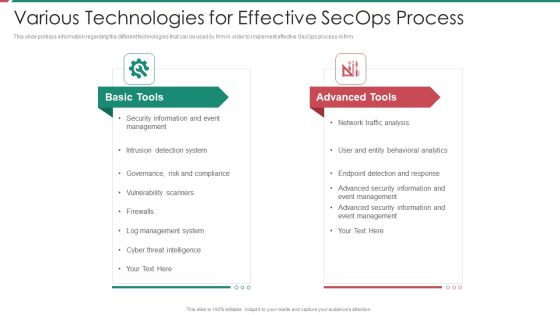
Security And Process Integration Various Technologies For Effective Secops Process Clipart PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. This is a security and process integration various technologies for effective secops process clipart pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like basic tools, advanced tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Addressing Frequent Communication For Project Quality Management Icons PDF
This slide provides information regarding meetings that held in order to keep consistent quality entire project. These meetings are held on quarterly, annual basis. Presenting project security administration it addressing frequent communication for project quality management icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like executive, leaders, coordinators, initiation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Ensuring Vital Records Maintenance Topics PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization ensuring vital records maintenance topics pdf. Use them to share invaluable insights on ensuring vital records maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secured Video Hosting Platform Investor Capital Funding Solutions Provided By Online Video Hosting Platform Introduction PDF
This slide caters details about solutions rendered by video hosting platform in order to solve issues by providing platform to upload videos and video conversion for accessibility. Presenting secured video hosting platform investor capital funding solutions provided by online video hosting platform introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like solutions provided by online video hosting platform. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Vital Records Maintenance Summary PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver an awe inspiring pitch with this creative corporate security and risk management ensuring vital records maintenance summary pdf bundle. Topics like ensuring vital records maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Evaluating Financial Practices In Firm Graphics PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. This is a corporate security and risk management evaluating financial practices in firm graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluating financial practices in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Integrating Data Privacy System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in sixty four slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Use this Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing Information Technology Security Awareness Training Program For Employees Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides
Use this Developing IT Security Strategy To Prevent Data Assets Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy one slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Increasing Information Security Awareness In Company Using Various Techniques Complete Deck
Use this Increasing Information Security Awareness In Company Using Various Techniques Complete Deck to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in fifteen slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
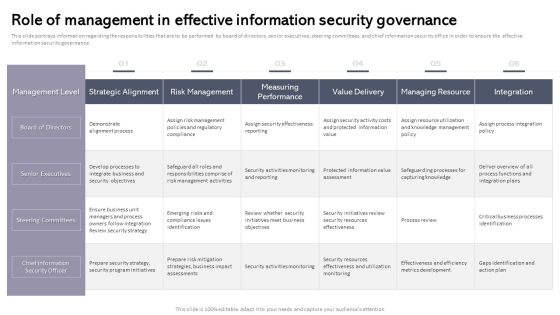
Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Retrieve professionally designed Workplace Portable Device Monitoring And Administration Role Of Management In Effective Information Security Governance Inspiration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Slidegeeks is here to make your presentations a breeze with Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Issues Addressed By Dcaas Elements PDF
This slide brings forth various issues which are addressed by data service centers to provide users a solution in order to improve current business performance. The various issues addressed are data management, hyper converged infrastructure, data security and file storage. Presenting Issues Addressed By Dcaas Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Management, Data Security, Converged Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home