Roadmap Safety

Information Security Data Privacy In Healthcare Ppt PowerPoint Presentation File Layouts PDF
This slide represents data privacy in the healthcare industry, decreasing risks and keeping the business operations functioning. There are so many reasons you need a Information Security Data Privacy In Healthcare Ppt PowerPoint Presentation File Layouts PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Addressing Various Food Quality Management Tools Food Security Excellence Ppt Inspiration Example PDF
This slide provides information regarding various quality tools that can be used by firm in checking food and process quality such as scatter diagrams, histogram, process flow charts, pareto charts. This is a addressing various food quality management tools food security excellence ppt inspiration example pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like scatter diagrams, histogram, process flow charts, pareto chart. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF
template covers guidelines to drive unpaid traffic with Search engine optimization. It also depicts that SEO is the process of optimizing webpages so that they rank higher in search engines.Presenting Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Relevant Information, Inbound Outbound, Engage Positively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Collaboration Plan Key Activities Information PDF
This slide presents a schedule timeline for tracking and monitoring key activities in order to successful completion of project. Its key tasks includes combined event action plan, short term security generation, competitive intelligence processes, branding, linking contacts in datasets, etc. Showcasing this set of slides titled Business Collaboration Plan Key Activities Information PDF. The topics addressed in these templates are Branding, Acquisition Positioning, Partners Communication, Short Term Security Generation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Online Settlement Revolution Payment Security And Fraud Management Solutions Analysis Ppt Slides File Formats PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions analysis ppt slides file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like before the payment, on the payment page, after the payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

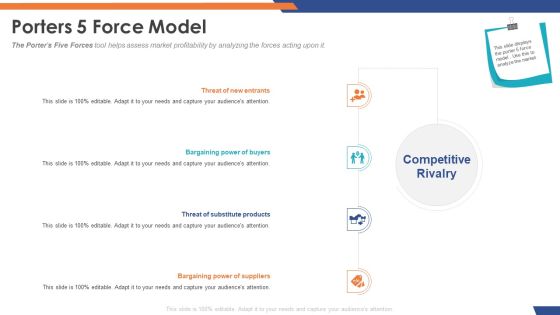
Cloud Based Email Security Market Report Porters 5 Force Model Ppt Inspiration Sample PDF
The Porters Five Forces tool helps assess market profitability by analyzing the forces acting upon it. This is a cloud based email security market report porters 5 force model ppt inspiration sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat of new entrants, bargaining power of buyers, threat of substitute products, bargaining power of suppliers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
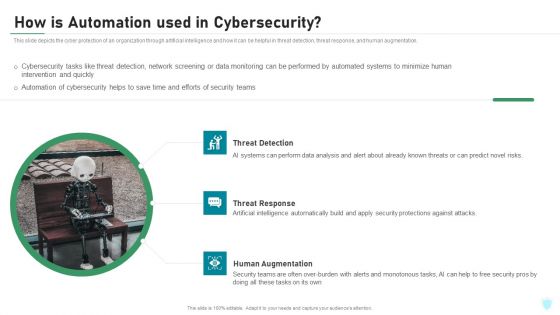
How Is Automation Used In Cybersecurity IT Security IT Ppt Topics PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. This is a how is automation used in cybersecurity it security it ppt topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat detection, threat response, human augmentation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Dispose Data And Equipment Properly Ppt Infographics Styles PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information security dispose data and equipment properly ppt infographics styles pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Minimize Administrative And Staff Privileges Ppt Slides Pictures PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a information security minimize administrative and staff privileges ppt slides pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Prepare A Disaster Recovery Plan Ppt Model Aids PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting information security prepare a disaster recovery plan ppt model aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, location, risk assessment report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization roles and responsibilities to ensure work environment slides pdf
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a cyber security administration in organization roles and responsibilities to ensure work environment slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsibilities, manager, assessment, manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Types Of Latest Threats In Electronic Information Security Ppt Portfolio Icon PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a cybersecurity types of latest threats in electronic information security ppt portfolio icon pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Redis Cache Data Structure IT Implement Traffic Monitoring To Secure Redis Server Ideas PDF
This slide describes implementing traffic monitoring to check the usage patterns and raise flags to incase anything unusual happens. Presenting redis cache data structure it implement traffic monitoring to secure redis server ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, system, location. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Secured Video Hosting Platform Investor Capital Funding Addressing Purpose Defining Brand And Culture Graphics PDF
This slide caters details about purpose that act as a driving force in enabling firm in defining its brand and culture and it caters details about the three mantras that reflect its purpose in market. Presenting secured video hosting platform investor capital funding addressing purpose defining brand and culture graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like upload content, browse content, share content. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
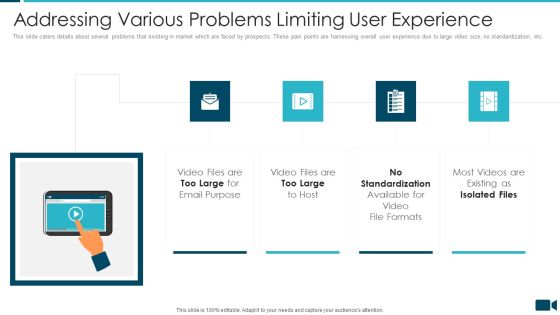
Secured Video Hosting Platform Investor Capital Funding Addressing Various Problems Limiting User Experience Topics PDF
This slide caters details about several problems that existing in market which are faced by prospects. These pain points are harnessing overall user experience due to large video size, no standardization, etc. This is a secured video hosting platform investor capital funding addressing various problems limiting user experience topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like addressing various problems limiting user experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
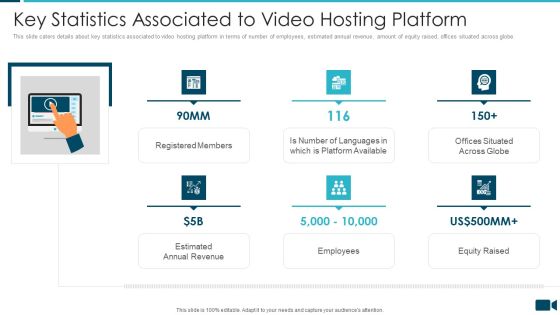
Secured Video Hosting Platform Investor Capital Funding Key Statistics Associated To Video Hosting Platform Rules PDF
This slide caters details about key statistics associated to video hosting platform in terms of number of employees, estimated annual revenue, amount of equity raised, offices situated across globe. Presenting secured video hosting platform investor capital funding key statistics associated to video hosting platform rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like registered members, employees, equity raised, estimated annual revenue. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Indicators Associated To Insider Cyber Threats Topics PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. This is a corporate security and risk management addressing indicators associated to insider cyber threats topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like excessive orphaned files or user accounts, no proper authentication levels, data exfiltration . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Prepare Data Backup For Sensitive Information Ppt Portfolio Slide Download PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Presenting it security prepare data backup for sensitive information ppt portfolio slide download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prepare data backup for sensitive information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
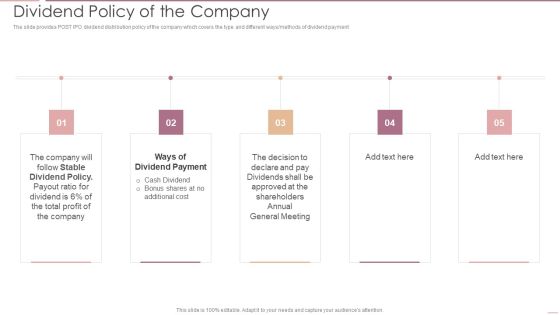
Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF
The slide provides POST IPO dividend distribution policy of the company which covers the type and different ways methods of dividend payment.Presenting Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Stable Dividend, Dividend Payment, General Meeting In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF
This template covers first step for LinkedIn marketing such as update company profile and position the company account according to the target audience. This is a Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Profiles Position, Target Audience, Account According. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF
This template covers account based marketing strategy such as create content that provide value to the customers. It also depicts that Different types of target accounts require additional content focuses.Presenting Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Competitors Customers, Strategic Importance, Different. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF
This template covers content creation tactics in account based marketing such as launching multi touch campaigns, use of marketing automated tools etc.This is a Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Campaign Launch, Campaign Workflow, Ensure Prospects. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF
This template covers the email marketing strategy to leverage the in house email database for email automation, customer retargeting and audience creation. Presenting Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Communications Towards, Automated Messages, Social Platforms. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF
This template covers search engine optimization guidelines for images. It also depicts that Alt Attributes must be added at backend of the images to assists search engine crawlers in indexing. This is a Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Descriptions, Search Engine, Assisting Indexing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF
This template covers the use of automated software for email marketing. It also depicts that email marketing platforms engage allows users to create multiple sales flow with combination of manual and automated emails and phone calls.Presenting Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Combination Manual, Leads Prioritize, Identify Most. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF
This template depicts that Facebook Ads needs three parts to run such as a campaign, ad set, and ad. All these parts are called campaign structure and help run ads the way the company wants and reach the right prospects.his is a Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Powerful Consisting, Features Campaigns, Define Creative. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. This is a IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Customers, Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Restrictions, Internet Settings, Additional Settings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
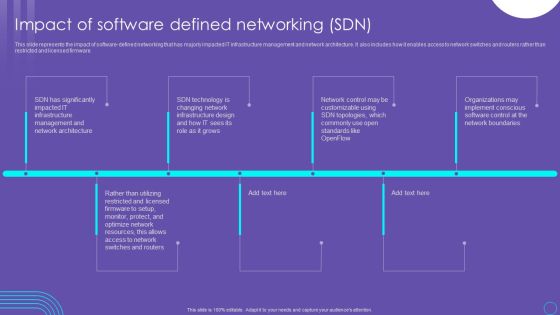
SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF
This slide represents the impact of software defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF from Slidegeeks and deliver a wonderful presentation.

Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF
This slide showcases obstacles faced in bring your own device and with tips for solutions. It also includes obstacles such as device loss, malicious mobile apps, insecure cloud based storage systems, etc. Presenting Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Challenges, Mitigation Tips, Malicious Mobile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Strategy Role Of Chief Information Security Officer Rules PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. This is a information technology strategy role of chief information security officer rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information, stay informed, monthly reports. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF
The following slide highlights multiple solutions to prevent security risks and issues. It also includes elements such as risk evaluation, security awareness, checklist, policies and regulation, recovery plan etc. Presenting Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk Evaluation, Security Awareness, Security Checklist, Policies And Regulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
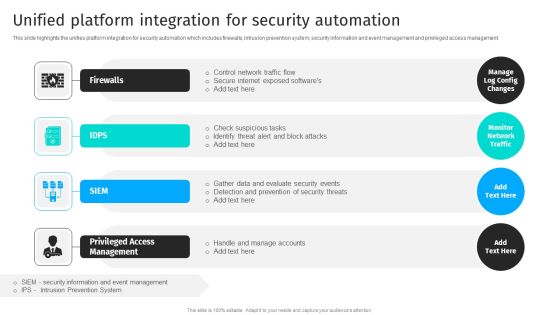
Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management.The Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Machine Driven Learning Anywhere Machine Driven Learning Tool Ppt Layouts Samples PDF
This slide defines the automation anywhere tool for robotic process automation and its pros and cons. It also covers the features of the tool that are intelligent automation, valuable insight and security. Presenting machine driven learning anywhere machine driven learning tool ppt layouts samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like services, organizations, security, analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
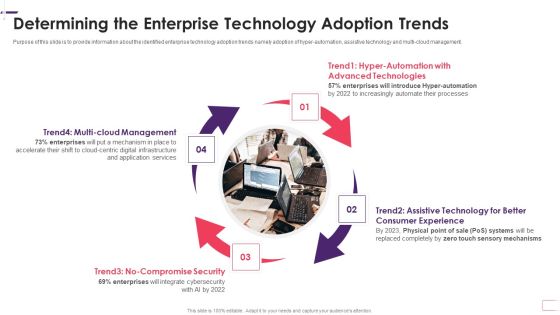
Determining The Enterprise Technology Adoption Trends Demonstration PDF
Purpose of this slide is to provide information about the identified enterprise technology adoption trends namely adoption of hyper automation, assistive technology and multi-cloud management. Presenting determining the enterprise technology adoption trends demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, services, application, enterprises, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

About Us NFT Trading Platform Ppt File Model PDF
This slide represents our company which caters to many renowned businesses and even individuals to trade NFTs and cryptocurrencies securely. This is a about us nft trading platform ppt file model pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, services, businesses, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
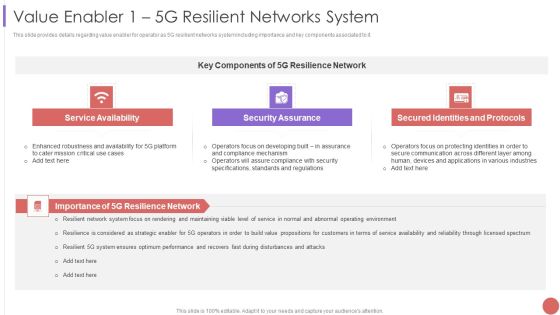
Value Enabler 1 5G Resilient Networks System Professional PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Value Enabler 1 5G Resilient Networks System Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Availability, Security Assurance, Secured Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Elements PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. This is a Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Elements PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service, Security Incidents, Team Productivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
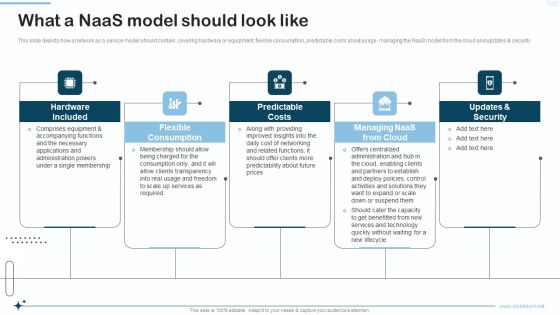
Naas Integrated Solution IT What A Naas Model Should Look Like Brochure PDF
This slide depicts how a network as a service model should contain, covering hardware or equipment, flexible consumption, predictable costs about usage, managing the NaaS model from the cloud and updates and security. This is a Naas Integrated Solution IT What A Naas Model Should Look Like Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Flexible Consumption, Predictable Costs, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational And Business Benefits Presentation Backgrounds
This is a operational and business benefits presentation backgrounds. This is a seven stage process. The stages in this process are vision, plan, design, build, deliver, operate, people change and learning, process and package, business intelligence, information technology, security and controls, tax.

Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. The Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. The Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. The Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Business Intranet For Secure Communication Vector Icon Ppt PowerPoint Presentation Infographic Template Design Ideas PDF
Presenting business intranet for secure communication vector icon ppt powerpoint presentation infographic template design ideas pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business intranet for secure communication vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Explore a selection of the finest Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Employee Engagement Model With Recognition And Security Ppt File Templates PDF
Persuade your audience using this employee engagement model with recognition and security ppt file templates pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including recognition, exciting work, security, education, conditions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
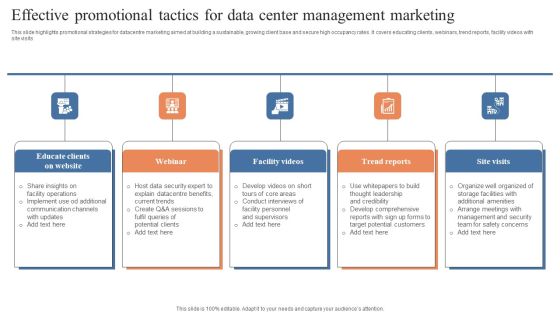
Effective Promotional Tactics For Data Center Management Marketing Rules PDF
This slide highlights promotional strategies for datacentre marketing aimed at building a sustainable, growing client base and secure high occupancy rates. It covers educating clients, webinars, trend reports, facility videos with site visits . Presenting Effective Promotional Tactics For Data Center Management Marketing Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Educate Clients Website, Facility Videos, Trend Reports. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. The Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. The Information Security Monitor Access To Sensitive And Regulated Data Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
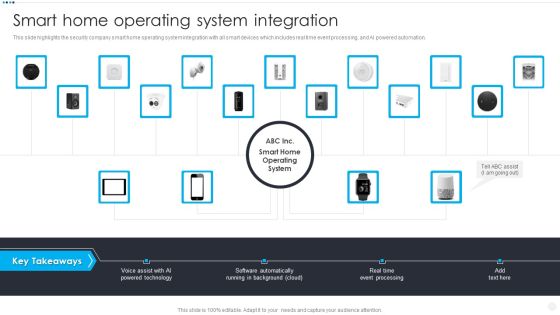
Smart Home Security Solutions Company Profile Smart Home Operating System Integration Elements PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. This is a Smart Home Security Solutions Company Profile Smart Home Operating System Integration Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Voice Assist AI, Powered Technology Software, Automatically Running Background. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Three Stages Of Network Security Management Ppt PowerPoint Presentation Layouts Influencers PDF
Presenting three stages of network security management ppt powerpoint presentation layouts influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Phases Of Network Security Issues Ppt PowerPoint Presentation Icon Portrait PDF
Presenting three phases of network security issues ppt powerpoint presentation icon portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Security Analysis Process With Audit And Mitigate Ppt PowerPoint Presentation File Pictures PDF
Presenting this set of slides with name business security analysis process with audit and mitigate ppt powerpoint presentation file pictures pdf. This is a six stage process. The stages in this process are monitor, analysis, mitigate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Functioning Centre Timeframe For Incident Management Ppt Slides Template PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. This is a security functioning centre timeframe for incident management ppt slides template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeframe for incident management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Four Linear Options Tags Powerpoint Template
Our PowerPoint template has been designed with graphics four linear options tags. This business diagram relates to concept of process control and security. Grab center stage with this slide
Three Seps Of Enterprise Network Security With Icons Ppt PowerPoint Presentation Icon Slide Portrait PDF
Presenting three seps of enterprise network security with icons ppt powerpoint presentation icon slide portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, scope contain remediate, detect block defend. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
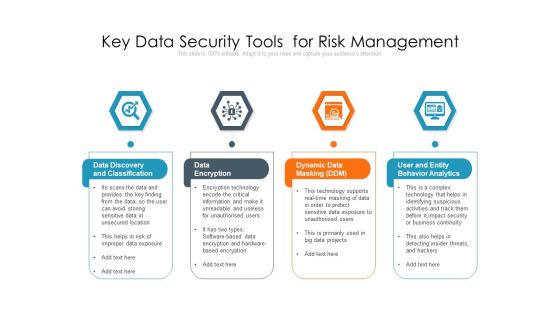
Key Data Security Tools For Risk Management Ppt PowerPoint Presentation Outline Guide PDF
Persuade your audience using this key data security tools for risk management ppt powerpoint presentation outline guide pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including data discovery and classification, data encryption, dynamic data masking ddm, user and entity behavior analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF
Persuade your audience using this Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Report, Declare, Remediate, Close, Respond, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
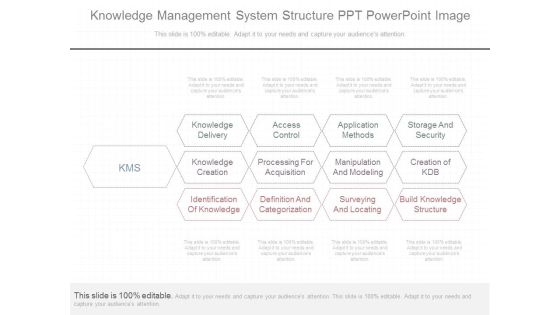
Knowledge Management System Structure Ppt Powerpoint Image
This is a knowledge management system structure ppt powerpoint image. This is a three stage process. The stages in this process are knowledge delivery, access control, application methods, storage and security, knowledge creation, processing for acquisition, manipulation and modeling, creation of kdb, identification of knowledge, definition and categorization, surveying and locating, build knowledge structure, kms.

Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
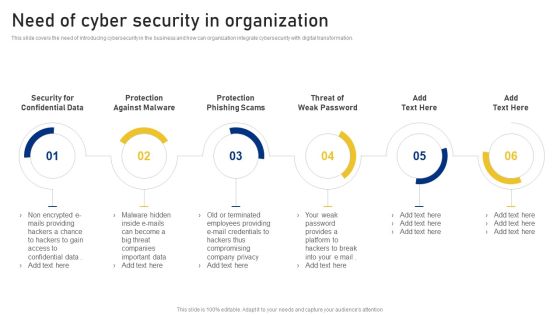
Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
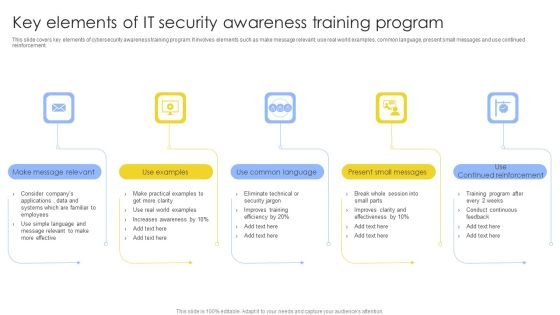
Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF
This slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Presenting Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Make Message Relevant, Use Examples, Use Common Language. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Alert On Computer Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Computer PowerPoint Templates because they pinpoint the core values of your organisation. Use our Technology PowerPoint Templates because these ideas abound in the strong branches of your brain. Download our Signs PowerPoint Templates because health of the determines the quality of our lives. Present our Business PowerPoint Templates because your fledgling career is in the chrysallis stage. Nurture it and watch it grow into a beautiful butterfly. Download and present our Triangles PowerPoint Templates because it unravels each one for your audience while setting key timelines as you go along.Use these PowerPoint slides for presentations relating to Alert button on a black computer keyboard, computer, technology, signs, business, triangles. The prominent colors used in the PowerPoint template are Red, Black, Yellow. We assure you our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Customers tell us our keyboard PowerPoint templates and PPT Slides are Classic. You can be sure our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Beautiful. People tell us our a PowerPoint templates and PPT Slides are Splendid. Presenters tell us our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Adorable. People tell us our technology PowerPoint templates and PPT Slides are Efficient.

Determine Different Trends Associated To Devops Industry Option Software Graphics PDF
This slide provides information regarding different DevOps industry trends such as focus on modular approach in building system, reduced deployment time to production, etc. This is a determine different trends associated to devops industry option software graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like programming, software, implementation, design, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Template PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge or problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a way to overcome security monitoring challenges setting up an advanced cybersecurity template pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like establish security, monitoring strategy, supporting policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3Rd Party API Integration To Check Security Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting 3rd party api integration to check security ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including check security, implementation, mission. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Show Infographics
This is a analysis and valuation of equity securities ppt powerpoint presentation show infographics. This is a three stage process. The stages in this process are industry analysis, financial statement analysis, management, marketing, business, strategy.
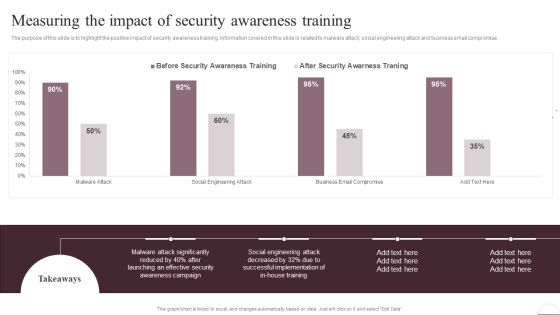
Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. The Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
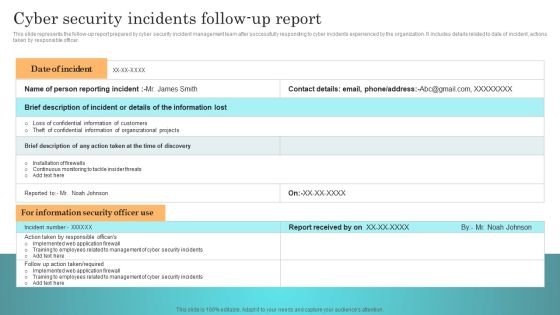
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Identity Based Security Access Management Ppt PowerPoint Presentation Gallery Background Cpb
Presenting this set of slides with name identity based security access management ppt powerpoint presentation gallery background cpb. This is an editable Powerpoint five stages graphic that deals with topics like identity based security access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Monitoring Management Security Ppt PowerPoint Presentation Summary Clipart Images Cpb
Presenting this set of slides with name network monitoring management security ppt powerpoint presentation summary clipart images cpb. This is an editable Powerpoint five stages graphic that deals with topics like network monitoring management security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Financial Security Concept Padlock And Dollars PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Financial Security Concept Padlock And Dollars PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Future PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners. Download and present our Money PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are endowed to endure. Ideas conveyed through them will pass the test of time.Use these PowerPoint slides for presentations relating to dollar currency notes with lock and chain, future, money, chains, finance, shapes. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
Risk Contingency Plan Example With Security Controls Ppt PowerPoint Presentation File Outline
Presenting this set of slides with name risk contingency plan example with security controls ppt powerpoint presentation file outline. This is a six stage process. The stages in this process are risk framework, risk management, planning process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Categorization Of Cyber Risks Ppt Gallery Template PDF
Presenting this set of slides with name computer security incident handling categorization of cyber risks ppt gallery template pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF
The following slide depicts fraud alert and case management approach. It provides information about anti money laundering, transaction monitoring system, request for information, fraud detection, suspicious activity reporting SAR, etc. The KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Current Trends In Information Technology Template Powerpoint Slide
This is a current trends in information technology template powerpoint slide. This is a eight stage process. The stages in this process are network management, programming, scalable architecture, cloud computing, data governance, data analytics, data quality, security.
Email Security Market Research Report Porters 5 Force Model Designs PDF
Presenting this set of slides with name email security market research report porters 5 force model designs pdf. This is a four stage process. The stages in this process are threat of substitute products, bargaining power of suppliers, bargaining power of buyers, threat of new entrants. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Porters 5 Force Model Designs PDF
Presenting this set of slides with name global cloud based email security market porters 5 force model designs pdf. This is a four stage process. The stages in this process are threat of substitute products, bargaining power of suppliers, bargaining power of buyers, threat of new entrants. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Operations Compliance And Security Testing Ppt PowerPoint Presentation Slides Master Slide
This is a operations compliance and security testing ppt powerpoint presentation slides master slide. This is a three stage process. The stages in this process are quality assurance, quality analysis, qa, testing process, bugs analysis.

Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF
This slide covers cyber security incident response KPI dashboard. It involves details such as intent alarm, event trend sources, event trend, sensor activity, major operating systems and asset information. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF. This layout presents information on Top Alarms Method, Alarms Intent, Timely Event Trend. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Example Of Internet Of Things Security Problems Ppt Sample Ppt Files
This is a example of internet of things security problems ppt sample ppt files. This is a four stage process. The stages in this process are things, gateway, network, cloud.

Corporate Security And Risk Management Financial Performance Tracking Dashboard Introduction PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an awe inspiring pitch with this creative corporate security and risk management financial performance tracking dashboard introduction pdf bundle. Topics like revenue and expense trends, receivables analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Steps Of Online Security With Icons Ppt PowerPoint Presentation Gallery Portfolio PDF
Presenting this set of slides with name steps of online security with icons ppt powerpoint presentation gallery portfolio pdf. This is a eight stage process. The stages in this process are mobile security, computer security, secure payment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Trends Influencing HR Automation Software And Processes Infographics PDF
The following slide highlights the business trends influencing human resource automation. It showcases remote teams, cloud based hr, recruitment experience, learning and development, analytics and data security. Presenting Business Trends Influencing HR Automation Software And Processes Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Recruitment Experience, Remote Teams, Learning And Development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Top Trends In Database Management Template Presentation Design
This is a top trends in database management template presentation design. This is a three stage process. The stages in this process are databases in the cloud, automated management, an increased focus on security.

Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Compliance Set Of Icons Ppt PowerPoint Presentation Infographics Graphics Tutorials
Presenting this set of slides with name security compliance set of icons ppt powerpoint presentation infographics graphics tutorials. This is a six stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Addressing Various Trends Associated To Devops Implementation Clipart PDF
This is a addressing various trends associated to devops implementation clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like devops automation, using serverless architecture, focus on embedded security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Consumer Finance Areas Of Expertise Ppt Presentation Slide
This is a consumer finance areas of expertise ppt presentation slide. This is a ten stage process. The stages in this process are product regulation, payment services, governance risk and compliance, dispute resolution and contentious regulatory, portfolio transfers and acquisitions, asset finance, retail finance, digital banking, fraud financial crime and corruption, secured recoveries and professional negligence, commercial.
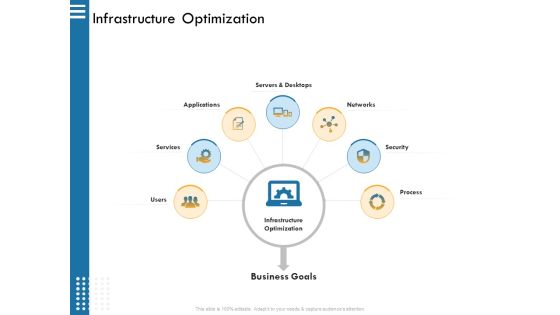
IT Infrastructure Governance Infrastructure Optimization Ppt Inspiration Background PDF
This is a it infrastructure governance infrastructure optimization ppt inspiration background pdf. template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like services, applications, servers and desktops, networks, security, process, users. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
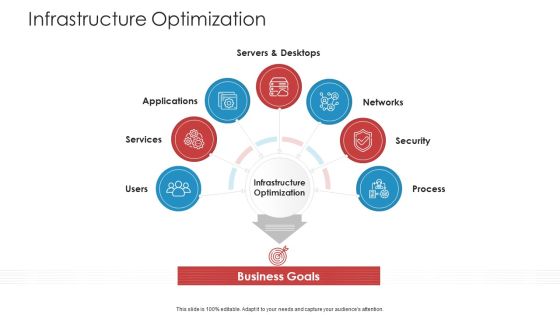
Landscape Architecture Planning And Management Infrastructure Optimization Structure PDF
This is a landscape architecture planning and management infrastructure optimization structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, services, users, networks, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Examples Of Business Processes Linear Flow 3 Stages Post It Notes Ppt PowerPoint Template
We present our examples of business processes linear flow 3 stages post it notes ppt PowerPoint template.Present our Advertising PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download our Business PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Present our Boxes PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Present our Shapes PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are designed to help you succeed. They have all the ingredients you need.Use these PowerPoint slides for presentations relating to Banners, Note, Paper, Vector, Box, Clip, Green, Background, Paperclip, Product, Website, Wallpaper, Secure, Attractive, Post It, Tag, Brochure, Recycle, Clean, Card, Striped, Simple, Padlock, Label, Abstract, Modern, Palette, Illustration, Stationery, Number, Notepaper, Cool, Backdrop, Graphic Design, Web, Paper Clip, Colorful, Stationary, Recyclable, Text Sample, Info Graphic, Stripe, Advertising. The prominent colors used in the PowerPoint template are Blue, Gray, White.
Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Seven Step Cyber Insurance Ppt PowerPoint Presentation Infographic Template Graphic Tips
This is a cyber security seven step cyber insurance ppt powerpoint presentation infographic template graphic tips. This is a seven stage process. The stages in this process are develop a plan, assess and measure, cyber insurance, mitigate risk, get started.

Financial Instruments Bonds And Fixed Income Securities Ppt PowerPoint Presentation Inspiration Templates
This is a financial instruments bonds and fixed income securities ppt powerpoint presentation inspiration templates. This is a two stage process. The stages in this process are marketing, business, management, planning, strategy.
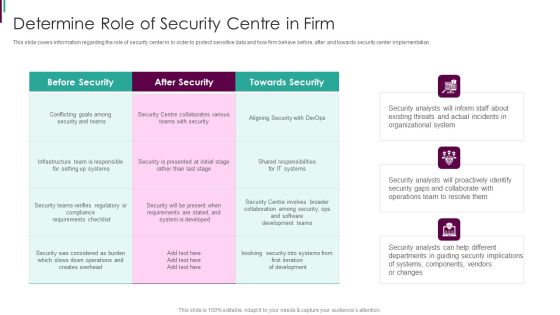
Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF bundle. Topics like Before Security, After Security, Towards Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Business Marketing Plan Ppt PowerPoint Presentation Show Graphics Design Cpb
Presenting this set of slides with name security business marketing plan ppt powerpoint presentation show graphics design cpb. This is a three stage process. The stages in this process are security business marketing plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Steps Of Cyber Security With Icons Ppt PowerPoint Presentation Model Samples
Presenting this set of slides with name five steps of cyber security with icons ppt powerpoint presentation model samples. This is a five stage process. The stages in this process are security servery, solutions deployment, review and adjustment, monitoring and evaluation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security System For Business Quality Control Ppt PowerPoint Presentation Gallery Templates PDF
Presenting this set of slides with name online security system for business quality control ppt powerpoint presentation gallery templates pdf. This is a six stage process. The stages in this process are network engineering program, information security management, social engineering program, ethical hacking program, crime investigation program, internet security program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Methods To Develop Advanced Essential Elements Of Security Monitoring Plan Formats PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver and pitch your topic in the best possible manner with this methods to develop advanced essential elements of security monitoring plan formats pdf. Use them to share invaluable insights on network security, critical infrastructure, cloud security, application security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
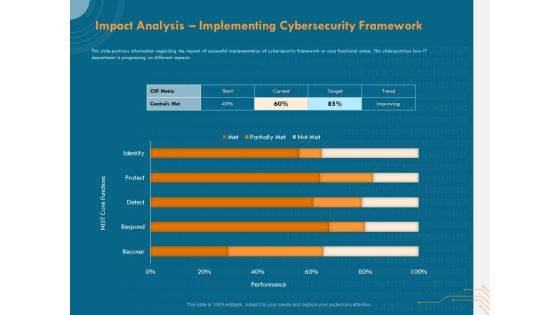
Cyber Security Implementation Framework Impact Analysis Implementing Cybersecurity Framework Ppt Show Graphics PDF
Presenting this set of slides with name cyber security implementation framework impact analysis implementing cybersecurity framework ppt show graphics pdf. The topics discussed in these slides are csf metric, controls met, nist core functions, target, trend. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF
Pitch your topic with ease and precision using this Cloud Security KPI Dashboard With Key Statistics Ppt Icon Examples PDF. This layout presents information on Compliance Trend, Risk Status, Risk Severity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Rules And Regulations With Accuracy Ppt PowerPoint Presentation Slides Outfit
Presenting this set of slides with name cyber security rules and regulations with accuracy ppt powerpoint presentation slides outfit. This is a six stage process. The stages in this process are purpose and manner of collection, accuracy and duration of retention, use of personal data, security of personal data, information to be generally available, access to personal data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Advantages Of Cloud Computing With Flexibility And Security Ppt PowerPoint Presentation Portfolio Format PDF
Presenting this set of slides with name advantages of cloud computing with flexibility and security ppt powerpoint presentation portfolio format pdf. This is a eight stage process. The stages in this process are flexibility, disaster recovery, automatic software updates, pay as you go, increased collaboration, document control, security, location independent. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF
Presenting Table Of Contents For Security And Performance Digital Marketing Playbook Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Automation Throughout, Automated Sequences, Reporting Dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Lock And Us Dollar Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Lock And US Dollar Security PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Download and present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Download our Success PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Use our Money PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Download our Marketing PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter.Use these PowerPoint slides for presentations relating to Lock and us dollar with green and white backgrounds, business, finance, success, money, marketing. The prominent colors used in the PowerPoint template are Green, White, Yellow. PowerPoint presentation experts tell us our Lock And US Dollar On White And Green Background PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. People tell us our white PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Presenters tell us our Lock And US Dollar On White And Green Background PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. The feedback we get is that our green PowerPoint templates and PPT Slides will save the presenter time. Customers tell us our Lock And US Dollar On White And Green Background PowerPoint Templates PPT Backgrounds For Slides 0113 are topically designed to provide an attractive backdrop to any subject. People tell us our white PowerPoint templates and PPT Slides will impress their bosses and teams.

Information Security Process To Manage Firms Sensitive Data Ppt Infographics Background Image PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative information security process to manage firms sensitive data ppt infographics background image pdf bundle. Topics like management, system, security, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
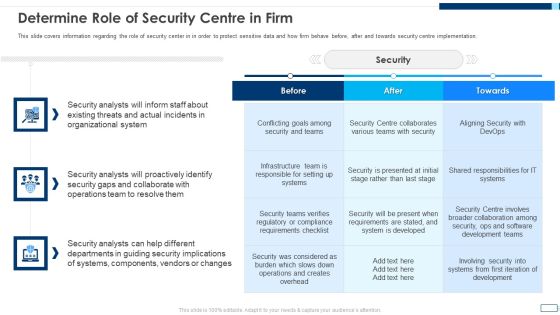
Evolving BI Infrastructure Determine Role Of Security Centre In Firm Summary PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative evolving bi infrastructure determine role of security centre in firm summary pdf bundle. Topics like organizational, security analysts, collaborate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
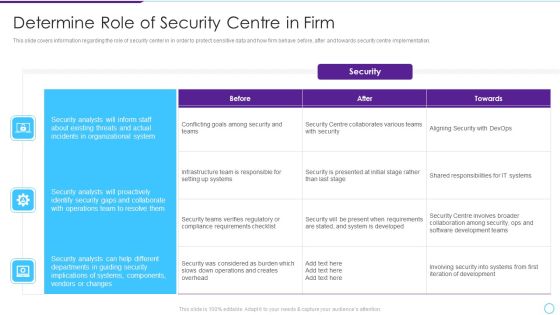
Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF bundle. Topics like Security, Organizational System, Operations Team, Conflicting Goals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF bundle. Topics like Organizational System, Security Analysts, Collaborate With Operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Types Of Attacks In Network Security Ppt PowerPoint Presentation Portfolio Layouts
Presenting this set of slides with name types of attacks in network security ppt powerpoint presentation portfolio layouts. This is a four stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Security Methods With Disaster Recovery Ppt PowerPoint Presentation Pictures Vector
Presenting this set of slides with name data security methods with disaster recovery ppt powerpoint presentation pictures vector. This is a five stage process. The stages in this process are data deduplication, disaster recovery, the encryption algorithm, disk mirroring and storage replication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Advantages Of Cloud Computing In Business With Higher Security Ppt PowerPoint Presentation File Infographic Template PDF
Presenting this set of slides with name advantages of cloud computing in business with higher security ppt powerpoint presentation file infographic template pdf. This is a six stage process. The stages in this process are more flexible, infrastructure, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Backup Maintenance Developing Alternate Sites Slides PDF
Presenting this set of slides with name computer security incident handling backup maintenance developing alternate sites slides pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Developing Alternate Sites Ppt Templates PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance developing alternate sites ppt templates pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Categorization Of Cyber Risks Ppt Model Designs Download PDF
Presenting this set of slides with name strategies to mitigate cyber security risks categorization of cyber risks ppt model designs download pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Backup Maintenance Developing Alternate Sites Ppt PowerPoint Presentation Model Images PDF
Presenting this set of slides with name cyber security implementation framework backup maintenance developing alternate sites ppt powerpoint presentation model images pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Categorization Of Cyber Risks Ppt PowerPoint Presentation Portfolio Sample PDF
Presenting this set of slides with name cyber security implementation framework categorization of cyber risks ppt powerpoint presentation portfolio sample pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Computing Technology Implementation Plan Serverless Technology Industry Trends Diagrams PDF
Purpose of the following slide is to display multiple trends that will effect the global serverless computing market, these trends can be emergence of new testing tools, new server security tools and easy monitoring software. Presenting cloud computing technology implementation plan serverless technology industry trends diagrams pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like new testing tools, server security tools, easy monitoring software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Application Protection Ppt Layout Presentation Design
This is a application protection ppt layout presentation design. This is a seven stage process. The stages in this process are content security, risk mitigation, risk assessment, application security, evaluation and assessment, endpoint security, network security.
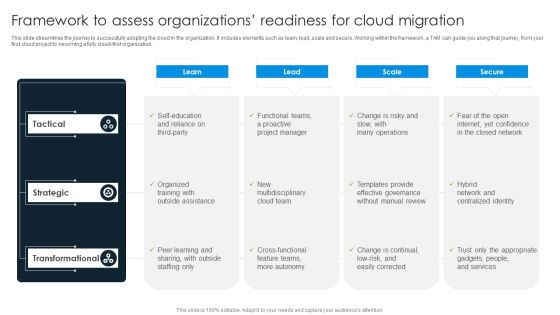
Framework To Assess Organizations Readiness For Cloud Migration Information PDF
This slide streamlines the journey to successfully adopting the cloud in the organization. It includes elements such as learn, lead, scale and secure. Working within the framework, a TAM can guide you along that journey, from your first cloud project to becoming a fully cloud-first organization. Pitch your topic with ease and precision using this Framework To Assess Organizations Readiness For Cloud Migration Information PDF. This layout presents information on Tactical, Strategic, Transformational. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
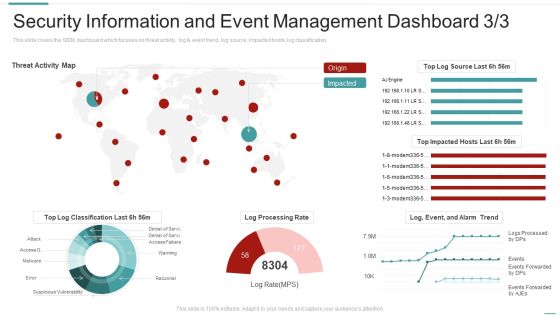
Risk Recognition Automation Security Information And Event Management Dashboard Activity Ppt Styles Influencers PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard activity ppt styles influencers pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
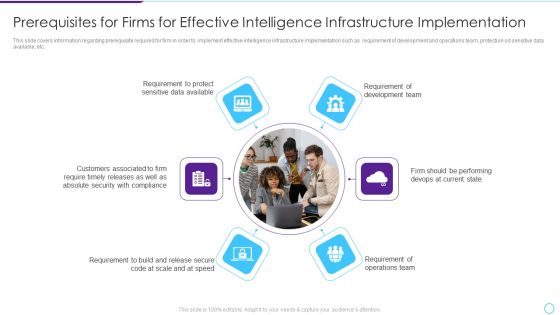
Intelligent Infrastructure Prerequisites For Firms For Effective Intelligence Infrastructure Rules PDF
This slide covers information regarding prerequisite required for firm in order to implement effective intelligence infrastructure implementation such as requirement of development and operations team, protection od sensitive data available, etc. Presenting Intelligent Infrastructure Prerequisites For Firms For Effective Intelligence Infrastructure Rules PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protect Sensitive Data Available, Customers Associated, Absolute Security, Build And Release Secure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends Best, Smart Home Security, Systems Consumer Technology, Association Consumer Technology, Association Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Information And Secured Data PowerPoint Templates Ppt Backgrounds For Slides 0713
Our Global Information And Secured Data PowerPoint Templates PPT Backgrounds For Slides will will follow the drill. They accomplish the task assigned to them. Do the drill with our Technology PowerPoint Templates. Your ideas will march ahead. Place the orders with your thoughts. Our Business PowerPoint Templates know the drill.
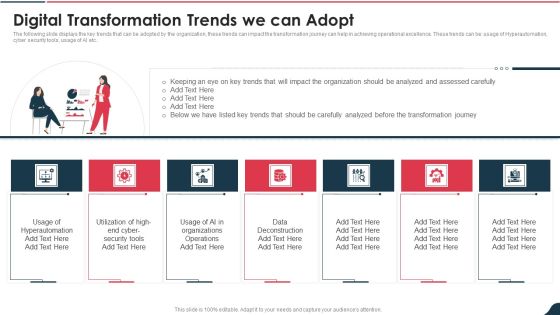
Electronic Playbook Digital Transformation Trends We Can Adopt Microsoft PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyperautomation, cyber security tools, usage of AI etc.Presenting electronic playbook digital transformation trends we can adopt microsoft pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like digital transformation trends we can adopt In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Challenges Faced By Ecommerce Marketing Manager Deploying Ecommerce Order Management Introduction PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience.Want to ace your presentation in front of a live audience Our Challenges Faced By Ecommerce Marketing Manager Deploying Ecommerce Order Management Introduction PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security Learning System For Malware Threat Control Ppt PowerPoint Presentation Layouts Portfolio PDF
Presenting this set of slides with name online security learning system for malware threat control ppt powerpoint presentation layouts portfolio pdf. This is a three stage process. The stages in this process are network protection and control, access control protection, email and web browser protections, virus penetration testing and control fundamentals, password protection, wireless protection, cyber incitement management, ethical hacking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Blockchain Technology Implementation In Various Banking Activities Develop Organizational Productivity Enhancing Business Process Pictures PDF
This slide shows the role of blockchain technology in banking that enhances the digital banking services which are to be provided. Blockchain technology help to eliminate the middlemen in various banking services enhancing the overall efficiency. This is a blockchain technology implementation in various banking activities develop organizational productivity enhancing business process pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like payments, clearance and settlement systems, fundraising, securities, loans and credit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Top Digital Industry Trends In Banking In 2021 Ideas PDF
This slide shows some of the top digital industry trends in banking that are most widely adopted such as seamless payments, next gen and digital banks, mobile applications, robotics process automation and ai artificial intelligence, cybersecurity etc. This is a top digital industry trends in banking in 2021 ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like seamless payments, mobile applications, cyber security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Reasons For Poor Security Management In The Company Topics PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company topics pdf bundle. Topics like outdated software, lack of proper protection, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
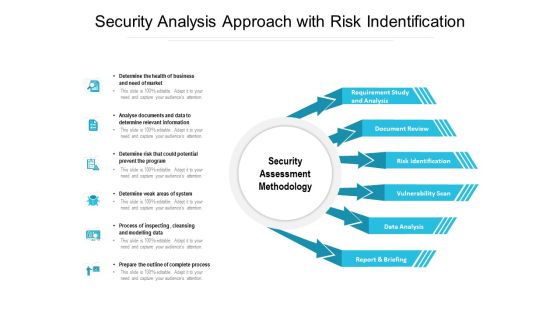
Security Analysis Approach With Risk Indentification Ppt PowerPoint Presentation Professional Gridlines PDF
Presenting security analysis approach with risk indentification ppt powerpoint presentation professional gridlines pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including analyse, of business, need of market, prevent the program, process of inspecting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Graphics PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail evaluating information processing assets graphics pdf. Use them to share invaluable insights on security management plan steps in detail evaluating information processing assets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. It includes benefits of order management system such as fast delivery, less mistakes etc. It includes benefits of order management system such as fast delivery, less mistakes etc. This Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today

Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF
This template covers account-based marketing strategy such as the use of social media channels and techniques to increase brand recognition, and nurture the target prospects and lead through the digital marketing funnel.This is a Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Prospects Obtained, Nurturing Sequences, Channels Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF
This slide showcases areas where the funds that are collected in series C funding round will be allocated like- marketing, sales and research and development. If you are looking for a format to display your unique thoughts, then the professionally designed Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Introduction PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver an awe inspiring pitch with this creative security management plan steps in detail risk assessment and analysis introduction pdf bundle. Topics like information, system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
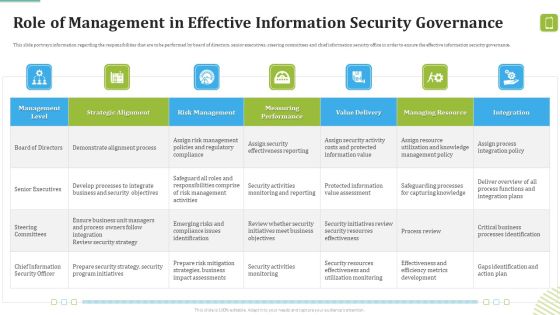
MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Demonstrate Alignment, Business Security, Program Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home