Roadmap Safety

New Year Business Concept PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our New Year Business Concept PowerPoint Templates PPT Backgrounds For Slides 1112.Use our New Year PowerPoint Templates because its New Year time. Download our Security PowerPoint Templates because you are going along well but your foresight shows that it may need a slight change in plans or direction. Present our Success PowerPoint Templates because you have come up with a brilliant breakthrough idea. you can also visualise the interest it will generate. Download and present our Holidays PowerPoint Templates because you have a good idea of the roadmap to your desired destination. Download and present our Shapes PowerPoint Templates because they pinpoint the core values of your organisation.Use these PowerPoint slides for presentations relating to New year 2013 keys, security, holidays, shapes, success, new year . The prominent colors used in the PowerPoint template are Brown, Black, Yellow. Presenters tell us our New Year Business Concept PowerPoint Templates PPT Backgrounds For Slides 1112 are Magical. Professionals tell us our security PowerPoint templates and PPT Slides are Playful. Presenters tell us our New Year Business Concept PowerPoint Templates PPT Backgrounds For Slides 1112 are Energetic. Presenters tell us our 2013 PowerPoint templates and PPT Slides are Functional. Use our New Year Business Concept PowerPoint Templates PPT Backgrounds For Slides 1112 are Fun. PowerPoint presentation experts tell us our keys PowerPoint templates and PPT Slides are incredible easy to use.

Key With A Piggy Bank And Coins Banking PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Key With A Piggy Bank And Coins Banking PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Security PowerPoint Templates because this diagram has the unique ability to drive home your ideas and show how they mesh to guarantee success. Download and present our Future PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Use our Money PowerPoint Templates because you have a good idea of the roadmap to your desired destination. Download and present our Finance PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Present our Success PowerPoint Templates because you have come up with a brilliant breakthrough idea. you can also visualise the interest it will generate.Use these PowerPoint slides for presentations relating to Keys to financial success, future, money, finance, success, security. The prominent colors used in the PowerPoint template are Green, Brown, Black. Use our Key With A Piggy Bank And Coins Banking PowerPoint Templates PPT Backgrounds For Slides 1212 are Glamorous. Presenters tell us our money PowerPoint templates and PPT Slides are Majestic. People tell us our Key With A Piggy Bank And Coins Banking PowerPoint Templates PPT Backgrounds For Slides 1212 are Upbeat. You can be sure our security PowerPoint templates and PPT Slides are Perfect. Professionals tell us our Key With A Piggy Bank And Coins Banking PowerPoint Templates PPT Backgrounds For Slides 1212 are Ritzy. Professionals tell us our money PowerPoint templates and PPT Slides are Reminiscent.

Key Activities Security Service Provider Business Model BMC SS V
This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Activities Security Service Provider Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
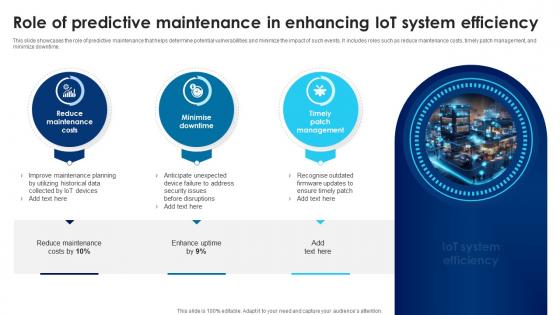
Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V
This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Subsequential Description Using Arrows 7 Stages Flow Chart Examples PowerPoint Templates
We present our subsequential description using arrows 7 stages flow chart examples PowerPoint templates.Use our Arrows PowerPoint Templates because, Our Template designs are State of the Art. Use our Leadership PowerPoint Templates because,You will be able to Highlight your ideas broad-based on strong fundamentals and illustrate how they step by step acheive the set growth factor. Use our Business PowerPoint Templates because,You have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries Use our Symbol PowerPoint Templates because,You have a good idea of the roadmap to your desired destination. Use our Process and Flows PowerPoint Templates because, Our Template designs are State of the Art.Use these PowerPoint slides for presentations relating to Arrow, Arrows, Block, Business, Chart, Design, Development, Diagram, Direction, Element, Flow, Flowchart, Graph, Linear, Management, Organization, Process, Program, Section, Sign, Solution, Symbol. The prominent colors used in the PowerPoint template are Green, Gray, Black. People tell us our subsequential description using arrows 7 stages flow chart examples PowerPoint templates are Energetic. PowerPoint presentation experts tell us our Block PowerPoint templates and PPT Slides are Stunning. PowerPoint presentation experts tell us our subsequential description using arrows 7 stages flow chart examples PowerPoint templates are Second to none. Professionals tell us our Block PowerPoint templates and PPT Slides are Efficacious. Professionals tell us our subsequential description using arrows 7 stages flow chart examples PowerPoint templates will get their audience's attention. People tell us our Block PowerPoint templates and PPT Slides are Luxuriant.
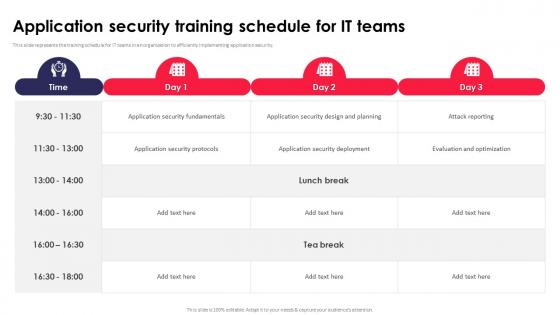
Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait
This slide represents the training schedule for IT teams in an organization to efficiently implementing application security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Table Of Contents For Zero Trust Network Security Introduction Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Zero Trust Network Security Introduction Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Key Aspects Of Legal And Regulatory Compliance Successful Launch Ppt Slide
The following slide showcases legal and regulatory compliance for organic cosmetic series to ensure product safety, transparency, and trustworthiness. It outlines elements such as ingredient safety, labeling requirements, product claims, allergen information, microbial safety, packaging and sustainability, transparency, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Aspects Of Legal And Regulatory Compliance Successful Launch Ppt Slide from Slidegeeks and deliver a wonderful presentation.

Business Performance Analysis After Using Fwaas Network Security Sample Pdf
This slide demonstrates the performance analysis of Firewall-as-a-Service. The purpose of this slide is to compare the before and after business situation based on several factors such as network downtime, security incidents, cost of security, time to deploy security, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Performance Analysis After Using Fwaas Network Security Sample Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

CASB 2 0 IT Popular Cloud Access Security Broker Vendors
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. CASB 2 0 IT Popular Cloud Access Security Broker Vendors will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Quality Management Control Process Ppt Powerpoint Guide
This is a quality management control process ppt powerpoint guide. This is a three stage process. The stages in this process are quality control, product safety, certification, quality assurance, quality control.
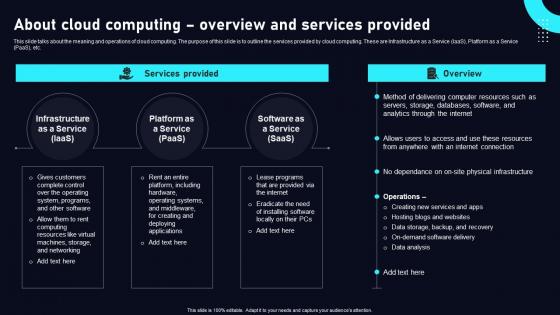
About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Architect Design And Solutions Diagram Powerpoint Slides
This is a architect design and solutions diagram powerpoint slides. This is a six stage process. The stages in this process are data safety, efficiently, speed, reliability, convenience, security.
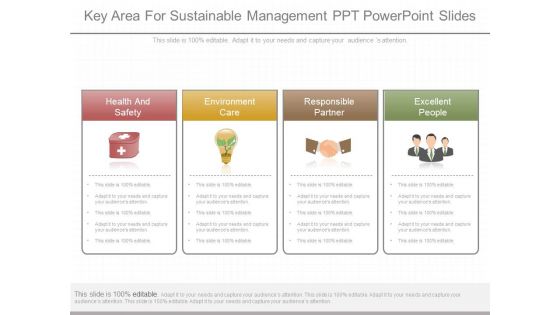
Key Area For Sustainable Management Ppt Powerpoint Slides
This is a key area for sustainable management ppt powerpoint slides. This is a four stage process. The stages in this process are health and safety, environment care, responsible partner, excellent people.\n\n \n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n
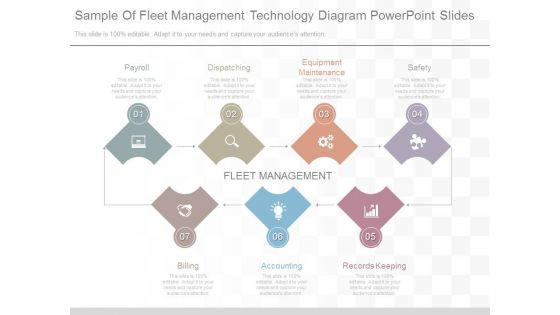
Sample Of Fleet Management Technology Diagram Powerpoint Slides
This is a sample of fleet management technology diagram powerpoint slides. This is a seven stage process. The stages in this process are payroll, dispatching, equipment maintenance, safety, billing, accounting, records keeping.

Hr Departments Mission And Values Example Ppt Sample Download
This is a hr departments mission and values example ppt sample download. This is a seven stage process. The stages in this process are selection and recruitment, labor relations, personnel administration, job safety, organisation, development, communication.

Life Insurance Marketing Plan Template Powerpoint Slide Show
This is a life insurance marketing plan template powerpoint slide show. This is a six stage process. The stages in this process are service provider, confidence, protection, safety, consumers, company.

Stock Photo Traffic Light Red Yellow Green Signal PowerPoint Slide
This image is designed with 3d graphic of traffic lights. It contains red green yellow signal in order to display the concept of following traffic rules for safety. Use this image to explain traffic rules in presentations.

Stock Photo Traffic Light With Signals PowerPoint Slide
This image is designed with 3d graphic of traffic lights. It contains red green yellow signal in order to display the concept of following traffic rules for safety. Use this image to explain traffic rules in presentations.

Stock Photo Yellow Color Directions Signs Boards PowerPoint Slide
This image is designed with yellow color direction signs. It contains road signs in order to display the concept of following traffic rules for safety. Use this image to explain traffic rules in presentations.

Stock Photo Red Green Yellow Signal Light PowerPoint Slide
This image slide has been designed with 3d graphic of traffic lights. It contains red green yellow signal in order to show the concept of following traffic rules for safety. Use this image to explain traffic rules in presentations.

Enterprise Sustainability Management Sample Diagram Powerpoint Idea
This is a enterprise sustainability management sample diagram powerpoint idea. This is a six stage process. The stages in this process are environment health and safety, energy management, management carbon, management operational risk, product stewardship, sustainability reporting, enterprise sustainability management.

Benefits Of Educational Blogging Sample Diagram Ppt Images
This is a benefits of educational blogging sample diagram ppt images. This is a nine stage process. The stages in this process are global connection, classroom community, literacy, maths, ict skills, social skills, authentic audience, internet safety, home school, benefits.
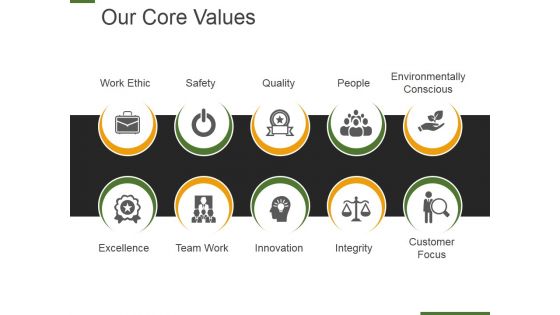
Our Core Values Template 2 Ppt PowerPoint Presentation Portfolio Summary
This is a our core values template 2 ppt powerpoint presentation portfolio summary. This is a ten stage process. The stages in this process are work ethic, safety, quality, people, environmentally conscious.

Core Values Ppt PowerPoint Presentation Model Gallery
This is a core values ppt powerpoint presentation model gallery. This is a ten stage process. The stages in this process are work ethic, safety, quality, people, environmentally conscious.

Our Core Values Template 3 Ppt PowerPoint Presentation Model Skills
This is a our core values template 3 ppt powerpoint presentation model skills. This is a ten stage process. The stages in this process are work ethic, safety, quality, excellence, team work.

Senseable Cities Technology Impact On Society Ideas PDF
This slide showcasing impact on individual or society when cities get smarter using technological advancements. It includes elements such as public safety, healthcare, mobility, workforce and environmental. Presenting Senseable Cities Technology Impact On Society Ideas PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Public Safety, Healthcare, Mobility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Systems Security And Risk Management Plan Quotes Guidelines PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Quotes Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
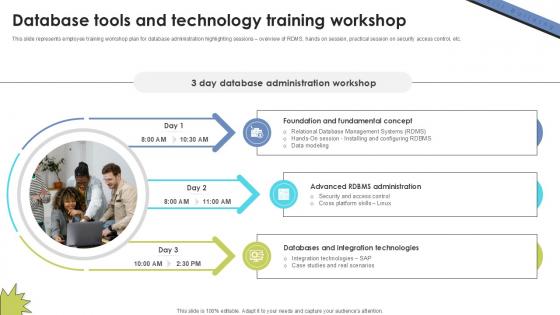
Database Tools And Technology Skill Building Plan For Application PPT Presentation DTE SS V
This slide represents employee training workshop plan for database administration highlighting sessions overview of RDMS, hands on session, practical session on security access control, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Database Tools And Technology Skill Building Plan For Application PPT Presentation DTE SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Security Control Techniques For Real Estate Project Risk Mitigation Plan For Construction Site Hazards Microsoft PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security Control Techniques For Real Estate Project Risk Mitigation Plan For Construction Site Hazards Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Checklist For Work From Home Data Security Improving Cybersecurity With Incident Structure PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Work From Home Data Security Improving Cybersecurity With Incident Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
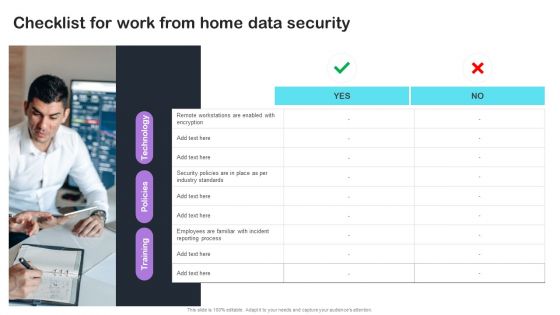
Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Diverging Flow Chart Consisting 11 Stages Business Target Network PowerPoint Slides
We present our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides.Present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Circle Charts PowerPoint Templates because they have fired the dreams of many fertile minds. Download and present our Arrows PowerPoint Templates because you have a good idea of the roadmap to your desired destination. Download and present our Shapes PowerPoint Templates because it helps you to get your team in the desired sequence into the bracket. Use our Flow charts PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Use these PowerPoint slides for presentations relating to Arrows, blank, business, central, centralized, chart, circle, circular, circulation concept, conceptual, converging, design, diagram, empty, executive, icon, idea illustration, management, map, mapping, moa, model, numbers, organization outwards, pointing, procedure, process, radial, radiating, relationship, resource sequence, sequential, seven, square, strategy, template. The prominent colors used in the PowerPoint template are Yellow, Gray, White. Presenters tell us our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides are Efficient. Presenters tell us our central PowerPoint templates and PPT Slides are Fantastic. PowerPoint presentation experts tell us our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides are Fantastic. We assure you our centralized PowerPoint templates and PPT Slides are Reminiscent. Customers tell us our diverging flow chart consisting 11 stages business Target Network PowerPoint Slides are Excellent. People tell us our centralized PowerPoint templates and PPT Slides are Stylish.

Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides
This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
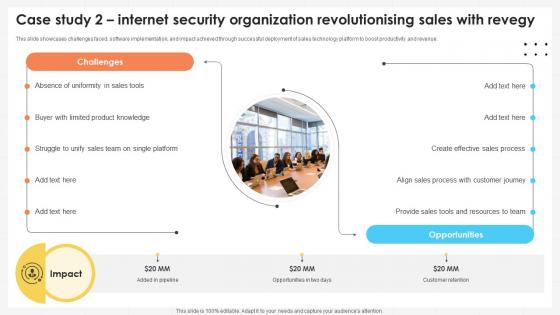
Business Development Team Case Study 2 Internet Security Organization SA SS V
This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Development Team Case Study 2 Internet Security Organization SA SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example
This slide represents the tokenization case study at comforte fashion retailer. The purpose of this slide is to give an overview of the retailer, including the challenges they face and the solutions provided by tokenization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF
The following slide exhibits the current and most important customer service statistics. Information covered in this slide is related to training requirement, positive customer experience, customized experiences, buying decision on the services offered by the agents etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
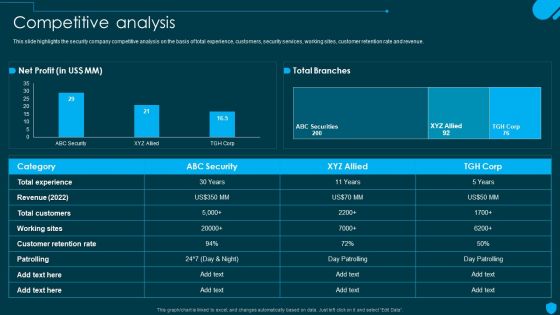
Security And Human Resource Services Business Profile Competitive Analysis Elements PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security And Human Resource Services Business Profile Competitive Analysis Elements PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Defense Security Statistics By Global Security Industry PPT Sample IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates.Defense Security Statistics By Global Security Industry PPT Sample IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
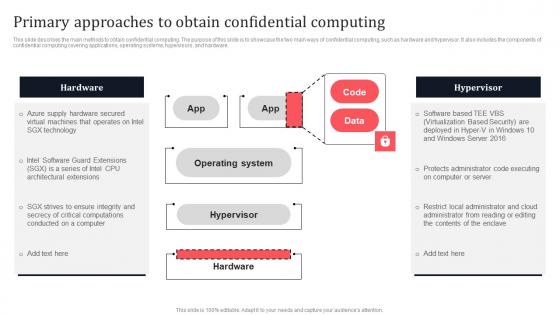
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
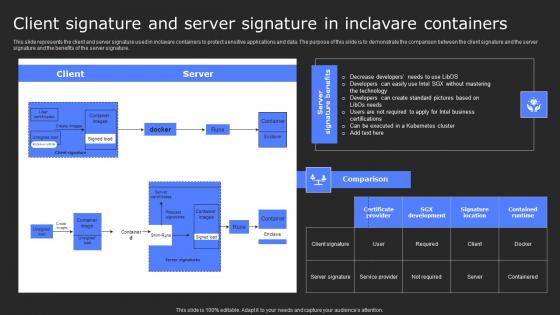
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
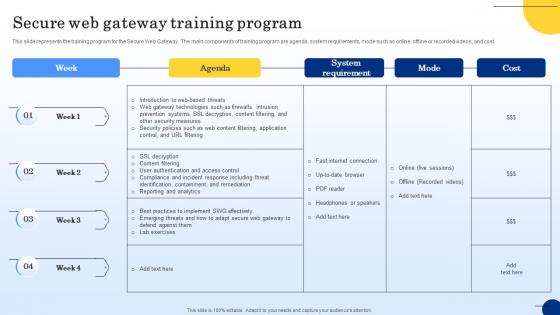
Secure Web Gateway Training Program Web Threat Protection System
This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Secure Web Gateway Training Program Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
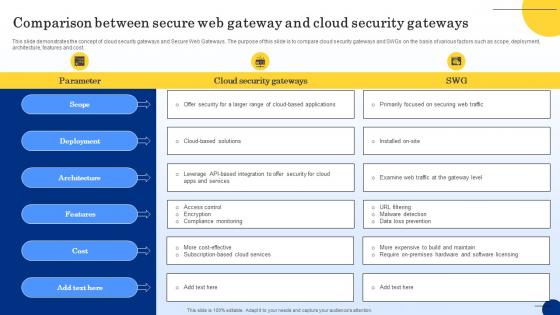
Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
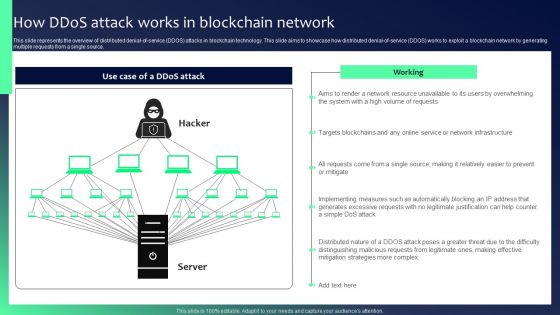
Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
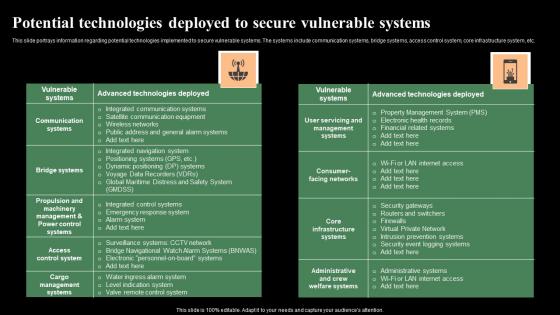
Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf
This slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Potential Technologies Deployed To Secure Vulnerable Monitoring Digital Assets Summary Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Prevailing Trends In Food Manufacturing Industry Ppt Show Designs Download PDF
This slide covers the major trends prevailing in food manufacturing industry such as high reliance on technology, sustainable products and packaging, transparency in food safety, desire for functional ingredients and plant based foods. Presenting Prevailing Trends In Food Manufacturing Industry Ppt Show Designs Download PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like High Reliance, Technology, Transparency Food Safety, Demand Plant Based. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
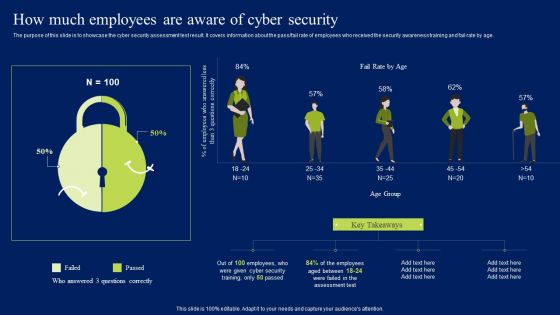
How Much Employees Are Aware Of Cyber Security Ppt Ideas Portrait PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. How Much Employees Are Aware Of Cyber Security Ppt Ideas Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
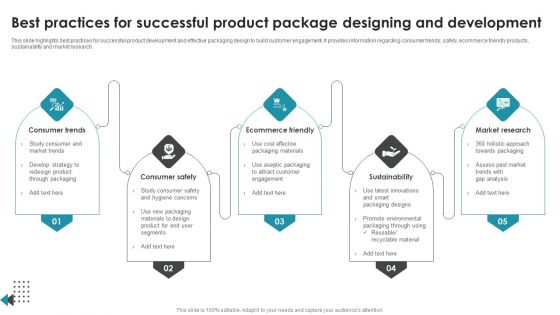
Best Practices For Successful Product Package Designing And Development Background PDF
This slide highlights best practices for successful product development and effective packaging design to build customer engagement. It provides information regarding consumer trends, safety, ecommerce friendly products, sustainability and market research. Presenting Best Practices For Successful Product Package Designing And Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Consumer Trends, Consumer Safety, Ecommerce Friendly, Sustainability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home