Risk

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

E Commerce Strengths Weaknesses Opportunities And Threats Analysis For Business Growth Background PDF
This slide elaborates about the strengths, weakness, opportunity and threat of the e-commerce business that will help for knowing what is needed and what areas need improvements for the company growth.Presenting E Commerce Strengths Weaknesses Opportunities And Threats Analysis For Business Growth Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mismanagement, Opportunities, Considerable This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF
This slide covers the strategies that are been developed by doing the SWOT strengths, weakness, opportunities and threats analysis of an organization to help the managers or owners to make decisions accordingly.Persuade your audience using this Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Ineffective Marketing, Unable To Establish, Large Diversified Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strengths Weaknesses Opportunities And Threats Analysis Matrix For Effective Marketing Growth Sample PDF
This slide covers the strengths , weaknesses , opportunities and threats analysis of the business for the effective marketing growth. This will help the business to expand in may areas by working on its weakness and knowing their opportunities.Presenting Strengths Weaknesses Opportunities And Threats Analysis Matrix For Effective Marketing Growth Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Communication Among, Implementation, Increase Prices This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. This is a Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Could, Business Partners, Data Stored. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
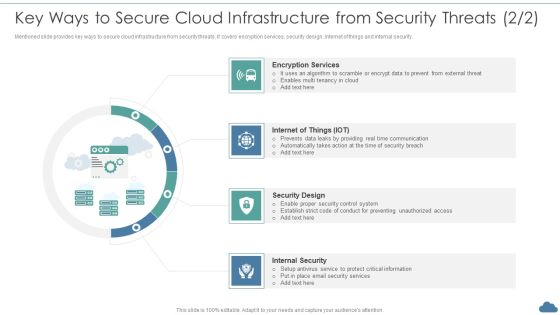
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Presenting Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Partners, Contract Breaches, Against The Organization In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Presenting Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Storage Locations, Natural Disasters, Massive Impact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF
This slide shows comparison of software available for detecting insider threat. It provides information about tools, features, user reviews, detection rate, free trial and pricing. Pitch your topic with ease and precision using this Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF. This layout presents information on User Reviews, Detection Rate, Free Trial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
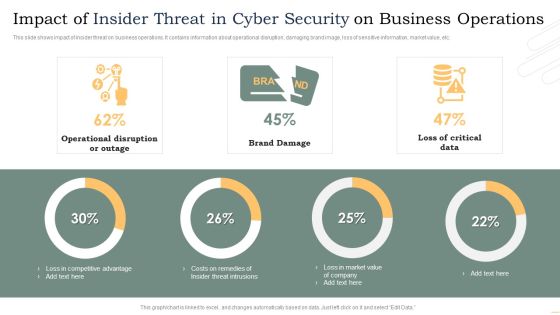
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF. Use them to share invaluable insights on Manual Testing, Fix Error, 3 Working Days and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
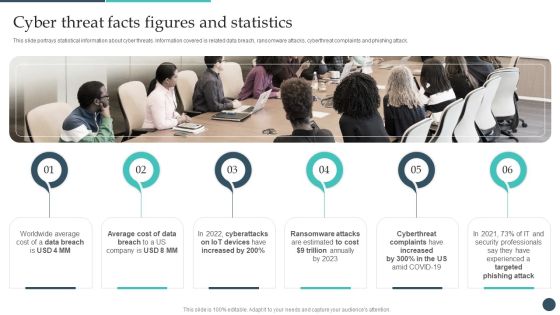
Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Boost your pitch with our creative Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Security Automation To Analyze And Mitigate Cyberthreats Time To Fix Security Threat Ideas PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Security Automation To Analyze And Mitigate Cyberthreats Time To Fix Security Threat Ideas PDF from Slidegeeks and deliver a wonderful presentation.

Confidential Data Theft Threats Mitigation Heat Map Ppt Portfolio Microsoft PDF
This slide covers heat map depicting data theft mitigation strategies and task prioritization. It includes process such as to discover employees roles and access levels, analyse threats and execute plan to reduce or eliminate data theft. Presenting Confidential Data Theft Threats Mitigation Heat Map Ppt Portfolio Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Discover, Analyze, Execute And Educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
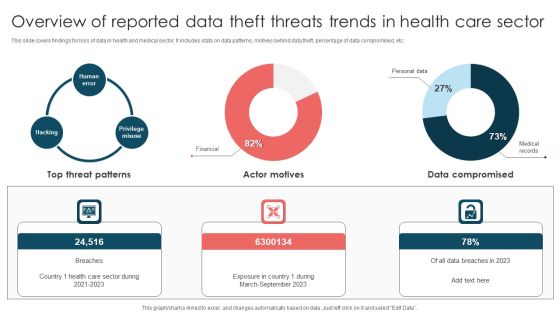
Overview Of Reported Data Theft Threats Trends In Health Care Sector Introduction PDF
This slide covers findings for loss of data in health and medical sector. It includes stats on data patterns, motives behind data theft, percentage of data compromised, etc. Pitch your topic with ease and precision using this Overview Of Reported Data Theft Threats Trends In Health Care Sector Introduction PDF. This layout presents information on Top Threat Patterns, Exposure Country, March To September 2023. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Demonstration PDF
Create an editable Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF
Find highly impressive Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cyber Threat Facts Figures And Statistics Improving Cybersecurity With Incident Icons PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.
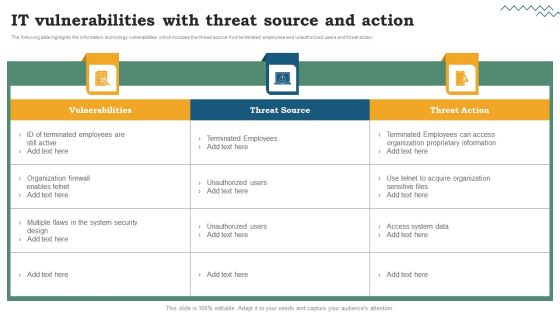
Software Development Life Cycle Planning IT Vulnerabilities With Threat Source And Action Structure PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Welcome to our selection of the Software Development Life Cycle Planning IT Vulnerabilities With Threat Source And Action Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Critical Measures For Ensuring Contingency Plan For Threat Handling At Workplace Graphics PDF
This slide portrays information contingency plan for handling threats at workplace with the help of technical equipment that assist contingency solution and considerations. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Critical Measures For Ensuring Contingency Plan For Threat Handling At Workplace Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF
This slide provides information regarding various types of cyberthreats existing at workspace in terms of malware, ransomware, etc. The sources of cyber threats include criminal groups, hackers, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Various Cyber Threats Existing At Workplace Ppt Infographic Template Designs Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Various Types Of Workplace Violence And Threats Ppt Pictures Outline PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Present like a pro with Various Types Of Workplace Violence And Threats Ppt Pictures Outline PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents Overview On Mitigating Workplace IT Threats Slides PDF.

Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF
The firm will track the various incidents issues faced and resolved in the firm. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF
This slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti-phishing, data discovery, and packet-level visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Save Your Document From Threat PowerPoint Templates Ppt Backgrounds For Slides 0513
Our Save Your Document From Threat PowerPoint Templates PPT Backgrounds For Slides heighten concentration. Your audience will be on the edge. Get an edge with our Security PowerPoint Templates. They give you advantage plus. Edit your work with our Success PowerPoint Templates. They will help you give the final form.

Secure Your Data From Threats PowerPoint Templates Ppt Backgrounds For Slides 0613
Draw ahead of others with our Secure Your Data From Threats PowerPoint Templates PPT Backgrounds For Slides. Cross the line and win the race. Draw out the best in you with our Security PowerPoint Templates. Let your inner brilliance come to the surface. Draw out the talents of your team. Use our Technology PowerPoint Templates to give them an incentive.

Put Warnings For Threats PowerPoint Templates Ppt Backgrounds For Slides 0713
Lower the drawbridge with our Put Warnings For Threats PowerPoint Templates PPT Backgrounds For Slides. Capture the minds of your audience. Cajole them with our Transportation PowerPoint Templates. Your audience will be drawn to your ideas. Draw up your agenda on our Road signs PowerPoint Templates. Coax your audience into acceptance.

Steps To Stay Safe From Cyber Attacks Threat Modelling Ppt PowerPoint Presentation Infographics Gallery
Presenting this set of slides with name steps to stay safe from cyber attacks threat modelling ppt powerpoint presentation infographics gallery. This is a six stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Alignment Framework Icons Slide Threat Ppt PowerPoint Presentation Ideas Information
Presenting this set of slides with name it alignment framework icons slide threat ppt powerpoint presentation ideas information. The topics discussed in these slides are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
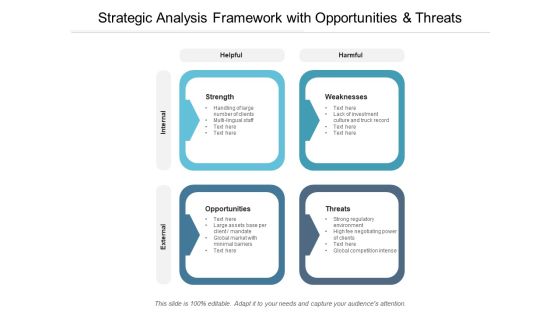
Strategic Analysis Framework With Opportunities And Threats Ppt Powerpoint Presentation Professional Inspiration
Presenting this set of slides with name strategic analysis framework with opportunities and threats ppt powerpoint presentation professional inspiration. This is a four stage process. The stages in this process are market entry analysis, market attractiveness, strategic analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
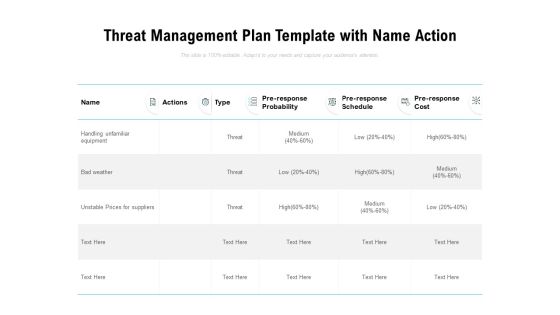
Threat Management Plan Template With Name Action Ppt PowerPoint Presentation Visual Aids Show
Presenting this set of slides with name threat management plan template with name action ppt powerpoint presentation visual aids show. The topics discussed in these slides are name, actions, type, pre response probability, pre response schedule, pre response cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Threat And Opportunity Drivers Barriers Business Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name business threat and opportunity drivers barriers business ppt powerpoint presentation complete deck. The topics discussed in these slides are drivers, barriers, business, commercialization, expansion. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
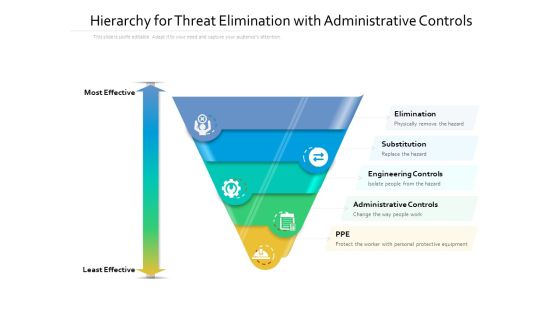
Hierarchy For Threat Elimination With Administrative Controls Ppt PowerPoint Presentation Files PDF
Presenting this set of slides with name hierarchy for threat elimination with administrative controls ppt powerpoint presentation files pdf. This is a five stage process. The stages in this process are elimination, substitution, engineering controls, administrative controls, ppe, most effective, least effective. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Travel Business Opportunity And Threat Analysis Ppt PowerPoint Presentation Gallery Diagrams PDF
Presenting this set of slides with name travel business opportunity and threat analysis ppt powerpoint presentation gallery diagrams pdf. This is a four stage process. The stages in this process are strengths, opportunities, weakness. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Control Dashboard With High And Average Levels Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name threat control dashboard with high and average levels ppt powerpoint presentation file outline pdf. The topics discussed in these slides are governance, industrials, monitored. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Potential Investors List Template With Threats And Opportunities Ppt PowerPoint Presentation File Ideas PDF
Presenting this set of slides with name potential investors list template with threats and opportunities ppt powerpoint presentation file ideas pdf. The topics discussed in these slides are marketing, weaknesses, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Key Cyber Threat Issues To Online Business Industry Ppt PowerPoint Presentation Icon Example File PDF
Presenting this set of slides with name key cyber threat issues to online business industry ppt powerpoint presentation icon example file pdf. This is a six stage process. The stages in this process are commerce, industry, service. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Safety Solution Roadmap With Kpis And Threats Ppt PowerPoint Presentation File Outline PDF
Showcasing this set of slides titled safety solution roadmap with kpis and threats ppt powerpoint presentation file outline pdf. The topics addressed in these templates are experiments, innovations, 2019, 2020, bad internal press. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Safety Threat Assessment Chart Ppt PowerPoint Presentation File Summary PDF
Pitch your topic with ease and precision using this data safety threat assessment chart ppt powerpoint presentation file summary pdf. This layout presents information on improbable, probable, occasional, serious, catastrophic. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Key Safety Audits For Cyber Threat Prevention Ppt PowerPoint Presentation Icon Example PDF
Presenting key safety audits for cyber threat prevention ppt powerpoint presentation icon example pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security, awareness, training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Opportunities And Threats For Penetrating In New Market Segments Icons Slide Pictures PDF
Introducing our well designed opportunities and threats for penetrating in new market segments icons slide pictures pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Opportunities And Threats For Penetrating In New Market Segments Local Partner Selection Professional PDF
Deliver an awe inspiring pitch with this creative opportunities and threats for penetrating in new market segments local partner selection professional pdf bundle. Topics like technical capabilities, industry attractiveness, unique competencies, complementary capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home