Programme
Production Scheduling Business Performance Optimization New Operations Strategy Information Pdf
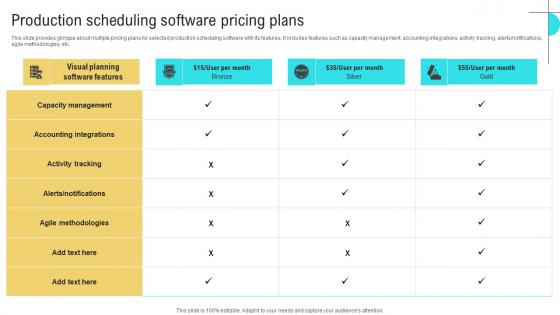
This slide provides glimpse about multiple pricing plans for selected production scheduling software with its features. It includes features such as capacity management, accounting integrations, activity tracking, alertsnotifications, agile methodologies, etc. Create an editable Production Scheduling Business Performance Optimization New Operations Strategy Information Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Production Scheduling Business Performance Optimization New Operations Strategy Information Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Production Scheduling Software Operations Strategy Improve Business Productivity Inspiration Pdf
This slide provides glimpse about multiple pricing plans for selected production scheduling software with its features. It includes features such as capacity management, accounting integrations, activity tracking, alerts notifications, agile methodologies, etc. Create an editable Production Scheduling Software Operations Strategy Improve Business Productivity Inspiration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Production Scheduling Software Operations Strategy Improve Business Productivity Inspiration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Maersk Cyber Attack In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Maersk Cyber Attack In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Maersk Cyber Attack that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Files Mostly Attacked During Cyber Security Breach Structure Pdf
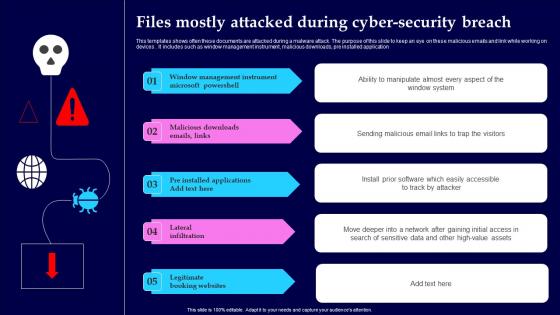
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf
Showcasing this set of slides titled Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf The topics addressed in these templates are Fraud Threat Evaluation, Icon Showcasing Hacker All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Process Hacker In Powerpoint And Google Slides Cpb
Introducing our well-designed Process Hacker In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Process Hacker. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT
This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. This modern and well-arranged Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT
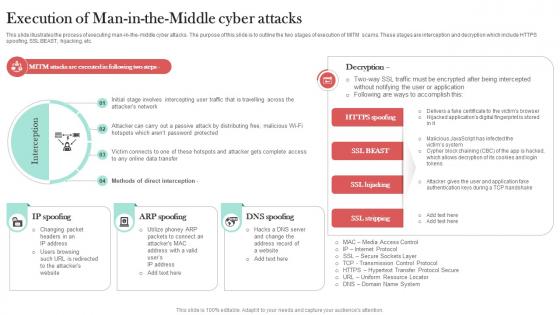
This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc. Welcome to our selection of the Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Slidegeeks has constructed Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Brainstorming Session Six Thinking Hats Presentation Images
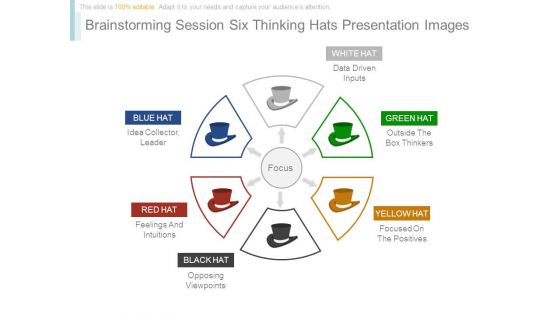
This is a brainstorming session six thinking hats presentation images. This is a six stage process. The stages in this process are focus, white hat data driven inputs, green hat outside the box thinkers, yellow hat focused on the positives, black hat opposing viewpoints, red hat feelings and intuitions, blue hat idea collector leader.
IT Project Yearly Schedule Planner Icons PDF
This slide showcases an yearly calendar highlighting schedule of an IT project for successful completion within stipulated timeframe. Its key tasks are planning, wireframes, graphics and designing, incorporation search, testing and optimization, platform adaptation, app development, marketing and documentation. Pitch your topic with ease and precision using this IT Project Yearly Schedule Planner Icons PDF. This layout presents information on Project Yearly, Schedule Planner. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icons Slide For Create Timetable And Financial Forecast Bundle Introduction PDF
Introducing our well designed icons slide for create timetable and financial forecast bundle introduction pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icon Slide For Program Management Timetable Bundle Ppt Ideas Information PDF
Introducing our well designed icon slide for program management timetable bundle ppt ideas information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
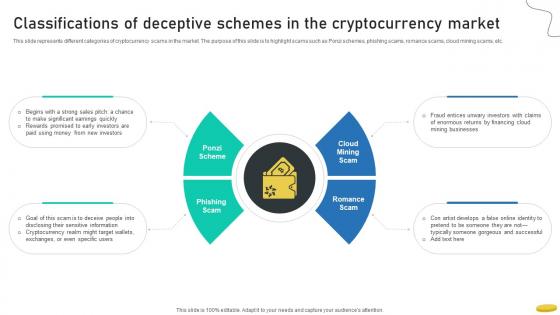
Classifications Of Deceptive Schemes In The Cryptocurrency Management With Blockchain
This slide represents different categories of cryptocurrency scams in the market. The purpose of this slide is to highlight scams such as Ponzi schemes, phishing scams, romance scams, cloud mining scams, etc.Find highly impressive Classifications Of Deceptive Schemes In The Cryptocurrency Management With Blockchain on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Classifications Of Deceptive Schemes In The Cryptocurrency Management With Blockchain for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
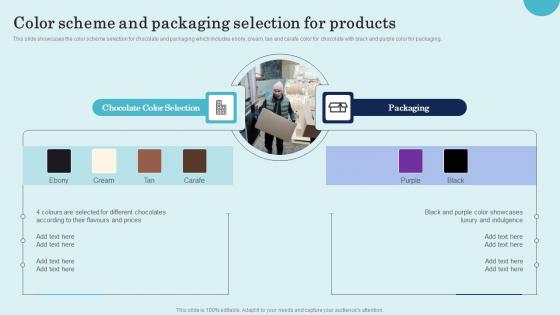
Color Scheme And Packaging Selection For Products Product Repositioning Technique Topics Pdf
This slide showcases the color scheme selection for chocolate and packaging which includes ebony, cream, tan and carafe color for chocolate with black and purple color for packaging. Want to ace your presentation in front of a live audience Our Color Scheme And Packaging Selection For Products Product Repositioning Technique Topics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
Program Management Timetable Bundle Corrective Action Log Ppt Icon Structure PDF
Deliver and pitch your topic in the best possible manner with this program management timetable bundle corrective action log ppt icon structure pdf. Use them to share invaluable insights on identified problem, required corrective action, person responsible and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
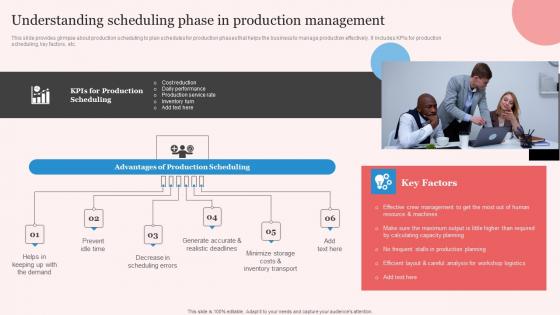
Understanding Scheduling Enhancing Manufacturing Operation Effectiveness Guidelines Pdf
This slide provides glimpse about production scheduling to plan schedules for production phases that helps the business to manage production effectively. It includes KPIs for production scheduling, key factors, etc. Are you searching for a Understanding Scheduling Enhancing Manufacturing Operation Effectiveness Guidelines Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Understanding Scheduling Enhancing Manufacturing Operation Effectiveness Guidelines Pdf from Slidegeeks today.
Business Planner Calendar Icon With Marked Schedule Sample PDF
Presenting business planner calendar icon with marked schedule sample pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including business planner calendar icon with marked schedule. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Popular Clickjacking Methods Used By Hackers Comprehensive Smartphone Banking Microsoft Pdf
This slide contains overview section which can be used to get basic understanding of clickjacking as a cyberattack. It also includes information about most famous clickjacking methods which are cursor jacking, mousejack, filejack and cookieJacking. Slidegeeks is here to make your presentations a breeze with Popular Clickjacking Methods Used By Hackers Comprehensive Smartphone Banking Microsoft Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Calendar Time Management Vector Icon Ppt PowerPoint Presentation Deck
This is a calendar time management vector icon ppt powerpoint presentation deck. This is a three stage process. The stages in this process are agenda, schedule, timetable.
Work Plan With Timetable Template 1 Ppt PowerPoint Presentation Icon Slides
This is a work plan with timetable template 1 ppt powerpoint presentation icon slides. This is a two stage process. The stages in this process are month, activities, business, marketing, success.
Work Plan With Timetable Template 1 Ppt PowerPoint Presentation Icon Show
This is a work plan with timetable template 1 ppt powerpoint presentation icon show. This is a two stage process. The stages in this process are acceptance of the research proposal, talks with local representatives in study area, development of research tools, sample selection and talks with community, training of enumerators.
Program Management Timetable Bundle Detailed Cost Estimate Variance Log Ppt Icon Outfit PDF
Deliver an awe inspiring pitch with this creative program management timetable bundle detailed cost estimate variance log ppt icon outfit pdf bundle. Topics like budget, variance, project manager can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Program Management Timetable Bundle Revised Cost Request Ppt Icon Design Templates PDF
Deliver and pitch your topic in the best possible manner with this program management timetable bundle revised cost request ppt icon design templates pdf. Use them to share invaluable insights on services and charges, supplies, capital outlays and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
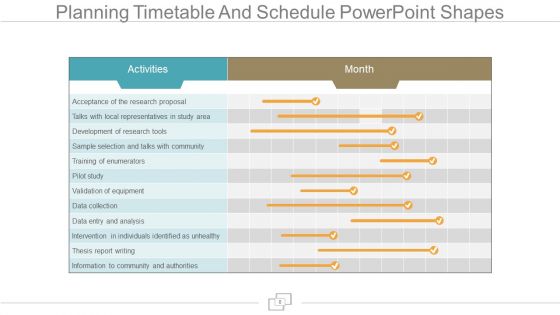
Planning Timetable And Schedule Powerpoint Shapes
This is a planning timetable and schedule powerpoint shapes. This is a one stage process. The stages in this process are activities, month.
Yearly Schedule Planner Icon With Event Timeline Inspiration PDF
Pitch your topic with ease and precision using this Yearly Schedule Planner Icon With Event Timeline Inspiration PDF. This layout presents information on Schedule Planner, Event Timeline. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
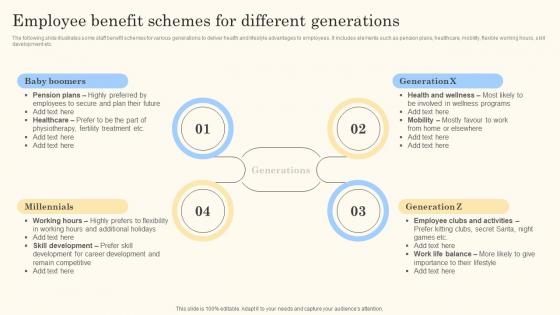
Employee Benefit Schemes For Different Action Steps For Employee Engagement Professional Pdf
The following slide illustrates some staff benefit schemes for various generations to deliver health and lifestyle advantages to employees. It includes elements such as pension plans, healthcare, mobility, flexible working hours, skill development etc.Presenting this PowerPoint presentation, titled Employee Benefit Schemes For Different Action Steps For Employee Engagement Professional Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Employee Benefit Schemes For Different Action Steps For Employee Engagement Professional Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Employee Benefit Schemes For Different Action Steps For Employee Engagement Professional Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Color Scheme And Packaging Rebranding Marketing Strategies For Effective Mockup Pdf
This slide showcases the color scheme selection for chocolate and packaging which includes ebony, cream, tan and carafe color for chocolate with black and purple color for packaging. Want to ace your presentation in front of a live audience Our Color Scheme And Packaging Rebranding Marketing Strategies For Effective Mockup Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Five Year Application Deployment Planner Work Schedule Icons
We present our five year application deployment planner work schedule icons. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five year application deployment planner work schedule icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Three Months Social Media Management Planner Work Schedule Icons
Presenting our jaw-dropping three months social media management planner work schedule icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Understanding Scheduling Phase Operations Strategy Improve Business Productivity Mockup Pdf
This slide provides glimpse about production scheduling to plan schedules for production phases that helps the business to manage production effectively. It includes KPIs for production scheduling, key factors, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Understanding Scheduling Phase Operations Strategy Improve Business Productivity Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Understanding Scheduling Phase Operations Strategy Improve Business Productivity Mockup Pdf today and make your presentation stand out from the rest
Sales Diagram Agenda List Of Items Business Diagram
Touch Base With Our Sales Diagram Agenda List Of Items Business Diagram Powerpoint Templates. Review Your Growth With Your Audience.
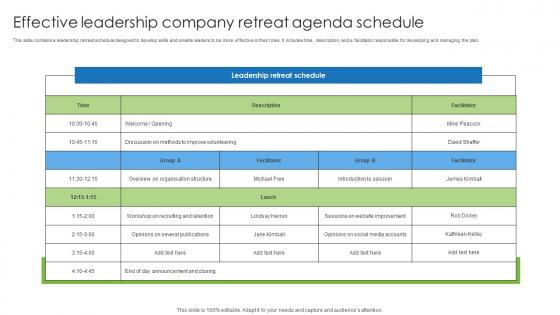
Effective Leadership Company Retreat Agenda Schedule Introduction Pdf
This slide contains a leadership retreat schedule designed to develop skills and enable leaders to be more effective in their roles. It includes time, description, and a facilitator responsible for developing and managing the plan. Pitch your topic with ease and precision using this Effective Leadership Company Retreat Agenda Schedule Introduction Pdf. This layout presents information on Effective, Company, Schedule. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Monthly Product Master Production Schedule Streamlining Production Operational Inspiration PDF
This slide provides glimpse about creating master production schedule for efficient inventory and demand management. It includes month, beginning inventory, total demand, balance, required production, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Monthly Product Master Production Schedule Streamlining Production Operational Inspiration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Monthly Product Master Production Schedule Streamlining Production Operational Inspiration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Hacker Performing Cyber Attack Vector Icon Ppt PowerPoint Presentation Icon Professional PDF
Presenting hacker performing cyber attack vector icon ppt powerpoint presentation icon professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including hacker performing cyber attack vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon Of Hacker Launching Cyber Phishing Scams And Attacks Background PDF
Presenting icon of hacker launching cyber phishing scams and attacks background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including icon of hacker launching cyber phishing scams and attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Monthly Product Master Production Schedule Production Quality Administration Background Pdf
This slide provides glimpse about creating master production schedule for efficient inventory and demand management. It includes month, beginning inventory, total demand, balance, required production, etc.If you are looking for a format to display your unique thoughts, then the professionally designed Monthly Product Master Production Schedule Production Quality Administration Background Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Monthly Product Master Production Schedule Production Quality Administration Background Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
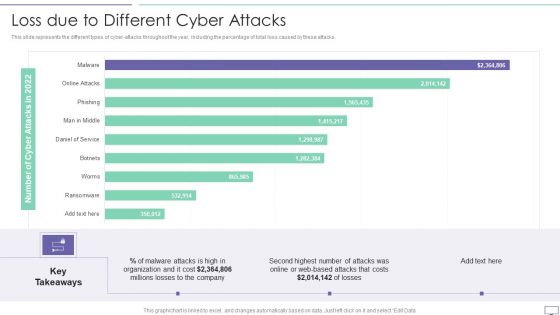
IT Security Hacker Loss Due To Different Cyber Attacks Rules PDF
This slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks.Deliver an awe inspiring pitch with this creative IT Security Hacker Loss Due To Different Cyber Attacks Rules PDF bundle. Topics like Malware Attacks, Millions Losses, Based Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Russian Cyber Attacks On Ukraine IT Hacker Group Anonymous Has Waged Icons PDF
This slide depicts the anonymous organization and how they have started a cyberwar against Russia by gathering worldwide hackers through Twitter. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it hacker group anonymous has waged icons pdf. Use them to share invaluable insights on hacker group anonymous has waged a cyberwar against russia and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Wiper Spyware Attack Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Sample PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack ukraine and russia cyber warfare russian vigilante hacker sample pdf Use them to share invaluable insights on ukraine and russia cyber warfare russian vigilante hacker and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Diagram List Of Items For Agenda Meeting Presentation Template
This business slide has been designed with list diagram with stop watch. You may download this diagram to display business agenda. Emphasize on business process with this diagram slide. Chart the course you intend to take.
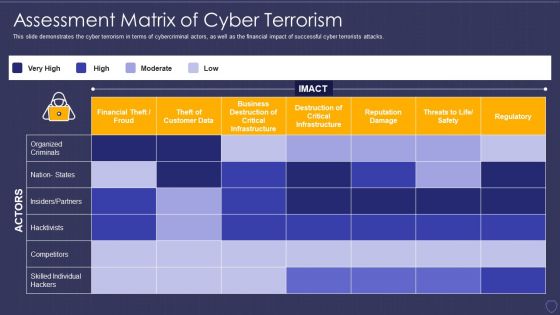
Global Cyber Terrorism Incidents On The Rise IT Assessment Matrix Of Cyber Terrorism Ideas PDF
This slide demonstrates the cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it assessment matrix of cyber terrorism ideas pdf bundle. Topics like financial theft or froud, reputation damage, regulatory, competitors, destruction of critical infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Agenda PowerPoint Icon C
photo of a day planner.
Agenda PowerPoint Icon Cc
photo of a day planner.
Agenda PowerPoint Icon F
photo of a day planner.
Agenda PowerPoint Icon R
photo of a day planner.
Agenda PowerPoint Icon S
photo of a day planner.
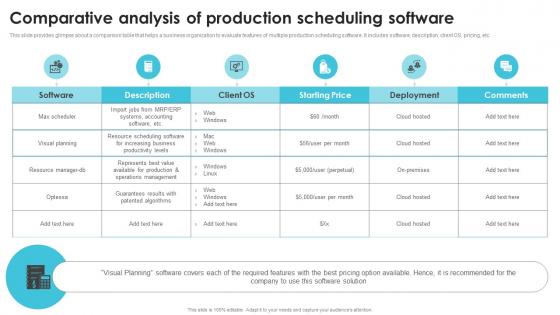
Comparative Analysis Of Production Scheduling Streamlining Production Operational Ideas PDF
This slide provides glimpse about a comparison table that helps a business organization to evaluate features of multiple production scheduling software. It includes software, description, client OS, pricing, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Comparative Analysis Of Production Scheduling Streamlining Production Operational Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
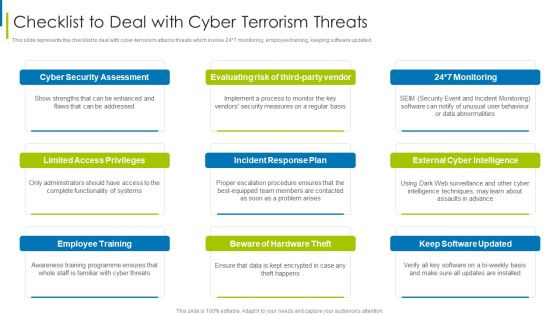
Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Planning Timeline Eight Steps With Icons Ppt PowerPoint Presentation Inspiration Graphic Tips
This is a project planning timeline eight steps with icons ppt powerpoint presentation inspiration graphic tips. This is a eight stage process. The stages in this process are agenda, schedule, timetable.
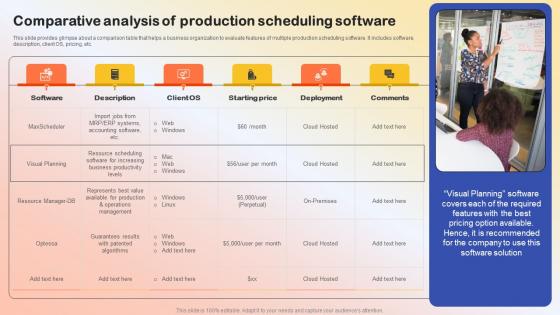
Comparative Analysis Of Production Scheduling Production Quality Administration Inspiration Pdf
This slide provides glimpse about a comparison table that helps a business organization to evaluate features of multiple production scheduling software. It includes software, description, client OS, pricing, etc.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Comparative Analysis Of Production Scheduling Production Quality Administration Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Third Schedule Case In Powerpoint And Google Slides Cpb
Introducing our well designed Third Schedule Case In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Third Schedule Case. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Overview Of Black Hat SEO With Techniques Training Ppt
This slide provides information regarding the overview of black hat SEO. It covers details of common black hat SEO techniques such as cloaking, redirecting to different URLs, etc. Further, it includes advantages and disadvantages of black hat SEO techniques.
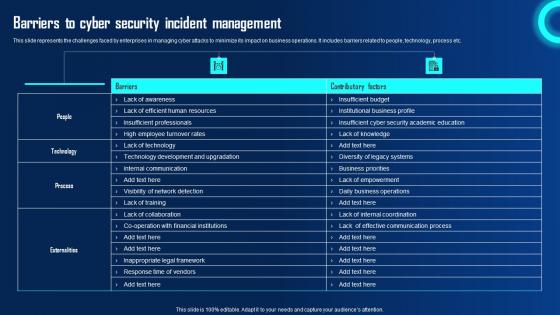
Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Portrait PDF
This slide depicts the russian vigilante hacker who was able to bring down some official ukrainian websites and one military website along with his group of 6 hackers. Welcome to our selection of the Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Flexible Work Schedules HR Policy Overview Powerpoint Presentation Ppt Template Pdf
Welcome to our selection of the Flexible Work Schedules HR Policy Overview Powerpoint Presentation Ppt Template Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
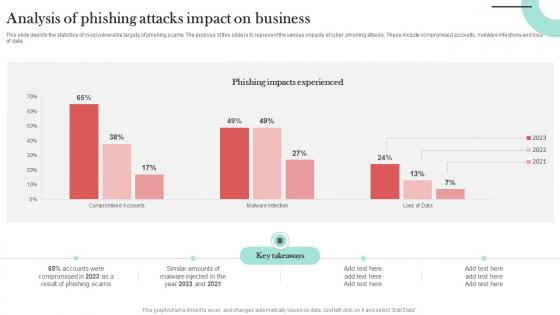
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Schedule PowerPoint Icon C
man drew a blank schedule on white background
Schedule PowerPoint Icon Cc
man drew a blank schedule on white background
Schedule PowerPoint Icon S
man drew a blank schedule on white background

Agenda Schedule Management Techniques For Project Goals PPT Presentation
Find a pre-designed and impeccable Agenda Schedule Management Techniques For Project Goals PPT Presentation. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
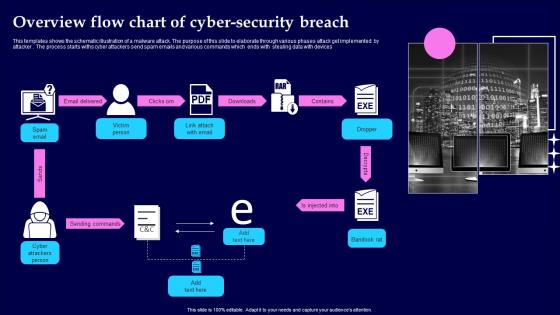
Overview Flow Chart Of Cyber Security Breach Summary Pdf
This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices Pitch your topic with ease and precision using this Overview Flow Chart Of Cyber Security Breach Summary Pdf This layout presents information on Email Delivered, Sending Commands, Injected Into It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Top Countries Effect By Cyber Security Breach Background Pdf
This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc. Pitch your topic with ease and precision using this Top Countries Effect By Cyber Security Breach Background Pdf This layout presents information on Malware Attack, Countries Effect, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Exploitation IT Purpose Of Hackers Infographics PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a cyber exploitation it purpose of hackers infographics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computer fraud, privacy breach, electronic money laundering, electronic funds transfer, denial of service attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
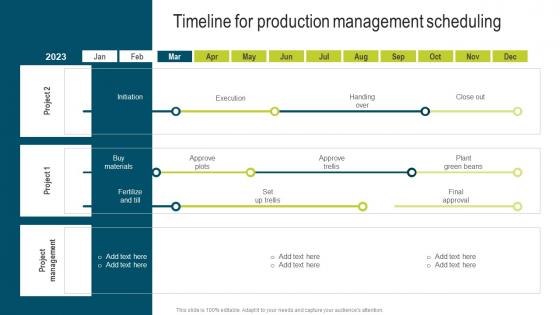
Timeline For Production Management Scheduling Developing Extensive Plan For Operational Structure Pdf
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Timeline For Production Management Scheduling Developing Extensive Plan For Operational Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Timeline For Production Management Scheduling Developing Extensive Plan For Operational Structure Pdf today and make your presentation stand out from the rest.

Production Scheduling Software Pricing Developing Extensive Plan For Operational Structure Pdf
This slide provides glimpse about multiple pricing plans for selected production scheduling software with its features. It includes features such as capacity management, accounting integrations, activity tracking, alertsnotifications, agile methodologies, etc. Want to ace your presentation in front of a live audience Our Production Scheduling Software Pricing Developing Extensive Plan For Operational Structure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Modernization And Product Listening Hats With Process Dealing Approach Formats PDF
This slide covers listening hats based on process fact creativity benefits cautions and feelings. This is a modernization and product listening hats with process dealing approach formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like instinct based approach, spotting risk, negative approach, logical reasoning, positives, plus points, red hat thinking feelings, black hat thinking cautions, yellow hat thinking benefits, green hat thinking creativity, white hat thinking facts, blue hat thinking process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
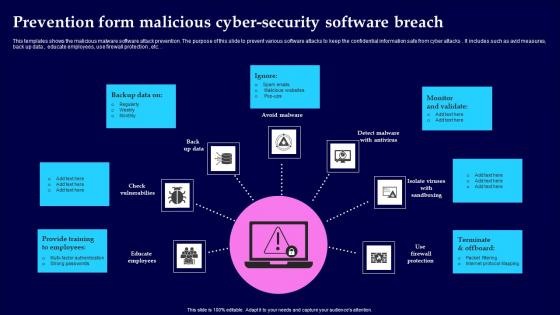
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Calendar Schedule Planner Vector Icon Ppt PowerPoint Presentation Gallery Demonstration PDF
Presenting calendar schedule planner vector icon ppt powerpoint presentation gallery demonstration pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including calendar schedule planner vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Time And Date Schedule Planner Vector Icon Ppt PowerPoint Presentation File Layouts PDF
Presenting time and date schedule planner vector icon ppt powerpoint presentation file layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including time and date schedule planner vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Yearly Schedule Planner Icon With Event Date And Time Clipart PDF
Presenting Yearly Schedule Planner Icon With Event Date And Time Clipart PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Planner Icon, Event Date And Time. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Overview Of Different Types Of Phishing Attacks Man In The Middle Phishing IT
This slide outlines the various types of cyber phishing attacks. The types include email phishing, HTTPS phishing, whaling, smishing, angler phishing, pharming, spear phishing, pop-up phishing, clone phishing, evil twin scams, watering hole attacks, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Overview Of Different Types Of Phishing Attacks Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest
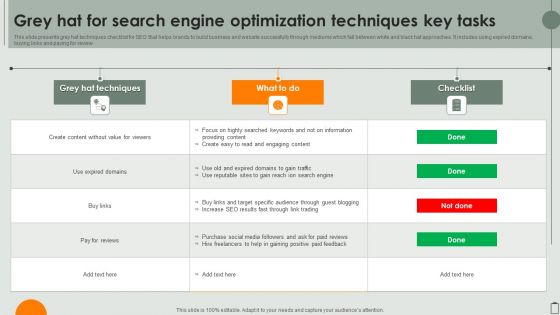
Grey Hat For Search Engine Optimization Techniques Key Tasks Elements PDF
This slide presents grey hat techniques checklist for SEO that helps brands to build business and website successfully through mediums which fall between white and black hat approaches. It includes using expired domains, buying links and paying for review. Showcasing this set of slides titled Grey Hat For Search Engine Optimization Techniques Key Tasks Elements PDF. The topics addressed in these templates are Information Providing Content, Expired Domains Gain Traffic, Target Specific Audience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

White Hat SEO With Techniques Advantages And Limitations Training Ppt
The purpose of the following slide is to provide an overview of white hat SEO. It also includes information regarding the major white hat techniques, advantages, and limitations.
Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Coders Guide To Web Design Development Project Strategy Icon Slides PDF
Persuade your audience using this Coders Guide To Web Design Development Project Strategy Icon Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Coders Guide Web Design, Development Project Strategy Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Modernization And Product Listening Hats For Situation Handling And Analysis Formats PDF
This slide covers listening hats to analyze and handling situation based on factual emotional critical positive creative and process controlling approach. This is a modernization and product listening hats for situation handling and analysis formats pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like white factual, red emotional, black critical, yellow positive, green creative, blue process control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
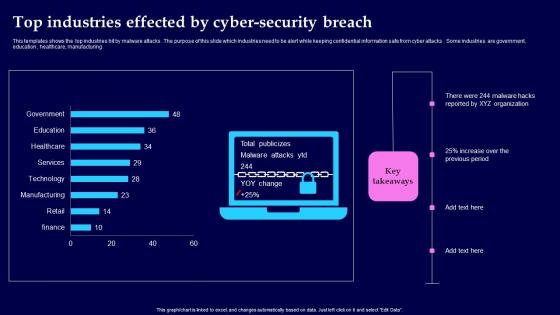
Top Industries Effected By Cyber Security Breach Background Pdf
This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing Showcasing this set of slides titled Top Industries Effected By Cyber Security Breach Background Pdf The topics addressed in these templates are Top Industries Effected, Cyber Security Breach All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
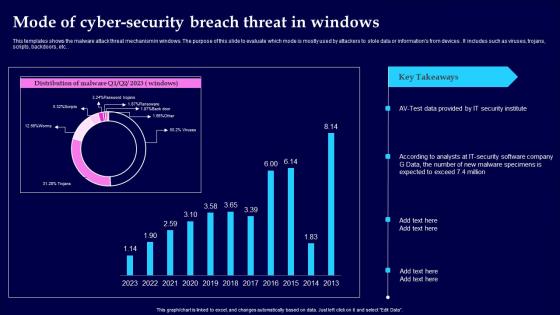
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
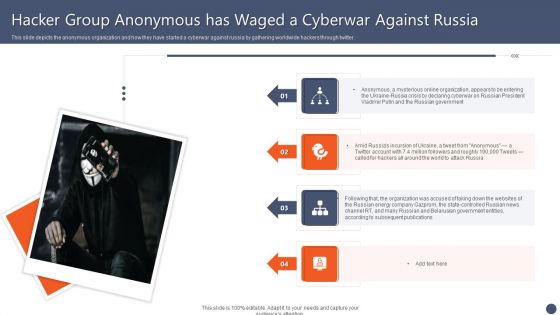
Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF
This slide depicts the anonymous organization and how they have started a cyberwar against russia by gathering worldwide hackers through twitter. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Exploitation IT Impact Of Ethical Hackers On Business Template PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc. Deliver an awe inspiring pitch with this creative cyber exploitation it impact of ethical hackers on business template pdf bundle. Topics like impact of ethical hackers on business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Russian Cyber Attacks On Ukraine Summary PDF
This is a agenda for russian cyber attacks on ukraine summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technical, analysis, websites, globally. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
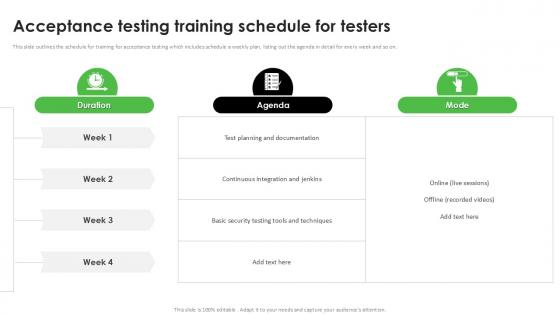
Acceptance Testing Training Schedule For Testers Acceptance Testing PPT Sample
This slide outlines the schedule for training for acceptance testing which includes schedule a weekly plan, listing out the agenda in detail for every week and so on. There are so many reasons you need a Acceptance Testing Training Schedule For Testers Acceptance Testing PPT Sample. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Stock Photo White Hat For Patrick Day PowerPoint Slide
We have added colors in the celebration of Patrick's Day. To show our joy we have designed this beautiful image . This image contains the graphic of white hat which is a traditional hat of this festival. Display the colors of this festival in your creativity by using this exclusive image.

Roles And Responsibilities In Project Schedule Management Techniques PPT Template
This slide presents roles and responsibilities involved in project scheduling for organised operations throughout different phases. It includes owner, responsibilities and status of tasks allotted. Take your projects to the next level with our ultimate collection of Roles And Responsibilities In Project Schedule Management Techniques PPT Template. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Russian Cyber Attacks On Ukraine IT Ukraine And Russia Cyber Warfare Impact Information PDF
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it ukraine and russia cyber warfare impact information pdf bundle. Topics like ukraine and russia cyber warfare russian vigilante hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
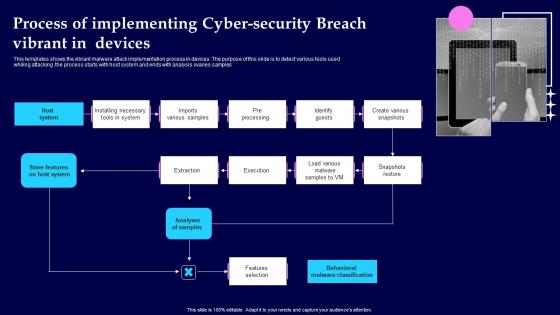
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
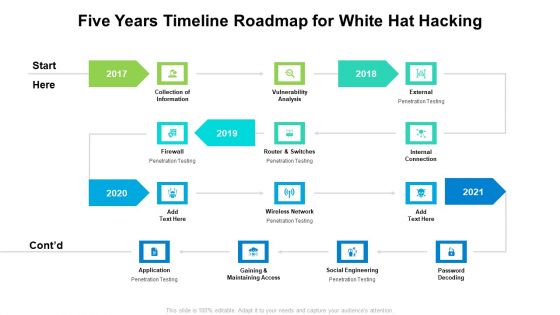
Five Years Timeline Roadmap For White Hat Hacking Structure
We present our five years timeline roadmap for white hat hacking structure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five years timeline roadmap for white hat hacking structure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Timeline Roadmap For White Hat Hacking Guidelines
We present our half yearly timeline roadmap for white hat hacking guidelines. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly timeline roadmap for white hat hacking guidelines in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
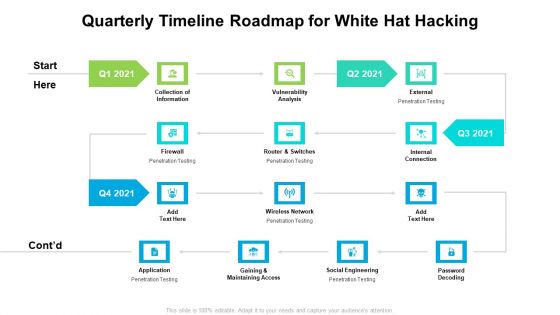
Quarterly Timeline Roadmap For White Hat Hacking Slides
We present our quarterly timeline roadmap for white hat hacking slides. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly timeline roadmap for white hat hacking slides in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Timeline Roadmap For White Hat Hacking Themes
We present our six months timeline roadmap for white hat hacking themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months timeline roadmap for white hat hacking themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
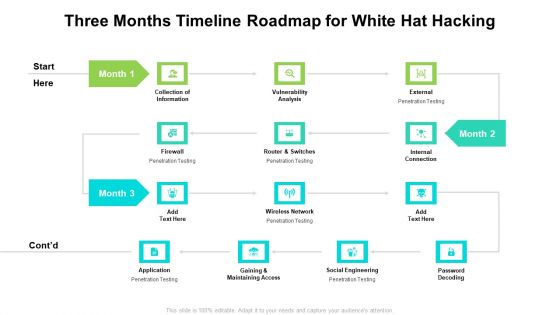
Three Months Timeline Roadmap For White Hat Hacking Topics
We present our three months timeline roadmap for white hat hacking topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months timeline roadmap for white hat hacking topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Understanding Scheduling Phase Developing Extensive Plan For Operational Ideas Pdf
This slide provides glimpse about production scheduling to plan schedules for production phases that helps the business to manage production effectively. It includes KPIs for production scheduling, key factors, etc. Find highly impressive Understanding Scheduling Phase Developing Extensive Plan For Operational Ideas Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Understanding Scheduling Phase Developing Extensive Plan For Operational Ideas Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Understanding Scheduling Phase In Production Streamlining Production Operational Slides PDF
This slide provides glimpse about production scheduling to plan schedules for production phases that helps the business to manage production effectively. It includes KPIs for production scheduling, key factors, etc. Are you searching for a Understanding Scheduling Phase In Production Streamlining Production Operational Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Understanding Scheduling Phase In Production Streamlining Production Operational Slides PDF from Slidegeeks today.
Icons Slide For White Hat Hacking Ppt Inspiration Sample PDF
Presenting our innovatively structured icons slide for white hat hacking ppt inspiration sample pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
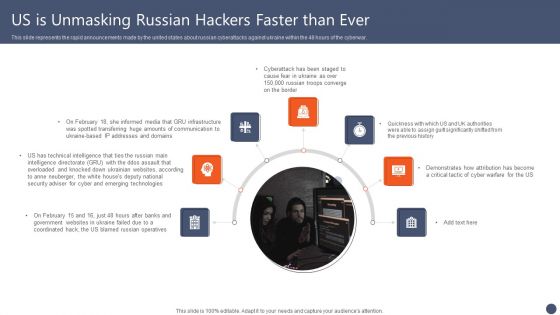
Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF
This slide represents the rapid announcements made by the united states about russian cyberattacks against ukraine within the 48 hours of the cyberwar. Explore a selection of the finest Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Series Of Cyber Security Atta to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
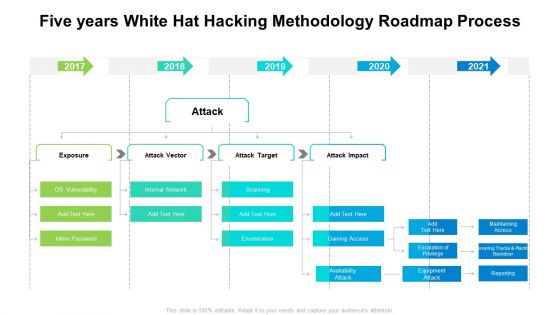
Five Years White Hat Hacking Methodology Roadmap Process Slides
Presenting our innovatively structured five years white hat hacking methodology roadmap process slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
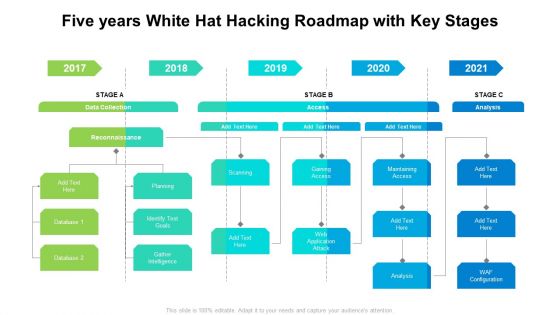
Five Years White Hat Hacking Roadmap With Key Stages Topics
Introducing our five years white hat hacking roadmap with key stages topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Half Yearly White Hat Hacking Methodology Roadmap Process Professional
Presenting our innovatively structured half yearly white hat hacking methodology roadmap process professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
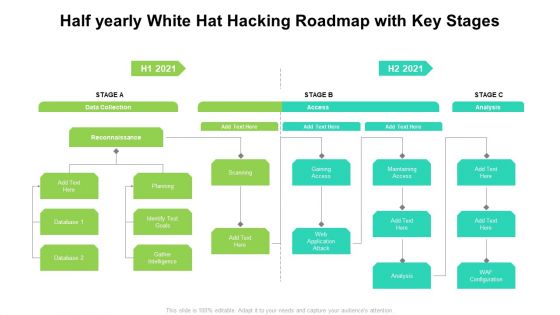
Half Yearly White Hat Hacking Roadmap With Key Stages Brochure
Introducing our half yearly white hat hacking roadmap with key stages brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
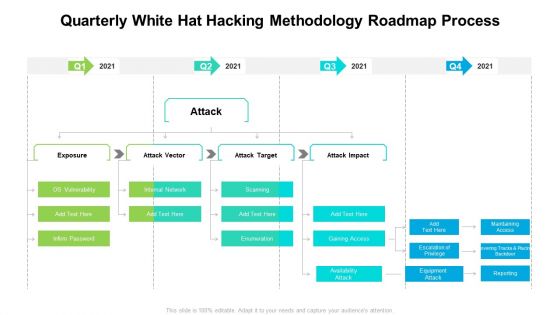
Quarterly White Hat Hacking Methodology Roadmap Process Information
Presenting our innovatively structured quarterly white hat hacking methodology roadmap process information Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
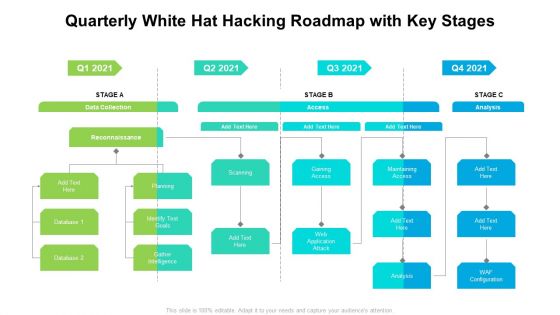
Quarterly White Hat Hacking Roadmap With Key Stages Designs
Introducing our quarterly white hat hacking roadmap with key stages designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Quarterly White Hat Hacking With Penetration Testing Roadmap Rules
Presenting our jaw dropping quarterly white hat hacking with penetration testing roadmap rules. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
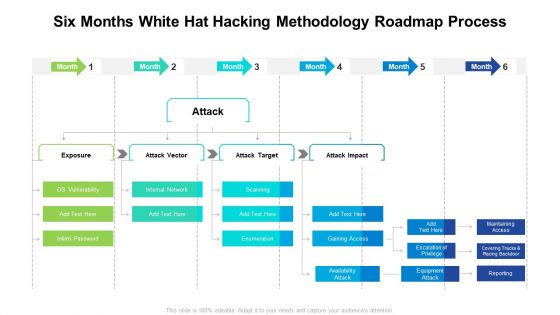
Six Months White Hat Hacking Methodology Roadmap Process Infographics
Presenting our innovatively structured six months white hat hacking methodology roadmap process infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Six Months White Hat Hacking Roadmap With Key Stages Infographics
Introducing our six months white hat hacking roadmap with key stages infographics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Three Months White Hat Hacking Methodology Roadmap Process Professional
Presenting our innovatively structured three months white hat hacking methodology roadmap process professional Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Three Months White Hat Hacking Roadmap With Key Stages Guidelines
Introducing our three months white hat hacking roadmap with key stages guidelines. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides
This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
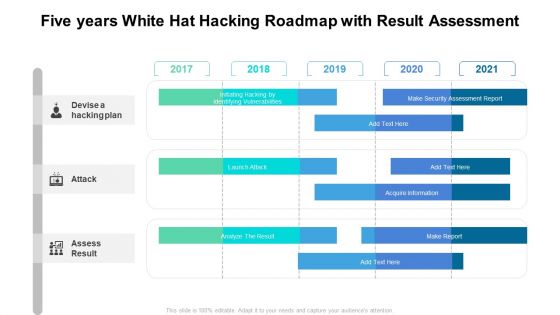
Five Years White Hat Hacking Roadmap With Result Assessment Guidelines
Presenting the five years white hat hacking roadmap with result assessment guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Five Years White Hat Hacking With Penetration Testing Roadmap Icons
Presenting our jaw dropping five years white hat hacking with penetration testing roadmap icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
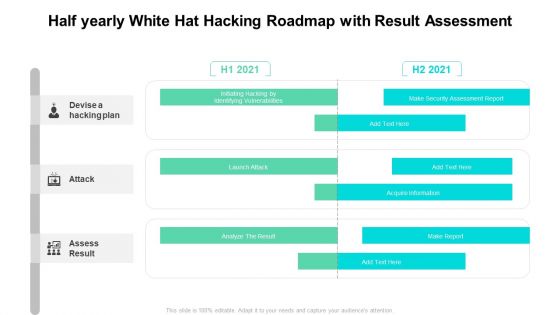
Half Yearly White Hat Hacking Roadmap With Result Assessment Graphics
Presenting the half yearly white hat hacking roadmap with result assessment graphics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
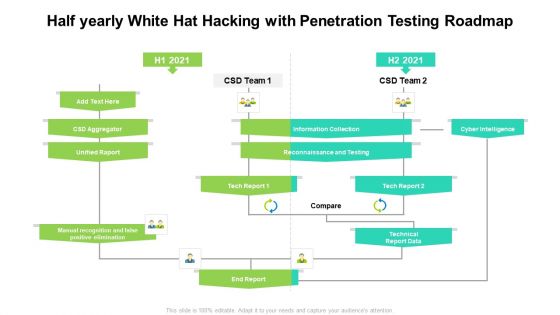
Half Yearly White Hat Hacking With Penetration Testing Roadmap Designs
Presenting our jaw dropping half yearly white hat hacking with penetration testing roadmap designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
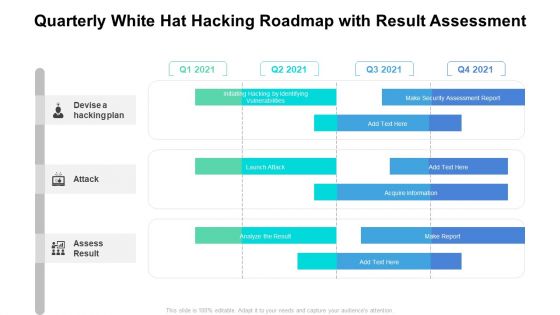
Quarterly White Hat Hacking Roadmap With Result Assessment Microsoft
Presenting the quarterly white hat hacking roadmap with result assessment microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
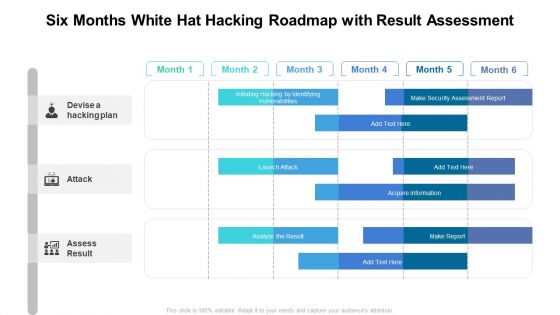
Six Months White Hat Hacking Roadmap With Result Assessment Rules
Presenting the six months white hat hacking roadmap with result assessment rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months White Hat Hacking With Penetration Testing Roadmap Infographics
Presenting our jaw dropping six months white hat hacking with penetration testing roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Three Months White Hat Hacking Roadmap With Result Assessment Mockup
Presenting the three months white hat hacking roadmap with result assessment mockup. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

 Home
Home