Process Safety Dashboard
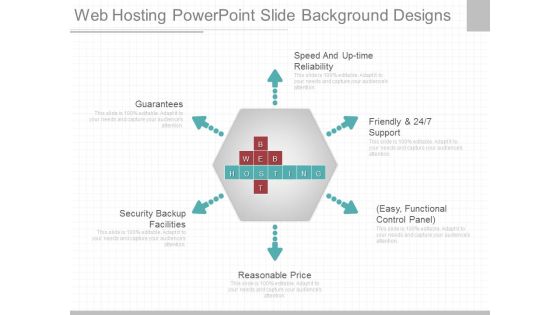
Web Hosting Powerpoint Slide Background Designs
This is a web hosting powerpoint slide background designs. This is a six stage process. The stages in this process are speed and up time reliability, friendly and support, easy, functional control panel, reasonable price, security backup facilities, guarantees, best, web, hosting.

Implementation Of Effective Data Governance Ppt Powerpoint Show
This is a implementation of effective data governance ppt powerpoint show. This is a six stage process. The stages in this process are dwh and bi management, data quality management, document and contain management, reference and master data management, business intelligence management, database operations management, meta data management, database security management, data architecture and modelling management, data development, data governance.

Roadmap To Organizing A Successful Conference Ppt Presentation
This is a roadmap to organizing a successful conference ppt presentation. This is a six stage process. The stages in this process are set and data, roadmap to organizing a successful conference, secure location, determine target groups, set vision and objectives, start securing speakers.

System Integration With Configuration Deployment And Visualization Ppt PowerPoint Presentation File Skills
Presenting this set of slides with name system integration with configuration deployment and visualization ppt powerpoint presentation file skills. This is a eight stage process. The stages in this process are configuration, deployment, historization, connectivity, visualization, web reporting, collaboration, security, plant model. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Enterprise Integration Solution Diagram Powerpoint Guide
This is a enterprise integration solution diagram powerpoint guide. This is a six stage process. The stages in this process are policy management, log management, vulnerability assessment, web application scanning, file integrity monitoring, vulnerability management, discovery, protection, monitoring, reporting, security, risk and compliance.
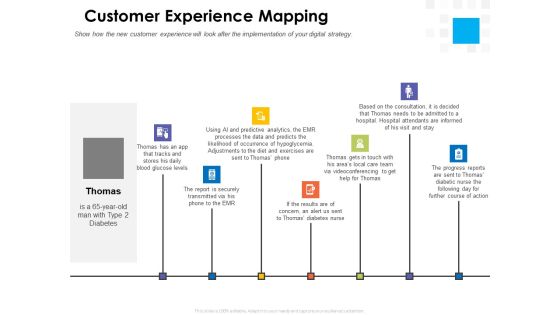
Digital Transformation Strategy Roadmap Customer Experience Mapping Ppt PowerPoint Presentation Inspiration Maker PDF
Presenting this set of slides with name digital transformation strategy roadmap customer experience mapping ppt powerpoint presentation inspiration maker pdf. This is a seven stage process. The stages in this process are blood glucose levels, securely transmitted, progress reports, consultation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Android Framework For Apps Development And Deployment Overcoming The Challenges By The Company Inspiration PDF
Presenting this set of slides with name android framework for apps development and deployment overcoming the challenges by the company inspiration pdf. This is a four stage process. The stages in this process are data security, price transparency, informative. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
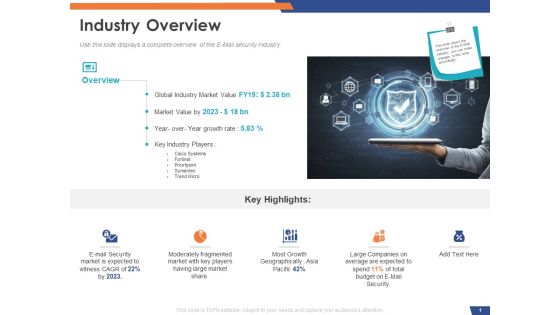
Email Security Market Research Report Industry Overview Ppt Outline Graphic Images PDF
Presenting this set of slides with name email security market research report industry overview ppt outline graphic images pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Five Steps Of Effective Investment Plan Ppt PowerPoint Presentation Portfolio Infographics PDF
Presenting five steps of effective investment plan ppt powerpoint presentation portfolio infographics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including margin of safety, invest in assets you understand, measuring success by the underlying operating, performance of the business, not the stock price, be rational about price, minimize costs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
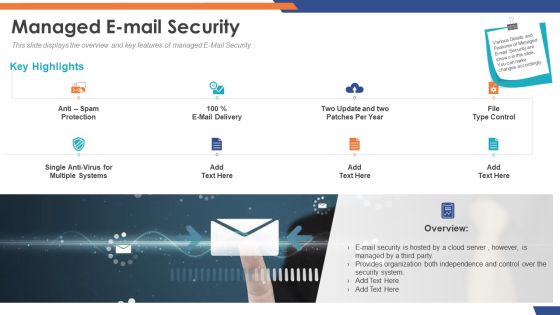
Email Security Market Research Report Managed E Mail Security Introduction PDF
Presenting this set of slides with name email security market research report managed e mail security introduction pdf. This is a two stage process. The stages in this process are e mail security is hosted by a cloud server, however is managed by a third party, provides organization both independence and control over the security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
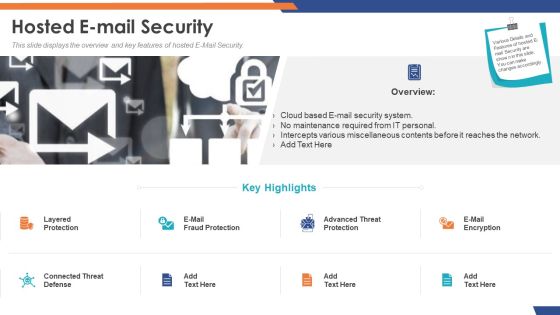
Email Security Market Research Report Hosted E Mail Security Formats PDF
Presenting this set of slides with name email security market research report hosted e mail security formats pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
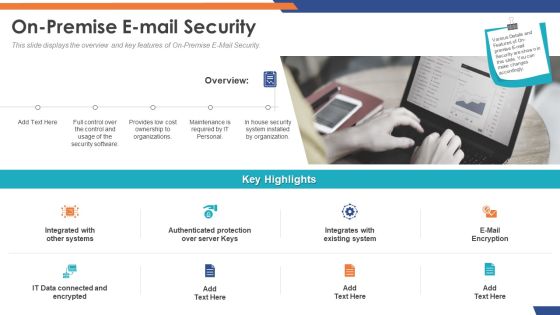
Email Security Market Research Report On Premise E Mail Security Mockup PDF
Presenting this set of slides with name email security market research report on premise e mail security mockup pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Table Of Contents Topics PDF
Presenting this set of slides with name email security market research report table of contents topics pdf. This is a eight stage process. The stages in this process are market introduction, market dynamics, market by segments, market competition analysis, market forecasting and projections, issues faced by companies, porter 5 force model. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Key Stats Department Topics PDF
Presenting this set of slides with name email security market research report key stats department topics pdf. This is a five stage process. The stages in this process are 95 percent of malware are delivered via e mails, 79 percent of it companies consider phishing most challenging issue. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
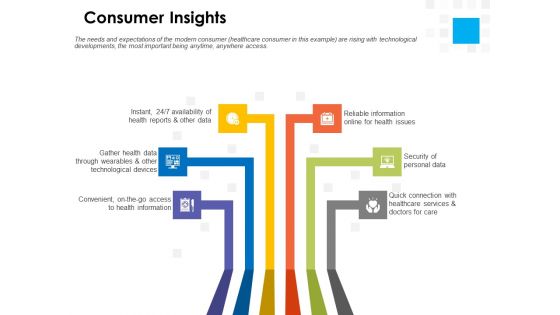
Digital Transformation Strategy Roadmap Consumer Insights Ppt PowerPoint Presentation Layouts Design Inspiration PDF
Presenting this set of slides with name digital transformation strategy roadmap consumer insights ppt powerpoint presentation layouts design inspiration pdf. This is a six stage process. The stages in this process are convenient access, health information, quick connection, healthcare services, security personal data, reliable information online health issues, health reports, gather health data through wearables, technological devices. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Next Steps For Company Online Database Security Infographics PDF
Presenting this set of slides with name best data security software next steps for company online database security infographics pdf. This is a two stage process. The stages in this process are discuss the desired changes, accept the proposal, once we get the notification of your proposal acceptance, we will send you the separate copy of the signed contract for your record. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
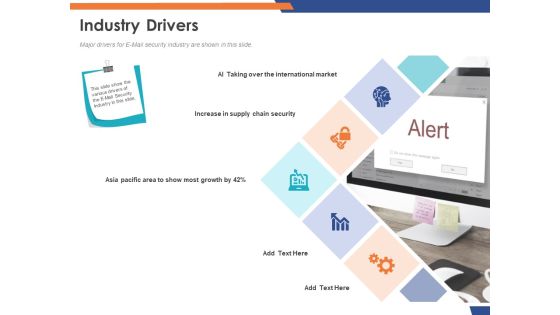
Email Security Market Research Report Industry Drivers Ppt Outline Maker PDF
Presenting this set of slides with name email security market research report industry drivers ppt outline maker pdf. This is a five stage process. The stages in this process are increase in supply chain security, asia pacific area to show most growth, ai taking over the international market. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Banking Overview Diagram Sample Ppt Slides
This is a banking overview diagram sample ppt slides. This is a one stage process. The stages in this process are banking and finance, wealth management, network security and solution, systems integration, commercial banking, database development and administration, data warehouse solutions, consumer banking, ui, ux, application design and development, project management, business analysis and quality assurance, investment banking, architecture services, big data and cloud computing.

ITIL Strategy Service Excellence Client Standards Checklist Contd Ppt PowerPoint Presentation Styles Example PDF
Presenting this set of slides with name itil strategy service excellence client standards checklist contd ppt powerpoint presentation styles example pdf. This is a one stage process. The stages in this process are genuine anti spam solution, vendor supported server, licensed firewall between internal, secured encryption, wireless data traffic, environment, high speed internet access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
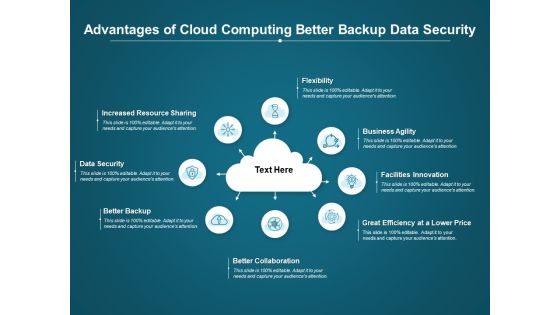
Advantages Of Cloud Computing Better Backup Data Security Ppt PowerPoint Presentation Infographics Graphics Pictures
Presenting this set of slides with name advantages of cloud computing better backup data security ppt powerpoint presentation infographics graphics pictures. This is a eight stage process. The stages in this process are flexibility, business agility, facilities innovation, increased resource sharing, data security, better backup, better collaboration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Rules And Regulations With Accuracy Ppt PowerPoint Presentation Slides Outfit
Presenting this set of slides with name cyber security rules and regulations with accuracy ppt powerpoint presentation slides outfit. This is a six stage process. The stages in this process are purpose and manner of collection, accuracy and duration of retention, use of personal data, security of personal data, information to be generally available, access to personal data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
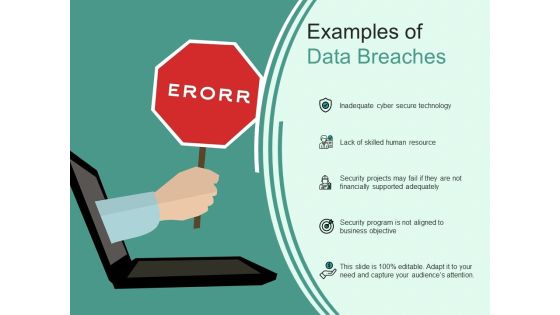
Examples Of Data Breaches Ppt PowerPoint Presentation Summary Portrait PDF
Presenting this set of slides with name examples of data breaches ppt powerpoint presentation summary portrait pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
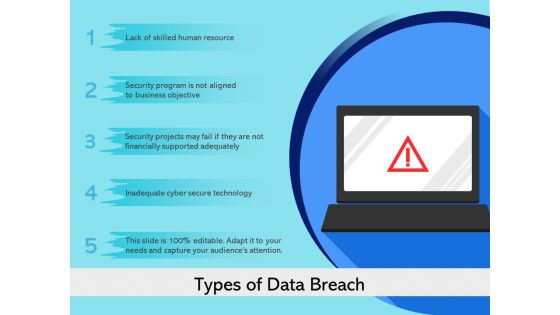
Types Of Data Breach Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name types of data breach ppt powerpoint presentation inspiration ideas pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

How System Components Work Together To Enable Amrs Mockup PDF
This slide represents how system components work together to enable autonomous mobile robots. The system components include on-site edge, network edge, core network, cloud data center, remote fleet control, sensors, compute, safety, and control module. There are so many reasons you need a How System Components Work Together To Enable Amrs Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
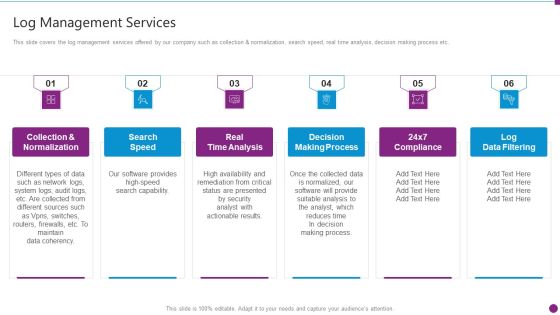
Security Information And Event Management Strategies For Financial Audit And Compliance Log Management Services Microsoft PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. This is a security information and event management strategies for financial audit and compliance log management services microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collection and normalization, search speed, real time analysis, decision making process, log data filtering. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Analysis Of Data Migration Strategic Plan Diagrams PDF
The following slide represents the comparative assessment of various types of data migration strategies to select the best based on the requirements. It includes elements such as scalability, cost effectiveness, safety, accessibility etc. Presenting Comparative Analysis Of Data Migration Strategic Plan Diagrams PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cost Effective, Application, Cloud. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Real Time Assessment Of Security Threats Log Management Services Information PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting real time assessment of security threats log management services information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Advantages And Disadvantages Application Areas Of Nanotechnology On Various Sectors Elements PDF
This slide covers advantages caused by the use of nanotechnology material in various fields like electronics, medicine along with beneficial impact and also disadvantage caused on the environment and economy like loss of jobs. Presenting Advantages And Disadvantages Application Areas Of Nanotechnology On Various Sectors Elements PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Promote Renewable energies, More Effective medicine, Compromises Safety. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Challenges With Traditional Manufacturing System Formats PDF
This slide represents the challenges with traditional manufacturing systems and it includes the limitation on customization, supply chain disruptions, labour shortage, worker safety, and longer production time. These challenges cause a delay in projects. The Challenges With Traditional Manufacturing System Formats PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Financial Reporting Considerations For The Shipping Industry Going Concern Considerations Rules PDF
This template covers evaluating impact to operating costs such as, crew costs travel, safety, sanitary etc, Additional provisions, spare parts, minimization of riding teams, inflation etc.Deliver and pitch your topic in the best possible manner with this financial reporting considerations for the shipping industry going concern considerations rules pdf. Use them to share invaluable insights on determining fuel market patterns, determining the patterns in equal value of vessels, supplementary arrangements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
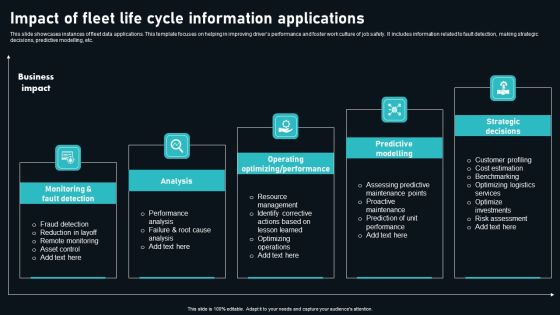
Impact Of Fleet Life Cycle Information Applications Download PDF
This slide showcases instances of fleet data applications. This template focuses on helping in improving drivers performance and foster work culture of job safety. It includes information related to fault detection, making strategic decisions, predictive modelling, etc. Presenting Impact Of Fleet Life Cycle Information Applications Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Monitoring Fault Detection, Analysis, Operating Optimizing Performance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Benefits Of Fleet Information On Business Organization Mockup PDF
This slide showcases uses of fleet data in improving performance. This template focuses on using data to improve fleet performance and increase efficiency. It includes information related to optimizing routes, improving fuel efficiency, etc. Persuade your audience using this Benefits Of Fleet Information On Business Organization Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Improve Fleet Safety, Optimize Routes, Improve Customer Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Benefits Post Implementing Risk Mitigation Strategies Topics PDF
The following slide exhibits the positive impact of implementing risk management strategies in real estate business. Customer satisfaction, improved data security, operational process improvement and reduced catastrophic events are some of the major benefits which are outlined in the slide. Deliver and pitch your topic in the best possible manner with this Key Benefits Post Implementing Risk Mitigation Strategies Topics PDF. Use them to share invaluable insights on Customer Satisfaction, Data Security, Process Improvement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Benefits Post Implementing Risk Mitigation Strategies Managing Commercial Property Risks Microsoft PDF
The following slide exhibits the positive impact of implementing risk management strategies in real estate business. Customer satisfaction, improved data security, operational process improvement and reduced catastrophic events are some of the major benefits which are outlined in the slide. Deliver an awe inspiring pitch with this creative Key Benefits Post Implementing Risk Mitigation Strategies Managing Commercial Property Risks Microsoft PDF bundle. Topics like Customer Satisfaction, Improved Data, Process Improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Science Learning Benefits In Financial Institution Ppt Icon Slide PDF
This slide contains the benefits that a finance company get from using AI, ML and DL to outsmart the competition and achieve desired business growth. It includes investment predictions, process automation, secure transactions, etc. Presenting Data Science Learning Benefits In Financial Institution Ppt Icon Slide PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investment Predictions, Process Automation, Secure Transactions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Deployment Of Smart Factory Solutions Major Impact Of Smart Factory On Enterprises Ideas PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee and asset security. This is a Deployment Of Smart Factory Solutions Major Impact Of Smart Factory On Enterprises Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Production Processes Monitoring, Asset Visibility, Data Analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
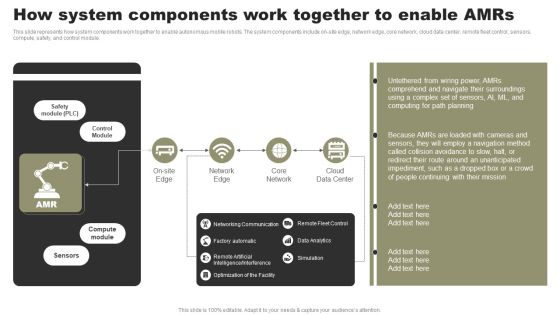
Types Of Independent Robotic System How System Components Work Together To Enable Amrs Diagrams PDF
This slide represents how system components work together to enable autonomous mobile robots. The system components include on-site edge, network edge, core network, cloud data center, remote fleet control, sensors, compute, safety, and control module. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Types Of Independent Robotic System How System Components Work Together To Enable Amrs Diagrams PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
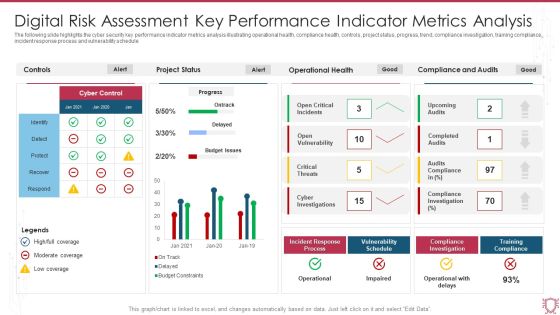
Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF
The following slide highlights the cyber security key performance indicator metrics analysis illustrating operational health, compliance health, controls, project status, progress, trend, compliance investigation, training compliance, incident response process and vulnerability schedule. Showcasing this set of slides titled Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF. The topics addressed in these templates are Project Status, Operational Health, Compliance And Audits. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
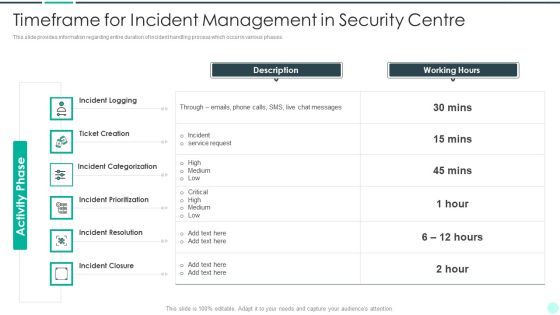
Executing Advance Data Analytics At Workspace Timeframe For Incident Management Download PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace timeframe for incident management download pdf. Use them to share invaluable insights on timeframe for incident management in security centre and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementation Steps Introduction For Identifying Users To Access CRM Portrait PDF
This slide covers the process of determining the CRM users and creating their roles and profiles in order to maintain data security. Deliver an awe inspiring pitch with this creative Implementation Steps Introduction For Identifying Users To Access CRM Portrait PDF bundle. Topics like Marketing Executive, Sales Executive, Training Executive can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
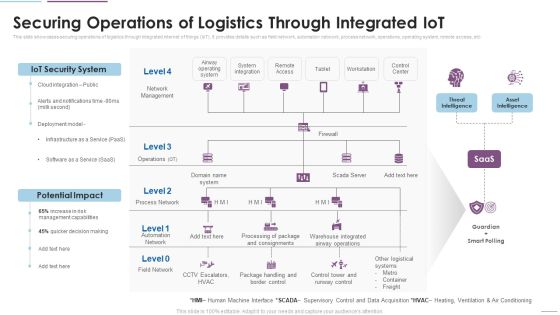
Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. This is a Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IoT Security System, Potential Impact, Network Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
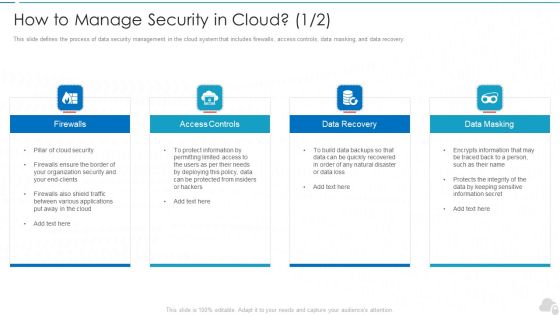
How To Manage Security In Cloud Cloud Computing Security IT Ppt Model Graphic Images PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting how to manage security in cloud cloud computing security it ppt model graphic images pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like firewalls, access controls, data recovery, data masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment How Does Cloud Security Work Formats PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Security Assessment How Does Cloud Security Work Formats PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Information Against, Transparency, Regulations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SWOT Analysis Of Cloud Computing Technology Download PDF
The following slide depicts the strengths, weaknesses, opportunities and threats SWOT to define critical success factors and assess current status. It includes elements such as flexibility, low system maintenance, data security issues, process standardization etc. Presenting SWOT Analysis Of Cloud Computing Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strengths, Weakness, Threats, Opportunities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF
This slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
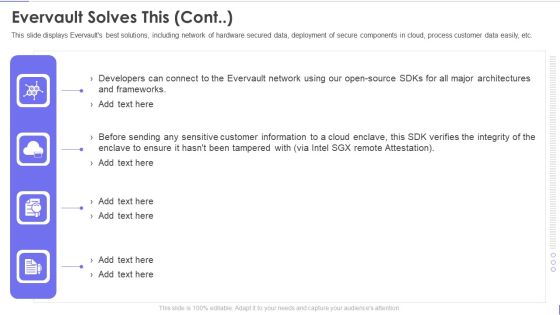
Evervault Capital Investment Elevator Pitch Deck Evervault Solves This Cont Guidelines PDF
This slide displays Evervaults best solutions, including network of hardware secured data, deployment of secure components in cloud, process customer data easily, etc. This is a evervault capital investment elevator pitch deck evervault solves this cont guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evervault solves this. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Application Threat Modeling Procedure Designs PDF
This slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Persuade your audience using this Business Application Threat Modeling Procedure Designs PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Examine Existing, Understand Capabilities, Recommendations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Checklist Of Merger And Acquisition Integration Designs PDF
This slide highlights the it checklist for merger and acquisition integration illustrating functions, objective and status. The key functions includes transition, department assignment, security access, network infrastructure, technology implementation, process and data transfer, financial integration, operations integration and human resource Presenting IT Checklist Of Merger And Acquisition Integration Designs PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Department Assignment, Financial Integration, Operation Integration This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Cyber Threat Prevention Technology Market Topics PDF
This slide provides the statistical data for IT security software user market to help business and organizations enhance process efficiency. Major security technology are authentication, IoT, Zero trust, Cloud, application security, etc. Pitch your topic with ease and precision using this IT Cyber Threat Prevention Technology Market Topics PDF. This layout presents information on Key Insights, Progressive Rate, Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Real Time Assessment Of Security Threats Security Information And Event Management Services Information PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting real time assessment of security threats security information and event management services information pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deployment Of Automated Production Technology Major Impact Of Smart Factory On Enterprises Slides PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee asset security.This modern and well-arranged Deployment Of Automated Production Technology Major Impact Of Smart Factory On Enterprises Slides PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Security Information And Event Management Services Mockup PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting security information and event management services mockup pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CRM System Implementation Stages Implementation Steps Introduction For Identifying Users To Access CRM Rules PDF
This slide covers the process of determining the CRM users and creating their roles and profiles in order to maintain data security. Presenting CRM System Implementation Stages Implementation Steps Introduction For Identifying Users To Access CRM Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sales Executive, Marketing Executive, Marketing Intern. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
 Home
Home