Problem List/icons/appstore.png

Cyber Threat Landscape In IT Security IT Ppt Infographics Design Inspiration PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this cyber threat landscape in it security it ppt infographics design inspiration pdf. Use them to share invaluable insights on competitors, organized criminals, business, infrastructure, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Circle Procedure Infographic To Manage Threat Detection And Response Ppt Styles Sample PDF
Persuade your audience using this circle procedure infographic to manage threat detection and response ppt styles sample pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including circle procedure infographic to manage threat detection and response. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing Firm Security Strategy Plan Contingency Plan For Threat Handling At Workplace Summary PDF
This slide portrays information contingency plan for handling threats at workplace with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative developing firm security strategy plan contingency plan for threat handling at workplace summary pdf bundle. Topics like server, website, local area network, wide area network, mainframe systems, distributes systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Cyber Threat Landscape In Data Security Ppt Layouts Brochure PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an awe inspiring pitch with this creative information security cyber threat landscape in data security ppt layouts brochure pdf bundle. Topics like organized criminals, financial, business disruption, reputation damage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Addressing Indicators Associated To Insider Cyber Threats Themes PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing indicators associated to insider cyber threats themes pdf. Use them to share invaluable insights on unauthorized, privileged, measures, authentication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Contingency Plan For Cyber Threat Handling Brochure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver an awe inspiring pitch with this creative cyber security administration in organization contingency plan for cyber threat handling brochure pdf bundle. Topics like contingency, implementation, components, documentation, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Cyber Threat Landscape In Cloud Security Ppt Inspiration Microsoft PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this cybersecurity cyber threat landscape in cloud security ppt inspiration microsoft pdf. Use them to share invaluable insights on business disruption, strategic plans, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Cyber Threat Landscape In Computer Security Ideas PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this desktop security management cyber threat landscape in computer security ideas pdf. Use them to share invaluable insights on business disruption, strategic plans, financial, reputation damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Contingency Plan For Cyber Infographics PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities contingency plan for cyber infographics pdf. Use them to share invaluable insights on contingency solutions, contingency considerations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Statistics Associated To Workplace Threats Elements PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Deliver and pitch your topic in the best possible manner with this cyber safety incident management statistics associated to workplace threats elements pdf. Use them to share invaluable insights on cyber attacks costs, organizations, organizations have, organizations face, data records and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Information And Event Management Real Time Assessment Of Security Threats Template PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event management real time assessment of security threats template pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda Of Handling Cyber Threats In A Digital Era Ppt Infographics Objects PDF
This is a agenda of handling cyber threats in a digital era ppt infographics objects pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of handling cyber threats in a digital era. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
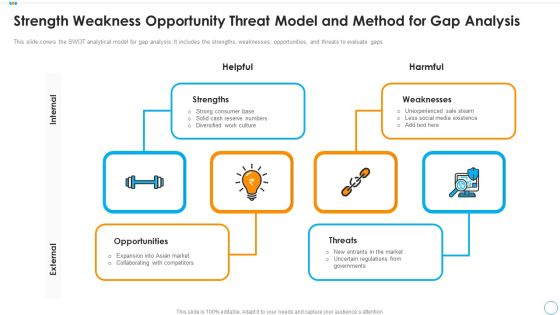
Strength Weakness Opportunity Threat Model And Method For Gap Analysis Designs PDF
This slide covers the SWOT analytical model for gap analysis. It includes the strengths, weaknesses, opportunities, and threats to evaluate gaps. Presenting strength weakness opportunity threat model and method for gap analysis designs pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including strengths, opportunities, weaknesses. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Cyber Threat Landscape In Information Technology Security Download PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this it security cyber threat landscape in information technology security download pdf. Use them to share invaluable insights on business, competitors, reputation damage, organized criminals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
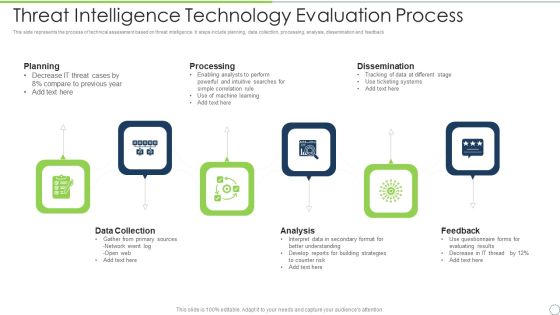
Threat Intelligence Technology Evaluation Process Ppt PowerPoint Presentation File Shapes PDF
This slide represents the process of technical assessment based on threat intelligence. It steps include planning, data collection, processing, analysis, dissemination and feedback. Presenting threat intelligence technology evaluation process ppt powerpoint presentation file shapes pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including planning, processing, dissemination, feedback, analysis, data collection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda Of Data Safety Initiatives For Effective IT Security Threats Administration Professional PDF
This is a agenda of data safety initiatives for effective it security threats administration professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security program keeping, threat drivers, cybersecurity attacks resulting, business agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Cyber Threat Landscape In Information Security Ppt PowerPoint Presentation File Slides PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this info security cyber threat landscape in information security ppt powerpoint presentation file slides pdf. Use them to share invaluable insights on business disruption, financial theft, fraud, reputation damage, tenant damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
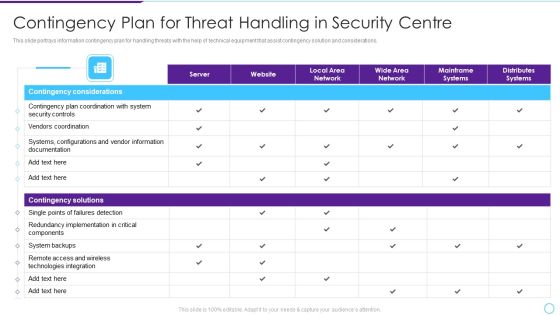
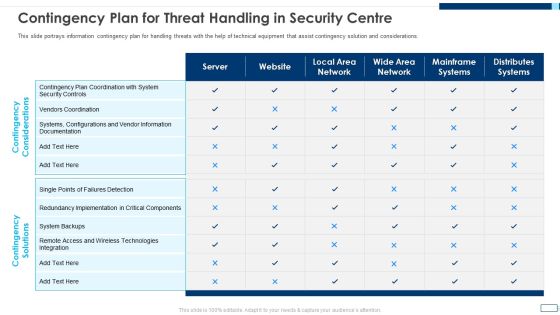
Intelligent Infrastructure Contingency Plan For Threat Handling In Security Centre Mockup PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Contingency Plan For Threat Handling In Security Centre Mockup PDF bundle. Topics like Contingency Considerations, Contingency Solutions, Server, Local Area Network, Local Area Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver and pitch your topic in the best possible manner with this Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF Use them to share invaluable insights on Contingency Solutions, Contingency Considerations, Information Documentation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
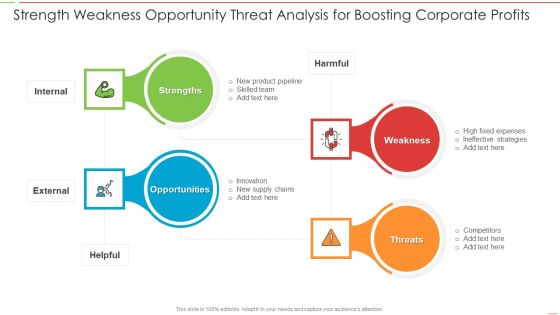
Strength Weakness Opportunity Threat Analysis For Boosting Corporate Profits Download PDF
Persuade your audience using this Strength Weakness Opportunity Threat Analysis For Boosting Corporate Profits Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strength, Weakness, Threats, Opportunity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing Business Analytics Framework Contingency Plan For Threat Handling Mockup PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this Developing Business Analytics Framework Contingency Plan For Threat Handling Mockup PDF Use them to share invaluable insights on Contingency Considerations, Contingency Solutions, Technologies Integration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Insider Threat In Cyber Security Detection And Prevention Framework Information PDF
This slide shows insider threat prevention and detection framework. It contains information user characteristics, attack status, vulnerability, personality, past record, motivation behind attack, etc. Presenting Insider Threat In Cyber Security Detection And Prevention Framework Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Actor Characteristic, Attack Characteristic, Organisation Characteristic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF
This slide shows timeline depicting insider threat user logs. It contains information about archived activities, user event, policy violation trigger, capture continuation, etc. Pitch your topic with ease and precision using this Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF. This layout presents information on User Event, Policy Violation Trigger, Archived Logs. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strength Weakness Opportunity Threat Analysis For Business Competitors Background Inspiration PDF
This Slide illustrates strength weakness opportunity threat SWOT analysis for market competitors which contains distinctions and themes. Showcasing this set of slides titled Strength Weakness Opportunity Threat Analysis For Business Competitors Background Inspiration PDF. The topics addressed in these templates are Customer, Services In Industry, Advertising Approaches. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF
Persuade your audience using this Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Threats Management, Confidential Data Reports, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

OP Risk Management Defining Risk Grades And Score Introduction PDF
Firm can use the slide to provide grades and scores to the risk events. Here the risk scores will be calculated by multiplying consequence rating with likelihood rating. Deliver an awe inspiring pitch with this creative op risk management defining risk grades and score introduction pdf bundle. Topics like defining risk grades and score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

OP Risk Management Operational Risks Mapping Rules PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe inspiring pitch with this creative op risk management operational risks mapping rules pdf bundle. Topics like external fraud, cyber attack, business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
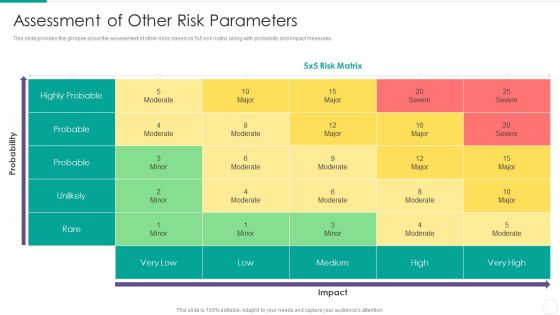
Quantitative Risk Assessment Assessment Of Other Risk Parameters Portrait PDF
This slide provides the glimpse about the assessment of other risks based on 5x5 risk matrix along with probability and impact measures. Deliver and pitch your topic in the best possible manner with this Quantitative Risk Assessment Assessment Of Other Risk Parameters Portrait PDF. Use them to share invaluable insights on Assessment Of Other Risk Parameters and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Risk Reporting And Likelihood Summary PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Risk Reporting And Likelihood Summary PDF bundle. Topics like Unavailability Of Power, Risk Encountered, Attack Scenario can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Defining Risk Level Icons PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Defining Risk Level Icons PDF bundle. Topics like Extremely Critical, Requires Immediate, Operations Of Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Change And Stress Administration Methods Positive Effect From Stress Management Training Information PDF
This slide highlights the positive effect of stress management on organization and employees which includes reduce workplace conflicts, accidents and sexual harassment and improvement in employee productivity etc.Deliver an awe inspiring pitch with this creative Business Change And Stress Administration Methods Positive Effect From Stress Management Training Information PDF bundle. Topics like Workplace Conflicts, Employee Productivity, Reduction Accidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Investor Personality Template 1 Ppt PowerPoint Presentation Infographics Icons
This is a investor personality template 1 ppt powerpoint presentation infographics icons. This is a four stage process. The stages in this process are risk tolerance score, time horizon score.
Return On Investment Icons Ppt Powerpoint Presentation Gallery Brochure
This is a return on investment icons ppt powerpoint presentation gallery brochure. This is a two stage process. The stages in this process are risks, sales, capital, return, finance.

Payroll Challenges Faced By Global Enterprises Summary PDF
This slide shows various payroll challenges which are faced by multinational companies. These challenges includes payroll data handling, data protection, currency challenges, language and cultural challenges. Presenting Payroll Challenges Faced By Global Enterprises Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Handling, Data Protection, Currency Challenges . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Methodology Quality Risk Review Introduction PDF
This slide covers quality risk review from initial risk identification and review assessment along with factors that can impact quality, initial risk ranking, risk mitigation, final risk evaluation etc. Find highly impressive Risk Based Methodology Quality Risk Review Introduction PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Risk Based Methodology Quality Risk Review Introduction PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
Virtual Team Challenges Ppt PowerPoint Presentation Slides Show
This is a virtual team challenges ppt powerpoint presentation slides show. This is a three stage process. The stages in this process are virtual team challenges.
Virtual Teams Challenges Ppt PowerPoint Presentation Icon Graphics Download Cpb
This is a virtual teams challenges ppt powerpoint presentation icon graphics download cpb. This is a seven stage process. The stages in this process are virtual teams challenges.

Challenges Virtual Teams Ppt PowerPoint Presentation Icon Information
This is a challenges virtual teams ppt powerpoint presentation icon information. This is a five stage process. The stages in this process are challenges virtual teams.

Virtual Team Challenge Ppt PowerPoint Presentation Professional Demonstration
This is a Virtual Team Challenge Ppt PowerPoint Presentation Professional Demonstration. This is a four stage process. The stages in this process are Virtual Team Challenge.

Team Challenges Virtual Ppt PowerPoint Presentation File Elements Cpb
This is a team challenges virtual ppt powerpoint presentation file elements cpb. This is a five stage process. The stages in this process are team challenges virtual.

Marketing Challenges Ppt PowerPoint Presentation Slides Inspiration Cpb
This is a marketing challenges ppt powerpoint presentation slides inspiration cpb. This is a three stage process. The stages in this process are marketing challenges.

Challenges Product Development Ppt PowerPoint Presentation Summary Format Ideas Cpb
This is a challenges product development ppt powerpoint presentation summary format ideas cpb. This is a three stage process. The stages in this process are challenges product development.

Product Development Challenges Ppt PowerPoint Presentation Show Display Cpb
This is a product development challenges ppt powerpoint presentation show display cpb. This is a six stage process. The stages in this process are product development challenges.
Process Management Challenges Ppt PowerPoint Presentation Slides Visuals Cpb
This is a process management challenges ppt powerpoint presentation slides visuals cpb. This is a five stage process. The stages in this process are process management challenges.

Communication Challenges Ppt PowerPoint Presentation Summary Examples Cpb
This is a communication challenges ppt powerpoint presentation summary examples cpb. This is a four stage process. The stages in this process are communication challenges.

Project Scope Challenges Ppt PowerPoint Presentation Professional Visual Aids Cpb
This is a project scope challenges ppt powerpoint presentation professional visual aids cpb. This is a four stage process. The stages in this process are project scope challenges.

Data Challenges Ppt PowerPoint Presentation Show Graphic Tips Cpb
This is a data challenges ppt powerpoint presentation show graphic tips cpb. This is a four stage process. The stages in this process are data challenges.

Lead Scoring Challenges Ppt PowerPoint Presentation Infographic Template Samples Cpb
This is a lead scoring challenges ppt powerpoint presentation infographic template samples cpb. This is a four stage process. The stages in this process are lead scoring challenges.

Engaging Icebreaker Activities Challenges For Virtual Employees Summary PDF
This slide illustrates Engaging ice breaking challenges that can be conducted for employees working in a virtual setting. The challenges for virtual employees are GIF off, daily step challenge, healthy eating challenge and recreate photo challenge. Persuade your audience using this Engaging Icebreaker Activities Challenges For Virtual Employees Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Animated Graphics, Daily Step Challenge, Healthy Eating Challenge. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Channel Sales Taking Your Product To Market Challenges Related To Channel Sales Pictures PDF
Presenting this set of slides with name channel sales taking your product to market challenges related to channel sales pictures pdf. This is a seven stage process. The stages in this process are revenue, access, brand risk, profitable, predictable. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Law And Governance Icons Set Ppt PowerPoint Presentation Inspiration Design Templates
This is a law and governance icons set ppt powerpoint presentation inspiration design templates. This is a two stage process. The stages in this process are risk management icon, governance icon, compliance icon.
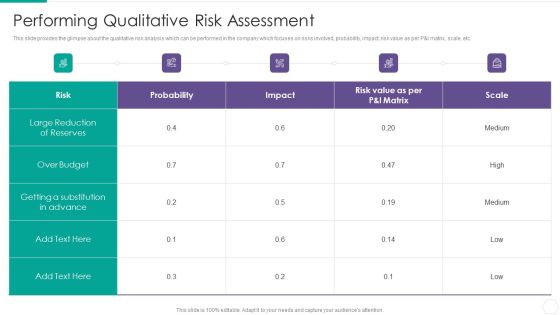
Quantitative Risk Assessment Performing Qualitative Risk Assessment Template PDF
This slide provides the glimpse about the qualitative risk analysis which can be performed in the company which focuses on risks involved, probability, impact, risk value as per P and I matrix, scale, etc. Deliver and pitch your topic in the best possible manner with this Quantitative Risk Assessment Performing Qualitative Risk Assessment Template PDF. Use them to share invaluable insights on Over Budget, Matrix, Value, Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
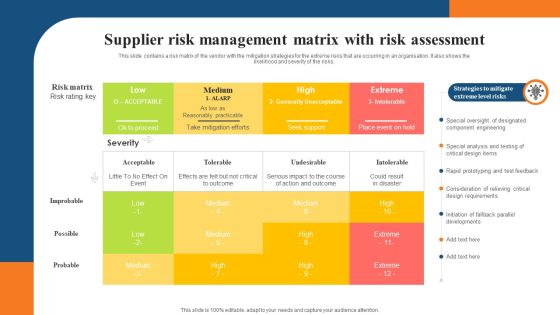
Supplier Risk Management Matrix With Risk Assessment Clipart PDF
This slide contains a risk matrix of the vendor with the mitigation strategies for the extreme risks that are occurring in an organisation. It also shows the likelihood and severity of the risks. Showcasing this set of slides titled Supplier Risk Management Matrix With Risk Assessment Clipart PDF. The topics addressed in these templates are Risk Matrix, Strategies To Mitigate, Special Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Post Merger Integration Process Presentation Images
This is a post merger integration process presentation images. This is a two stage process. The stages in this process are org m and a business objectives, time constraints, cost constraints, integration end state, data, applications, systems and architecture, architecture, it organization, integration program management, change management.

Post Merger Integration Process Powerpoint Ideas
This is a post merger integration process powerpoint ideas. This is a two stage process. The stages in this process are systems and architecture, applications, constraints, integration end statedata, it organization, integration program management, change management, integration end statedata, m and a business objectives, time constraints, cost.
Risk Assessment For Legal Regulations Ppt Risk Powerpoint Guide
This is a risk assessment for legal regulations ppt risk powerpoint guide. This is a five stage process. The stages in this process are compliance, rules, guidelines, regulations, laws.

Qualitative Risk Analysis Risk Estimator Ppt PowerPoint Presentation Infographics Gallery
This is a qualitative risk analysis risk estimator ppt powerpoint presentation infographics gallery. This is a five stage process. The stages in this process are business, management, strategy, analysis, marketing.

Risk Management Plan Risk Estimator Ppt PowerPoint Presentation Ideas Examples
This is a risk management plan risk estimator ppt powerpoint presentation ideas examples. This is a four stage process. The stages in this process are business, management, strategy, analysis, marketing.
Risk Tracker Risk Estimator Ppt PowerPoint Presentation Styles Files
This is a risk tracker risk estimator ppt powerpoint presentation styles files. This is a three stage process. The stages in this process are business, management, strategy, analysis, marketing.

OP Risk Management Operational Risk Assessment Worksheet Microsoft PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative op risk management operational risk assessment worksheet microsoft pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

OP Risk Management Risk Events Types And Frequency Template PDF
Mentioned slide shows information about risk event types ant its occurring frequency. It includes information of risk event, its overview, impact and frequency. Deliver an awe inspiring pitch with this creative op risk management risk events types and frequency template pdf bundle. Topics like overview, impact, frequency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risks Involved And Mitigation Strategies To Eliminate Risks Background PDF
This is a risks involved and mitigation strategies to eliminate risks background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like skilled labor shortage, technology failure risk, high competition risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Risk Control Strategies Operational Risk Management Brochure PDF
Persuade your audience using this IT Risk Control Strategies Operational Risk Management Brochure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including IT Risk Control, Strategies Operational, Risk Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Company Project Planning Risk Identification Risk Ppt Styles Elements PDF
Presenting company project planning risk identification risk ppt styles elements pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like risk, severity, plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF.

Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. This Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.
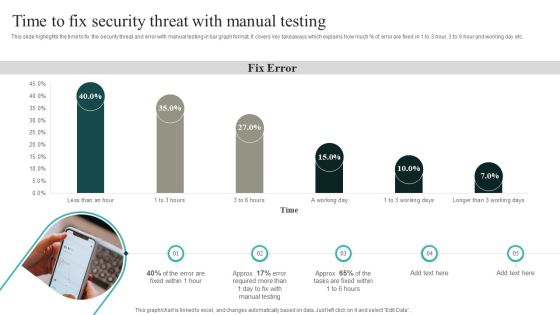
IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF

Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF.

Impact Analysis For Effective Threat Management In Securing Workplace Professional PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Impact Analysis For Effective Threat Management In Securing Workplace Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF
The following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Are you searching for a Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF from Slidegeeks today.

Challenge Game PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with challenge concept with two different colored chess piece sides

Challenge And Success Leadership PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with abstract illustration showing the challenge and success

Challenge And Success Leadership PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with abstract illustration showing the challenge and success

Current Challenges Faced By B2B Marketers Ppt Summary Icon PDF
This slide covers the challenges faced by the B2B marketers along with the solutions to overcome such challenges.Deliver an awe-inspiring pitch with this creative current challenges faced by B2B marketers ppt summary icon pdf. bundle. Topics like challenges, solution, technology integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
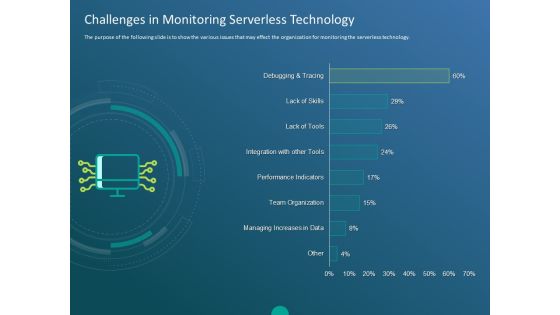
Functioning Of Serverless Computing Challenges In Monitoring Serverless Technology Ppt Design Ideas PDF
The purpose of the following slide is to show the various issues that may effect the organization for monitoring the serverless technology. Deliver an awe-inspiring pitch with this creative functioning of serverless computing challenges in monitoring serverless technology ppt design ideas pdf bundle. Topics like managing increases data, team organization, performance indicators, integration tools, lack tools, lack skills, debugging and tracing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Database Expansion And Optimization Key Challenges Of Current Data Management System Ppt Model Display
This slide provides information regarding major issues faced by the organization with the existing data repository system covering details regarding low database throughput, nonavailability of active connections, high latency, etc. during peak hours. This is a database expansion and optimization key challenges of current data management system ppt model display template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like non availability of active connections, low throughput, high latency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Scale Up Plan For Data Inventory Model Key Challenges Of Current Data Management System Themes PDF
This slide provides information regarding major issues faced by the organization with the existing data repository system covering details regarding low database throughput, nonavailability of active connections, high latency, etc. during peak hours. This is a scale up plan for data inventory model key challenges of current data management system themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like non availability of active connections, low throughput, high latency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Tactical Plan For Upgrading DBMS Key Challenges Of Current Data Management System Microsoft PDF
This slide provides information regarding major issues faced by the organization with the existing data repository system covering details regarding low database throughput, nonavailability of active connections, high latency, etc. during peak hours. This is a tactical plan for upgrading dbms key challenges of current data management system microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like non availability of active connections, low throughput, high latency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cognitive Computing Action Plan Addressing Current Challenges Faced By Firm Ppt Outline Infographic Template PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in IT infrastructure cost, delay in service as result in digital advancement lag. Deliver an awe inspiring pitch with this creative cognitive computing action plan addressing current challenges faced by firm ppt outline infographic template pdf bundle. Topics like it infrastructure cost, customer attrition, issues related to employees can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Major Advantages Of Banking Industry Revolution Challenges And Solutions Regarding Diagrams PDF
This slide shows the benefits of mobile banking that improves and enhances the banking services and leads to a positive digital banking transformation such as 24 7 service availability, paperless transactions, facilitation of location-based services, increased efficiency and compliance etc. Presenting major advantages of banking industry revolution challenges and solutions regarding diagrams pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like securing media communications, drifting away from legacy applications, security issues In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Horizontal Scaling Technique For Information Key Challenges Of Current Data Management Rules PDF
This slide provides information regarding major issues faced by the organization with the existing data repository system covering details regarding low database throughput, nonavailability of active connections, high latency, etc. during peak hours.This is a Horizontal Scaling Technique For Information Key Challenges Of Current Data Management Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Active Connections, Low Throughput, High Latency You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Automating Supply Chain Cost And Time Management Challenges Faced By Company In Warehouse Template PDF
This slide covers the statistical representation of warehouse cost and time distribution issues in an organization. It includes time spent on activities such as search, travel, order set up, pick and put, etc. it also includes operating cost distribution such as order picking, storage, shipping, receiving, etc. Deliver an awe inspiring pitch with this creative Automating Supply Chain Cost And Time Management Challenges Faced By Company In Warehouse Template PDF bundle. Topics like Warehouse Operating, Cost Distribution, Poor Purchase can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Company Event Communication Plan Event Communication Challenges Faced By Company Mockup PDF
This slide covers various issues faced while communicating about the event. It includes steps such as encouraging participation, promoting the event, managing registration and attendance, building an online community, etc. This is a Effective Company Event Communication Plan Event Communication Challenges Faced By Company Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encouraging Participation, Managing Registration, Promoting Event You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Simulation Human Thinking Addressing Current Challenges Faced By Firm Portrait PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in IT infrastructure cost, delay in service as result in digital advancement lag. Deliver an awe inspiring pitch with this creative Computer Simulation Human Thinking Addressing Current Challenges Faced By Firm Portrait PDF bundle. Topics like IT Infrastructure Cost, Issues Related, Employees, Customer Attrition can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Company Event Communication Tactics Event Communication Challenges Faced By Company Download PDF
This slide covers various issues faced while communicating about the event. It includes steps such as encouraging participation, promoting the event, managing registration and attendance, building an online community, etc. This is a Effective Company Event Communication Tactics Event Communication Challenges Faced By Company Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encouraging Participation, Promoting Event, Registration Attendance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
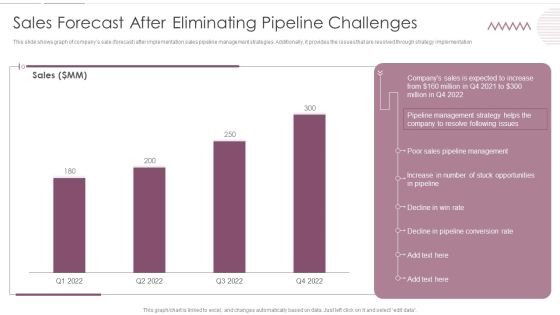
Sales Management Pipeline For Effective Lead Generation Sales Forecast After Eliminating Pipeline Challenges Inspiration PDF
This slide shows graph of companys sale forecast after implementation sales pipeline management strategies. Additionally, it provides the issues that are resolved through strategy implementation. Deliver and pitch your topic in the best possible manner with this Sales Management Pipeline For Effective Lead Generation Sales Forecast After Eliminating Pipeline Challenges Inspiration PDF. Use them to share invaluable insights on Sales Pipeline Management, Opportunities, Pipeline Conversion Rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Major Challenges In Release Management Process Plan Ppt Inspiration Ideas PDF
The following slide showcases some significant issues in release management to analyze and formulate plan to minimize its affect. It includes elements such as bad quality, security, slow builds etc. Persuade your audience using this Major Challenges In Release Management Process Plan Ppt Inspiration Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Build Quality, Security, Slow Builds. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Challenges In Green Supply Chain Management Ppt PowerPoint Presentation Inspiration Smartart PDF
The following slide highlights some major issues in green supply chain management GSCM to formulate strategies to resolve them. It includes elements such as mismanaged implementation, complicated process, lack of reliability, poor alignment of responsibilities, increased cost etc.Persuade your audience using this Challenges In Green Supply Chain Management Ppt PowerPoint Presentation Inspiration Smartart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Mismanaged Implementation, Complicated Process, Increased Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Pharmaceutical Brand Strategic Plan Set Up Challenges And Improvements Ppt PowerPoint Presentation File Gallery PDF
This slide covers pharmaceutical brand plan with objectives. The purpose of this plan is to improve production efficiency and public protection. It includes element such as P and L forecast, drivers, key issues , strategies and goals.Pitch your topic with ease and precision using this Pharmaceutical Brand Strategic Plan Set Up Challenges And Improvements Ppt PowerPoint Presentation File Gallery PDF. This layout presents information on Dynamic Environment, Key Improvement, Brand Alignment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Client Retargeting Strategy Retargeting Solutions For Major Marketing Challenges Pictures PDF
This slide covers remarketing remedies for issues faced by the healthcare organization. It also includes the critical results of the retargeting campaign, such as increased conversions, decreased cost per lead, increased opportunity to customer rate, etc. Want to ace your presentation in front of a live audience Our Client Retargeting Strategy Retargeting Solutions For Major Marketing Challenges Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Robotics Process Automation In Supply Chain Implementation For Services Challenges Inspiration PDF
Following slide covers use of robotic automation to solve logistic service issues. Purpose of this slide is to assure accurate and cost effective logistics services. It include pointers such as resource planning, client services and invoicing. Persuade your audience using this Robotics Process Automation In Supply Chain Implementation For Services Challenges Inspiration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Resource Planning, Client Service, Invoicing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Charity Fundraising Marketing Plan Website Challenges Faced In Nonprofit Marketing Guidelines PDF
This slide provides an overview of the issues faced by marketers on nonprofit websites. The slide depicts decrease in traffic and increase in bounce rate. Present like a pro with Charity Fundraising Marketing Plan Website Challenges Faced In Nonprofit Marketing Guidelines PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Guide For Marketing Analytics To Improve Decisions Major Challenges And Solutions Of Data Analytics Formats PDF
The following slide illustrates multiple issues in marketing data management along with their solutions to achieve desired goals and results. It includes elements such as real time data collection, visual presentation, data inaccessibility, lack of expertise, automation etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Guide For Marketing Analytics To Improve Decisions Major Challenges And Solutions Of Data Analytics Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Solutions To Tackle Inventory Management Challenges Faced By Organization Professional PDF
This slide showcases solutions that can be implemented by organization to tackle inventory management issues. Key solutions include warehouse automation, inventory forecasting and inventory control. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Solutions To Tackle Inventory Management Challenges Faced By Organization Professional PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
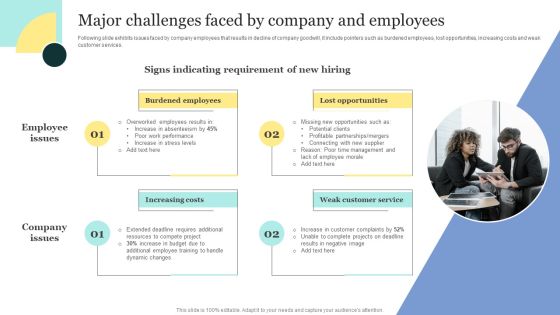
Strategic Approaches To Efficient Candidate Selection Major Challenges Faced By Company And Employees Guidelines PDF
Following slide exhibits issues faced by company employees that results in decline of company goodwill, it include pointers such as burdened employees, lost opportunities, increasing costs and weak customer services. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Strategic Approaches To Efficient Candidate Selection Major Challenges Faced By Company And Employees Guidelines PDF from Slidegeeks and deliver a wonderful presentation.

Strategic Marketing For Hair And Beauty Salon To Increase Major Challenges Encountered Pictures PDF
This slide presents the key issues faced by a salon business. It includes information about fewer leads, ineffective bookings, low retention, limited service line and infrequent client visits. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Strategic Marketing For Hair And Beauty Salon To Increase Major Challenges Encountered Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Risk Management Powerpoint Presentation Examples
This is a risk management powerpoint presentation examples. This is a four stage process. The stages in this process are identify, assess, risk management, control monitor, evaluate.

Risk Mitigation Planning Ppt Examples
This is a risk mitigation planning ppt examples. This is a two stage process. The stages in this process are risk, strategies.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
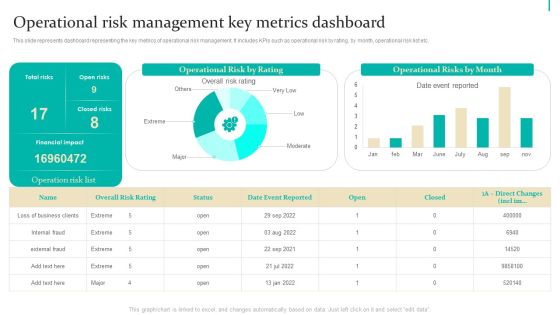
Enterprise Risk Management Operational Risk Management Key Metrics Inspiration PDF
This slide represents dashboard representing the key metrics of operational risk management. It includes KPIs such as operational risk by rating, by month, operational risk list etc. Boost your pitch with our creative Enterprise Risk Management Operational Risk Management Key Metrics Inspiration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Enterprise Risk Management Strategic Risk Assessment And Management Demonstration PDF
This slide represents the matrix which enables enterprise to identify specific risk types, their probability and severity and maintain real-time view of evolving risk environment. It includes details related to risk category, description, probability etc. There are so many reasons you need a Enterprise Risk Management Strategic Risk Assessment And Management Demonstration PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Risk Based Methodology Quality Risk Acceptance Criteria Guidelines PDF
This slide covers risk quantifies from the aspects of individuals, environment, and economy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Risk Based Methodology Quality Risk Acceptance Criteria Guidelines PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Risk Based Methodology Quality Risk Acceptance Criteria Guidelines PDF today and make your presentation stand out from the rest

Risk Based Methodology Risk Control Policy Template PDF
This slide covers Risk control policy including level of risk, risk colour, control policy and control schemes. This Risk Based Methodology Risk Control Policy Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Various Ways To Manage Project Safety By Managing Threats Contd Ppt Styles Diagrams PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting various ways to manage project safety by managing threats contd ppt styles diagrams pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, systems, service, resources, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
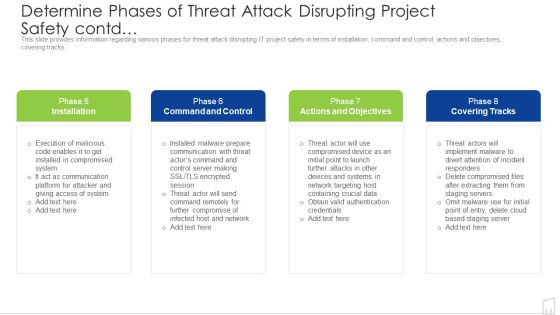
Determine Phases Of Threat Attack Disrupting Project Safety Contd Ppt Inspiration Summary PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. This is a determine phases of threat attack disrupting project safety contd ppt inspiration summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, network, data, server. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Compliance Violations Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a cloud security threats compliance violations cloud computing security it ppt layouts slide portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like businesses, organizations, serious repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Contract Breaches With Clients Cloud Computing Security IT Ppt Ideas Introduction PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting cloud security threats contract breaches with clients cloud computing security it ppt ideas introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, organization, sensitive data stored. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Loss Of Data Cloud Computing Security IT Ppt Infographics Graphic Tips PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a cloud security threats loss of data cloud computing security it ppt infographics graphic tips pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like locations, cloud service, strategies, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Evolving BI Infrastructure Contingency Plan For Threat Handling In Security Centre Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this evolving bi infrastructure contingency plan for threat handling in security centre pictures pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Project Security Administration IT Contingency Plan For Managing Threats To Ensure It Project Safety Mockup PDF
This slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver an awe inspiring pitch with this creative project security administration it contingency plan for managing threats to ensure it project safety mockup pdf bundle. Topics like distributes systems, mainframe systems, wide area network, local area network, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Contd Sample PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a project security administration it various ways to manage project safety by managing threats contd sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deactivate orphaned user accounts, develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
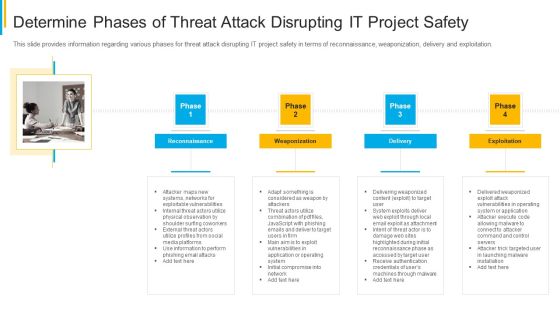
Project Security Administration IT Determine Phases Of Threat Attack Disrupting IT Project Safety Brochure PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a project security administration it determine phases of threat attack disrupting it project safety brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Phases Of Threat Attack Disrupting It Project Safety Elements PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Presenting upgrading total project safety it determine phases of threat attack disrupting it project safety elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Elements PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. This is a upgrading total project safety it determine phases of threat attack disrupting project safety contd elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Latest Threats In Data Security Ppt Summary Slides PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a information security latest threats in data security ppt summary slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Types Of Latest Threats In Electronic Information Security Ppt Portfolio Icon PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a cybersecurity types of latest threats in electronic information security ppt portfolio icon pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Various Ways To Handle Mitigating Cybersecurity Threats And Vulnerabilities Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a addressing various ways to handle mitigating cybersecurity threats and vulnerabilities template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like user accounts, implement active remediation, management policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Various Types Of Workplace Download PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a mitigating cybersecurity threats and vulnerabilities various types of workplace download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threatening behavior, stalking, assault harassment, property damage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Internal And External Business Environment Analysis STEP Analysis For Opportunity And Threat Evaluation Introduction PDF
This slide shows STEP analysis to analyze likelihood, importance and influence of political, economic, social and technological factors on organizational activities This is a internal and external business environment analysis step analysis for opportunity and threat evaluation introduction pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technological, threats or opportunity, influence on the organization You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Different Kinds Of Insider Digital Threats Download PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber safety incident management different kinds of insider digital threats download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malicious insider, negligent or careless insider, third party insider. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Impact Analysis Of Successful Threat Management Implementation Summary PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. This is a cyber safety incident management impact analysis of successful threat management implementation summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like focus area, past state, present state, benefit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Key Activities Checklist Associated To Insider Threat Program Download PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver and pitch your topic in the best possible manner with this cyber safety incident management key activities checklist associated to insider threat program download pdf. Use them to share invaluable insights on plan and collet, review and analyze, develop strategic framework, key activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
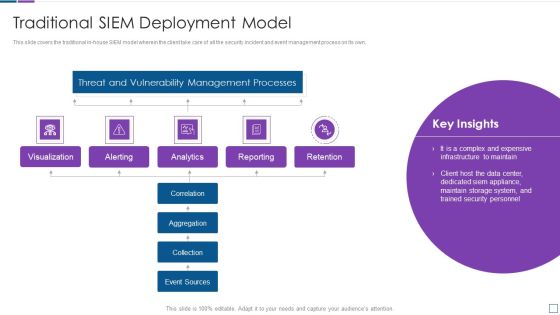
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Companys Enhanced Features And Capabilities Introduction PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting real time assessment of security threats companys enhanced features and capabilities introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Information And Event Management Services Information PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting real time assessment of security threats security information and event management services information pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Benchmarking With Security Operations Maturity Model Infographics PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting real time assessment of security threats benchmarking with security operations maturity model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like centralized forensic visibility, mean time to detect, mean time to respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
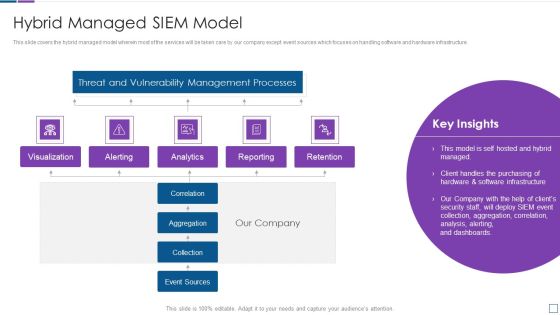
Real Time Assessment Of Security Threats Hybrid Managed SIEM Model Brochure PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative real time assessment of security threats hybrid managed siem model brochure pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
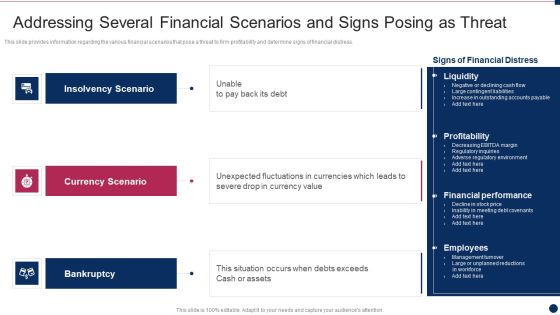
Threat Management At Workplace Addressing Several Financial Scenarios And Signs Portrait Pdf
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting threat management at workplace addressing several financial scenarios and signs portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like currency scenario, insolvency scenario, bankruptcy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
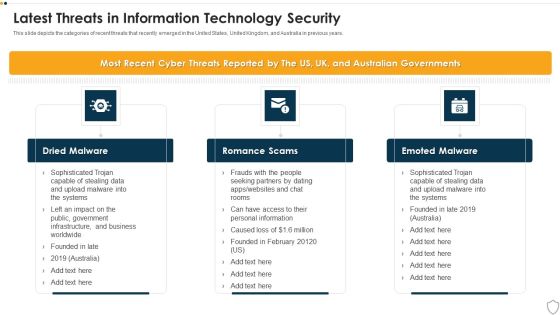
IT Security Latest Threats In Information Technology Security Ppt Slides Visuals PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting it security latest threats in information technology security ppt slides visuals pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dried malware, romance scams, emoted malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

E Commerce Strengths Weaknesses Opportunities And Threats Analysis For Business Growth Background PDF
This slide elaborates about the strengths, weakness, opportunity and threat of the e-commerce business that will help for knowing what is needed and what areas need improvements for the company growth.Presenting E Commerce Strengths Weaknesses Opportunities And Threats Analysis For Business Growth Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mismanagement, Opportunities, Considerable This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF
This slide covers the strategies that are been developed by doing the SWOT strengths, weakness, opportunities and threats analysis of an organization to help the managers or owners to make decisions accordingly.Persuade your audience using this Strengths Weaknesses Opportunities And Threats Analysis Of Automotive Industry Elements PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Ineffective Marketing, Unable To Establish, Large Diversified Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strengths Weaknesses Opportunities And Threats Analysis Matrix For Effective Marketing Growth Sample PDF
This slide covers the strengths , weaknesses , opportunities and threats analysis of the business for the effective marketing growth. This will help the business to expand in may areas by working on its weakness and knowing their opportunities.Presenting Strengths Weaknesses Opportunities And Threats Analysis Matrix For Effective Marketing Growth Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Communication Among, Implementation, Increase Prices This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. This is a Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Could, Business Partners, Data Stored. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
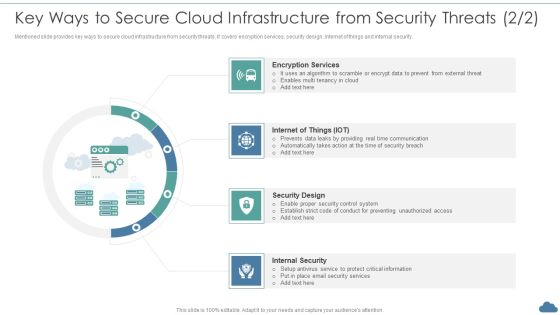
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Presenting Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Partners, Contract Breaches, Against The Organization In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Presenting Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Storage Locations, Natural Disasters, Massive Impact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF
This slide shows comparison of software available for detecting insider threat. It provides information about tools, features, user reviews, detection rate, free trial and pricing. Pitch your topic with ease and precision using this Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF. This layout presents information on User Reviews, Detection Rate, Free Trial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
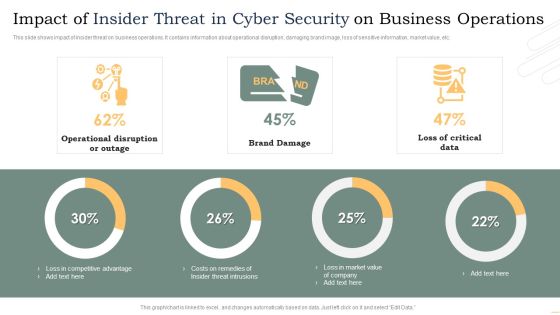
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF. Use them to share invaluable insights on Manual Testing, Fix Error, 3 Working Days and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
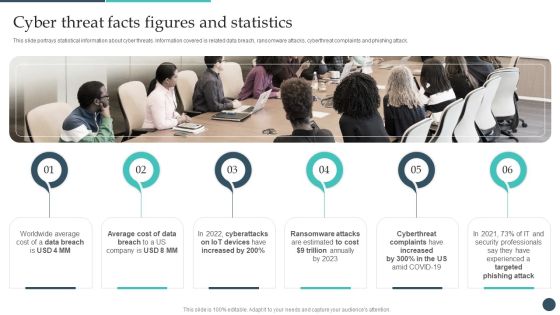
Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Boost your pitch with our creative Safety Breach Response Playbook Cyber Threat Facts Figures And Statistics Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Security Automation To Analyze And Mitigate Cyberthreats Time To Fix Security Threat Ideas PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Security Automation To Analyze And Mitigate Cyberthreats Time To Fix Security Threat Ideas PDF from Slidegeeks and deliver a wonderful presentation.

Confidential Data Theft Threats Mitigation Heat Map Ppt Portfolio Microsoft PDF
This slide covers heat map depicting data theft mitigation strategies and task prioritization. It includes process such as to discover employees roles and access levels, analyse threats and execute plan to reduce or eliminate data theft. Presenting Confidential Data Theft Threats Mitigation Heat Map Ppt Portfolio Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Discover, Analyze, Execute And Educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
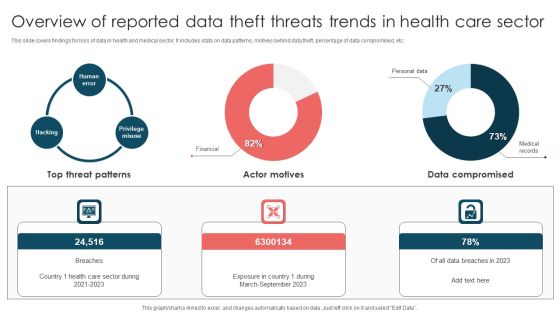
Overview Of Reported Data Theft Threats Trends In Health Care Sector Introduction PDF
This slide covers findings for loss of data in health and medical sector. It includes stats on data patterns, motives behind data theft, percentage of data compromised, etc. Pitch your topic with ease and precision using this Overview Of Reported Data Theft Threats Trends In Health Care Sector Introduction PDF. This layout presents information on Top Threat Patterns, Exposure Country, March To September 2023. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Demonstration PDF
Create an editable Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.


 Continue
with Email
Continue
with Email
 Sign
up for an account
Sign
up for an account

 Home
Home


































