Problem List/icons/appstore.png
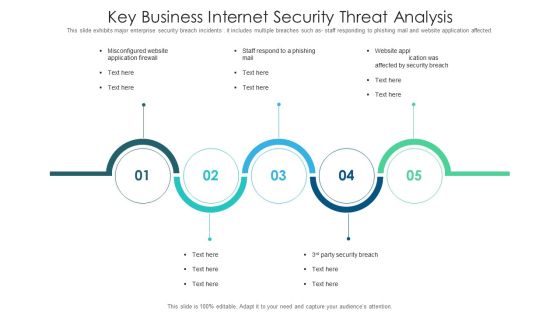
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

SWOT Analysis Of ABC Software Company Threats Structure PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like revenues, profitability, quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of How To Intensify Project Threats Portrait PDF
This is a agenda of how to intensify project threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of how to intensify project threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda Of Mitigating Cybersecurity Threats And Vulnerabilities Guidelines PDF
Presenting agenda of mitigating cybersecurity threats and vulnerabilities guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like agenda of mitigating cybersecurity threats and vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
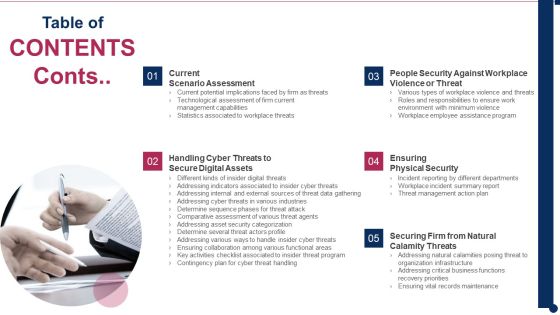
Threat Management At Workplace Contents Conts Diagrams Pdf
This is a threat management at workplace contents conts diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, current scenario assessment, people security against workplace violence or threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
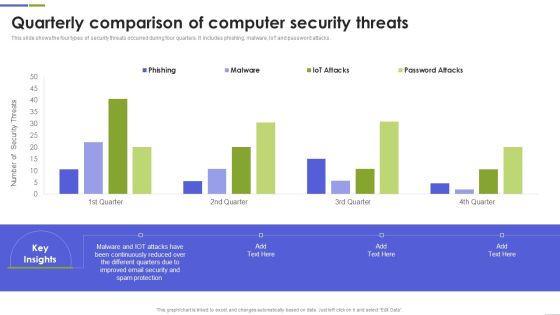
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Threats Contract Breaches With Clients Download PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting Cloud Security Threats Contract Breaches With Clients Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Organization, Business Partners, Information Could. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Insider Threat Detection In Computer System Icon Sample PDF
Persuade your audience using this Insider Threat Detection In Computer System Icon Sample PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Insider Threat Detection, Computer System, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Threat Assessment Process Icon With Statistics Ppt Slides Styles PDF
Persuade your audience using this Threat Assessment Process Icon With Statistics Ppt Slides Styles PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Assessment Process, Icon With Statistics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Threats And Vulnerability Administration Plan Process Guidelines PDF
This slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting Threats And Vulnerability Administration Plan Process Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Evaluating Vulnerabilities, Reporting Vulnerabilities, Treating Vulnerabilities, Identifying Vulnerabilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF
Persuade your audience using this Threats And Vulnerability Administration Plan Requirement Icon Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Threats And Vulnerability, Administration Plan, Requirement Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF
This slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Showcasing this set of slides titled Threat And Vulnerability Administration Plan Analysis Dashboard Slides PDF. The topics addressed in these templates are Exposure Score, Configuration Score, Severity Distribution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
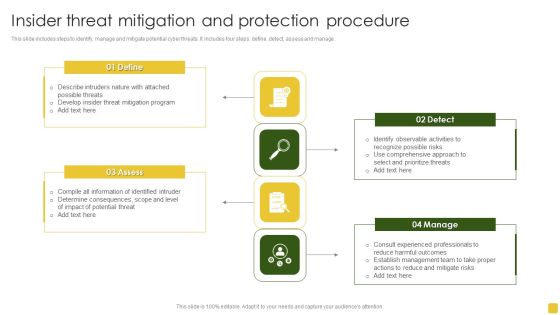
Insider Threat Mitigation And Protection Procedure Professional PDF
This slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage.Presenting Insider Threat Mitigation And Protection Procedure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mitigation Program, Compile Information, Determine Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Authentication Based Cyber Threat Prevention Techniques Download PDF
The below slide provides benefits of using various authentication technology for user identification which helps business and organizations to enhance customer experience. Major categories are multi factor authentication, password based, bio-metrics, etc. Showcasing this set of slides titled Authentication Based Cyber Threat Prevention Techniques Download PDF. The topics addressed in these templates are Techniques, Authentication, Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
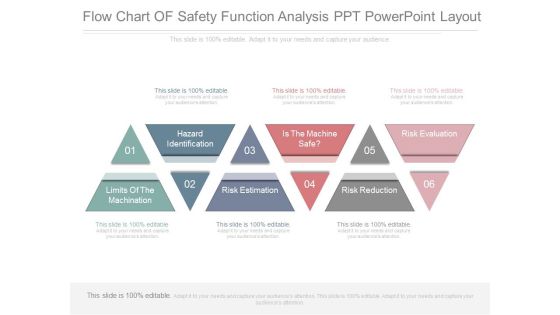
Flow Chart Of Safety Function Analysis Ppt Powerpoint Layout
This is a flow chart of safety function analysis ppt powerpoint layout. This is a six stage process. The stages in this process are hazard identification, limits of the machination, risk estimation, is the machine safe, risk reduction, risk evaluation.

Current Operational Process Improvement Challenges The Company Is Facing Ideas PDF
This slide shows some of the current Operational Process Improvement challenges and issues that are faced by the company. Deliver an awe inspiring pitch with this creative current operational process improvement challenges the company is facing ideas pdf bundle. Topics like business, management, process development, improvement plan, security risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
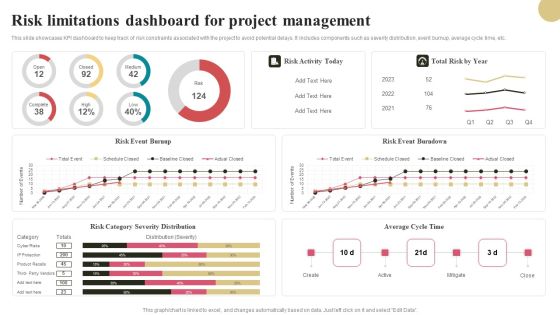
Risk Limitations Dashboard For Project Management Elements PDF
This slide showcases KPI dashboard to keep track of risk constraints associated with the project to avoid potential delays. It includes components such as severity distribution, event burnup, average cycle time, etc. Showcasing this set of slides titled Risk Limitations Dashboard For Project Management Elements PDF. The topics addressed in these templates are Risk Activity Today, Risk Event Burndown, Average Cycle Time. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
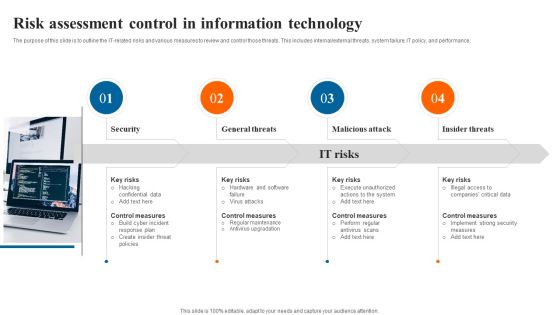
Risk Assessment Control In Information Technology Download PDF
The purpose of this slide is to outline the IT related risks and various measures to review and control those threats. This includes internal or external threats, system failure, IT policy, and performance. Presenting Risk Assessment Control In Information Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including General Threats, Malicious Attack, Insider Threats, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Identification And Remediation In Information Technology Template PDF
The purpose of this slide is to outline the IT related risks and various measures to review and control those threats. This includes internal or external threats, system failure, IT policy, and performance. Persuade your audience using this Risk Identification And Remediation In Information Technology Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Insider Threats, General Threats, Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Issue Log In Project Management For Multiple Projects Ppt PowerPoint Presentation File Designs Download PDF
This slide showcases log table that can help organization to manage plus track risk and issues of multiple projects and resolve them within stipulated time. Its key components are projects, risk title, description, identification date and chances of conversion into issue. Showcasing this set of slides titled issue log in project management for multiple projects ppt powerpoint presentation file designs download pdf. The topics addressed in these templates are projects, risk title, risk description, identification date, chances of conversion into issue. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Challenges Associated With Mobile Banking Ppt Show Maker PDF
This slide shows main challenges faced by banks as well as customers after adopting mobile banking. These major challenges includes online hackers, privacy issues and technical issues. Find highly impressive Major Challenges Associated With Mobile Banking Ppt Show Maker PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Major Challenges Associated With Mobile Banking Ppt Show Maker PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Addressing Present Challenges Faced By IT Department Download PDF
This slide provides information regarding various challenges faced by IT department in terms of rise in IT infrastructure cost, reasons for rise in IT spending and reported financial losses due to increase in security threats. Deliver and pitch your topic in the best possible manner with this Addressing Present Challenges Faced By IT Department Download PDF. Use them to share invaluable insights on Management Tools, Financial, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
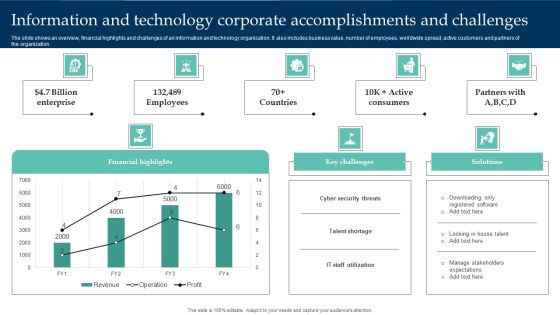
Information And Technology Corporate Accomplishments And Challenges Structure PDF
The slide shows an overview, financial highlights and challenges of an information and technology organization. It also includes business value, number of employees, worldwide spread, active customers and partners of the organization. Pitch your topic with ease and precision using this Information And Technology Corporate Accomplishments And Challenges Structure PDF. This layout presents information on Financial Highlights, Cyber Security Threats, Enterprise. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Store Launch Event Solutions To Overcome Challenges Information PDF
This slide signifies the retail store opening key threats and strategies implemented to overcome them. It covers information about challenges like hiring efficient employee, huge number of competitors and engaging customer with solutions to overcome them. Showcasing this set of slides titled Store Launch Event Solutions To Overcome Challenges Information PDF. The topics addressed in these templates are Efficient Employees And Staff, Engaging Customers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Current Potential Challenges Faced By Firm Topics PDF
This slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Want to ace your presentation in front of a live audience Our Current Potential Challenges Faced By Firm Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Brand Element Challenges And Solutions To Overcome Designs PDF
This slide signifies the challenges and solutions for effective brand assets. It includes threats like poor consumer awareness, limited expansion and minimal brand equity along with strategies implemented to overcome. Presenting Brand Element Challenges And Solutions To Overcome Designs PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Limited Expansion, Poor Consumer Awareness, Existing Brand Elements. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Integrated Team Management Solutions To Overcome Challenges Mockup PDF
This slide highlights the cross functional management challenges and solutions to overcome. It covers information about threats like lack of trust, poor communication and misaligned goals along with strategies implement to overcome. Presenting Integrated Team Management Solutions To Overcome Challenges Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Lack Trust, Poor Communication, Misaligned Goals Priorities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Website Management Key Challenges And Solutions To Overcome Structure PDF
This slide depicts the website maintenance key threats and strategies to overcome them. It covers information about challenges like broken external links, crashed servers and technologies shifts with solutions to overcome them. Presenting Website Management Key Challenges And Solutions To Overcome Structure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Broken External Links, Crashed Servers, Increase Return Investment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
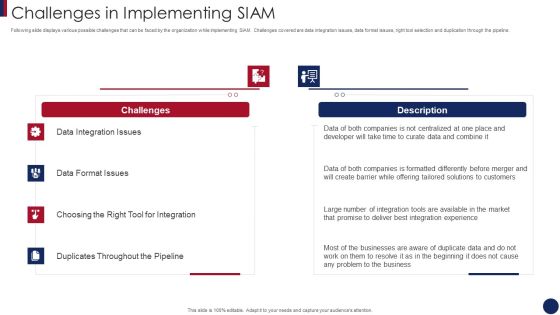
Post Merger Information Technology Service Delivery Amalgamation Challenges In Implementing SIAM Template PDF
Following slide displays various possible challenges that can be faced by the organization while implementing SIAM. Challenges covered are data integration issues, data format issues, right tool selection and duplication through the pipeline. Deliver an awe inspiring pitch with this creative post merger information technology service delivery amalgamation challenges in implementing siam template pdf bundle. Topics like integration issues, format issues, experience, customers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Consolidation Post Mergers And Acquisition Solutions To Counter Possible Challenges Professional PDF
Mentioned slide portrays right measures that can be used by by the organization to overcome possible challenges such as data integration issues, data format issues, right tool selection and duplication through the pipeline while implementing SIAM. This is a IT Consolidation Post Mergers And Acquisition Solutions To Counter Possible Challenges Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Format Issues, Data Integration Issues, Solutions, Challenges, Data Transformation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
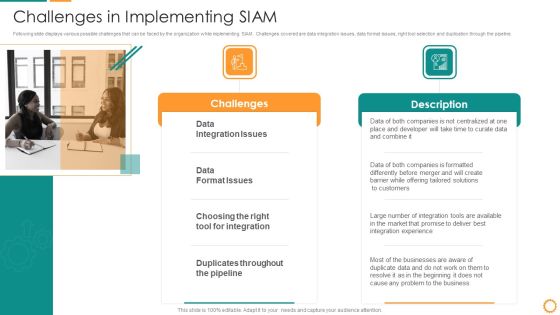
IT Consolidation Post Mergers And Acquisition Challenges In Implementing SIAM Slides PDF
Following slide displays various possible challenges that can be faced by the organization while implementing SIAM. Challenges covered are data integration issues, data format issues, right tool selection and duplication through the pipeline. Presenting IT Consolidation Post Mergers And Acquisition Challenges In Implementing SIAM Slides PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Market, Integration Tools, Developer, Data Integration Issues, Data Format Issues. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Selecting Secured Threat Management Software Information PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative cyber safety incident management selecting secured threat management software information pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Analysis Of Successful Threat Management Implementation Background PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Analysis Of Successful Threat Management Implementation Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Analysis Of Successful Threat Management Implementation Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Real Time Assessment Of Security Threats Icons Slide For Real Time Assessment Of Security Threats Sample PDF
Presenting our innovatively structured real time assessment of security threats icons slide for real time assessment of security threats sample pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Measures To Mitigate Execute Operational Procedure Challenges Slides PDF
This slide provides information about the ways and measures through which the company can overcome the challenges and issues related to Operational Process Improvement Deliver and pitch your topic in the best possible manner with this measures to mitigate execute operational procedure challenges slides pdf. Use them to share invaluable insights on inability to access knowledge, managing overhead costs, operational process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Measures To Mitigate Operational Process Improvement Challenges Summary PDF
This slide provides information about the ways and measures through which the company can overcome the challenges and issues related to Operational Process Improvement. Deliver and pitch your topic in the best possible manner with this measures to mitigate operational process improvement challenges summary pdf. Use them to share invaluable insights on implement, management, security, technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Challenges Faced By Shipment Services Companies Diagrams PDF
This slide shows the challenges faced by transportation industry. It includes supply chain integration, digital transformation, proactive cyber security, parking issues and traffic. Pitch your topic with ease and precision using this Challenges Faced By Shipment Services Companies Diagrams PDF. This layout presents information on Online Sales, Proactive Cyber Security, Workforce. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Apache Hadoop Software Deployment Challenges Of Hadoop Platform Structure PDF
This slide describes the challenges of the Hadoop platform, including slow processing speed, no caching, iterative processing, small file issues, and lengthy coding.Deliver and pitch your topic in the best possible manner with this Apache Hadoop Software Deployment Challenges Of Hadoop Platform Structure PDF. Use them to share invaluable insights on Iterative Processing, Processing Speed, Random Reading and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Branding Fundamental Challenges Faced By Marketing Managers Inspiration PDF
The following slide exhibits challenges faced by managers in branding. The issues covered are maintain consistency across multiple platforms, dealing with negativity and future business planning. Showcasing this set of slides titled Branding Fundamental Challenges Faced By Marketing Managers Inspiration PDF. The topics addressed in these templates are Improves Customer Relationship, Demanding Customers, Ineffective Customer Service. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Content Performance Analysis Challenges With Mitigation Plan Formats PDF
This slide exhibits content performance issue with remedies to achieve goals and produce effective outcomes. It includes challenges no plan, content relevancy, inconsistency and selection of niche. Presenting Content Performance Analysis Challenges With Mitigation Plan Formats PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Irrelevant Content, Inconsistency, Niche Selection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Devops Benefits And Challenges Ppt PowerPoint Presentation File Professional PDF
This slide provides the glimpse about the DevOps benefits and challenges which covers the details of the advantages and the issues faced by the company due to DevOps adoption. There are so many reasons you need a Devops Benefits And Challenges Ppt PowerPoint Presentation File Professional PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Common Challenges Of Permission Advertising Strategy Infographics PDF
This slide shows permission marketing challenges that negatively effect marketing program and goodwill. It include various issues such as lack of strategy, resources, processes, information etc. with key insights. Showcasing this set of slides titled Common Challenges Of Permission Advertising Strategy Infographics PDF. The topics addressed in these templates are Strategy, Finances, Permission Marketing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Challenges In Business Environmental Assessment Rules PDF
Following slide represents potential issues faced by companies while conduct business environment assessment. It includes challenges such as uncertainty, complexity, limited resources etc. Find a pre-designed and impeccable Major Challenges In Business Environmental Assessment Rules PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Financial Assessment Method Challenges In Making Reports Guidelines PDF
This slide shows different limitations to process of financial evaluation of firm while making report. It include challenges like biasness, based on past data , comparability issues etc. Presenting Financial Assessment Method Challenges In Making Reports Guidelines PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Biasness, Comparability, Reliability Figures. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
SWOT Analysis Of ABC Software Company Threats Icons PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like liability laws, intense competition, shortage of skilled workforce. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
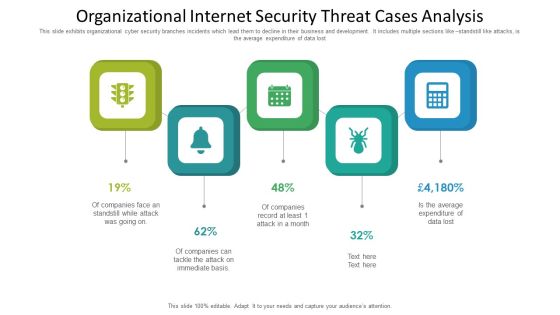
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
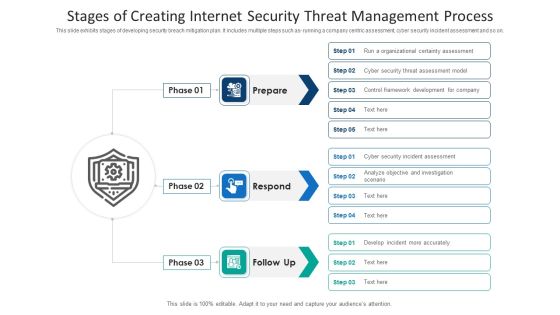
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
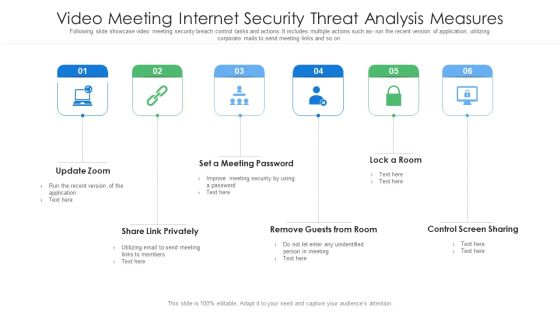
Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
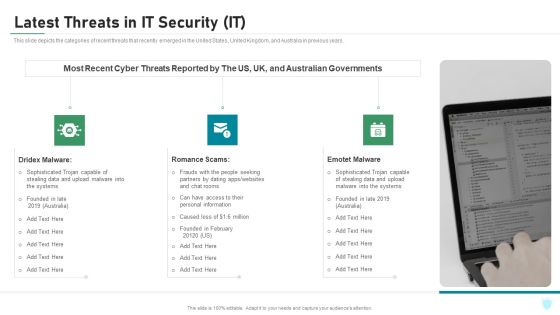
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
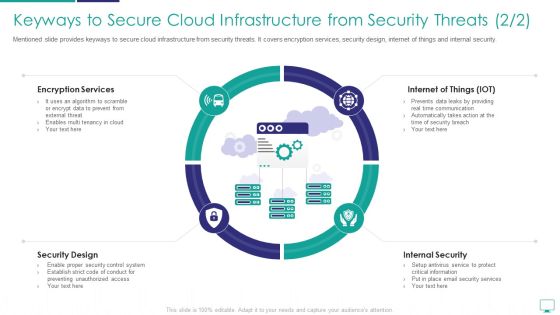
Keyways To Secure Cloud Infrastructure From Security Threats Formats PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a keyways to secure cloud infrastructure from security threats formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encryption services, internet of things, security design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Latest Threats In Computer Security Inspiration PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting desktop security management latest threats in computer security inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial, information, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
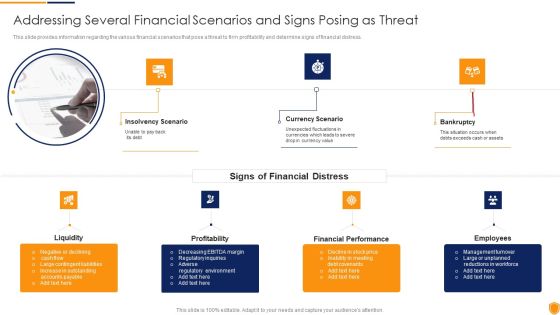
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Several Financial Diagrams PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. This is a mitigating cybersecurity threats and vulnerabilities addressing several financial diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insolvency scenario, currency scenario, bankruptcy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Key Activities Checklist Diagrams PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a mitigating cybersecurity threats and vulnerabilities key activities checklist diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collect, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
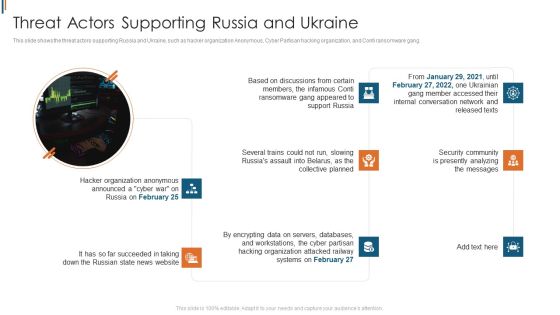
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF
This slide highlights different dimensions of marketing analysis which will assist the firm to mitigate business environment threats. The dimensions are market size, market trends, distribution channels, and market profitability. Persuade your audience using this Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Market Size, Market Trends, Distribution Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
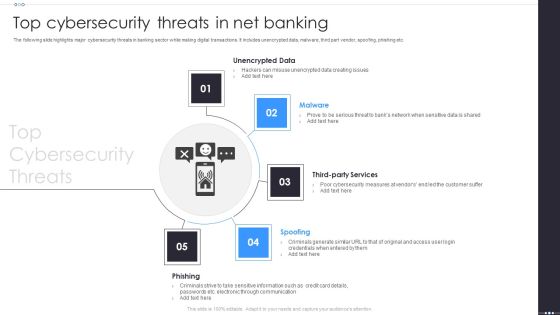
Top Cybersecurity Threats In Net Banking Download PDF
The following slide highlights major cybersecurity threats in banking sector while making digital transactions. It includes unencrypted data, malware, third part vendor, spoofing, phishing etc. Persuade your audience using this Top Cybersecurity Threats In Net Banking Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Unencrypted Data, Spoofing, Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Threats Loss Of Data Guidelines PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a Cloud Security Threats Loss Of Data Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategies, Service Provider, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety And Security Threat Report With Action Plan Mockup PDF
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Threat Modeling Procedure Themes PDF
This slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method.Presenting Best Practices For Threat Modeling Procedure Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Project Execution, Determine Budget, Existing Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Comparative Analysis Of Threat Intelligence Tools Rules PDF
This slide provides a key comparison of cyber intelligence tools that enable organizations to gather and examine threat data from multiple sources in order to safeguard business against potential weaknesses. It compares tools on the basis of parameters such as features, USP, pricing ,etc. Showcasing this set of slides titled Comparative Analysis Of Threat Intelligence Tools Rules PDF. The topics addressed in these templates are Description, Features, Unique Selling Proposition. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF
This slide represents an architecture for gathering reliable data and sustainable computing based on a block chain proposed cyber threat intelligence framework . It includes three layers device, feed and cloud. Showcasing this set of slides titled Threat Intelligence System Architecture For Reliable Data Collection Pictures PDF. The topics addressed in these templates are Cloud Server, Accurate Information Storing, Open Source Service. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roadmap For Financial Accounting Transformation Key Challenges In Achieving Objectives Of Financial Professional PDF
The slide provides the key challenges faced by the company while achieving the objective of accounting and finance transformation. Key issues include responsiveness to business needs efficiency and cost pressures technical issues governance, risk and compliance etc. This is a roadmap for financial accounting transformation key challenges in achieving objectives of financial professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsiveness to business needs, efficiency and cost pressures, technology, governance, risk and compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Of Risks Ppt PowerPoint Presentation Slides Portfolio
This is a types of risks ppt powerpoint presentation slides portfolio. This is a four stage process. The stages in this process are political issues, legal issues, terrorism, natural disasters.

Issue Log In Project Management With Mitigation Strategy Ppt PowerPoint Presentation File Objects PDF
This slide showcases log table that can help organization to identify the possible risks for different project activities and formulate strategies to avoid the issue formation. Its key components are project elements, risk, identification date and mitigation plan. Showcasing this set of slides titled issue log in project management with mitigation strategy ppt powerpoint presentation file objects pdf. The topics addressed in these templates are project elements, risk, identified date risk, mitigation strategy, avoid issue conversion. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Diagram Umbrella For Protection Against External Threats Presentation Template
This business diagram is designed with graphics of umbrella. You may use this business slide to present protection against external threats. This diagram provides an effective way of displaying information you can edit text, color, shade and style as per you need.
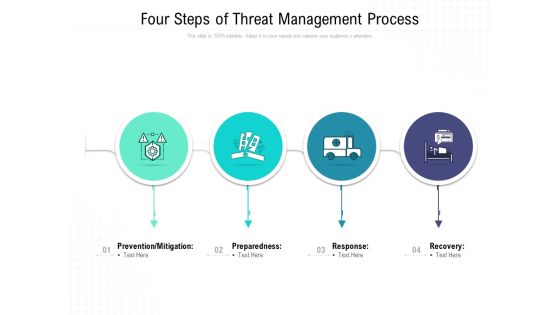
Four Steps Of Threat Management Process Ppt Show Inspiration PDF
Presenting this set of slides with name four steps of threat management process ppt show inspiration pdf. This is a four stage process. The stages in this process are prevention, mitigation, preparedness, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Analysis Process Planning Management Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name threat analysis process planning management ppt powerpoint presentation complete deck. The topics discussed in these slides are process, planning, management, evaluation, organization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Mitigation Strategies For Operational Threat Location Ppt Portfolio Introduction PDF
This is a mitigation strategies for operational threat location ppt portfolio introduction pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like location. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigation Strategies For Operational Threat Dashboard Ppt Layouts Topics PDF
Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat dashboard ppt layouts topics pdf bundle. Topics like dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For How To Intensify Project Threats Elements PDF
Download our innovative and attention grabbing icons slide for how to intensify project threats elements pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

How To Intensify Project Threats Post It Notes Clipart PDF
Presenting how to intensify project threats post it notes clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How To Intensify Project Threats Roadmap Slides PDF
Presenting how to intensify project threats roadmap slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Intensify Project Threats Timeline Themes PDF
This is a how to intensify project threats timeline themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Threat Administration Bundle Guidelines PDF
Introducing our well designed icons slide for threat administration bundle guidelines pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Threat Administration Bundle Table Of Contents Microsoft PDF
Presenting threat administration bundle table of contents microsoft pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like business, organization, management, communication, action plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For Mitigating Cybersecurity Threats And Vulnerabilities Microsoft PDF
Introducing our well designed icons slide for mitigating cybersecurity threats and vulnerabilities microsoft pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Threat Management At Workplace Elements Pdf
Introducing our well designed icons slide for threat management at workplace elements pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Icons Slide For IT Threats Response Playbook Download PDF
Download our innovative and attention grabbing Icons Slide For IT Threats Response Playbook Download PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

IT Threats Response Playbook Incident Management Workflow Themes PDF
Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Incident Management Workflow Themes PDF bundle. Topics like Incident Occurs, Incident Resolution, Resolution Achieved can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Threats Response Playbook Incident Response Categories Rules PDF
Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Incident Response Categories Rules PDF. Use them to share invaluable insights on Identification Suspicious, Direct Impact, Time To Report and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook SWOT Analysis Professional PDF
This is a IT Threats Response Playbook SWOT Analysis Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For IT Threats Response Playbook Clipart PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For IT Threats Response Playbook Clipart PDF. Use them to share invaluable insights on Security Incidents, Figures And Statistics, Ransom Payment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Icons Slides For Fraud Threat Administration Guide Pictures PDF
Introducing our well designed Icons Slides For Fraud Threat Administration Guide Pictures PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Threat Management Model With Performance Strategy Topics PDF
Showcasing this set of slides titled Threat Management Model With Performance Strategy Topics PDF. The topics addressed in these templates are Monthly Performance Plan, Weekly Performance Plan, Annual Performance Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Icons Slide For Information Technology Threat Mitigation Methods Icons PDF
Presenting our innovatively structured Icons Slide For Information Technology Threat Mitigation Methods Icons PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
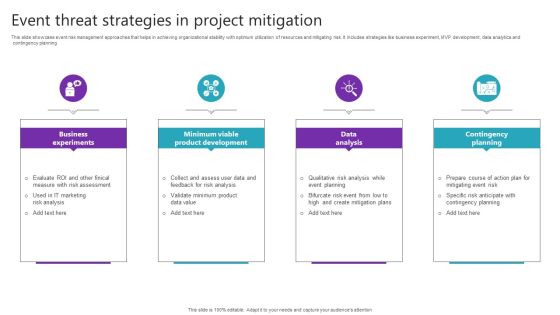
Event Threat Strategies In Project Mitigation Diagrams PDF
Presenting Event Threat Strategies In Project Mitigation Diagrams PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Business Experiments, Minimum Viable, Product Development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Online Gaming Funding Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Portrait PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver an awe inspiring pitch with this creative online gaming funding pitch deck what video game experience challenges are faced by prospect portrait pdf bundle. Topics like security threats, regulatory compliances can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Virtual Adventure Gaming Investor Elevator Pitch Deck What Video Game Experience Challenges Professional PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver and pitch your topic in the best possible manner with this virtual adventure gaming investor elevator pitch deck what video game experience challenges professional pdf. Use them to share invaluable insights on security threats, regulatory compliances and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Electronic Game Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Topics PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver an awe inspiring pitch with this creative electronic game pitch deck what video game experience challenges are faced by prospect topics pdf bundle. Topics like security threats, regulatory compliances, systems information breach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Computerized Game Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Download PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver and pitch your topic in the best possible manner with this computerized game pitch deck what video game experience challenges are faced by prospect download pdf. Use them to share invaluable insights on regulatory compliances, security threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Online Gaming Fundraising Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Slides PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver and pitch your topic in the best possible manner with this online gaming fundraising pitch deck what video game experience challenges are faced by prospect slides pdf. Use them to share invaluable insights on security threats, regulatory compliances and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Solutions To Fundamental Challenges Faced By Supply Chain Managers Professional PDF
This slide showcases significant supply chain management concerns faced by managers. The issues covered are managing supplier, risk mitigation, managing customer expectations, inventory management, product packaging and shipping costs. Presenting Solutions To Fundamental Challenges Faced By Supply Chain Managers Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Managing Suppliers, Risk Mitigation, Managing Customer Expectations, Shipping Costs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
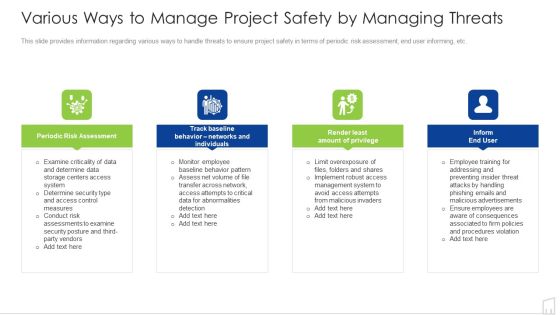
Various Ways To Manage Project Safety By Managing Threats Ppt Ideas Deck PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting various ways to manage project safety by managing threats ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine, system, data, risk, periodic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
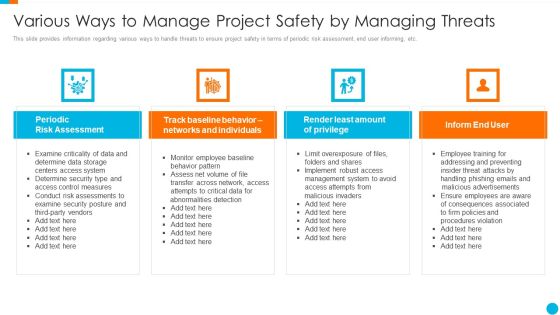
Upgrading Total Project Safety IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. This is a upgrading total project safety it various ways to manage project safety by managing threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Asset Allocation Ppt Powerpoint Presentation Icon Background Images
This is a asset allocation ppt powerpoint presentation icon background images. This is a two stage process. The stages in this process are risk, reward, compare, risk reward ratio, marketing.

Two Steps To Deal With New Threats Ppt PowerPoint Presentation Gallery Examples PDF
Presenting two steps to deal with new threats ppt powerpoint presentation gallery examples pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including finding risk, deal with new threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

4 Types Of Security Assessment With Threat And Vulnerability Ppt PowerPoint Presentation Outline Inspiration PDF
Presenting 4 types of security assessment with threat and vulnerability ppt powerpoint presentation outline inspiration pdf. to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including risk assessment, vulnerability assessment, threat assessment, impact assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

PEST Analysis To Understand Market Opportunities And Threats Mockup PDF
This slide provides a framework for understanding the external environment and identifying potential opportunities and threats to help make informed decisions. The slide covers political, economic, technological and socio cultural factors. Present like a pro with PEST Analysis To Understand Market Opportunities And Threats Mockup PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Addressing Threat Management Team Training Schedule Designs PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Addressing Threat Management Team Training Schedule Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Commodity Expansion Key Challenges And Solutions To Overcome Pictures PDF
This slide signifies the commodity expansion strategy key threats and strategies implemented to overcome. It covers information about ineffective marketing strategy, large no of competitors with solutions to overcome them. Presenting Commodity Expansion Key Challenges And Solutions To Overcome Pictures PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Competitors Analysis, Management System, Customer Conversion. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Swot Analysis Threats Related To The Company Template PDF
Presenting swot analysis threats related to the company template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high competition, growing concerns about health, change in market trends. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SWOT Analysis Of ADC Cosmetics Company Threats Download PDF
Presenting swot analysis of adc cosmetics company threats download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like intense competition from similar companies, changes in consumer demand and preferences , government regulations and currency fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
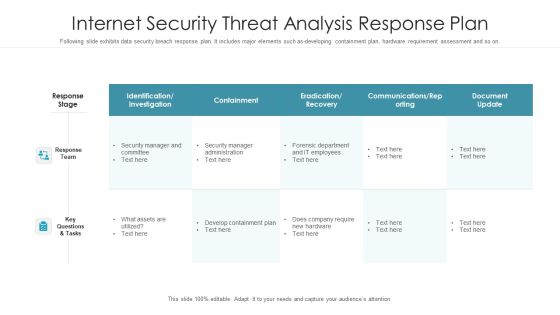
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
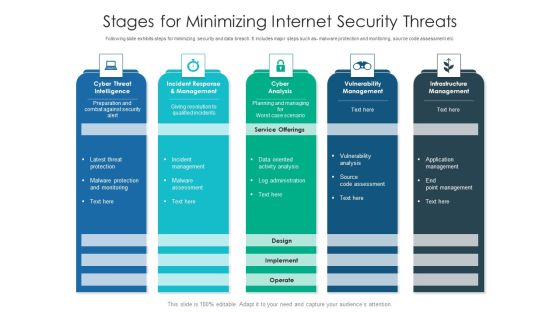
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
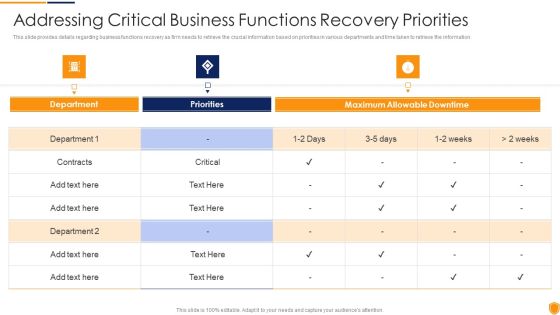
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Critical Business Information PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing critical business information pdf bundle. Topics like addressing critical business functions recovery priorities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Mitigating Cybersecurity Threats And Vulnerabilities Evaluating Financial Practices Themes PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities evaluating financial practices themes pdf bundle. Topics like evaluating financial practices in firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Mitigating Cybersecurity Threats And Vulnerabilities Financial Performance Tracking Designs PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities financial performance tracking designs pdf. Use them to share invaluable insights on receivables analysis, revenue and expense trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Technological Assessment Sample PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities technological assessment sample pdf bundle. Topics like Industry Standard, Firms Standard, Client Onboarding, Service Failure Rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
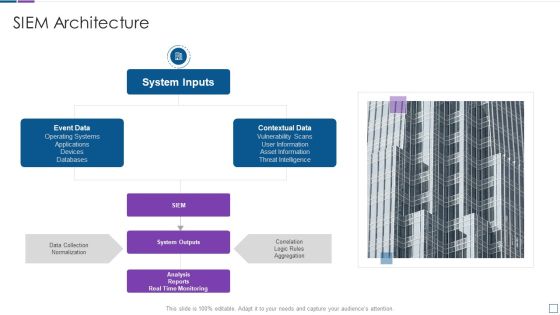
Real Time Assessment Of Security Threats SIEM Architecture Sample PDF
This is a real time assessment of security threats siem architecture sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system inputs, event data, contextual data, system outputs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda Of Threat Management At Workplace Professional Pdf
This is a agenda of threat management at workplace professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital assets, financial assets, physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Budget For Effective Threat Management At Workplace Structure Pdf
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative budget for effective threat management at workplace structure pdf bundle. Topics like client onboarding process, information management, implement duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Addressing Asset Security Categorization Diagrams Pdf
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Deliver and pitch your topic in the best possible manner with this threat management at workplace addressing asset security categorization diagrams pdf. Use them to share invaluable insights on confidentiality, security categorization, ownership, integrity, description and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Threat Management At Workplace Financial Performance Tracking Dashboard Introduction Pdf
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this threat management at workplace financial performance tracking dashboard introduction pdf. Use them to share invaluable insights on revenue trends, expense trends, receivables analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Purpose Of IT Threats Response Playbook Professional PDF
This is a Purpose Of IT Threats Response Playbook Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Standardized Cybersecurity, Future Security, Appropriate Manner. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Fraud Threat Administration Guide Slide Structure PDF
Presenting Table Of Contents Fraud Threat Administration Guide Slide Structure PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Protect Business, Framework Prevent, Activities Initiatives. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Information Technology Threat Mitigation Methods Background PDF
This is a Agenda For Information Technology Threat Mitigation Methods Background PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise, Organization, Management Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Natural Calamities Posing Threat To Organization Infrastructure Brochure PDF
Boost your pitch with our creative Addressing Natural Calamities Posing Threat To Organization Infrastructure Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Organizational Security Solutions Analysing Various Threats Faced By Firm Professional PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative organizational security solutions analysing various threats faced by firm professional pdf bundle. Topics like threats, negligent, occurrence, compromised, malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Analyzing Various Threats Faced By Firm Introduction PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative security functioning centre analyzing various threats faced by firm introduction pdf bundle. Topics like threats, operations, compromised can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Challenges Of Implementing Supplier Development Program Slide Introduction PDF
The purpose of this slide is to highlight the key challenges of implementing supplier development program such as suppliers rigidity, trust issues, non disclosure of price models and prejudice towards business owners. It also provides information regarding the strategies to overcome such issues.Want to ace your presentation in front of a live audience Our Key Challenges Of Implementing Supplier Development Program Slide Introduction PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Kraljics Matrix Product Procurement Management Strategies Ppt File Microsoft PDF
This slide covers strategies used by each driver in kraljics matrix to identify and minimize risk and disruptions. The major categories are leverage, strategic, non-critical and bottleneck. Persuade your audience using this Kraljics Matrix Product Procurement Management Strategies Ppt File Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Leverage Categories, Strategic Categories, Bottleneck Categories. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Assessing Risks With Gap Analysis Example Background Designs
This is a assessing risks with gap analysis example background designs. This is a five stage process. The stages in this process are evaluate effectiveness, establish a context for analysis, analyze risk, identify model potential threats, determine risk treatment, threat identification, diagram of flow.
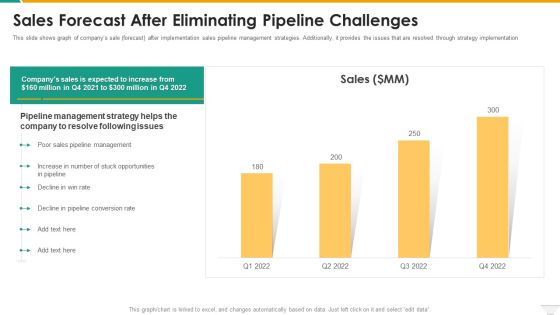
Sales Forecast After Eliminating Pipeline Challenges Guidelines PDF
This slide shows graph of companys sale forecast after implementation sales pipeline management strategies. Additionally, it provides the issues that are resolved through strategy implementation. Deliver and pitch your topic in the best possible manner with this Sales Forecast After Eliminating Pipeline Challenges Guidelines PDF. Use them to share invaluable insights on Management, Sales, Opportunities, Rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
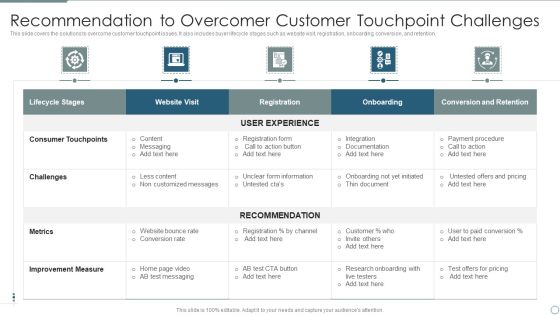
Recommendation To Overcomer Customer Touchpoint Challenges Formats PDF
This slide covers the solutions to overcome customer touchpoint issues. It also includes buyer lifecycle stages such as website visit, registration, onboarding, conversion, and retention. Showcasing this set of slides titled Recommendation To Overcomer Customer Touchpoint Challenges Formats PDF. The topics addressed in these templates are Consumer Touchpoints, Metrics, Improvement Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Fundamental Challenges Of New Product Development Information PDF
This slide depicts the difficulties that Product Managers confront while working on a new product initiative. The issues covered are workflow management, pricing policies and time to market. Presenting Fundamental Challenges Of New Product Development Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Workflow Management, Interacting, Time To Market. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly Information Technology Security Roadmap For Continuous Threat Analysis Download
Presenting the quarterly information technology security roadmap for continuous threat analysis download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
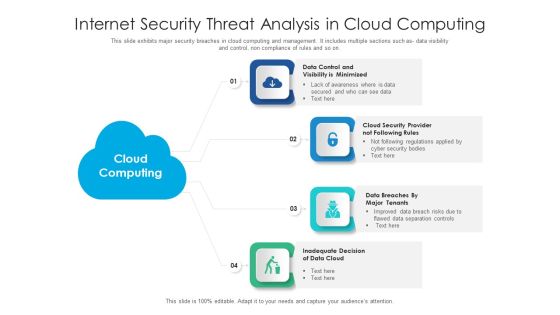
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
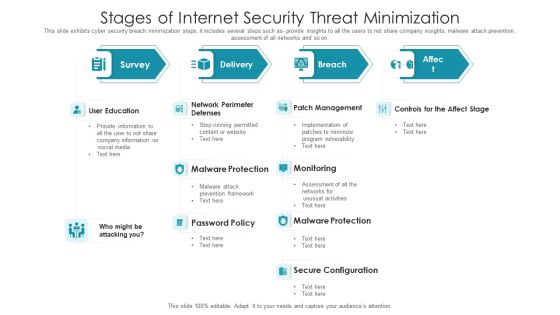
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

How To Intensify Project Threats Hierarchical Escalation Process Summary PDF
This slide provides the glimpse about the hierarchical escalation along with the hierarchy structure and meaning of such an escalation. This is a how to intensify project threats hierarchical escalation process summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, service, hierarchical, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Functional Escalation Process Rules PDF
This slide provides the glimpse about the functional escalation along with the functional structure and meaning of such an escalation. This is a how to intensify project threats functional escalation process rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, service, functional escalation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Vital Records Inspiration PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. This is a mitigating cybersecurity threats and vulnerabilities ensuring vital records inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring vital records maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Themes PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting mitigating cybersecurity threats and vulnerabilities incident reporting themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
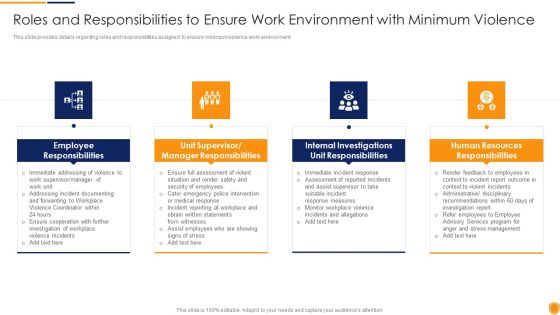
Mitigating Cybersecurity Threats And Vulnerabilities Roles And Responsibilities Introduction PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Workplace Employee Rules PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting mitigating cybersecurity threats and vulnerabilities workplace employee rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
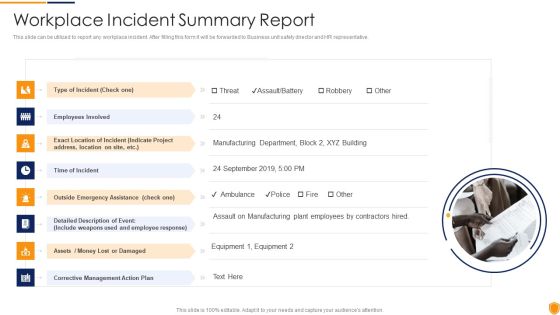
Mitigating Cybersecurity Threats And Vulnerabilities Workplace Incident Summary PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a mitigating cybersecurity threats and vulnerabilities workplace incident summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like type of incident, time of incident, corrective management action plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
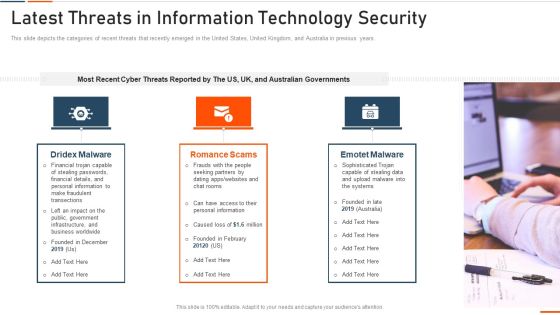
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Management At Workplace Ensuring Vital Records Maintenance Demonstration Pdf
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this threat management at workplace ensuring vital records maintenance demonstration pdf. Use them to share invaluable insights on primary location of records, scanned images on network drive other parties, department file cabinets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management At Workplace Employee Assistance Program Demonstration PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace employee assistance program demonstration pdf. Use them to share invaluable insights on clinical services, work and life services, employer services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
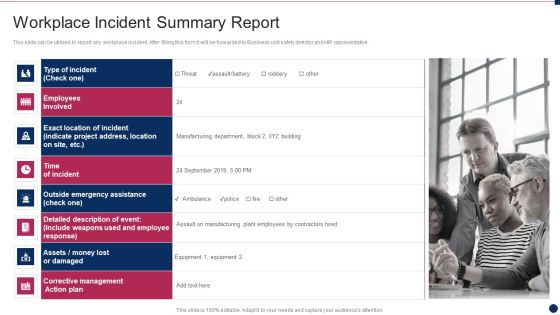
Threat Management At Workplace Incident Summary Report Ideas PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Presenting threat management at workplace incident summary report ideas pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like time of incident, corrective management action plan, exact location of incident. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
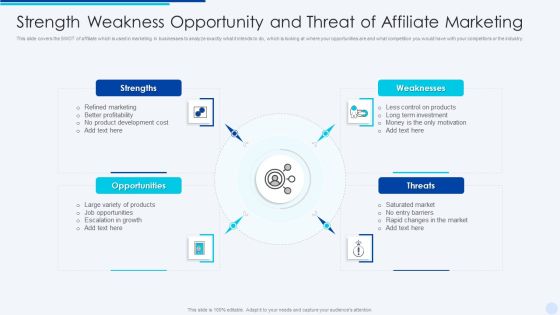
Strength Weakness Opportunity And Threat Of Affiliate Marketing Sample PDF
This slide covers the SWOT of affiliate which is used in marketing in businesses to analyze exactly what it intends to do, which is looking at where your opportunities are and what competition you would have with your competitors or the industry. Persuade your audience using this Strength Weakness Opportunity And Threat Of Affiliate Marketing Sample PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Weaknesses, Opportunities, Strengths Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Supply Chain Strength Weakness Opportunity Threat Analysis Rules PDF
This slide showcases the SWOT analysis of the supply chain of n organization to provide better customer experience and deliver the goods at a fast pace. Persuade your audience using this Supply Chain Strength Weakness Opportunity Threat Analysis Rules PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Opportunities, Weaknesses, Strengths Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Disaster Threat Cause Pie Chart Ppt Pictures Gallery PDF
The given below slide showcases the major causes of business disasters to assess and formulate recovery plan accordingly. It mainly includes software failure, data sabotage, ransomware, human error, hardware failure etc. Showcasing this set of slides titled Business Disaster Threat Cause Pie Chart Ppt Pictures Gallery PDF. The topics addressed in these templates are Key Insights, Few Possible Solutions, Implement Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Breach Threats Process Flow Model Ppt Model Maker PDF
This slide covers process of data breach in an organisation. It includes steps such as researching weak points, staging attack and exfiltration of data resulting it to data breach in an organisation. Persuade your audience using this Data Breach Threats Process Flow Model Ppt Model Maker PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Stage Attack, Exfiltrate, Social Engineering. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strengths Weakness Opportunities And Threat Prioritization Structure Template PDF
The following slide presents the SWOT analysis of an organization to evaluate current status and form new strategies. It includes some activities and each activity given a plus point and post that total is evaluated. Pitch your topic with ease and precision using this Strengths Weakness Opportunities And Threat Prioritization Structure Template PDF. This layout presents information on Market Awareness, Opportunities, Organic Growth. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Cyber Threat Prevention Flowchart Slides PDF
The below slide provides a cloud security framework which encourages security companies to clarify the roles played by the various cloud security stakeholders within their organization and enhance overall security compliance. Major stages are visibility, governance, resolve violation, etc. Showcasing this set of slides titled Cloud Computing Cyber Threat Prevention Flowchart Slides PDF. The topics addressed in these templates are Visibility, Governance, Resolve Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email
 Sign up for an account
Sign up for an account
 Home
Home