Privacy

Contact Us For Security Camera Services One Pager Sample Example Document
This slide depicts the contact information of the bidding company for the client covering details about the address, contact numbers, and email address. Presenting you an exemplary Contact Us For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Contact Us For Security Camera Services One Pager Sample Example Document brilliant piece now.

Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document
This slide illustrates the cover letter for the business proposal providing a brief overview of the clients wants and a brief introduction to the project. Presenting you an exemplary Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document brilliant piece now.

Next Steps For Security Camera Services One Pager Sample Example Document
This slide indicates the next steps to execute post acceptance of business proposal with signatures of both project lead and client. Presenting you an exemplary Next Steps For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Steps For Security Camera Services One Pager Sample Example Document brilliant piece now.

Our Team For Security Camera Sarvices One Pager Sample Example Document
This slide shows the project execution team with the individual members name, designation, and brief work description. Presenting you an exemplary Our Team For Security Camera Sarvices One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Team For Security Camera Sarvices One Pager Sample Example Document brilliant piece now.

Plan Of Action For Security Camera Services One Pager Sample Example Document
This slide indicates the project plan of action showing the multistep approach to be followed by the bidding company for the successful execution of the business project for the client. Presenting you an exemplary Plan Of Action For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Plan Of Action For Security Camera Services One Pager Sample Example Document brilliant piece now.

Project Context And Objectives For Security Camera Services One Pager Sample Example Document
This slide covers the project context highlighting multiple challenges faced by the client along with detailed objectives of the business proposal. Presenting you an exemplary Project Context And Objectives For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Project Context And Objectives For Security Camera Services One Pager Sample Example Document brilliant piece now.

Statement Of Work And Contract For Security Camera Services One Pager Sample Example Document
This slide depicts the terms and conditions of the proposal contract covering details about the client name, address, and company information. Presenting you an exemplary Statement Of Work And Contract For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Statement Of Work And Contract For Security Camera Services One Pager Sample Example Document brilliant piece now.

Why Us For Security Camera Services One Pager Sample Example Document
This slide depicts the why us slide of the project highlighting multiple strengths that will be added to the clients company on acceptance of the business proposal. Presenting you an exemplary Why Us For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Why Us For Security Camera Services One Pager Sample Example Document brilliant piece now.

Your Investment For Security Camera Services One Pager Sample Example Document
This slide tabulates the cost associated with the multiple stages of the project with tax rate and total amount. Presenting you an exemplary Your Investment For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Investment For Security Camera Services One Pager Sample Example Document brilliant piece now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. There are so many reasons you need a Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF
Explore a selection of the finest Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cybersecurity Awareness Program To Prevent Attacks Major Statistics Of Cyber Security Awareness Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
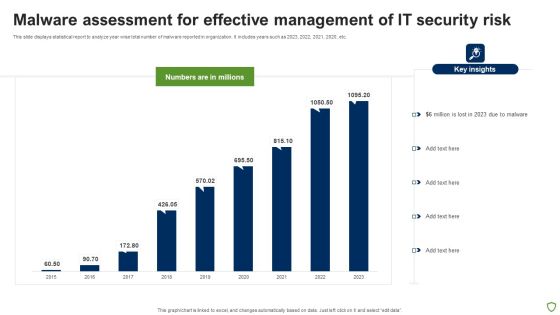
Malware Assessment For Effective Management Of IT Security Risk Portrait PDF
This slide displays statistical report to analyze year wise total number of malware reported in organization. It includes years such as 2023, 2022, 2021, 2020, etc. Showcasing this set of slides titled Malware Assessment For Effective Management Of IT Security Risk Portrait PDF. The topics addressed in these templates are Malware Assessment For Effective, Management IT Security Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Want to ace your presentation in front of a live audience Our Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF
This slide shows cyber security events matrices. The purpose of this dashboard is to track cyber threat incidents and to classify resolve and unresolve incidents. It includes elements such as incident status, new incidents, last six months incident graph. Showcasing this set of slides titled Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF. The topics addressed in these templates are Current Month, Closed Incidents, Last Month, Resolved Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Cases Action Plans Process Ppt PowerPoint Presentation File Show PDF
This slide covers procedure of cyber security incident response. The purpose of this process is to examine the cyber threat and try to find the ways to mitigate the risk. It includes four steps such as identification and detection, containment, eradication and recovery and post recovery. Presenting Cyber Security Cases Action Plans Process Ppt PowerPoint Presentation File Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identification And Detection, Containment, Eradication And Recovery, Post Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF
This slide covers cyber security incident response proposition. The purpose of this plan is to provide direction of action to the whole response team. It includes elements such as list of incidents, their responses, responsible person and resolve date. Showcasing this set of slides titled Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF. The topics addressed in these templates are Data Stealing Through, Network Monitoring, Server Crashing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF
This slide covers classification of cyber security events of financial organizations. The purpose of this classification is to identify events which needs immediate response. It includes elements such as severity level, cyber incidents, occurrence pattern, performance impact, data breach and financial costs Pitch your topic with ease and precision using this Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF. This layout presents information on Severity Level, Cyber Incidents, Occurrence Pattern, Performance Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF
This slide highlights scorecard related to security breaches in gaming field. The purpose of this template is to rate the incidents based on severity. It includes elements such as account taken over, personal details posting on web, spyware, data breaches and cyber bullying. Showcasing this set of slides titled Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF. The topics addressed in these templates are Incident, Score, Data Breaches, Low, High. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF
Find highly impressive Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF
The slide highlights a process of cloud audit to test the security controls. Various steps involved are planning, data collection, analyse, recommendations and remediation Persuade your audience using this Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Analyse, Recommendations, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF
The slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Persuade your audience using this Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF. This PPT design covers FOUR stages, thus making it a great tool to use. It also caters to a variety of topics including Calculate Score, Understand The Model, Analyse Validate Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Benefits Of Cloud Security Assessment Ppt PowerPoint Presentation Icon Infographics PDF
The slide exhibits various advantages of the cloud audit in assessing and improvising the overall security controls. Various benefits included are ensure compliance, understand the system, evaluate the effectiveness and overall improvement. Presenting Key Benefits Of Cloud Security Assessment Ppt PowerPoint Presentation Icon Infographics PDF to dispense important information. This template comprises FOUR stages. It also presents valuable insights into the topics including Ensure Compliance, Evaluate The Effectiveness, Understand The System, Overall Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
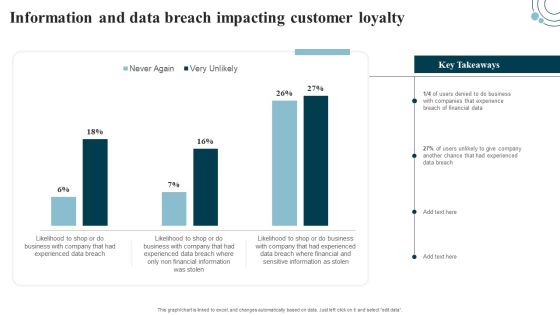
Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Get a simple yet stunning designed Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
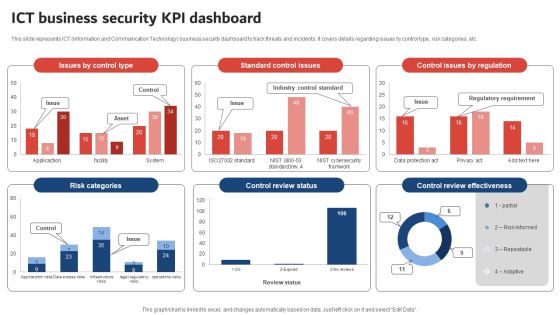
Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF
This slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Boost your pitch with our creative Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard To Track IT Security Incidents Prevailing Across Firm Inspiration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF from Slidegeeks and deliver a wonderful presentation.

Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. The Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF
This Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Agenda SDN Security Architecture Ppt PowerPoint Presentation Diagram Graph Charts PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Agenda SDN Security Architecture Ppt PowerPoint Presentation Diagram Graph Charts PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Agenda SDN Security Architecture Ppt PowerPoint Presentation Diagram Graph Charts PDF today and make your presentation stand out from the rest

Table Of Contents For SDN Security Architecture Ppt PowerPoint Presentation File Diagrams PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Table Of Contents For SDN Security Architecture Ppt PowerPoint Presentation File Diagrams PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Table Of Contents For SDN Security Architecture Ppt PowerPoint Presentation File Diagrams PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
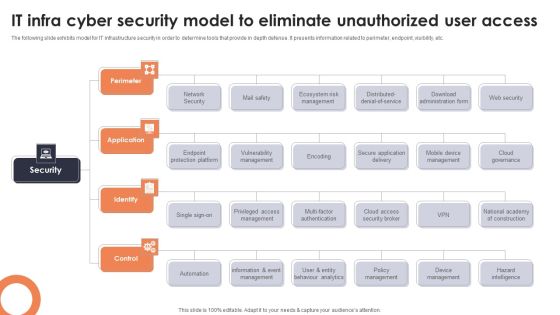
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF
This slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Presenting Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Static Properties Analysis, Interactive Behavior Analysis, Full Automated Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Make sure to capture your audiences attention in your business displays with our gratis customizable Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
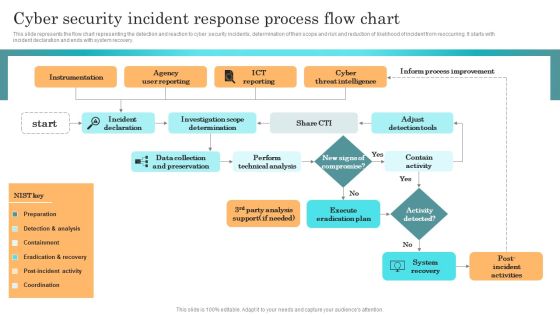
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.
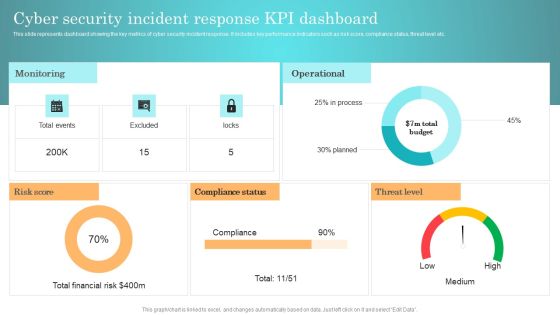
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Technology Policy And Processes Information Security Policy For Employees Structure PDF
This slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Technology Policy And Processes Information Security Policy For Employees Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
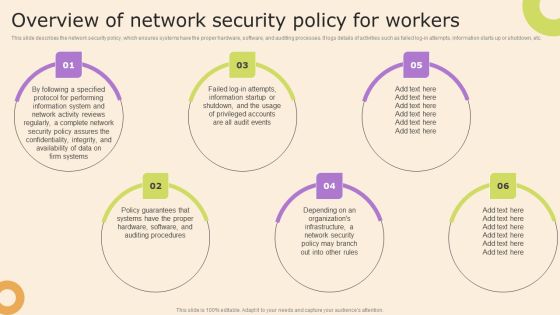
Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF from Slidegeeks and deliver a wonderful presentation.
Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF
The following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Want to ace your presentation in front of a live audience Our Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. The Deploying Corporate Aligned IT Strategy How Management Enables Effective Corporate Security Governance Topics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
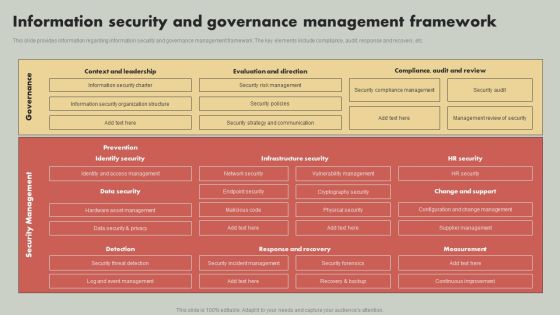
IT Reducing Costs And Management Tips Information Security And Governance Management Framework Demonstration PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate IT Reducing Costs And Management Tips Information Security And Governance Management Framework Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
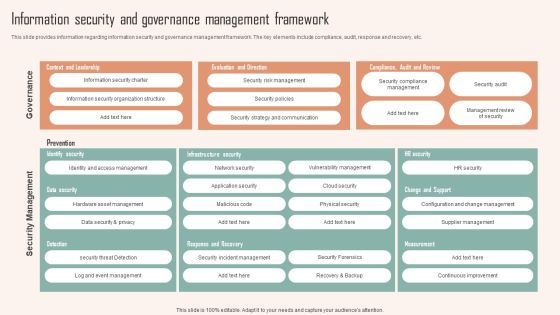
Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security And Governance Management Framework Ppt PowerPoint Presentation Diagram Images PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Secure Web Gateway SWG Importance For Businesses Ppt Professional Graphics PDF
This slide outlines the importance of secure web gateways to businesses. The purpose of this slide is to demonstrate the need for SWGs for companies to protect their critical data and applications from malicious activities and actors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Secure Web Gateway SWG Importance For Businesses Ppt Professional Graphics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
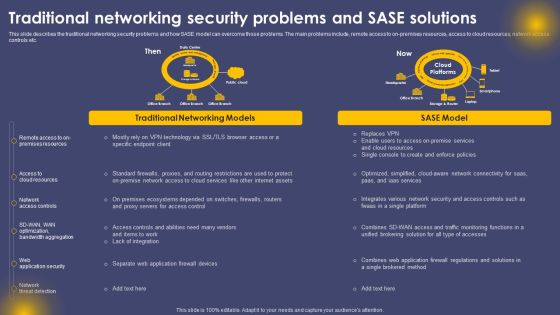
Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.

Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. There are so many reasons you need a Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
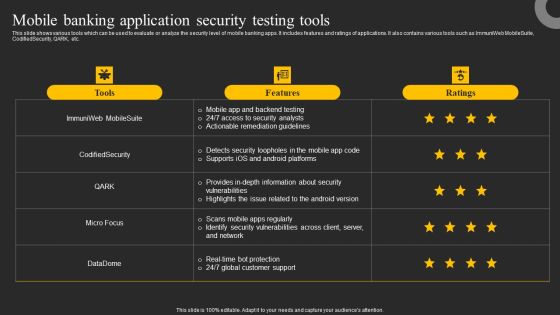
Mobile Banking Application Security Testing Tools Ppt Infographics Graphics Download PDF
This slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Mobile Banking Application Security Testing Tools Ppt Infographics Graphics Download PDF from Slidegeeks and deliver a wonderful presentation.

Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF
The following slide showcases perceptive of expert analysts about IT company i.e. Awake Society. It showcase reviews of IT manager, chief information security officer and IT director. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF can be your best option for delivering a presentation. Represent everything in detail using Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
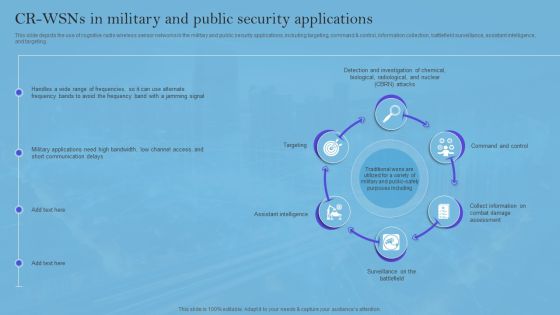
Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Want to ace your presentation in front of a live audience Our Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
 Home
Home