Privacy

Healthcare Information Security Risk Management And Management Plan Information PDF
This slide shows information security risk treatment and acceptance plan for hospitals which can benefit them in securing their data. It contains details such as possession type, risk acceptance criteria, treating the risk, techniques and approaches for risk, residual risk acceptance measures, etc. Pitch your topic with ease and precision using this Healthcare Information Security Risk Management And Management Plan Information PDF. This layout presents information on Measures, Risk Acceptance Criteria, Treating The Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Security And Automation Control System Demonstration PDF
The purpose of this slide is to highlight the incorporation between business security and automation system which enables faster threat detection along with prominent control measures. The automated security system includes alarm systems, fire emergency buttons, control systems, and surveillance systems. Persuade your audience using this Business Security And Automation Control System Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Siren Alarm Systems, Fire Emergency Buttons, Surveillance Systems, Control System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Manpower Corporate Security Business Profile Swot Analysis Introduction PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Swot Analysis Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weaknesses, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security In 5G Technology Architecture 5G Functional Architecture Formats PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.This is a Security In 5G Technology Architecture 5G Functional Architecture Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previous Generations, Distinguish Authentication, Transactions Adaptable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Securing Operations Of Logistics Through Integrated Iot Professional PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver and pitch your topic in the best possible manner with this Securing Operations Of Logistics Through Integrated Iot Professional PDF PDF. Use them to share invaluable insights on Iot Security System, Potential Impact, Management Capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
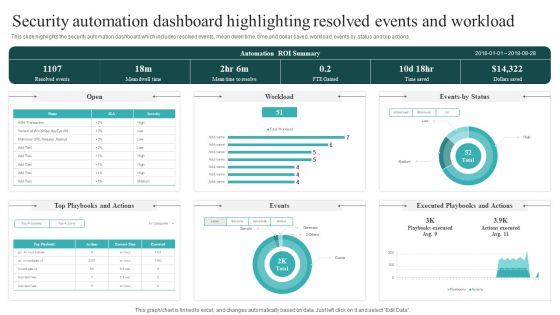
Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. This Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

IT Security Awareness Training Program Plan Ppt Show Tips PDF
This slide covers cybersecurity awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public wi-fi, phishing attacks, mobile device security and passwords and authentication. Showcasing this set of slides titled IT Security Awareness Training Program Plan Ppt Show Tips PDF. The topics addressed in these templates are Training Topic, Mode Of Training, Training Hours. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
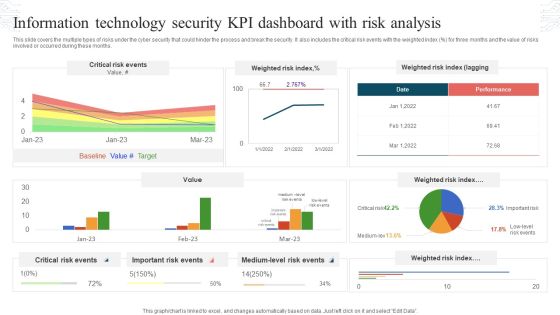
Information Technology Security KPI Dashboard With Risk Analysis Topics PDF
This slide covers the multiple types of risks under the cyber security that could hinder the process and break the security. It also includes the critical risk events with the weighted index percent for three months and the value of risks involved or occurred during these months. Showcasing this set of slides titled Information Technology Security KPI Dashboard With Risk Analysis Topics PDF. The topics addressed in these templates are Critical Risk Events, Weighted Risk Index, Important Risk Events. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
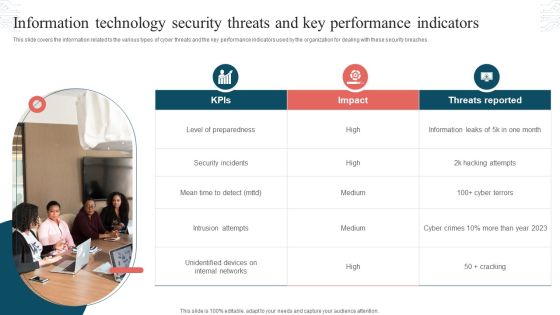
Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
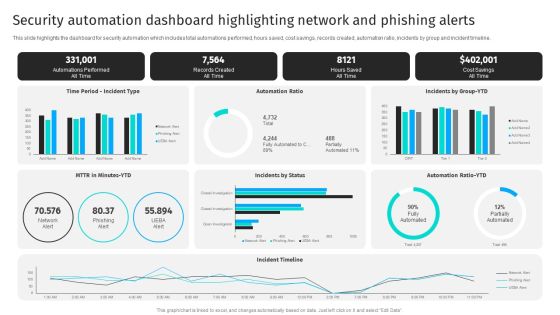
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Elements Of IT Security Plan Background PDF
This slide represents key elements of cyber security strategy such as cyber risk management, security regulatory and compliance, cyber transformation, cyber strategy etc. Persuade your audience using this Key Elements Of IT Security Plan Background PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Strategy, Executive Cyber Dashboard, Education Training Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
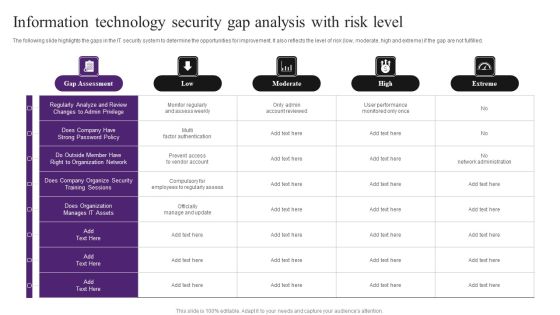
Information Technology Security Gap Analysis With Risk Level Information PDF
The following slide highlights the gaps in the IT security system to determine the opportunities for improvement. It also reflects the level of risk low, moderate, high and extreme if the gap are not fulfilled. Pitch your topic with ease and precision using this Information Technology Security Gap Analysis With Risk Level Information PDF. This layout presents information on Organize Security, Regularly Analyze, Gap Assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
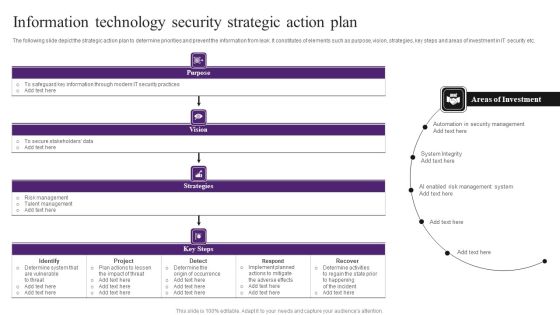
Information Technology Security Strategic Action Plan Themes PDF
The following slide depict the strategic action plan to determine priorities and prevent the information from leak. It constitutes of elements such as purpose, vision, strategies, key steps and areas of investment in IT security etc. Showcasing this set of slides titled Information Technology Security Strategic Action Plan Themes PDF. The topics addressed in these templates are Determine System, Implement, Security Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
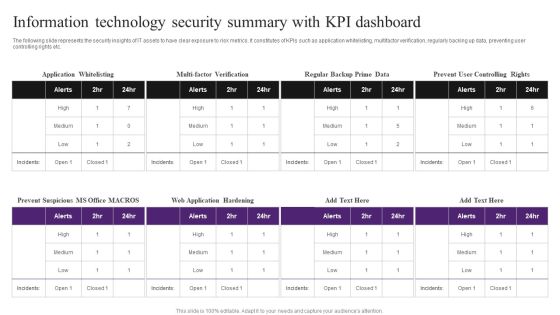
Information Technology Security Summary With KPI Dashboard Inspiration PDF
The following slide represents the security insights of IT assets to have clear exposure to risk metrics. It constitutes of KPIs such as application whitelisting, multifactor verification, regularly backing up data, preventing user controlling rights etc. Pitch your topic with ease and precision using this Information Technology Security Summary With KPI Dashboard Inspiration PDF. This layout presents information on Information Technology Security, Summary With KPI Dashboard. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Problems Management And Action Plan Microsoft PDF
The following slide illustrates the cyber security risk management plan to outline business security threats and draft proposed strategies. It also includes elements such as objectives, issues, breach response actions, employee training etc. Persuade your audience using this Cyber Security Problems Management And Action Plan Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Breach Response Actions, Employee Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Security Management Tool Assessment Matrix Microsoft PDF
This slide highlights a tools comparison matrix for data security governance and management. It includes key components such as threat intelligence, advanced data governance, source score, data helpdesk, price and customer satisfaction. Persuade your audience using this Data Security Management Tool Assessment Matrix Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Threat Intelligence, Advanced Data Governance, Secure Score. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Management Framework With Stakeholders Diagrams PDF
This slide presents a framework of information security governance for proactive risk compliance. It includes key components such as stakeholders, corporate executives, managers, auditors, enterprise, report, evaluate, direct, monitor, information security management, etc. Persuade your audience using this Information Security Management Framework With Stakeholders Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholders, Auditors, Corporate Executives. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

DLT Technology Is Blockchain Technology Secure Pictures PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download DLT Technology Is Blockchain Technology Secure Pictures PDF from Slidegeeks and deliver a wonderful presentation.

IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Amrs In Autonomous Security Robots Asrs Inspiration PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Boost your pitch with our creative Amrs In Autonomous Security Robots Asrs Inspiration PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Running Cyber Security Awareness Campaign For Employees Background PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Running Cyber Security Awareness Campaign For Employees Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Security And Governance Management Framework Elements PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. This Information Security And Governance Management Framework Elements PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security And Governance Management Framework Elements PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
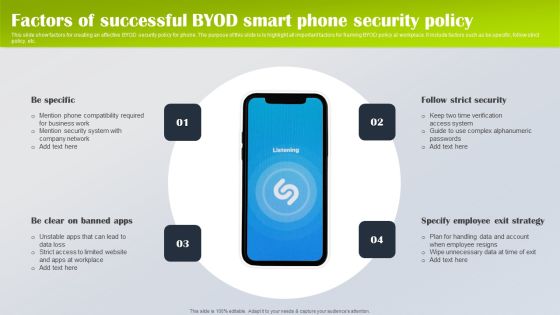
Factors Of Successful Byod Smart Phone Security Policy Designs PDF
This slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting Factors Of Successful Byod Smart Phone Security Policy Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Be Specific, Specify Employee Exit Strategy, Follow Strict Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
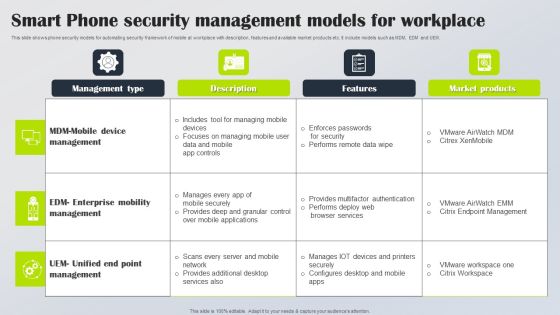
Smart Phone Security Management Models For Workplace Rules PDF
This slide shows phone security models for automating security framework of mobile at workplace with description, features and available market products etc. It include models such as MDM, EDM and UEM. Showcasing this set of slides titled Smart Phone Security Management Models For Workplace Rules PDF. The topics addressed in these templates are Management Type, Description, Features. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
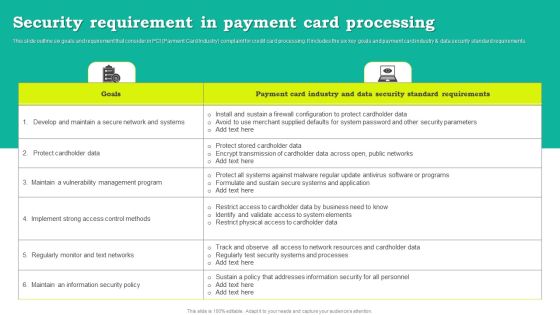
Security Requirement In Payment Card Processing Download PDF
This slide outline six goals and requirement that consider in PCI Payment Card Industry complaint for credit card processing. It includes the six key goals and payment card industry and data security standard requirements. Showcasing this set of slides titled Security Requirement In Payment Card Processing Download PDF. The topics addressed in these templates are Goals, Payment Card Industry, Data Security Standard Requirements. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Risk Management Framework To Manage Security Threats Template PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. The IT Risk Management Framework To Manage Security Threats Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
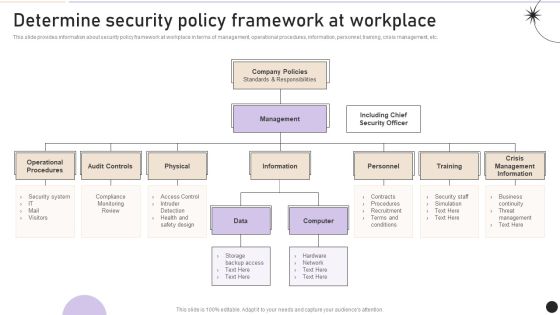
Determine Security Policy Framework At Workplace Pictures PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Get a simple yet stunning designed Determine Security Policy Framework At Workplace Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Security Policy Framework At Workplace Pictures PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Incident Management Checklist Before An Incident Icons PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cyber Security Incident Management Checklist Before An Incident Icons PDF from Slidegeeks and deliver a wonderful presentation.

Cyber Security Risk Impact And Probability Assessment Inspiration PDF
This slide defines the risk impact and likelihood assessment in cyber security. It includes information related to creating awareness in top management regarding technical, commercial, and branding damages deriving from suffering a cyber-attack. Showcasing this set of slides titled Cyber Security Risk Impact And Probability Assessment Inspiration PDF. The topics addressed in these templates are Business Continuity, Restoring Cost, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF
This slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward How Management Enables Effective Corporate Security Governance Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal How Management Enables Effective Corporate Security Governance Topics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
RCA Plan For System Security Breach Icons PDF
This slide shows RCA format to address every activity in proper timeline for identifying potential risks and strategies to resolve same. It include elements such as event timeline, security breach activities and action plan, etc. Showcasing this set of slides titled RCA Plan For System Security Breach Icons PDF Diagrams Wd Introduction PDF Diagrams. The topics addressed in these templates are Event Timeline, Security Breach Activities, Action Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Crisis Management Communication Plan Microsoft PDF
This slide illustrates RACI Responsible, accountable, consulted, and informed chart of the cyber security crisis management communication plan. It includes elements such as authority, name, emergency contact etc. Showcasing this set of slides titled IT Security Crisis Management Communication Plan Microsoft PDF. The topics addressed in these templates are Chief Information Officers, Chief Information Security Officers, Crisis Management Lead Assistant. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Incident Escalation Communication Plan Flowchart Structure PDF
This slide illustrates a flow chart of the cyber security incident escalation communication plan to manage an attack and minimize the impact. It includes elements such as security team, incident identifier vendor notification etc. Presenting IT Security Incident Escalation Communication Plan Flowchart Structure PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Identifier, Vendor Notification, Website Gets Crashed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF
This slide presents a cyber security and information technology communication plan flowchart to be implemented by managers to safeguard information technology assets and raise awareness regarding the plans. Major elements covered are incident identification, notifying the security team, incident assessment, etc. Presenting Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Incident Identification, Initial Incident Assessment, Continue Training Team Strengthening. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Services Security Architecture Assessment Infographics PDF
The slideshows an assessment model of CSP cloud service security. It includes identification of existing warrant, verification of certificates and reports, evidence review and additional information collection about third party warrant and certificates. Showcasing this set of slides titled Cloud Computing Services Security Architecture Assessment Infographics PDF. The topics addressed in these templates are Cloud Control Profile, Administrative Need, Safety Security Needs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
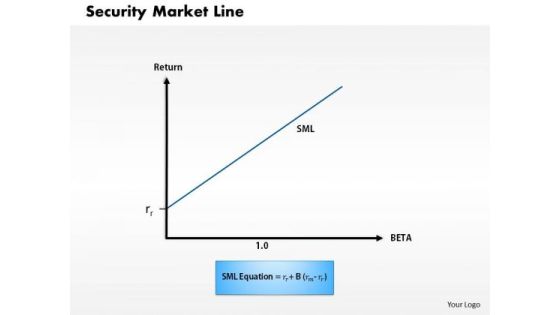
Business Framework Security Market Line 1 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

Business Framework Security Market Line 11 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.
Circle With Icons Of Law Time And Security PowerPoint Templates
This creative business PowerPoint slide is designed with icons of law time and security. Use this slide to display information in visual manner. Use this diagram in business presentations to give better impact.
Icons Of Business Goal And Global Security Powerpoint Templates
Our professionally designed business diagram is as an effective tool for communicating ideas and planning. It contains icons of business goal and global security. Design your presentation with this diagram slide. It will amplify the strength of your logic.
Vendor Application Security Testing Ppt Example Ppt Presentation
This is a vendor application security testing ppt example ppt presentation. This is a five stage process. The stages in this process are enterprise customer, vast program, third party vendor.

Income Securities Risk And Return Ppt Background Graphics
This is a income securities risk and return ppt background graphics. This is a four stage process. The stages in this process are cash, fixed interest, property, shares, risk.

Fixed Income Securities And Valuation Powerpoint Slides Design
This is a fixed income securities and valuation powerpoint slides design. This is a four stage process. The stages in this process are principal, maturity, interest rates, redemption features.

Data Security And Control Framework Sample Diagram Ppt
This is a data security and control framework sample diagram ppt. This is a four stage process. The stages in this process are define, data classification, data discovery, dissect, data intelligence, data analytics.
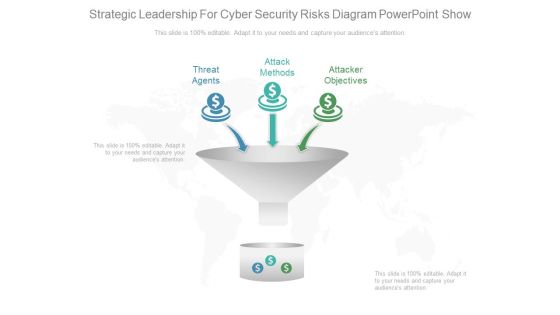
Strategic Leadership For Cyber Security Risks Diagram Powerpoint Show
This is a strategic leadership for cyber security risks diagram powerpoint show. This is a three stage process. The stages in this process are threat agents, attack methods, attacker objectives.
 Home
Home