Phishing
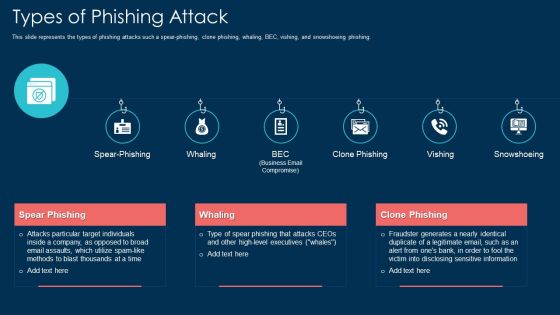
Types Of Phishing Attack Ppt Outline PDF
This slide represents the types of phishing attacks such a spear-phishing, clone phishing, whaling, BEC, vishing, and snowshoeing phishing. Presenting types of phishing attack ppt outline pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like types of phishing attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phishing Attacks Awareness Training Icon Designs PDF
Presenting Phishing Attacks Awareness Training Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness, Training Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Monthly Phishing Awareness Training Program Timeline Infographics PDF
This slide covers monthly phishing awareness training program timeline.It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Pitch your topic with ease and precision using this Monthly Phishing Awareness Training Program Timeline Infographics PDF. This layout presents information on Risk Assessments, System, Awareness Training Program Timeline. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
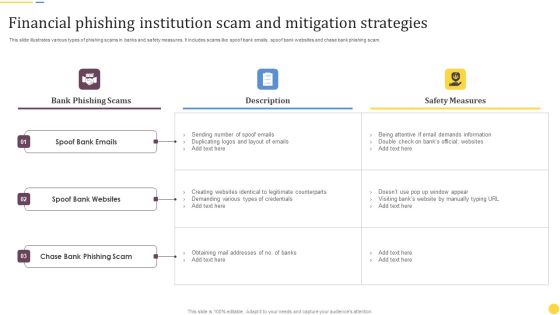
Financial Phishing Institution Scam And Mitigation Strategies Sample PDF
This slide illustrates various types of phishing scams in banks and safety measures. It includes scams like spoof bank emails, spoof bank websites and chase bank phishing scam. Showcasing this set of slides titled Financial Phishing Institution Scam And Mitigation Strategies Sample PDF. The topics addressed in these templates are Bank Phishing Scams, Spoof Bank Emails, Spoof Bank Websites. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat Icon For Financial Information Phishing Mockup PDF
Presenting Insider Threat Icon For Financial Information Phishing Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Insider Threat Icon, Financial Information Phishing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phishing Attacks Awareness Training For Employees Icon Clipart PDF
Presenting Phishing Attacks Awareness Training For Employees Icon Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness Training, Employees Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phishing Attacks Awareness Training Program Icon Demonstration PDF
Presenting Phishing Attacks Awareness Training Program Icon Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness, Training Program Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Statistics Of Cyber Phishing Scams And Attacks Designs PDF
Mentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Pitch your topic with ease and precision using this major statistics of cyber phishing scams and attacks designs pdf. This layout presents information on major statistics of cyber phishing scams and attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Techniques In Phishing Attacks Awareness Training Program Themes PDF
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Phishing Incident Management Dashboard For Attacks Awareness Training Icons PDF
This slide covers phishing incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Pitch your topic with ease and precision using this Phishing Incident Management Dashboard For Attacks Awareness Training Icons PDF. This layout presents information on Phishing Incident Management Dashboard, Attacks Awareness Training. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Types Phishing Email Ppt PowerPoint Presentation Outline Background Image Cpb
Presenting this set of slides with name types phishing email ppt powerpoint presentation outline background image cpb. This is an editable Powerpoint five stages graphic that deals with topics like types phishing email to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
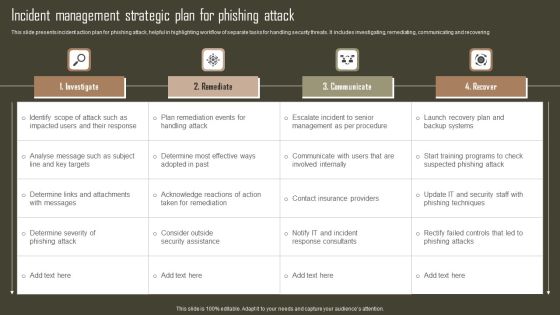
Incident Management Strategic Plan For Phishing Attack Sample PDF
This slide presents incident action plan for phishing attack, helpful in highlighting workflow of separate tasks for handling security threats. It includes investigating, remediating, communicating and recovering. Pitch your topic with ease and precision using this Incident Management Strategic Plan For Phishing Attack Sample PDF. This layout presents information on Investigate, Remediate, Communicate, Recover. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Measures To Prevent Phishing Attacks Ppt Gallery Deck PDF
This slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi factor authentication, and so on. This is a security measures to prevent phishing attacks ppt gallery deck pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, organization, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

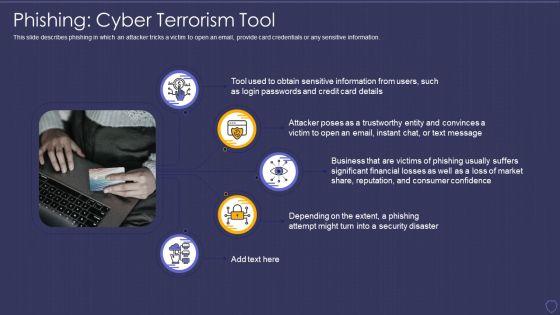
Cyber Terrorism Assault Phishing Cyber Terrorism Tool Slides PDF
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information.Presenting cyber terrorism assault phishing cyber terrorism tool slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like attacker poses, sensitive information, business that are victims In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Statistics Of Cyber Phishing Scams And Attacks Pictures PDF
Mentioned slide showcases major statistics of cyber phishing. Statistics mentioned in the slide are average daily legitimate emails, email volume change, average daily spam volume, change in spam volume percentage etc. Persuade your audience using this key statistics of cyber phishing scams and attacks pictures pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including average, email. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices For Phishing Attacks Awareness Training Topics PDF
This slide covers best practices for phishing awareness training plan for successful implementation. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Phishing Attacks Awareness Training Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Establishing Basics, Including Everyone. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Analysis For Phishing Attacks Awareness Training Tools Rules PDF
This slide covers comparative analysis for phishing awareness training tools for effective decision making. It involves features such simulate top cyber attacks, assess employees, monitor and analyse results and measurable impact. Showcasing this set of slides titled Comparative Analysis For Phishing Attacks Awareness Training Tools Rules PDF. The topics addressed in these templates are Analyse Results, Measurable Impact, Living Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Effective Methods Of Phishing Attacks Awareness Training Slides PDF
This slide covers key ways to conduct effective phishing training for employees for overall development. It involves interactive video learning, PowerPoint presentations, quizzes and chunk lessons. Persuade your audience using this Effective Methods Of Phishing Attacks Awareness Training Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Interactive Video Learning, Powerpoint Presentations, Quizzes. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Steps To Conduct Phishing Attacks Awareness Training Template PDF
This slide covers key steps to conduct effective phishing awareness training plan. It involves five steps such as analyse training need, plan, deploy,measure training and optimize results. Persuade your audience using this Key Steps To Conduct Phishing Attacks Awareness Training Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Analyze, Plan, Deploy, Measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Phishing Attacks Awareness Training Program Plan Inspiration PDF
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Phishing Attacks Awareness Training Program Process Brochure PDF
This slide covers phishing awareness training program and development procedure to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Presenting Phishing Attacks Awareness Training Program Process Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Training Need, Evaluate Training Program, Identify Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
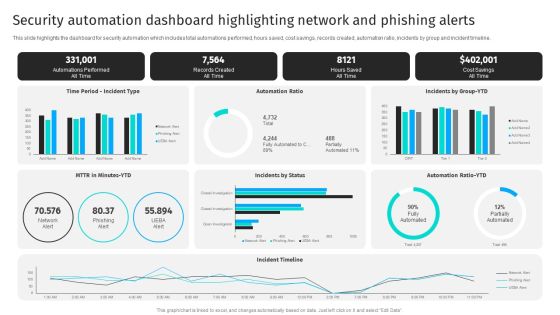
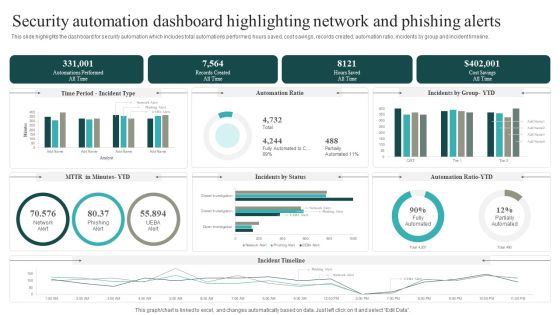
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF
Persuade Your Audience Using This Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF. This PPT Design Covers Five Stages, Thus Making It A Great Tool To Use. It Also Caters To A Variety Of Topics Including Updating Security Software, Backing Up Data, Block Unreliable Websites. Download This PPT Design Now To Present A Convincing Pitch That Not Only Emphasizes The Topic But Also Showcases Your Presentation Skills.

Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Welcome to our selection of the Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. This modern and well arranged Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Phishing Attacks Awareness Training Ppt PowerPoint Presentation Complete With Slides
Share a great deal of information on the topic by deploying this Phishing Attacks Awareness Training Ppt PowerPoint Presentation Complete With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of seventeen slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Global Cyber Terrorism Incidents On The Rise IT Phishing Techniques Misused For Cyber Assault Ideas PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Presenting global cyber terrorism incidents on the rise it phishing techniques misused for cyber assault ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like spear phishing, smishing and vishing, whaling, email phishing scams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Phishing Techniques Misused For Cyber Assault Slides PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. This is a cyber terrorism assault phishing techniques misused for cyber assault slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like smishing and vishing, spear phishing, contact information through You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
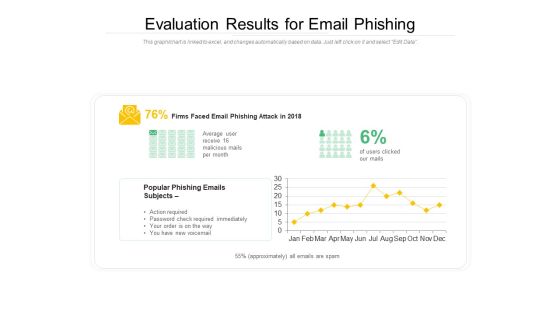
Evaluation Results For Email Phishing Ppt PowerPoint Presentation Gallery Format PDF
Showcasing this set of slides titled evaluation results for email phishing ppt powerpoint presentation gallery format pdf. The topics addressed in these templates are evaluation results for email phishing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Phishing Scams And Attacks Icon To Steal Confidential Data Elements PDF
Showcasing this set of slides titled cyber phishing scams and attacks icon to steal confidential data elements pdf. The topics addressed in these templates are cyber phishing scams and attacks icon to steal confidential data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icon Of Hacker Launching Cyber Phishing Scams And Attacks Background PDF
Presenting icon of hacker launching cyber phishing scams and attacks background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including icon of hacker launching cyber phishing scams and attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Global Cyber Terrorism Incidents On The Rise IT Phishing Cyber Terrorism Tool Rules PDF
This slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Presenting global cyber terrorism incidents on the rise it phishing cyber terrorism tool rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like phishing cyber terrorism tool. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Assessment Of Anti Phishing Software To Prevent Cyber Scams And Attacks Structure PDF
Mentioned slide showcases comparison of various softwares which can be used to prevent cyber phishing attacks. The key features of softwares are spam filters, customizable filtering, malicious file integration, integration, report attacks etc. Showcasing this set of slides titled comparative assessment of anti phishing software to prevent cyber scams and attacks structure pdf. The topics addressed in these templates are comparative assessment of anti phishing software to prevent cyber scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Phishing Scams And Attacks Dashboard With Improvement Curve Sample PDF
Mentioned slide showcases a comprehensive dashboard used to measure the cyber phishing attacks. Information covered in this slide is related to organization health risk, attack vendors, most vulnerable employees to attacks, improvement curve. Pitch your topic with ease and precision using this cyber phishing scams and attacks dashboard with improvement curve sample pdf. This layout presents information on cyber phishing scams and attacks dashboard with improvement curve. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Kpis To Measure Phishing Scams And Attacks Topics PDF
Mentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Showcasing this set of slides titled cyber security kpis to measure phishing scams and attacks topics pdf. The topics addressed in these templates are cyber security kpis to measure phishing scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Cyber Phishing Scams And Attacks With Key Strategies Slides PDF
Mentioned slide showcases various cyber phishing attacks such as deceptive, spear, whaling and vishing. It provides detailed information about likelihood of attack, examples of attacks and strategies which can be implemented to overcome phishing attacks. Showcasing this set of slides titled major cyber phishing scams and attacks with key strategies slides pdf. The topics addressed in these templates are target, information, email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phishing Scams And Attacks Assessment And Cyber Security Training Inspiration PDF
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Internet Threats For Credit Card Phishing Ppt PowerPoint Presentation File Layouts PDF
Persuade your audience using this internet threats for credit card phishing ppt powerpoint presentation file layouts pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including internet threats for credit card phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

7 Step Model Of Spear Phishing Scams And Attacks Designs PDF
Mentioned slide showcases multistep model of cyber phishing attack. The model include points such as attacker sends the email, user opens the email, target system exploitation, installation of RAT etc. Persuade your audience using this 7 step model of spear phishing scams and attacks designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including internal network, compromised system, targeted users. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Dashboard To Assess Phishing Attacks Awareness Training Program Efficiency Professional PDF
This slide covers KPI dashboard to assess phishing awareness training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Showcasing this set of slides titled Dashboard To Assess Phishing Attacks Awareness Training Program Efficiency Professional PDF. The topics addressed in these templates are Applicability, Employee Satisfaction, Mitigation Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Employee Questionnaire To Assess Phishing Attacks Awareness Training Effectiveness Formats PDF
This slide covers employee questionnaire to assess phishing training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess Phishing Attacks Awareness Training Effectiveness Formats PDF. The topics addressed in these templates are Organization, Equipment, Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Why Phishing Attacks Awareness Training Is Essential For Employees Clipart PDF
This slide covers need of phishing awareness training within organization. It involves reasons such as increases employee awareness, assures educated staff, enhances organizational reputation and boosts confidence. Presenting Why Phishing Attacks Awareness Training Is Essential For Employees Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assures Staff Education, Enhances Organizational Reputation, Boosts Confidence. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Analysis Of Phishing And Simulation Training Program Tools Professional PDF
This slide covers comparative analysis of phishing and simulation training tools. It involves features such simulate top cyber attacks, assess employees, monitor and analyse results and measurable impact. Showcasing this set of slides titled Comparative Analysis Of Phishing And Simulation Training Program Tools Professional PDF. The topics addressed in these templates are Assess Employees, Price, User Rating. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

White Hat Hacking What Is Phishing Attack Ppt Outline Design Inspiration PDF
This is a white hat hacking what is phishing attack ppt outline design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, purchasing, required, source. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Phishing Scams And Attacks Ppt PowerPoint Presentation Complete With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cyber phishing scams and attacks ppt powerpoint presentation complete with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the fourteen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Table Of Content Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Elements PDF
Deliver an awe inspiring pitch with this creative table of content cyber security and phishing awareness training hacking prevention awareness training for it security elements pdf bundle. Topics like training, awareness, strategies, communication, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Cyber Security And Phishing Awareness Training Hacking Prevention Awareness Training For IT Security Sample PDF
Presenting agenda for cyber security and phishing awareness training hacking prevention awareness training for it security sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like safeguard, integrity, cybersecurity, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Crime Security PowerPoint Template 0810
An open door with hands holding guns surrounded by words like cyber-crime stolen identity virus phishing and security

Managing IT Security IT 30 Days Plan Ppt Gallery Graphics Download PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing it security it 30 days plan ppt gallery graphics download pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
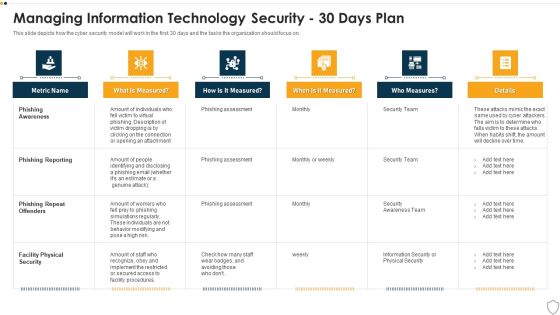
IT Security Managing Information Technology Security 30 Days Plan Themes PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF
Deliver an awe inspiring pitch with this creative Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF bundle. Topics like Attacked Phishing, Employees Will, Phishing During can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
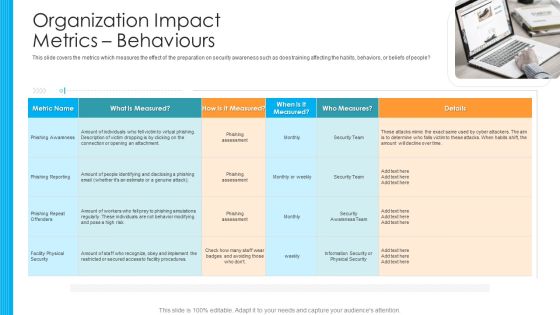
Organization Impact Metrics Behaviours Hacking Prevention Awareness Training For IT Security Designs PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. This is a organization impact metrics behaviours hacking prevention awareness training for it security designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like phishing awareness, phishing reporting, phishing repeat offenders, facility physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
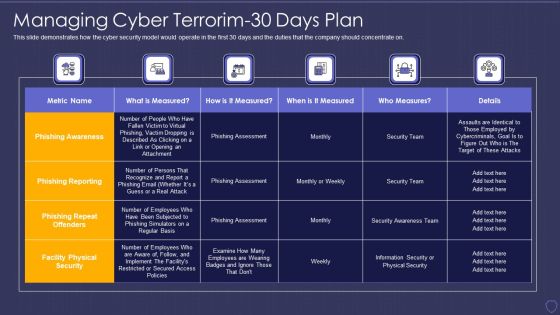
Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorim 30 Days Plan Information PDF
This slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it managing cyber terrorim 30 days plan information pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Unified Threat Management Concept Template Presentation Visuals
This is a unified threat management concept template presentation visuals. This is a six stage process. The stages in this process are vpn, content filtering, intrusion protection, spam protection, phishing protection, spyware protection.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Icons PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach icons pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
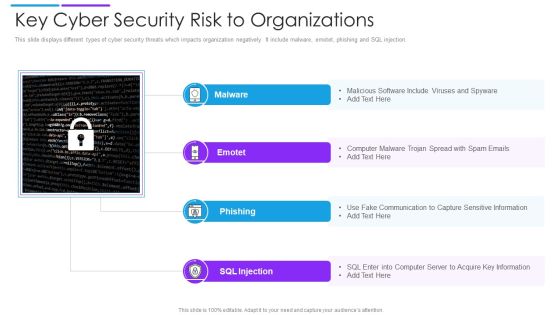
Key Cyber Security Risk To Organizations Structure PDF
This slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Presenting key cyber security risk to organizations structure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware, phishing, sql injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Terrorism Assault Managing Cyber Terrorism 30 Days Plan Infographics PDF
This slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on.Deliver an awe inspiring pitch with this creative cyber terrorism assault managing cyber terrorism 30 days plan infographics pdf bundle. Topics like facility physical security, phishing repeat offenders, phishing reporting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
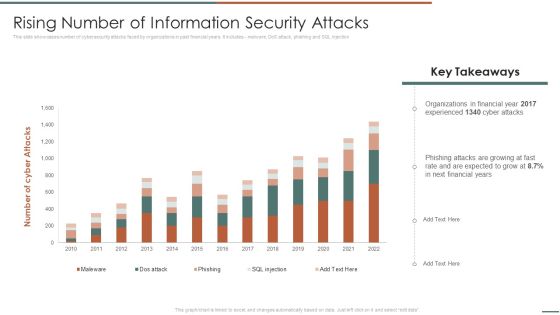
Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF. Use them to share invaluable insights on Organizations In Financial, Experienced, Phishing Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organization Impact Metrics Behaviours Structure PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people This is a organization impact metrics behaviours structure pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like phishing reporting, phishing repeat offenders. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
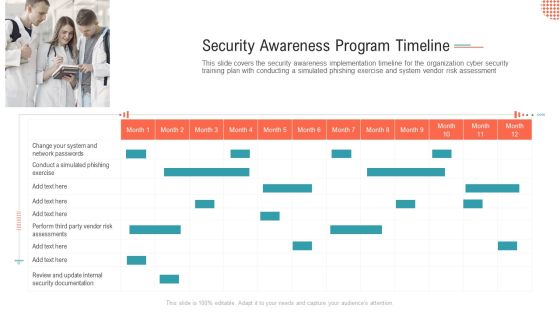
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
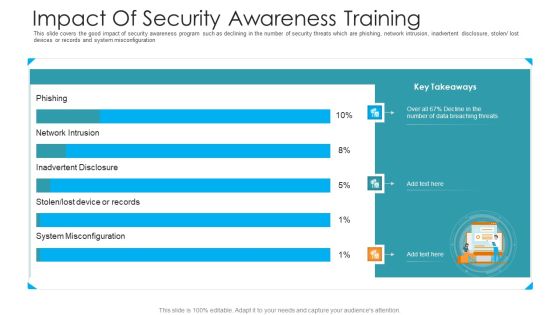
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Facilities Offered By Successful Implementation Guidelines PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a information and technology security operations facilities offered by successful implementation guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Companys Data Safety Recognition Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative companys data safety recognition security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Facilities Offered By Successful Implementation Clipart PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a organizational security solutions facilities offered by successful implementation clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilities Offered By Successful Implementation Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a facilities offered by successful implementation formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Enhanced Protection Corporate Event Administration Facilities Offered By Successful Implementation Background PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a enhanced protection corporate event administration facilities offered by successful implementation background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Facilities Offered By Successful Implementation Sample PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a security and process integration facilities offered by successful implementation sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Evolving BI Infrastructure Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting evolving bi infrastructure facilities offered by implementation of security centre formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Project Security Administration IT Facilities Rendered By Security Centre Implementation Clipart PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting project security administration it facilities rendered by security centre implementation clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Facilities Rendered By Security Centre Implementation Sample PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting upgrading total project safety it facilities rendered by security centre implementation sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
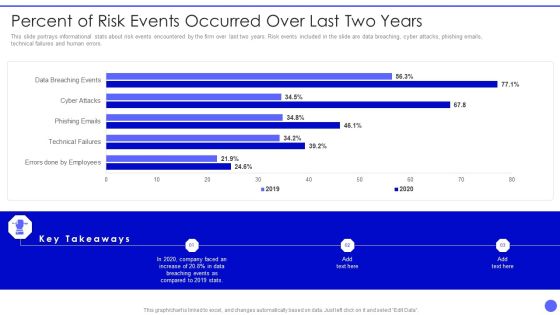
Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Percent Of Risk Events Occurred Over Last Two Years Clipart PDF bundle. Topics like Errors Done By Employees, Technical Failures, Phishing Emails, Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Investigations by HR, Phishing Detection And Prevention, Risk Mitigation of Left Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
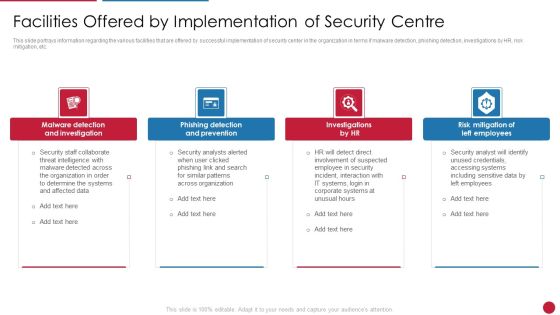
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Detection And Investigation, Phishing Detection, Left Employees In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
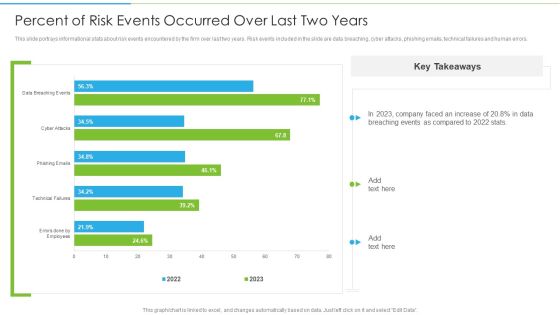
Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF. Use them to share invaluable insights on Technical Failures, Phishing Emails, Cyber Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
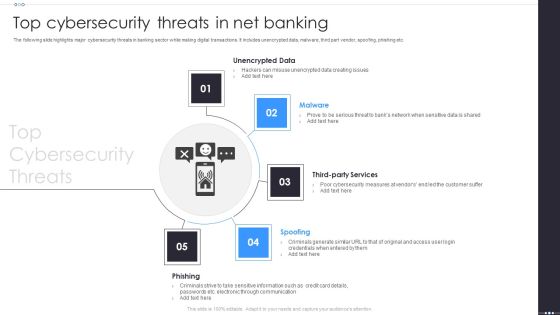
Top Cybersecurity Threats In Net Banking Download PDF
The following slide highlights major cybersecurity threats in banking sector while making digital transactions. It includes unencrypted data, malware, third part vendor, spoofing, phishing etc. Persuade your audience using this Top Cybersecurity Threats In Net Banking Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Unencrypted Data, Spoofing, Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
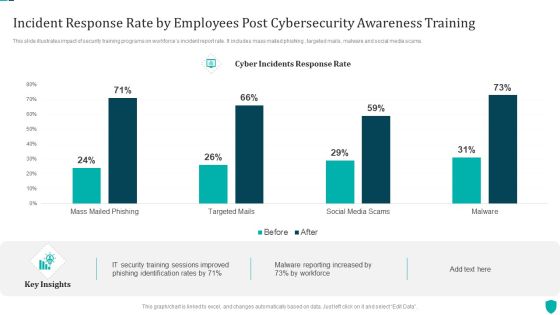
Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF
This slide illustrates impact of security training programs on workforces incident report rate. It includes mass mailed phishing , targeted mails, malware and social media scams.Pitch your topic with ease and precision using this Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF. This layout presents information on Training Sessions, Phishing Identification, Malware Reporting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This is a Security Awareness Packages Offered By Third Party Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unlimited Phishing, Automated Awareness, Industry Benchmarking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF bundle. Topics like Technical Failures, Phishing Emails, Data Breaching can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organization Security Issues And Solution Assessment Ideas PDF
This slide showcases problems in firm related to security of crucial data important for organization. The issues include data breach, SPAM, phishing and insider threat. Persuade your audience using this Organization Security Issues And Solution Assessment Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breach, SPAM And Phishing, Insider Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF
This slide covers monthly cybersecurity awareness training program timeline. It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Showcasing this set of slides titled Monthly IT Security Awareness Training Program Timeline Ppt Model Demonstration PDF. The topics addressed in these templates are Authentication And Passwords, Conduct Phishing Exercise, Remote Access Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF
The following slide represents the common types of cyber threats. It includes malware, phishing, password attacks, drive by downloads, man in the middle and denial of service attacks. Persuade your audience using this Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Malware Through, Phishing Through, Password Attacks Through. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

ML Business Applications In Cybersecurity Business Information PDF
This slide represents machine learning use cases which industries utilize to combat cybersecurity threats, analyze vulnerabilities and provide protection against attacks. Use cases included in this slide are malware detection, software vulnerabilities, phishing attacks, etc. Presenting ML Business Applications In Cybersecurity Business Information PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Network Logs Analysis, Phishing Attacks, Malware Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
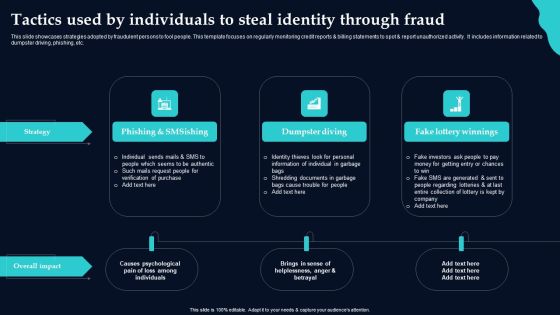
Tactics Used By Individuals To Steal Identity Through Fraud Introduction PDF
This slide showcases strategies adopted by fraudulent persons to fool people. This template focuses on regularly monitoring credit reports and billing statements to spot and report unauthorized activity. It includes information related to dumpster driving, phishing, etc. Presenting Tactics Used By Individuals To Steal Identity Through Fraud Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Smsishing, Dumpster Diving, Fake Lottery Winnings. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
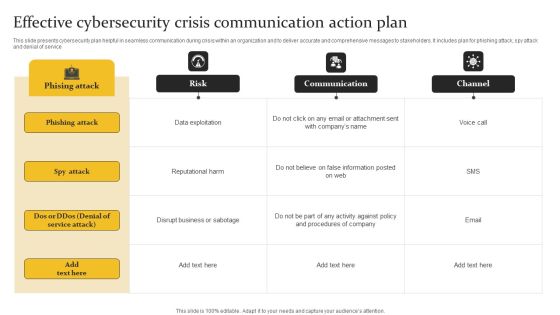
Effective Cybersecurity Crisis Communication Action Plan Graphics PDF
This slide presents cybersecurity plan helpful in seamless communication during crisis within an organization and to deliver accurate and comprehensive messages to stakeholders. It includes plan for phishing attack, spy attack and denial of service. Pitch your topic with ease and precision using this Effective Cybersecurity Crisis Communication Action Plan Graphics PDF. This layout presents information on Phishing Attack, Data Exploitation, Reputational Harm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
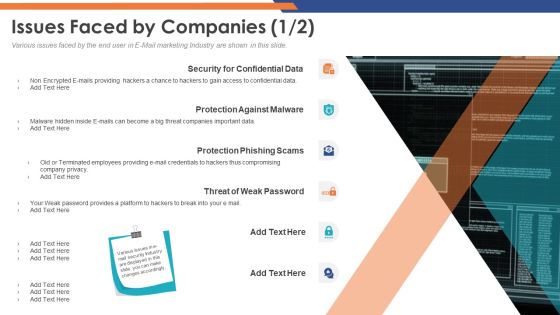
Email Security Market Research Report Issues Faced By Companies Professional PDF
Presenting this set of slides with name email security market research report issues faced by companies professional pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Issues Faced By Companies Services Portrait PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies services portrait pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
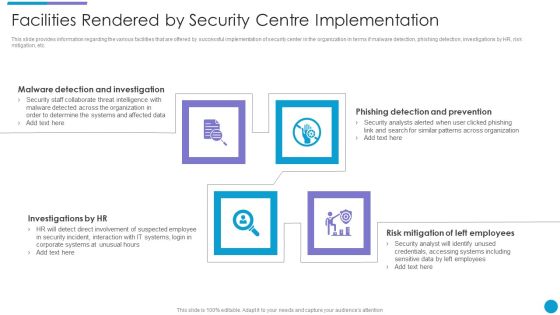
Major Techniques For Project Safety IT Facilities Rendered By Security Centre Implementation Designs PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a major techniques for project safety it facilities rendered by security centre implementation designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, investigations by hr, phishing detection and prevention, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a developing firm security strategy plan facilities offered by implementation of security centre formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Email Security Market Research Report Key Stats Department Topics PDF
Presenting this set of slides with name email security market research report key stats department topics pdf. This is a five stage process. The stages in this process are 95 percent of malware are delivered via e mails, 79 percent of it companies consider phishing most challenging issue. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Security Awareness Training Ppt Pictures Design Templates PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt pictures design templates pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Awareness Tracking Kpis Ppt Layouts Graphics Template PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction.Deliver an awe-inspiring pitch with this creative security awareness tracking kpis ppt layouts graphics template pdf. bundle. Topics like phishing informants, social engineering, refresher training scores can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Staff Learning Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
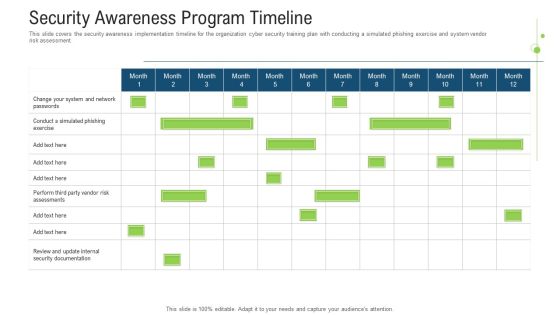
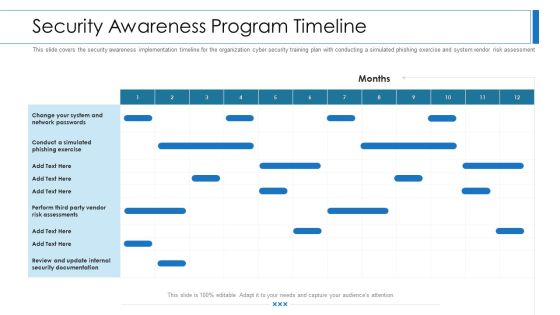
Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
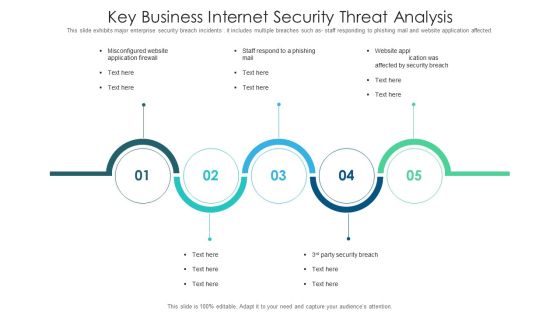
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
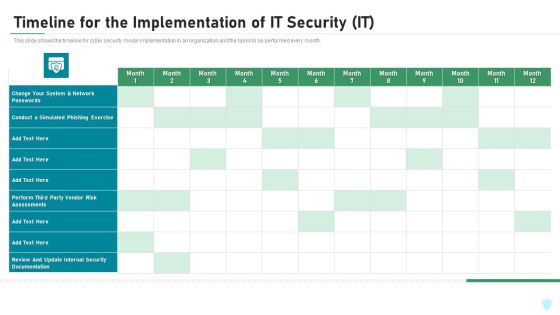
Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
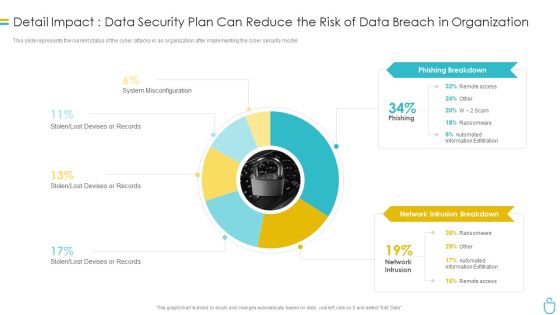
Information Security Detail Impact Data Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Slides Influencers PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this information security detail impact data security plan can reduce the risk of data breach in organization ppt slides influencers pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
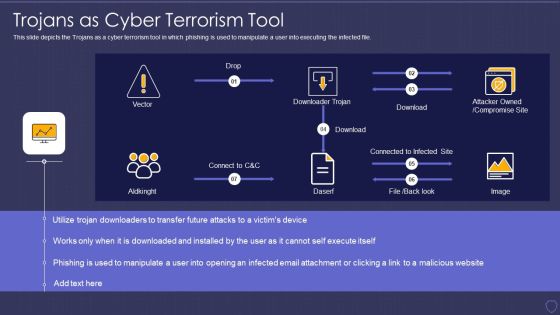
Global Cyber Terrorism Incidents On The Rise IT Trojans As Cyber Terrorism Tool Graphics PDF
This slide depicts the Trojans as a cyber terrorism tool in which phishing is used to manipulate a user into executing the infected file. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it trojans as cyber terrorism tool graphics pdf bundle. Topics like trojans as cyber terrorism tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Terrorism Assault Trojans As Cyber Terrorism Tool Brochure PDF
This slide depicts the Trojans as a cyber terrorism attacks tool in which phishing is used to manipulate a user into executing the infected file.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault trojans as cyber terrorism tool brochure pdf Use them to share invaluable insights on trojans as cyber terrorism tool and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF. Use them to share invaluable insights on Risk Encountered, Affected Asset, Phishing Emails and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Events Reporting And Likelihood Topics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Events Reporting And Likelihood Topics PDF bundle. Topics like Risk Encountered, Phishing Emails, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF bundle. Topics like Phishing Attacks, Cross Attack, Security Vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home