Password Security

KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Actual Time Transaction Monitoring Software And Strategies Key Members Of Financial Security Department Diagrams PDF
The following slide highlights key members of financial security department. It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Actual Time Transaction Monitoring Software And Strategies Key Members Of Financial Security Department Diagrams PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Find highly impressive Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. This modern and well arranged Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. Increase malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cybersecurity Awareness Program To Prevent Attacks Cyber Security Awareness Trends Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring The Impact Of Security Awareness Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Slidegeeks has constructed Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

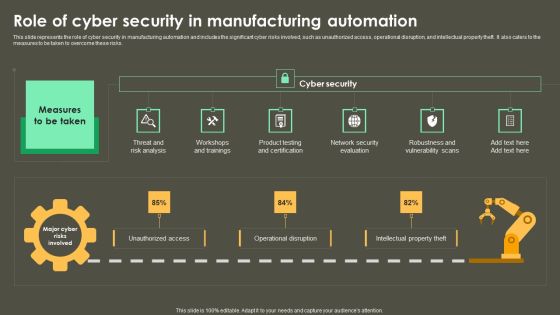
Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well arranged Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Welcome to our selection of the Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF
This slide highlights schedule for training team to handle cyber security incidents in the company. The purpose of this template is to provide an overview on training program conducted by the company. It includes elements such as training topics covered, requirements along with duration of videos and certification post training. Persuade your audience using this Training Plan For Cyber Security Cases Action Plan Response Team Ppt PowerPoint Presentation Gallery Format PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Training Learnings, Training Requirements, Training Details. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Present like a pro with Impact Of Cyber Security Breach General Consequences Ppt Styles Icon PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Present like a pro with Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Slidegeeks is here to make your presentations a breeze with Strategies We Will Implement To Make Security Awareness Training Interactive Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF.

Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.

Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF
This slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business owned devices, and installation maintenance of operating systems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Execution Of ICT Strategic Plan Best Practices For Effective Endpoint Security Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
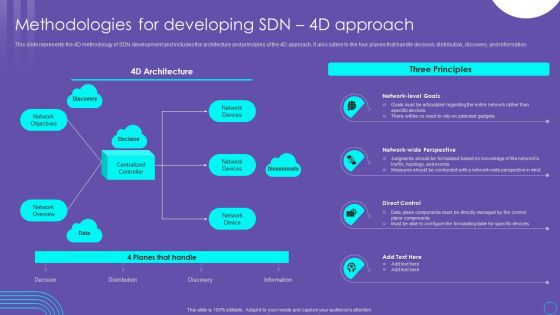
SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF
This slide represents the 4D methodology of SDN development and includes the architecture and principles of the 4D approach. It also caters to the four planes that handle decision, distribution, discovery, and information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF.

Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
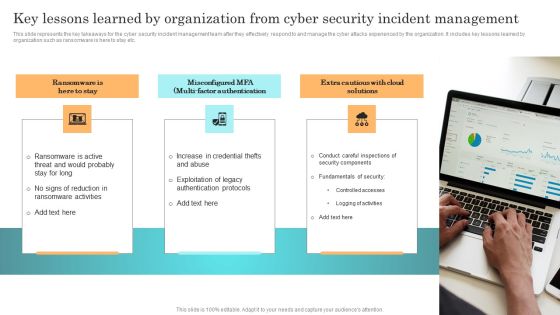
Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
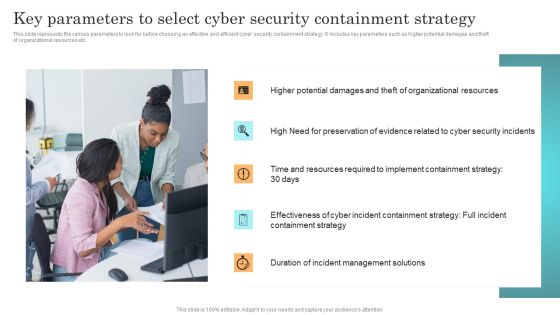
Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Present like a pro with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Incident Response Techniques Deployement Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. This Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
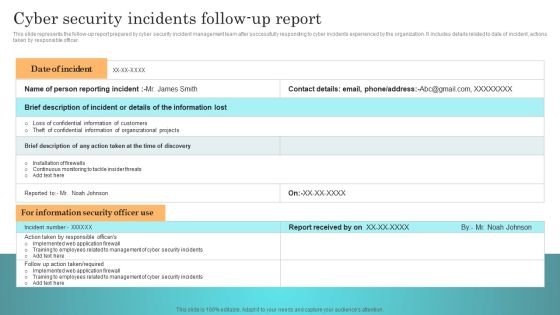
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.

Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
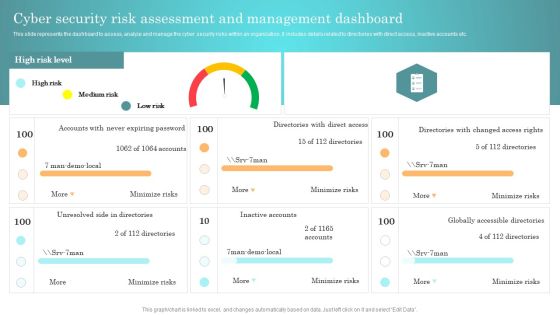
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
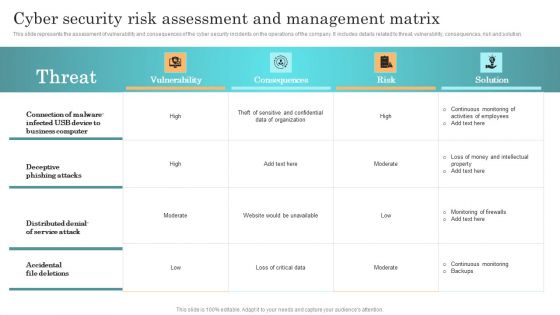
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
The following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
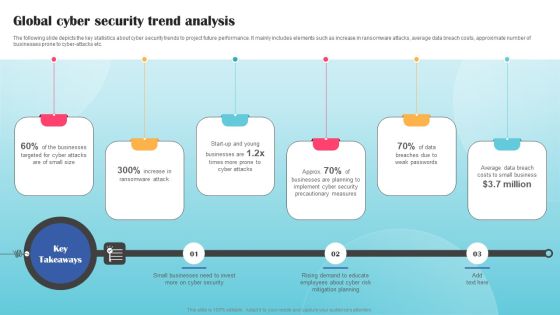
Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. The Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF
The following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Take your projects to the next level with our ultimate collection of Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Retrieve professionally designed Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
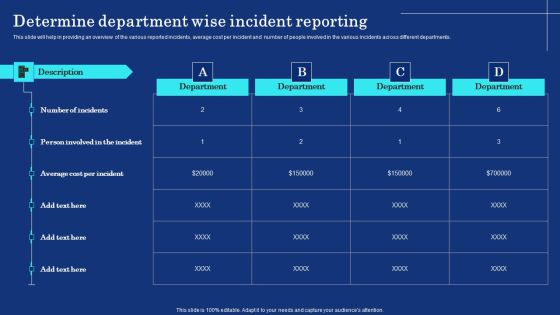
Organizational Assets Security Management Strategy Determine Department Wise Incident Reporting Guidelines PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizational Assets Security Management Strategy Determine Department Wise Incident Reporting Guidelines PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizational Assets Security Management Strategy Determine Department Wise Incident Reporting Guidelines PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF
This slide covers information regarding how firm can handle financial crisis by safeguarding financial stability in terms of abundant cash requirements, overhead analysis, currency hedging, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizational Assets Security Management Strategy How To Handle Financial Crisis At Workplace Formats PDF today and make your presentation stand out from the rest.
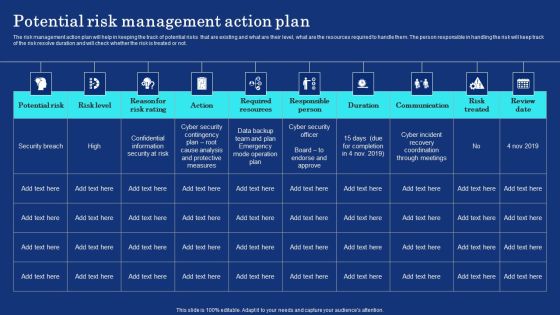
Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF can be your best option for delivering a presentation. Represent everything in detail using Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF.

Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides
Using this ready-made PowerPoint slide, you can incorporate your own data to make an impact with your business innovation and clarity of goals. Use this brilliantly designed Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides to showcase how ultimately all business concepts are related. This presentation template can also be used to record resource allocation in a visual form. The twenty one Slide Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides is suitable for all your business needs, where you need to make sure that all bases are covered. Download this PPT template now to start a journey on your chosen business, with customer satisfaction the key aim.
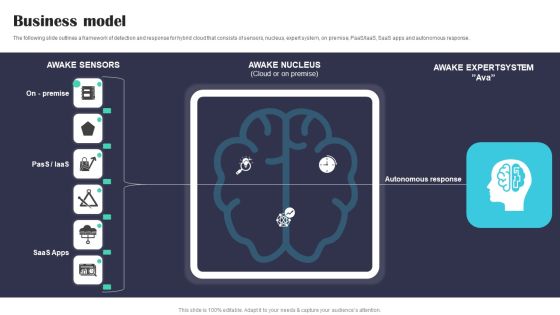
Security Software Company Investor Funding Pitch Deck Business Model Structure PDF
The following slide outlines a framework of detection and response for hybrid cloud that consists of sensors, nucleus, expert system, on premise, PaaS or IaaS, SaaS apps and autonomous response. Create an editable Security Software Company Investor Funding Pitch Deck Business Model Structure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Security Software Company Investor Funding Pitch Deck Business Model Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF
The following slide showcases key personnel of executive team of IT company which are CEO, chief architect, VP marketing, sales, product, engineering, chief data scientist, chief scientist, etc. Get a simple yet stunning designed Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF today and make your presentation stand out from the rest.

Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF
This slide showcases the organization structure of an IT company which includes CEO, chief architect, VP marketing, VP sales, chief data scientist, chief scientist, VP product, VP engineering, founding BOD, former board member, founder, former CEO. Find highly impressive Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF
This slide showcases areas where the funds that are collected in series C funding round will be allocated like- marketing, sales and research and development. If you are looking for a format to display your unique thoughts, then the professionally designed Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Software Company Investor Funding Pitch Deck Allocation Of Funds Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF
This slide showcases forecasted growth of company that will assist investors to determine future potential of business and make investment decision that will be amost profitable for them. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present like a pro with Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Create an editable CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Present like a pro with Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well-arranged Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This modern and well arranged Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF
This slide describes the different methods used by blockchain technology to prevent data from fraud and stealing. The purpose of this slide is to showcase the various techniques and technologies used in blockchain technology to prevent fraud and data theft. Get a simple yet stunning designed Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF
This slide highlights the main phases of blockchain penetration testing. The purpose of this slide is to showcase the different stages of penetration testing, including information gathering and threat modeling, testing and discovery, and exploitation. Find highly impressive Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Developing Firm Security Strategy Plan Contingency Plan For Threat Handling At Workplace Summary PDF
This slide portrays information contingency plan for handling threats at workplace with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative developing firm security strategy plan contingency plan for threat handling at workplace summary pdf bundle. Topics like server, website, local area network, wide area network, mainframe systems, distributes systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF. Use them to share invaluable insights on Demographics, Social Networks, Sessions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

3d Locked Notebook Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Use our Shapes PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Use our Business PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Present our Computer PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Vector Notebook Lockable pattern, shapes, technology, business, computer, signs. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. You can be sure our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. Professionals tell us our Lockable PowerPoint templates and PPT Slides are designed to make your presentations professional. Customers tell us our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113 will get their audience's attention. Presenters tell us our pattern PowerPoint templates and PPT Slides will make the presenter successul in his career/life. We assure you our 3d Locked Notebook Security PowerPoint Templates PPT Backgrounds For Slides 0113 are incredible easy to use. Presenters tell us our pattern PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home.
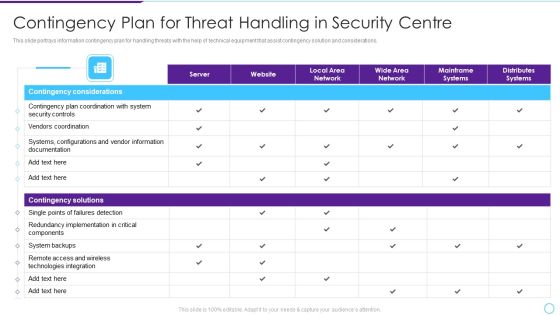
Intelligent Infrastructure Contingency Plan For Threat Handling In Security Centre Mockup PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Contingency Plan For Threat Handling In Security Centre Mockup PDF bundle. Topics like Contingency Considerations, Contingency Solutions, Server, Local Area Network, Local Area Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Damage Security Insurance Proposal Insurance Claim Procedure For Liability Insurance Proposal Ppt Infographic Template Summary PDF
This is a damage security insurance proposal insurance claim procedure for liability insurance proposal ppt infographic template summary pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cashless claim process, reimbursement claim process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Monitoring Plan Professional PDF
Presenting way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan professional pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like monitoring all systems, monitoring network traffic, monitoring user activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
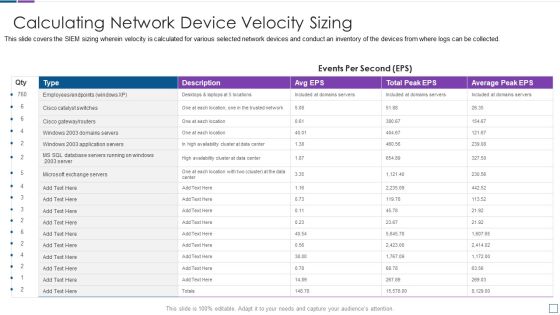
Real Time Assessment Of Security Threats Calculating Network Device Velocity Sizing Portrait PDF
This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Deliver an awe inspiring pitch with this creative real time assessment of security threats calculating network device velocity sizing portrait pdf bundle. Topics like calculating network device velocity sizing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Three Seps Of Enterprise Network Security With Icons Ppt PowerPoint Presentation Icon Slide Portrait PDF
Presenting three seps of enterprise network security with icons ppt powerpoint presentation icon slide portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, scope contain remediate, detect block defend. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Levels Vertical Layout For Network Security Phases Ppt PowerPoint Presentation Portfolio Background Designs PDF
Persuade your audience using this three levels vertical layout for network security phases ppt powerpoint presentation portfolio background designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IPO Process Layout For Network Security Issues Ppt PowerPoint Presentation Outline Graphics Template PDF
Persuade your audience using this ipo process layout for network security issues ppt powerpoint presentation outline graphics template pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including processing, output, input. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Three Phases Of Network Security In Pie Chart Ppt PowerPoint Presentation Gallery Graphics Download PDF
Pitch your topic with ease and precision using this three phases of network security in pie chart ppt powerpoint presentation gallery graphics download pdf. This layout presents information on discover enforce harden, detect block defend, scope contain remediate. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
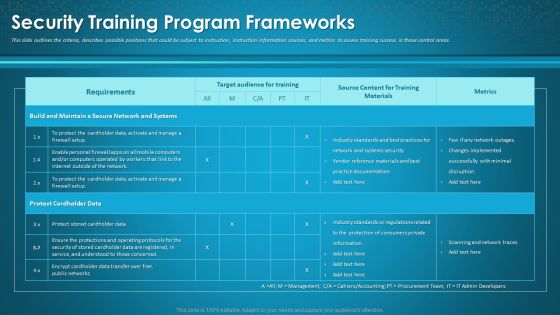
Organizational Network Awareness Staff Learning Security Training Program Frameworks Sample PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this organizational network awareness staff learning security training program frameworks sample pdf. Use them to share invaluable insights on target audience for training, source content, metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Network Staff Learning Employee Security Awareness Training Budget Information PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver and pitch your topic in the best possible manner with this organizational network staff learning employee security awareness training budget information pdf. Use them to share invaluable insights on capability level, budget, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Damage Security Insurance Proposal Our Offerings For Liability Insurance Proposal Ppt Show Ideas PDF
Presenting damage security insurance proposal our offerings for liability insurance proposal ppt show ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, assets, liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Cover Letter For Liability Insurance Proposal Ppt Slides Graphic Tips PDF
Presenting damage security insurance proposal cover letter for liability insurance proposal ppt slides graphic tips pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cover letter. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Insurance Outline For Liability Insurance Proposal Ppt Visual Aids Show PDF
This is a damage security insurance proposal insurance outline for liability insurance proposal ppt visual aids show pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like opportunity, legally, liability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Damage Security Insurance Proposal Next Step For Liability Insurance Proposal Ppt Summary Outline PDF
Presenting damage security insurance proposal next step for liability insurance proposal ppt summary outline pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like next step. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Our Major Clients For Liability Insurance Proposal Ppt Inspiration Backgrounds PDF
Presenting damage security insurance proposal our major clients for liability insurance proposal ppt inspiration backgrounds pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like major clients liability insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Project Context For Liability Insurance Proposal Ppt File Examples PDF
This is a damage security insurance proposal project context for liability insurance proposal ppt file examples pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like liability, human resource, insurance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Training And Building Role Competencies Infographics PDF
This is a security management plan steps in detail training and building role competencies infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsible for conducting, responsible for managing, project management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF
Find a pre designed and impeccable Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Damage Security Insurance Proposal 30 60 90 Days Plan Ppt Pictures PDF
This is a damage security insurance proposal 30 60 90 days plan ppt pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Damage Security Insurance Proposal Table Of Content Ppt Styles Graphics Example PDF
Presenting damage security insurance proposal table of content ppt styles graphics example pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like prices, insurance, offerings, client testimonials, major clients. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Terms And Conditions Ppt Pictures Visual Aids PDF
This is a damage security insurance proposal terms and conditions ppt pictures visual aids pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insurance reimbursement, cancelation of insurance, terms of payment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF
The slide provides a list of companys clients in different sectors manufacturing, construction, financials services, energy. Mining, automobile etc. Along with the service which the company offers to specific client.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF bundle. Topics like Financials Services, Assets Management, Underwriting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ensuring Food Safety Practices To Prevent Contamination Food Security Excellence Ppt Outline Styles PDF
This slide provides information regarding food safety practices and checklist implemented by firm in order to prevent food contamination. Deliver an awe inspiring pitch with this creative ensuring food safety practices to prevent contamination food security excellence ppt outline styles pdf bundle. Topics like ensuring food safety practices to prevent contamination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
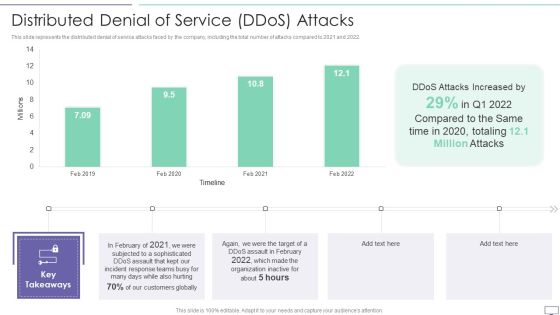
IT Security Hacker Distributed Denial Of Service Ddos Attacks Template PDF
This slide represents the distributed denial of service attacks faced by the company, including the total number of attacks compared to 2021 and 2022.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Distributed Denial Of Service Ddos Attacks Template PDF. Use them to share invaluable insights on Attacks Increased, Incident Response, Customers Globally and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Security Financial Services Ppt PowerPoint Presentation Styles Design Templates Cpb Pdf
Presenting this set of slides with name data security financial services ppt powerpoint presentation styles design templates cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like data metrics inside application to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Software Testing Service Differentiators With Digital Security Management Ppt PowerPoint Presentation File Graphics Download PDF
Persuade your audience using this software testing service differentiators with digital security management ppt powerpoint presentation file graphics download pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including attractive design, enterprise solutions, software testing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Based Email Security Market Report Issues Faced By Companies Services Ppt Pictures Slide Portrait PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Deliver an awe inspiring pitch with this creative cloud based email security market report issues faced by companies services ppt pictures slide portrait pdf bundle. Topics like issues faced by companies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Management Services And Action Plan 4 Dimensions Of Infrastructure Security Rules PDF
Presenting construction management services and action plan 4 dimensions of infrastructure security rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
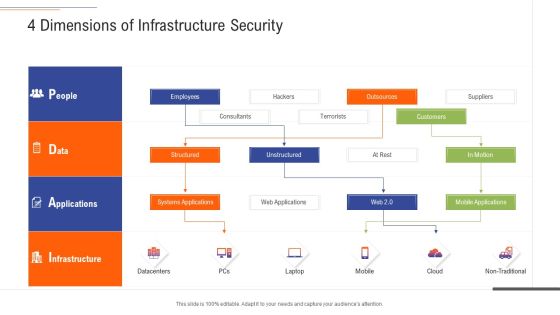
Support Services Management 4 Dimensions Of Infrastructure Security Ppt Slides Ideas PDF
This is a support services management 4 dimensions of infrastructure security ppt slides ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Log Management Services Metrics Slides PDF
This is a real time assessment of security threats log management services metrics slides pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configurations, log management, metrics, virtualization, databases. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Food Safety Records Maintenance Food Security Excellence Ppt Portfolio Layout PDF
This slide provides information regarding food safety records maintenance such as vendor certification records, employee training records. etc. Deliver and pitch your topic in the best possible manner with this addressing food safety records maintenance food security excellence ppt portfolio layout pdf. Use them to share invaluable insights on maintenance, sanitation, monitoring, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
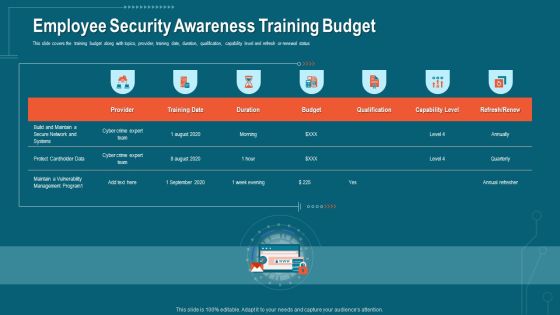
Companys Data Safety Recognition Employee Security Awareness Training Budget Formats PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative companys data safety recognition employee security awareness training budget formats pdf bundle. Topics like budget, capability level, training date, duration, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Companys Data Safety Recognition Security Training Program Frameworks Contd Infographics PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this companys data safety recognition security training program frameworks contd infographics pdf. Use them to share invaluable insights on requirements, target audience, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

HACCP Worksheet To Monitor Food Safety Hazards Food Security Excellence Ppt Pictures Design Ideas PDF
This slide provides information regarding HACCP Worksheet to ensure food quality by addressing possible hazards, critical limits, corrective actions, verification, record keeping, etc. Deliver an awe inspiring pitch with this creative haccp worksheet to monitor food safety hazards food security excellence ppt pictures design ideas pdf bundle. Topics like process, monitoring, possible hazards, corrective action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
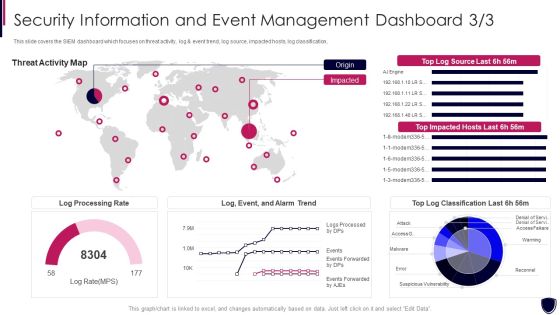
Security Information And Event Enhancing Cyber Safety With Vulnerability Administration Portrait PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event enhancing cyber safety with vulnerability administration portrait pdf bundle. Topics like log processing rate, threat activity map can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Icons PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach icons pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Assessment Matrix Of Cyber Risks Ppt PowerPoint Presentation Icon Styles PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative info security assessment matrix of cyber risks ppt powerpoint presentation icon styles pdf bundle. Topics like employee devices, webserver network, cloud, retail, data center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver and pitch your topic in the best possible manner with this Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images Pdf. Use them to share invaluable insights on key program, targeted training, management, methodologies, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
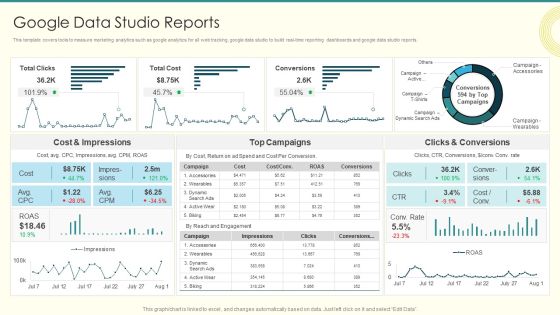
Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF bundle. Topics like Impressions, Clicks Conversions, Cost Impressions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF
This template covers working of Facebooks machine learning or algorithms to filter through a massive amount of data and generate a list of qualified, cold prospects.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF bundle. Topics like Interests Activity, Common Builds, Target Customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Security And Performance Digital Marketing Playbook Slide Inspiration PDF
This is a Table Of Contents For Security And Performance Digital Marketing Playbook Slide Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Target Strategic, Build Personas, Create Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps Of Security Patching With Scanning And Assessing Ppt PowerPoint Presentation Slides Portrait PDF
Presenting this set of slides with name steps of security patching with scanning and assessing ppt powerpoint presentation slides portrait pdf. This is a four stage process. The stages in this process are scanning, assessing, deploying, monitoring, device group, device, installed patches, missing patches, service packs, patches, bulletins, progress, results. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Warehouse Security Issues Ppt PowerPoint Presentation Inspiration Master Slide Cpb Pdf
Presenting this set of slides with name data warehouse security issues ppt powerpoint presentation inspiration master slide cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like data services market data pricing analytics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Email Security Encryption And Data Loss Prevention Table Of Content Slides PDF
Presenting email security encryption and data loss prevention table of content slides pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like project context, our services, action plan, investment, about us, case study, our team, client testimonials, terms and conditions. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
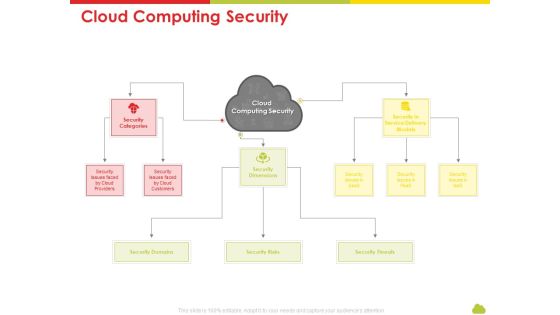
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Security Rules PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan cloud computing security rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like risks, threats, domains, service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Addressing Employee Crisis Prevention Inspiration PDF
The crisis management team should assist employees so that they can avoid the crisis before it hits. The firm should ensure that employee behave loyally and lawfully, refraining from any kind of misconduct. Deliver an awe inspiring pitch with this creative developing firm security strategy plan addressing employee crisis prevention inspiration pdf bundle. Topics like services, communication mode, frequency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Information And Event Management Strategies For Financial Audit And Compliance Table Of Contents Diagrams PDF
This is a security information and event management strategies for financial audit and compliance table of contents diagrams pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like company overview, challenges and solutions, services offered, features and benefits, siem architecture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF bundle. Topics like Operations Status Tool, Management Services Managed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
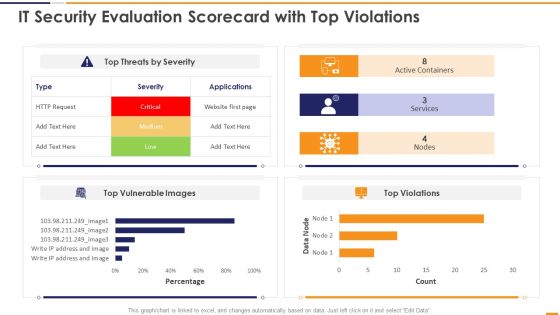
IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF bundle. Topics like Top Threats Severity, Active Containers Services, Top Vulnerable Images can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Addressing The Companies Digitization Levels By Sectors Clipart PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Addressing The Companies Digitization Levels By Sectors Clipart PDF bundle. Topics like Overall Digitization, Professional Services, Business Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF. Use them to share invaluable insights on Logging Process, Capture Requirements, Service Desk Agent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Selecting Suitable Mobile Device Management Solutions Mobile Device Security Inspiration PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management.Deliver an awe inspiring pitch with this creative Selecting Suitable Mobile Device Management Solutions Mobile Device Security Inspiration PDF bundle. Topics like Experience Management, Geofencing, Self Registration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Major Activities To Enhance Housing Society Security Ppt PowerPoint Presentation Gallery Background Designs PDF
Presenting major activities to enhance housing society security ppt powerpoint presentation gallery background designs pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including eliminate potential hazards, ensure members are properly trained, provide visual safety aids and messages, create a safety committee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Essential Trainings To Employees Food Security Excellence Ppt Professional Icons PDF
This slide provides information regarding the crucial trainings such as design control quality, safety, environmental trainings, etc. Deliver and pitch your topic in the best possible manner with this essential trainings to employees food security excellence ppt professional icons pdf. Use them to share invaluable insights on management, technology, environmental, safety, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Present our Arrows PowerPoint Templates because You can Bind your ideas with our PowerPoint Templates and Slides. They will add great value to the worth of your package. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use our Finance PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Use our Success PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level.Use these PowerPoint slides for presentations relating to Internet Virus, technology, arrows, signs, finance, success. The prominent colors used in the PowerPoint template are Yellow, Black, White. Professionals tell us our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. You can be sure our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 will make you look like a winner. PowerPoint presentation experts tell us our arrows PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words.

Money House Captital Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Money PowerPoint Templates because It will get your audience in sync. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Download our Sales PowerPoint Templates because Your audience will believe you are the cats whiskers. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to money house, money, business, sales, signs, success. The prominent colors used in the PowerPoint template are Green, Yellow, Black. PowerPoint presentation experts tell us our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides will make the presenter successul in his career/life. You can be sure our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our signs PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Presenters tell us our Money House Captital Security PowerPoint Templates PPT Backgrounds For Slides 0113 will impress their bosses and teams. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides will make you look like a winner.

Cyber Security Detection Response Ppt PowerPoint Presentation Model Infographic Template Cpb Pdf
Presenting this set of slides with name cyber security detection response ppt powerpoint presentation model infographic template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like customer centric systems to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cyber Security For Your Organization Budget For Effective Cybersecurity Management Ppt Ideas Objects PDF
Presenting this set of slides with name cyber security for your organization budget for effective cybersecurity management ppt ideas objects pdf. This is a one stage process. The stages in this process are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security For Your Organization Business Impact Assessment Ppt Icon Designs PDF
Presenting this set of slides with name cyber security for your organization business impact assessment ppt icon designs pdf. This is a three stage process. The stages in this process are department function, executive dexter hastings, employees, bcp representative, primary business function, strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Email Security Market Research Report Porters 5 Force Model Designs PDF
Presenting this set of slides with name email security market research report porters 5 force model designs pdf. This is a four stage process. The stages in this process are threat of substitute products, bargaining power of suppliers, bargaining power of buyers, threat of new entrants. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Porters 5 Force Model Designs PDF
Presenting this set of slides with name global cloud based email security market porters 5 force model designs pdf. This is a four stage process. The stages in this process are threat of substitute products, bargaining power of suppliers, bargaining power of buyers, threat of new entrants. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Table Of Contents Formats PDF
Presenting this set of slides with name global cloud based email security market table of contents formats pdf. This is a eight stage process. The stages in this process are market introduction, market dynamics, market by segments, market competition analysis, market forecasting and projections, issues faced by companies, porter 5 force model. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Key Stats Drivers Ppt Professional Background PDF
Presenting this set of slides with name global cloud based email security market key stats drivers ppt professional background pdf. The topics discussed in these slides are incremental growth, key drivers, the market is fairly concentrated with quite a few players occupying the larger market share. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Business Impact Assessment Ppt Pictures Summary PDF
Presenting this set of slides with name strategies to mitigate cyber security risks business impact assessment ppt pictures summary pdf. This is a three stage process. The stages in this process are strengths, weaknesses, loss impact, primary business function, bcp representative, number employees, executive dexter hastings, department, function. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Table Of Contents Ppt Inspiration Professional PDF
Presenting this set of slides with name strategies to mitigate cyber security risks table of contents ppt inspiration professional pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role personnel, cost associated to firm, impact analysis dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Cybersecurity Contingency Plan Business Impact Analysis Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cybersecurity contingency plan business impact analysis brochure pdf. This is a three stage process. The stages in this process are determining vital it resources, determining issues impacts and acceptable outage time, assign recovery priorities, settlement agreements, litigation files, department file cabinets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

COVID 19 Mitigating Impact On High Tech Industry Security Maturity Hierarchy Including Five Levels Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry security maturity hierarchy including five levels brochure pdf. The topics discussed in these slides are business unit, awareness and training, compliance and it audit, emerging it threats, incident response ir, operations and support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Staff Training Schedule With Cost Ppt PowerPoint Presentation Pictures Slideshow PDF
Presenting this set of slides with name cyber security implementation framework staff training schedule with cost ppt powerpoint presentation pictures slideshow pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module, supplier relationship management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Table Of Contents Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name cyber security implementation framework table of contents ppt powerpoint presentation icon portfolio pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role of personnel, cost associated to firm, impact analysis, dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Multi Stages System For Contractor Security Management With Key Tasks Ppt PowerPoint Presentation Styles Tips PDF
Presenting this set of slides with name multi stages system for contractor security management with key tasks ppt powerpoint presentation styles tips pdf. This is a five stage process. The stages in this process are contract definition and award, pre commencement, contract execution and control, hand over and acceptance, close out and review. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Email Security Encryption And Data Loss Prevention 30 60 90 Days Plan Diagrams PDF
This is a email security encryption and data loss prevention 30 60 90 days plan diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Email Security Encryption And Data Loss Prevention Client Testimonial Guidelines PDF
This Slide shows the testimonials of the previous clients who have worked with you. Presenting email security encryption and data loss prevention client testimonial guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like client testimonial. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Different Types Of Threats In IT Security Ppt PowerPoint Presentation Portfolio Model PDF
Persuade your audience using this different types of threats in it security ppt powerpoint presentation portfolio model pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including malware, botnets, virus, trojan, spam, phishing, malicious codes, web based attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
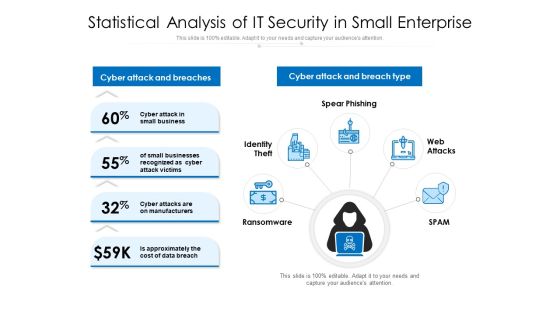
Statistical Analysis Of IT Security In Small Enterprise Ppt PowerPoint Presentation Ideas Design Inspiration PDF
Persuade your audience using this statistical analysis of it security in small enterprise ppt powerpoint presentation ideas design inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber attack and breaches, cyber attack and breach type, spear phishing, web attacks, spam, ransomware, identity theft. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
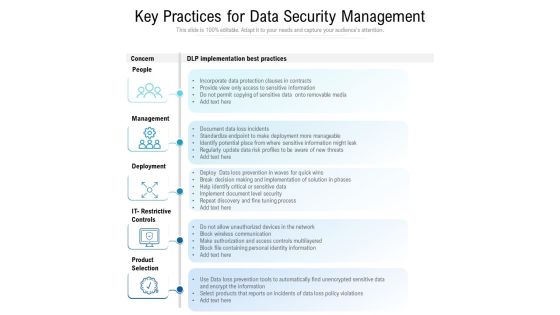
Key Practices For Data Security Management Ppt PowerPoint Presentation File Background Designs PDF
Persuade your audience using this key practices for data security management ppt powerpoint presentation file background designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including management, deployment, implementation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Stages Of IT Security Systems Development Process Ppt PowerPoint Presentation Slides Display PDF
Presenting key stages of it security systems development process ppt powerpoint presentation slides display pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including investigation, analysis, logical design, physical design, implementation, maintenance and change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Disaster Recuperation Half Yearly Quarterly Roadmap To Eradicate Intrusion Graphics
Presenting our innovatively-structured cyber security disaster recuperation half yearly quarterly roadmap to eradicate intrusion graphics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Disaster Recuperation Three Months Roadmap To Eradicate Intrusion Topics
Presenting our jaw-dropping cyber security disaster recuperation three months roadmap to eradicate intrusion topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
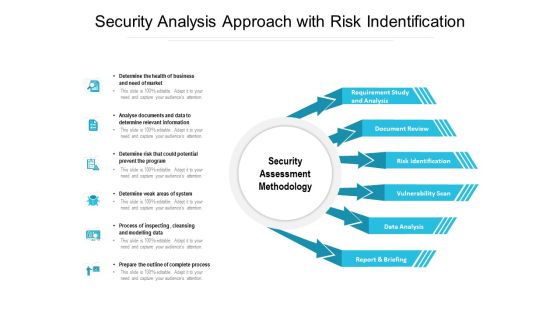
Security Analysis Approach With Risk Indentification Ppt PowerPoint Presentation Professional Gridlines PDF
Presenting security analysis approach with risk indentification ppt powerpoint presentation professional gridlines pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including analyse, of business, need of market, prevent the program, process of inspecting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Stages To Develop Strong Cyber Security Analysis Process Ppt PowerPoint Presentation Outline Example File PDF
Persuade your audience using this stages to develop strong cyber security analysis process ppt powerpoint presentation outline example file pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including formulate remediation steps and prioritize risks, analysing collected, recipient on the phone, teleconference. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT And Cloud Facilities Management 4 Dimensions Of Infrastructure Security Professional PDF
This is a it and cloud facilities management 4 dimensions of infrastructure security professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like structured, unstructured, systems applications, web applications, outsources, mobile applications, non traditional, datacenters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
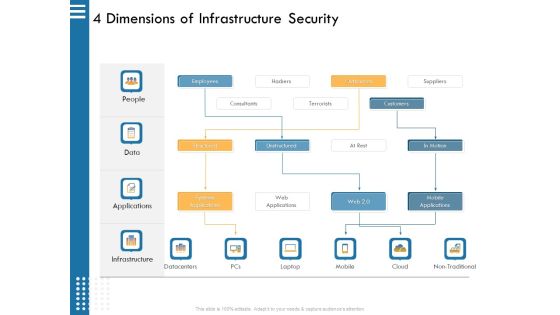
IT Infrastructure Governance 4 Dimensions Of Infrastructure Security Ppt File Example PDF
This is a it infrastructure governance 4 dimensions of infrastructure security ppt file example pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, outsources, hackers, terrorists, consultants. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

 Home
Home