Password Security
Requirement For Security Planning And Risk Mitigation Process Ppt PowerPoint Presentation Infographics Icon PDF
Pitch your topic with ease and precision using this requirement for security planning and risk mitigation process ppt powerpoint presentation infographics icon pdf. This layout presents information on main requirements, supporting requirements, security plan review, threat levels, impact risks, risk steward. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Utilizing Infrastructure Management Using Latest Methods Interdependence Resiliency And Security Themes PDF
This is a utilizing infrastructure management using latest methods interdependence resiliency and security themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical infrastructure dependencies and interdependencies assessment framework, infrastructure resilience wheel, lifecycle adaptive components resilience framework, dimensions infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Eight Steps Of Portfolio Management With Security Analysis Ppt PowerPoint Presentation Gallery Deck PDF
Persuade your audience using this eight steps of portfolio management with security analysis ppt powerpoint presentation gallery deck pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including security analysis, portfolio analysis, portfolio evaluation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Management And Security With Contract File Vector Icon Ppt PowerPoint Presentation Gallery Display PDF
Persuade your audience using this data management and security with contract file vector icon ppt powerpoint presentation gallery display pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data management and security with contract file vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Software Deployed To Countermeasure Internet Threats Ppt PowerPoint Presentation Gallery Icon PDF
Persuade your audience using this security software deployed to countermeasure internet threats ppt powerpoint presentation gallery icon pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security software deployed to countermeasure internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Construction Engineering And Industrial Facility Management Interdependence Resiliency And Security Graphics PDF
This is a construction engineering and industrial facility management interdependence resiliency and security graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Workforce Security Realization Coaching Plan Ideas PDF
This is a table of contents for workforce security realization coaching plan ideas pdf template with various stages. Focus and dispense information on fourteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security awareness, tracking, communication plan, current scenario, training formats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
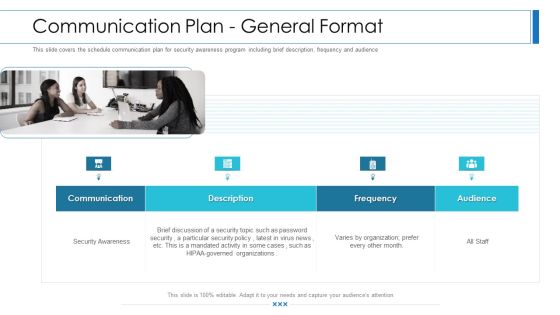
Workforce Security Realization Coaching Plan Communication Plan General Format Brochure PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Presenting workforce security realization coaching plan communication plan general format brochure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, description, frequency, audience. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Communication Plan For Cybersecurity Events And Incidents Graphics PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan communication plan for cybersecurity events and incidents graphics pdf bundle. Topics like resources training, department awareness training, approved communication topics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
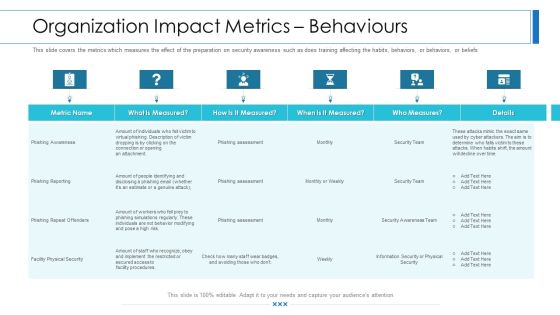
Workforce Security Realization Coaching Plan Organization Impact Metrics Behaviours Infographics PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization impact metrics behaviours infographics pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Access Control On Security Surveillance Vector Icon Ppt PowerPoint Presentation Gallery Graphics Download PDF
Persuade your audience using this access control on security surveillance vector icon ppt powerpoint presentation gallery graphics download pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including access control on security surveillance vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Guard With Surveillance System Vector Icon Ppt PowerPoint Presentation File Model PDF
Persuade your audience using this security guard with surveillance system vector icon ppt powerpoint presentation file model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security guard with surveillance system vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Risk Mitigation Strategy Model Icon With Security Shield Symbol Ppt PowerPoint Presentation Icon Inspiration PDF
Persuade your audience using this risk mitigation strategy model icon with security shield symbol ppt powerpoint presentation icon inspiration pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including risk mitigation strategy model icon with security shield symbol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Breach Prevention Recognition Automated Security Awareness Platform And Cost Slides PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative data breach prevention recognition automated security awareness platform and cost slides pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
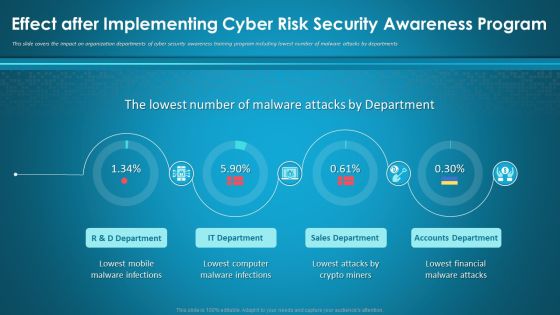
Effect After Implementing Cyber Risk Security Awareness Program Ppt Layouts Visuals PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Deliver an awe-inspiring pitch with this creative effect after implementing cyber risk security awareness program ppt layouts visuals pdf bundle. Topics like mobile, sales department, accounts department, financial, computer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Contingency Plan For Threat Handling Clipart PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative information and technology security operations contingency plan for threat handling clipart pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Essential Roles And Responsibilities Involved In Secops Topics PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this information and technology security operations essential roles and responsibilities involved in secops topics pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
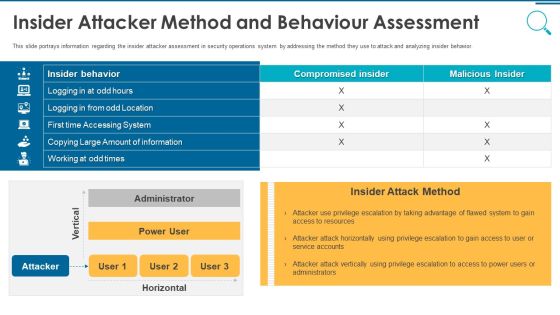
Information And Technology Security Operations Insider Attacker Method And Behaviour Assessment Inspiration PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this information and technology security operations insider attacker method and behaviour assessment inspiration pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions Budget For Effective Secops System Management Rules PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this organizational security solutions budget for effective secops system management rules pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions Essential Roles And Responsibilities Involved In Secops Download PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this organizational security solutions essential roles and responsibilities involved in secops download pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
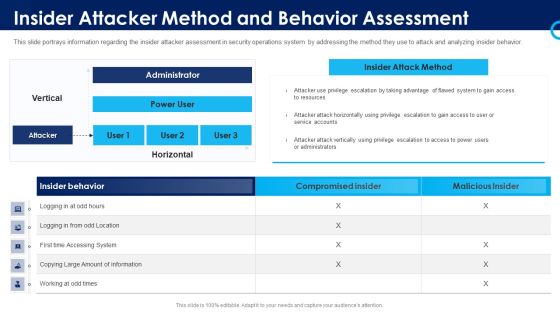
Organizational Security Solutions Insider Attacker Method And Behavior Assessment Introduction PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this organizational security solutions insider attacker method and behavior assessment introduction pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Employee Engagement Model With Recognition And Security Ppt File Templates PDF
Persuade your audience using this employee engagement model with recognition and security ppt file templates pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including recognition, exciting work, security, education, conditions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
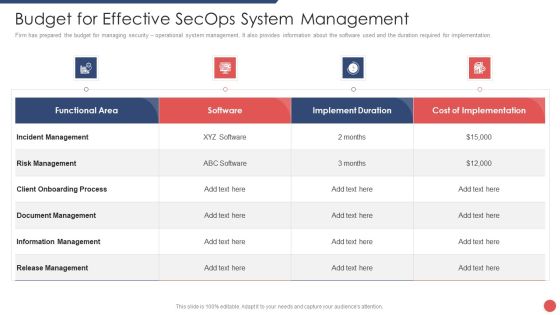
Security Functioning Centre Budget For Effective Secops System Management Formats PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security functioning centre budget for effective secops system management formats pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Insider Attacker Method And Behaviour Assessment Ideas PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security functioning centre insider attacker method and behaviour assessment ideas pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Impact Of Successful Implementation Of Secops System Slides PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Deliver an awe inspiring pitch with this creative security functioning centre impact of successful implementation of secops system slides pdf bundle. Topics like security analyst productivity, threat, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Table Of Contents Ppt Professional Graphic Tips PDF
Presenting security functioning centre table of contents ppt professional graphic tips pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like dashboard, impact analysis, incident management, security operations centre, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Budget For Effective Secops System Management Brochure PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security and process integration budget for effective secops system management brochure pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Contingency Plan For Threat Handling Template PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative security and process integration contingency plan for threat handling template pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Essential Roles And Responsibilities Involved In Secops Background PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this security and process integration essential roles and responsibilities involved in secops background pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
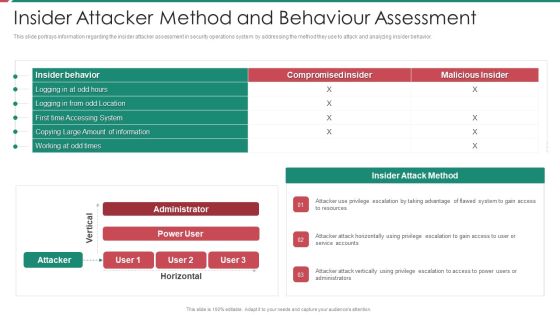
Security And Process Integration Insider Attacker Method And Behaviour Assessment Microsoft PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security and process integration insider attacker method and behaviour assessment microsoft pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
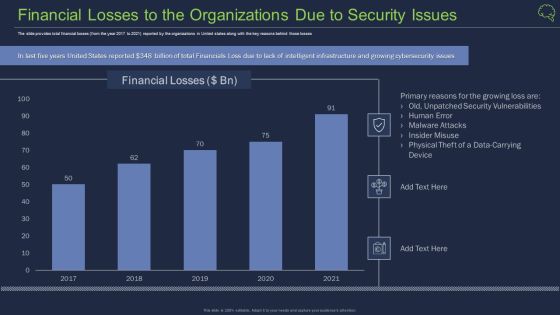
Financial Losses To The Organizations Due To Security Issues Ppt Background PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues ppt background pdf bundle. Topics like financial losses to the organizations due to security issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Management Plan Framework For Data Security Ppt Inspiration Background Designs PDF
Persuade your audience using this management plan framework for data security ppt inspiration background designs pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including procedures, data security, framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Management Plan Steps In Detail Identifying Goals And Objectives Clipart PDF
Presenting security management plan steps in detail identifying goals and objectives clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like implementation of security, organizational objectives, represent the business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Professional PDF
This is a security management plan steps in detail data backup and data loss recovery plan professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security tools, categories of application, data backup frequency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Risk Assessment And Analysis Template PDF
This is a security management plan steps in detail risk assessment and analysis template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential consequence, security risks or liabilities, management to educate You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Figures Icon Infographics For Security Best Practices Ppt PowerPoint Presentation File Graphics Example PDF
Persuade your audience using this figures icon infographics for security best practices ppt powerpoint presentation file graphics example pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including figures icon infographics for security best practices. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

3 Months Timeline Saas Data Security Ppt PowerPoint Presentation Gallery Master Slide PDF
Persuade your audience using this 3 months timeline saas data security ppt powerpoint presentation gallery master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including 3 months timeline saas data security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Implementing Security Management Strategy To Mitigate Risk Topics PDF
This is a agenda for implementing security management strategy to mitigate risk topics pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for implementing security management strategy to mitigate risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
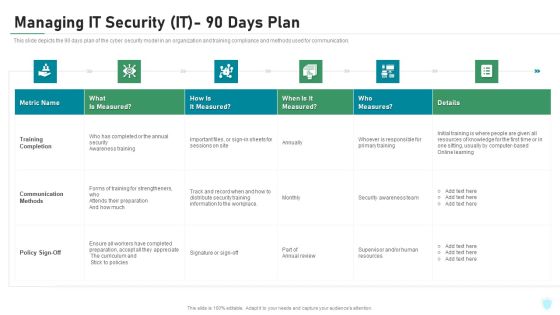
Managing IT Security IT 90 Days Plan Ppt Layouts Picture PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this managing it security it 90 days plan ppt layouts picture pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
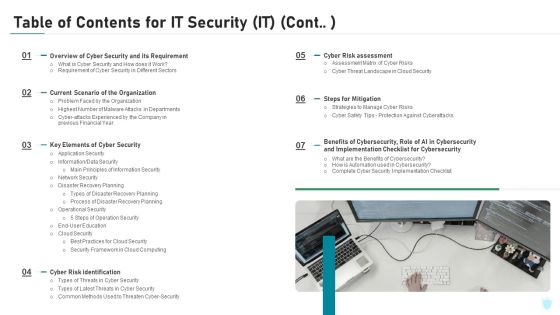
Table Of Contents For IT Security IT Cont Cyber Ppt Slides Graphics Tutorials PDF
This is a table of contents for it security it cont cyber ppt slides graphics tutorials pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, cyber security, implementation, financial, strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
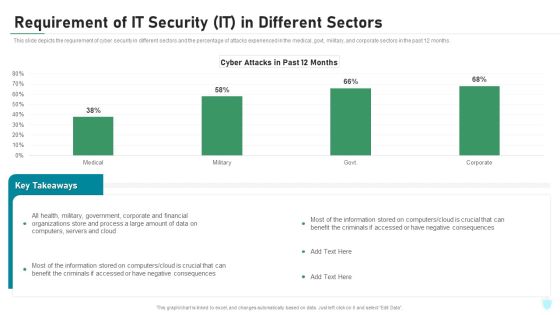
Requirement Of IT Security IT In Different Sectors Ppt Inspiration Deck PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative requirement of it security it in different sectors ppt inspiration deck pdf bundle. Topics like corporate, financial, organizations, process, computers, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

8 Cycle Representation Of Security Policy Ppt PowerPoint Presentation Gallery Grid PDF
Persuade your audience using this 8 cycle representation of security policy ppt powerpoint presentation gallery grid pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 cycle representation of security policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

8 Steps Circle Of Internal Audit And Cyber Security Ppt PowerPoint Presentation Gallery Themes PDF
Persuade your audience using this 8 steps circle of internal audit and cyber security ppt powerpoint presentation gallery themes pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 steps circle of internal audit and cyber security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

8 Components Graphics For Business Security Techniques Ppt Inspiration Shapes PDF
Persuade your audience using this 8 components graphics for business security techniques ppt inspiration shapes pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 components graphics for business security techniques. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5 Stage Framework Security Policy Management Slide Ppt PowerPoint Presentation Outline Examples PDF
Persuade your audience using this 5 stage framework security policy management slide ppt powerpoint presentation outline examples pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including 5 stage framework security policy management slide. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

3 Groups Infographic For Packet Broker Security Ppt PowerPoint Presentation File Visual Aids PDF
Persuade your audience using this 3 groups infographic for packet broker security ppt powerpoint presentation file visual aids pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including 3 groups infographic for packet broker security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparing Two Choices Diagram For Security Policy Orchestration Ppt PowerPoint Presentation Gallery Design Templates PDF
Persuade your audience using this comparing two choices diagram for security policy orchestration ppt powerpoint presentation gallery design templates pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including comparing two choices diagram for security policy orchestration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Circle Procedure Slide Of Hybrid Cloud Security System Requirements Ppt Infographic Template Graphics Pictures PDF
Persuade your audience using this circle procedure slide of hybrid cloud security system requirements ppt infographic template graphics pictures pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including circle procedure slide of hybrid cloud security system requirements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Management Plan System Management Checklist With Key Activities Structure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative cyber security risk management plan system management checklist with key activities structure pdf bundle. Topics like system monitoring, data backup, security patches, virus scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Using System Categorization Sheet For Asset Identification Template PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information. Deliver an awe inspiring pitch with this creative cyber security risk management plan using system categorization sheet for asset identification template pdf bundle. Topics like location, accessibility, organization, access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Scorecard Information Security Risk Rating Scorecard With Customer Order Slides PDF
This is a cybersecurity risk scorecard information security risk rating scorecard with customer order slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security risk rating scorecard with customer order. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
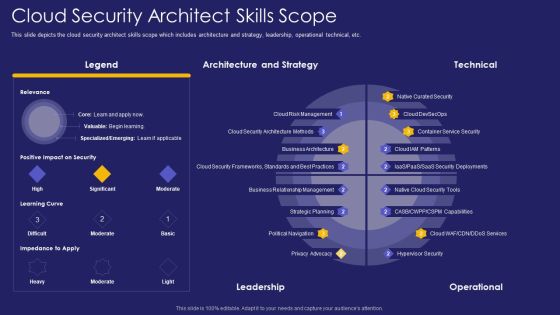
Role IT Team Digital Transformation Cloud Security Architect Skills Scope Rules PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative role it team digital transformation cloud security architect skills scope rules pdf bundle. Topics like architecture, strategy, leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
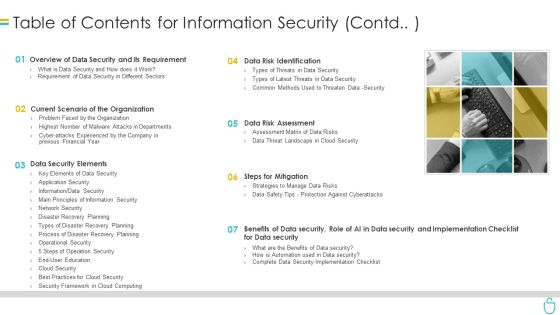
Table Of Contents For Information Security Contd Ppt Show Topics PDF
This is a table of contents for information security contd ppt show topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, requirement, data security, data risk assessment, steps for mitigation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agile Information Technology Project Administration Agile Performance Evaluation Metrics Security Ideas PDF
This slide covers the metrics used by the organisation to measure agile capability on the basis of product performance, security level and user satisfaction Deliver and pitch your topic in the best possible manner with this agile information technology project administration agile performance evaluation metrics security ideas pdf. Use them to share invaluable insights on agile performance evaluation metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Elements Of Electronic Information Security End User Education Ppt Show Brochure PDF
This is a cybersecurity elements of electronic information security end user education ppt show brochure pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, measures, security, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
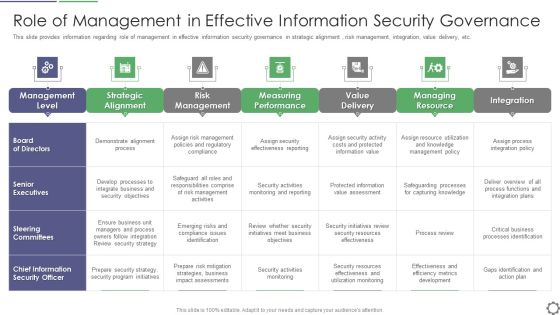
Role Of Management In Effective Information Security Governance Ppt PowerPoint Presentation File Rules PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative role of management in effective information security governance ppt powerpoint presentation file rules pdf bundle. Topics like management level, strategic alignment, risk management, measuring performance, value delivery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Data Repository Sync Process With Firewall And Security Brochure PDF
Presenting cloud data repository sync process with firewall and security brochure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including synergy database server, scheduled cloud sync, firewall and security, synergy cloud data repository . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
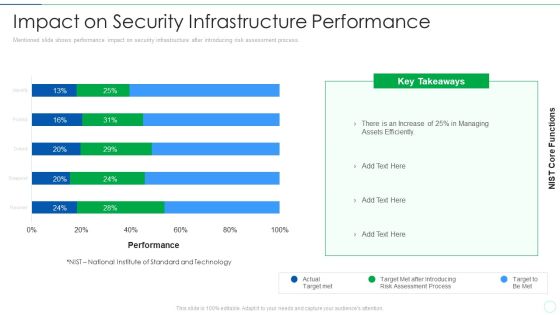
Effective IT Risk Management Process Impact On Security Infrastructure Structure PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this effective it risk management process impact on security infrastructure structure pdf. Use them to share invaluable insights on target, risk, performance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
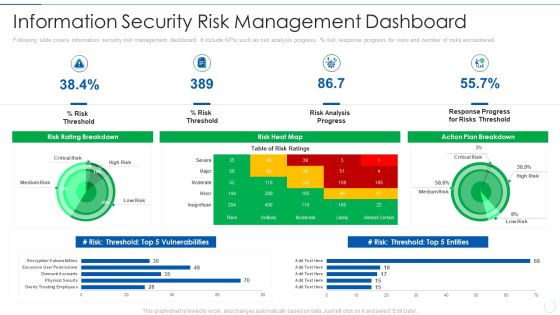
Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
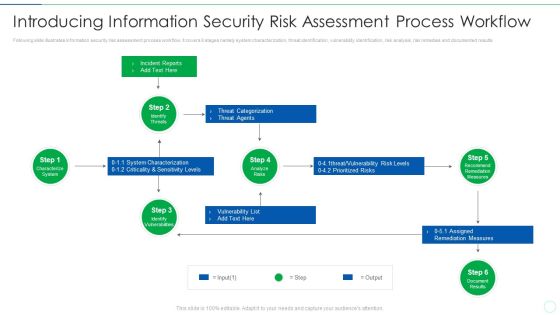
Effective IT Risk Management Process Introducing Information Security Risk Designs PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an awe inspiring pitch with this creative effective it risk management process information security risk assessment formats pdf bundle. Topics like system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icon Showcasing Information Availability Security Against Risks And Threats Designs PDF
Persuade your audience using this icon showcasing information availability security against risks and threats designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including icon showcasing information availability security against risks and threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risk Security Industry Overview With Technology Adoption Rate Slides PDF
This slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Pitch your topic with ease and precision using this cyber risk security industry overview with technology adoption rate slides pdf. This layout presents information on key highlights, technology investment, malware reported. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Risk Security Planning With Educate And Retest Stage Demonstration PDF
The following slide highlights the cyber threat security planning to minimize threats in organizations. It include six stages to deploy cyber threat to organization. Presenting cyber risk security planning with educate and retest stage demonstration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including assess, choose, educate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

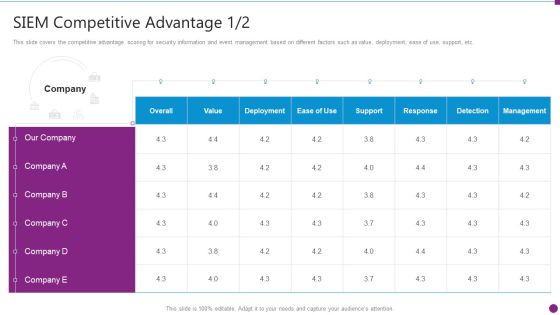
Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Competitive Guidelines PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance siem competitive guidelines pdf. Use them to share invaluable insights on siem competitive advantage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
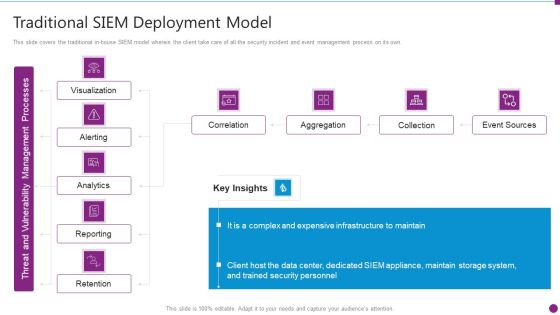
Security Information And Event Management Strategies For Financial Audit And Compliance Traditional SIEM Deployment Guidelines PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance traditional siem deployment guidelines pdf bundle. Topics like correlation, aggregation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda Of Security Information And Event Management Strategies For Financial Audit And Compliance Infographics PDF
This is a agenda of security information and event management strategies for financial audit and compliance infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like customers, security intelligence, log management and compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
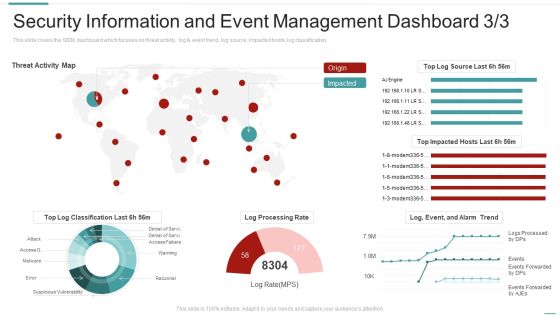
Risk Recognition Automation Security Information And Event Management Dashboard Activity Ppt Styles Influencers PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard activity ppt styles influencers pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
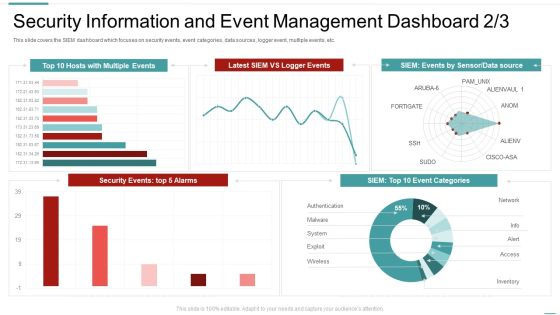
Risk Recognition Automation Security Information And Event Management Dashboard Source Ppt Professional Display PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this risk recognition automation security information and event management dashboard source ppt professional display pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Application Development Life Cycle Security Sample PDF
This is a table of contents for application development life cycle security sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, implementation, models. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Security Lifecycle Ppt Summary Brochure PDF
This is a handling cyber threats digital era security lifecycle ppt summary brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Information Technology Security Requirement Ppt Styles Sample PDF
This slide depicts the categories of recent threats that table of contents for information technology security requirement ppt styles sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like latest threats in information technology security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
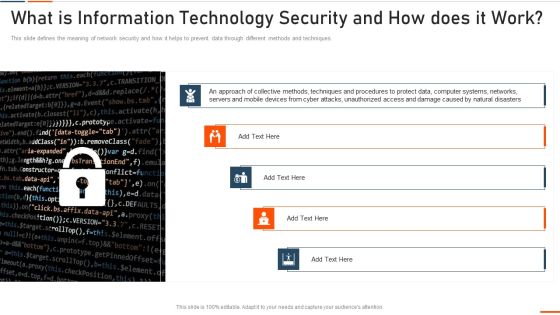
What Is Information Technology Security And How Does It Work Ppt Portfolio Sample PDF
This is a what is information technology security and how does it work ppt portfolio sample pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it risk assessment, it risk identification, key elements it security, steps mitigation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For IT Security Cyber Ppt Inspiration Introduction PDF
This is a table of contents for it security cyber ppt inspiration introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology security, implementation, organization, cyber risk assessment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Methods To Develop Advanced IT Security Monitoring Plan Graphics PDF
This is a agenda for methods to develop advanced it security monitoring plan graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collecting and analyzing, key performance indicators, potential security monitoring threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
This is a agenda for modern security observation plan to eradicate cybersecurity risk and data breach information pdf template with various stages. Focus and dispense information on senen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for modern security observation plan to eradicate cybersecurity risk and data breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Info Security Wd Ppt PowerPoint Presentation Gallery Maker PDF
Presenting table of contents for info security wd ppt powerpoint presentation gallery maker pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like cyber risk assessment, steps for mitigation, cyber risk identification, key elements of information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Timeline For Implementation Of Cyber Security In The Company Sample PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism.Deliver an awe inspiring pitch with this creative cyber terrorism assault timeline for implementation of cyber security in the company sample pdf bundle. Topics like require remote access, testing for business continuity, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
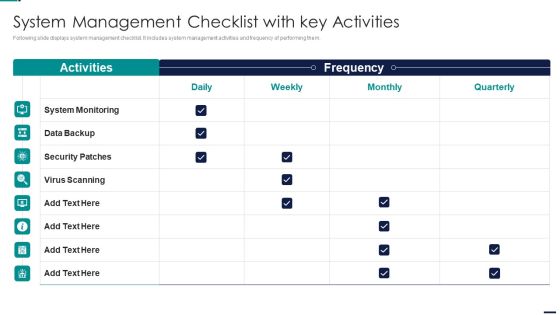
Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF bundle. Topics like System Monitoring, Data Backup, Security Patches, Virus Scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Table Of Contents Brochure PDF
This is a Risk Management Model For Data Security Table Of Contents Brochure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Risks, Defining Risk Level, Setting Scenario, Security Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc.Deliver an awe inspiring pitch with this creative Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF bundle. Topics like Architecture And Strategy, Technical, Leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
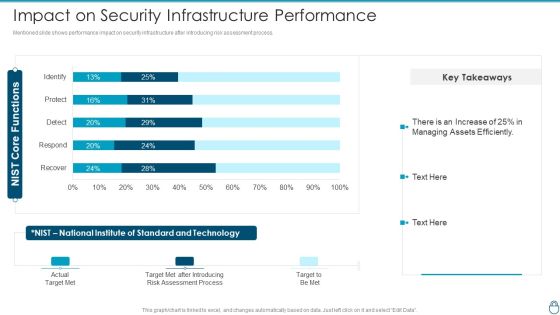
Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
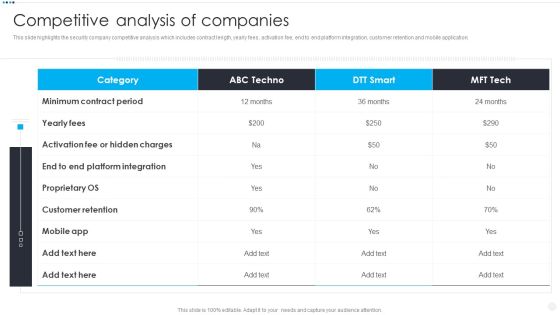
Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF bundle. Topics like Minimum Contract Period, Activation Fee Hidden, Customer Retention Mobile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
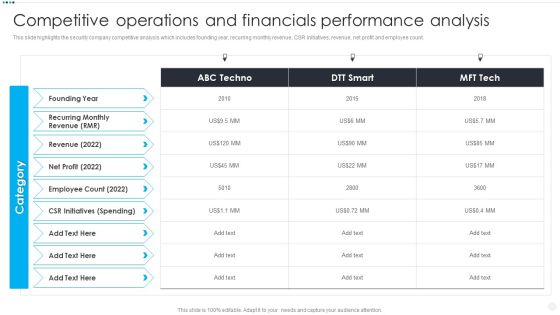
Smart Home Security Solutions Company Profile Competitive Operations And Financials Background PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Competitive Operations And Financials Background PDF. Use them to share invaluable insights on Recurring Monthly Revenue, Employee Count 2022, CSR Initiatives Spending and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Smart Home Security Solutions Company Profile Key CSR Initiatives Background PDF
This slide highlights the corporate social responsibilities activities of security company which includes electric vehicle, blood donation camps, engage empower and educate , free surgeries. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Key CSR Initiatives Background PDF. Use them to share invaluable insights on Add Electric Vehicles, Blood Donation Camps, 3Es Engage Empower and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
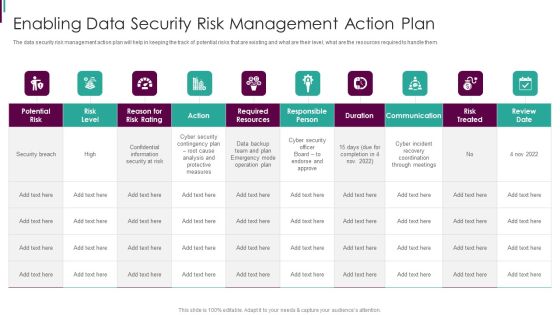
Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational, technical, etc. Deliver and pitch your topic in the best possible manner with this CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF. Use them to share invaluable insights on Architecture Strategy, Risk Management, Business Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Management Level, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF. Use them to share invaluable insights on Recognize Critical, Discover Malicious, Risk Assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF bundle. Topics like Risk Heat, Action Plan, Risk Rating Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF
Persuade your audience using this Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Various Charts, Security KPI Dashboard, Graphs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF bundle. Topics like Risk Management, Measuring Performance, Managing Resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
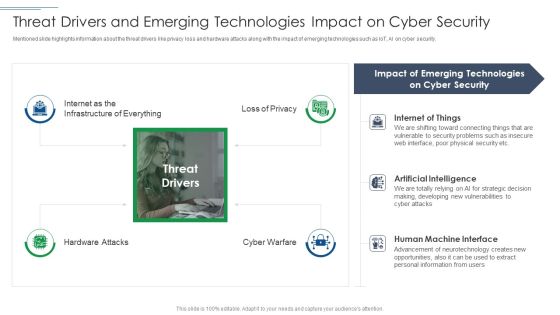
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer System Interface Icon Depicting Mobile Security Ppt Show Example PDF
Persuade your audience using this Computer System Interface Icon Depicting Mobile Security Ppt Show Example PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Computer System, Interface Icon, Depicting Mobile Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF
Persuade your audience using this Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security Computer System, Interface Icon, Cloud Storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF bundle. Topics like Shared And Accessed, Risk Assessment, Review Specifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Competitive Analysis Of Companies Brochure PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Competitive Analysis Of Companies Brochure PDF. Use them to share invaluable insights on Customer Retention, Platform Integration, Minimum Contract and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF bundle. Topics like Employee Count, Recurring Revenue, Spending can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

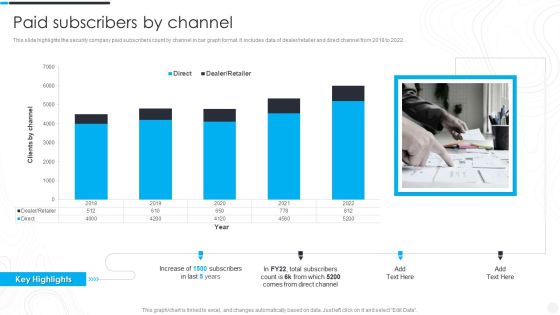
Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF bundle. Topics like Direct Channel, Subscribers In Last, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
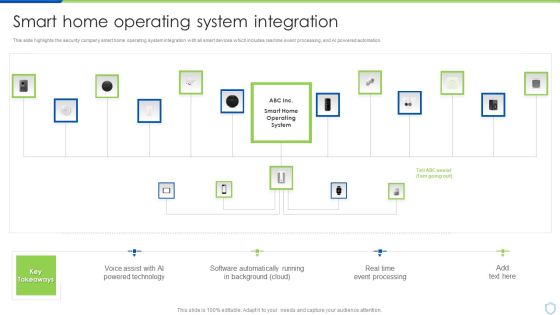
Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Competitive Analysis Of Companies Mockup PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Competitive Analysis Of Companies Mockup PDF. Use them to share invaluable insights on Customer Retention, Hidden Charges, Minimum Contract and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
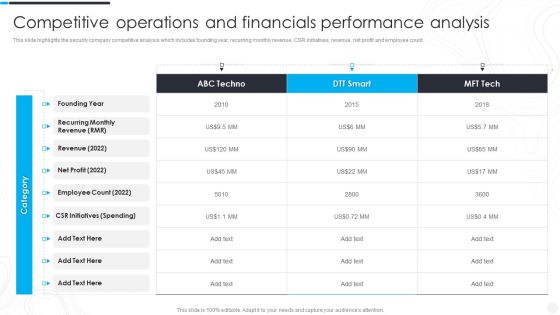
Security Camera System Company Profile Competitive Operations And Financials Slides PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Competitive Operations And Financials Slides PDF bundle. Topics like Employee Count, Initiatives Spending, Revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Camera System Company Profile Paid Subscribers By Channel Sample PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Paid Subscribers By Channel Sample PDF bundle. Topics like Total Subscribers, Direct Channel, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
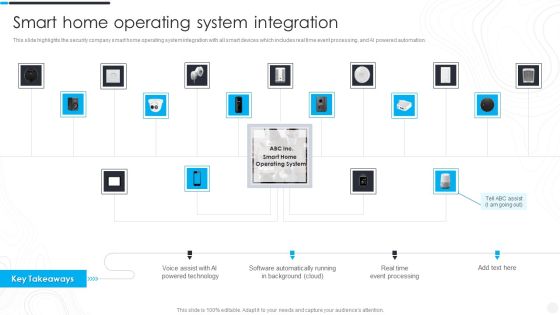
Security Camera System Company Profile Smart Home Operating System Integration Background PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Smart Home Operating System Integration Background PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Saas Cloud Security Best Practices Icon Ppt PowerPoint Presentation File Guidelines PDF
Persuade your audience using this Saas Cloud Security Best Practices Icon Ppt PowerPoint Presentation File Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Saas Cloud Security, Best Practices, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

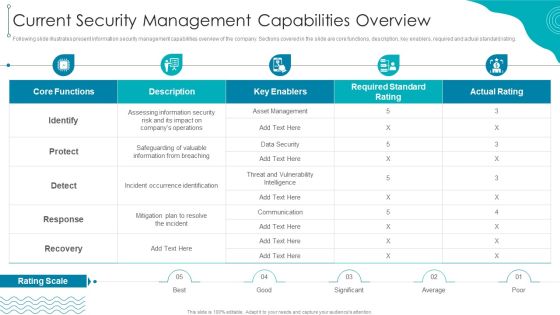
ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF. Use them to share invaluable insights on Assessing Information, Occurrence Identification, Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF bundle. Topics like Vulnerabilities, Rating Breakdown, Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Cyber Attacks Faced By Different Departments Professional PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Cyber Attacks Faced By Different Departments Professional PDF bundle. Topics like Marketing Department, Operations Department, Accounts Department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF
Presenting Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Scenario Assessment, Security Capabilities, Overview Of Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF
Persuade your audience using this 8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF
Persuade your audience using this 6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Business Goals. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Improved Digital Expenditure Role Of Management In Effective Information Security Governance Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Improved Digital Expenditure Role Of Management In Effective Information Security Governance Microsoft PDF bundle. Topics like Management Level, Board Directors, Senior Executives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Deliver and pitch your topic in the best possible manner with this Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF. Use them to share invaluable insights on Risks, Current Value, Risk Level and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver and pitch your topic in the best possible manner with this CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF. Use them to share invaluable insights on Management Level, Strategic Alignment, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF bundle. Topics like Senior Executives, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Occurrence Identification, Communication, Required Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Agency Business Profile Government And Private Sector Clients Sample PDF
This slide highlights the security company clients from government and private sector which includes offices with location and industries with company name. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Government And Private Sector Clients Sample PDF bundle. Topics like Location, Industry can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF
This slide highlights the security company weapon and logistics vehicle details which includes repeater, MG16, doble cabin car, bullet proof vehicle, and patrolling vehicle. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF bundle. Topics like Weapon, Logistics Vehicle Details can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Digitization Of Security Systems Icon With Gear Ppt Portfolio Tips PDF
Persuade your audience using this Digitization Of Security Systems Icon With Gear Ppt Portfolio Tips PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Digitization, Security Systems, Icon With Gear. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For IT Professional Data Certification Program Security Icons PDF
Presenting Table Of Contents For IT Professional Data Certification Program Security Icons PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Certified Information Systems, Security Professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF bundle. Topics like Consumers, Implements Applications, Outlines Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template
Heres a predesigned Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template for you. Built on extensive research and analysis, this one-pager template has all the centerpieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Construction Project Workplace Security Policy Brief One Pager PDF Document PPT Template Download now.

Rental Agreement And Security Deposit Slip One Pager PDF Document PPT Template
Presenting you a fantastic Rental Agreement And Security Deposit Slip One Pager PDF Document PPT Template. This one-pager document is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this Rental Agreement And Security Deposit Slip One Pager PDF Document PPT Template Download now.

One Pager For Cyber Security Firm Seminar Overview PDF Document PPT Template
Looking for a predesigned One Pager For Cyber Security Firm Seminar Overview PDF Document PPT Template Heres the perfect piece for you It has everything that a well-structured one-pager template should have. Besides, it is 100 percent editable, which offers you the cushion to make adjustments according to your preferences. Grab this One Pager For Cyber Security Firm Seminar Overview PDF Document PPT Template Download now.

Manpower Corporate Security Business Profile Government And Private Sector Clients Sample PDF
This slide highlights the security company clients from government and private sector which includes offices with location and industries with company name. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Government And Private Sector Clients Sample PDF bundle. Topics like Industry, Location, Treasure Office can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Company Business Model Canvas Structure PDF
This slide highlights the business model of security guard company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Company Business Model Canvas Structure PDF. Use them to share invaluable insights on Revenue Stream, Cost Structure, Customer Segments and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Manpower Corporate Security Business Profile Staff Recruiting Criteria And Training Centre Sample PDF
This slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Staff Recruiting Criteria And Training Centre Sample PDF bundle. Topics like Selection Criteria, Authorized Training Centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Weapon And Logistics Vehicle Details Rules PDF
This slide highlights the security company weapon and logistics vehicle details which includes repeater, MG16, doble cabin car, bullet proof vehicle, and patrolling vehicle. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Weapon And Logistics Vehicle Details Rules PDF. Use them to share invaluable insights on Weapon, Logistics Vehicle Details and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
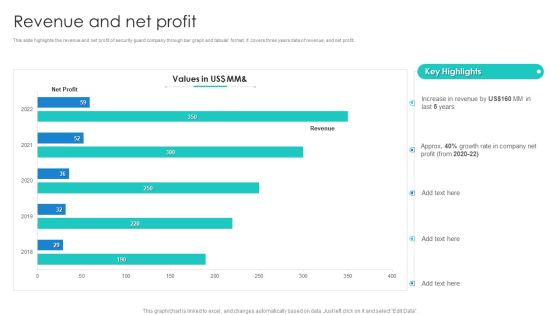
Manpower Corporate Security Business Profile Revenue And Net Profit Inspiration PDF
This slide highlights the revenue and net profit of security guard company through bar graph and tabular format. It covers three years data of revenue, and net profit. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Revenue And Net Profit Inspiration PDF. Use them to share invaluable insights on Revenue, Profit, Growth Rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
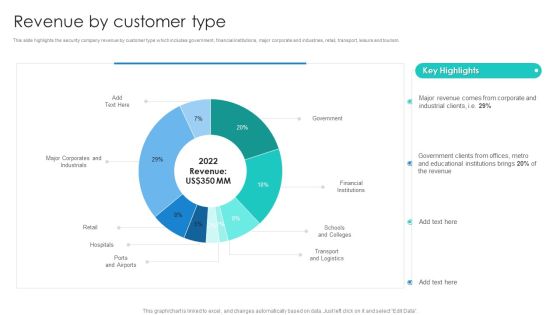
Manpower Corporate Security Business Profile Revenue By Customer Type Download PDF
This slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Revenue By Customer Type Download PDF bundle. Topics like Revenue, Financial Institutions, Transport And Logistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Analyzing Budget For Effective Mobile Device Management Mobile Device Security Management Sample PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative Analyzing Budget For Effective Mobile Device Management Mobile Device Security Management Sample PDF bundle. Topics like Risk Management, Document Management, Information Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Deliver and pitch your topic in the best possible manner with this Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF. Use them to share invaluable insights on Asset Management, Critical Infrastructure, Recovering Capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Tracking Mobile Device Activities At Workplace Mobile Device Security Management Topics PDF
This slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Deliver and pitch your topic in the best possible manner with this Tracking Mobile Device Activities At Workplace Mobile Device Security Management Topics PDF. Use them to share invaluable insights on Ownership, Seen Breakdown, Total Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF bundle. Topics like Gap Analysis, Environmental Trends, Business Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF
This slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up. Presenting Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Problem Detection, Define, Investigate, Identify Resolutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF
This slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Determine Strategies, Risk Mitigation, Engagement Incident. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security Incident Response Lifecycle Ppt Styles Example Topics PDF
This slide covers cyber security incident response lifecycle. It involves four phases such as preparation, detection, containment and post incident activity. Presenting Managing Cyber Security Incident Response Lifecycle Ppt Styles Example Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Preparation, Post Incident Activity, Detection And Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Find a pre-designed and impeccable Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Icons Slide For Business Mobile Device Security Management And Mitigation Guidelines PDF
Help your business to create an attention grabbing presentation using our Icons Slide For Business Mobile Device Security Management And Mitigation Guidelines PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide For Business Mobile Device Security Management And Mitigation Guidelines PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF
Persuade your audience using this Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showing Data Security, Blockchain Technology Supply Chain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. There are so many reasons you need a Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Security For Cloud Based Systems Management Icon For IT Project Rules PDF
Persuade your audience using this Security For Cloud Based Systems Management Icon For IT Project Rules PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Management, IT Project. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF
Persuade your audience using this Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Incident, Alert Icon, Desktop Screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Incident Icon With Man In Black Hood Ppt Inspiration Images PDF
Persuade your audience using this Cyber Security Incident Icon With Man In Black Hood Ppt Inspiration Images PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Incident, Icon With Man, Black Hood. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF
Persuade your audience using this Cloud Online Certificate Icon For Information Security Ppt Styles Example Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Online, Certificate Icon, Information Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
One Page Software Security Management Fact Report PDF Document PPT Template
Presenting you a fantastic One Page Software Security Management Fact Report PDF Document PPT Template. This one-pager document is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this One Page Software Security Management Fact Report PDF Document PPT Template Download now.

One Pager Fact Sheet For Revenue Security PDF Document PPT Template
Presenting you a fantastic One Pager Fact Sheet For Revenue Security PDF Document PPT Template. This one-pager document is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this One Pager Fact Sheet For Revenue Security PDF Document PPT Template Download now.
Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF
Persuade your audience using this Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Overview Of Key Insights, Cyber Security Trends Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

One Page Boundary And Partition Security Fact Sheet PDF Document PPT Template
Presenting you an exemplary One Page Boundary And Partition Security Fact Sheet PDF Document PPT Template. Our one-pager template comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Boundary And Partition Security Fact Sheet PDF Document PPT Template Download now.

Icons Slide For KYC Transaction Monitoring System For Business Security Slides PDF
Help your business to create an attention-grabbing presentation using our Icons Slide For KYC Transaction Monitoring System For Business Security Slides PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide For KYC Transaction Monitoring System For Business Security Slides PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.

One Page Yearly Report For Internet Security Company One Pager Documents
Here is a predesigned One Page Yearly Report For Internet Security Company One Pager Documents for you. Built on extensive research and analysis, this one-complete deck has all the centerpieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this One Page Yearly Report For Internet Security Company One Pager Documents A4 One-pager now.

Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents
Presenting you an exemplary Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents brilliant piece now.

Governance Risk And Compliance Icon To Manage IT And Security Risk Guidelines PDF
Presenting Governance Risk And Compliance Icon To Manage IT And Security Risk Guidelines PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Governance, Risk And Compliance, Icon To Manage, IT And Security, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Proposal For Enterprise Security System Example Document Report Doc Pdf Ppt
Heres a predesigned Proposal For Enterprise Security System Example Document Report Doc Pdf Ppt for you. Built on extensive research and analysis, this one complete deck has all the center pieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Proposal For Enterprise Security System Example Document Report Doc Pdf Ppt A4 One pager now.

Proposal For Enterprise Security System 30 60 90 Days Plan One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System 30 60 90 Days Plan One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System 30 60 90 Days Plan One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Contact Us One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Contact Us One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Contact Us One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document brilliant piece now.
Proposal For Enterprise Security System Icons Slide One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Icons Slide One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Icons Slide One Pager Sample Example Document brilliant piece now.
Proposal For Enterprise Security System Roadmap One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Roadmap One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Roadmap One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Timeline One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Timeline One Pager Sample Example Document brilliant piece now.

Proposal For House Security Devices Installation Example Document Report Doc Pdf Ppt
Heres a predesigned Proposal For House Security Devices Installation Example Document Report Doc Pdf Ppt for you. Built on extensive research and analysis, this one complete deck has all the center pieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Proposal For House Security Devices Installation Example Document Report Doc Pdf Ppt A4 One pager now.

30 60 90 Days Plan For Home Security Equipment Installation One Pager Sample Example Document
Presenting you an exemplary 30 60 90 Days Plan For Home Security Equipment Installation One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this 30 60 90 Days Plan For Home Security Equipment Installation One Pager Sample Example Document brilliant piece now.

Contact Us For Home Security Equipment Installation Proposal One Pager Sample Example Document
Presenting you an exemplary Contact Us For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Contact Us For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

 Home
Home