Password Security

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Survey Template Ppt Example
This is a information security survey template ppt example. This is a four stage process. The stages in this process are information, security, personal, secret.

Enterprise Security Strategy Sample Diagram Ppt Design
This is a enterprise security strategy sample diagram ppt design. This is a five stage process. The stages in this process are security strategy, governance, drivers, compliance, capability.

Big Data Security Model Ppt Presentations
This is a big data security model ppt presentations. This is a three stage process. The stages in this process are security model, confidentiality, availability, integrity.

Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.

Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Web Acceleration Security Software Example Of Ppt
This is a web acceleration security software example of ppt. This is a four stage process. The stages in this process are web acceleration, security software, shopping carts, data services.

Data Security Challenges Template Powerpoint Templates
This is a data security challenges template powerpoint templates. This is a four stage process. The stages in this process are policy compliance, data management, data privacy, infrastructure security.

Security Management Consulting Sample Diagram Powerpoint Images
This is a security management consulting sample diagram powerpoint images. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.

Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.

What Is Cloud Security Guidelines PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Deliver an awe inspiring pitch with this creative What Is Cloud Security Guidelines PDF bundle. Topics like Computing Systems, Protocols, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Risk Management Assessment Checklist Inspiration PDF
This is a security risk management assessment checklist inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security policy, security of third party access, media handling security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Risk Management Assessment Checklist Structure PDF
Presenting security risk management assessment checklist structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, media handling security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

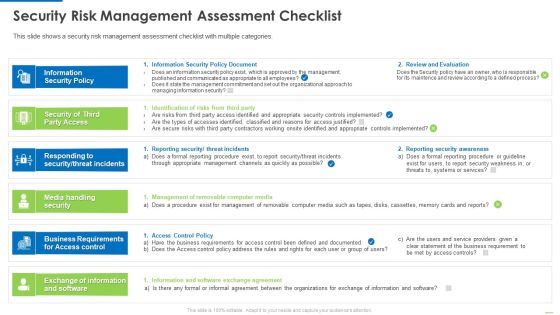
Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Risk Management Assessment Checklist Brochure PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver and pitch your topic in the best possible manner with this security risk management assessment checklist brochure pdf. Use them to share invaluable insights on security, management, requirements, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
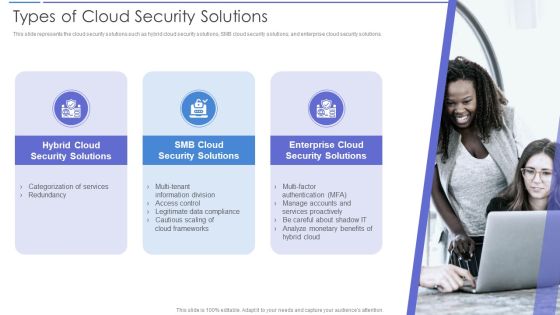
Types Of Cloud Security Solutions Demonstration PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. This is a Types Of Cloud Security Solutions Demonstration PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze, Services Proactively, Information Division. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Native Application Security PPT Template
This Cloud Native Application Security PPT Template is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This seventy two slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.

Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
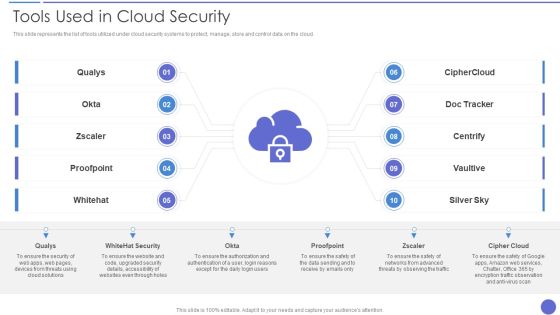
Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Website Template Powerpoint Slide Background Designs
This is a security website template powerpoint slide background designs. This is a six stage process. The stages in this process are inventory, secure coding, secure testing, remediation plan, define next steps, deep scan.

Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
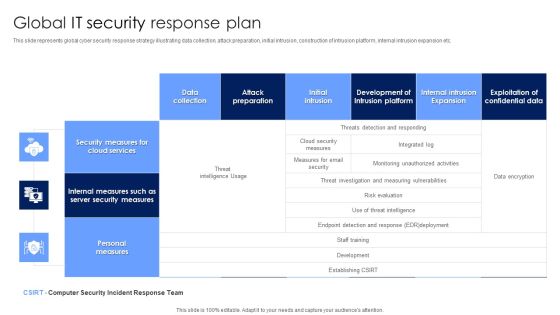
Global IT Security Response Plan Diagrams PDF
This slide represents global cyber security response strategy illustrating data collection, attack preparation, initial intrusion, construction of intrusion platform, internal intrusion expansion etc. Showcasing this set of slides titled Global IT Security Response Plan Diagrams PDF. The topics addressed in these templates are Security Measures, Cloud Services, Personal Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Data Protection Security Mechanism Portrait PDF
This slide exhibits broad categories in data protection which are traditional data protection, data security and privacy. It further includes data retention, backup, preventing data loss, risk monitoring, data governance, third party contracts, etc.Showcasing this set of slides titled Business Data Protection Security Mechanism Portrait PDF. The topics addressed in these templates are Data Retention, Physical Infrastructure, Date Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this impact of effective security management information pdf. Use them to share invaluable insights on malicious codes prevented, unauthorized ip addresses ports and traffic, security incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
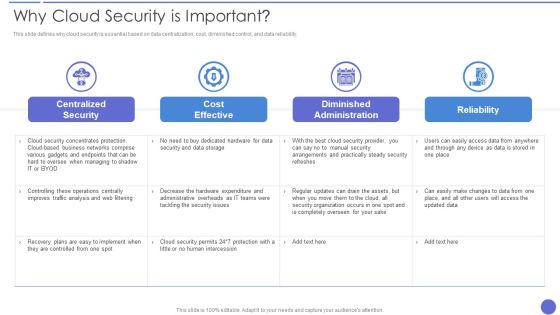
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Analysis Bar Graph Ppt Slides
This is a security analysis bar chart ppt slides. This is a one stage process. The stages in this process are business, finance, marketing.

Security Risk Assessment Sample Diagram Ppt Sample
This is a security risk assessment sample diagram ppt sample. This is a four stage process. The stages in this process are identify, document, decide, evaluate, review.
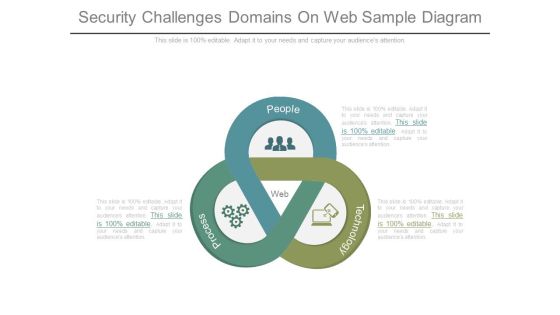
Security Challenges Domains On Web Sample Diagram
This is a security challenges domains on web sample diagram. This is a three stage process. The stages in this process are web, process, people, technology.

Security Patch Management Template Presentation Images
This is a security patch management template presentation images. This is a six stage process. The stages in this process are testing, architecture, quality assurance, analysis, design, synthesis.
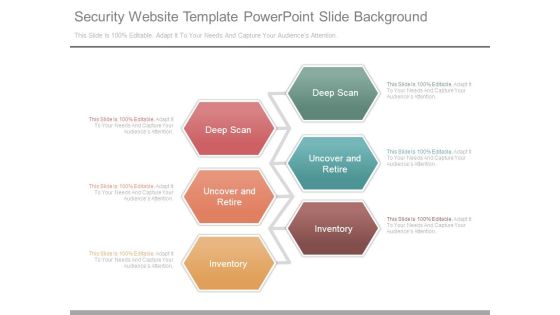
Security Website Template Powerpoint Slide Background
This is a security website template powerpoint slide background. This is a six stage process. The stages in this process are deep scan, uncover and retire, inventory.
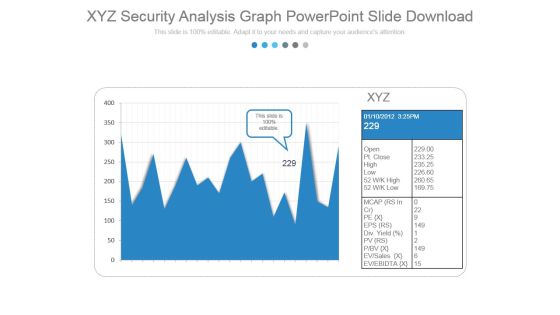
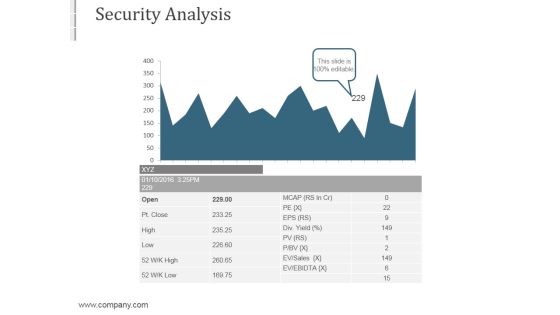
Xyz Security Analysis Graph Powerpoint Slide Download
This is a xyz security analysis graph powerpoint slide download. This is a two stage process. The stages in this process are business, marketing, growth, graph.

Security Analysis Ppt PowerPoint Presentation Slides
This is a security analysis ppt powerpoint presentation slides. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.

Security Analysis Ppt PowerPoint Presentation Layout
This is a security analysis ppt powerpoint presentation layout. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, success.
Security Analysis Ppt PowerPoint Presentation Infographics
This is a security analysis ppt powerpoint presentation infographics. This is a two stage process. The stages in this process are business, finance, growth, analysis, success.

Security Analysis Ppt PowerPoint Presentation Background Image
This is a security analysis ppt powerpoint presentation background image. This is a two stage process. The stages in this process are business, analysis, strategic, finance, management.
Security Analysis Ppt PowerPoint Presentation Guidelines
This is a security analysis ppt powerpoint presentation guidelines. This is a one stage process. The stages in this process are high risk, low risk.

Security Analysis Ppt PowerPoint Presentation Deck
This is a security analysis ppt powerpoint presentation deck. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.

Security Analysis Ppt PowerPoint Presentation Show
This is a security analysis ppt powerpoint presentation show. This is a one stage process. The stages in this process are open, high, low, business, marketing.

Security Analysis Ppt PowerPoint Presentation File Inspiration
This is a security analysis ppt powerpoint presentation file inspiration. This is a two stage process. The stages in this process are business, growth, analysis, strategy, management.

Security Analysis Ppt Powerpoint Presentation File Tips
This is a security analysis ppt powerpoint presentation file tips. This is a one stage process. The stages in this process are graph, marketing, business, growth, finance.

Cyber Security Ppt PowerPoint Presentation Layouts Brochure
This is a cyber security ppt powerpoint presentation layouts brochure. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing.

What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system. This is a What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Developing, Essential Strategy, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Management Form Guidelines PDF
This slide shows information security risk acceptance form which contains accountable person details, risk acceptance summary, acceptance advantages, justification, advice, etc. This can benefit cyber security department in careful review prior to the acceptance of major risks involved. Pitch your topic with ease and precision using this Information Security Risk Management Form Guidelines PDF. This layout presents information on Risk Modification, Risk Acceptance, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Computer Safety And Security Icon Infographics PDF
Persuade your audience using this Computer Safety And Security Icon Infographics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Computer Safety, Security Icon Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda Of Security Risk Management Graphics PDF
This is a agenda of security risk management graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerabilities, organizational, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Administrator Updating Information System Security Infographics PDF
Presenting administrator updating information system security infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including administrator updating information system security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Functional Technology Security Elements PDF
Presenting icon for functional technology security elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including icon for functional technology security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

KPI Dashboard Metrics Security Icon Download PDF
Persuade your audience using this KPI Dashboard Metrics Security Icon Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Dashboard, Metrics Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
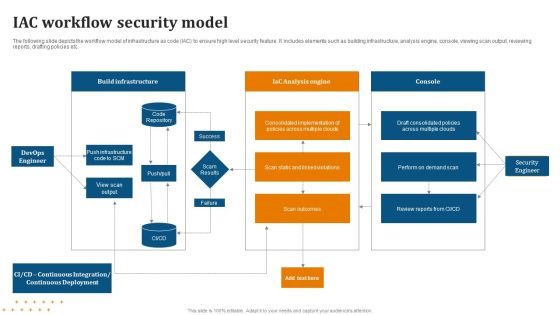
IAC Workflow Security Model Diagrams PDF
Showcasing this set of slides titled IAC Workflow Security Model Diagrams PDF. The topics addressed in these templates are Workflow, Security Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
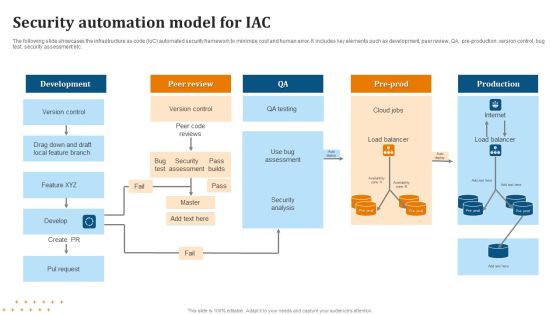
Security Automation Model For IAC Summary PDF
Pitch your topic with ease and precision using this Security Automation Model For IAC Summary PDF. This layout presents information on Security Automation, Model For IAC . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Data Storage Security Management Icon Professional PDF
Presenting Data Storage Security Management Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Storage, Security, Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Payment Card Security Processing Icon Portrait PDF
Presenting Payment Card Security Processing Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Payment Card Security, Processing Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Best Practices Themes PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Security Best Practices Themes PDF. Use them to share invaluable insights on Secure Your Cloud, Data Encryption, Recognize Critical Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Digital Transformation Purpose Sample PDF
The slide shows a modern security transformation agenda for securing business with advanced information security. It also highlights vision, strategies and service lines of technology advancement. Persuade your audience using this Cyber Security Digital Transformation Purpose Sample PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Agenda, Vision, Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Checklist Networking Elements PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting Cloud Security Checklist Networking Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Network, Encrypt Critical Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
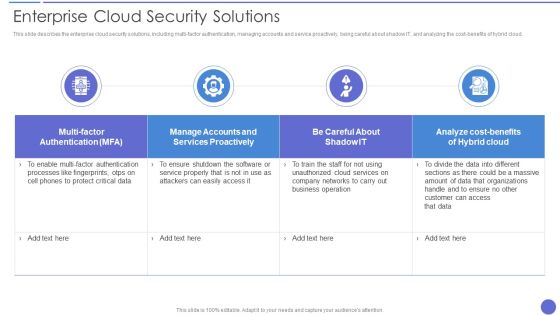
Enterprise Cloud Security Solutions Professional PDF
This slide describes the enterprise cloud security solutions, including multi factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost benefits of hybrid cloud. Deliver an awe inspiring pitch with this creative Enterprise Cloud Security Solutions Professional PDF bundle. Topics like Services Proactively, Analyze Cost Benefits, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
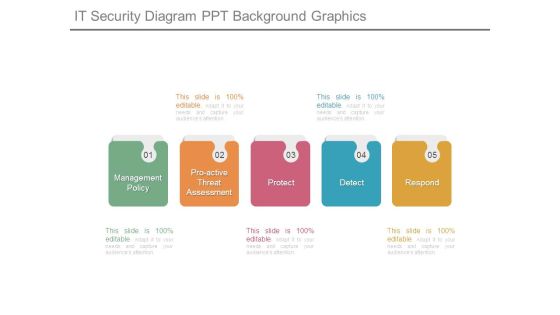
It Security Diagram Ppt Background Graphics
This is a it security diagram ppt background graphics. This is a five stage process. The stages in this process are management policy, proactive threat assessment, protect, detect, respond.

Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
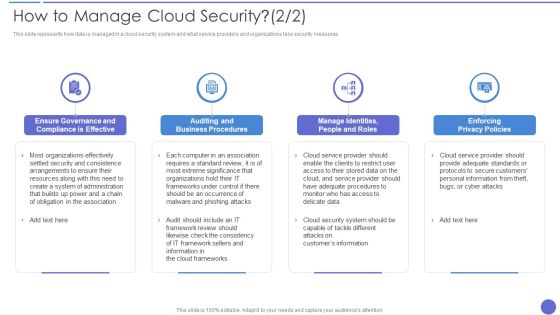
How To Manage Cloud Security Topics PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. This is a How To Manage Cloud Security Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enforcing Privacy Policies, Auditing And Business Procedures, Organizations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Segmentation Of Cloud Security Responsibilities Icons PDF
This slide shows cloud security responsibilities based on service type, namely Software as a Service SaaS, Platform as a service PaaS, Infrastructure as a Service IaaS. Presenting Segmentation Of Cloud Security Responsibilities Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cloud Security Responsibilities, Segmentation, Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Management System Auditing Brochure PDF
The following slide highlights the information security management system audit process illustrating information security system details, information collection, statement o applicability review, audit scope, risk management analysis, gap analysis, business continuity and contingency plan review, mitigation strategy and compliance audit activities PresentingInformation Security Management System Auditing Brochure PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Risk Management Analysis, Information Collection, Mitigation Strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
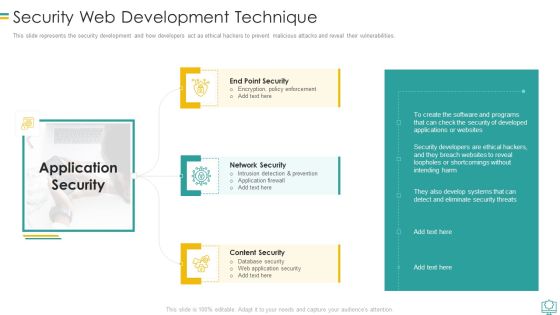
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
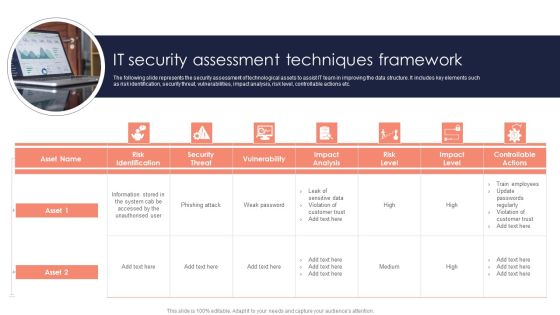
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Management Best Practices Themes PDF
This slide presents various best practices for information security governance to effectively manage and mitigate IT risks. It includes key practices such as reflect business objectives, develop and enforce security program, embrace organizations culture, etc. Presenting Information Security Management Best Practices Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Reflect Business Objectives, Spend Resources Effectively, Embrace Organizations Culture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Network Security Assessment Flowchart Structure PDF
This slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Showcasing this set of slides titled Digital Network Security Assessment Flowchart Structure PDF. The topics addressed in these templates are Account Holder, Information Leak, Network Service Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Assessment Services Sample Diagram Powerpoint Image
This is a security assessment services sample diagram powerpoint image. This is a six stage process. The stages in this process are define scope, agree start date, configuration review, vulnerability scanning, penetration testing, configuration review.

Strategy Of Proactive Security Process Ppt Presentation
This is a strategy of proactive security process ppt presentation. This is a three stage process. The stages in this process are environment scanning, pear networking, result, threat detection, incident response, cyber incident.

Security Policy Process Diagram Layout Ppt Gallery
This is a security policy process diagram layout ppt gallery. This is a five stage process. The stages in this process are executions, commercial bank, customer service assistance, bank office, custodian.
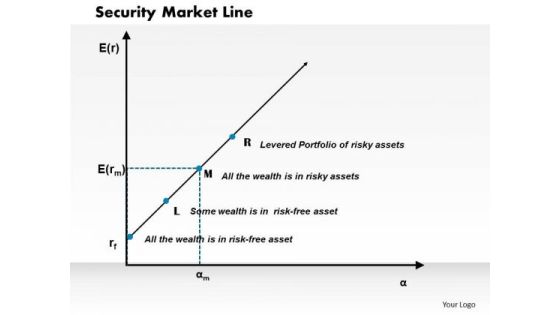
Security Market Line Business PowerPoint Presentation
Document The Process On Our Security Market Line Business Powerpoint Presentation Powerpoint Templates. Make A Record Of Every Detail. Satiate Desires With Our success Powerpoint Templates. Give Them All They Want And More.
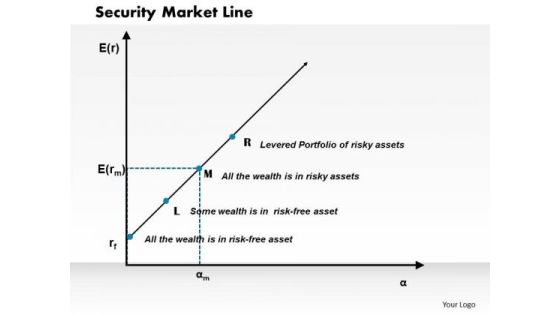
Business Framework Security Market Line PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

Security Of Supply Project Assessment Ppt Slides
This is a security of supply project assessment ppt slides. This is a four stage process. The stages in this process are project assessment, technical resilience, technical aspects, losses variation.
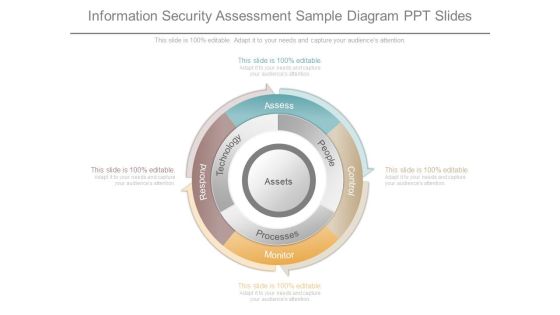
Information Security Assessment Sample Diagram Ppt Slides
This is a information security assessment sample diagram ppt slides. This is a four stage process. The stages in this process are assess, people, processes, technology, respond, monitor, control.
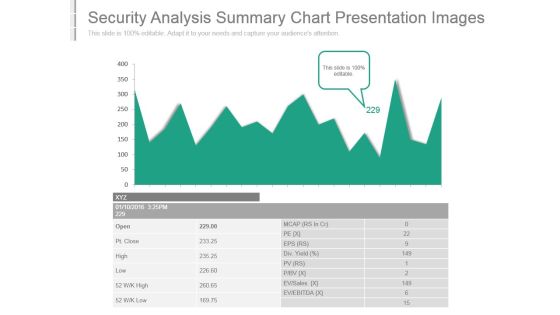
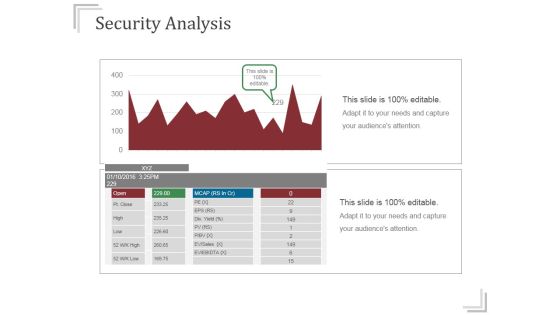
Security Analysis Summary Chart Presentation Images
This is a security analysis summary chart presentation images. This is a one stage process. The stages in this process are ev ebitda, ev sales, div yield, open, pt close, high, low, mcap, eps.

Cyber Security Incident Response Lifecycle Information PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Presenting this PowerPoint presentation, titled Cyber Security Incident Response Lifecycle Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Security Incident Response Lifecycle Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Security Incident Response Lifecycle Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Hybrid Cloud Security Solutions Rules PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy This is a Hybrid Cloud Security Solutions Rules PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Redundancy, Categorization Of Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda For Cloud Data Security Ideas PDF
This is a Agenda For Cloud Data Security Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Responsibilities And Service, Organizations, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
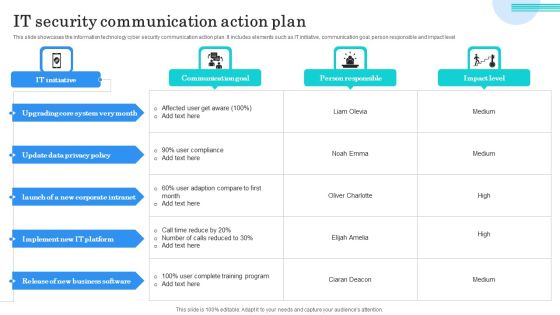
IT Security Communication Action Plan Portrait PDF
This slide showcases the information technology cyber security communication action plan. It includes elements such as IT initiative, communication goal, person responsible and impact level. Showcasing this set of slides titled IT Security Communication Action Plan Portrait PDF. The topics addressed in these templates are Upgrading Core System, Update Data Privacy, Implement IT Platform. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Encryption Ppt PowerPoint Presentation Layouts Cpb
Presenting this set of slides with name security encryption ppt powerpoint presentation layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like security encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
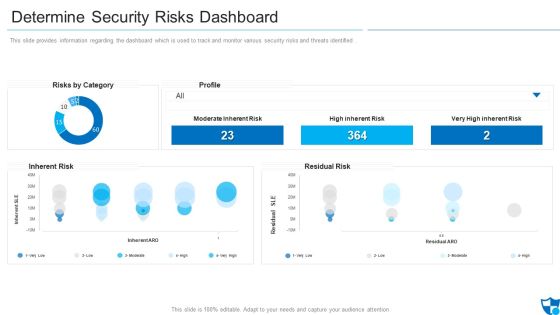
Determine Security Risks Dashboard Introduction PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified.Deliver and pitch your topic in the best possible manner with this determine security risks dashboard introduction pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
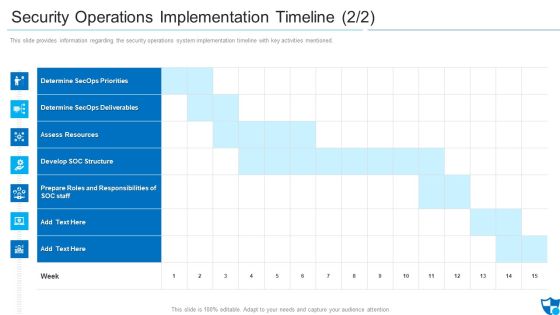
Security Operations Implementation Timeline Assess Diagrams PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned.Deliver and pitch your topic in the best possible manner with this security operations implementation timeline assess diagrams pdf. Use them to share invaluable insights on determine secops priorities, determine secops deliverables, assess resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
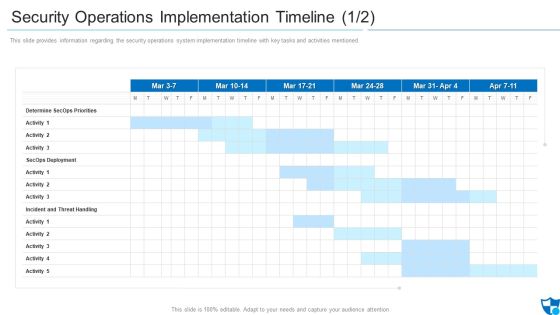
Security Operations Implementation Timeline Priorities Introduction PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned.Deliver an awe inspiring pitch with this creative security operations implementation timeline priorities introduction pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management System Microsoft PDF
The following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Pitch your topic with ease and precision using this cyber security risk management system microsoft pdf. This layout presents information on mapping threats, threat containment and remediation, identify management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
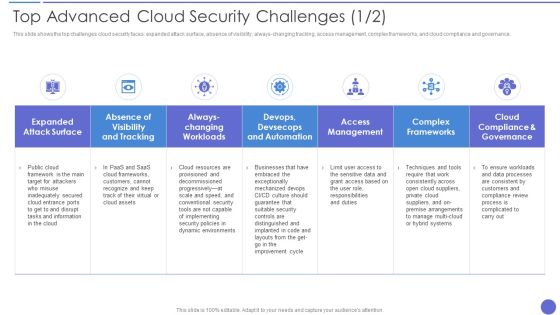
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
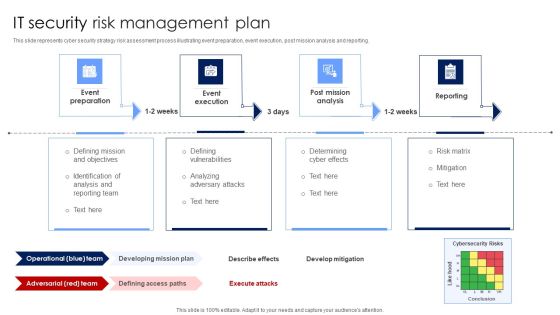
IT Security Risk Management Plan Mockup PDF
This slide represents cyber security strategy risk assessment process illustrating event preparation, event execution, post mission analysis and reporting. Presenting IT Security Risk Management Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Post Mission Analysis, Reporting, Event Execution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
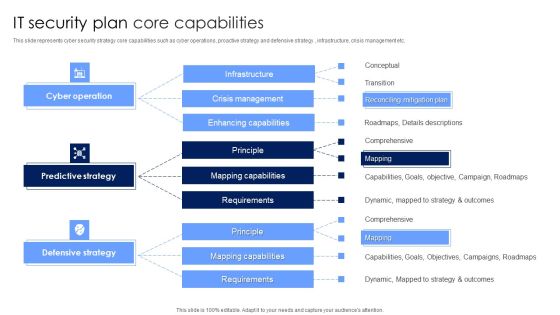
IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
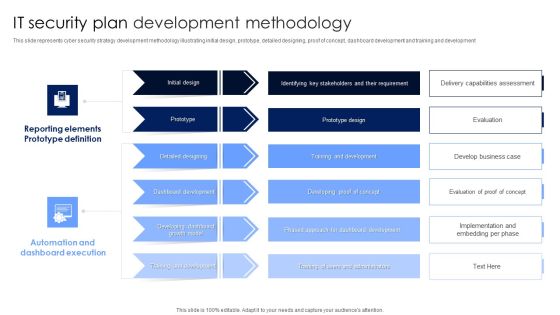
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

RPA Discovery Procedure Security Steps Brochure PDF
Following slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Presenting RPA Discovery Procedure Security Steps Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Bot Actions Accountability, Avoid Errors And Fraud, Secure Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Initiatives Protecting Recruitment Process Elements PDF
This slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Slidegeeks is here to make your presentations a breeze with Security Initiatives Protecting Recruitment Process Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

How Does Cloud Security Work Download PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a How Does Cloud Security Work Download PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Encryption Methods, Secure Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Compliance Violations Demonstration PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state. This is a Cloud Security Threats Compliance Violations Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Businesses, Organizations, Authentication Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Checklist Data Encryption Professional PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Presenting Cloud Security Checklist Data Encryption Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protect Keys, Encrypted Data, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Shared Vulnerabilities Graphics PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. This is a Cloud Security Threats Shared Vulnerabilities Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Could, Organizations, Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Incident Communication Strategy Information PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cyber Security Incident Communication Strategy Information PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cyber Security Incident Communication Strategy Information PDF.

Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
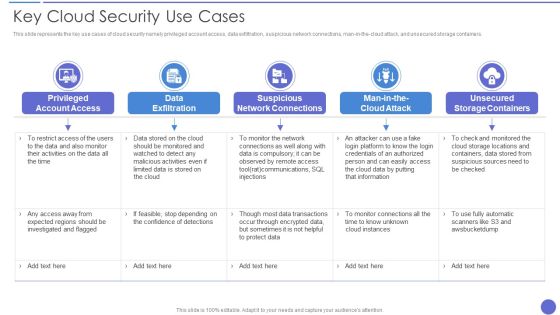
Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Five Year Strategic Timeline Demonstration
We present our cyber security five year strategic timeline demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security five year strategic timeline demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
IT Security Five Years Strategic Timeline Icons
We present our it security five years strategic timeline icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched it security five years strategic timeline icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Strategic Five Year Functional Timeline Graphics
We present our security strategic five year functional timeline graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched security strategic five year functional timeline graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Internet Security Incident Analysis Report Template PDF
This slide exhibits security data breach incident report. It includes multiple steps such as- report the number of personal data record lost, analyze the possible effects of personal data breaches and so on. Showcasing this set of slides titled internet security incident analysis report template pdf. The topics addressed in these templates are data breach details, consequences, measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
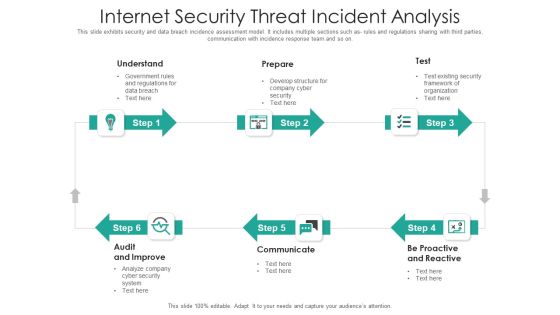
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Threats Malware Attacks Sample PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Security Threats Malware Attacks Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technology, Targets, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Revenue Losses Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Security Threats Revenue Losses Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organizations, Revenue, Investing Money. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Risks Or Threats Brochure PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Security Risks Or Threats Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Malware Attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
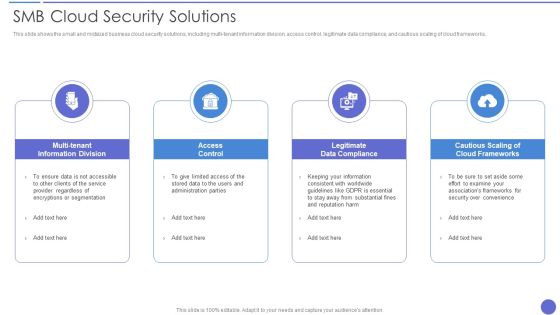
Smb Cloud Security Solutions Download PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. This is a Smb Cloud Security Solutions Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Legitimate Data Compliance, Cloud Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Incident Handling Checklist Elements PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Take your projects to the next level with our ultimate collection of Cyber Security Incident Handling Checklist Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Information Security Management Strategic Model Inspiration PDF
The following slide showcases a framework presenting strategy development and implementation phase in information security governance. It includes key components such as organizational structure, value delivery, strategic alignment, resource optimization, performance measurement, etc. Presenting Information Security Management Strategic Model Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Value Delivery, Key Insights, Organizational Structure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
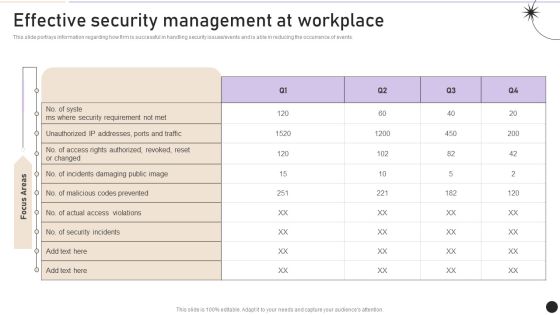
Effective Security Management At Workplace Designs PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present like a pro with Effective Security Management At Workplace Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

 Home
Home