Password Security

Five Years Engineering Roadmap With Security And Compliance Clipart
We present our five years engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five years engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
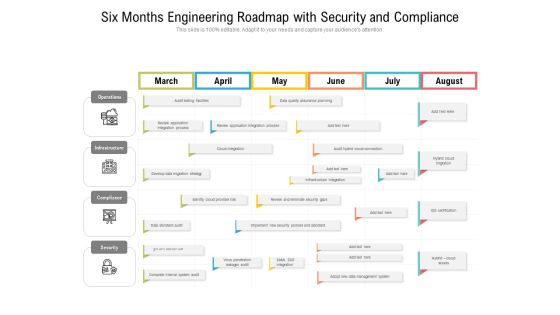
Six Months Engineering Roadmap With Security And Compliance Clipart
We present our six months engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Crisis Program Presentation Risk Management Action Plan Security Inspiration PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Deliver an awe-inspiring pitch with this creative crisis program presentation risk management action plan security inspiration pdf bundle. Topics like potential risk, communication, confidential information security, required resources, data backup team plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Security Five Years Roadmap With Deployment Plan Designs
We present our cloud computing security five years roadmap with deployment plan designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security five years roadmap with deployment plan designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Year Information Technology Security Analytics Improvement Roadmap Infographics
We present our five year information technology security analytics improvement roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year information technology security analytics improvement roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Enterprise Information Technology Security Roadmap Through Identification Summary
We present our half yearly enterprise information technology security roadmap through identification summary. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly enterprise information technology security roadmap through identification summary in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Quarterly Enterprise Information Technology Security Roadmap Through Identification Topics
We present our quarterly enterprise information technology security roadmap through identification topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly enterprise information technology security roadmap through identification topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Enterprise Information Technology Security Roadmap Through Identification Infographics
We present our six months enterprise information technology security roadmap through identification infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise information technology security roadmap through identification infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Three Months Enterprise Information Technology Security Roadmap Through Identification Introduction
We present our three months enterprise information technology security roadmap through identification introduction. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months enterprise information technology security roadmap through identification introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
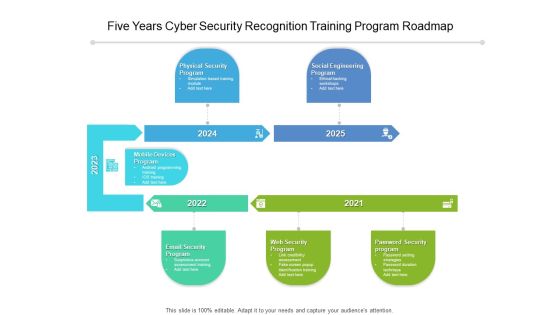
Five Years Cyber Security Recognition Training Program Roadmap Diagrams
We present our five years cyber security recognition training program roadmap diagrams. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five years cyber security recognition training program roadmap diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Cyber Security Recognition Training Program Roadmap Elements
We present our half yearly cyber security recognition training program roadmap elements. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly cyber security recognition training program roadmap elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Cyber Security Recognition Training Program Roadmap Introduction
We present our six months cyber security recognition training program roadmap introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months cyber security recognition training program roadmap introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Three Months Cyber Security Recognition Training Program Roadmap Icons
We present our three months cyber security recognition training program roadmap icons. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched three months cyber security recognition training program roadmap icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
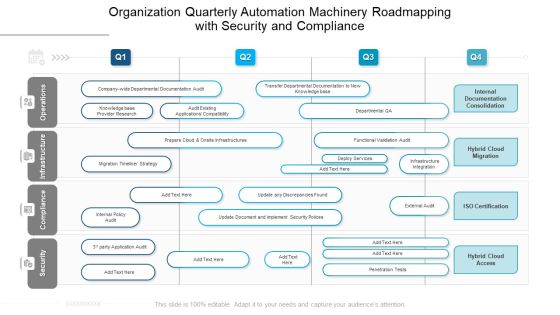
Organization Quarterly Automation Machinery Roadmapping With Security And Compliance Brochure
We present our organization quarterly automation machinery roadmapping with security and compliance brochure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched organization quarterly automation machinery roadmapping with security and compliance brochure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effect After Implementing Cyber Risk Security Awareness Program Professional PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments.This is a effect after implementing cyber risk security awareness program professional pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like lowest mobile malware infections, lowest computer malware infections. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Strategic Process Management Four Quarter Timeline Diagrams
We present our cyber security strategic process management four quarter timeline diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security strategic process management four quarter timeline diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
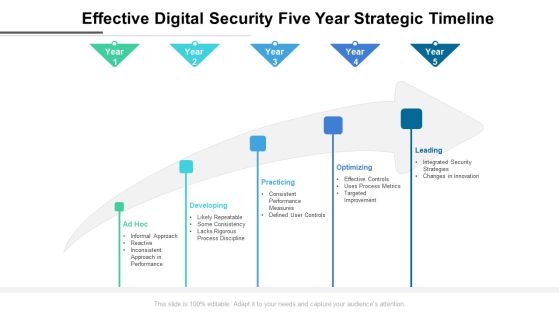
Effective Digital Security Five Year Strategic Timeline Formats
We present our effective digital security five year strategic timeline formats. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched effective digital security five year strategic timeline formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Organizational Security Solutions Analyzing Different SOC Deployment Models Themes PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a organizational security solutions analyzing different soc deployment models themes pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Security Solutions Prerequisites For Effective Secops Implementation Summary PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a organizational security solutions prerequisites for effective secops implementation summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Prerequisites For Effective Secops Implementation Professional PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a security functioning centre prerequisites for effective secops implementation professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development team, operations team, performing, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Months Action Plan Advantage Roadmap For Cyber Security Inspiration
We present our 3 months action plan advantage roadmap for cyber security inspiration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 3 months action plan advantage roadmap for cyber security inspiration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

6 Months Action Plan Advantage Roadmap For Cyber Security Diagrams
We present our 6 months action plan advantage roadmap for cyber security diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 6 months action plan advantage roadmap for cyber security diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Action Plan Advantage Roadmap For Cyber Security Themes
We present our half yearly action plan advantage roadmap for cyber security themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly action plan advantage roadmap for cyber security themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
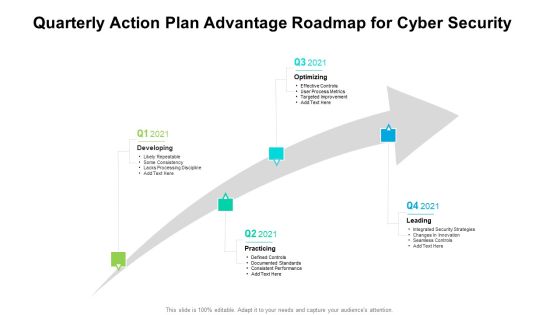
Quarterly Action Plan Advantage Roadmap For Cyber Security Sample
We present our quarterly action plan advantage roadmap for cyber security sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly action plan advantage roadmap for cyber security sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
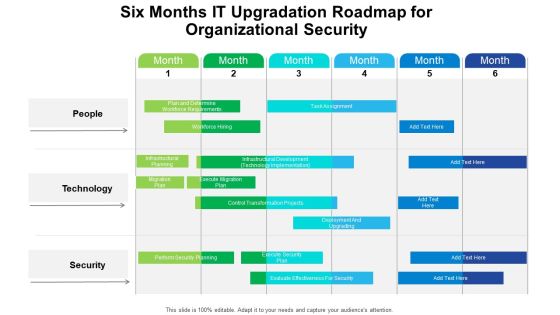
Six Months IT Upgradation Roadmap For Organizational Security Structure
We present our six months it upgradation roadmap for organizational security structure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months it upgradation roadmap for organizational security structure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Information And Event Management Logging Process Structure PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Management System Auditing Process Microsoft PDF
The following slide highlights the information security management system audit methodology illustrating key headings which includes steps and activities, where steps consists of document review, audit review, plan audit, perform audit and reporting Showcasing this set of slides titled Information Security Management System Auditing Process Microsoft PDF. The topics addressed in these templates are Plan Audit, Reporting, Audit Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Smart Home Security Solutions Company Profile Customer Testimonials Formats PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Smart Home Security Solutions Company Profile Customer Testimonials Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Testimonials. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Program To Measure Likelihood Of Impact Topics PDF
This slide represents the information security program to measure likelihood of impact which includes effects, system operationality that will help company to categorize risk level and develop risk mitigation strategies.Pitch your topic with ease and precision using this IT Security Program To Measure Likelihood Of Impact Topics PDF This layout presents information on System Operationality, Uncontrollable Situations, Confidentiality It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

How To Manage Security In Cloud Background PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting How To Manage Security In Cloud Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Firewalls, Access Controls, Data Recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

What Are The Downsides Of A Cloud Security Download PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting What Are The Downsides Of A Cloud Security Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats End User Control Themes PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Security Threats End User Control Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Centralized Data, Customer, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certified Information Systems Security Professional CISSP Examination Details Designs PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. This is a Certified Information Systems Security Professional CISSP Examination Details Designs PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Risk Management, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Camera System Company Profile Customer Testimonials Summary PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Security Camera System Company Profile Customer Testimonials Summary PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Testimonials. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile SWOT Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. This is a Security Camera System Company Profile SWOT Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF
The purpose of this slide is to highlight the security gap analysis of the organization. Information covered in this slide is related to current vs desired state of the company, reasons identified, techniques to be used and the priority level.Deliver an awe inspiring pitch with this creative Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF bundle. Topics like Facing Ransomware, Reasons Identified, Organization Malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Cyber Security Breach General Consequences Ideas PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. This is a Impact Of Cyber Security Breach General Consequences Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reputational Damage, Monetary Penalty, Operational Disruption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Benefits Of Cyber Security Awareness Training Background PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide.This is a Key Benefits Of Cyber Security Awareness Training Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drive Awareness, Reduce Threat, Amongst Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
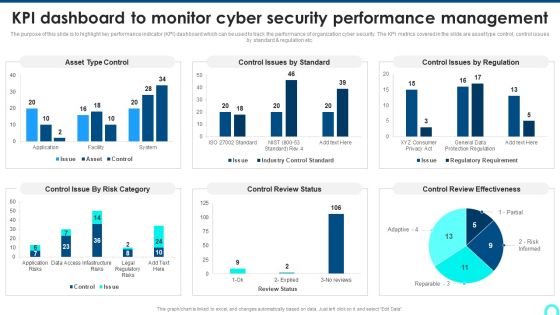
KPI Dashboard To Monitor Cyber Security Performance Management Background PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc.Deliver and pitch your topic in the best possible manner with this KPI Dashboard To Monitor Cyber Security Performance Management Background PDF. Use them to share invaluable insights on Control Issue, Control Review, Review Effectiveness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
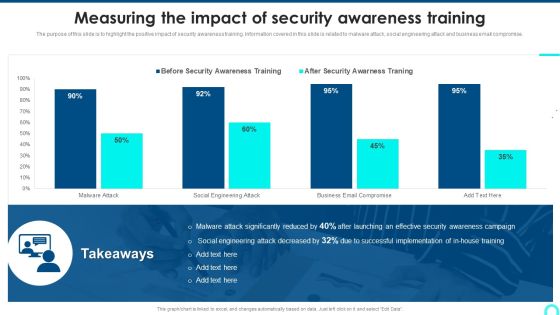
Measuring The Impact Of Security Awareness Training Structure PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Deliver and pitch your topic in the best possible manner with this Measuring The Impact Of Security Awareness Training Structure PDF. Use them to share invaluable insights on Attack Significantly, Awareness Campaign, Social Engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Overview Of Cyber Security Awareness Course Clipart PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This is a Overview Of Cyber Security Awareness Course Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Learning Outcome, Attendees, Course Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Components Of People Centric Work Culture Security Ideas PDF
The following slide highlights the key elements of people centric security to prevent data breaches and IT damages. It includes activities such as personalized training, artificial intelligence AI and machine learning ML tools and prompt social engineering attacks etc. Persuade your audience using this Key Components Of People Centric Work Culture Security Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Personalized Training, Artificial Intelligence, Engineering Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Executive Summary Graphics PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures. This is a Security Agency Business Profile Executive Summary Graphics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Total Revenue, Employees, Customers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Our Business Approach Diagrams PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. This is a Security Agency Business Profile Our Business Approach Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Planning, Participatory Management, Productivity Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Practices To Implement Digitization Of Security Systems Icons PDF
The following slide highlights best practices which can be implemented by firm for digitization of security systems. The major practices are prioritize automation, start with manual playbooks, adopt automation gradually and invest in the training of IT team. Presenting Key Practices To Implement Digitization Of Security Systems Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Prioritize Automation, Start Manual Playbooks, Adopt Automation Gradually. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organization Security Issues And Solution Assessment Ideas PDF
This slide showcases problems in firm related to security of crucial data important for organization. The issues include data breach, SPAM, phishing and insider threat. Persuade your audience using this Organization Security Issues And Solution Assessment Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breach, SPAM And Phishing, Insider Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Dashboard With KPI Metrics Elements PDF
This slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Showcasing this set of slides titled Cyber Security Risk Dashboard With KPI Metrics Elements PDF. The topics addressed in these templates are Vulnerability Management Program, Reports And Metrics Elaboration, Critical Risk Identified. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber IT Security Vulnerability Analysis Checklist Microsoft PDF
This slide contains the checklist of multiple human threats human error, dishonesty, social engineering attacks and general threats with their impact and probability to occur in the business. Persuade your audience using this Cyber IT Security Vulnerability Analysis Checklist Microsoft PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security, Awareness, Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information IT Security Swot Analysis Matrix Clipart PDF
This slide covers the strengths, weaknesses, opportunities and threats analysis of the company. IT showcases how the company is providing security to its client and on which areas they need to work upon. Persuade your audience using this Information IT Security Swot Analysis Matrix Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Opportunities, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Multistep Process Of Security Risk Management Slides PDF
This slide shows multistep process of security risk acceptance which contains identifying risk, summarizing risk and risk acceptance and action. This can assist businesses in understanding the cause and effect of risks. Persuade your audience using this Multistep Process Of Security Risk Management Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Identifying Risk, Summarizing Risk, Risk Acceptance And Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Case Study Mockup PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. This is a Manpower Corporate Security Business Profile Case Study Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Solution, Benefits, The Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Organization Chart Rules PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. This is a Manpower Corporate Security Business Profile Organization Chart Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Operations Supervisor, Audit Team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Crisis Communication Process Framework Icons PDF
This slide showcases a model of crisis communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Presenting Cyber Security Crisis Communication Process Framework Icons PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Implement Strategy, Identify Community, Set Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF
This slide covers cyber security incident response lifecycle model. It involves stages such as prepare, identify, eradicate, contain and recover. Persuade your audience using this Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare, Identify, Contain, Communication, Eradicate, Lessons Learned. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Managing Cyber Security Incident Response Plan Checklist Ppt Picture PDF
This slide covers cyber security incident response plan checklist. It involves pre-requisites such as identify fundamentals, terms and contracts, identify phases, team communication plan and incident response forms. Showcasing this set of slides titled Managing Cyber Security Incident Response Plan Checklist Ppt Picture PDF. The topics addressed in these templates are Identify Fundamentals, Checklist, Terms And Contracts. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Managing Cyber Security Incident Response Plan Ppt Styles Diagrams PDF
This slide covers cyber security incident response plan. It involves activities such as run simulation to train team members, assign tasks, conduct post mortems. Persuade your audience using this Managing Cyber Security Incident Response Plan Ppt Styles Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Assess, Action Plan, Duration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF
This slide covers strategies for efficient cyber security incident management. It involves strategies such as create incident management plan and team, conduct regular training and conduct post incident analysis. Presenting Strategies For Efficient Managing Cyber Security Incident Management Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Incident Management Plan, Create Incident, Response Team, Conduct Regular Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills

Table Of Contents Cyber Security Automation Framework Layer Elements PDF
Find highly impressive Table Of Contents Cyber Security Automation Framework Layer Elements PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Cyber Security Automation Framework Layer Elements PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents IT Security Automation Systems Guide Clipart PDF
Explore a selection of the finest Table Of Contents IT Security Automation Systems Guide Clipart PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Table Of Contents IT Security Automation Systems Guide Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Allocating Budget For Information Security Risk Management Programme Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Allocating Budget For Information Security Risk Management Programme Brochure PDF from Slidegeeks and deliver a wonderful presentation.

Information Technology Security Team Analytics Dashboard With KPI Themes PDF
This slide elaborates about the number of incidents that have taken place in cyber security and the malware types with per incident. It also includes the number of open and resolved ticked. Showcasing this set of slides titled Information Technology Security Team Analytics Dashboard With KPI Themes PDF. The topics addressed in these templates are Open Incidents, Resolved Incidents, Open Tickets, Resolved Tickets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Automation Dashboard Highlighting Resolved Events And Workload Portrait PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security Automation Dashboard Highlighting Resolved Events And Workload Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Assessment Control Measures Slides PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain likely possible unlikely and rare. Showcasing this set of slides titled Cyber Security Risk Assessment Control Measures Slides PDF. The topics addressed in these templates are Cyber Security Risk, Assessment Control Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
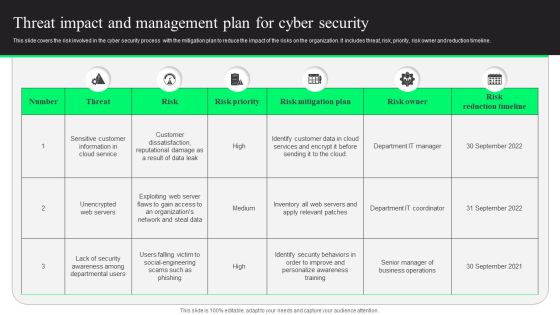
Threat Impact And Management Plan For Cyber Security Designs PDF
This slide covers the risk involved in the cyber security process with the mitigation plan to reduce the impact of the risks on the organization. It includes threat, risk, priority, risk owner and reduction timeline. Showcasing this set of slides titled Threat Impact And Management Plan For Cyber Security Designs PDF. The topics addressed in these templates are Risk Mitigation Plan, Risk Reduction Timeline, Customer Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
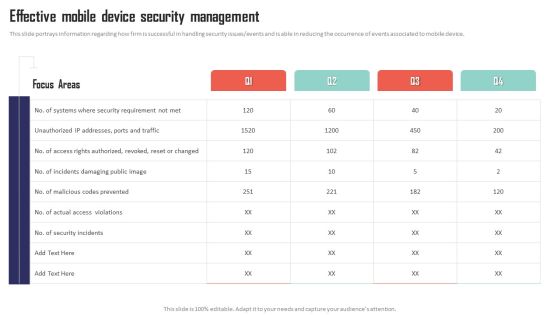
Mobile Device Management Effective Mobile Device Security Management Formats PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Want to ace your presentation in front of a live audience Our Mobile Device Management Effective Mobile Device Security Management Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Agenda For Cyber Physical System To Enhance Security Ideas PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Agenda For Cyber Physical System To Enhance Security Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Agenda For Cyber Physical System To Enhance Security Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Security Incident Response Plan Timeline Mockup PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Incident Response Plan Timeline Mockup PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Table Of Contents For Information Security Law Summary PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Information Security Law Summary PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Information Security Law Summary PDF today and make your presentation stand out from the rest.

Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Role Of Management In Security Governance Across Firm Mockup PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. The Role Of Management In Security Governance Across Firm Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Standards Compliance Traceability Matrix Information PDF
This slide represents the cyber security standards compliance matrix. The purpose of this slide is to demonstrate the various cybersecurity standards and their compliance requirements for businesses. The primary standards include ISO27001, PCI DSS, HIPPA, FINRA and GDPR. Showcasing this set of slides titled Cyber Security Standards Compliance Traceability Matrix Information PDF. The topics addressed in these templates are Standards, Requirements, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Management Risk And Compliance Model Summary PDF
The following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Showcasing this set of slides titled Cloud Security Management Risk And Compliance Model Summary PDF. The topics addressed in these templates are Governance, Risk, Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Business Automated Security Management Framework Professional PDF
This slide showcases a framework of automated security governance for an IT business to safeguard technology infrastructure from risks. It includes key components such as policies, constraints, business rules, analysis, diagnosis, trials, logs, etc. Showcasing this set of slides titled IT Business Automated Security Management Framework Professional PDF. The topics addressed in these templates are Monitor, Direct, Evaluator. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Systems Security And Risk Management Plan Target Formats PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Information Systems Security And Risk Management Plan Target Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Information Systems Security And Risk Management Plan Target Formats PDF today and make your presentation stand out from the rest.
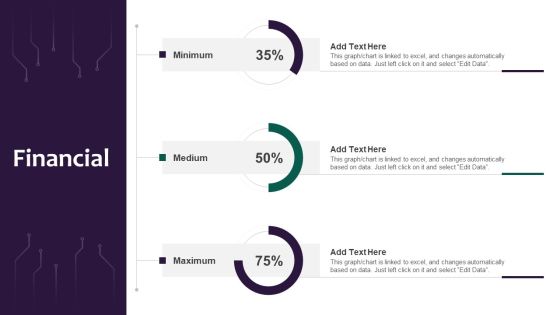
Information Systems Security And Risk Management Plan Financial Professional PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Systems Security And Risk Management Plan Financial Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Systems Security And Risk Management Plan Financial Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Comparative Assessment Of Security Awareness Online Courses Template PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Find a pre-designed and impeccable Comparative Assessment Of Security Awareness Online Courses Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Conducting Cyber Security Gap Analysis Of Organization Formats PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Boost your pitch with our creative Conducting Cyber Security Gap Analysis Of Organization Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Risk Identification And Remediation Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain, likely, possible, unlikel, and rare. Showcasing this set of slides titled Cyber Security Risk Identification And Remediation Matrix Background PDF. The topics addressed in these templates are Cyber Security Risk Identification, Remediation Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Role Of Management In Security Governance Across Firm Elements PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Boost your pitch with our creative Role Of Management In Security Governance Across Firm Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

How Management Enables Effective Corporate Security Governance Graphics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. This modern and well-arranged How Management Enables Effective Corporate Security Governance Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Comparison Analysis Between Security Operations And Devops Inspiration PDF
This slide summarizes the difference between SecOps and DevOps methodologies that increase the efficiency and scalability of complex operations. It includes parameters such as goal, processing strategy, change implementation, focus on, team involved, etc. Showcasing this set of slides titled Comparison Analysis Between Security Operations And Devops Inspiration PDF. The topics addressed in these templates are Implementation, Processing Strategy, Security Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Potential Threats For Smart Phone Security Summary PDF
This slide show various categories of potential risks for phone security that can lead to various type of loss. It include potential risks such as surveillance threat, data theft and financial loss, etc. Persuade your audience using this Key Potential Threats For Smart Phone Security Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Botnet Activities, Impersonation Threats, Financial Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Dashboard For Technological Smart Homes Security System Management Designs PDF
This side showcase the dashboard of security system management for tracking and forecasting matrices for better functioning of devices. It include the statistic data such as temperature, power consumed, devices working, and list of devices connected. Showcasing this set of slides titled Dashboard For Technological Smart Homes Security System Management Designs PDF. The topics addressed in these templates are Smart Light, Smart Heating, Smart Cooling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementing Cyber Security Awareness Training Program Professional PDF
The purpose of this slide is to delineate a comprehensive security awareness training program that can assist corporates to mitigate cyber attacks and reduce downtime. Information covered in this slide is related to training goals, major topics to cover, and projected result. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Awareness Training Program Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Security Implementation Approach Conceptual Structure Professional PDF
Following slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Presenting Cyber Security Implementation Approach Conceptual Structure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State, Evaluation, Target State . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Organizational Assets Security Management Strategy Information PDF
Find highly impressive Table Of Contents Organizational Assets Security Management Strategy Information PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Organizational Assets Security Management Strategy Information PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Addressing Performance Indicators To Determine Security Standards Introduction PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Boost your pitch with our creative Addressing Performance Indicators To Determine Security Standards Introduction PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Budget Analysis For Effective Security Management At Workplace Demonstration PDF
Firm has prepared a budget for managing security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Budget Analysis For Effective Security Management At Workplace Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Table Of Contents For Workplace Security Management Program Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Workplace Security Management Program Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Workplace Security Management Program Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Security Incident Response KPI Dashboard Microsoft PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Slidegeeks has constructed Cyber Security Incident Response KPI Dashboard Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Cyber Security Incidents Follow Up Report Summary PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Take your projects to the next level with our ultimate collection of Cyber Security Incidents Follow Up Report Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Cyber Security Risk Assessment And Management Matrix Inspiration PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Find a pre designed and impeccable Cyber Security Risk Assessment And Management Matrix Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Implementing Cyber Security Incident Management Table Of Contents Clipart PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Management Table Of Contents Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Management Table Of Contents Clipart PDF today and make your presentation stand out from the rest.

Efficient Communication Technique In Cyber Security Mockup PDF
This slide shows communication certain strategies used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person, etc. Showcasing this set of slides titled Efficient Communication Technique In Cyber Security Mockup PDF. The topics addressed in these templates are Date, Communication Objectives, Activity, Mode Of Communication, Accountable Person. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Best Practices To Develop IT Security Communication Plan Diagrams PDF
This slide illustrates various best practices for developing an effective Cyber security communication plan. It includes best practices such as make plan flexible, provide visibility to audience and keep relevant and engaging content. Presenting Best Practices To Develop IT Security Communication Plan Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Make Plan Flexible, Provide Visibility Audience, Keep Relevant Engaging. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
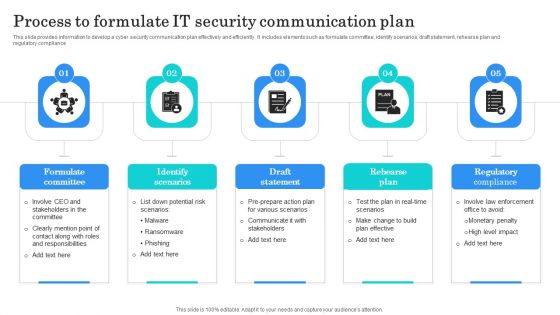
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Qualitative Risk Analysis Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management. This is categorized as certain, likely, possible, unlikely, and rare. Pitch your topic with ease and precision using this Cyber Security Qualitative Risk Analysis Matrix Background PDF. This layout presents information on Risk Matrix, High Severity, Cyber Security Qualitative. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Communication Plan For Cyber Security Attack Summary PDF
This slide consists of an information technology communication plan that can be implemented by managers to safeguard from cyber security attacks and create an effective response plan. Major cyber attack elements covered are malware, phishing, ransomware, etc. Presenting Information Technology Communication Plan For Cyber Security Attack Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Reporting Response, Prevention Measures, Incident Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Communication Channel Selection Plan Template PDF
Following slide consists of a matrix for selecting information technology security communication channels in order to ensure the seamless delivery of key messages to relevant stakeholders. Key content types are detailed messages, notifications, community feeds, documents, etc. Presenting Information Technology Security Communication Channel Selection Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Detailed Message, Notifications, Community Feed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Crisis Communication Plan Checklist Professional PDF
Following slide presents an information technology security crisis communication plan checklist that can be used by information technology managers to ensure the effective preparation of a communication plan. Key elements covered in the checklist are identifying office protocol, creating a list of IT terms, etc. Presenting Information Technology Security Crisis Communication Plan Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Communications Team, Internal Communication Plan, Dissemination Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Website Management Project To Maintain High Security Demonstration PDF
This slide signifies the website development project to increase security. It covers information about project and key activities to be done in every week, month, quarter and year. Presenting Website Management Project To Maintain High Security Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fix broken link, Update plugins, Confirm content. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

3 Key Areas For Document Management Security Controls Ideas PDF
This slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Persuade your audience using this 3 Key Areas For Document Management Security Controls Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cryptography, Practice Guidelines, Attestations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risk Approaches For Security Protection Structure PDF
The following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Showcasing this set of slides titled cyber risk approaches for security protection structure pdf. The topics addressed in these templates are traditional approach, ai based approach, cybersecurity threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computer Security Incident Handling Determining Firm Current Capabilities Inspiration PDF
Presenting this set of slides with name computer security incident handling determining firm current capabilities inspiration pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Collateral Documents Granting Security Ppt PowerPoint Presentation Summary Graphic Tips
Presenting this set of slides with name collateral documents granting security ppt powerpoint presentation summary graphic tips. This is a three stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Collateral Security Document Vector Icon Ppt PowerPoint Presentation Outline Information
Presenting this set of slides with name collateral security document vector icon ppt powerpoint presentation outline information. This is a one stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Collateral Security Papers Icon Ppt PowerPoint Presentation Styles Background
Presenting this set of slides with name collateral security papers icon ppt powerpoint presentation styles background. This is a one stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Home Security Network Icon Ppt PowerPoint Presentation Portfolio Ideas
Presenting this set of slides with name home security network icon ppt powerpoint presentation portfolio ideas. The topics discussed in these slides are communication, teamwork, build network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Organizational Network Security Awareness Staff Learning Comparison Formats PDF
This is a organizational network security awareness staff learning comparison formats pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Security Awareness Staff Learning Financials Portrait PDF
Presenting organizational network security awareness staff learning financials portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Idea Generation Designs PDF
This is a organizational network security awareness staff learning idea generation designs pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like idea generation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Network Security Awareness Staff Learning Location Information PDF
Presenting organizational network security awareness staff learning location information pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like location. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Organizational Network Security Awareness Staff Learning Post It Icons PDF
This is a organizational network security awareness staff learning post it icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Network Security Awareness Staff Learning Venn Summary PDF
Presenting organizational network security awareness staff learning venn summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like venn. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
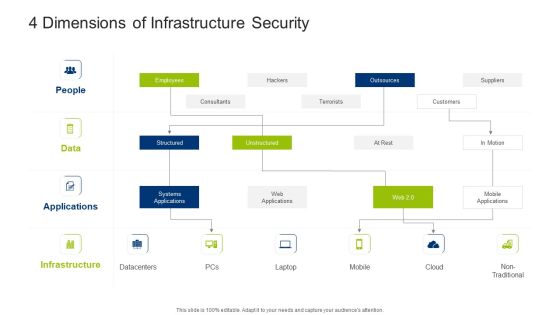
Infrastructure Building Administration 4 Dimensions Of Infrastructure Security Designs PDF
Deliver and pitch your topic in the best possible manner with this infrastructure building administration 4 dimensions of infrastructure security designs pdf. Use them to share invaluable insights on systems applications, structured, unstructured, employees, outsources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Damage Security Insurance Proposal Roadmap Ppt Layouts Infographics PDF
This is a damage security insurance proposal roadmap ppt layouts infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Damage Security Insurance Proposal Timeline Ppt Summary Vector PDF
Presenting damage security insurance proposal timeline ppt summary vector pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2020. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Client Testimonial Ppt Model PDF
This is a damage security insurance proposal client testimonial ppt model pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like client testimonial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Email Security Market Research Report Industry Verticals Retail Icons PDF
Presenting this set of slides with name email security market research report industry verticals retail icons pdf. The topics discussed in these slides are financial service, healthcare, government, accommodations, professionals, manufacturing, retail. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report About Us Ppt Clipart PDF
Presenting this set of slides with name email security market research report about us ppt clipart pdf. This is a three stage process. The stages in this process are target audiences, premium services, value clients. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Effective IT Risk Management Process Information Security Risk Clipart PDF
Deliver and pitch your topic in the best possible manner with this effective it risk management process information security risk clipart pdf. Use them to share invaluable insights on equipment, software application, service denial, valuable information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Loan And Security Agreement Ppt PowerPoint Presentation Icon Images
Presenting this set of slides with name loan and security agreement ppt powerpoint presentation icon images. This is a one stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
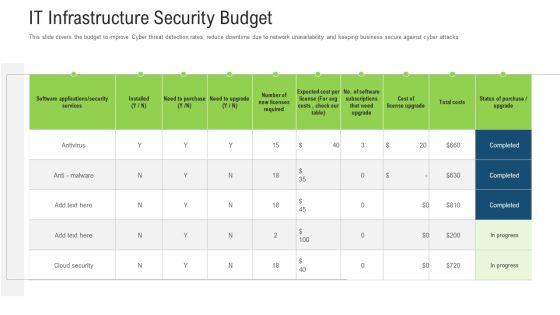
It Infrastructure Security Budget Ppt Outline Mockup PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this it infrastructure security budget ppt outline mockup pdf. Use them to share invaluable insights on services, software, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Security Agreement Operate Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name data security agreement operate ppt powerpoint presentation complete deck. The topics discussed in these slides are operate, data, accountability framework, data privacy, public interest, risk assessment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Employee Benefits Concept Social Security Ppt PowerPoint Presentation Icon Backgrounds
Presenting this set of slides with name employee benefits concept social security ppt powerpoint presentation icon backgrounds. This is a six stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Employee Benefits Concept Social Security Ppt PowerPoint Presentation Outline Show
Presenting this set of slides with name employee benefits concept social security ppt powerpoint presentation outline show. The topics discussed in these slides are business, planning, strategy, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Employee Benefits Template Social Security Ppt PowerPoint Presentation Layouts Guide
Presenting this set of slides with name employee benefits template social security ppt powerpoint presentation layouts guide. This is a eight stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Debentures Security Conversion Ppt PowerPoint Presentation Show Aids
Presenting this set of slides with name debentures security conversion ppt powerpoint presentation show aids. This is a four stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Loan Categories Security Checklist Ppt PowerPoint Presentation Portfolio Examples
Presenting this set of slides with name loan categories security checklist ppt powerpoint presentation portfolio examples. This is a eight stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Ecommerce Challenges Online Security Ppt PowerPoint Presentation Styles Gridlines
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation styles gridlines. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Icon Show
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation icon show. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Employee Benefits Template Social Security Ppt PowerPoint Presentation Slides
Presenting this set of slides with name employee benefits template social security ppt powerpoint presentation slides. This is a five stage process. The stages in this process are agenda, target audiences, preferred by many, values client, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Home Security System Vector Icon Ppt PowerPoint Presentation File Influencers
Presenting this set of slides with name home security system vector icon ppt powerpoint presentation file influencers. This is a four stage process. The stages in this process are iot icon, smartphone vector, headphones. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Formation Of Acquired Entities Security Ppt PowerPoint Presentation Portfolio Images
Presenting this set of slides with name formation of acquired entities security ppt powerpoint presentation portfolio images. This is a four stage process. The stages in this process are formation, entities, business, development, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Vector Icon Ppt PowerPoint Presentation Ideas Example File
Presenting this set of slides with name cyber security vector icon ppt powerpoint presentation ideas example file. This is a one stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Types Of Cyber Security Testing Ppt PowerPoint Presentation Gallery Portfolio
Presenting this set of slides with name types of cyber security testing ppt powerpoint presentation gallery portfolio. This is a three stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Goal Security Analysis And Assessment Ppt PowerPoint Presentation Topics
Presenting this set of slides with name business goal security analysis and assessment ppt powerpoint presentation topics. This is a three stage process. The stages in this process are general outcomes framework, practical level platform, implementation level toolkit and prototypes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Deployment Ppt Professional Tips PDF
Presenting this set of slides with name email security market research report deployment ppt professional tips pdf. The topics discussed in these slides are deployment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Financial Ppt Gallery Deck PDF
Presenting this set of slides with name email security market research report financial ppt gallery deck pdf. This is a three stage process. The stages in this process are minimum, medium, maximum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Key Players Ppt Model PDF
Presenting this set of slides with name email security market research report key players ppt model pdf. The topics discussed in these slides are company name, founded in, headquarters, market share, geographical presence, no of employees. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Email Security Market Research Report Timeline Ppt Styles Good PDF
Presenting this set of slides with name email security market research report timeline ppt styles good pdf. This is a six stage process. The stages in this process are timeline, 2015 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Thesis Process Research Introduction Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name security thesis process research introduction ppt powerpoint presentation complete deck. The topics discussed in these slides are process, research, introduction, interests, conclusions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
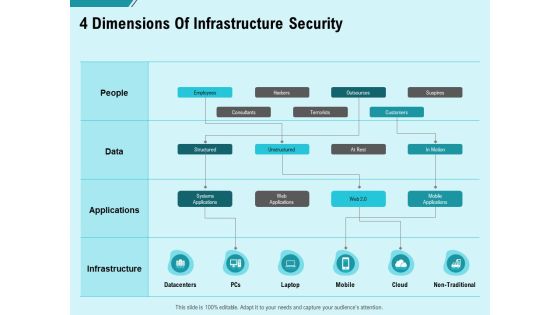
Facility Operations Contol 4 Dimensions Of Infrastructure Security Brochure PDF
Presenting this set of slides with name facility operations contol 4 dimensions of infrastructure security brochure pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Construction Production Facilities 4 Dimensions Of Infrastructure Security Icons PDF
Presenting this set of slides with name construction production facilities 4 dimensions of infrastructure security icons pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Construction Production Facilities Asset Management Lifecycle Security Designs PDF
Presenting this set of slides with name construction production facilities asset management lifecycle security designs pdf. This is a five stage process. The stages in this process are plan, acquire, deploy, retire, manage. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Management Action Plan Graphics PDF
Presenting this set of slides with name computer security incident handling cybersecurity management action plan graphics pdf. The topics discussed in these slides are risk identification, risk treatment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Risk Management Worksheet Ideas PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management worksheet ideas pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Dashboard Cyber Risk Management Download PDF
Presenting this set of slides with name computer security incident handling dashboard cyber risk management download pdf. The topics discussed in these slides are risk rating breakdown, risk heat map, action plan breakdown, risk analysis progress, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Clustered Column Ppt Show Styles PDF
Presenting this set of slides with name computer security incident handling clustered column ppt show styles pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Dashboard Ppt Model Introduction PDF
Presenting this set of slides with name computer security incident handling dashboard ppt model introduction pdf. This is a three stage process. The stages in this process are minimum, medium, maximum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Financial Ppt Portfolio Pictures PDF
Presenting this set of slides with name computer security incident handling financial ppt portfolio pictures pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Our Mission Ppt Styles Slides PDF
Presenting this set of slides with name computer security incident handling our mission ppt styles slides pdf. This is a three stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Our Team Ppt Model Files PDF
Presenting this set of slides with name computer security incident handling our team ppt model files pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Thank You Ppt Summary Designs PDF
Presenting this set of slides with name computer security incident handling thank you ppt summary designs pdf. This is a one stage process. The stages in this process are thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Essential Contingency Plan Strategies Ideas PDF
Presenting this set of slides with name computer security incident handling essential contingency plan strategies ideas pdf. The topics discussed in these slides are contingency considerations, contingency solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Recovery Task List Maintenance Background PDF
Presenting this set of slides with name computer security incident handling recovery task list maintenance background pdf. The topics discussed in these slides are task no., task description, estimated time, actual time, assigned to, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Timeframe For Incident Management Infographics PDF
Presenting this set of slides with name computer security incident handling timeframe for incident management infographics pdf. The topics discussed in these slides are incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Vital Records Maintenance Register Icons PDF
Presenting this set of slides with name computer security incident handling vital records maintenance register icons pdf. The topics discussed in these slides are primary location of records, alternate location of records, other sources to obtain records. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
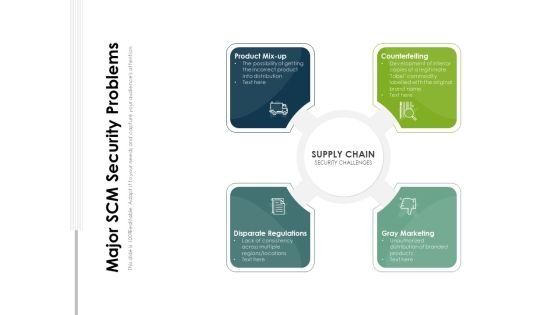
Major SCM Security Problems Ppt PowerPoint Presentation File Grid PDF
Presenting this set of slides with name major scm security problems ppt powerpoint presentation file grid pdf. This is a four stage process. The stages in this process are disparate regulations, gray marketing, counterfeiting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Dashboard Ppt Gallery Template PDF
Presenting this set of slides with name cyber security implementation framework dashboard ppt gallery template pdf. This is a three stage process. The stages in this process are minimum, medium, maximum. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Financial Ppt Slides Good PDF
Presenting this set of slides with name cyber security implementation framework financial ppt slides good pdf. This is a three stage process. The stages in this process are revenue, deposits, net income. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Present Concerns Impeding Cybersecurity Clipart PDF
Presenting this set of slides with name cyber security implementation framework present concerns impeding cybersecurity clipart pdf. The topics discussed in these slides are data breaches and records exposed, reported financial losses due to increase cybercrimes, financial losses, cybercrimes incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home