Password Security

Role Of Management In Effective Information Security Governance Rules PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Role Of Management In Effective Information Security Governance Rules PDF bundle. Topics like Senior Executives, Steering Committees, Chief Information Security Officer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Crisis Management Team Rules PDF
This slide highlights the security company crisis management team which includes general manager, guard supervisor, mobile response team manpower and equipment Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Crisis Management Team Rules PDF bundle. Topics like Team Driver, Security Guards, Equipment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
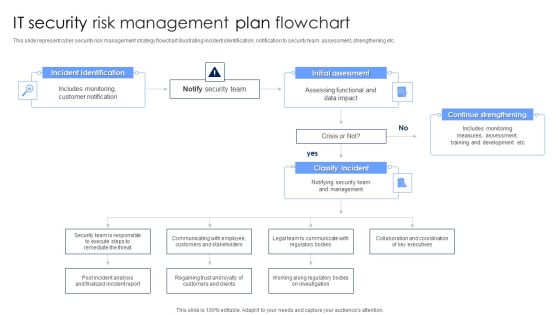
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
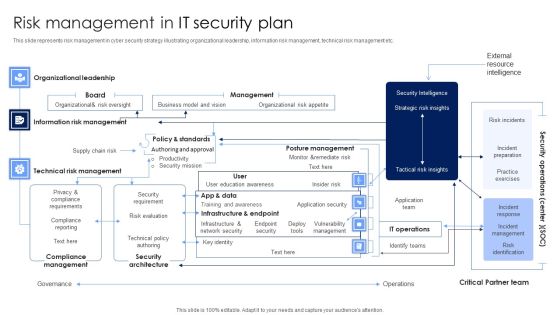
Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. There are so many reasons you need a IT Risk Management Framework To Manage Security Threats Background PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Addressing Compliance Classes In Iot Security Framework Ppt Icon Smartart
This slide provides information regarding different compliance classes in IoT security framework catering different security objective. Find a pre designed and impeccable Addressing Compliance Classes In Iot Security Framework Ppt Icon Smartart. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF
The slide showcases the key difference between cyber security and cyber resilience. It compares on the basis of aspects like definition, focus, function and requirement. Showcasing this set of slides titled Comparative Analysis Of Cyber Risk Prevention And Security Themes PDF. The topics addressed in these templates are Cyber Security, Cyber Resilience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Application Security Architecture Framework Elements PDF
The slide shows a framework describing security architecture to meet organizational unique requirements. It includes setting goals, determining process, constructing architecture and reviewing and revising security model. Showcasing this set of slides titled Cloud Computing Application Security Architecture Framework Elements PDF. The topics addressed in these templates are Set Goals, Determine Process, Construct Architecture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Companys Data Safety Recognition Security Awareness Training Roadmap Themes PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a companys data safety recognition security awareness training roadmap themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical security, data security, personal information, privacy threats, practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Organizational Network Staff Learning Security Awareness Tracking Kpis Demonstration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a organizational network staff learning security awareness tracking kpis demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Private Security Service Provider Company Summary Report Clipart PDF
This slide provide information of firm providing security services to safeguards life of human beings who are facing threats. It includes elements such as about, category, services, company stats, packages, our service benefits. Pitch your topic with ease and precision using this Private Security Service Provider Company Summary Report Clipart PDF. This layout presents information on Provide World, Security Guard, Security Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strategies For Safety And Security In Hotel Industry Sample PDF
This slide outlines measures to ensure safety and security in hospitality sectors. It highlights four basic ways i.e. cyber security, add intelligence to video surveillance, internal theft and fraud and establish evergreen background screening protocol.Persuade your audience using this Strategies For Safety And Security In Hotel Industry Sample PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Internal Theft And Fraud, Establish Evergreen Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
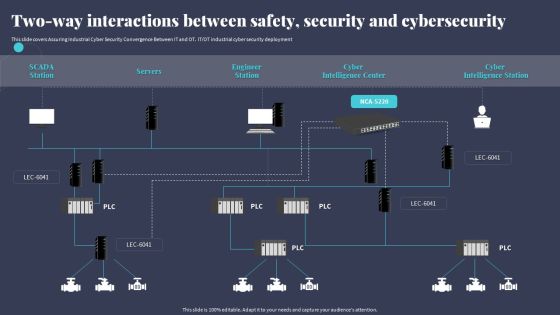
Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. ITOT industrial cyber security deployment. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Companys Data Safety Recognition Security Awareness Tracking Kpis Ideas PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a companys data safety recognition security awareness tracking kpis ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, incident reduction, security culture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Business Driven Security Architecture Introduction PDF
The slide shows a security framework of business driven services. It highlight cloud computing services such as SaaS, PaaS and IaaS and security services such as data security management, software and service assertion, technical service control, risk management infrastructure management, etc. Showcasing this set of slides titled Cloud Computing Business Driven Security Architecture Introduction PDF. The topics addressed in these templates are Strategies, Delegation Authority, Service Goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Impact Of Security Awareness Training Ppt Inspiration Design Templates PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt inspiration design templates pdf. Use them to share invaluable insights on impact of security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
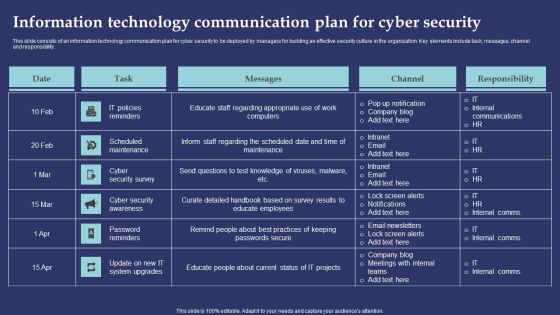
Information Technology Communication Plan For Cyber Security Information PDF
This slide consists of an information technology communication plan for cyber security to be deployed by managers for building an effective security culture in the organization. Key elements include task, messages, channel and responsibility. Showcasing this set of slides titled Information Technology Communication Plan For Cyber Security Information PDF. The topics addressed in these templates are IT Policies Reminders, Scheduled Maintenance, Cyber Security Survey. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Bar Chart Representing Security Incident Strategic Action Plan Themes PDF
This slide shows the graphical presentation of security incident response plan which covers the effectiveness of response plan strategies such as hiring skilled employees, engaging security service providers, improving governance practices, etc. Showcasing this set of slides titled bar chart representing security incident strategic action plan themes pdf. The topics addressed in these templates are bar chart representing security incident strategic action plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Awareness Program Checklist Ppt Model Graphics Design PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness.Presenting security awareness program checklist ppt model graphics design pdf. to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating the security awareness program, implementing security awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Chain And Person Security PowerPoint Templates And PowerPoint Themes 0612
Chain And Person Security PowerPoint Templates And PowerPoint Themes 0612-Microsoft Powerpoint Templates and Background with human character person and a chain

Security Analysis Ppt PowerPoint Presentation Infographic Template Shapes
This is a security analysis ppt powerpoint presentation infographic template shapes. This is a one stage process. The stages in this process are open, high, low, sales, ebidta.

Thank You Computer Security Ppt PowerPoint Presentation Outline Guidelines
This is a thank you computer security ppt powerpoint presentation outline guidelines. This is a one stage process. The stages in this process are thank you.
Thank You It Security Ppt PowerPoint Presentation Outline Infographics
This is a thank you it security ppt powerpoint presentation outline infographics. This is a one stage process. The stages in this process are thank you.
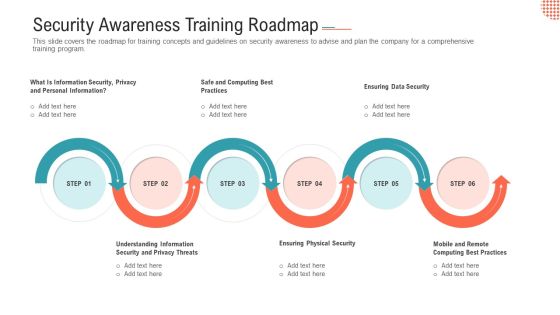
Security Awareness Training Roadmap Ppt Layouts Layouts PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program.Presenting security awareness training roadmap ppt layouts layouts pdf. to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like safe and computing best practices, ensuring data security, ensuring physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Breach Prevention Recognition Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a data breach prevention recognition security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
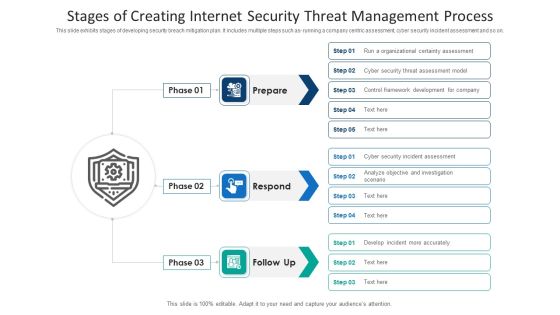
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Current Security Management Challenges The Company Is Facing Elements PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.This is a Current security management challenges the company is facing elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, employee management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Measures And Ways To Mitigate Security Management Challenges Structure PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.This is a Measures and ways to mitigate security management challenges structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, weak links in the supply chain. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operations Management Skills Software Security Skills Pictures PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Presenting operations management skills software security skills pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Security Of Employees Devices Ppt Styles Graphic Images PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. This is a cybersecurity security of employees devices ppt styles graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security of employees devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Technology Skills Gap Analysis Priorities Clipart PDF
This slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Showcasing this set of slides titled cyber security technology skills gap analysis priorities clipart pdf. The topics addressed in these templates are cyber security technology skills gap analysis priorities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
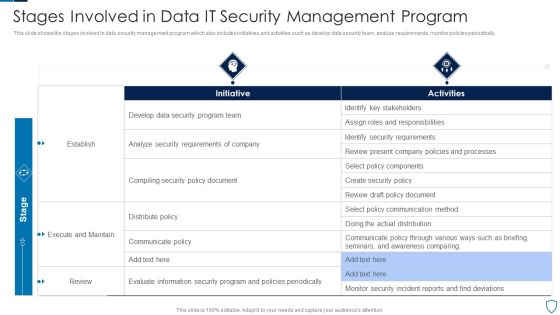
Stages Involved In Data IT Security Management Program Diagrams PDF
This slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically.Pitch your topic with ease and precision using this Stages Involved In Data IT Security Management Program Diagrams PDF This layout presents information on Identify Stakeholders, Security Requirements, Execute Maintain It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Checklist Policies And Procedures Rules PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. This is a Cloud Security Checklist Policies And Procedures Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Organization, Security Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it nowC

Pillars Of Cloud Security Visibility And Consistency Demonstration PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Presenting Pillars Of Cloud Security Visibility And Consistency Demonstration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Best Cloud Framework, Data Security, Asset Inventory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Camera System Company Profile Our Expertise Pictures PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Security Camera System Company Profile Our Expertise Pictures PDF template with various stages. Focus and dispense information on Eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Internet Protocol, Physical Security, Communication Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Organization Chart Topics PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. This is a Security Agency Business Profile Organization Chart Topics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operations Supervisor, Security Personnel, Relief Security Personnel. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF
The following slide shows cyber analytics dashboard to monitor and inspect threats and accordingly plan preventive actions. It includes open and resolved incidents and tickets. Pitch your topic with ease and precision using this Cyber Security Team Analytics Dashboard With KPI Metrics Icons PDF. This layout presents information on Energy Security Team, Digital Security Center, Security Operations Center. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Security Policy In Business Organization Download PDF
This slide depicts the IT security policies that shape organizations preparedness and response to security incidents within the organization. Certain policies include acceptable, use policy, access control policy, security training policy, incident response policy, and remote access policy. Presenting Information Technology Security Policy In Business Organization Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Access Control Policy, Acceptable Use Policy, Remote Access Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Current State Of Security Automation With Projected Development Icons PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation.Want to ace your presentation in front of a live audience Our Current State Of Security Automation With Projected Development Icons PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF
This slide covers prioritization matrix for cyber security based on risk, cost, value and efforts. It includes actions such as recommendations to analyst, security solution designing, security tools selection, team trainings, etc.Presenting Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Tool Recommendations, Design Process, Team Trainings. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Operations Team Roles And Responsibilities Infographics PDF
This slide exhibits key roles on the SecOps team with their roles and responsibilities that manage cybersecurity threats and attacks. It includes a security investigator, advanced security analyst, SOC manager, and security manager. Presenting Security Operations Team Roles And Responsibilities Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Skills Required, Determine, Develop Mitigation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Applications Of AI In Cyber Security Infographics PDF
This slide signifies the software of artificial intelligence to increase cyber security. It covers information about applications like system security, crime prevention, analyse mobile endpoints and detection of cyber attacks Presenting Applications Of AI In Cyber Security Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Iot Systems Security, Crime Prevention, Analyse Mobile Endpoints. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Addressing Role Of Chief Security Officer At Workplace Clipart PDF
This slide provides information regarding role of chief security officer at workplace and determine their key priorities in terms of day to day operations, security, compliance, innovation, etc. Create an editable Addressing Role Of Chief Security Officer At Workplace Clipart PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Addressing Role Of Chief Security Officer At Workplace Clipart PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Comparative Assessment Of Hotel Protection And Security Solutions Mockup PDF
This slide covers comparative assessment of hotel safety and security solutions. It involves parameters of comparison such as anti slip solution, fire retarder, anti theft, test alarms and cost involved. Persuade your audience using this Comparative Assessment Of Hotel Protection And Security Solutions Mockup PDF This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Comparative Assessment, Hotel Protection, Security Solutions Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
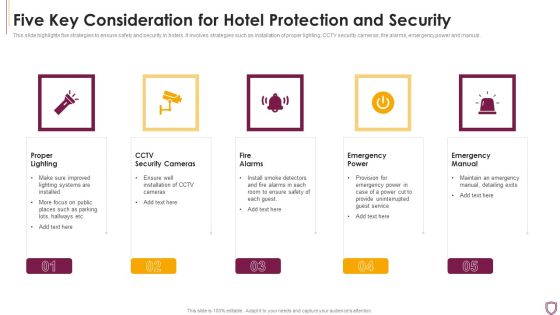
Five Key Consideration For Hotel Protection And Security Infographics PDF
This slide highlights five strategies to ensure safety and security in hotels. It involves strategies such as installation of proper lighting, CCTV security cameras, fire alarms, emergency power and manual.Presenting Five Key Consideration For Hotel Protection And Security Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Emergency Power, Emergency Manual, Proper Lighting This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Protect Risk Security Umbrella Icon Ppt PowerPoint Presentation Infographics Show
This is a protect risk security umbrella icon ppt powerpoint presentation infographics show. This is a four stage process. The stages in this process are risk management, governance icon, compliance icon.
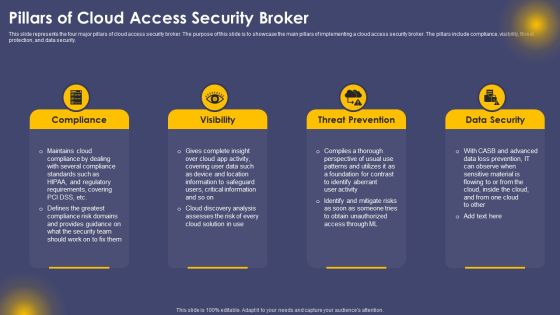
Pillars Of Cloud Access Security Broker Ppt Show Background PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Pillars Of Cloud Access Security Broker Ppt Show Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Pillars Of Cloud Access Security Broker Ppt Show Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Icon For Implementation Of Complete Digital Security Network Professional PDF
Presenting Icon For Implementation Of Complete Digital Security Network Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon For Implementation, Complete Digital Security Network. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
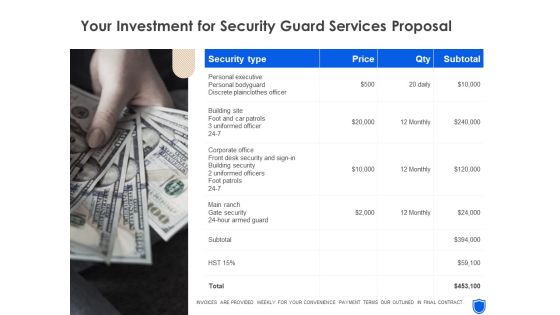
Your Investment For Security Guard Services Proposal Topics PDF
Deliver an awe-inspiring pitch with this creative your investment for security guard services proposal topics pdf bundle. Topics like your investment, security guard services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Sample Of Internet Of Things Security Ppt Sample Ppt Files
This is a sample of internet of things security ppt sample ppt files. This is a five stage process. The stages in this process are personalized information service intelligent transportation environmental monitoring, cloud computing intelligent computing, interest mobile communication network satellite nets, network infrastructure and communication protocols, supports layer, network layer, perceptual layer, application layer, network security management, rfid reader sensor gpb.

Network Cloud Network Security Analysis Icon Icons PDF
Persuade your audience using this Network Cloud Network Security Analysis Icon Icons PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Network Cloud, Network Security, Analysis Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home