Password Security

Infographics Option Banner With Umbrella Powerpoint Templates
Who doesn?t want to have a secure life? Be it financial security, safety of your child or safe environment at home and at work place. Well we hope for that but we can definitely save you from making ugly PowerPoint presentations. Above is the slide which is of umbrella with four options and along with it are four icons. This slide is one of our most downloaded PowerPoint slides and can be used to depict safety and security of any kind. The umbrella here can be used to indicate the safety, security, protection so you can choose this slide to show why it is safe to be associated with your company, or with your business, with your school, how your money is safe and secured in your bank or how it is safe if you pay online and much more. It is a multipurpose slide and can easily be modified as you want. Choose this slide to make your PowerPoint presentation look even more fantastic.

Challenges And Solutions Regarding Digital Transformation In Banking Introduction PDF
This slide shows major challenges regarding digital transformation in banking such as securing media communications, drifting away from legacy applications, security issues, eliminating silos etc. along with relative solutions. This is a challenges and solutions regarding digital transformation in banking introduction pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like securing, media, communications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF
This slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Showcasing this set of slides titled Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF. The topics addressed in these templates are Compromise On Business, Cloud Configurations, Weak Passwords. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF
This slide covers business security assurance and maintenance lifecycle vulnerability management ,policy management and operational monitoring.Showcasing this set of slides titled Business Information Protection Assurance And Maintenance Lifecycle Brochure PDF. The topics addressed in these templates are Encrypting Communication, Detecting Suspicious, Authentication Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

KPI Dashboard To Track Enterprise Information Protection Topics PDF
This slide shows key performance indicator dashboard which can be used by organizations to monitor business information protection. It includes metrics such as compliance, project protection, stimulating projects, etc. Showcasing this set of slides titled KPI Dashboard To Track Enterprise Information Protection Topics PDF. The topics addressed in these templates are Security Projects, Projects Sustainability, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Aligning Business Information Protection Program Action Structure PDF
This slide covers aligning business security program action which includes direct product evaluation participation and impact analysis.Showcasing this set of slides titled Aligning Business Information Protection Program Action Structure PDF. The topics addressed in these templates are Setting Priorities, Assets Stakeholders, Decision Making. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Information Resource Protection With Policy Compliance Information PDF
This slide covers business resource security with policy compliance which includes user group, roles and permissions. Showcasing this set of slides titled Business Information Resource Protection With Policy Compliance Information PDF. The topics addressed in these templates are Product Designer, Organization Manage, Resource Manage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
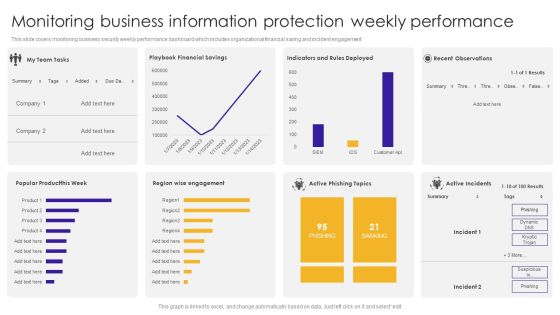
Monitoring Business Information Protection Weekly Performance Summary PDF
This slide covers monitoring business security weekly performance dashboard which includes organizational financial saving and incident engagement. Pitch your topic with ease and precision using this Monitoring Business Information Protection Weekly Performance Summary PDF. This layout presents information on Active Phishing, Active Incidents, Recent Observations. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
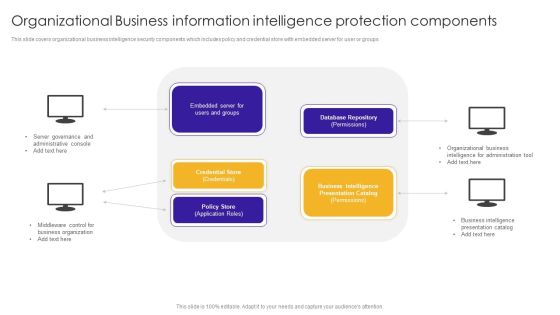
Organizational Business Information Intelligence Protection Components Background PDF
This slide covers organizational business intelligence security components which includes policy and credential store with embedded server for user or groups. Presenting Organizational Business Information Intelligence Protection Components Background PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Administrative Console, Server Governance, Middleware Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF
This slide covers business strategy and attributes mapping for security controls which includes mapping business requirements, evaluating risk and product with service mapping. Showcasing this set of slides titled Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF. The topics addressed in these templates are Major Identification, Service Mapping, Recommendation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Information And Application Layers With Protection And Encryption Brochure PDF
This slide covers business application layers with security and encryption with data access logic, presentation logic and business logic.Pitch your topic with ease and precision using this Business Information And Application Layers With Protection And Encryption Brochure PDF. This layout presents information on Organizational Service, Components Duration, Operating System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Enhanced Protection Corporate Event Administration Essential Roles And Responsibilities Involved In Secops Guidelines PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration essential roles and responsibilities involved in secops guidelines pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
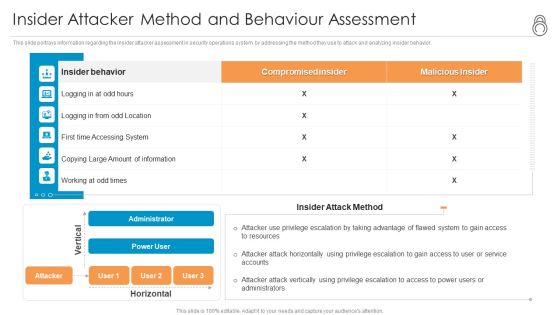
Enhanced Protection Corporate Event Administration Insider Attacker Method And Behaviour Assessment Topics PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration insider attacker method and behaviour assessment topics pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CASB Vs CSPM Vs CWPP Ppt PowerPoint Presentation File Infographics PDF
This slide describes the difference between cloud access security broker CASB, cloud security posture management CSPM, and cloud workload protection platforms CWPP. The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CASB Vs CSPM Vs CWPP Ppt PowerPoint Presentation File Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CASB Vs CSPM Vs CWPP Ppt PowerPoint Presentation File Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Data Governance IT Why Is Data Stewardship Important Formats PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Are you searching for a Data Governance IT Why Is Data Stewardship Important Formats PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Data Governance IT Why Is Data Stewardship Important Formats PDF from Slidegeeks today.

Why Is Data Stewardship Important Sample PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Slidegeeks has constructed Why Is Data Stewardship Important Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Information Technology Expenditure Summary Dashboard Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. This Information Technology Expenditure Summary Dashboard Ppt PowerPoint Presentation Diagram Graph Charts PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF
The following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Conduct Third Party Risk Assessment Ppt PowerPoint Presentation File Ideas PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Business Strategy Marketing PowerPoint Templates And PowerPoint Themes 1112
We present our Business Strategy Marketing PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, Discuss each one and slowly but surely move up the pyramid narrowing down to the best and most success oriented project. Use our Success PowerPoint Templates because, Profit fairly earned is what you believe in. Use our Business PowerPoint Templates because,Marketing Strategy Business Template:- Maximising sales of your product is the intended destination. Use our Finance PowerPoint Templates because, Sales Template:- Generation of sales is the core of any business. Use our Marketing PowerPoint Templates because,There are so many different pieces to the puzzle.Use these PowerPoint slides for presentations relating to Strategy gold key, security, success, business, finance, marketing. The prominent colors used in the PowerPoint template are Orange, Yellow, Black

Functioning Of Serverless Computing Serverless Technology Industry Trends Ppt Portfolio Example Topics PDF
Purpose of the following slide is to display multiple trends that will effect the global serverless computing market, these trends can be emergence of new testing tools, new server security tools and easy monitoring software. This is a functioning of serverless computing serverless technology industry trends ppt portfolio example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like new testing tools, server security tools, easy monitoring software, better software that analyze and monitor multiple application running, serverless computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Where The Company Will Use Its Funds Virtual Currency Financing Pitch Deck Topics PDF
The slide provides the details about use of fund which the company will raise from ICO Initial Coin Offering. The company spend its funding amount on website and app development new technology and security expansions etc. Presenting where the company will use its funds virtual currency financing pitch deck topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like expansion in new countries and increase number of partners, website and app development, other uses team development, new hiring, promotion activities etc, new technology and security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Six Focus Areas To Be Prioritized In Healthcare Sector Ppt Outline Icon PDF
This slide covers the six areas which must be prioritized in healthcare sector such as virtual workforce, extraordinary scaling, security and compliance, power care operations, digital solutions, and technological roles. Presenting six focus areas to be prioritized in healthcare sector ppt outline icon pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like enable virtual workforce, scale extraordinary circumstances, establish elastic security and compliance, power care and operations with better insight, enable new digital and virtual care solutions, elevate role technology. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Investor Pitch Deck To Generate Capital From Initial Currency Offering Where The Company Will Use Its Funds Summary PDF
The slide provides the details about use of fund which the company will raise from ICO Initial Coin Offering The company spend its funding amount on website and app development new technology and security expansions etc.This is a investor pitch deck to generate capital from initial currency offering where the company will use its funds summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like website and app development, new technology and security, expansion in new countries and increase number of partners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
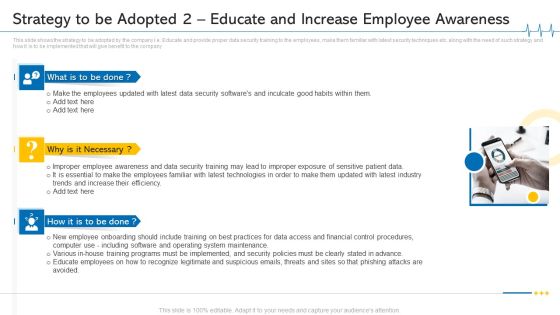
Strategy To Be Adopted 2 Educate And Increase Employee Awareness Ppt Pictures File Formats PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness ppt pictures file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technologies, financial control procedures, operating system maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
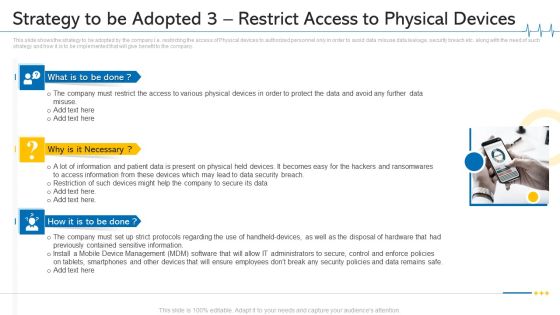
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 3 Restrict Access To Physical Devices Ideas PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. This is a minimize cloud risks medical care business case competition strategy to be adopted 3 restrict access to physical devices ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mobile device management, data security breach, physical devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Inspiration PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Infographics PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 2 educate and increase employee awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Execute Operational Procedure Plan Steps In Detail Developing An Implementation Plan And Timeline Pictures PDF
This slide provides information about the Fifth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline.This is a execute operational procedure plan steps in detail developing an implementation plan and timeline pictures pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation plan, stakeholders to define, identify problem to be solved. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps In Detail Formats PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e Monitoring and Optimization. This is a operational efficiency execution strategy improve quality operational process improvement plan steps in detail formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performance, process optimization, implementation costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
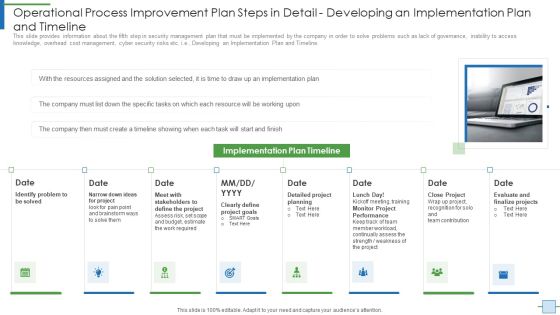
Operational Process Improvement Plan Steps In Detail Developing An Implementation Brochure PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Developing an Implementation Plan and Timeline. This is a operational process improvement plan steps in detail developing an implementation brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project, budget, risk, required, goals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
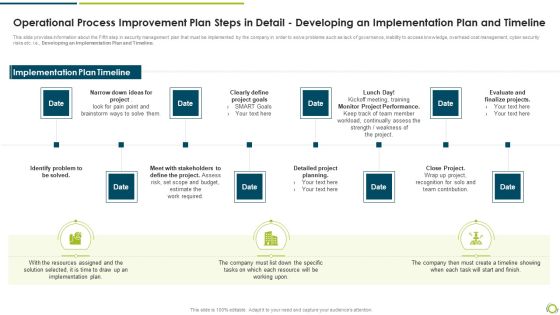
Operational Process Improvement Plan Steps In Detail Developing An Implementation Plan And Timeline Demonstration PDF
This slide provides information about the Fifth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline.This is a operational process improvement plan steps in detail developing an implementation plan and timeline demonstration pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identify problem to be solved, clearly define project goals, monitor project performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Developing An Implementation Plan And Timeline Sample PDF
This slide provides information about the Fifth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline. This is a operational process improvement plan steps in detail developing an implementation plan and timeline sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like resources, implementation plan, project, goals, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Process Analysis Microsoft PDF
This slide provides information about the second and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. This is a operational process improvement plan steps in detail process analysis microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like analysis process, resources, deploying, implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Management At Workplace Threat Management Action Plan Responsible Person Template PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Monitoring Plan Steps In Detail Aligning The Incident Management Policies Sample PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Presenting cybersecurity monitoring plan steps in detail aligning the incident management policies sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security monitoring solutions, ongoing management, incident logging, incident categorization, incident prioritization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Debt Retrieval Techniques Detailed Analysis Of Debt Collection Process Ppt Pictures Layout Ideas PDF
Purpose of the following slide is to display the detailed analysis of the debt collection process as it highlights the key steps in the process, these steps can be detailed analysis of case, establishing contact with client, Assessing the case, security adjustment Presenting debt retrieval techniques detailed analysis of debt collection process ppt pictures layout ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like detailed analysis of particular case, establishing contact with clients, assessing the case, security adjustment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ukraine Cyberwarfare International Cyber Aid To Ukraine Brochure Pdf
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia. This is a ukraine cyberwarfare international cyber aid to ukraine brochure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine is in grave danger, australia has also announced that it will teach ukrainian officials on cyber security, australia has also pledged to help the ukrainian government with cyber security through a bilateral cyber policy dialogue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Debt Collection Improvement Plan Detailed Analysis Of Debt Collection Process Ideas PDF
Purpose of the following slide is to display the detailed analysis of the debt collection process as it highlights the key steps in the process, these steps can be detailed analysis of case, establishing contact with client, Assessing the case, security adjustment. This is a debt collection improvement plan detailed analysis of debt collection process ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like detailed analysis, particular case, establishing contact, assessing case, security adjustment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
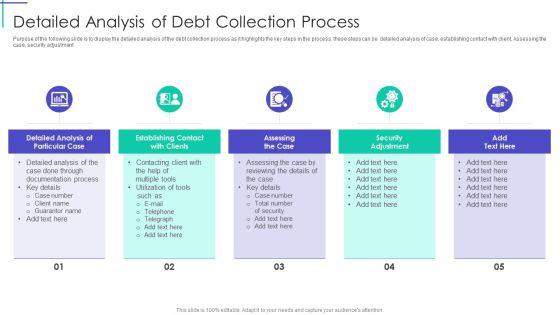
Mortgage Recovery Strategy For Finance Companies Detailed Analysis Of Debt Collection Process Brochure PDF
Purpose of the following slide is to display the detailed analysis of the debt collection process as it highlights the key steps in the process, these steps can be detailed analysis of case, establishing contact with client, Assessing the case, security adjustment. This is a Mortgage Recovery Strategy For Finance Companies Detailed Analysis Of Debt Collection Process Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Documentation Process, Detailed Analysis, Security Adjustment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. This modern and well arranged Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Mobile Device Management Determining Roles And Responsibilities For Risk Handling Microsoft PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Mobile Device Management Determining Roles And Responsibilities For Risk Handling Microsoft PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Mobile Device Management For Improving IT Operations Determining Roles And Responsibilities Themes PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Get a simple yet stunning designed Mobile Device Management For Improving IT Operations Determining Roles And Responsibilities Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Mobile Device Management For Improving IT Operations Determining Roles And Responsibilities Themes PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Chief Information Officers Guide On Technology Plan IT Risk Management Framework Infographics PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Chief Information Officers Guide On Technology Plan IT Risk Management Framework Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF

Enhancing Information Technology With Strategic IT Risk Management Framework Graphics PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Slidegeeks is here to make your presentations a breeze with Enhancing Information Technology With Strategic IT Risk Management Framework Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Conventional CASB Vs Next Generation CASB Ppt PowerPoint Presentation File Files PDF
This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Present like a pro with Conventional CASB Vs Next Generation CASB Ppt PowerPoint Presentation File Files PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
 Home
Home