AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Operations
Operations

Table Of Contents For Russian Cyber Attacks On Ukraine Elements PDF
Presenting table of contents for russian cyber attacks on ukraine elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cybersecurity, websites, technical, analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For Russian Cyber Attacks On Ukraine IT Pictures PDF
Presenting our innovatively structured icons slide for russian cyber attacks on ukraine it pictures pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Four Stages Of Protecting Functional Technology From Cyber Attacks Guidelines PDF
Persuade your audience using this four stages of protecting functional technology from cyber attacks guidelines pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including aware, vigilant, resilient. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF
Showcasing this set of slides titled Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF. The topics addressed in these templates are Endpoint Security, Network Security, Messaging Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda For Series Of Cyber Security Attacks Against Ukraine 2022 Sample PDF
Find a pre designed and impeccable Agenda For Series Of Cyber Security Attacks Against Ukraine 2022 Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Icons Slide For Series Of Cyber Security Attacks Against Ukraine 2022 Template PDF
Presenting our innovatively structured Icons Slide For Series Of Cyber Security Attacks Against Ukraine 2022 Template PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
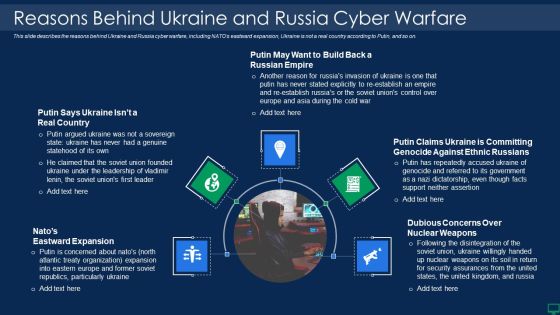
Russian Cyber Attacks On Ukraine IT Reasons Behind Ukraine And Russia Graphics PDF
This slide describes the reasons behind Ukraine and Russia cyber warfare, including NATOs eastward expansion, Ukraine is not a real country according to Putin, and so on. Presenting russian cyber attacks on ukraine it reasons behind ukraine and russia graphics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reasons behind ukraine and russia cyber warfare. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
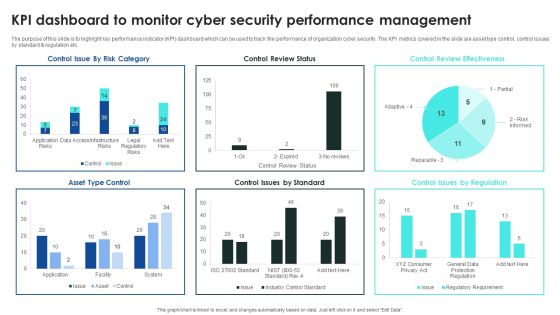
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Change Management Agents Corporate Transformation Strategic Outline Elements PDF
Deliver an awe inspiring pitch with this creative change management agents corporate transformation strategic outline elements pdf bundle. Topics like board, sponsors, leaders, team members, stakeholders can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
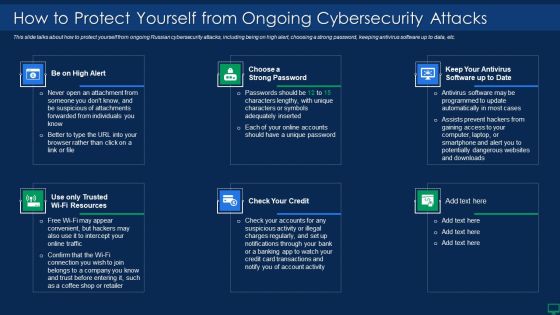
Russian Cyber Attacks On Ukraine IT How To Protect Yourself Summary PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Presenting russian cyber attacks on ukraine it how to protect yourself summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like resources, account, potentially. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault How To Protect Company From Trojan Attacks Demonstration PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a cyber terrorism assault how to protect company from trojan attacks demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like device conventional, next generation antivirus, prevent trojan infection You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Policies Inspiration PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Presenting continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring policies inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Prevention Of Information Understanding The Frequency And Weightage Of Cyber Attacks Professional PDF
The purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Present like a pro with Prevention Of Information Understanding The Frequency And Weightage Of Cyber Attacks Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
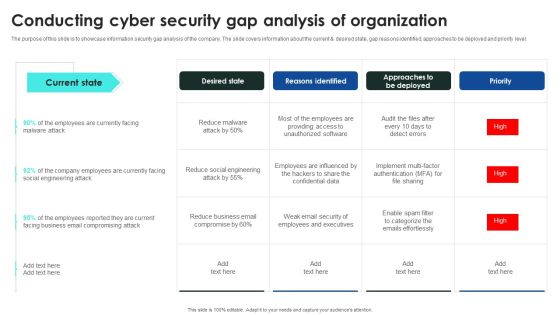
Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Get a simple yet stunning designed Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF

Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF
The following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti-virus, preventing to open suspicious emails, keeping systems up-to date etc. Find highly impressive Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Best Practices To Prevent Cyber Attacks Ppt PowerPoint Presentation File Model PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Infographics PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks current security monitoring infographics pdf bundle. Topics like monitoring, service, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Estimated Security Monitoring Designs PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Russian Cyber Attacks On Ukraine IT Are There International Mockup PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts. This is a russian cyber attacks on ukraine it are there international mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, strategic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Are There International Laws Establishing Cyber Policies Professional PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts.Presenting data wiper spyware attack are there international laws establishing cyber policies professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like international agreement, coordinate state, responses to cybercrime In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Hybrid Warfare Cyber Rapid Response Download PDF
This slide talks about the cyber rapid response team deployed to protect Ukraine from Russian cyberattacks, including experts from Lithuania, Croatia, Poland, Estonia, Romania, and the Netherlands.This is a data wiper spyware attack hybrid warfare cyber rapid response download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like launched throughout, cooperation among, vulnerability assessment You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack International Cyber Aid To Ukraine Icons PDF
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia.Presenting data wiper spyware attack international cyber aid to ukraine icons pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like might interrupt, critical services, jeopardizing national In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Safety Audits To Stop Cyber Attacks Ppt PowerPoint Presentation File Example Topics PDF
Persuade your audience using this key safety audits to stop cyber attacks ppt powerpoint presentation file example topics pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including inventory, secure configurations, continuous vulnerability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Best Mockup PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring best mockup pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Russian Cyber Attacks On Ukraine IT Triolan Suffers Severe Icons PDF
This slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider Triolan during the Russian Invasion. Deliver and pitch your topic in the best possible manner with this russian cyber attacks on ukraine it triolan suffers severe icons pdf. Use them to share invaluable insights on equipment, required, service, globally and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Russian Cyber Attacks On Ukraineteam Mockup PDF
This is a table of contents for russian cyber attacks on ukraineteam mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, technology, potential, accounts, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
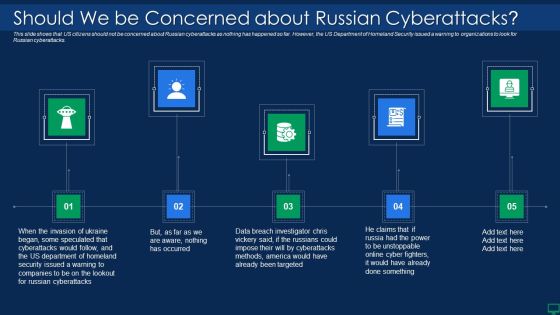
Russian Cyber Attacks On Ukraine IT Should We Be Concerned Slides PDF
Presenting russian cyber attacks on ukraine it should we be concerned slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like targeted, methods, security, cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

One Page Real Estate Agent To Agent Commission Agreement Form PDF Document PPT Template
Presenting you an exemplary One Page Real Estate Agent To Agent Commission Agreement Form PDF Document PPT Template. Our one-pager template comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Real Estate Agent To Agent Commission Agreement Form PDF Document PPT Template Download now.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan To Eliminate Cyber Attacks Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This continuous development evaluation plan to eliminate cyber attacks ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of forty seven slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring tools diagrams pdf bundle. Topics like cybersecurity monitoring tools to be implemented can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Russian Cyber Attacks On Ukraine IT Continued Impact Of Ongoing Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. This is a russian cyber attacks on ukraine it continued impact of ongoing microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sources, service, network, internet. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
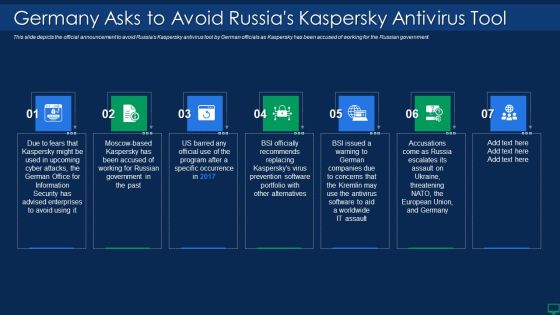
Russian Cyber Attacks On Ukraine IT Germany Asks To Avoid Russias Sample PDF
This slide depicts the official announcement to avoid Russias Kaspersky antivirus tool by German officials as Kaspersky has been accused of working for the Russian government. This is a russian cyber attacks on ukraine it germany asks to avoid russias sample pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, portfolio. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
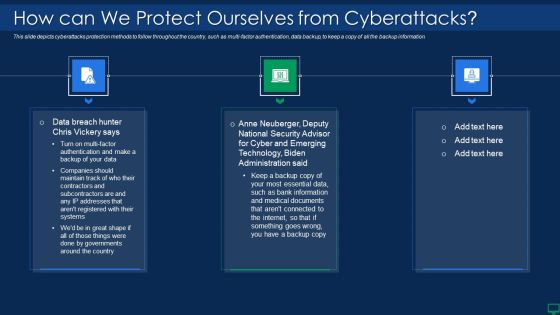
Russian Cyber Attacks On Ukraine IT How Can We Protect Ourselves Rules PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. This is a russian cyber attacks on ukraine it how can we protect ourselves rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internet, documents, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF
This slide signifies three step process to maintain and recover from ransomware and computer malfunction. It covers information about stages like prepare recovery plan, limit damage scope and incrementally remove risk. Persuade your audience using this 3 Stage Plan To Prevent And Recover From Cyber Attack Ppt Ideas Show PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Recovery Plan, Limit Scope Damage, Incrementally Remove Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Series Of Cyber Security Attacks Against Ukraine 2022 Ppt PowerPoint Presentation Complete With Slides
People are consistently online to look for new ways to start a business or make money. What better than impressing that target audience with your Series Of Cyber Security Attacks Against Ukraine 2022 Ppt PowerPoint Presentation Complete With Slides, with its relatable and valuable content. This sixty one slide complete deck will turn a mundane session into a power-packed wow level presentation that your prospects will love to revisit over and over. This actionable preset will cover the nuances of all business slides. You can populate the slides in this template with your content and share the file with the presentation attendees as well.

Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF
Retrieve professionally designed Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
