Market Access
Sensitive Access Analysis Ppt PowerPoint Presentation Styles Influencers Cpb Pdf
Presenting this set of slides with name sensitive access analysis ppt powerpoint presentation styles influencers cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like sensitive access analysis to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Access Database Replication Ppt PowerPoint Presentation Inspiration Show Cpb Pdf
Presenting this set of slides with name access database replication ppt powerpoint presentation inspiration show cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like access database replication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
User Access Provisioning Process Ppt PowerPoint Presentation Example Cpb
Presenting this set of slides with name user access provisioning process ppt powerpoint presentation example cpb. This is an editable Powerpoint three stages graphic that deals with topics like user access provisioning process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Access Review Process Ppt PowerPoint Presentation Show Graphic Images Cpb
Presenting this set of slides with name access review process ppt powerpoint presentation show graphic images cpb. This is an editable Powerpoint four stages graphic that deals with topics like access review process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Business Value Identity Access Management Ppt PowerPoint Presentation Summary Cpb
Presenting this set of slides with name business value identity access management ppt powerpoint presentation summary cpb. This is an editable Powerpoint three stages graphic that deals with topics like business value identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Framework Ppt PowerPoint Presentation Portfolio Summary Cpb
Presenting this set of slides with name identity access management framework ppt powerpoint presentation portfolio summary cpb. This is an editable Powerpoint four stages graphic that deals with topics like identity access management framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Secure Access Management Ppt PowerPoint Presentation Pictures Layout Cpb Pdf
Presenting this set of slides with name secure access management ppt powerpoint presentation pictures layout cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like secure access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Provide Access To Resources That Streamline Partner Relationship Ppt Slides
This slide details the access to resources to be provided during partner onboarding stage. It includes tools such as, marketing kit, partner portal, referral program and product or service demos. Get a simple yet stunning designed Provide Access To Resources That Streamline Partner Relationship Ppt Slides. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Provide Access To Resources That Streamline Partner Relationship Ppt Slides can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Zero Trust Model Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Model Zero Trust Network Access System Use Cases that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Zero Trust Network Access System Use Cases from Slidegeeks today.

Zero Trust Network Access Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Overview Of Zero Trust Solution Categories for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
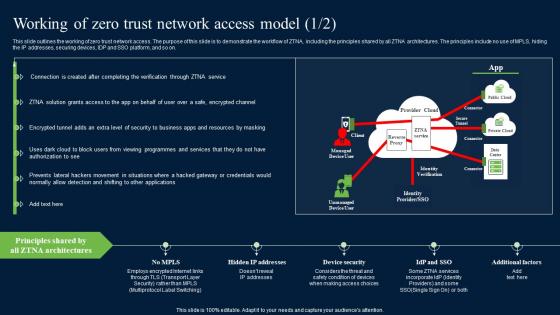
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Are you searching for a Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation from Slidegeeks today.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
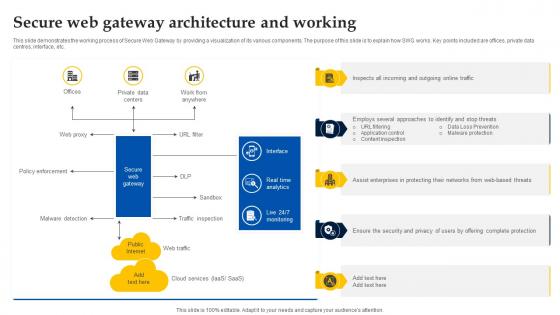
Web Access Control Solution Secure Web Gateway Architecture And Working
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Web Access Control Solution Secure Web Gateway Architecture And Working for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
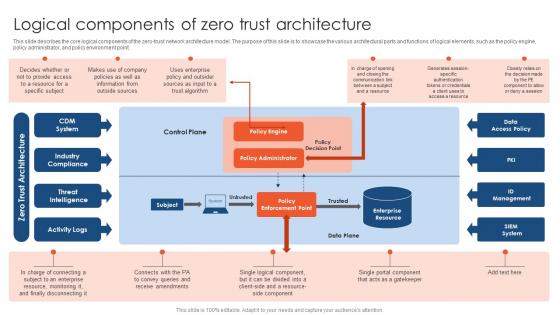
Zero Trust Network Access Logical Components Of Zero Trust Architecture
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Take your projects to the next level with our ultimate collection of Zero Trust Network Access Logical Components Of Zero Trust Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Ensure Security And Access Controls Ppt PowerPoint Presentation Portfolio Images
This is a ensure security and access controls ppt powerpoint presentation portfolio images. This is a two stage process. The stages in this process are icons, strategy, business, management, marketing.

Dashboard To Access Online Promotion Effectiveness Template PDF Pictures PDF
Showcasing this set of slides titled Dashboard To Access Online Promotion Effectiveness Template PDF Pictures PDF The topics addressed in these templates are Dashboard To Access Online Promotion Effectiveness All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.

Zero Trust Network Access Vs Virtual Private Network Ideas PDF
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Vs Virtual Private Network Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
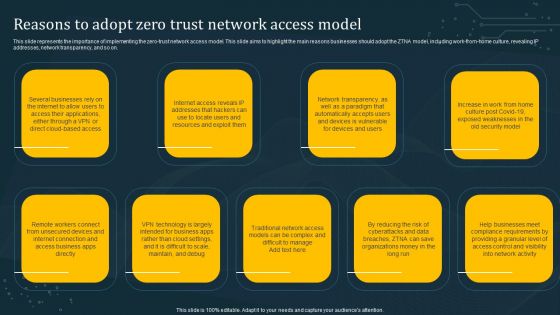
Reasons To Adopt Zero Trust Network Access Model Demonstration PDF
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Reasons To Adopt Zero Trust Network Access Model Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
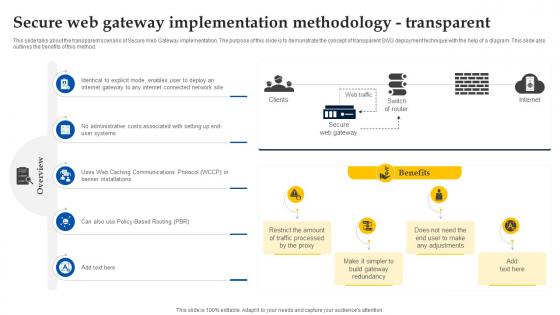
Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
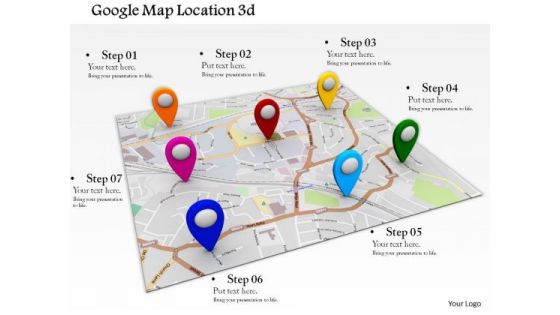
Stock Photo Google Maps Location Access PowerPoint Slide
Use this google maps image slide to make presentations related to technology, satellites, GPS or wireless networks. Design your presentation with this amazing slide and impress your audiences.

Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Presenting this PowerPoint presentation, titled Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Web Access Control Solution Key Growth Drivers Of Next Generation Swg Market that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Implementation Steps Introduction For Identifying Users To Access CRM Portrait PDF
This slide covers the process of determining the CRM users and creating their roles and profiles in order to maintain data security. Deliver an awe inspiring pitch with this creative Implementation Steps Introduction For Identifying Users To Access CRM Portrait PDF bundle. Topics like Marketing Executive, Sales Executive, Training Executive can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Role Of SDN In Edge Computing IOT And Remote Access Evolution Of SDN Controllers Topics Pdf
This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. This Role Of SDN In Edge Computing IOT And Remote Access Evolution Of SDN Controllers Topics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
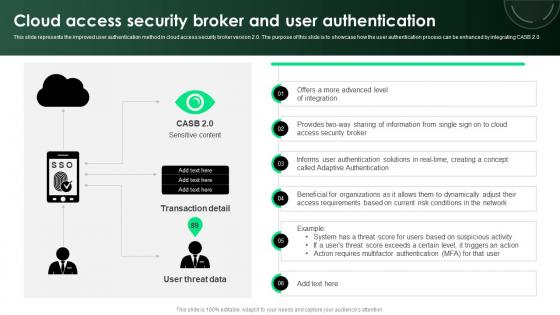
CASB 2 0 IT Cloud Access Security Broker And User Authentication
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Hand Sign With Cross For Banned Access Ppt PowerPoint Presentation Inspiration Format PDF
Presenting this set of slides with name hand sign with cross for banned access ppt powerpoint presentation inspiration format pdf. The topics discussed in these slide is hand sign with cross for banned access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Key Focus Areas In Digital Security And Access Management Ppt Visual Aids Model PDF
Showcasing this set of slides titled key focus areas in digital security and access management ppt visual aids model pdf. The topics addressed in these templates are digital security, cyber security, access management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
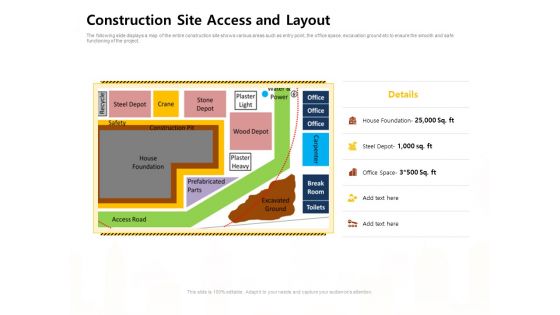
Managing Construction Work Construction Site Access And Layout Ppt Ideas Information PDF
The following slide displays a map of the entire construction site shows various areas such as entry point, the office space, excavation ground etc to ensure the smooth and safe functioning of the project. Deliver an awe-inspiring pitch with this creative managing construction work construction site access and layout ppt ideas information pdf bundle. Topics like construction site access and layout can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Reverse Proxy Server IT Setting Up Reverse Proxy For Access Management Ppt Ideas Guide PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources. Presenting reverse proxy server it setting up reverse proxy for access management ppt ideas guide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like access manager, identity manager, identity applications, identity reporting, access gateway, identity provider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Document Encryption File Access Vector Icon Ppt PowerPoint Presentation Inspiration Guidelines
Presenting this set of slides with name document encryption file access vector icon ppt powerpoint presentation inspiration guidelines. This is a one stage process. The stages in this process are market asses, strategic market, business. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Projected Access Documents With Key Vector Icon Ppt PowerPoint Presentation Model Samples
Presenting this set of slides with name projected access documents with key vector icon ppt powerpoint presentation model samples. This is a one stage process. The stages in this process are market asses, strategic market, business. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Local Area Network For Internet Access Vector Icon Ppt PowerPoint Presentation Ideas Graphics Download PDF
Presenting local area network for internet access vector icon ppt powerpoint presentation ideas graphics download pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including local area network for internet access vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
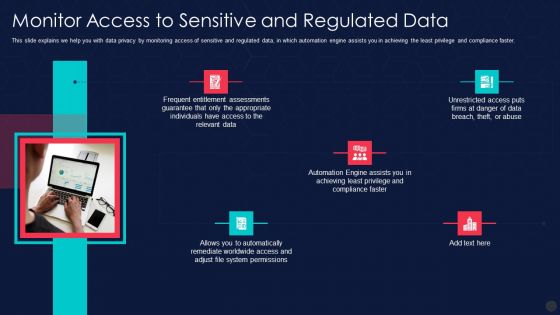
Information Privacy IT Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. This is a information privacy it monitor access to sensitive and regulated data structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitor access to sensitive and regulated data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Guidelines IT Overview Of Remote Access Policy For Employees Structure PDF
This slide represents the remote access policy to connect to the companys network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. Create an editable Cybersecurity Guidelines IT Overview Of Remote Access Policy For Employees Structure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cybersecurity Guidelines IT Overview Of Remote Access Policy For Employees Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Technology Policy And Processes Overview Of Remote Access Policy For Employees Structure PDF
This slide represents the remote access policy to connect to the companys network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. The Information Technology Policy And Processes Overview Of Remote Access Policy For Employees Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
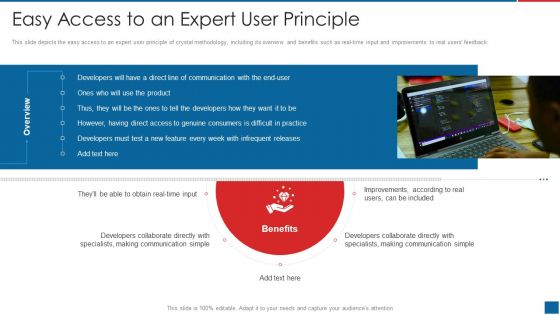
Agile Crystal Method Easy Access To An Expert User Principle Information PDF
This slide depicts the easy access to an expert user principle of crystal methodology, including its overview and benefits such as real time input and improvements to real users feedback.Presenting Agile Crystal Method Easy Access To An Expert User Principle Information PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Developers Collaborate, Specialists Making Communication, Making Communication Simple In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
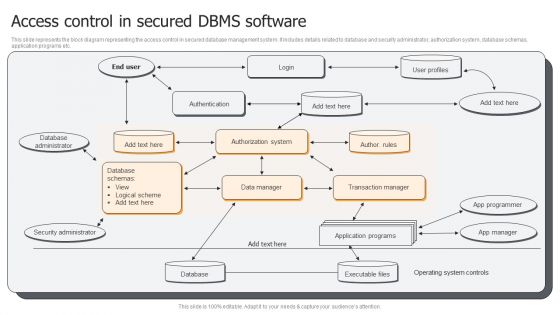
Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF
This slide represents the block diagram representing the access control in secured database management system. It includes details related to database and security administrator, authorization system, database schemas, application programs etc. Presenting Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Database Administrator, Security Administrator, Database, Application Programs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Network Access Ppt Powerpoint Presentation Complete Deck With Slides

Five Stages Of Software Testing With Scanning And Maintaining Access Ppt PowerPoint Presentation Pictures Slides
Presenting this set of slides with name five stages of software testing with scanning and maintaining access ppt powerpoint presentation pictures slides. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security For Network Protection From Unauthorized Access Vector Icon Ppt PowerPoint Presentation File Summary PDF
Presenting this set of slides with name security for network protection from unauthorized access vector icon ppt powerpoint presentation file summary pdf. This is a three stage process. The stages in this process are security for network protection from unauthorized access vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vector Icon Showing Network Access Denial On Mobile Ppt PowerPoint Presentation Styles Grid PDF
Presenting this set of slides with name vector icon showing network access denial on mobile ppt powerpoint presentation styles grid pdf. This is a three stage process. The stages in this process are vector icon showing network access denial on mobile. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
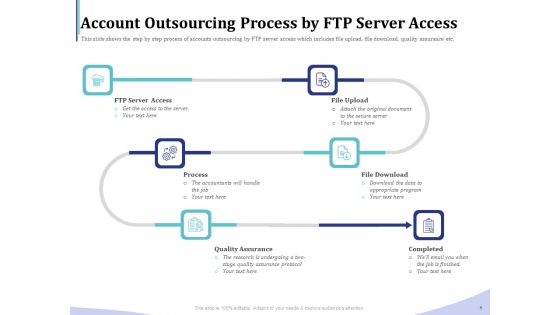
Accounting Bookkeeping Services Account Outsourcing Process By FTP Server Access Ppt Infographics Deck PDF
Presenting this set of slides with name accounting bookkeeping services account outsourcing process by ftp server access ppt infographics deck pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
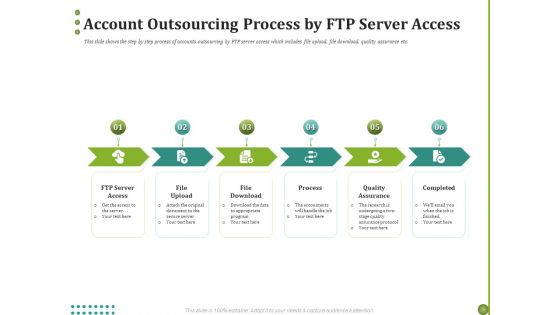
BPO Managing Enterprise Financial Transactions Account Outsourcing Process By FTP Server Access Download PDF
Presenting this set of slides with name bpo managing enterprise financial transactions account outsourcing process by ftp server access download pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Outsource Bookkeeping Service Manage Financial Transactions Account Outsourcing Process By FTP Server Access Clipart PDF
Presenting this set of slides with name outsource bookkeeping service manage financial transactions account outsourcing process by ftp server access clipart pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Layered Framework With Data Access Ppt PowerPoint Presentation File Format Ideas PDF
Presenting this set of slides with name layered framework with data access ppt powerpoint presentation file format ideas pdf. This is a three stage process. The stages in this process are data layer, data access layer, business layer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
CCTV Access On Mobile Phone Vector Icon Ppt PowerPoint Presentation Pictures Deck PDF
Presenting this set of slides with name cctv access on mobile phone vector icon ppt powerpoint presentation pictures deck pdf. This is a three stage process. The stages in this process are cctv access on mobile phone vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Firm Productivity Administration BI Design And Development Access Ppt PowerPoint Presentation Show Examples PDF
Presenting this set of slides with name firm productivity administration bi design and development access ppt powerpoint presentation show examples pdf. This is a four stage process. The stages in this process are web based access, component based architecture, service oriented architecture, ssl security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
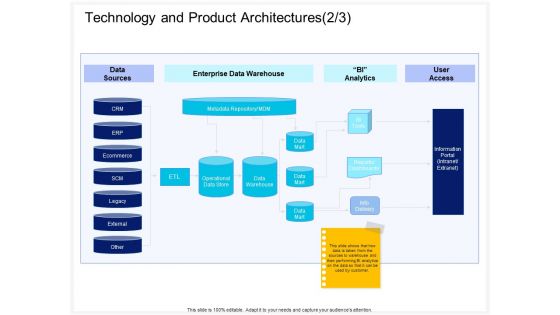
Enterprise Problem Solving And Intellect Technology And Product Architectures Access Summary PDF
Presenting this set of slides with name enterprise problem solving and intellect technology and product architectures access summary pdf. This is a one stage process. The stages in this process are data sources, enterprise data warehouse, bi analytics, user access, crm, erp, ecommerce, scm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
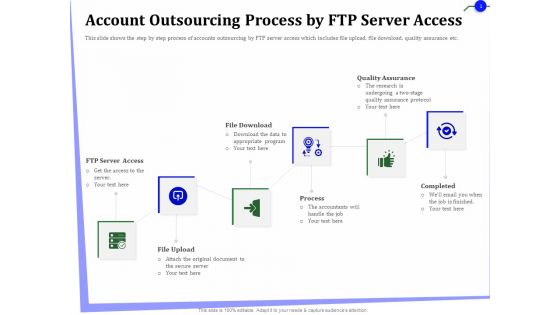
Outsourcing Of Finance And Accounting Processes Account Outsourcing Process By FTP Server Access Rules PDF
Presenting this set of slides with name outsourcing of finance and accounting processes account outsourcing process by ftp server access rules pdf. This is a six stage process. The stages in this process are server, access, process, quality, assurance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Hotel Card Door Lock Access Control Vector Icon Ppt PowerPoint Presentation File Icon PDF
Presenting hotel card door lock access control vector icon ppt powerpoint presentation file icon pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including hotel card door lock access control vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Identity Based Security Access Management Ppt PowerPoint Presentation Gallery Background Cpb
Presenting this set of slides with name identity based security access management ppt powerpoint presentation gallery background cpb. This is an editable Powerpoint five stages graphic that deals with topics like identity based security access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
procedure of record keeping system with ease of access ppt powerpoint presentation icon master slide
Presenting this set of slides with name procedure of record keeping system with ease of access ppt powerpoint presentation icon master slide. This is a four stage process. The stages in this process are records management policy, retention schedule, choose the right solution, ease of access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Identity Access Management Challenges Ppt PowerPoint Presentation Show Graphic Tips Cpb
Presenting this set of slides with name identity access management challenges ppt powerpoint presentation show graphic tips cpb. This is an editable Powerpoint four stages graphic that deals with topics like identity access management challenges to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Cloud Computing Ppt PowerPoint Presentation Infographic Template Slide Cpb
Presenting this set of slides with name identity access management cloud computing ppt powerpoint presentation infographic template slide cpb. This is an editable Powerpoint four stages graphic that deals with topics like identity access management cloud computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Strategy Ppt PowerPoint Presentation Infographics Infographic Template Cpb
Presenting this set of slides with name identity access management strategy ppt powerpoint presentation infographics infographic template cpb. This is an editable Powerpoint five stages graphic that deals with topics like identity access management strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Access Control Security SAP Ppt PowerPoint Presentation Portfolio Designs Cpb Pdf
Presenting this set of slides with name access control security sap ppt powerpoint presentation portfolio designs cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like access control security sap to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Identity Access Management Cloud Computing Ppt PowerPoint Presentation Infographic Template Tips Cpb Pdf
Presenting this set of slides with name identity access management cloud computing ppt powerpoint presentation infographic template tips cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like identity access management cloud computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Technologies Ppt PowerPoint Presentation Portfolio Good Cpb Pdf
Presenting this set of slides with name identity access management technologies ppt powerpoint presentation portfolio good cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like identity access management technologies to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

 Home
Home