It Security Roadmap

Global Cloud Based Email Security Market Industry Trends Ppt Professional Example PDF
Presenting this set of slides with name global cloud based email security market industry trends ppt professional example pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Awareness System For Online Security Improvement Ppt PowerPoint Presentation Show Samples PDF
Presenting this set of slides with name awareness system for online security improvement ppt powerpoint presentation show samples pdf. This is a three stage process. The stages in this process are cyber focus, planning, 2020, build security policy, security architecture, cyber disaster management, evaluate supply chain security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Technology Strategy Role Of Chief Information Security Officer Rules PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. This is a information technology strategy role of chief information security officer rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information, stay informed, monthly reports. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year. Presenting Smart Home Security Solutions Company Profile Awards And Accolades Icons PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Digital Trends Best, Smart Home Security, Systems Consumer Technology, Association Consumer Technology, Association Security Today. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF
The following slide highlights multiple solutions to prevent security risks and issues. It also includes elements such as risk evaluation, security awareness, checklist, policies and regulation, recovery plan etc. Presenting Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk Evaluation, Security Awareness, Security Checklist, Policies And Regulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF bundle. Topics like Gap Analysis, Environmental Trends, Business Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Graphics PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail evaluating information processing assets graphics pdf. Use them to share invaluable insights on security management plan steps in detail evaluating information processing assets and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Summary PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail risk assessment and analysis summary pdf. Use them to share invaluable insights on security management plan steps in detail risk assessment and analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
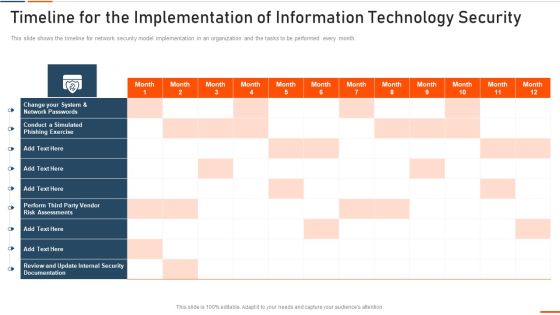
Timeline For The Implementation Of Information Technology Security Ppt Portfolio Slideshow PDF
This slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of information technology security ppt portfolio slideshow pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Canva Pro Business Profile Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in app permissions. Presenting Business Profile Canva Security Processes And Systems Elements PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Data Security, Monitoring, Secure Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Timeline For The Implementation Of Electronic Information Security Ppt Infographic Template Information PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative cybersecurity timeline for the implementation of electronic information security ppt infographic template information pdf bundle. Topics like security documentation, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
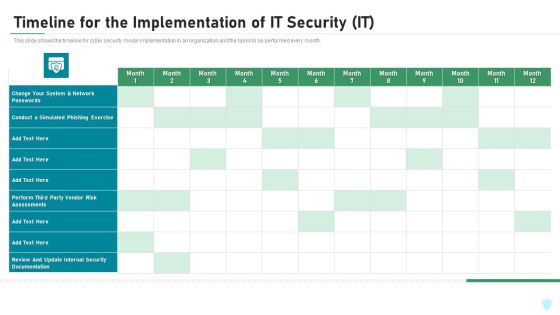
Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF
This slide portrays information regarding development of corporate security governance framework including board of directors, senior executives, steering committees in order to ensure the effective corporate security governance. Create an editable Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Critical Measures For Ensuring Building Corporate Security Governance Framework Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
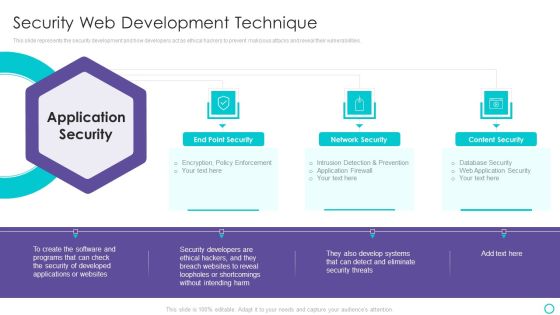
Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF
This slide exhibits the different types of managed security services such as risk management, virtual CISO and security awareness education. It also provides information about the multiple offerings of each service. Persuade your audience using this Multiple Types Of Managed Cyber Security Solutions Services Ppt Styles Layout Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Offerings, Security Awareness Education, Virtual CISO. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Security System For Business Quality Control Ppt PowerPoint Presentation Gallery Templates PDF
Presenting this set of slides with name online security system for business quality control ppt powerpoint presentation gallery templates pdf. This is a six stage process. The stages in this process are network engineering program, information security management, social engineering program, ethical hacking program, crime investigation program, internet security program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Determine Role Of Security Centre To Ensure Project Safety Ppt Professional Example PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative determine role of security centre to ensure project safety ppt professional example pdf bundle. Topics like security, system, developed, requirements, teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Ethical Hackers Roles And Responsibilities Security Inspiration PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Presenting cyber exploitation it ethical hackers roles and responsibilities security inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, organizations, analyze, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
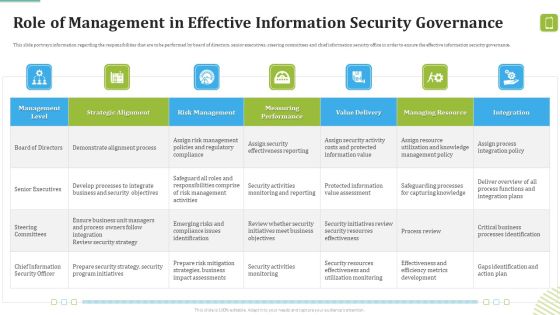
MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Demonstrate Alignment, Business Security, Program Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Risk Assessment And Analysis Introduction PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver an awe inspiring pitch with this creative security management plan steps in detail risk assessment and analysis introduction pdf bundle. Topics like information, system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Four Steps Arrow For Business Data Security Process Ppt PowerPoint Presentation File Background Image PDF
Presenting four steps arrow for business data security process ppt powerpoint presentation file background image pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including four steps arrow for business data security process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF
This slide defines the techniques of analyzing and protecting against websites attack. It includes information related to automated scanning, security testing, web application firewalls WAFs and secure development testing SDT. Presenting Analyzing And Protecting Against Cyber Security Attack Ppt Pictures Background Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Web Application Firewalls, Secure Development Testing, Automated Scanning, Security Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Demonstration PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan. Presenting Security management plan steps in detail data backup and data loss recovery plan demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security management plan steps in detail - data backup and data loss recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

3 Groups Slide For Cloud Native Security Assessments Ppt PowerPoint Presentation File Professional PDF
Presenting 3 groups slide for cloud native security assessments ppt powerpoint presentation file professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including 3 groups slide for cloud native security assessments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Nine Bullet Diagram For Medical Iot Security Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting nine bullet diagram for medical iot security ppt powerpoint presentation icon portfolio pdf to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including nine bullet diagram for medical iot security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Plan With Key Trends Ppt PowerPoint Presentation Summary Mockup PDF
Showcasing this set of slides titled internet security threat analysis plan with key trends ppt powerpoint presentation summary mockup pdf. The topics addressed in these templates are internet security threat analysis plan with key trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3Rd Party API Integration To Check Security Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting 3rd party api integration to check security ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including check security, implementation, mission. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
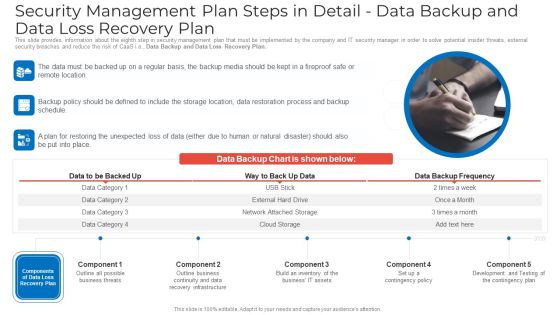
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Activity Template PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration security operations implementation timeline activity template pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
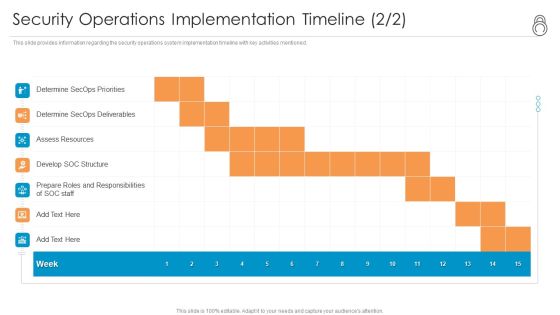
Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Staff Background PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security operations implementation timeline staff background pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF
This slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Security Business Marketing Plan Ppt PowerPoint Presentation Show Graphics Design Cpb
Presenting this set of slides with name security business marketing plan ppt powerpoint presentation show graphics design cpb. This is a three stage process. The stages in this process are security business marketing plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Steps Of Cyber Security With Icons Ppt PowerPoint Presentation Model Samples
Presenting this set of slides with name five steps of cyber security with icons ppt powerpoint presentation model samples. This is a five stage process. The stages in this process are security servery, solutions deployment, review and adjustment, monitoring and evaluation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Management Plan Steps In Detail Training And Building Role Competencies Topics PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, competencies required. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Slides PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies slides pdf to provide visual cues and insights. Share and navigate important information on five tages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
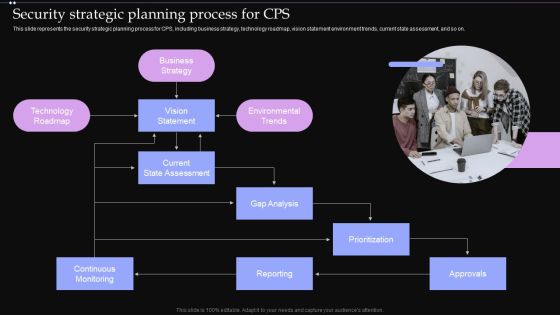
Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Security Strategic Planning Process For CPS Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document brilliant piece now.

Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Picture Editing Company Outline Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in- app permissions. Welcome to our selection of the Picture Editing Company Outline Canva Security Processes And Systems Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

3 Months Timeline Saas Data Security Ppt PowerPoint Presentation Gallery Master Slide PDF
Persuade your audience using this 3 months timeline saas data security ppt powerpoint presentation gallery master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including 3 months timeline saas data security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home