Iot Security

Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112
We present our Login Screen And Credit Card Services Security PowerPoint Templates And PowerPoint Themes 1112.Use our Technology PowerPoint Templates because, The structure of our templates allows you to effectively highlight the key issues concerning the growth of your business. Use our Business PowerPoint Templates because, Let your words be the drops of wisdom spreading knowledge and peace like ripples through the expectant minds of your devoted followers. Use our Computer PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Internet PowerPoint Templates because,The basic stages are in place, you need to build upon them with our PowerPoint templates. Use our Success PowerPoint Templates because, You have some great folks working with you, thinking with you.Use these PowerPoint slides for presentations relating to laptop screen, internet, computer, technology, business, success. The prominent colors used in the PowerPoint template are Gray, Blue, Black

Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black.

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF
This slide depicts the four critical areas where SDN can make a difference in an organization, such as network programmability, centralized intelligence and control, abstraction of the network, and openness. Welcome to our selection of the SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Keys Tied To Chain Security PowerPoint Templates Ppt Background For Slides 1112
We present our Keys Tied To Chain Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Success PowerPoint Templates because,This Slide offers an excellent background to build up the various stages of your business process. Use our Chains PowerPoint Templates because,Our PowerPoint templates designed for your ideas to sell. Use our Finance PowerPoint Templates because,Let this slide illustrates others piggyback on you to see well over the horizon Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Keys tied to chain, business, success, chains, finance, marketing. The prominent colors used in the PowerPoint template are Yellow, Brown, White

Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112
We present our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because,You too have got the framework of your companys growth in place. Use our Success PowerPoint Templates because, You can Transmit this concern to your staff using our helpful slides. Use our Puzzles or jigsaws PowerPoint Templates because,We all know that alphabetical order is a time honoured concept. Use our Shapes PowerPoint Templates because,you can put it up there for all to see. Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Key chain tied with puzzle piece, business, success, puzzles or jigsaws, shapes, marketing. The prominent colors used in the PowerPoint template are Yellow, Black, Red

Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF
This slide showcases dashboard to review bank transactions and activities. It provides information about credit, check, ATM, debit card, transaction volume, decline rate, visa, maestro, network end points, etc. This KYC Transaction Monitoring System Business Security Dashboard To Monitor Bank Transactions Mockup PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Use Internet Security For Business PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Use Internet Security For Business PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download and present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team. Present our Globe PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Computer mouse is connected to a globe - surfing and browsing is blocked by a red do not enter sign that cuts the cable, technology, communication, signs, globe, business. The prominent colors used in the PowerPoint template are Blue, White, Black.

Wireless Network Security System Smart Lock Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this wireless network security system smart lock ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF
This is a Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Global Market, IoT Products, Companies Digitization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
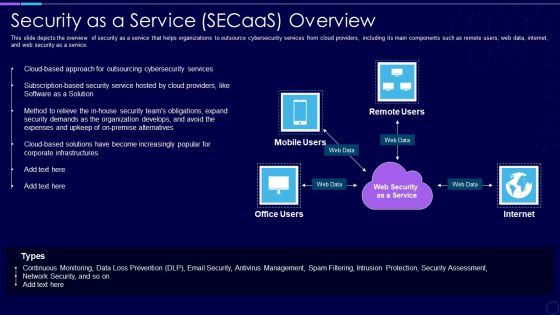
Everything As A Service Xaas For Cloud Computing IT Security As A Service Secaas Overview Portrait PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service. Presenting everything as a service xaas for cloud computing it security as a service secaas overview portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like expenses, security, organization, services, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Series Of Cyber Security Attacks Against Ukraine 2022 Triolan Suffers Severe Cyberattacks During Russian Invasion Designs PDF
This slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider triolan during the russian invasion. This modern and well arranged Series Of Cyber Security AttaSeries Of Cyber Security Attacks Against Ukraine 2022 Triolan Suffers Severe Cyberattacks During Russian Invasion Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Security Information And Event Management Strategies For Financial Audit And Compliance Next Evolution Of Siem Software Download PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting security information and event management strategies for financial audit and compliance next evolution of siem software download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like user entity and behavior analytics, network traffic analysis, endpoint monitoring, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF
This slide represents the technical analysis of ddos attacks against ukrainian websites by showing the internet traffic to the oschad bank website on 15 16 february 2022. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF
The following slide showcases best practices to secure IOT gateway that are device establishment, establishing strong identity and provide identity to ecosystem. Presenting Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Performance Metrics For Project Management Office, Requirement Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Access Service Edge Importance Ppt Outline Graphics Example PDF
This slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. This modern and well arranged Secure Access Service Edge Importance Ppt Outline Graphics Example PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

COVID 19 Mitigating Impact On High Tech Industry The Impact Of COVID 19 On Internet Of Things Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry the impact of covid 19 on internet of things brochure pdf. The topics discussed in these slides are positive impact, iot vendors, negative impact iot vendors, impact not clear, enterprise technology needs, technology general, iot technology, specific iot applications, iot security and privacy, people and relationship. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Is Secure Internet PowerPoint Template 1110
3d illustration of a lock sitting in front of a computer display showing a file folder
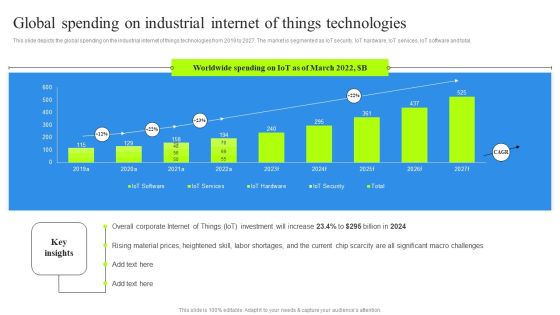
Global Spending On Industrial Internet Of Things Technologies Graphics PDF
This slide depicts the global spending on the industrial internet of things technologies from 2019 to 2027. The market is segmented as IoT security, IoT hardware, IoT services, IoT software and total. Boost your pitch with our creative Global Spending On Industrial Internet Of Things Technologies Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Transforming Manufacturing With Automation Global Spending On Industrial Elements PDF
This slide depicts the global spending on the industrial internet of things technologies from 2019 to 2027. The market is segmented as IoT security, IoT hardware, IoT services, IoT software and total. Find a pre designed and impeccable Transforming Manufacturing With Automation Global Spending On Industrial Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. Slidegeeks has constructed Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
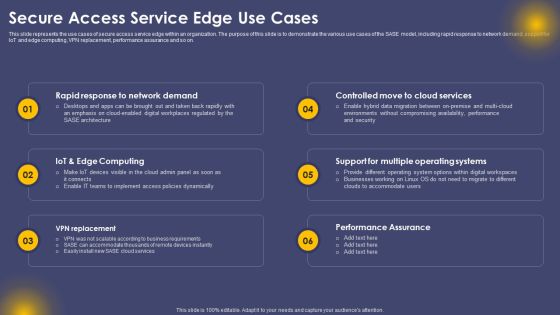
Secure Access Service Edge Use Cases Ppt Outline Images PDF
This slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Explore a selection of the finest Secure Access Service Edge Use Cases Ppt Outline Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Secure Access Service Edge Use Cases Ppt Outline Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.

Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Mobile Security, IoT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Secured Internet Connections PowerPoint Templates Ppt Backgrounds For Slides 0813
Get the doers into action. Activate them with our Secured Internet Connections PowerPoint Templates PPT Backgrounds For Slides. Put your money on our Technology PowerPoint Templates. Your ideas will rake in the dollars. Put in a dollop of our Security PowerPoint Templates. Give your thoughts a distinctive flavour.

Secured Internet Connection PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secured Internet Connection PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Present our Technology PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Download and present our Shapes PowerPoint Templates because You will get more than you ever bargained for. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience.Use these PowerPoint slides for presentations relating to Browser window with a Key, security, business, technology, signs, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Black.

Secure Internet Browser PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secure Internet Browser PowerPoint Templates PPT Backgrounds For Slides 0313.Use our Network diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Technology PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script.Use these PowerPoint slides for presentations relating to Secure Internet Browser, network diagrams, security, technology, signs, shapes. The prominent colors used in the PowerPoint template are Gray, Yellow, Black.
Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it

Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a lock padlock intersecting it

Secure Internet Access Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a large chrome key protruding out from the window

Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a large chrome key protruding out from the window
Secure Digital Mail Internet PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface

Secure Digital Mail Internet PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface

Secure Digital Mail Internet PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface

Secure Digital Mail Internet PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface

Secure Digital Mail Internet PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface

Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Deliver an awe inspiring pitch with this creative Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF bundle. Topics like Digital Data, Blockchain Networks, Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
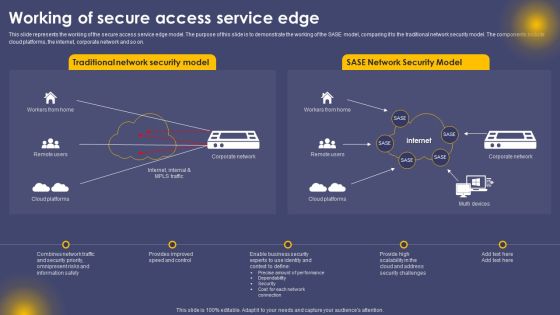
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF
This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Secure Hybrid Network Ppt PowerPoint Presentation Ideas Slides Cpb
Presenting this set of slides with name secure hybrid network ppt powerpoint presentation ideas slides cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure hybrid network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Secure Network Construction Proposal Example Document Report Doc Pdf Ppt
Heres a predesigned Secure Network Construction Proposal Example Document Report Doc Pdf Ppt for you. Built on extensive research and analysis, this one-complete deck has all the center pieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Secure Network Construction Proposal Example Document Report Doc Pdf Ppt A4 One-pager now.
Timeline Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.

Business Governance Framework For Cryptographically Secured Services Structure PDF
This slide signifies the organisation governance model for cryptographically secured services. It includes steps like generic value network, analysis, canvas analysis and plan.Persuade your audience using this Business Governance Framework For Cryptographically Secured Services Structure PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Suggested Service, Provider Business, Business Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Person Browsing Securely Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with person sitting on the floor, chatting using a notebook
 Home
Home