Iot Security
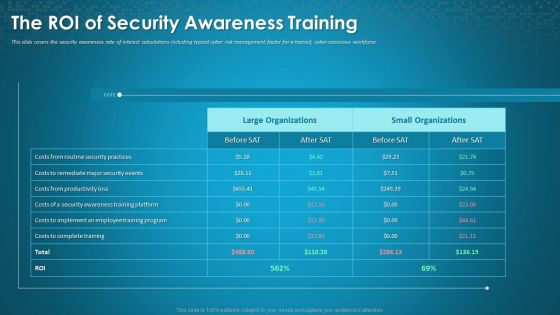
Organizational Network Staff Learning The ROI Of Security Awareness Training Designs PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this organizational network staff learning the roi of security awareness training designs pdf. Use them to share invaluable insights on employee training program, security awareness training platform, productivity loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
Security Gateway For Web Enabled Network Network Application Icon Demonstration PDF
Presenting Security Gateway For Web Enabled Network Network Application Icon Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Gateway, Web Enabled, Network Network, Application Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Network Security Protection Ensuring Safety From Online Threat Ppt PowerPoint Presentation Portfolio Influencers PDF
Persuade your audience using this network security protection ensuring safety from online threat ppt powerpoint presentation portfolio influencers pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network security protection ensuring safety from online threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
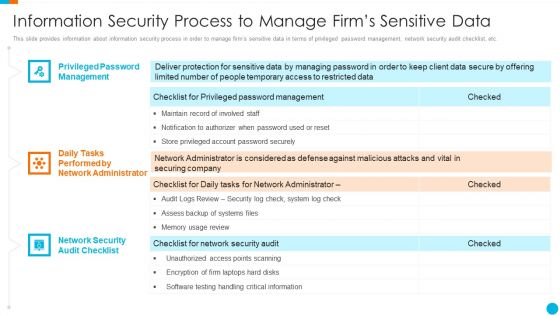
Upgrading Total Project Safety IT Information Security Process To Manage Firms Sensitive Data Structure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Presenting upgrading total project safety it information security process to manage firms sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
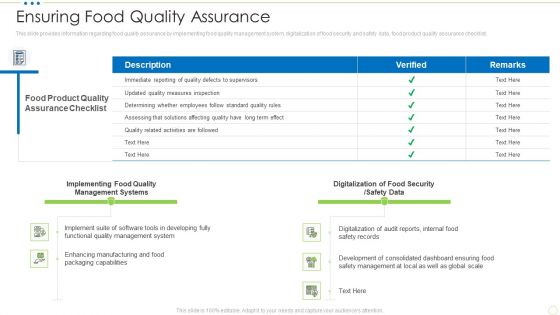
Ensuring Food Quality Assurance Food Security Excellence Ppt Infographic Template Graphic Images PDF
This slide provides information regarding food quality assurance by implementing food quality management system, digitalization of food security and safety data, food product quality assurance checklist. Deliver and pitch your topic in the best possible manner with this ensuring food quality assurance food security excellence ppt infographic template graphic images pdf. Use them to share invaluable insights on management, implementing, digitalization, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Internet Security Firewall Protection Vector Icon Ppt PowerPoint Presentation Pictures Smartart PDF
Presenting internet security firewall protection vector icon ppt powerpoint presentation pictures smartart pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including internet security firewall protection vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Techniques For Project Safety IT Information Security Process To Manage Firms Sensitive Data Designs PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver and pitch your topic in the best possible manner with this major techniques for project safety it information security process to manage firms sensitive data designs pdf. Use them to share invaluable insights on privileged password management, daily tasks performed by network administrator, network security audit checklist and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Online Security Lock To Prevent Internet Threats Ppt PowerPoint Presentation File Layouts PDF
Presenting online security lock to prevent internet threats ppt powerpoint presentation file layouts pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including online security lock to prevent internet threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
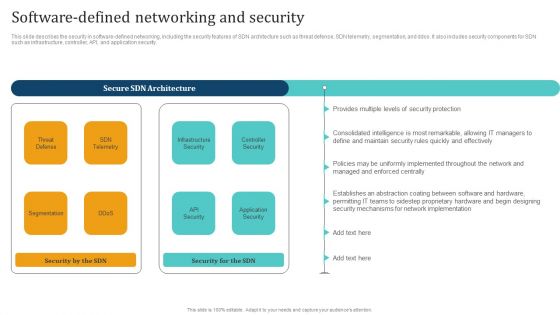
Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing Information Technology Security 30 Days Plan Ppt Professional Examples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 30 days plan ppt professional examples pdf bundle. Topics like managing information technology security 30 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing Information Technology Security 60 Days Plan Ppt Ideas Graphics PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this managing information technology security 60 days plan ppt ideas graphics pdf . Use them to share invaluable insights on managing information technology security 60 days plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Managing Information Technology Security 60 Days Ppt Infographic Template Samples PDF
This slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative managing information technology security 60 days ppt infographic template samples pdf bundle. Topics like managing information technology security 60 days plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Timeline For The Implementation Of Electronic Information Security Ppt Infographic Template Information PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative cybersecurity timeline for the implementation of electronic information security ppt infographic template information pdf bundle. Topics like security documentation, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline For The Implementation Of Information Technology Security Ppt Portfolio Slideshow PDF
This slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of information technology security ppt portfolio slideshow pdf bundle. Topics like timeline for the implementation of information technology security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Requirement Of Information Technology Security In Different Sectors Ppt Ideas Shapes PDF
This slide depicts the requirement of network security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with requirement of information technology security in different sectors ppt ideas shapes pdf bundle. Topics like requirement of information technology security in different sectors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Feature In Internet Modem Vector Icon Ppt PowerPoint Presentation File Professional PDF
Pitch your topic with ease and precision using this security feature in internet modem vector icon ppt powerpoint presentation file professional pdf. This layout presents information on security feature in internet modem vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Security Assessment By Computer Forensics Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting internet security assessment by computer forensics ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including internet security assessment by computer forensics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Plan With Key Trends Ppt PowerPoint Presentation Summary Mockup PDF
Showcasing this set of slides titled internet security threat analysis plan with key trends ppt powerpoint presentation summary mockup pdf. The topics addressed in these templates are internet security threat analysis plan with key trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
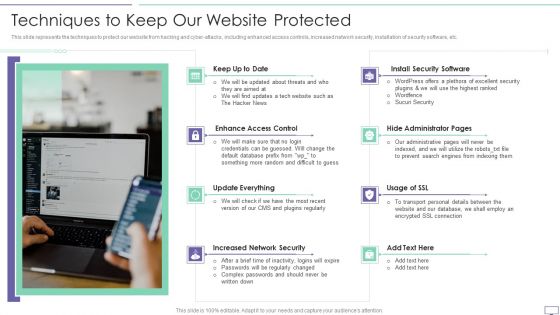
IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Data Security Industry Report Cybersecurity Industry Competitor Analysis With Attributes IR SS V
The slide presents the key players in the cybersecurity industry. The purpose of the slide is to provide glimpse and competitor analysis of major players in the cybersecurity industry to gain insight into their products, services, and sales. It covers companies such as Palo alto networks, Inc, Fortinet, CrowdStrike, Checkpoint, and Zscaler, Inc. Present like a pro with Global Data Security Industry Report Cybersecurity Industry Competitor Analysis With Attributes IR SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. This Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Security For Network Protection From Unauthorized Access Vector Icon Ppt PowerPoint Presentation File Summary PDF
Presenting this set of slides with name security for network protection from unauthorized access vector icon ppt powerpoint presentation file summary pdf. This is a three stage process. The stages in this process are security for network protection from unauthorized access vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Network Protection With Firewall Security System Ppt PowerPoint Presentation File Pictures PDF
Presenting network protection with firewall security system ppt powerpoint presentation file pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network protection with firewall security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
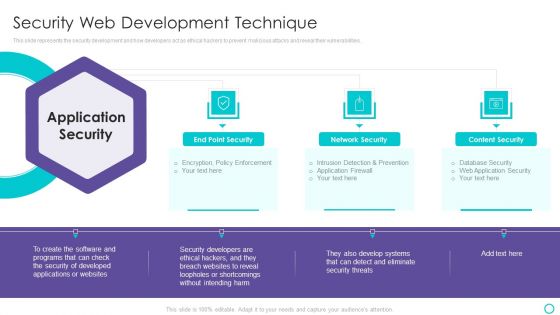
Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
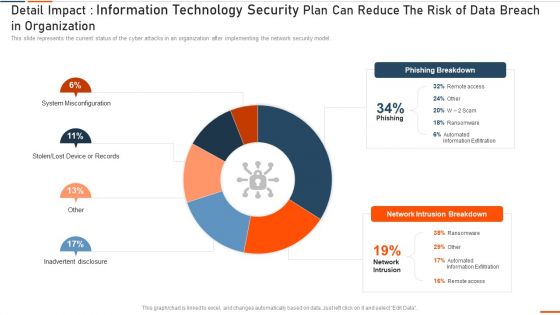
Detail Impact Information Technology Security Plan Can Reduce Ppt Show Slide Download PDF
This slide represents the current status of the cyber attacks in an organization after implementing the network security model. Deliver an awe inspiring pitch with this creative it security detail impact detail impact information technology security plan can reduce ppt show slide download pdf bundle. Topics like detail impact information technology security plan can reduce the risk of data breach in organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Corporate Data Management For Network Security Vector Icon Ppt PowerPoint Presentation Icon Portfolio PDF
Pitch your topic with ease and precision using this corporate data management for network security vector icon ppt powerpoint presentation icon portfolio pdf. This layout presents information on corporate data management for network security vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Importance Of Firewall Network Security In Business Vector Icon Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name importance of firewall network security in business vector icon ppt powerpoint presentation file aids pdf. This is a three stage process. The stages in this process are importance of firewall network security in business vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF
Help your business to create an attention-grabbing presentation using our Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide Safeguarding Network With SDN Security Ppt File Summary PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
Virtual Private Network With Internet Security Firewall Protection Ppt PowerPoint Presentation File Master Slide PDF
Persuade your audience using this virtual private network with internet security firewall protection ppt powerpoint presentation file master slide pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network with internet security firewall protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
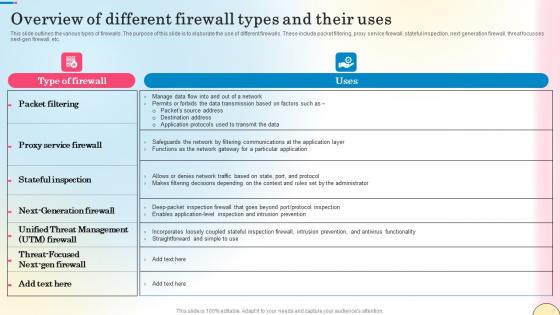
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF
This slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Welcome to our selection of the Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
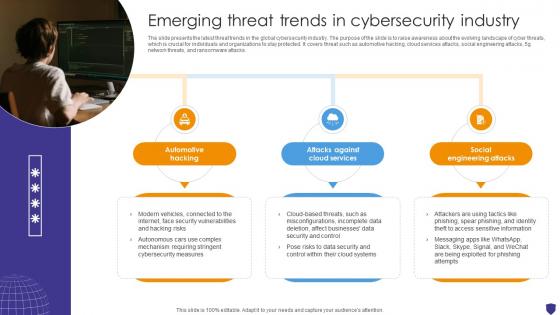
Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
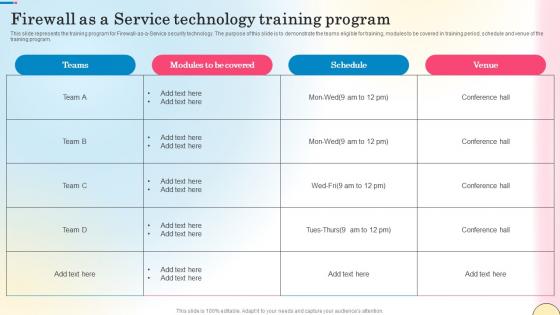
Firewall As A Service Technology Training Program Network Security Brochure Pdf
This slide represents the training program for Firewall-as-a-Service security technology. The purpose of this slide is to demonstrate the teams eligible for training, modules to be covered in training period, schedule and venue of the training program. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Firewall As A Service Technology Training Program Network Security Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Firewall As A Service Technology Training Program Network Security Brochure Pdf
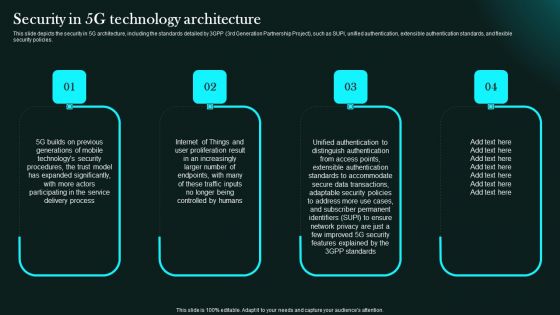
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
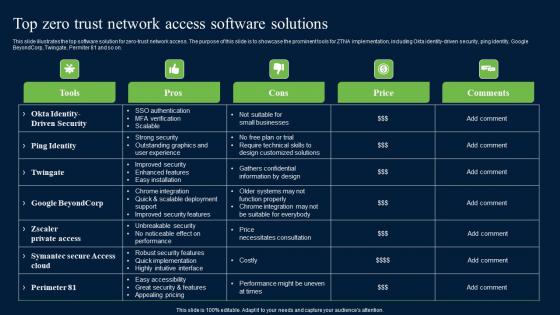
Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Business Diagram Correct Wrong And Security Icons For Antivirus Software Presentation Template
This business slide displays correct wrong and security icons. Download this slide to depict antivirus and software protection related concepts. It will make your presentation look professional and keep your audience mesmerized.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
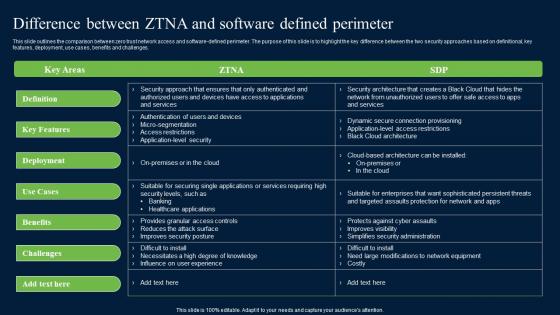
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Icon Of Wireless Network Security System For WIFI Networks With Smart Lock Sample PDF
Persuade your audience using this icon of wireless network security system for wifi networks with smart lock sample pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including icon of wireless network security system for wifi networks with smart lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
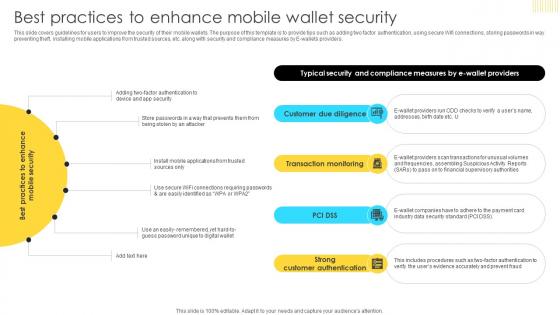
Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V
This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers. There are so many reasons you need a Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Network Security Devices Computer Network Ppt PowerPoint Presentation Visual Aids Background Images Cpb Pdf
Presenting this set of slides with name network security devices computer network ppt powerpoint presentation visual aids background images cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like network security devices computer network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
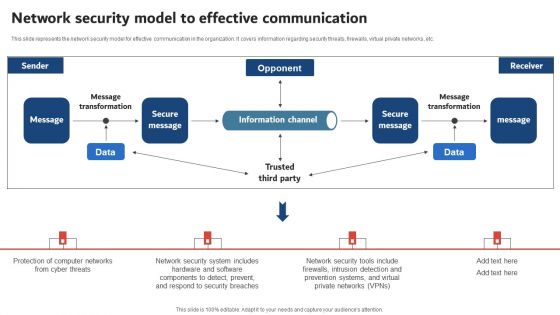
Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
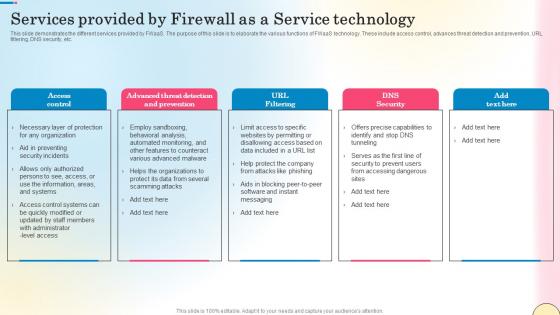
Services Provided By Firewall As A Service Technology Network Security Infographics Pdf
This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc. There are so many reasons you need a Services Provided By Firewall As A Service Technology Network Security Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Security Software Deployed To Countermeasure Internet Threats Ppt PowerPoint Presentation Gallery Icon PDF
Persuade your audience using this security software deployed to countermeasure internet threats ppt powerpoint presentation gallery icon pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security software deployed to countermeasure internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home