Ios
Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF
This slide depicts an system architecture for complete threat evaluation using cyber intelligence to control the number of cyber-attacks. It includes testing methods, functions, categories, items and properties. Showcasing this set of slides titled Intelligence Architecture For Comprehensive Threat Evaluation Mockup PDF. The topics addressed in these templates are Performance, Timeliness, Customization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
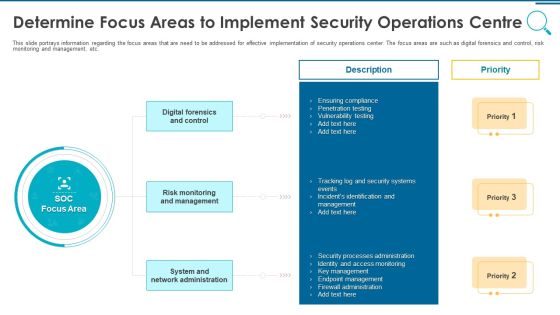
Information And Technology Security Operations Determine Focus Areas To Implement Security Operations Centre Download PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a information and technology security operations determine focus areas to implement security operations centre download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Enhanced Protection Corporate Event Administration Determine Focus Areas To Implement Security Operations Centre Icons PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a enhanced protection corporate event administration determine focus areas to implement security operations centre icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
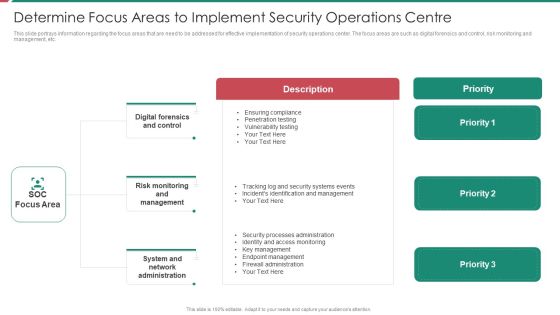
Security And Process Integration Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security and process integration determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
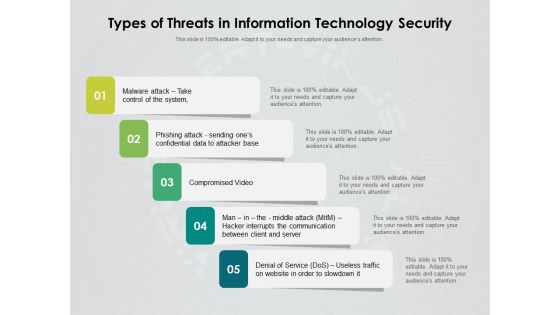
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Relocation Of Business Process Offshoring Own Office Offshoring Model Mockup PDF
This slide shows the own office model which is used for larger businesses or for extending the team for various reasons like embarking on a new project, enhancing the line of services, or products etc. This is a relocation of business process offshoring own office offshoring model mockup pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team, processes, systems, quality control, employees, setup and management costs, legal and compliance requirements fulfilled. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Minimize Cloud Risks Medical Care Business Case Competition Challenge And Solutions 3 Employee Error Portrait PDF
This slide shows the problem that the company is facing related to improper and unaware employee behavior leading to data loss and misuse. Also, some solutions are provided to solve the problem. Deliver and pitch your topic in the best possible manner with this minimize cloud risks medical care business case competition challenge and solutions 3 employee error portrait pdf. Use them to share invaluable insights on security training programs, operating system maintenance, financial control procedures, training programs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financial Technology Firm Addressing Key Challenges Faced By Prospect Ideas PDF
This slide caters details about key challenges faced by prospects in terms of cost, time consuming process, no control over employees spending, outdated bank interface system, etc. This is a financial technology firm addressing key challenges faced by prospect ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like consuming process, technology, business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
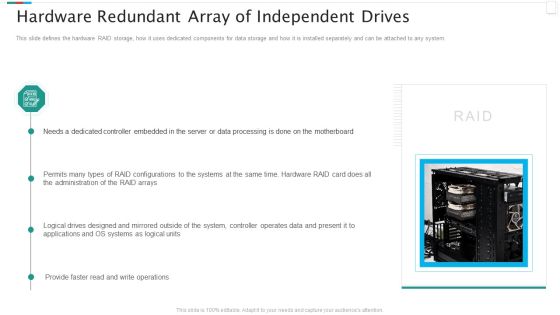
Redundant Array Of Independent Disks Storage IT Hardware Redundant Array Of Independent Drives Designs PDF
This slide defines the hardware RAID storage, how it uses dedicated components for data storage and how it is installed separately and can be attached to any system. Deliver an awe inspiring pitch with this creative redundant array of independent disks storage it hardware redundant array of independent drives designs pdf bundle. Topics like data processing, server, administration, controller operates data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Tools Used In Cloud Security Cloud Computing Security IT Ppt Background Images PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a tools used in cloud security cloud computing security it ppt background images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like silver sky, centrify, doc tracker, proofpoint, whitehat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How Does Cloud Security Work Cloud Computing Security IT Ppt Show Graphics Design PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting how does cloud security work cloud computing security it ppt show graphics design pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data security, access management, governance, business continuity planning, legal compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Vital Success Factors Associated To Devops Automation Topics PDF
This slide provides information regarding the critical success factors associated to DevOps in terms of executing DevOps CI CD automation toolset, tracking and KPIs. Presenting addressing vital success factors associated to devops automation topics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like automation, systems, control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Fintech Solutions Company Venture Capitalist Funding Elevator Addressing Key Challenges Faced By Prospect Slides PDF
This slide caters details about key challenges faced by prospects in terms of cost, time consuming process, no control over employees spending, outdated bank interface system, etc. Presenting fintech solutions company venture capitalist funding elevator addressing key challenges faced by prospect slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like addressing key challenges faced by prospect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot And Digital Twin To Reduce Costs Post Covid How Rail Transportation Operates After Inspiration PDF
This slide shows the functioning of rail transport industry after successful implementation of IoT and digital twin such as connected commuter, mobility as a service, etc. Presenting iot and digital twin to reduce costs post covid how rail transportation operates after inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like connected commuter, mobility as a service, rolling stock predictive maintenance, automation of train control systems, digital interlocking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Collection Of Quality Assurance PPT 6 Steps To Conduct Root Cause Analysis Ideas PDF
Following slide portrays seven steps of hazard analysis critical control point for ensuring food safety. Steps covered are perform a hazard analysis, determine CCPs, set critical limits, establish a monitoring system, establish corrective actions, verification procedures and recordkeeping procedures. Presenting collection of quality assurance ppt 6 steps to conduct root cause analysis ideas pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like analysis, develop, plan, measurable, determine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Iot Digital Twin Technology Post Covid Expenditure Management How Rail Transportation Operates Guidelines PDF
This slide shows the functioning of rail transport industry after successful implementation of IoT and digital twin such as connected commuter, mobility as a service, etc. This is a iot digital twin technology post covid expenditure management how rail transportation operates guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like informative, service, purchasing, control systems, punctuality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strawman Proposal For Enterprise Critical Thinking Quality Check Schedule Professional PDF
Quality check will be done regular intervals. These checks can be on daily, weekly, monthly, quarterly basis by reviewing product on several parameters. This is a strawman proposal for enterprise critical thinking quality check schedule professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like replace filters analyzers, temperature control analyzers, cleaning ac filter, printer maintenance, system audit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Technology Framework IT Pros And Cons Of Private Blockchain Brochure PDF
This slide represents the use case of blockchain in the government sector how it would benefit voting, data security, budgeting and corruption. This is a blockchain technology framework it blockchain technology in government sector designs pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital paperwork systems, interagency data control, fighting corruption, data security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

E Commerce Distribution Structure With Order Shipping Themes PDF
This slide exhibits E commerce distribution structure with order shipping and utilization. It includes multiple steps such as- warehouse inventory control via centralized inventory management system and quality assessment of products. Showcasing this set of slides titled e commerce distribution structure with order shipping themes pdf. The topics addressed in these templates are warehousing, order process, delivery. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Storage For Compliance Ppt Pictures Background Images PDF
This slide depicts the use of cloud storage services for data compliance through compliance controls, WORM restrictions, and audit log solutions. This is a cloud storage for compliance ppt pictures background images pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, implement, data, requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Threat Status In Project Management Dashboard With Reported Incidents Introduction PDF
This slide represents open and closed cybersecurity risk incidents in areas such as 2 factor authentication, daily backup data etc. Showcasing this set of slides titled cybersecurity threat status in project management dashboard with reported incidents introduction pdf. The topics addressed in these templates are application control, application patch, operating system patch, restricted admin privileges, untrusted application alert. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
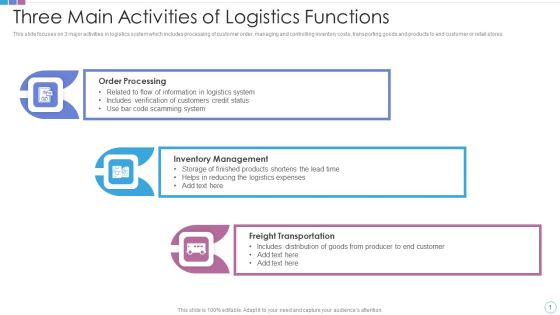
Three Main Activities Of Logistics Functions Diagrams PDF
This slide focuses on 3 major activities in logistics system which includes processing of customer order, managing and controlling inventory costs, transporting goods and products to end customer or retail stores Presenting three main activities of logistics functions diagrams pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including order processing, inventory management, freight transportation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
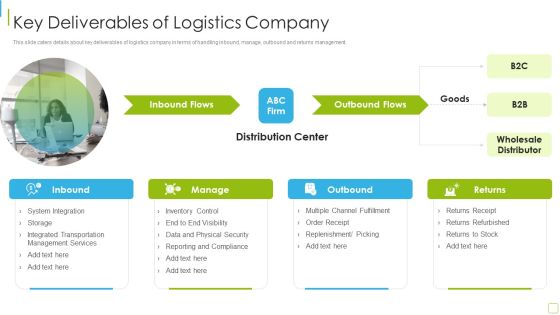
Performance Analysis Of New Product Development Key Deliverables Of Logistics Company Information PDF
This slide caters details about key deliverables of logistics company in terms of handling inbound, manage, outbound and returns management. Presenting performance analysis of new product development key deliverables of logistics company information pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like system integration, management services, inventory control, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective Remuneration Management Talent Acquisition Retention Challenges In Effective Compensation Rules PDF
The slide shows the challenges that are involved in implementing a structured and efficient compensation management system in the company. This is a effective remuneration management talent acquisition retention challenges in effective compensation rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like petitive pay, forms of compensation, overseas business operations, controlling labor costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Remuneration Management Talent Acquisition Retention Factors Affecting Compensation Management Microsoft PDF
The slide shows the external factors that effect the compensation management system of the company and these factors are externally related to the organization. This is a effective remuneration management talent acquisition retention factors affecting compensation management microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like labor market conditions, economic conditions, prevailing wage level, government control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Purpose Digital Twin Internet Things Reducing Costs After COVID Era How Rail Transportation Operates Template PDF
This slide shows the functioning of rail transport industry after successful implementation of IoT and digital twin such as connected commuter, mobility as a service, etc. Presenting purpose digital twin internet things reducing costs after covid era how rail transportation operates template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like connected commuter, mobility service, predictive maintenance, control systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Partnership With Servicing Company Improving Internal Operations Functional Offshoring Model Slides PDF
This slide shows the functional offshoring model, wherein we can offshore part of our operations to another firm to get functional expertise in the organization. Presenting partnership with servicing company improving internal operations functional offshoring model slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like insurance services, deliverables, process, systems, quality controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
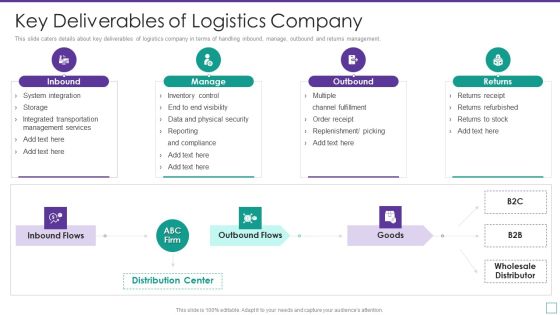
Supply Chain Logistics Fundraising Pitch Deck Key Deliverables Of Logistics Company Infographics PDF
This slide caters details about key deliverables of logistics company in terms of handling inbound, manage, outbound and returns management. This is a supply chain logistics fundraising pitch deck key deliverables of logistics company infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system integration, inventory control, channel fulfillment, returns refurbished. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Sales Comparison With Actual And Predictive Data Ppt Model Slide PDF
The following slide highlights the annual sales forecast report for business illustrating key headings which includes product, last year, forecast, actual, number of customers, average sales per customer and net sales. Showcasing this set of slides titled business sales comparison with actual and predictive data ppt model slide pdf. The topics addressed in these templates are antivirus protection, cloud solutions, system controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

How Rail Transportation Operates After Implementing Iot And Digital Twin Portrait PDF
This slide shows the functioning of rail transport industry after successful implementation of IoT and digital twin such as connected commuter, mobility as a service, etc. This is a how rail transportation operates after implementing iot and digital twin portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service, control systems, digital interlocking, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
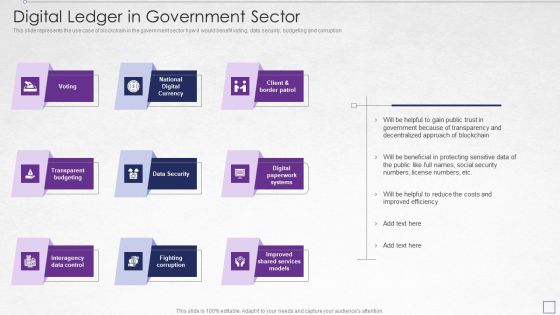
Digitized Record Book Technology Digital Ledger In Government Sector Designs PDF
This slide represents the use case of blockchain in the government sector how it would benefit voting, data security, budgeting and corruption. Presenting digitized record book technology digital ledger in government sector designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data security, transparent budgeting, interagency data control, fighting corruption, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
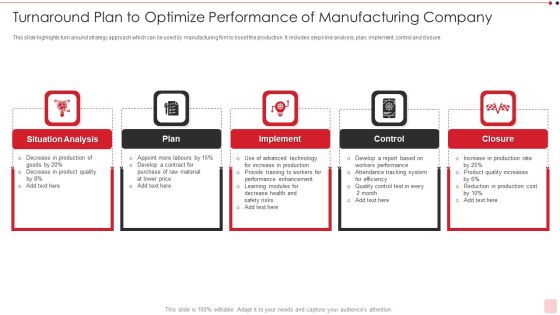
Turnaround Plan To Optimize Performance Of Manufacturing Company Ideas PDF
This slide highlights turn around strategy approach which can be used by manufacturing firm to boost the production. It includes steps like analysis, plan, implement, control and closure Persuade your audience using this turnaround plan to optimize performance of manufacturing company ideas pdf This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including situation analysis, implement, attendance tracking system Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
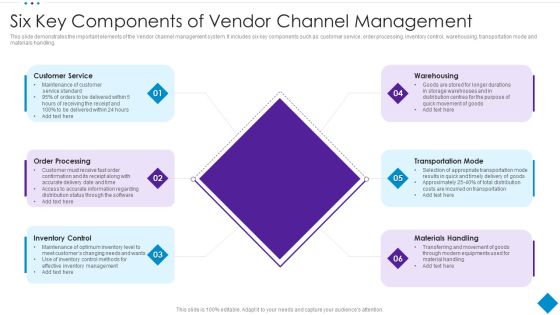
Six Key Components Of Vendor Channel Management Template PDF
This slide demonstrates the important elements of the Vendor channel management system. It includes six key components such as customer service, order processing, inventory control, warehousing, transportation mode and materials handling. Persuade your audience using this Six Key Components Of Vendor Channel Management Template PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Service, Transportation Mode, Materials Handling. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing Business Analytics Framework Determine Overview Of Established Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Developing Business Analytics Framework Determine Overview Of Established Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Command And Control, Incident Response, Threat Intelligence You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. This is a Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Solutions, Advanced Threats, Cipher Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Central Repository, Access Management, Authorization Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
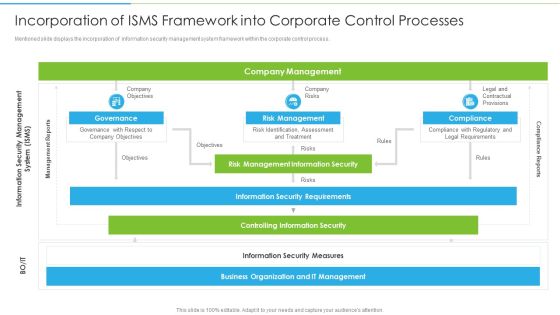
Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process. This is a Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Company Objectives, Company Management, Company Risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Automating Supply Chain Process For Adopting Warehouse Automation Strategies Background PDF
This slide covers the process of warehouse automation. It includes steps such as creating implementation plan, collecting critical data, evaluating inventory control, warehouse management system automation, determining warehouse automation type, etc. Deliver and pitch your topic in the best possible manner with this Automating Supply Chain Process For Adopting Warehouse Automation Strategies Background PDF. Use them to share invaluable insights on Create Implementation, Collect Critical, Evaluate Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Contents For QA Plan And Process Set 3 7 Steps Of Haccp To Ensure Food Safety Diagrams PDF
Following slide portrays seven steps of hazard analysis critical control point for ensuring food safety. Steps covered are perform a hazard analysis, determine CCPs, set critical limits, establish a monitoring system, establish corrective actions, verification procedures and recordkeeping procedures.Deliver an awe inspiring pitch with this creative Contents For QA Plan And Process Set 3 7 Steps Of Haccp To Ensure Food Safety Diagrams PDF bundle. Topics like Determine Critical, Establish A Monitoring, Establish Corrective can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

What Are The Downsides Of A Cloud Security Download PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting What Are The Downsides Of A Cloud Security Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Cloud Security Work Governance Professional PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting How Does Cloud Security Work Governance Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Access Management, Business Continuity Planning, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
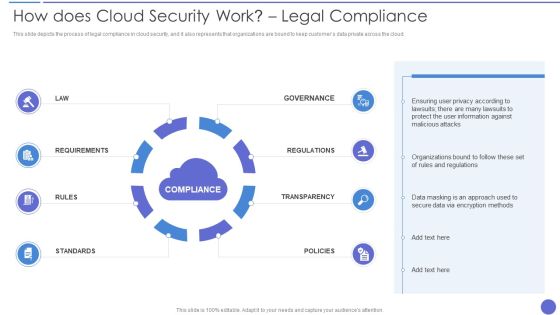
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.This is a Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Business Continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment What Are The Downsides Of A Cloud Security Infographics PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches.This is a Cloud Security Assessment What Are The Downsides Of A Cloud Security Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Services Organizations, Company Employees, Monetary Losses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Computer Virtualization Types Of End User Computing Mockup PDF
This slide represents the types of end user computing and it includes traditional end user computing, end user control and end user development.Presenting Computer Virtualization Types Of End User Computing Mockup PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Departments Purchase, Environment Strong, Computer Systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Governance Maturity Model Framework Ppt PowerPoint Presentation Gallery Layout PDF
This slide depicts data governance maturity model framework that defines the roles, responsibilities, policies, and procedures of initiatives taken up. The framework lists core initiatives and programmes which are controlled by an overall data management system. Pitch your topic with ease and precision using this Data Governance Maturity Model Framework Ppt PowerPoint Presentation Gallery Layout PDF. This layout presents information on Core Initiatives, Core Programmes, Data Access Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
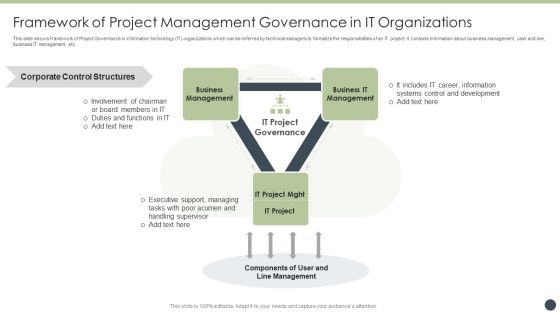
Framework Of Project Management Governance In It Organizations Information PDF
This slide shows Framework of Project Governance in information technology IT organizations which can be referred by technical managers to formalize the responsibilities of an IT project. It contains information about business management, user and line, business IT management, etc. Presenting Framework Of Project Management Governance In It Organizations Information PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Business Management, Development, Systems Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Parallel Computing Processing Multiple Instruction And Single Data Stream MISD Professional PDF
This slide outlines another type of parallel processing that is MISD, and its components such as memory, control unit, processor, data stream, and instruction stream. As no actual system has been built utilizing the MISD architecture, it is solely of theoretical importance. Deliver an awe inspiring pitch with this creative Parallel Computing Processing Multiple Instruction And Single Data Stream MISD Professional PDF bundle. Topics like Multiple Instruction, Single Data Stream can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Critical Violations Security Dashboard With KPI Metrics Graphics PDF
This slide shows dashboard of security to mitigate violation by prioritizing KPIs. It includes application control, operating systems, restrict admin privileges, multi factor authentication and backup of important data. Showcasing this set of slides titled Critical Violations Security Dashboard With KPI Metrics Graphics PDF. The topics addressed in these templates are Risk Model, Application Components, Technologies Overview. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
 Home
Home