Introduction To Cybersecurity
Visionary Guide To Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V
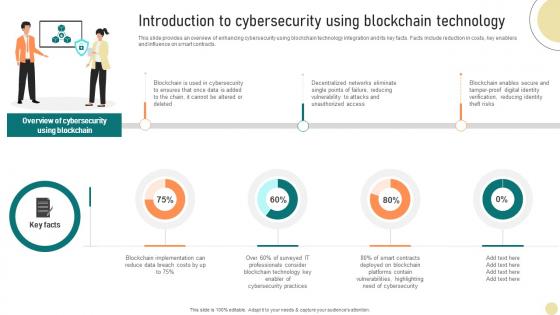
This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Slidegeeks has constructed Visionary Guide To Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
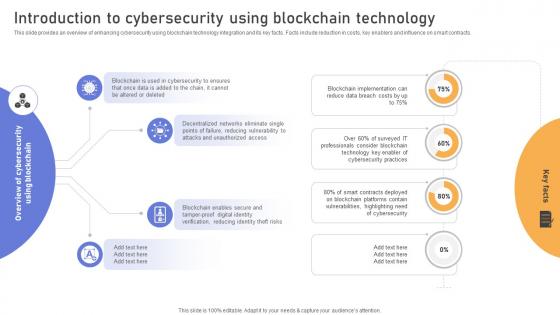
Comprehensive Look At Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V
This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Retrieve professionally designed Comprehensive Look At Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
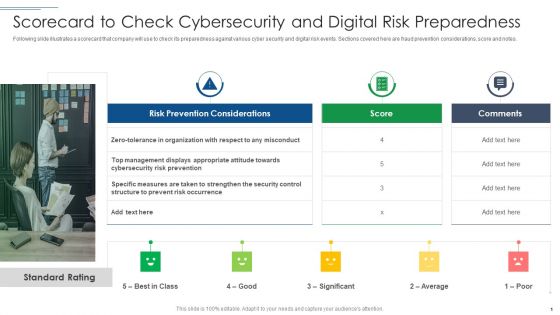
IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
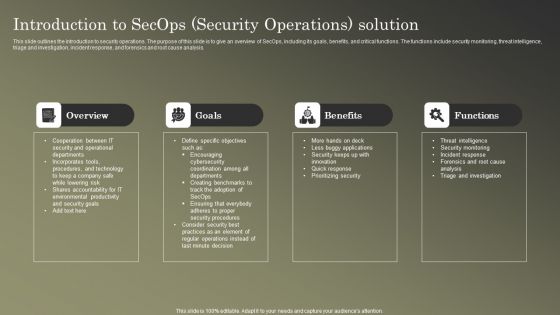
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Cybersecurity Guidelines IT Introduction To Information Technology Policy Icons PDF
This slide represents the introduction to information technology policy, and it also describes the components of IT policy, such as investments, business applications, architecture, and infrastructure. The Cybersecurity Guidelines IT Introduction To Information Technology Policy Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
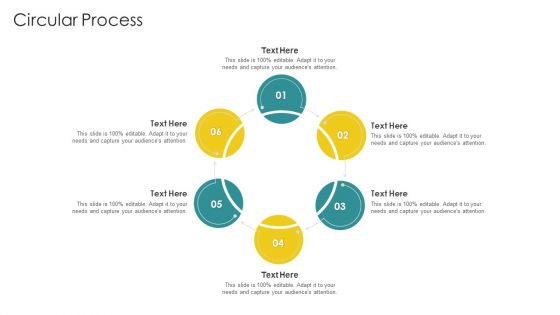
Cybersecurity Risk Scorecard Circular Process Introduction PDF
This is a cybersecurity risk scorecard circular process introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like circular process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Online Cybersecurity Training Programs For Workforce Icon Introduction PDF
Persuade your audience using this Online Cybersecurity Training Programs For Workforce Icon Introduction PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Online Cybersecurity, Training Programs, Workforce Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
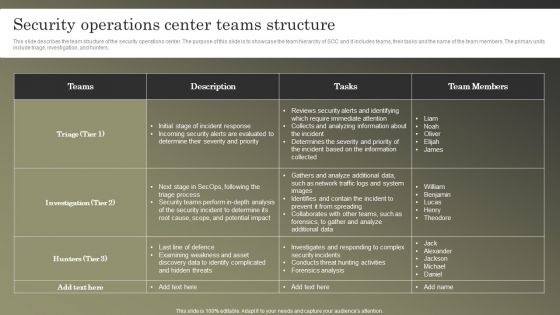
Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF
This slide describes the team structure of the security operations center. The purpose of this slide is to showcase the team hierarchy of SOC and it includes teams, their tasks and the name of the team members. The primary units include triage, investigation, and hunters. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
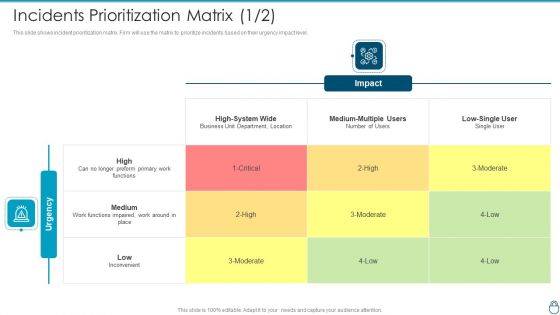
Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Business Introduction PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Business Introduction PDF bundle. Topics like Business Unit Department, Functions Impaired, Medium Multiple can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
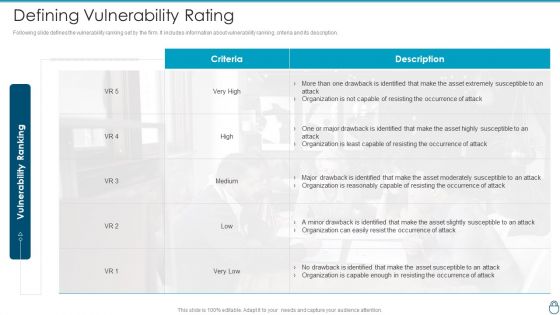
Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF Use them to share invaluable insights on Organization Is Not Capable, Resisting The Occurrence Of Attack, Drawback Is Identified and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Cybersecurity Risk Administration Plan Introduction PDF
This is a Table Of Contents Cybersecurity Risk Administration Plan Introduction PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Present Scenario, Training And Budget, Managing The Risks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Cybersecurity Risk Assessment And Administration Plan Introduction PDF
Welcome to our selection of the Agenda For Cybersecurity Risk Assessment And Administration Plan Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Mitigating Cybersecurity Threats And Vulnerabilities Roles And Responsibilities Introduction PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Operations Cybersecops Vulnerabilities Tracking Dashboard For Secops Introduction PDF
This slide represents the vulnerabilities tracking dashboard for SecOps. The purpose of this slide is to demonstrate the tracking of vulnerabilities of an organizations assets, services with the most vulnerabilities, mean time to remediate, and the average age of vulnerabilities. This modern and well arranged Cybersecurity Operations Cybersecops Vulnerabilities Tracking Dashboard For Secops Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Guidelines IT Information Security Policy For Employees Introduction PDF
This slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cybersecurity Guidelines IT Information Security Policy For Employees Introduction PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF
The following slide showcases various courses associated with cyber security training to aware workforce with latest security threats. It includes elements such as course name, features, cost, duration etc. Presenting Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Introduction To Cybersecurity, Cyber Online, IT And Cybersecurity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
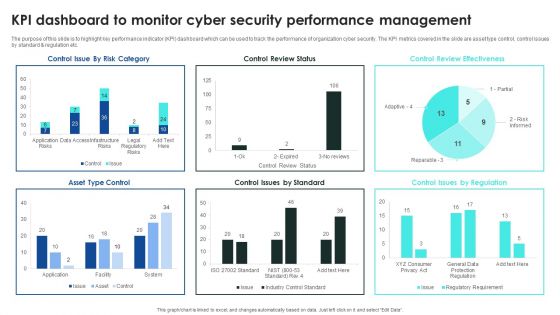
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF
Present like a pro with Implementing Cybersecurity Awareness Program To Prevent Attacks Tracking Sheet To Monitor The Performance Introduction PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF
This slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing, Malware, Blackmail Hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Guidelines IT Timeline To Develop An Information Technology Policy Introduction PDF
This slide represents the timeline to develop an information technology policy and it includes all the steps to be performed while developing an IT policy. Present like a pro with Cybersecurity Guidelines IT Timeline To Develop An Information Technology Policy Introduction PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc.Welcome to our selection of the Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
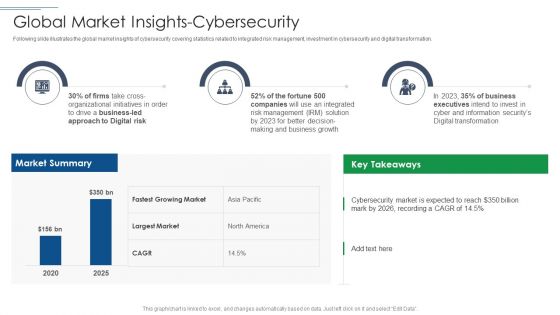
IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF bundle. Topics like Business Growth, Risk Management, Organizational Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Managing Electronic Information Security 90 Days Plan Ppt Pictures Example Introduction PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this cybersecurity managing electronic information security 90 days plan ppt pictures example introduction pdf. Use them to share invaluable insights on measured, awareness, security, communication methods and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF
This is a IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technical Control, Management Controls, Operational Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF
This slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti-phishing, data discovery, and packet-level visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Secops Software Tools Based On Threats Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Make sure to capture your audiences attention in your business displays with our gratis customizable Identifying The Severity Level And Impact Improving Cybersecurity With Incident Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this IT Security Hacker Cybersecurity Awareness Training For Staff Guidelines PDF. Use them to share invaluable insights on Project Managers, Senior Executives, Security Introduction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
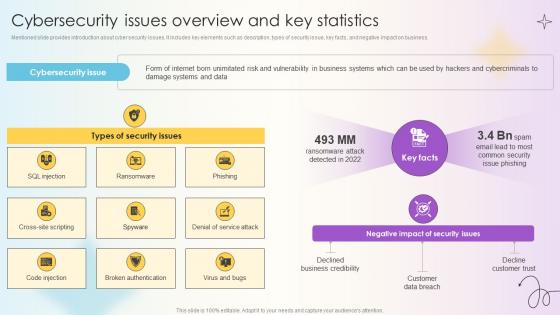
Managing Technical And Non Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Managing Technical And Non Cybersecurity Issues Overview And Key Statistics was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Managing Technical And Non Cybersecurity Issues Overview And Key Statistics.

Web Consulting Business Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Consulting Business Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
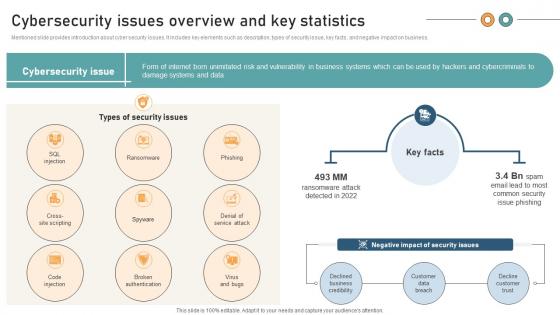
Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
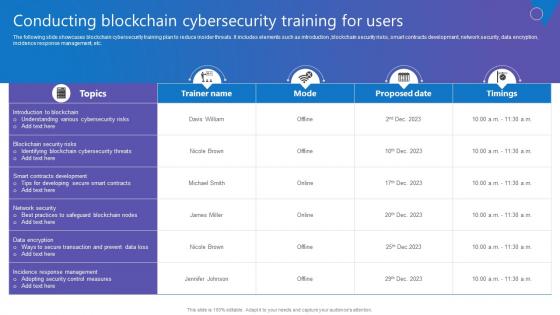
Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
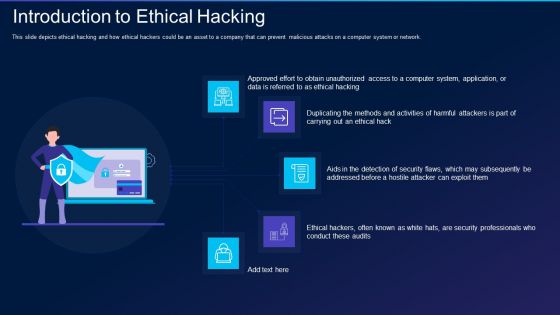
Cyber Exploitation IT Introduction To Ethical Hacking Introduction PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. This is a cyber exploitation it introduction to ethical hacking introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to ethical hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financial Modelling With Quantum Computing Ppt Ideas Introduction PDF
This slide represents the application of quantum computing in financial modeling, and it also depicts how current models are not sufficient for financial services. Deliver and pitch your topic in the best possible manner with this Financial Modelling With Quantum Computing Ppt Ideas Introduction PDF. Use them to share invaluable insights on Cybersecurity Systems, Asset Valuation, Portfolio Analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
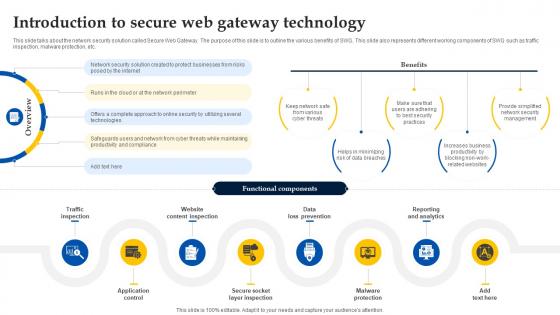
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
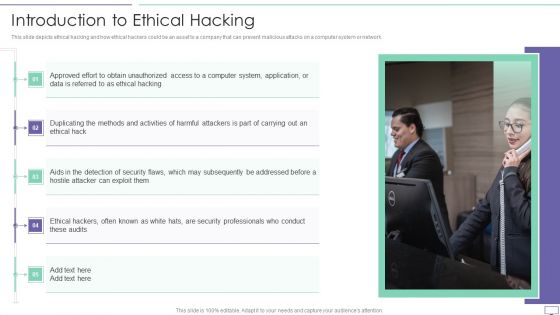
IT Security Hacker Introduction To Ethical Hacking Graphics PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network.This is a IT Security Hacker Introduction To Ethical Hacking Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Approved Effort, Data Is Referred, Ethical Hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
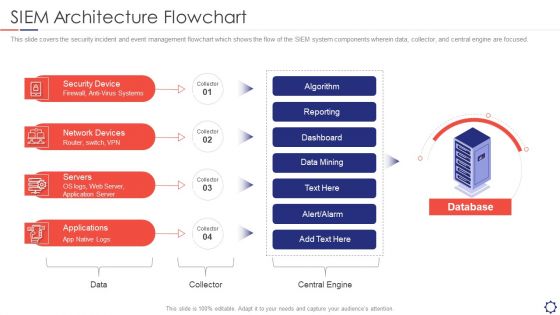
SIEM Architecture Flowchart Ppt Show Introduction PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart ppt show introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
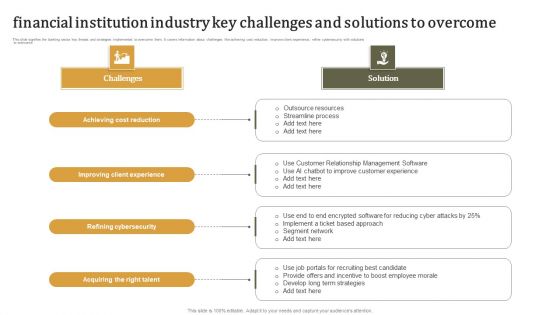
Financial Institution Industry Key Challenges And Solutions To Overcome Introduction PDF
This slide signifies the banking sector key threats and strategies implemented to overcome them. It covers information about challenges like achieving cost reduction, improve client experience, refine cybersecurity with solutions to overcome. Presenting Financial Institution Industry Key Challenges And Solutions To Overcome Introduction PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Financial Institution Industry, Key Challenges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
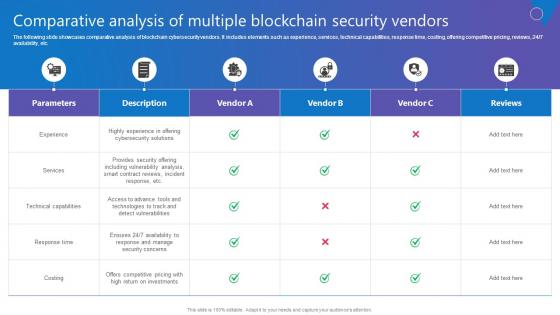
Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc. Do you know about Slidesgeeks Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Pharmaceutical Management Financial Performance Key Trends Ppt Portfolio Introduction PDF
Deliver and pitch your topic in the best possible manner with this pharmaceutical management financial performance key trends ppt portfolio introduction pdf. Use them to share invaluable insights on balancing inpatient and outpatient investments, updating financial leadership model, value based payments, creative partnerships and affiliations, cybersecurity investment, data analytics, avoid overbuilding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
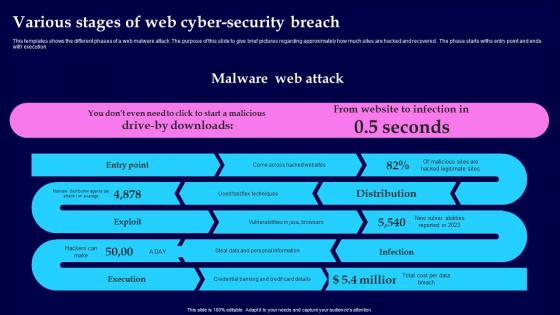
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Challenges Faced By Company Due To Lack Of Effective Software Application Deployment Project Plan Introduction PDF
This slide represents the problems faced by organizations due to lack of an effective software solution. It includes challenges such as cybersecurity, workload, analysis and data management, project management and digital transformation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Challenges Faced By Company Due To Lack Of Effective Software Application Deployment Project Plan Introduction PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Introduction To SD Wan Software Defined Wide Area Network Wide Area Network Services Background Pdf
This slide represents the overview of SD-WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD-WAN, including edge, orchestrator, and controller. If you are looking for a format to display your unique thoughts, then the professionally designed Introduction To SD Wan Software Defined Wide Area Network Wide Area Network Services Background Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Introduction To SD Wan Software Defined Wide Area Network Wide Area Network Services Background Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf
This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc. Retrieve professionally designed Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
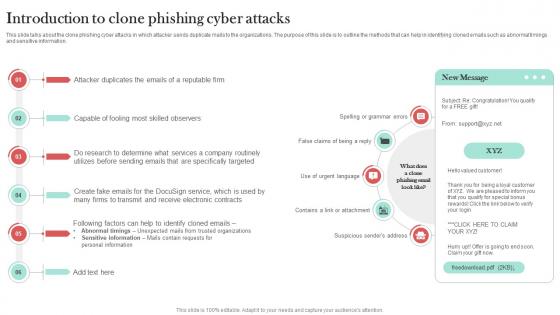
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Comprehensive Manual For Blockchain Introduction To Hybrid Blockchain Network BCT SS V
This slide covers brief summary of hybrid blockchain networks. It includes benefits such as working in a closed ecosystem, transactions are inexpensive and quick, safeguarding privacy, etc. along with characteristics comprising of closed ecosystem, data security, new regulations, transaction cost. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Manual For Blockchain Introduction To Hybrid Blockchain Network BCT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF
This slide represents the introduction to software defined networking that helps network managers to manage network resources faster. It also includes its components such as applications, control plane, SDN controller, SDN datapath, data plane, switches, and so on. Presenting this PowerPoint presentation, titled SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable SDN Security Architecture Introduction To Software Defined Networking SDN Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
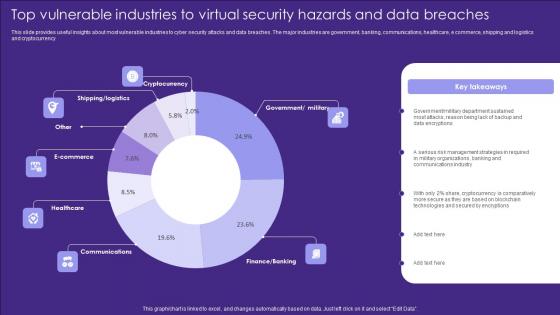
Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf
This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Pitch your topic with ease and precision using this Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf. This layout presents information on Cryptocurrency, Ecommerce, Healthcare. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
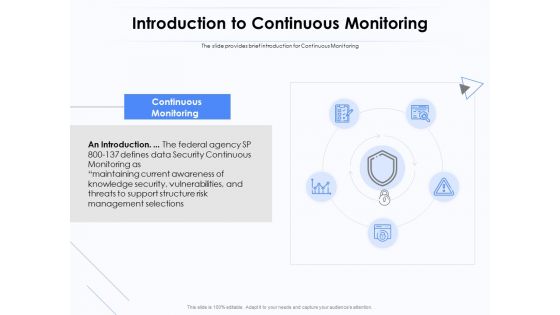
Network Monitoring Tool Overview Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Slide Download PDF
Presenting this set of slides with name network monitoring tool overview introduction to continuous monitoring ppt powerpoint presentation model slide download pdf. This is a five stage process. The stages in this process are continuous monitoring, introduction, data security, support structure, risk management selections, knowledge security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Impact Analysis Effective Security Management Introduction PDF
Presenting this set of slides with name strategies to mitigate cyber security risks impact analysis effective security management introduction pdf. The topics discussed in these slides are focus areas, security requirement, access rights authorized, incidents damaging, actual access violations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
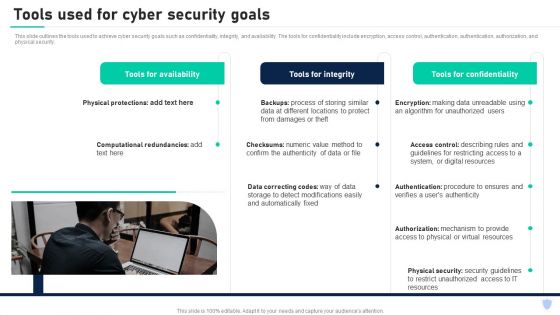
Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Virtual WAN Architecture Introduction To SD WAN Software Defined Wide Area Network Demonstration PDF
This slide represents the overview of SD-WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD-WAN, including edge, orchestrator, and controller. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Virtual WAN Architecture Introduction To SD WAN Software Defined Wide Area Network Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF
This slide represents security layers in internet banking system. It covers data layer, application layer, platform layer, network layer and physical layer. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Introduction To IT Project Development Using Optimized Tools For Continuous Monitoring Structure PDF
This slide provides the glimpse about the tools which can be used by the company for regular monitoring and optimization within the company. Deliver and pitch your topic in the best possible manner with this introduction to it project development using optimized tools for continuous monitoring structure pdf. Use them to share invaluable insights on management, system, network, security, information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Russia Ukraine War Influence On International Supply Chain Major Risks To Global Supply Chains Introduction PDF
This slide represents key risks disrupting global supply chain. It includes increase in commodity prices, export control, sanction, cyber security collateral damage and geopolitical instability.Presenting russia ukraine war influence on international supply chain major risks to global supply chains introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increase in commodity prices, export controls and sanctions, cyber security collateral damage In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
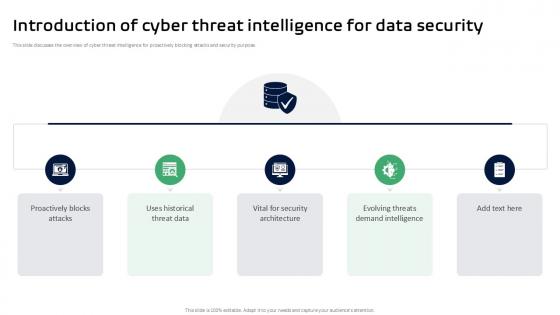
Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template
This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template

Table Of Contents For Zero Trust Network Security Introduction Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Zero Trust Network Security Introduction Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
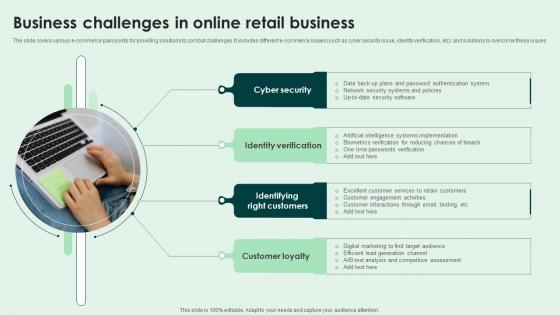
Business Challenges In Online Retail Business Introduction Pdf
The slide covers various e-commerce pain points for providing solutions to combat challenges. It includes different e-commerce issues such as cyber security issue, identity verification, etc and solutions to overcome these issues. Showcasing this set of slides titled Business Challenges In Online Retail Business Introduction Pdf. The topics addressed in these templates are Cyber Security, Identity Verification, Customer Loyalty. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Six Months Cyber Security Recognition Training Program Roadmap Introduction
We present our six months cyber security recognition training program roadmap introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months cyber security recognition training program roadmap introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
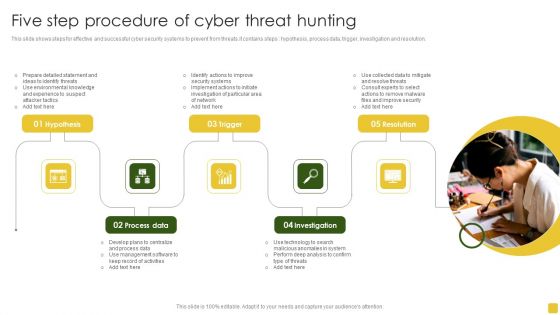
Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Predictive Data Model Outliers Model For Predictive Analytics Introduction PDF

Network Security Methods Using Distributed Ledger Technology Introduction Pdf
This slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication Pitch your topic with ease and precision using this Network Security Methods Using Distributed Ledger Technology Introduction Pdf This layout presents information on Strong Identities And Authentication, Securing Core Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
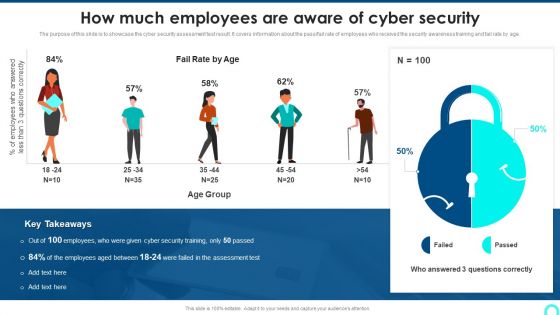
How Much Employees Are Aware Of Cyber Security Introduction PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age.This is a How Much Employees Are Aware Of Cyber Security Introduction PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Questions Correctly, Employees Answered, Employees Between. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Architectural Components Of Data Center Management Technology Introduction PDF
This slide outlines architectural components of datacentre technology with the purpose of meeting service level agreements to maintain efficiency and security. It covers network architecture, computing architecture, security and storage architecture. Presenting Key Architectural Components Of Data Center Management Technology Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Network Architecture, Computing Architecture, Security Architecture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
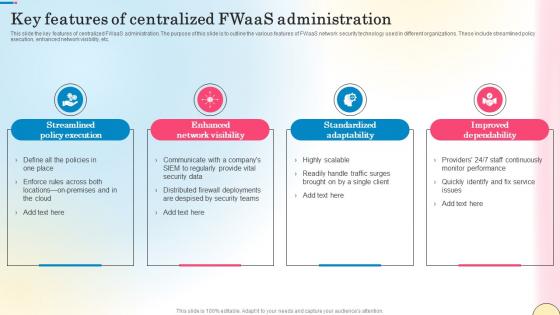
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

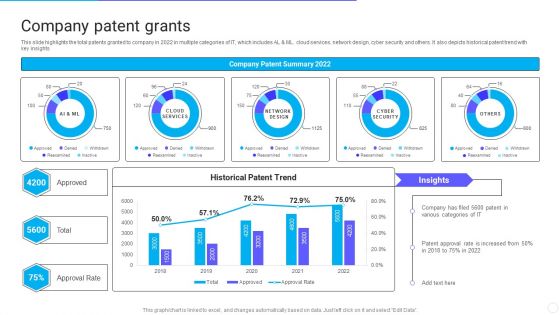
Company Patent Grants IT Software Development Company Profile Introduction PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver and pitch your topic in the best possible manner with this Company Patent Grants IT Software Development Company Profile Introduction PDF. Use them to share invaluable insights on Company Patent Summary, Historical Patent Trend and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
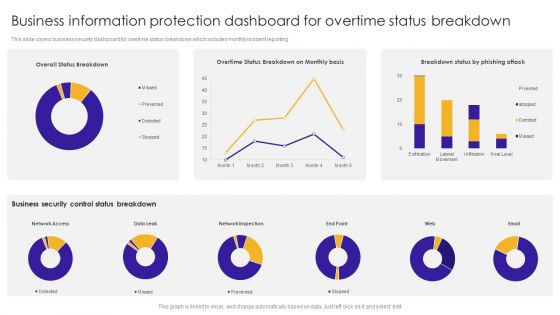
Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF
This slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting.Pitch your topic with ease and precision using this Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF. This layout presents information on Business Security, Control Status Breakdown, Network Inspection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
IT Application Services Company Outline Company Patent Grants Introduction PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative IT Application Services Company Outline Company Patent Grants Introduction PDF bundle. Topics like Approval Rate, Company Patent Grants can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Strategic Process Management Three Months Timeline Introduction
Presenting the cyber security strategic process management three months timeline introduction. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Five Ways For Re Training And Uptraining Warehouse Staff Introduction PDF
This slide represents the five ways in which organizations can reskill and upskill their warehouse staff. It includes five ways of reskilling staff such as safety upgradation, operational reskilling, project management, cybersecurity and warehouse management system. Persuade your audience using this Five Ways For Re Training And Uptraining Warehouse Staff Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Project Management, Cybersecurity, Operational Upskilling. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security IT Awareness Training For Staff Ppt Gallery Example Introduction PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this it security it awareness training for staff ppt gallery example introduction pdf. Use them to share invaluable insights on developers, organizations, senior executives, planning, strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
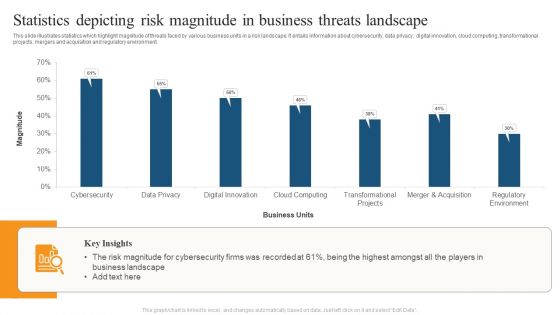
Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF
This slide illustrates statistics which highlight magnitude of threats faced by various business units in a risk landscape. It entails information about cybersecurity, data privacy, digital innovation, cloud computing, transformational projects, mergers and acquisition and regulatory environment. Pitch your topic with ease and precision using this Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF. This layout presents information on Business Units, Risk Magnitude, Business Landscape. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
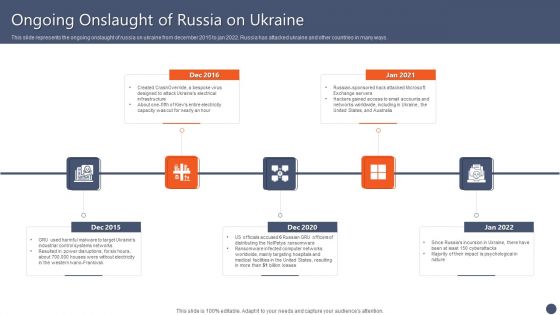
Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF
This slide represents the ongoing onslaught of russia on ukraine from december 2015 to jan 2022. Russia has attacked ukraine and other countries in many ways. If you are looking for a format to display your unique thoughts, then the professionally designed Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
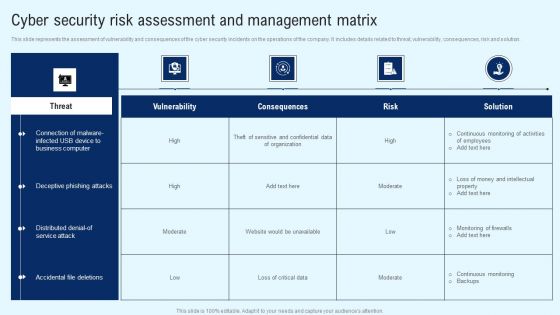
Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Get a simple yet stunning designed Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Managing Cyber Security Incident Response Plan Icon Ppt Ideas Example Introduction PDF
Presenting Managing Cyber Security Incident Response Plan Icon Ppt Ideas Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Managing Cyber Security, Incident Response, Plan Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
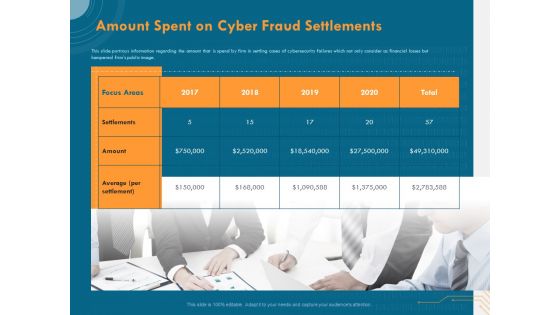
Cyber Security Implementation Framework Amount Spent On Cyber Fraud Settlements Ppt PowerPoint Presentation Summary Introduction PDF
Presenting this set of slides with name cyber security implementation framework amount spent on cyber fraud settlements ppt powerpoint presentation summary introduction pdf. This is a one stage process. The stages in this process are focus areas, settlements, amount, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Problems Solutions Ppt PowerPoint Presentation Styles Example Introduction Cpb
Presenting this set of slides with name cyber security problems solutions ppt powerpoint presentation styles example introduction cpb. This is an editable Powerpoint three stages graphic that deals with topics like cyber security problems solutions to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

List E Commerce Cyber Security Threats Ppt PowerPoint Presentation Slides Introduction Cpb
Presenting this set of slides with name list e commerce cyber security threats ppt powerpoint presentation slides introduction cpb. This is an editable Powerpoint four stages graphic that deals with topics like list e commerce cyber security threats to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
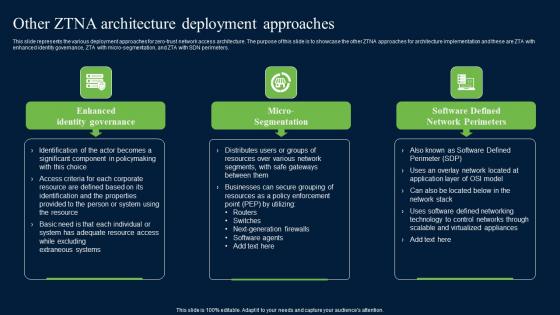
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
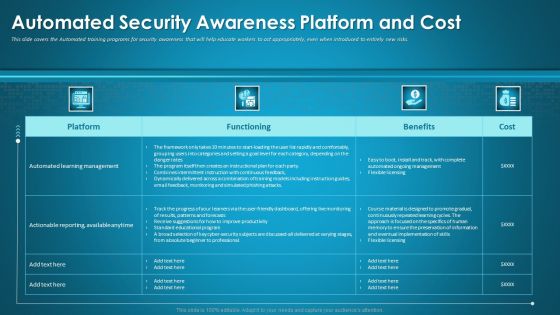
Organizational Network Staff Learning Automated Security Awareness Platform And Cost Introduction PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative organizational network staff learning automated security awareness platform and cost introduction pdf bundle. Topics like automated security awareness platform and cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
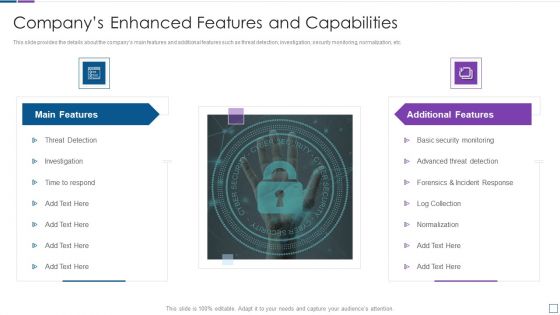
Real Time Assessment Of Security Threats Companys Enhanced Features And Capabilities Introduction PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting real time assessment of security threats companys enhanced features and capabilities introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Table Of Contents Introduction PDF
Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning table of contents introduction pdf. Use them to share invaluable insights on security awareness training, organization impact metrics, security awareness, communication plan, budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
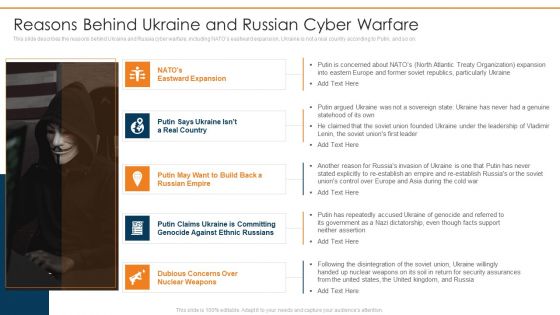
Data Wiper Spyware Attack Reasons Behind Ukraine And Russian Cyber Warfare Introduction PDF
This slide describes the reasons behind Ukraine and Russia cyber warfare, including NATOs eastward expansion, Ukraine is not a real country according to Putin, and so on.Deliver an awe inspiring pitch with this creative data wiper spyware attack reasons behind ukraine and russian cyber warfare introduction pdf bundle. Topics like reasons behind ukraine and russian cyber warfare can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Want to ace your presentation in front of a live audience Our Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
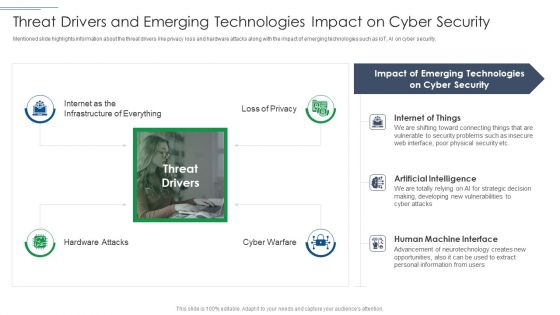
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. There are so many reasons you need a Technological Change Management Training Plan Introduction Of New Technology Ppt PowerPoint Presentation File Backgrounds PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Products And Services Offered Cloud Data Computing Company Fund Raising Introduction Pdf
Following slide provides insights into products and services offered by cloud-based data management company. It comprises of collaboration, data engineering, cyber security, data science and machine learning, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Products And Services Offered Cloud Data Computing Company Fund Raising Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Utilizing Cyber Technology For Change Process Challenges In Digital Transformation Introduction PDF
Digital transformation, especially in the healthcare sector, is a complex process and there are some hiccups that need to be addressed for complete success.Presenting utilizing cyber technology for change process challenges in digital transformation introduction pdf. to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like workforce training, technological gaps, lack connectivity, organizational culture, security, capital. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Training Program For Implementing Technological Change Management Training Plan Introduction PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Training Program For Implementing Technological Change Management Training Plan Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
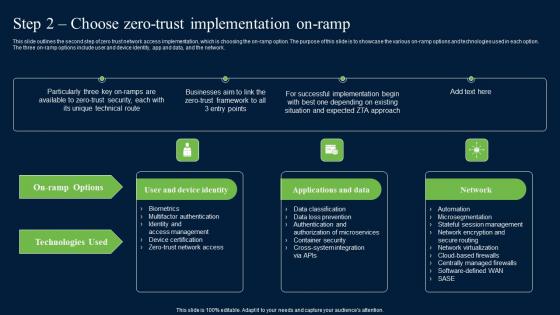
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Table Of Contents For IT Security Cyber Ppt Inspiration Introduction PDF
This is a table of contents for it security cyber ppt inspiration introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology security, implementation, organization, cyber risk assessment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF. Use them to share invaluable insights on Sprint Report, Product Report, Delivery Method and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF
This slide exhibits risk assessment of suppliers based on multiple procurement risks to identify supplier change requirements. It includes risks such as operational failures, administrations errors, late delivery, financial stability, legal compliance, frequency of price increases, product design improvements, cyber security, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Vendor Performance Analysis And Administration Supplier Performance Assessment Based On Procurement Risks Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
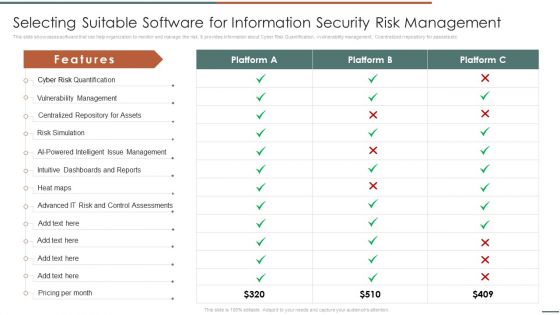
Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF
This slide showcases software that can help organization to monitor and manage the risk. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF. Use them to share invaluable insights on Vulnerability Management, Centralized Repository, Intelligent Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
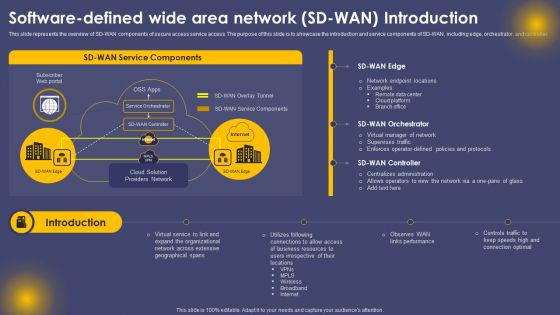
Software Defined Wide Area Network SD WAN Introduction Ppt Slides Objects PDF
This slide represents the overview of SD-WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD-WAN, including edge, orchestrator, and controller. Present like a pro with Software Defined Wide Area Network SD WAN Introduction Ppt Slides Objects PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

IT Development Company Pitch Deck Problems Faced By Companies Security Introduction PDF
This is a it development company pitch deck problems faced by companies security introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poor network security, backup issues, software concerns, qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Naas Architectural Framework Network As A Service Cloud Connections Introduction PDF
This slide represents the NaaS cloud connections, covering metro ethernet, layer 2 virtual private networks, layer 3 virtual private networks, internet protocol secure IPsec MPLS VPNs, SD-WAN, firewall, VCPE, remote access gateways, and so on. The Naas Architectural Framework Network As A Service Cloud Connections Introduction PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

New Product Launch Event Management Activities Existing Products And Service Offerings Of Firm Introduction PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Make sure to capture your audiences attention in your business displays with our gratis customizable New Product Launch Event Management Activities Existing Products And Service Offerings Of Firm Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Reverse Proxy Server IT Statistics Of Reverse Proxies Used By Websites Ppt Show Introduction PDF
This slide represents the statistics of reverse proxies used by websites, and it shows that most websites do not use any reverse proxy services, and 17 percent use CDNs. Presenting reverse proxy server it statistics of reverse proxies used by websites ppt show introduction pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like proxy services, content delivery network, security measure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SIEM Competitive Advantage Enhancing Cyber Safety With Vulnerability Administration Introduction PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Deliver and pitch your topic in the best possible manner with this siem competitive advantage enhancing cyber safety with vulnerability administration introduction pdf. Use them to share invaluable insights on security information and event management, application performance monitoring, digital experience management, service health check and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cisco Certified Network Professional Collection Of Information Technology Certifications Introduction PDF
This slide covers Cisco Certified Network Professional CCNP training courses such CCNA, specialist, CNP and CCIE. This is a cisco certified network professional collection of information technology certifications introduction pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like enterprise, security, service provider, data center. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security Monitoring, Internal Systems, Steering Committee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Minimize Cloud Risks Medical Care Business Case Competition ABS Healthcare Company Overview Introduction PDF
This slide shows details about ABC Carbonated Drink Company such as company type, employees, headquarters, annual revenue, CEO, founding year etc. This is a minimize cloud risks medical care business case competition ABS healthcare company overview introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business overview, annual revenue, cyber security cases, manufactures, global advertising expenses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role IT Team Digital Transformation It Professionals Challenges Related To Technical Skills Infographics PDF
This slide shows the challenges that are faced by IT Professionals related to technical skills data and analytics cybersecurity Application architecture and development Infrastructure, Operations and cloud Presenting role it team digital transformation it professional upskilling for cybersecurity introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like professionals, skills, challenges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Revolution In Online Business Need Of AI In Organization Ppt PowerPoint Presentation File Graphic Images PDF
This slide covers the key areas where business can be improved due to introduction of artificial intelligence such as customer experience, employee productivity, cybersecurity, decision making, etc. This is a Revolution In Online Business Need Of AI In Organization Ppt PowerPoint Presentation File Graphic Images PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Experience Based, Decision Making Multiple, Cybersecurity AI Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Accelerate Online Journey Now Need Of AI In Organization Brochure PDF
This slide covers the key areas where business can be improved due to introduction of artificial intelligence such as customer experience, employee productivity, cybersecurity, decision making, etc.This is a Accelerate Online Journey Now Need Of AI In Organization Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Decision Making, Customer Experience, Cybersecurity You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integration Of Digital Technology In Organization Need Of AI In Organization Guidelines PDF
This slide covers the key areas where business can be improved due to introduction of artificial intelligence such as customer experience, employee productivity, cybersecurity, decision making, etc.This is a Integration Of Digital Technology In Organization Need Of AI In Organization Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Experience, Decision Making, Cybersecurity You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Reshaping Business In Digital Need Of AI In Organization Guidelines PDF
This slide covers the key areas where business can be improved due to introduction of artificial intelligence such as customer experience, employee productivity, cybersecurity, decision making, etc. Presenting Reshaping Business In Digital Need Of AI In Organization Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Customer Experience, Decision Making, Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
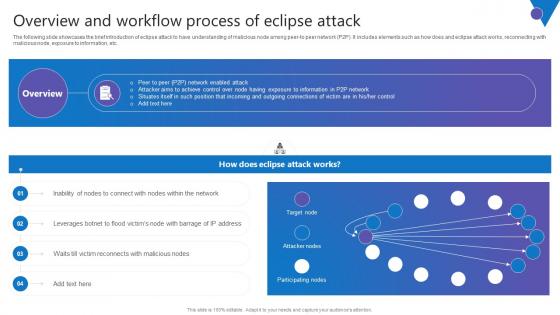
Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Overview And Workflow Process Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks and deliver a wonderful presentation.

Comprehensive Business Digitization Deck Need Of Ai In Organization Inspiration PDF
This slide covers the key areas where business can be improved due to introduction of artificial intelligence such as customer experience, employee productivity, cybersecurity, decision making, etc. This is a comprehensive business digitization deck need of ai in organization inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like customer experience, decision making, cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
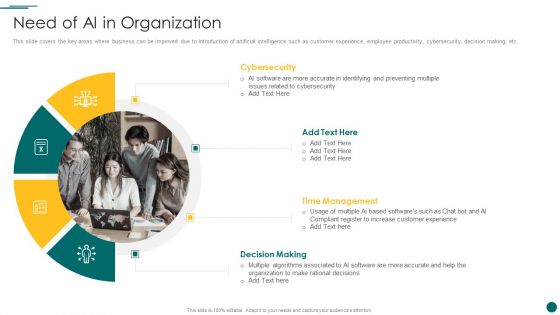
Organization Reinvention Need Of Ai In Organization Inspiration PDF
This slide covers the key areas where business can be improved due to introduction of artificial intelligence such as customer experience, employee productivity, cybersecurity, decision making, etc. This is a Organization Reinvention Need Of Ai In Organization Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cybersecurity, Time Management, Decision Making. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organization Transition Need Of AI In Organization Ppt PowerPoint Presentation File Influencers PDF
This slide covers the key areas where business can be improved due to introduction of artificial intelligence such as customer experience, employee productivity, cybersecurity, decision making, etc. This is a Organization Transition Need Of AI In Organization Ppt PowerPoint Presentation File Influencers PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Experience, Decision Making, Cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf
The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Retrieve professionally designed Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

 Home
Home