Information Security
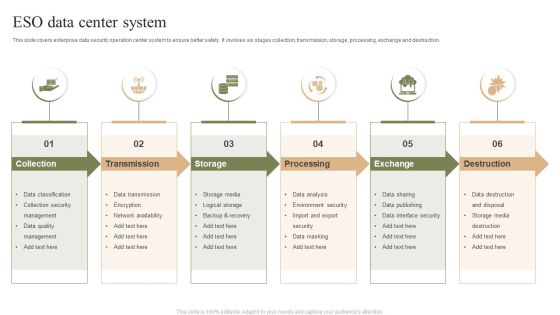
ESO Data Center System Ppt PowerPoint Presentation Gallery Grid PDF
This slide covers enterprise data security operation center system to ensure better safety. It involves six stages collection, transmission, storage, processing, exchange and destruction. Presenting ESO Data Center System Ppt PowerPoint Presentation Gallery Grid PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Collection, Transmission, Storage, Processing, Exchange. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Migration Project Risks With Mitigation Strategies Formats PDF
This slide showcases risks in implementing data migration projects that can cause data loss and security breachment. Its also outlines solutions to mitigate the hindrances and impact after the implementation. Showcasing this set of slides titled Data Migration Project Risks With Mitigation Strategies Formats PDF. The topics addressed in these templates are Mitigation Strategies, Impact, Risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
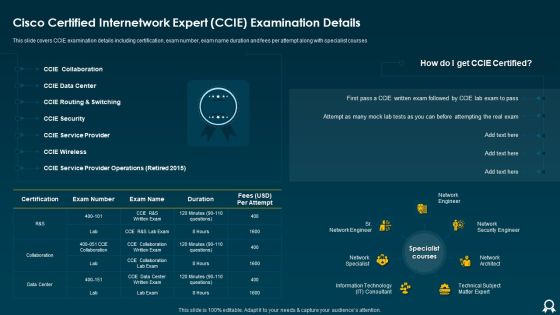
IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF
This slide covers CCIE examination details including certification, exam number, exam name duration and fees per attempt along with specialist courses. Deliver and pitch your topic in the best possible manner with this IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF. Use them to share invaluable insights on Data Center, Service Provider, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Professional Data Certification Program Comptia A Certification Courses Details Professional PDF
This slide covers certification details about CompTIA A such as who should take these certifications, courses offered in this certification etc. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Comptia A Certification Courses Details Professional PDF. Use them to share invaluable insights on Network Administrator, Systems Administrator, Security Administrator and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Companys Data Safety Recognition Organization Impact Metrics Behaviours Background PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people.Deliver and pitch your topic in the best possible manner with this companys data safety recognition organization impact metrics behaviours background pdf. Use them to share invaluable insights on organization impact metrics behaviours and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Biomedical Technology Role For Environment Sustainability Topics PDF
The below slide provides the importance of biofuel technology to increase energy security and protect environmental degradation. Key elements are reduced missions, eco friendly, automotive, recycle and energy saver. Presenting Biomedical Technology Role For Environment Sustainability Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Reduced Emissions, Automotive, Energy Saver. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Recognition Organization Impact Metrics Behaviours Pictures PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people.Deliver an awe-inspiring pitch with this creative data breach prevention recognition organization impact metrics behaviours pictures pdf bundle. Topics like organization impact metrics behaviours can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Configuration Management Audit Checklist Professional PDF
This slide covers cloud infrastructure management audit checklist. It involves data encryption, security controls, tested visibility, fully independent data centres, customer penetration and vulnerability.Presenting Cloud Computing Configuration Management Audit Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Management, Customer, Data Centres. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Barriers In Implementation Of Integrating Iiot Infographics PDF
This slide covers top 5 challenges companies face in implementing phase of IIOT. It includes key barriers such as connectivity, data analysis, skill gaps, financing problems and security issues. Presenting Barriers In Implementation Of Integrating Iiot Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Analysis, Connectivity, Financing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
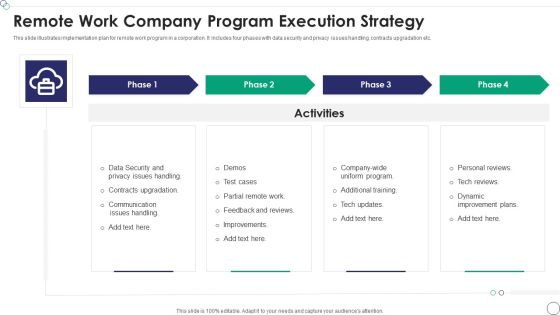
Remote Work Company Program Execution Strategy Rules PDF
This slide illustrates implementation plan for remote work program in a corporation. It includes four phases with data security and privacy issues handling, contracts upgradation etc.Presenting Remote Work Company Program Execution Strategy Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Contracts Upgradation, Communication Issues Handling, Dynamic Improvement Plans This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF bundle. Topics like Processing Data, Information, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF
The slide showcases the interconnected functions of a framework used to guide the organizations security measures. It covers identify, protect, detect, respond and recover. Presenting Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify, Protect, Detect. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Key Construction Site Safety Measures With Icons Ppt PowerPoint Presentation Summary Clipart PDF
Presenting key construction site safety measures with icons ppt powerpoint presentation summary clipart pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including safety training program, electrical safety at construction sites, implement strict security and safety protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing With Run Plan Build Ppt PowerPoint Presentation Show Outfit PDF
Presenting cloud computing with run plan build ppt powerpoint presentation show outfit pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including plan, build, run, application analysis and prioritization for deployments, deploy security controls and establish governance model, on going performance monitoring and cost optimization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps Of Vulnerabilities And Risk Mitigation Process Icons PDF
The following slide showcases some steps to mitigate risk for eliminating future expenses. It includes key elements such as find, prioritize, fix and monitor. Presenting Steps Of Vulnerabilities And Risk Mitigation Process Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Security Risks, Deploy Automated Tool, Resolve Risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
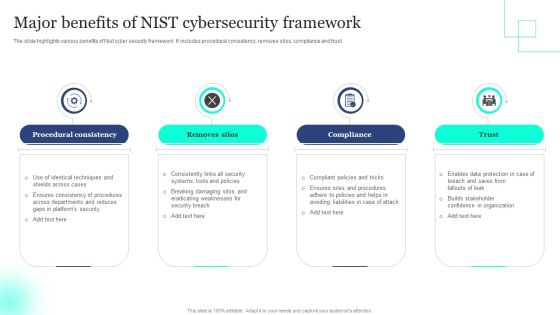
Major Benefits Of NIST Cybersecurity Framework Elements PDF
The slide highlights various benefits of Nist cyber security framework. It includes procedural consistency, removes silos, compliance and trust. Presenting Major Benefits Of NIST Cybersecurity Framework Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Procedural Consistency, Removes Silos, Compliance . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
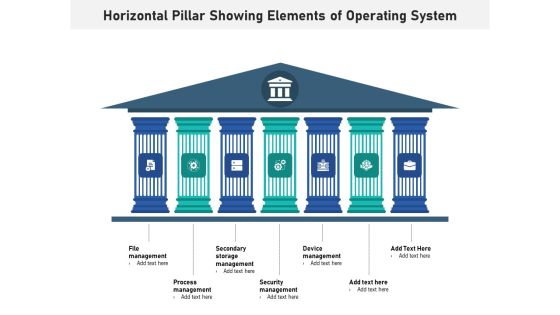
Horizontal Pillar Showing Elements Of Operating System Ppt PowerPoint Presentation Layouts Graphics Pictures PDF
Presenting horizontal pillar showing elements of operating system ppt powerpoint presentation layouts graphics pictures pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including file management, process management, secondary storage management, security management, device management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
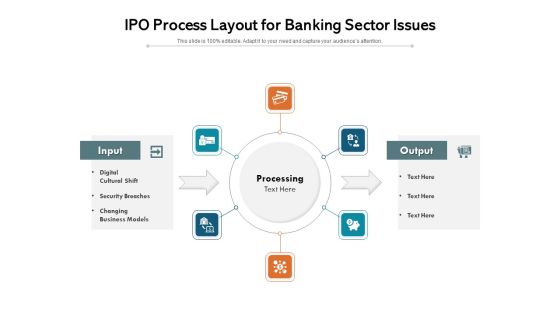
IPO Process Layout For Banking Sector Issues Ppt PowerPoint Presentation Show Design Templates PDF
Presenting ipo process layout for banking sector issues ppt powerpoint presentation show design templates pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including processing, output, input, digital cultural shift, security breaches, changing business models. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
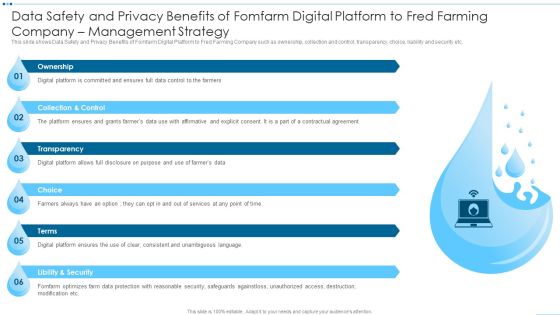
Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF
This slide shows Data Safety and Privacy Benefits of Fomfarm Digital Platform to Fred Farming Company such as ownership, collection and control, transparency, choice, liability and security etc. Deliver an awe inspiring pitch with this creative Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF bundle. Topics like Ownership, Collection And Control, Transparency, Choice can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Companys Data Safety Recognition Communication Plan For Cybersecurity Events And Incidents Themes PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver an awe-inspiring pitch with this creative companys data safety recognition communication plan for cybersecurity events and incidents themes pdf bundle. Topics like department awareness training, resources training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
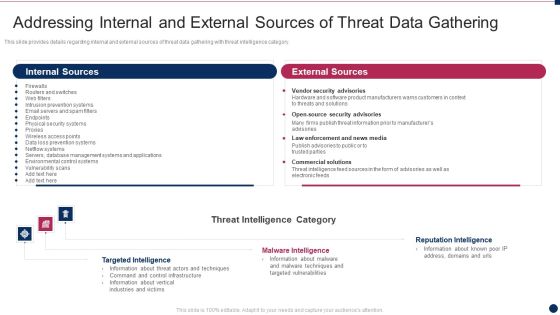
Threat Management At Workplace Addressing Internal And External Sources Of Threat Data Microsoft Pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver and pitch your topic in the best possible manner with this threat management at workplace addressing internal and external sources of threat data microsoft pdf. Use them to share invaluable insights on vendor security advisories, law enforcement and news media, commercial solutions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Wiper Spyware Attack Steps To Prepare For Cyberattacks By Russia Designs PDF
This slide represents the steps to take right now to prepare for cyberattacks by Russia, including access exposure, minimizing attack surface, executing the basics, and so on.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack steps to prepare for cyberattacks by russia designs pdf Use them to share invaluable insights on companies conducting, prepare ensure, security procedures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Analysis Reporting Tools Ppt PowerPoint Presentation Professional Layout Cpb Pdf
Presenting this set of slides with name data analysis reporting tools ppt powerpoint presentation professional layout cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Breach Prevention Recognition Communication Plan For Cybersecurity Events And Incidents Pictures PDF
This slide covers the communication delivery channels for cyber security awareness training for different departments target audience along with program topics. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition communication plan for cybersecurity events and incidents pictures pdf. Use them to share invaluable insights on communication plan for cybersecurity events and incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Effective IT Risk Management Process System Management Checklist Brochure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this effective it risk management process system management checklist brochure pdf. Use them to share invaluable insights on security patches, data backup, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solution Assessment Analysis With Multiple Options Sample PDF
This slide showcases numerous alternatives considered by organization to choose the best and suitable one as per firms requirement. It includes, budget, promotion techniques, processes, data security and financial investment. Showcasing this set of slides titled Solution Assessment Analysis With Multiple Options Sample PDF. The topics addressed in these templates are Budget, Manufacturing, Promotion Techniques. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF

Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer or retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF bundle. Topics like Total Subscribers, Dealer, Retailer, Direct, 2018 To 2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Understanding The Kubernetes Components Through Diagram Table Of Contents Ppt Ideas Graphic Images
Presenting this set of slides with name understanding the kubernetes components through diagram table of contents ppt ideas graphic images. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Understanding The Kubernetes Concepts And Architecture Table Of Contents Ppt Summary Inspiration PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture table of contents ppt summary inspiration pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Financial Transformation Key Success Metrics Assessment Digital Transformation Toolkit Accounting Finance Introduction PDF
In this slide we have showcased financial transformation effectiveness graph with key success metrics lincluding data management, IT system efficiency and cyber security Deliver an awe inspiring pitch with this creative financial transformation key success metrics assessment digital transformation toolkit accounting finance introduction pdf bundle. Topics like financial transformation key success metrics assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF
This slide covers the workforce training plan for new CRM software. It includes training details such as session, trainer, trainees, mode, duration, and cost. Deliver an awe inspiring pitch with this creative CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF bundle. Topics like System Configuration, Lead Management, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Exploitation IT Budget For IT Spending By The Company Professional PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Database Development Life Cycle Ppt PowerPoint Presentation Professional Inspiration Cpb Pdf
Presenting this set of slides with name database development life cycle ppt powerpoint presentation professional inspiration cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like data warehouse security issues to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Top Trending Tools In Machine Driven Learning Market Ppt Pictures Example PDF
This slide represents the market value of the top trending RPA tools on a yearly basis, and UiPath is the tool that conquered the market in the last years. Deliver an awe inspiring pitch with this creative top trending tools in machine driven learning market ppt pictures example pdf bundle. Topics like analytics, enterprises, data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Designing And Deployment CRM Training Program For Employees Introduction PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session. Deliver an awe inspiring pitch with this creative designing and deployment crm training program for employees introduction pdf bundle. Topics like training session, involved, trainer, program, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
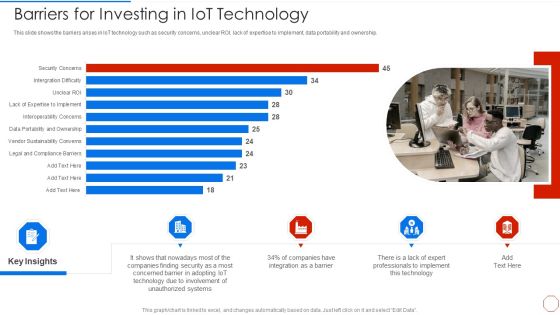
Minimizing Operational Cost Through Iot Virtual Twins Implementation Barriers For Investing In Iot Microsoft PDF
This slide shows the barriers arises in IoT technology such as security concerns, unclear ROI, lack of expertise to implement, data portability and ownership. Deliver and pitch your topic in the best possible manner with this minimizing operational cost through iot virtual twins implementation barriers for investing in iot microsoft pdf. Use them to share invaluable insights on involvement, systems, technology, implement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Managing Cyber Terrorism 60 Days Plan Clipart PDF
This slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault managing cyber terrorism 60 days plan clipart pdf Use them to share invaluable insights on time to detect an incident, data loss incidents, infected computers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Updating Hardware And Software In Company Infographics PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems.Deliver an awe inspiring pitch with this creative cyber terrorism assault updating hardware and software in company infographics pdf bundle. Topics like peripheral devices, security necessitates, traditional ways to data transport can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

BPO Call Center Company Profile Integrated Performance Of The Company Portrait PDF
This slide highlights the integrated performance of call center which covers different elements such as jobs created, percentage of women, renewable energy consumption, employees trained on data security and code of conduct.Deliver an awe inspiring pitch with this creative BPO Call Center Company Profile Integrated Performance Of The Company Portrait PDF bundle. Topics like Percentage Women, Agents Trained, Technology Analytics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT Implement Strong IT Guidelines Pictures PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it implement strong it guidelines pictures pdf bundle. Topics like implement strong it guidelines in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Infrastructure Management Time Spent On Monitoring IT Infrastructure Topics PDF
This slide covers the time spend in monitoring the IT infrastructure such as extracting and analyzing logs, interpreting reports and alerts, managing tools and agents, etc.Deliver and pitch your topic in the best possible manner with this IT Infrastructure Management Time Spent On Monitoring IT Infrastructure Topics PDF. Use them to share invaluable insights on Reasonable Amount, Little Time, Security Infrastructure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Career Certifications Benefits Of IT Certifications Technical Certifications And Business Individuals Themes PDF
This template covers IT certification Benefits for the employees such as expand individuals employment opportunities, gaining professional credibility, increase your job security and job stability etc. Deliver an awe inspiring pitch with this creative IT Career Certifications Benefits Of IT Certifications Technical Certifications And Business Individuals Themes PDF bundle. Topics like Expand Individuals, Employment Opportunities, Knowledge And Qualifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home