Information Security
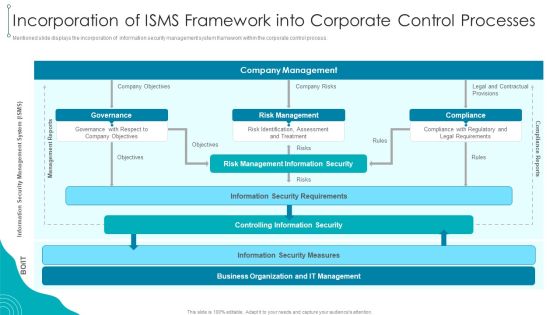
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. Slidegeeks has constructed Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Reverse Proxy Server IT Secure Client Connection To Proxy And Secure Proxy Connection Ppt Infographic Template Design Inspiration PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. This is a reverse proxy server it secure client connection to proxy and secure proxy connection ppt infographic template design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server outside firewall, encrypted, secure, proxy, client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Target Informational Posts Diagram Ppt Examples
This is a target informational posts diagram ppt examples. This is a four stage process. The stages in this process are problems solutions , solutions.
Obtain The Right Financing For Your Business Secure Professional PDF
This is a obtain the right financing for your business secure professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like investor, loan, secure, business financing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Virtual Coinage Icon For Secured Payment System Professional PDF
Presenting Virtual Coinage Icon For Secured Payment System Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Virtual Coinage Icon, Secured Payment System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Digital Mail PowerPoint Icon C
3d illustration of a chrome at/email symbol surrounded by a ring of glowing green binary digits with a heavy metallic padlock attached to it on a dark gray reflective surface

Secure Digital Mail PowerPoint Icon Cc
3d illustration of a chrome at/email symbol surrounded by a ring of glowing green binary digits with a heavy metallic padlock attached to it on a dark gray reflective surface

Secure Digital Mail PowerPoint Icon S
3d illustration of a chrome at/email symbol surrounded by a ring of glowing green binary digits with a heavy metallic padlock attached to it on a dark gray reflective surface
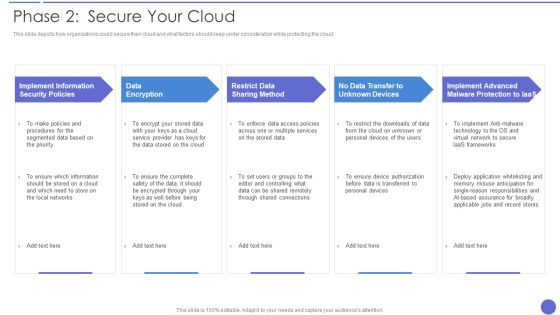
Phase 2 Secure Your Cloud Clipart PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Presenting Phase 2 Secure Your Cloud Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Encryption, Restrict Data Sharing Method, Implement Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Securities Risk Assessment In Investment Topics PDF
This slide shows the risk percentage of three securities purchased by an investor. It includes risk level during four quarters of all three securities. Pitch your topic with ease and precision using this Securities Risk Assessment In Investment Topics PDF. This layout presents information on Investment, Key Takeaways, Continuous Increase. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Checklist To Inform New Employee Hire Company Policies Ppt Layouts Graphics Download PDF
This slide covers checklist to provide employees information about different companys policies. It includes policies such as no password sharing, company BYOD, working hours, overtime pay, insurance policies, pension, etc. Presenting Checklist To Inform New Employee Hire Company Policies Ppt Layouts Graphics Download PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Checklist, Completed, Working Hours Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Modeling Procedure For Secure Data Assets Formats PDF
This slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Pitch your topic with ease and precision using this Threat Modeling Procedure For Secure Data Assets Formats PDF. This layout presents information on Execute Preventative, Identified Threat, Develop Controls. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
RPA Testing Procedure Design Test Deploy Ppt PowerPoint Presentation Icon Graphics
Presenting this set of slides with name rpa testing procedure design test deploy ppt powerpoint presentation icon graphics. This is a three stage process. The stages in this process are identify, automate, monitor, information security, rpa analysis, information security, process analysis, gap analysis, baseline validation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Lockable Informative Laptop PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Lockable Informative Laptop PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Download and present our Security PowerPoint Templates because You are well armed with penetrative ideas. Our PowerPoint Templates and Slides will provide the gunpowder you need. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Present our Shapes PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides.Use these PowerPoint slides for presentations relating to Notebook Lockable, computer, technology, security, signs, shapes. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
Secure Computer Database Access Icon Slides PDF
Presenting Secure Computer Database Access Icon Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Secure, Computer, Database Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Securities Finance Ppt PowerPoint Presentation Pictures Cpb
Presenting this set of slides with name securities finance ppt powerpoint presentation pictures cpb. This is an editable Powerpoint four stages graphic that deals with topics like securities finance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Is Secure Internet PowerPoint Template 1110
3d illustration of a lock sitting in front of a computer display showing a file folder

ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset consequences and risk to the firm.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF bundle. Topics like Risk Encountered, Asset And Consequences, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Health Protection Plan For Secured Life Vector Icon Ppt PowerPoint Presentation Slides Examples PDF
Pitch your topic with ease and precision using this health protection plan for secured life vector icon ppt powerpoint presentation slides examples pdf. This layout presents information on health protection plan for secured life vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy secure proxy to a content server.This is a Process Of Secure Reverse Proxying Reverse Proxy For Load Balancing Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secured Connection, Established Between, Underneath Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
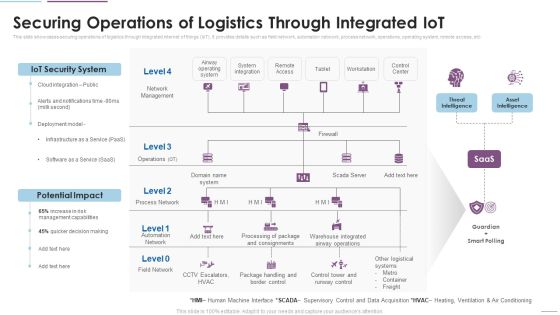
Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. This is a Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IoT Security System, Potential Impact, Network Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Designing And Deployment Securing Our Data With CRM Ppt PowerPoint Presentation File Backgrounds PDF
This slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. This is a designing and deployment securing our data with crm ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like crm data security model, security model, profile based security, record sharing, group based security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Benefit Of Block Chain Technology For Securing Confidential Data Icon Topics PDF
Presenting Benefit Of Block Chain Technology For Securing Confidential Data Icon Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benefit Of Block Chain, Technology For Securing, Confidential Data Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
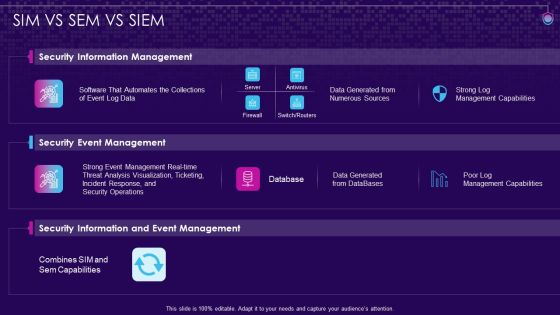
SIM VS SEM VS SIEM SIEM Services Ppt Show Slides PDF
Deliver and pitch your topic in the best possible manner with this sim vs sem vs siem siem services ppt show slides pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Recognition Automation Sim Vs Sem Vs Siem Ppt Professional Background Designs PDF
Deliver and pitch your topic in the best possible manner with this risk recognition automation sim vs sem vs siem ppt professional background designs pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
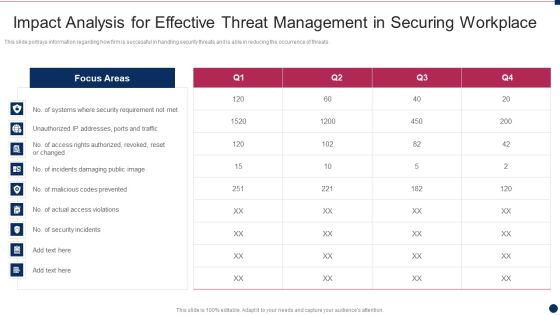
Threat Management At Workplace Impact Analysis For Effective Threat Management In Securing Structure PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative threat management at workplace impact analysis for effective threat management in securing structure pdf bundle. Topics like security incidents, incidents damaging public image, actual access violations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Optimizing Educational Technology Powerpoint Templates Microsoft
This is a optimizing educational technology powerpoint templates microsoft. This is a six stage process. The stages in this process are information security, technology and analytics, institutional data management, optimizing educational technology, it workforce hiring and retention, it funding models.
Financial And Operational Audits Business Diagram Powerpoint Images
This is a financial and operational audits business diagram powerpoint images. This is a four stage process. The stages in this process are financial audit, technology audit, operational audit, information security, audit.
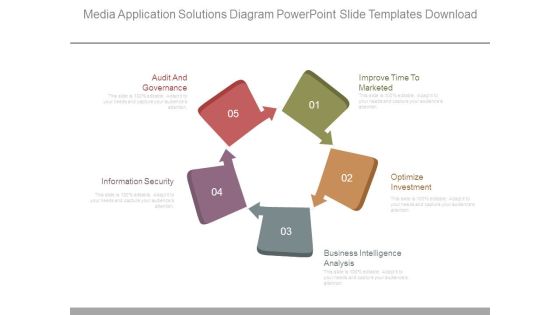
Media Application Solutions Diagram Powerpoint Slide Templates Download
This is a media application solutions diagram powerpoint slide templates download. This is a five stage process. The stages in this process are audit and governance, information security, improve time to marketed, optimize investment, business intelligence analysis.

Administration Assessment Example Sample Ppt Files
This is a administration assessment example sample ppt files. This is a six stage process. The stages in this process are aims and objective, implementation, feasibility, consultancy, solutions, audit and testing, information security.

Blue Prism Machine Driven Learning Tool Ppt Show Structure PDF
This slide describes the blue prism tool of the RPA along with the pros, cons and features of the tool such as robust, 24 7 workforce, information security and execution insight. This is a blue prism machine driven learning tool ppt show structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure, analytics, information, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.

Redis Cache Data Structure IT Encrypted Password For Securing Redis Settings Formats PDF
This slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. This is a redis cache data structure it encrypted password for securing redis settings formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypted password for securing redis settings. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Convertible Preferred Stock Funding Pitch Deck Return On Convertible Securities Discount Rate Portrait PDF
The slide provides the equity allocation and return on convertible note investment while the investment is raised at Discount Rate. This is a convertible preferred stock funding pitch deck return on convertible securities discount rate portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like return on convertible securities discount rate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Email Technology PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Communication PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Signs PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Illustration of envelope and email sign protect with padloc, security, communication, technology, business, signs. The prominent colors used in the PowerPoint template are Red, Gray, Yellow.
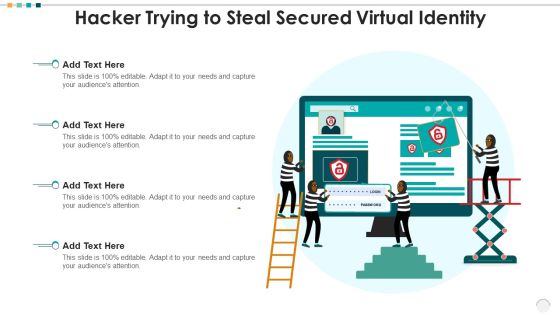
Hacker Trying To Steal Secured Virtual Identity Sample PDF
Persuade your audience using this hacker trying to steal secured virtual identity sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hacker trying to steal secured virtual identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Secure Your Money PowerPoint Templates Ppt Backgrounds For Slides 0413
Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 allow you to do it with ease. Just like picking the low hanging fruit. Boil the ocean with your thoughts. Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 will help create waves.
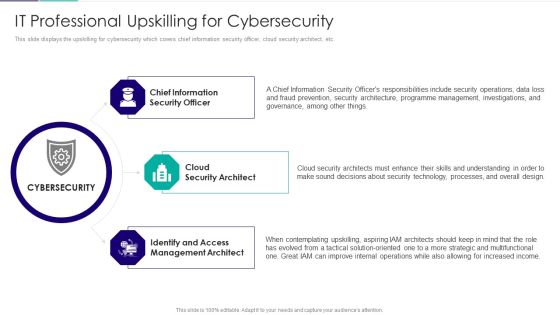
Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc.Presenting Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Chief Information Security, Cloud Security Architect, Identify And Access Management Architect In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
SIEM Sim Vs Sem Vs SIEM Ppt Icon Format Ideas PDF
This is a siem sim vs sem vs siem ppt icon format ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information management, security event management, security information and event management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it

Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a lock padlock intersecting it

CRM Implementation Strategy Securing Our Data With CRM Summary PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a CRM Implementation Strategy Securing Our Data With CRM Summary PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Communication Protection, Restrict Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Time Stamp, Blockchain Technology, Weaknesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
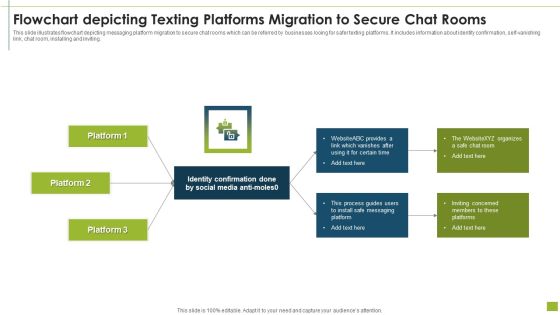
Flowchart Depicting Texting Platforms Migration To Secure Chat Rooms Inspiration PDF
This slide illustrates flowchart depicting messaging platform migration to secure chat rooms which can be referred by businesses looing for safer texting platforms. It includes information about identity confirmation, self-vanishing link, chat room, installing and inviting.Pitch your topic with ease and precision using this flowchart depicting texting platforms migration to secure chat rooms inspiration pdf This layout presents information on identity confirmation, process guides, install safe messaging It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

How Amazon Secured Brand Position By Maintaining Leadership Designs PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Get a simple yet stunning designed How Amazon Secured Brand Position By Maintaining Leadership Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Amazon Secured Brand Position By Maintaining Leadership Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
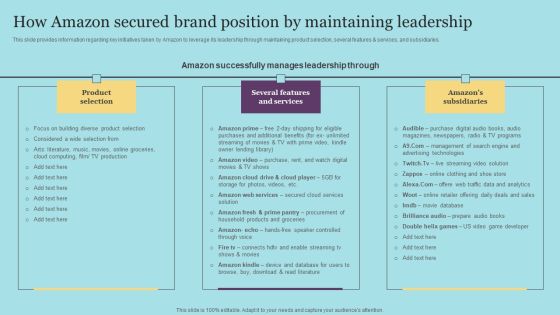
How Amazon Secured Brand Position By Maintaining Leadership Download PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. This modern and well-arranged How Amazon Secured Brand Position By Maintaining Leadership Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

How Amazon Secured Brand Position By Maintaining Leadership Topics PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. This modern and well-arranged How Amazon Secured Brand Position By Maintaining Leadership Topics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Computing Project Analysis Diagram Powerpoint Template
Our above PPT slide contains graphics of cloud with technology icons. This PowerPoint template may be used for project related to cloud computing. Use this diagram to impart more clarity to data and to create more sound impact on viewers.

How Amazon Secured Brand Position By Maintaining Leadership Slides PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. If you are looking for a format to display your unique thoughts, then the professionally designed How Amazon Secured Brand Position By Maintaining Leadership Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download How Amazon Secured Brand Position By Maintaining Leadership Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Deliver an awe inspiring pitch with this creative Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF bundle. Topics like Digital Data, Blockchain Networks, Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
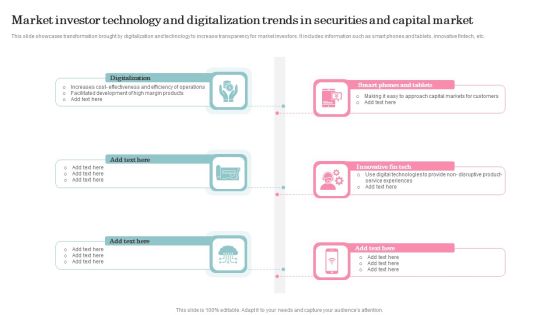
Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF
This slide showcases transformation brought by digitalization and technology to increase transparency for market investors. It includes information such as smart phones and tablets, innovative fintech, etc. Presenting Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF to dispense important information. This template comprises Six stages. It also presents valuable insights into the topics including Digitalization, Innovative Fin Tech. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely.Deliver and pitch your topic in the best possible manner with this Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF. Use them to share invaluable insights on Server Outside, Between Server, Situation Works and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Blue Prism Robotic Process Automated Tool Designs PDF
This slide describes the blue prism tool of the RPA along with the pros, cons and features of the tool such as robust, 24 into 7 workforce, information security and execution insight. Presenting Blue Prism Robotic Process Automated Tool Designs PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Secure And Accurate, Information Security, Execution Insight. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
 Home
Home