Information Security

Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Dispose Data And Equipment Properly Ppt Icon Example PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information technology security dispose data and equipment properly ppt outline layouts pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF
This slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Pitch your topic with ease and precision using this Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF. This layout presents information on Security For Cloud Based, Systems Strategic Checklist, For IT Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Locked And Protected Information PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Locked And Protected Information PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download and present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Present our Services PowerPoint Templates because It can Bubble and burst with your ideas.Use these PowerPoint slides for presentations relating to Notebook lockable information, security, communication, computer, technology, services. The prominent colors used in the PowerPoint template are Black, Yellow, Gray.

Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF
This slide provides information regarding security objectives such as confidentiality, integrity and availability and their role in IoT security compliance. Boost your pitch with our creative Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
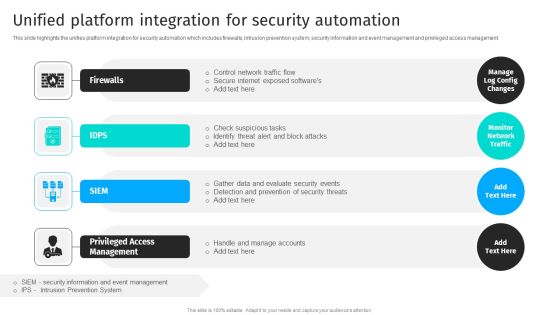
Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management.The Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Business Information Protection Recommended And Essential Control Background PDF
This slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Showcasing this set of slides titled Business Information Protection Recommended And Essential Control Background PDF. The topics addressed in these templates are Determining Threats, Business Vulnerabilities, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF
Pitch your topic with ease and precision using this Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF. This layout presents information on Pathway Change Framework, Food Security Sustainable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF
This slide signifies the enterprise resource planning evaluation to increase IT security. It covers information about automated testing tool, check system functionality and quality assurance etc. Pitch your topic with ease and precision using this Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF. This layout presents information on Checklist, Execution, Functionality. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Dashboard Icon Showing Security Performance Of A Company Ppt Slides Layout Ideas PDF
Pitch your topic with ease and precision using this Dashboard Icon Showing Security Performance Of A Company Ppt Slides Layout Ideas PDF. This layout presents information on Dashboard Icon, Security Performance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF
Pitch your topic with ease and precision using this Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF. This layout presents information on Virus Cyber Security, Attack Warning, Web Browser Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF
Pitch your topic with ease and precision using this Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF. This layout presents information on Showcasing Application, Computer Vision, Technologyin Digital Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Activity Template PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration security operations implementation timeline activity template pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
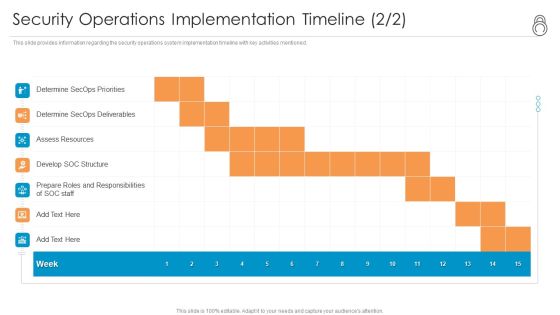
Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Staff Background PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security operations implementation timeline staff background pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Flying Security Camera With Smart Phone On Wooden Table Ppt PowerPoint Presentation File Topics PDF
Pitch your topic with ease and precision using this flying security camera with smart phone on wooden table ppt powerpoint presentation file topics pdf. This layout presents information on flying security camera with smart phone on wooden table. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Executing Advance Data Analytics At Workspace Determine Role Of Security Centre In Firm Sample PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. This is a executing advance data analytics at workspace determine role of security centre in firm sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine role of security centre in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security Monitoring, Internal Systems, Steering Committee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Security Officer Service Company Profile Company Overview With Key Services Background PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. This is a Security Officer Service Company Profile Company Overview With Key Services Background PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ABC Securities, Services And Solutions, Quality And Certifications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Information Strategic Objectives And Protection Procedures Portrait PDF
This slide covers business strategic objectives and security procedures which includes security process controlling.Pitch your topic with ease and precision using this Business Information Strategic Objectives And Protection Procedures Portrait PDF. This layout presents information on Business Security, Business Strategic, International Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Collaboration Plan Key Activities Information PDF
This slide presents a schedule timeline for tracking and monitoring key activities in order to successful completion of project. Its key tasks includes combined event action plan, short term security generation, competitive intelligence processes, branding, linking contacts in datasets, etc. Showcasing this set of slides titled Business Collaboration Plan Key Activities Information PDF. The topics addressed in these templates are Branding, Acquisition Positioning, Partners Communication, Short Term Security Generation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Governance And Security Model Vector Icon Ppt PowerPoint Presentation Show PDF
Pitch your topic with ease and precision using this data governance and security model vector icon ppt powerpoint presentation show pdf. This layout presents information on data governance and security model vector icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda Of Data Safety Initiatives For Effective IT Security Threats Administration Professional PDF
This is a agenda of data safety initiatives for effective it security threats administration professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security program keeping, threat drivers, cybersecurity attacks resulting, business agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Security Lifecycle Ppt Summary Brochure PDF
This is a handling cyber threats digital era security lifecycle ppt summary brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Workforce Security Realization Coaching Plan Ideas PDF
This is a table of contents for workforce security realization coaching plan ideas pdf template with various stages. Focus and dispense information on fourteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security awareness, tracking, communication plan, current scenario, training formats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Application Development Life Cycle Security Sample PDF
This is a table of contents for application development life cycle security sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, implementation, models. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Devops Market Trends Assessment Information PDF
This slide provides information regarding DevOps market trends in terms of DevOps market growth and how the market has been accelerating in past few years. Deliver and pitch your topic in the best possible manner with this addressing devops market trends assessment information pdf. Use them to share invaluable insights on Service, Implemented, improvements, processes, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secure Internet Access Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Business PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Technology PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Use our Internet PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download and present our Computer PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges.Use these PowerPoint slides for presentations relating to The data is secure, security, business, technology, internet, computer. The prominent colors used in the PowerPoint template are Black, Gray, Yellow. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our internet PowerPoint templates and PPT Slides are designed by a team of presentation professionals. You can be sure our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 have awesome images to get your point across. Customers tell us our business PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. People tell us our Secure Internet Access Security PowerPoint Templates PPT Backgrounds For Slides 0113 help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. People tell us our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses.
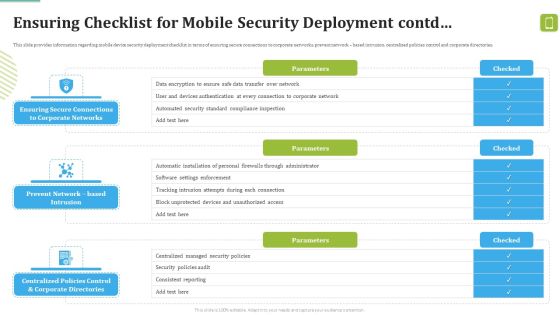
MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF. Use them to share invaluable insights on Against Malicious, Device Security, Automatic Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
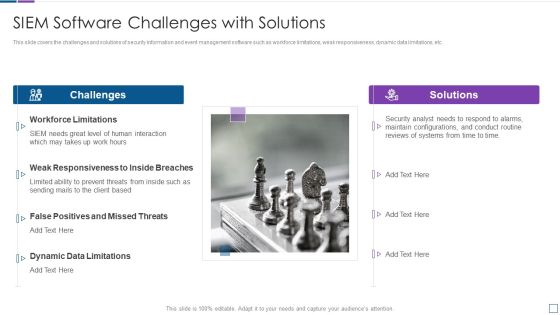
Real Time Assessment Of Security Threats SIEM Software Challenges With Solutions Inspiration PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a real time assessment of security threats siem software challenges with solutions inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, false positives and missed threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Picture Showing Security Officer In Building Control Room Ppt PowerPoint Presentation File Layout Ideas PDF
Pitch your topic with ease and precision using this picture showing security officer in building control room ppt powerpoint presentation file layout ideas pdf. This layout presents information on picture showing security officer in building control room. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Vector Showing Security Guard At Entrance Of Shopping Mall Ppt PowerPoint Presentation Gallery Design Ideas PDF
Pitch your topic with ease and precision using this vector showing security guard at entrance of shopping mall ppt powerpoint presentation gallery design ideas pdf. This layout presents information on vector showing security guard at entrance of shopping mall. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF
This slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting.Pitch your topic with ease and precision using this Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF. This layout presents information on Business Security, Control Status Breakdown, Network Inspection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF.

Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. This Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Overcome Payment Card Processing Errors Information PDF
This slide outline the how to overcome credit card processing errors. It includes various credit card issues such as credit card verification error, transaction not permitted, insufficient funds, incorrect security code and exceeded credit limit. Presenting Overcome Payment Card Processing Errors Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Credit Card Verification Error, Insufficient Funds, Exceeded Credit Limit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF
This slide represents career road map of various position from entry level to advance level for cyber security in an organization .It includes salary, skills required and qualification. Pitch your topic with ease and precision using this Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF. This layout presents information on Cyber Security Specialist, Skill Required, Advance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Officer Service Company Profile Employees Rules And Regulations Inspiration PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. This is a Security Officer Service Company Profile Employees Rules And Regulations Inspiration PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Officer, Employees, Security Officer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Create an editable Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
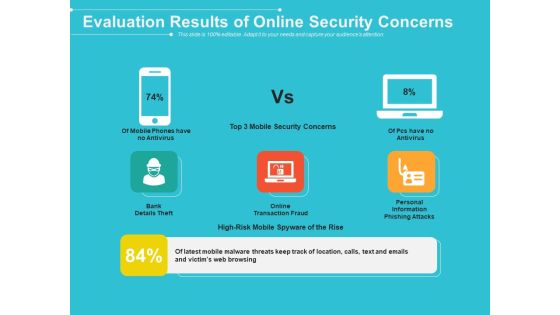
Evaluation Results Of Online Security Concerns Ppt PowerPoint Presentation File Summary PDF
Pitch your topic with ease and precision using this evaluation results of online security concerns ppt powerpoint presentation file summary pdf. This layout presents information on evaluation results of online security concerns. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Horizontal Scaling Technique For Information Team Structure For Data Management System Expansion Icons PDF
This slide represents the team structure for the data repository expansion project. It provides details regarding core and support team members in terms of job role and employee name.Deliver and pitch your topic in the best possible manner with this Horizontal Scaling Technique For Information Team Structure For Data Management System Expansion Icons PDF Use them to share invaluable insights on Documentation Information, Security Engineer, Information Security Engineer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Enabling Data Security Risk Management Action Plan Ppt Slides Icon PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative enabling data security risk management action plan ppt slides icon pdf bundle. Topics like risk, security, information, measures, analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
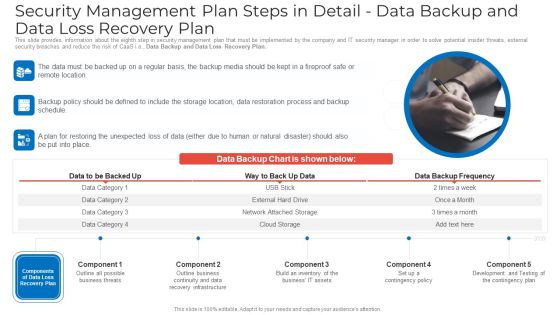
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
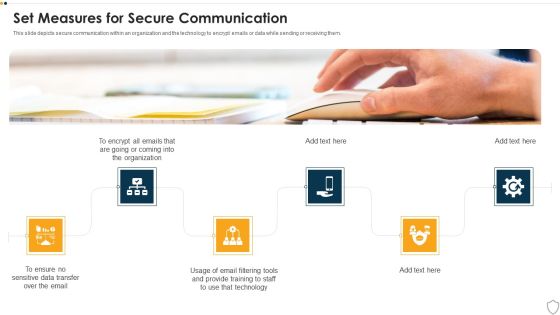
IT Security Set Measures For Secure Communication Ppt Infographic Template Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a it security set measures for secure communication ppt infographic template background designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, training, organization, data transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
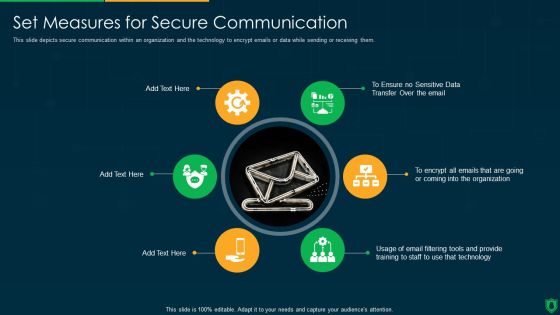
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF
This is a IT Security Automation Tools Integration Table Of Contents Ppt Ideas Graphic Tips PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ineffective Security System, Security Automation, Architecture And Importance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Professional PDF
This is a security management plan steps in detail data backup and data loss recovery plan professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security tools, categories of application, data backup frequency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents For IT Security Cyber Ppt Inspiration Introduction PDF
This is a table of contents for it security cyber ppt inspiration introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology security, implementation, organization, cyber risk assessment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF bundle. Topics like Before Security, After Security, Towards Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Roadmap For Security Guard Services Proposal Ppt Icon Graphic Images PDF
This is a roadmap for security guard services proposal ppt icon graphic images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap, security guard services, 2014 to 2020. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Testimonials In The Security Guard Services Proposal Ppt Gallery Format Ideas PDF
This is a testimonials in the security guard services proposal ppt gallery format ideas pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like testimonials, security guard services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF
This This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting 6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prioritize, Evaluate, Analyse, Treat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

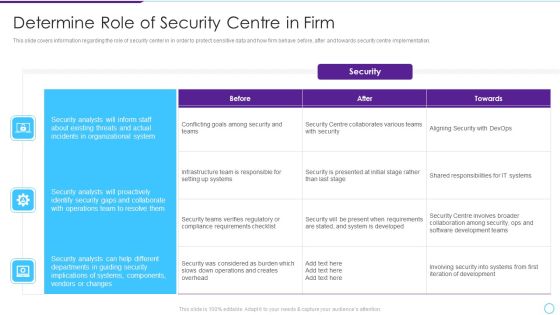
Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF bundle. Topics like Organizational System, Security Analysts, Collaborate With Operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
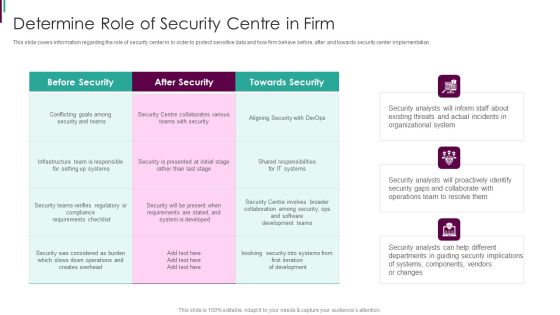
Evolving BI Infrastructure Determine Role Of Security Centre In Firm Summary PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative evolving bi infrastructure determine role of security centre in firm summary pdf bundle. Topics like organizational, security analysts, collaborate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
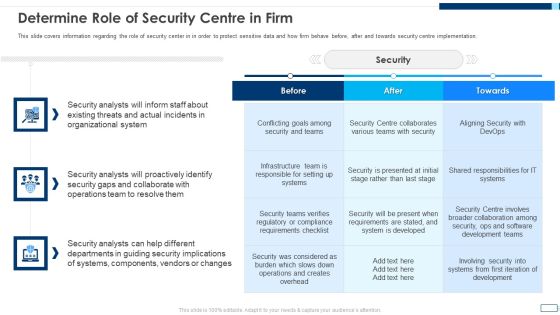
Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF bundle. Topics like Security, Organizational System, Operations Team, Conflicting Goals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF bundle. Topics like Armed Security Officer, Personal Protection Officers, Unarmed Security Officers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Agency Business Profile Company Overview With Key Services Inspiration PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Company Overview With Key Services Inspiration PDF bundle. Topics like Quality Management Systems, Industrial Security, Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparison Of Cyber Risk Security Vendors With Pricing And Use Case Formats PDF
Mentioned slide highlights the cyber threat security vendors with uses cases, metrics, intelligence , cyber security and pricing. Pitch your topic with ease and precision using this comparison of cyber risk security vendors with pricing and use case formats pdf. This layout presents information on financial services, cyber security, intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
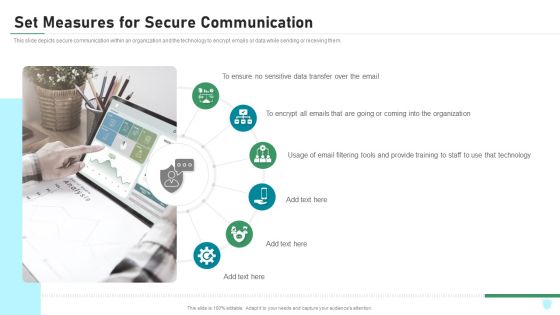
Set Measures For Secure Communication IT Security IT Ppt Styles Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting set measures for secure communication it security it ppt styles background designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like data transfer, organization, technology, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Elevating Brand Protection Strategy Mockup PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. This is a developing firm security strategy plan elevating brand protection strategy mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like overt security features, covert security features, serialization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration Overview Of Security Operations Centre Ppt Show Graphics Tutorials PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration overview of security operations centre ppt show graphics tutorials pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
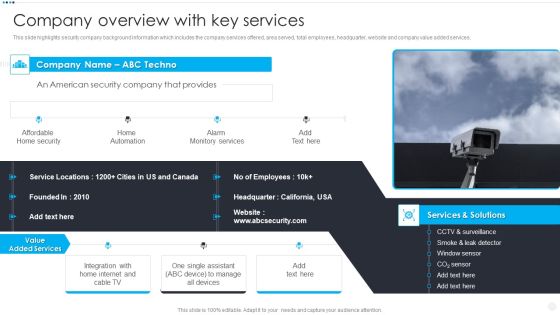
Smart Home Security Solutions Company Profile Company Overview With Key Services Brochure PDF
This slide highlights security company background information which includes the company services offered, area served, total employees, headquarter, website and company value added services. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Company Overview With Key Services Brochure PDF bundle. Topics like Affordable Home Security, Home Automation Alarm, Monitory Services Solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
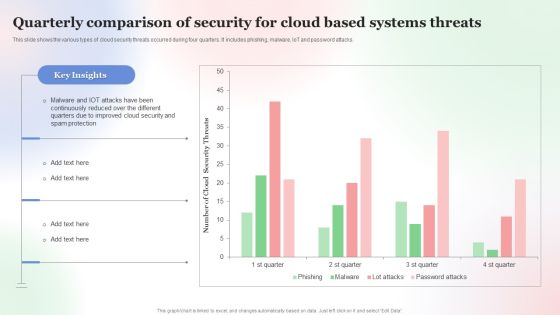
Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF
This slide shows the various types of cloud security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF. This layout presents information on Quarterly Comparison Of Security, Cloud Based Systems Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF
The following slide outlines a comprehensive training plan for managed security service and awareness for employees. It provides information about the training subject, trainer name, training hours, status and learning outcome. Pitch your topic with ease and precision using this Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF. This layout presents information on Training Plan, Managed Cyber Security, Solutions Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security And Surveillance Company Profile Company Overview With Key Services Professional PDF
This slide highlights security company background information which includes the company services offered, area served, total employees, headquarter, website and company value added services.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Company Overview With Key Services Professional PDF bundle. Topics like Manage Devices, Monitory Services, Services And Solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Camera System Company Profile Company Overview With Key Services Icons PDF
This slide highlights security company background information which includes the company services offered, area served, total employees, headquarter, website and company value added services.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Company Overview With Key Services Icons PDF bundle. Topics like Monitory Services, Home Automation, Manage All Devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Mapping Process Ppt PowerPoint Presentation Summary Microsoft Cpb
This is a information mapping process ppt powerpoint presentation summary microsoft cpb. This is a four stage process. The stages in this process are information mapping process.

Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icon Of Consumer Information Platform For Creating Profiles Icons PDF
Persuade your audience using this icon of consumer information platform for creating profiles icons pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including icon of consumer information platform for creating profiles. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Company Timeline From 1992 To 2022 Infographics PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. This is a Security Agency Business Profile Company Timeline From 1992 To 2022 Infographics PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security, Expand Services, Protection Officers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Company Timeline From 1992 To 2022 Demonstration PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. This is a Manpower Corporate Security Business Profile Company Timeline From 1992 To 2022 Demonstration PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Services, Protection Officers, Recruit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Reverse Proxy Server IT Reverse Proxy Server Side Technology Security Ppt Professional Backgrounds PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. This is a reverse proxy server it reverse proxy server side technology security ppt professional backgrounds pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security proxy session, security proxy, host. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Wireless Network Security System Icon Of Cloud Servers To Secure Data Clipart PDF
Persuade your audience using this wireless network security system icon of cloud servers to secure data clipart pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon of cloud servers to secure data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Functioning Centre Various Metrics To Measure Secops System Performance Icons PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. This is a security functioning centre various metrics to measure secops system performance icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security analysts productivity, escalation breakdown, average time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
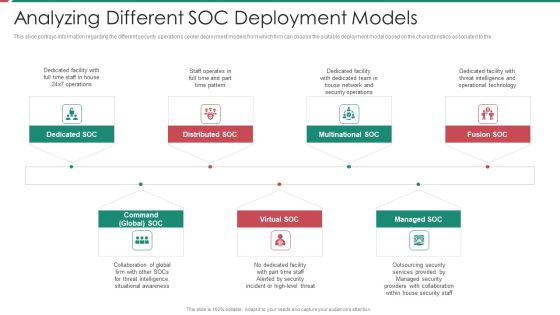
Security And Process Integration Analyzing Different SOC Deployment Models Diagrams PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a security and process integration analyzing different soc deployment models diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Data Management For Network Security Vector Icon Ppt PowerPoint Presentation Icon Portfolio PDF
Pitch your topic with ease and precision using this corporate data management for network security vector icon ppt powerpoint presentation icon portfolio pdf. This layout presents information on corporate data management for network security vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Retrieve professionally designed Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Client Testimonials And Reviews Infographics PDF
This slide highlights the security guard company client testimonials and reviews which includes ratings from - head of retail store, principal of school and manager of financial institution. This is a Manpower Corporate Security Business Profile Client Testimonials And Reviews Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Services, Financial Institution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. There are so many reasons you need a Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.

Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF
This slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Showcasing this set of slides titled Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF. The topics addressed in these templates are Internet Access Policy, Firewall Rules Policy, Wireless LAN Policy, Remote Connection Policy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Selecting Secured Threat Management Software Introduction PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management selecting secured threat management software introduction pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
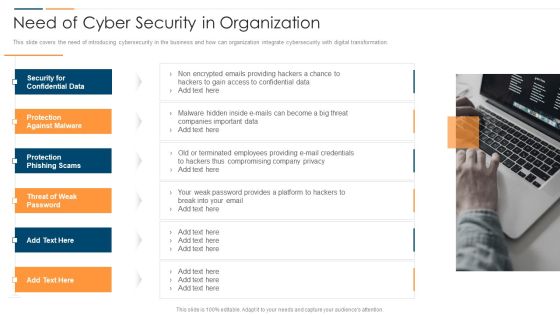
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF
This slide represents information management objectives in end user computing such as organizing information, maximization of information value, security and protection etc. Presenting Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Organizing Information Utilization, Security And Protection, Business Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

5 Steps To Write Professional Safety And Security Report Formats PDF
This slide shows various steps which can be used to write safety and security report. These steps are take notes, summary, detail the narrative, follow the form and proofread. Presenting 5 Steps To Write Professional Safety And Security Report Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Forms Accurately, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Welcome to our selection of the Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Develop Corporate Cyber Security Risk Mitigation Plan Awards And Recognition Organization Protection Services Clipart PDF
This is a develop corporate cyber security risk mitigation plan awards and recognition organization protection services clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like best cyber security, service provider, global leader, cyber security service, 2018, 2019. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
 Home
Home