Information Security
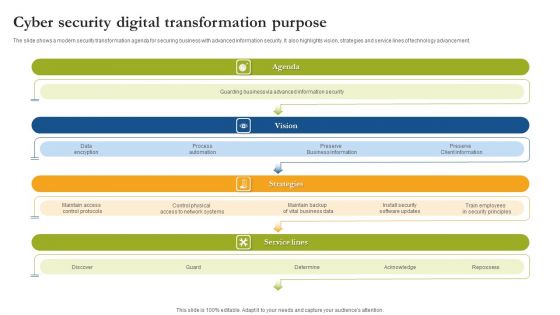
Cyber Security Digital Transformation Purpose Sample PDF
The slide shows a modern security transformation agenda for securing business with advanced information security. It also highlights vision, strategies and service lines of technology advancement. Persuade your audience using this Cyber Security Digital Transformation Purpose Sample PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Agenda, Vision, Strategies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Methodology Diagram Powerpoint Topics
This is a security methodology diagram powerpoint topics. This is a six stage process. The stages in this process are device protection, data separation, security operation, security organization, leak protection, sharing protection.
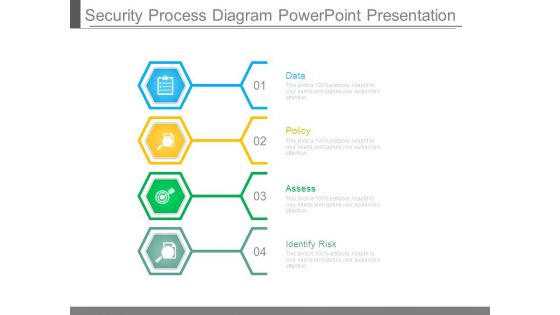
Security Process Diagram Powerpoint Presentation
This is a security process diagram powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.

Security Process Sample Powerpoint Presentation
This is a security process sample powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.

Internet Protocol Security PPT Example
This Internet Protocol Security PPT Example is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This eighty nine slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.

CCTV Security Services PPT Template
Drive the power of innovation with our revolutionary CCTV Security Services PPT Template. This dynamic tool empowers you to create visually-stunning presentations that leave a lasting impression. With its user-friendly interface and 100 percent editable features, you can effortlessly customize every aspect of your slides, ensuring they align perfectly with your message. No design skills No problem. Our expertly crafted template provides a solid foundation for your ideas, allowing you to focus on what matters most delivering a compelling presentation. Do not settle for mediocrity, choose excellence with our template today.
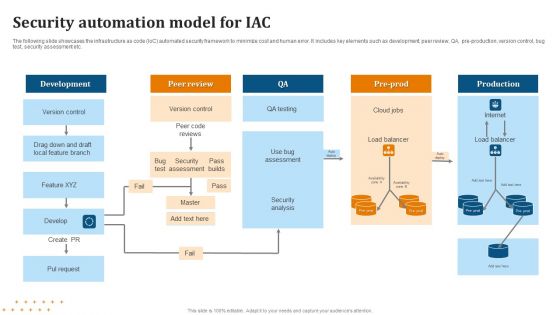
Security Automation Model For IAC Summary PDF
Pitch your topic with ease and precision using this Security Automation Model For IAC Summary PDF. This layout presents information on Security Automation, Model For IAC . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
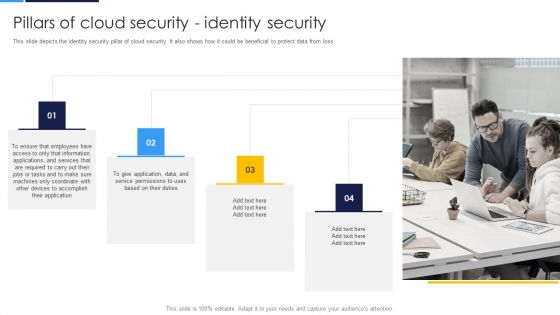
Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss.This is a Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Devices To Accomplish, Service Permissions, Information Applications You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Cloud Security Diagrams PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a desktop security management elements of computer security cloud security diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

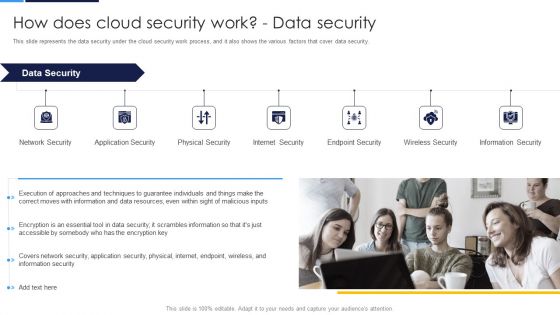
How Does Cloud Security Work Data Security Cloud Computing Security IT Ppt Ideas Slide Download PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting how does cloud security work data security cloud computing security it ppt ideas slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network security, internet security, endpoint security, wireless security, physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
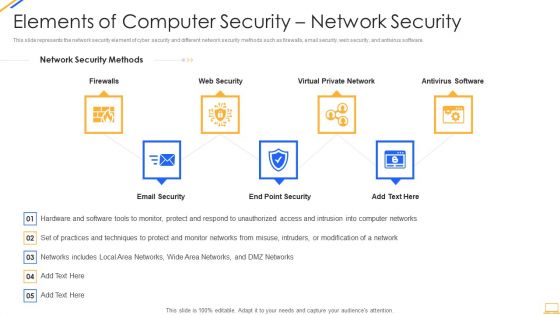
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Pillars Of Cloud Security Network Security Cloud Computing Security IT Ppt Summary Guidelines PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. Presenting pillars of cloud security network security cloud computing security it ppt summary guidelines pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like performing, traffic security, micro segmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Security Checklist Security Patches And Updates Cloud Computing Security IT Ppt File Icon PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting cloud security checklist security patches and updates cloud computing security it ppt file icon pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like organization, measures, technologies, developed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Pillars Of Cloud Security Network Security Mockup PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks.Presenting Cloud Security Assessment Pillars Of Cloud Security Network Security Mockup PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Premises Conditions, Difficult For Attackers, Them Individually In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Presenting Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Impact Analysis, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. It also caters to best practices and the security framework of the cloud. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
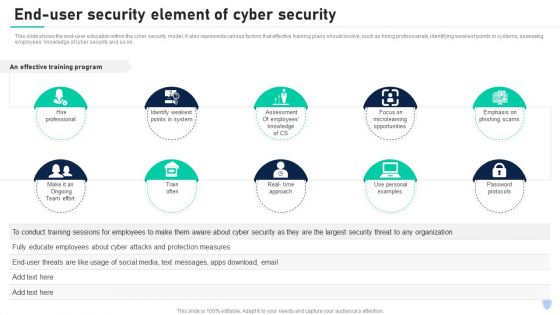
Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Find a pre designed and impeccable Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Brochure PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Data Security Compliance System Icon Clipart Pdf
Pitch your topic with ease and precision using this Data Security Compliance System Icon Clipart Pdf. This layout presents information on Data Security, Compliance System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
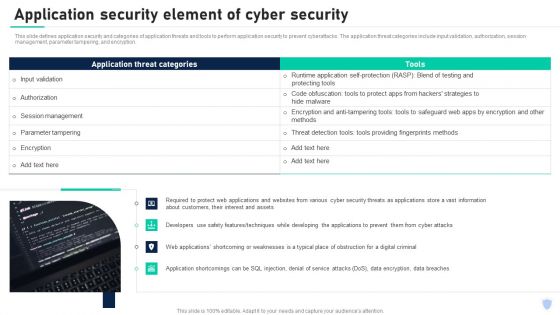
Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
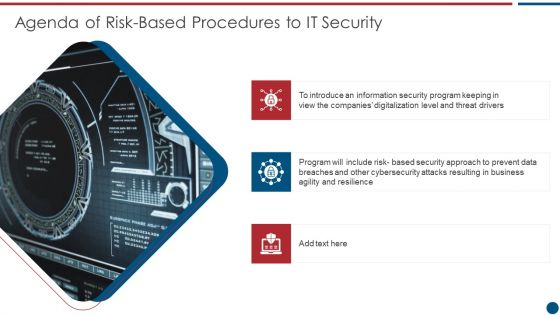
Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Mitigate Cyber Security Risks Selecting Security Incident Management Software Ppt Styles Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks selecting security incident management software ppt styles influencers pdf. This is a one stage process. The stages in this process are security incident forms, automated workflows, centralized platform, access rights, api integration, information security prevention, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
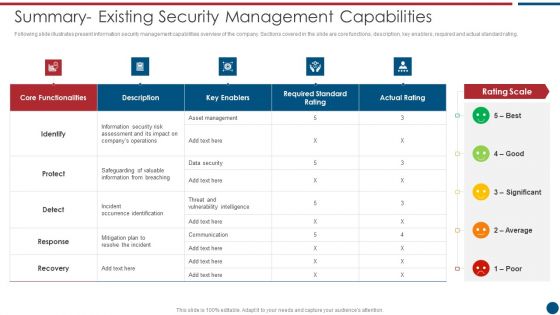
Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase 2 Secure Your Cloud Structure PDF bundle. Topics like Implement Information, Security Policies, Data Encryption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Construction Worker Security Checklist Icon Portrait Pdf
Pitch your topic with ease and precision using this Construction Worker Security Checklist Icon Portrait Pdf. This layout presents information on Construction Worker, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Food Quality Security Checklist Icon Guidelines Pdf
Pitch your topic with ease and precision using this Food Quality Security Checklist Icon Guidelines Pdf. This layout presents information on Food Quality, Security Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon Showcasing Security Network Analysis Structure Pdf
Pitch your topic with ease and precision using this Icon Showcasing Security Network Analysis Structure Pdf This layout presents information on Icon Showcasing Security, Network Analysis It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
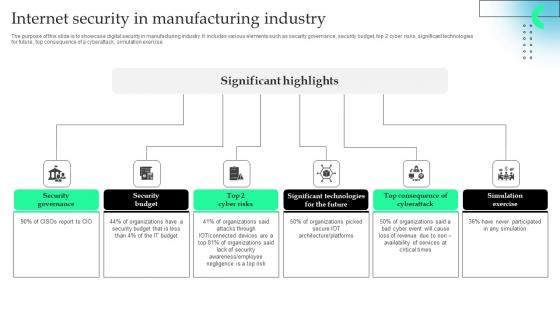
Internet Security In Manufacturing Industry Professional Pdf
The purpose of this slide is to showcase digital security in manufacturing industry. It includes various elements such as security governance, security budget, top 2 cyber risks, significant technologies for future, top consequence of a cyberattack, simulation exercise.Pitch your topic with ease and precision using this Internet Security In Manufacturing Industry Professional Pdf This layout presents information on Security Governance, Security Budget, Significant Technologies It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Big Data Monitoring Security Icon Download pdf
Pitch your topic with ease and precision using this Big Data Monitoring Security Icon Download pdf. This layout presents information on Big Data Monitoring, Security Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
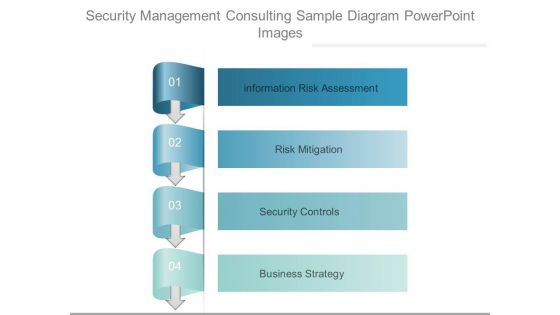
Security Management Consulting Sample Diagram Powerpoint Images
This is a security management consulting sample diagram powerpoint images. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.

Certified Information Systems Auditor Cisa Job Description Information PDF
This slide covers details about Certified Information Systems Auditor CISA such as demand for certification, training costs, exam costs, skills sets, roles and responsibilities.Deliver an awe inspiring pitch with this creative Certified Information Systems Auditor Cisa Job Description Information PDF bundle. Topics like Certified Information, Security Efficiency, Skilled Professionals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
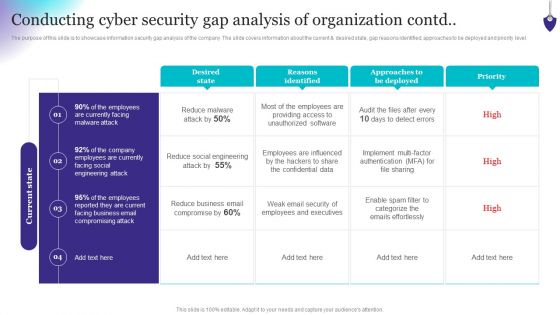
Organizing Security Awareness Conducting Cyber Security Gap Analysis Of Organization Contd Portrait PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. There are so many reasons you need a Organizing Security Awareness Conducting Cyber Security Gap Analysis Of Organization Contd Portrait PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Organizing Security Awareness Roles And Responsibilities Of Cyber Security Team Slides PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Find a pre-designed and impeccable Organizing Security Awareness Roles And Responsibilities Of Cyber Security Team Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
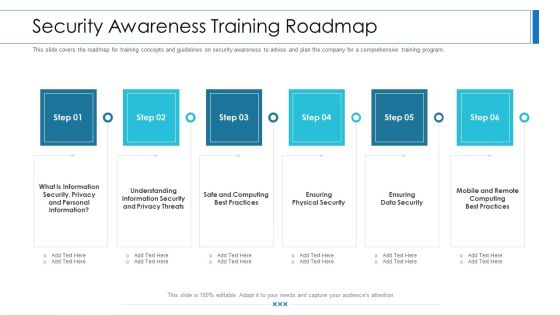
Workforce Security Realization Coaching Plan Security Awareness Training Roadmap Ppt Slides Visual Aids PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a workforce security realization coaching plan security awareness training roadmap ppt slides visual aids pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, privacy threats, physical security, data security, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Communication Action Plan Portrait PDF
This slide showcases the information technology cyber security communication action plan. It includes elements such as IT initiative, communication goal, person responsible and impact level. Showcasing this set of slides titled IT Security Communication Action Plan Portrait PDF. The topics addressed in these templates are Upgrading Core System, Update Data Privacy, Implement IT Platform. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Techniques And Strategies To Reduce Security Management Risks Security Risk Management Assessment Checklist Demonstration PDF
This slide shows a security risk management assessment checklist with multiple categories.Presenting techniques and strategies to reduce security management risks security risk management assessment checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, responding to security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
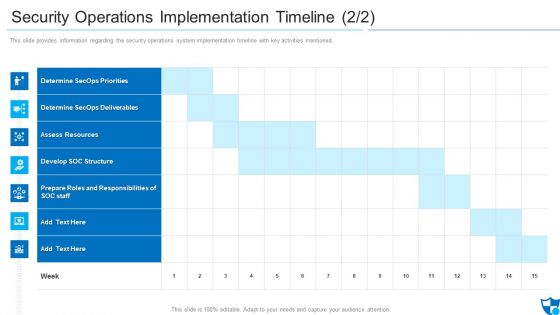
Security Operations Implementation Timeline Assess Diagrams PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned.Deliver and pitch your topic in the best possible manner with this security operations implementation timeline assess diagrams pdf. Use them to share invaluable insights on determine secops priorities, determine secops deliverables, assess resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Operations Implementation Timeline Priorities Introduction PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned.Deliver an awe inspiring pitch with this creative security operations implementation timeline priorities introduction pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
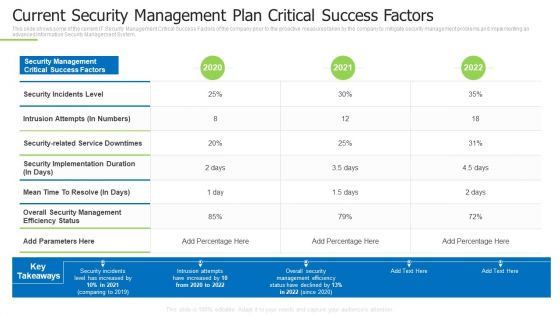
Techniques And Strategies To Reduce Security Management Risks Current Security Management Plan Ideas PDF
This slide shows some of the current IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks current security management plan ideas pdf bundle. Topics like intrusion attempts, overall security management, security incidents level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Corporate Security And Risk Management Icons PDF
This is a corporate security and risk management corporate security and risk management icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate security and risk management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
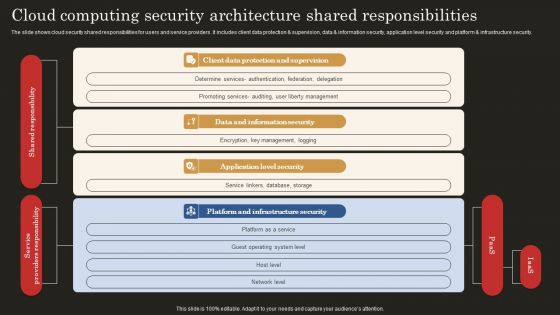
Cloud Computing Security Architecture Shared Responsibilities Brochure PDF
The slide shows cloud security shared responsibilities for users and service providers. It includes client data protection and supervision, data and information security, application level security and platform and infrastructure security. Showcasing this set of slides titled Cloud Computing Security Architecture Shared Responsibilities Brochure PDF. The topics addressed in these templates are Client Data Protection, Data Information Security, Application Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda Of Security Risk Management Graphics PDF
This is a agenda of security risk management graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerabilities, organizational, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Supply Chain Security Management Model Infographics PDF
This slide represents the framework showing the management of supply chain security. It includes details related to supply chain security goals such as facility, cargo, human resource, information and ABC companys management system along with their respective security measures. Presenting Supply Chain Security Management Model Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Human Resources Management, Cargo Management, Facility Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Vendor Data Security Checklist For Market Research Company Sample Pdf
The purpose of this slide is to showcase checklist for supplier information security for market research company. It includes various process to be completed such as vendor possess a security rating that meets with expectations, supplier has invested in data protection and information security controls etc. Pitch your topic with ease and precision using this Vendor Data Security Checklist For Market Research Company Sample Pdf. This layout presents information on Vendor Data Security, Market Research. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
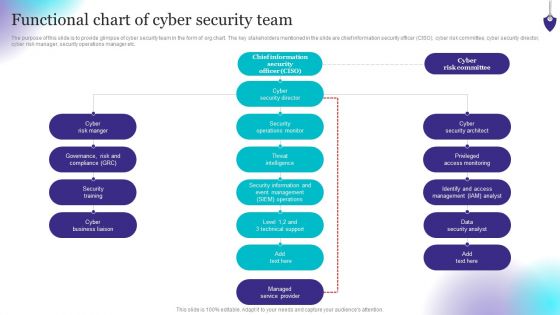
Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizing Security Awareness Functional Chart Of Cyber Security Team Background PDF today and make your presentation stand out from the rest.
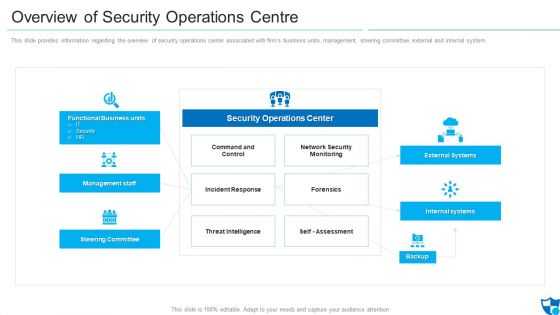
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
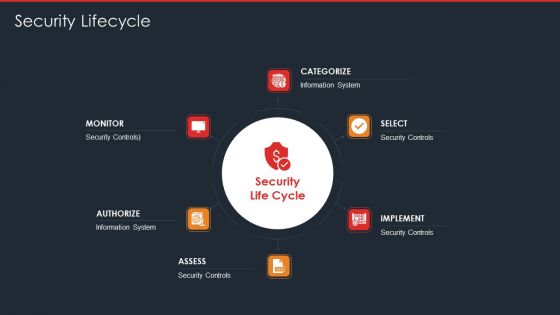
Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
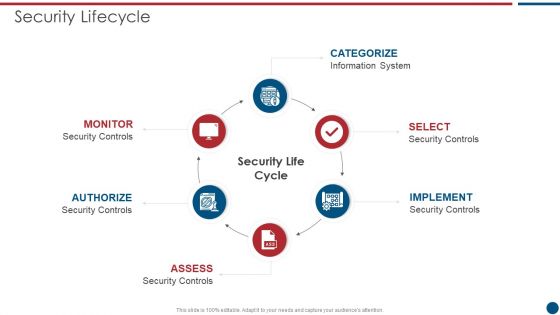
Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF
This is a Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information System, Security Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Shared Vulnerabilities Graphics PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. This is a Cloud Security Threats Shared Vulnerabilities Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Could, Organizations, Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
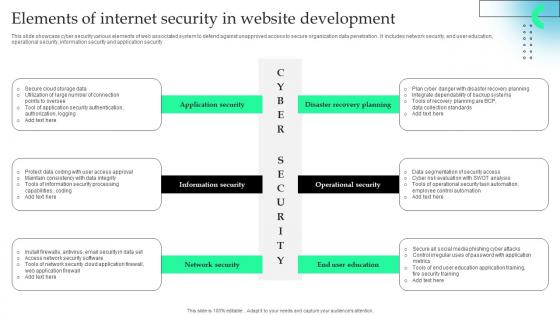
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Technology Governance Example Ppt Presentation Slides
This is a information technology governance example ppt presentation slides. This is a three stage process. The stages in this process are computer audit, it governance, it risk management, information security management.
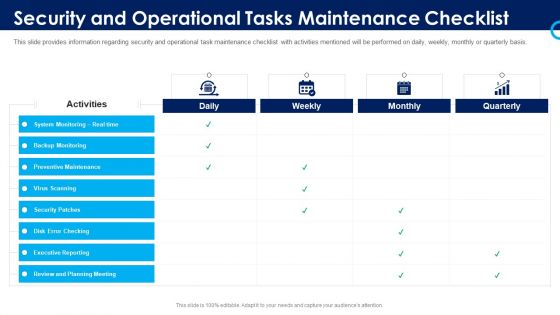
Organizational Security Solutions Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this organizational security solutions security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Security And Operational Tasks Maintenance Checklist Inspiration PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security functioning centre security and operational tasks maintenance checklist inspiration pdf. Use them to share invaluable insights on executive reporting, review and planning meeting, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
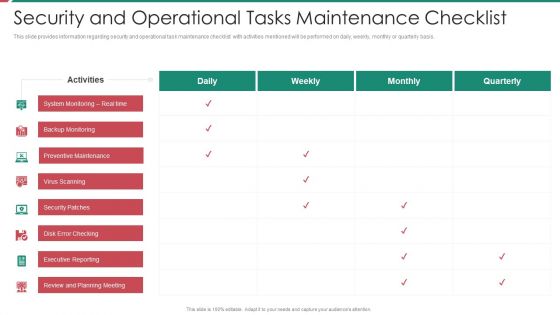
Security And Process Integration Security And Operational Tasks Maintenance Checklist Diagrams PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security and process integration security and operational tasks maintenance checklist diagrams pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
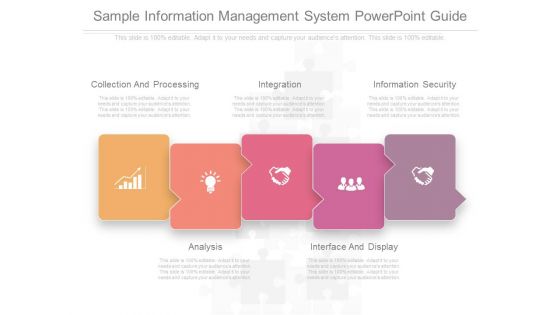
Sample Information Management System Powerpoint Guide
This is a sample information management system powerpoint guide. This is a five stage process. The stages in this process are collection and processing, integration , information security , analysis , interface and display.
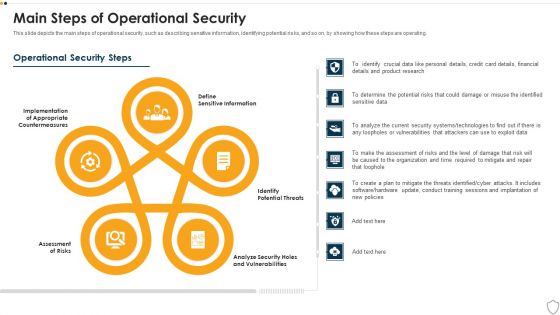
IT Security Main Steps Of Operational Security Ppt Show Design Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting it security main steps of operational security ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like assessment of risks, potential threats, sensitive information, analyze security holes and vulnerabilities, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Computer Cyber Security Icon Infographics PDF
Presenting Computer Cyber Security Icon Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Computer Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
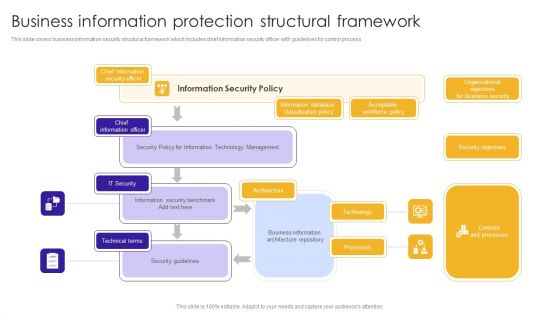
Business Information Protection Structural Framework Summary PDF
This slide covers business information security structural framework which includes chief information security officer with guidelines for control process.Showcasing this set of slides titled Business Information Protection Structural Framework Summary PDF. The topics addressed in these templates are Information Database, Classification Policy, Architecture Repository. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
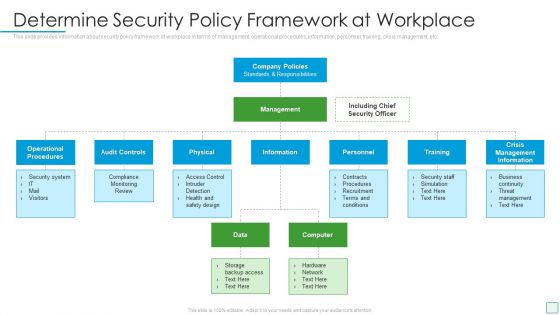
Developing Firm Security Strategy Plan Determine Security Policy Framework At Workplace Template PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Presenting developing firm security strategy plan determine security policy framework at workplace template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like operational procedures, audit controls, physical, training, crisis management information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
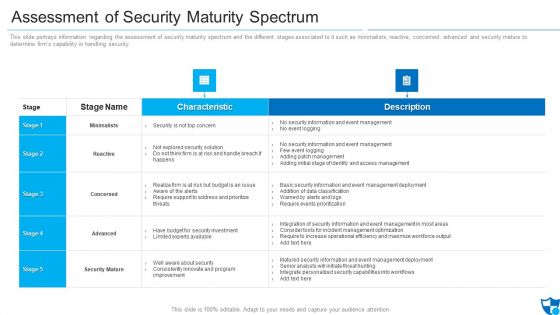
Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icon For Functional Technology Security Elements PDF
Presenting icon for functional technology security elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including icon for functional technology security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Essential Pillars Of Cloud Security Brochure PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Essential Pillars Of Cloud Security Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Based Security, Network Security, Identity Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
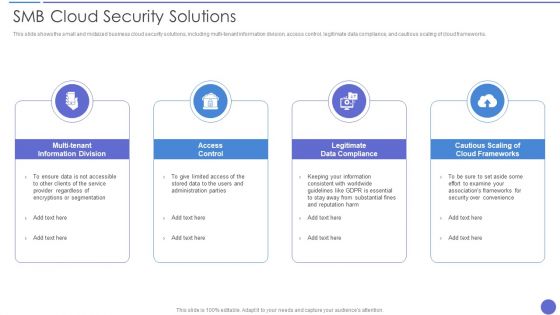
Smb Cloud Security Solutions Download PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. This is a Smb Cloud Security Solutions Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Legitimate Data Compliance, Cloud Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Cloud Data Security Ideas PDF
This is a Agenda For Cloud Data Security Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Responsibilities And Service, Organizations, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Data Storage Security Management Icon Professional PDF
Presenting Data Storage Security Management Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Storage, Security, Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Payment Card Security Processing Icon Portrait PDF
Presenting Payment Card Security Processing Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Payment Card Security, Processing Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
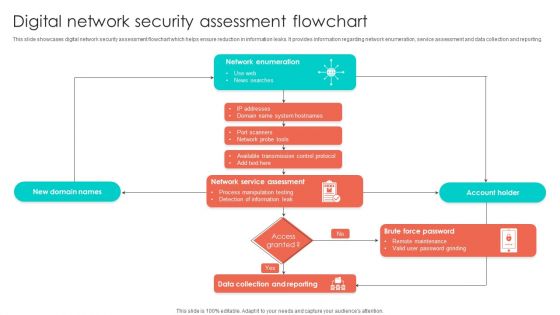
Digital Network Security Assessment Flowchart Structure PDF
This slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Showcasing this set of slides titled Digital Network Security Assessment Flowchart Structure PDF. The topics addressed in these templates are Account Holder, Information Leak, Network Service Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Info Security Ppt PowerPoint Presentation File Sample PDF
Presenting table of contents for info security ppt powerpoint presentation file sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like managing information security, information security budget, information security roadmap timeline, information security implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
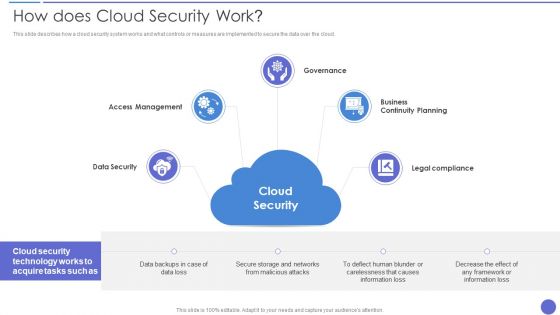
How Does Cloud Security Work Download PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a How Does Cloud Security Work Download PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Encryption Methods, Secure Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
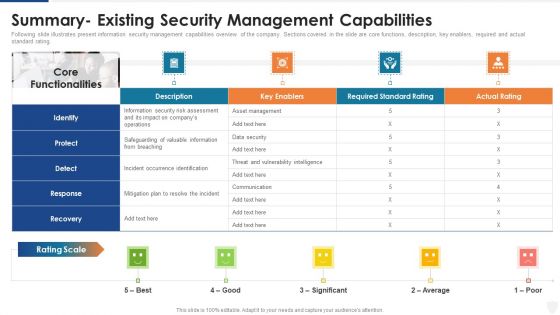
Summary Existing Security Management Capabilities Ppt Outline Themes PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative summary existing security management capabilities ppt outline themes pdf bundle. Topics like security, information, average can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
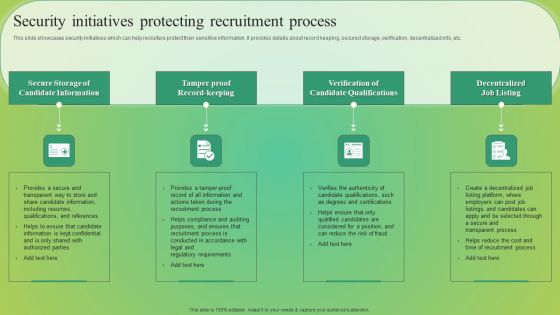
Security Initiatives Protecting Recruitment Process Elements PDF
This slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Slidegeeks is here to make your presentations a breeze with Security Initiatives Protecting Recruitment Process Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system. This is a What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Developing, Essential Strategy, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
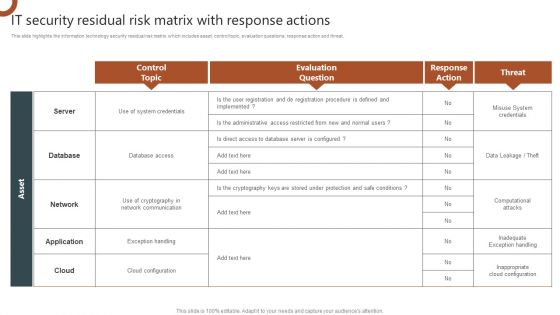
IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
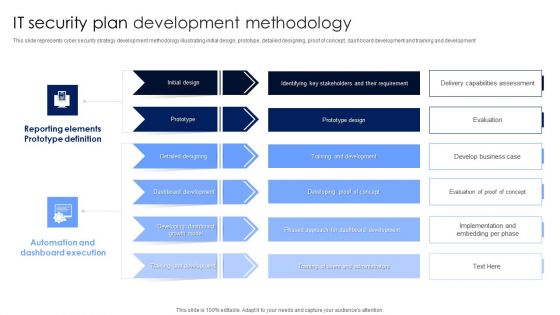
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
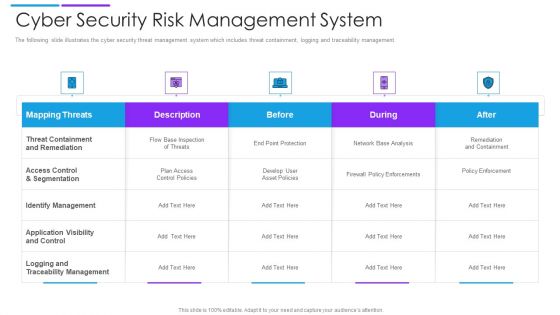
Cyber Security Risk Management System Microsoft PDF
The following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Pitch your topic with ease and precision using this cyber security risk management system microsoft pdf. This layout presents information on mapping threats, threat containment and remediation, identify management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Developing Firm Security Strategy Plan Addressing Different Security Priorities At Organization Background PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of fraud or threat protection, physical security and business continuity. This is a developing firm security strategy plan addressing different security priorities at organization background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fraud or threat protection, physical security, business continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Security Management At Workplace Designs PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present like a pro with Effective Security Management At Workplace Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security And Process Integration Security Operations Implementation Timeline Activity Inspiration PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative security and process integration security operations implementation timeline activity inspiration pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Security Operations Implementation Timeline Staff Ideas PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this security and process integration security operations implementation timeline staff ideas pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Firm Security Strategy Plan Workplace Physical Security Audit Checklist Download PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. Deliver an awe inspiring pitch with this creative developing firm security strategy plan workplace physical security audit checklist download pdf bundle. Topics like general, roofing, hvac, plumbing, lighting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
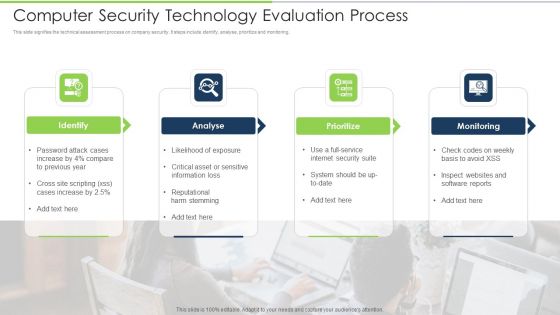
Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Risk Management Plan Mockup PDF
This slide represents cyber security strategy risk assessment process illustrating event preparation, event execution, post mission analysis and reporting. Presenting IT Security Risk Management Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Post Mission Analysis, Reporting, Event Execution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
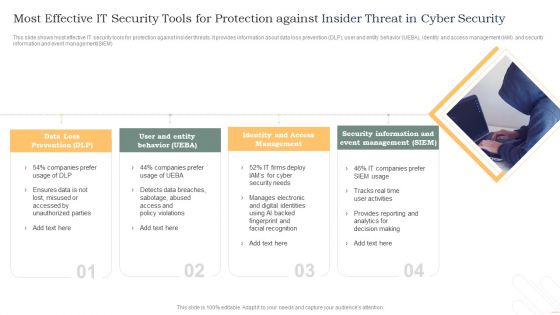
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Network Development Timeline Download PDF
The following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice. Presenting Cyber Security Network Development Timeline Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Establish, Analyse, Practice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Information Technology Management Ppt Images
This is a business information technology management ppt images. This is a five stage process. The stages in this process are bpms, applications, communications, information security, infrastructure and operations.

Desktop Security Management Managing Computer Security 90 Days Plan Professional PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 90 days plan professional pdf bundle. Topics like awareness, security, information, resources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF
The given slide depicts the cyber threat analytics to track the attacks. It includes the no. of incidents, open and solved tickets, category wise no. of incidents along with malware type etc. Pitch your topic with ease and precision using this Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF. This layout presents information on Power Security Team, Open Incidents, Incidents Solved, Open Tickets. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

RPA Discovery Procedure Security Steps Brochure PDF
Following slide exhibits steps for robotic process automation security. Purpose of this slide is to use business automation efficiently that prevents data leakage and fraud. It includes pointers such as bot actions accountability, avoid fraud, secure log integrity etc. Presenting RPA Discovery Procedure Security Steps Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Bot Actions Accountability, Avoid Errors And Fraud, Secure Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
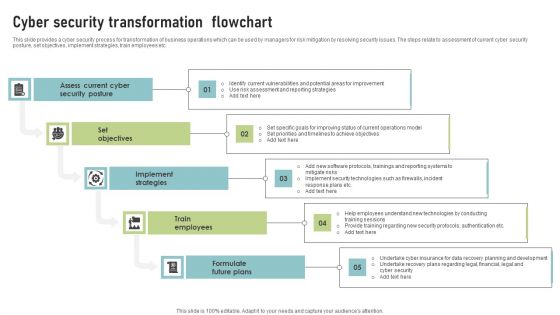
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
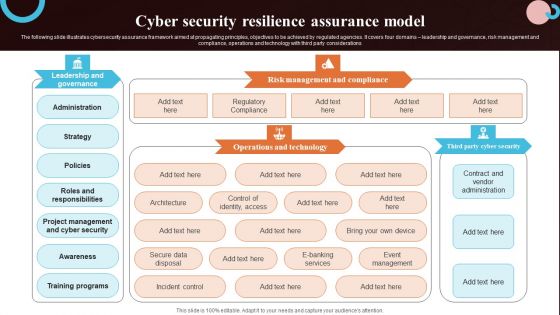
Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF. Use them to share invaluable insights on Effective Preventative, Information Systems, Security Consciousness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
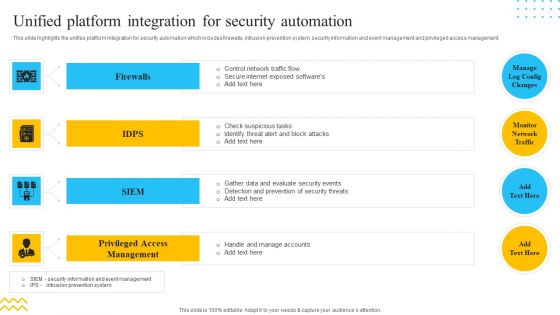
IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. This is a IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, IDPS, SIEM, Privileged Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Introducing Security At Workplace To Ensure Assets Safety Introduction PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Presenting developing firm security strategy plan introducing security at workplace to ensure assets safety introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security policy, organizational strategy, security mission statement, strategic security objectives. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this Ensuring Checklist For Mobile Security Deployment Mobile Device Security Management Pictures PDF. Use them to share invaluable insights on Remotely Locking, Protection Against, Malicious Codes and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Firm Security Strategy Plan Addressing Physical Security At Workplace Ideas PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Presenting developing firm security strategy plan addressing physical security at workplace ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like workplace surveillance, employee monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
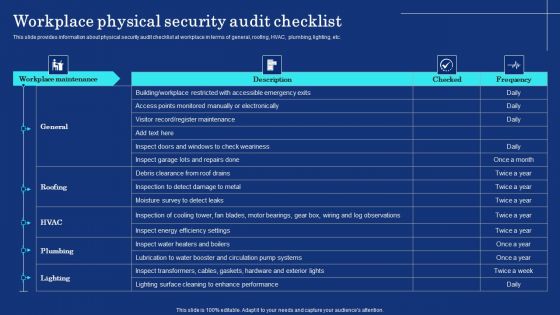
Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. This Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
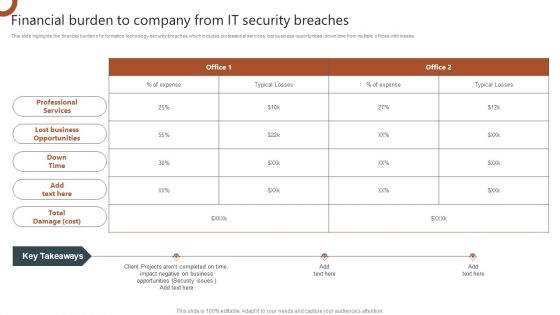
Organizations Risk Management And IT Security Financial Burden To Company From IT Security Breaches Brochure PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Welcome to our selection of the Organizations Risk Management And IT Security Financial Burden To Company From IT Security Breaches Brochure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
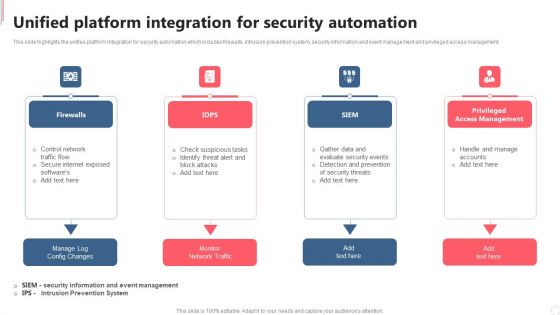
Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present like a pro with Cyber Security Automation Framework Unified Platform Integration For Security Automation Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
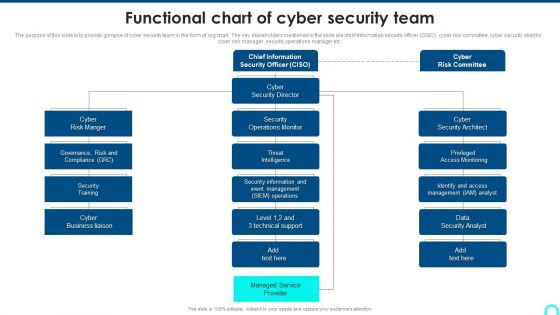
Functional Chart Of Cyber Security Team Diagrams PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc.Deliver an awe inspiring pitch with this creative Functional Chart Of Cyber Security Team Diagrams PDF bundle. Topics like Access Monitoring, Security Architect, Security Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Addressing Different Security Priorities At Organization Clipart PDF
This slide provides information about various security priorities essential in maintaining workplace security in terms of people security, intellectual property, brand protection, crisis management, corporate governance and information security. Find a pre designed and impeccable Addressing Different Security Priorities At Organization Clipart PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Security Agency Business Profile Retail And Shopping Complex Security Services Background PDF
This is a Security Agency Business Profile Retail And Shopping Complex Security Services Background PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Security, Shopping Complex Security, Theatre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Sample Of Security Knowledge Management Diagram Ppt Example
This is a sample of security knowledge management diagram ppt example. This is a four stage process. The stages in this process are detection of relocations, position information management, security management, management department.

Cloud Based Email Security Market Report Hosted E Mail Security Ppt Ideas Rules PDF
This slide displays the overview and key features of hosted E Mail Security. This is a cloud based email security market report hosted e mail security ppt ideas rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like maintenance, security, miscellaneous, protection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Risk Management Model For Data Security Structure PDF
This is a Agenda For Risk Management Model For Data Security Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Effectively Managing, Organizational Risks Arising, Threats And Vulnerabilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda Of IT Security Risk Management Approach Introduction Infographics PDF
This is a Agenda Of IT Security Risk Management Approach Introduction Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Business Agility, Risk Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Measures And Ways To Mitigate Security Management Challenges Icons PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver and pitch your topic in the best possible manner with this measures and ways to mitigate security management challenges icons pdf. Use them to share invaluable insights on information, security training, implementing, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
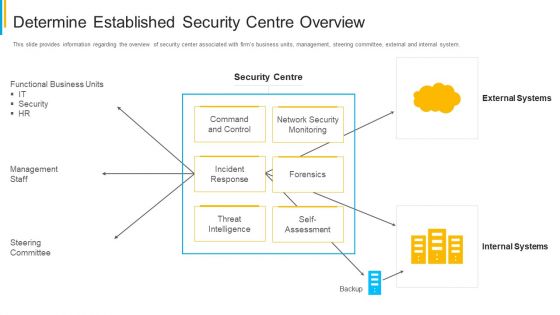
Project Security Administration IT Determine Established Security Centre Overview Infographics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this project security administration it determine established security centre overview infographics pdf. Use them to share invaluable insights on functional business units, management staff, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
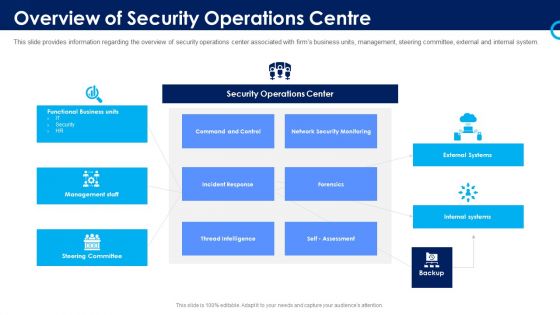
Organizational Security Solutions Overview Of Security Operations Centre Ppt Styles Graphics Pictures PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this organizational security solutions overview of security operations centre ppt styles graphics pictures pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
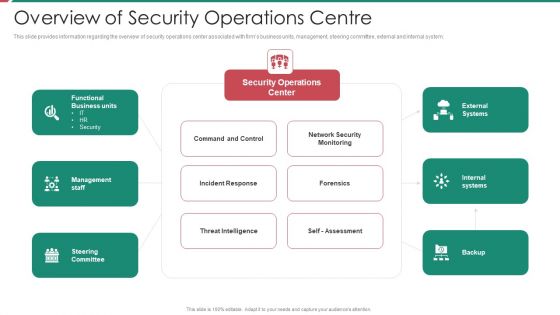
Security And Process Integration Overview Of Security Operations Centre Portrait PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security and process integration overview of security operations centre portrait pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home