Information Security Program
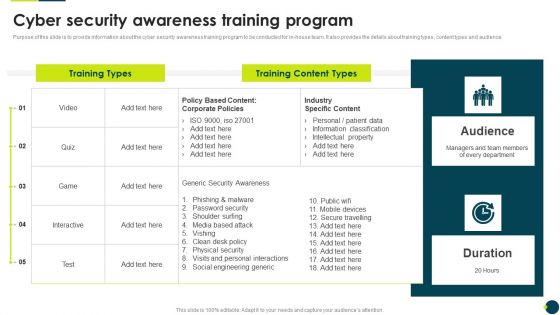
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
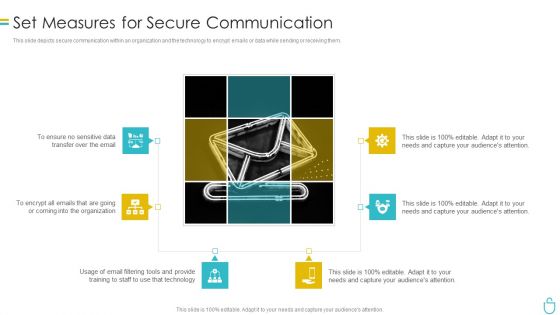
Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

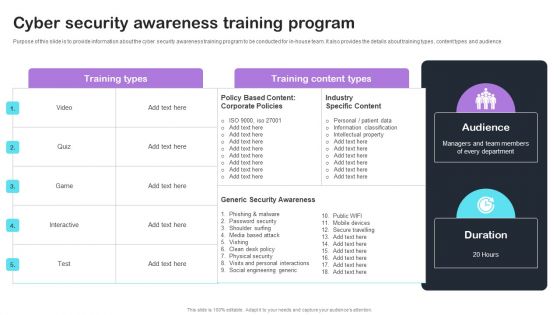
Safety Breach Response Playbook Cyber Security Awareness Training Program Diagrams PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience. Find a pre-designed and impeccable Safety Breach Response Playbook Cyber Security Awareness Training Program Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cyber Safety Awareness Program Services Platform Ppt Show Information PDF
This slide covers platform for providing security awareness training services to clients. It includes elements such as platforms comprising of security awareness training content, phishing case studies, quarterly cyber awareness training, human based testing, monthly incident reporting, etc. Showcasing this set of slides titled Cyber Safety Awareness Program Services Platform Ppt Show Information PDF. The topics addressed in these templates are Platforms, Development, Core Self Managed. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
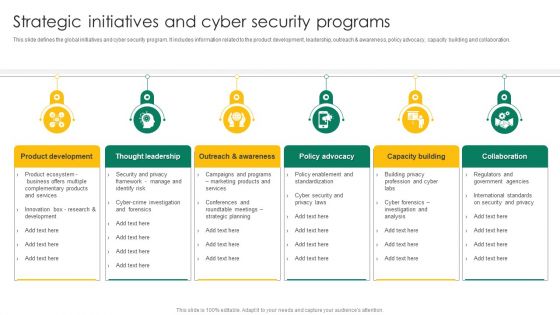
Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF
This slide defines the global initiatives and cyber security program. it includes information related to the product development, leadership, outreach and awareness, policy advocacy, capacity building and collaboration. Persuade your audience using this Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Product Development, Thought Leadership, Policy Advocacy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
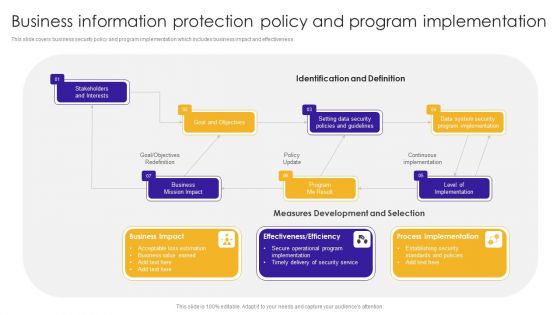
Business Information Protection Policy And Program Implementation Brochure PDF
This slide covers business security policy and program implementation which includes business impact and effectiveness.Showcasing this set of slides titled Business Information Protection Policy And Program Implementation Brochure PDF. The topics addressed in these templates are Acceptable Loss, Business Value Earned, Secure Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
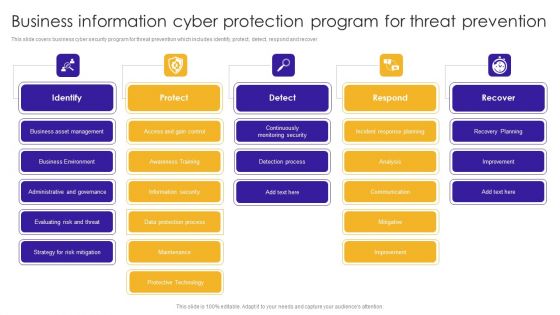
Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
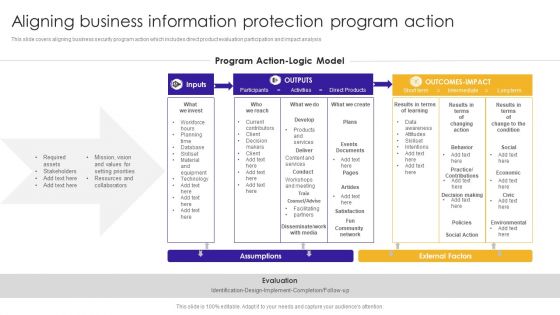
Aligning Business Information Protection Program Action Structure PDF
This slide covers aligning business security program action which includes direct product evaluation participation and impact analysis.Showcasing this set of slides titled Aligning Business Information Protection Program Action Structure PDF. The topics addressed in these templates are Setting Priorities, Assets Stakeholders, Decision Making. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance Key Features Of SIEM Information PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting security information and event management strategies for financial audit and compliance key features of siem information pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like compliance and internal auditing, comprehensive log collection, normalization classification. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Key Takeaways, Countries, Region and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. This Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
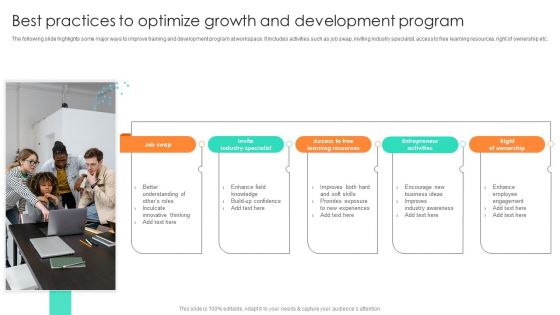
Best Practices To Optimize Growth And Development Program Information PDF
The following slide highlights some major ways to improve training and development program at workspace. It includes activities such as job swap, inviting industry specialist, access to free learning resources, right of ownership etc. Presenting Best Practices To Optimize Growth And Development Program Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Entrepreneur Activities, Right Of Ownership, Industry Awareness. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Effective IT Security Awareness Training Program Background PDF
This slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Effective IT Security Awareness Training Program Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Including Everyone, Establishing Basics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
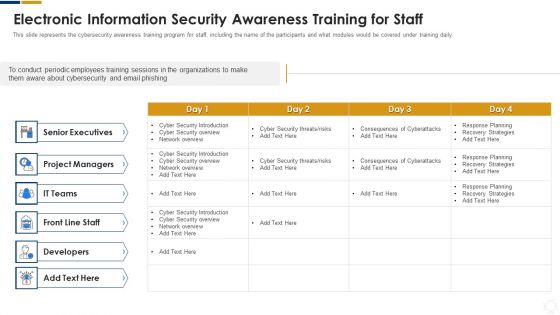
Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Client Profile And Information Security Vector Icon Ppt PowerPoint Presentation File Good PDF
Persuade your audience using this client profile and information security vector icon ppt powerpoint presentation file good pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including client profile and information security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity What Is Electronic Information Security And How Does It Work Ppt Model Shapes PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Presenting cybersecurity what is electronic information security and how does it work ppt model shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, devices, techniques. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various Data Security Threats That Might Affect Your Business Ppt PowerPoint Presentation Professional Information PDF
Persuade your audience using this various data security threats that might affect your business ppt powerpoint presentation professional information pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including data compliance, data corruption, dark data risk, data remanence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
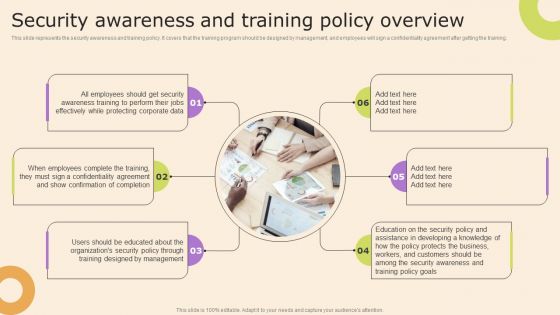
Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Presenting this PowerPoint presentation, titled Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Technology Policy And Processes Security Awareness And Training Policy Overview Mockup PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Laptop The Concept Of Information Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Laptop The Concept Of Information Security PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Secuity PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Download our Business PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please. Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one.Use these PowerPoint slides for presentations relating to Laptop the concept of information safety, security, success, business, technology, computer. The prominent colors used in the PowerPoint template are Blue, Yellow, Black. We assure you our Laptop The Concept Of Information Security PowerPoint Templates PPT Backgrounds For Slides 0113 will help them to explain complicated concepts. PowerPoint presentation experts tell us our security PowerPoint templates and PPT Slides have awesome images to get your point across. Presenters tell us our Laptop The Concept Of Information Security PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter successul in his career/life. Professionals tell us our safety PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. The feedback we get is that our Laptop The Concept Of Information Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our of PowerPoint templates and PPT Slides look good visually.

Email Locked Confidential Information Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Email Locked Confidential Information Security PowerPoint Templates PPT Backgrounds For Slides 0313.Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Use our Services PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download our Business PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides have the Brilliant backdrops. Guaranteed to illuminate the minds of your audience.Use these PowerPoint slides for presentations relating to Locked envelope with key security, security, services, technology, business, shapes. The prominent colors used in the PowerPoint template are Green, Black, Blue light.
Cloud Technology Information Security Management Vector Icon Ppt PowerPoint Presentation Gallery Influencers PDF
Presenting cloud technology information security management vector icon ppt powerpoint presentation gallery influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cloud technology information security management vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Laptop With Lock Information Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Lock Information Security PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Use our Technology PowerPoint Templates because You can Score a slam dunk with our PowerPoint Templates and Slides. Watch your audience hang onto your every word. Download our Security PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Use our Network Diagrams PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to 3d illustration of laptop with lock, business, computer, security, network diagrams, technology . The prominent colors used in the PowerPoint template are Blue, Gray, Yellow.
Protection Shield Icon For Information Security Ppt PowerPoint Presentation File Background PDF
Presenting protection shield icon for information security ppt powerpoint presentation file background pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including protection shield icon for information security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
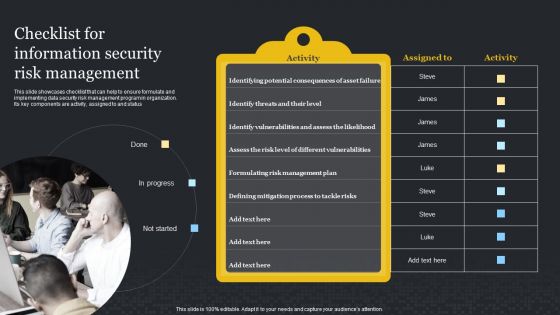
Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Concrete Wall With Shield For Security Vector Icon Ppt PowerPoint Presentation Infographic Template Information PDF
Presenting this set of slides with name concrete wall with shield for security vector icon ppt powerpoint presentation infographic template information pdf. This is a three stage process. The stages in this process are concrete wall with shield for security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Information Security Data Protection Vector Icon Ppt PowerPoint Presentation Gallery Clipart PDF
Persuade your audience using this information security data protection vector icon ppt powerpoint presentation gallery clipart pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including information security data protection vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Technology Security Vector Icon Ppt PowerPoint Presentation Infographic Template Grid PDF
Persuade your audience using this information technology security vector icon ppt powerpoint presentation infographic template grid pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including information technology security vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.This is a Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disaster, Environmental Control Failures, Deliberate Software Attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Operations Cyber Security Protection Icon Rules PDF
Persuade your audience using this Security Operations Cyber Security Protection Icon Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Protection Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
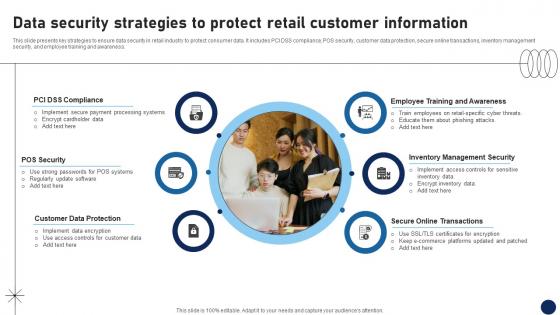
Data Security Strategies To Protect Retail Customer Information DT SS V
This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Security Strategies To Protect Retail Customer Information DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Security Operations Cyber Security Icon With Lock Clipart PDF
Persuade your audience using this Security Operations Cyber Security Icon With Lock Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Icon With Lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
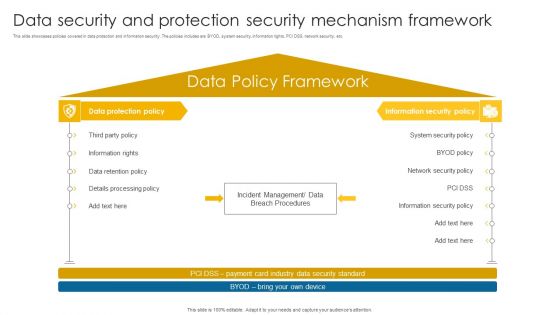
Data Security And Protection Security Mechanism Framework Background PDF
This slide showcases policies covered in data protection and information security. The policies includes are BYOD, system security, information rights, PCI DSS, network security, etc.Pitch your topic with ease and precision using this Data Security And Protection Security Mechanism Framework Background PDF. This layout presents information on Information Rights, Retention Policy, Details Processing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
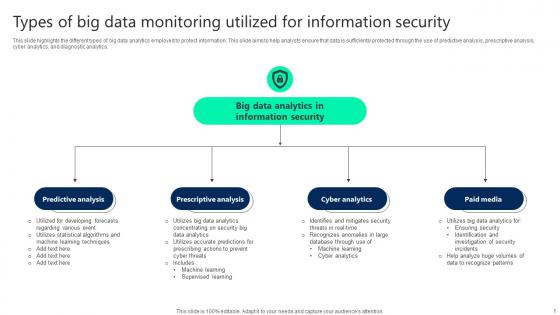
Types Of Big Data Monitoring Utilized For Information Security Elements pdf
This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Pitch your topic with ease and precision using this Types Of Big Data Monitoring Utilized For Information Security Elements pdf. This layout presents information on Predictive Analysis, Prescriptive Analysis, Cyber Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
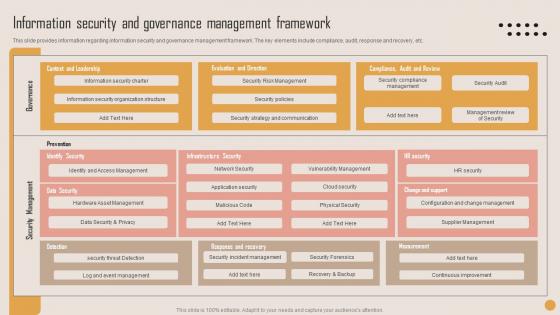
Information Security Governance Playbook For Strategic Actions To Improve IT Performance Themes Pdf
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. This Information Security Governance Playbook For Strategic Actions To Improve IT Performance Themes Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Governance Playbook For Strategic Actions To Improve IT Performance Themes Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Information Security Communication Plan Ppt Powerpoint Presentation Complete Deck With Slides This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fiveteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Pillars Of Cloud Security Network Security Rules PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. This is a Pillars Of Cloud Security Network Security Rules PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure, Network, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Roadmap For Computer Security Training Graphics PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting desktop security management roadmap for computer security training graphics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
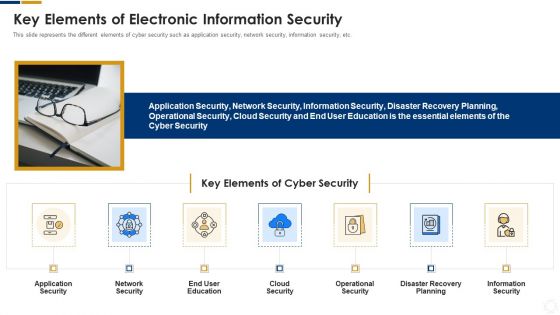
Cybersecurity Key Elements Of Electronic Information Security Ppt Styles Smartart PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a cybersecurity key elements of electronic information security ppt styles smartart pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Information Technology Security Ppt File Mockup PDF
Presenting table of contents for information technology security ppt file mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security implementation, managing it security, it security budget, it security roadmap timeline . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
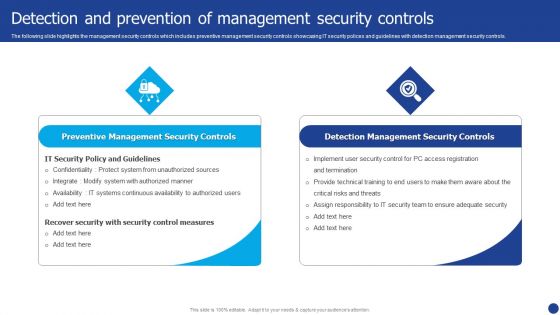
Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Cloud Security Work Data Security Infographics PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. This is a How Does Cloud Security Work Data Security Infographics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Security, Physical Security, Internet Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role IT Team Digital Transformation Role Of Chief Information Security Officer Summary PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting role it team digital transformation role of chief information security officer summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like security information, security staff, monthly reports. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
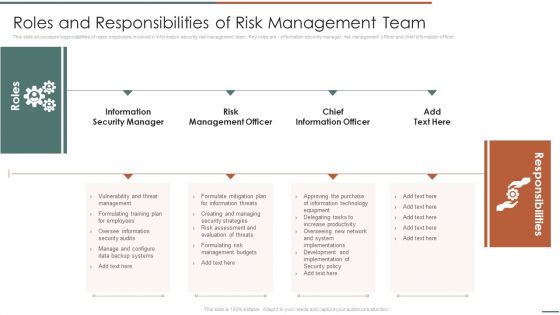
Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF bundle. Topics like Information Security Manager, Risk Management, Chief Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Role Of Security Operations Centre In Security Operations Structure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. This is a role of security operations centre in security operations structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like operations team is responsible, compliance requirements checklist, security will be present. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
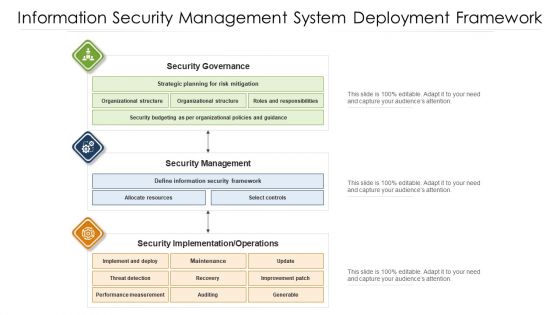
Information Security Management System Deployment Framework Ppt PowerPoint Presentation File Structure PDF
Showcasing this set of slides titled information security management system deployment framework ppt powerpoint presentation file structure pdf. The topics addressed in these templates are security management, security governance, security implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Process To Manage Firms Sensitive Data Ppt Infographics Background Image PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative information security process to manage firms sensitive data ppt infographics background image pdf bundle. Topics like management, system, security, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Role Of Security In Open RAN Standards Unlocking The Potential Of Open RAN Information Pdf
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Role Of Security In Open RAN Standards Unlocking The Potential Of Open RAN Information Pdf from Slidegeeks and deliver a wonderful presentation.
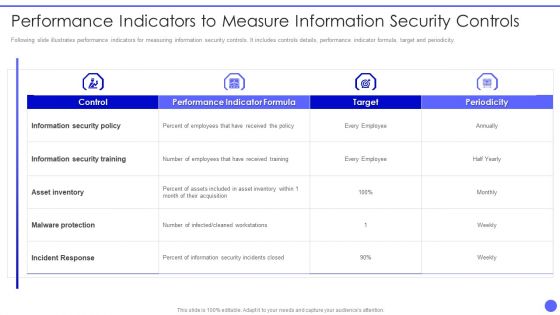
Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF. Use them to share invaluable insights on Information Security Policy, Information Security Training, Asset Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

International Organization Standardization 270001 Performance Indicators To Measure Information Security Controls Clipart PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 performance indicators to measure information security controls clipart pdf. Use them to share invaluable insights on information security policy, information security training, incident response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF. Use them to share invaluable insights on Cloud Frameworks, Information Division, Cautious Scaling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Uniformed Security Security Guard Services Proposal Specializing In Icons PDF
This is a uniformed security security guard services proposal specializing in icons pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like environments, security, investigations, communication, entertainment facilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.This is a Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Encrypted Data, Sensitive Information You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
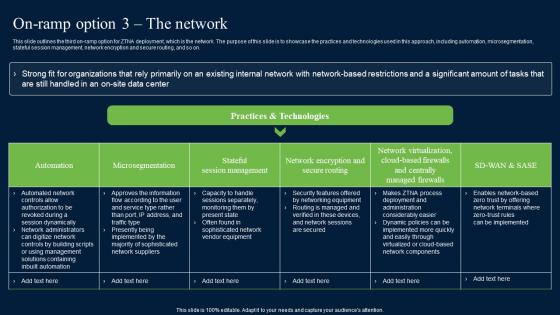
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today.

 Home
Home