Information Security Program

Phishing Attacks Awareness Training Program Plan Inspiration PDF
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Rescue Icon Rss Information PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Rescue Icon RSS Information PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Network diagrams PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Present our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download and present our Signs PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime.Use these PowerPoint slides for presentations relating to Rss feed vector with Life Buoy, network diagrams, business, marketing, signs, security. The prominent colors used in the PowerPoint template are Yellow, Red, White. We assure you our Rescue Icon RSS Information PowerPoint Templates PPT Backgrounds For Slides 0113 will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. PowerPoint presentation experts tell us our vector PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Presenters tell us our Rescue Icon RSS Information PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Professionals tell us our vector PowerPoint templates and PPT Slides will make you look like a winner. The feedback we get is that our Rescue Icon RSS Information PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our network PowerPoint templates and PPT Slides have awesome images to get your point across.
Locked Folder For Confidential Information Vector Icon Ppt Icon Layout PDF
Presenting locked folder for confidential information vector icon ppt icon layout pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including locked folder for confidential information vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
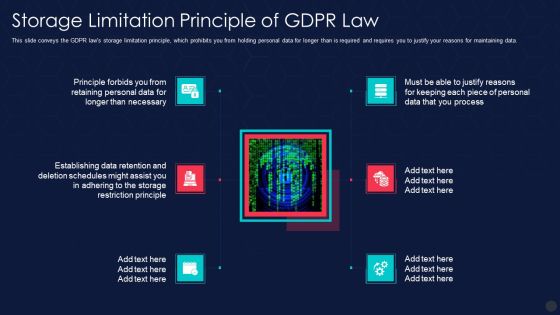
Information Privacy IT Storage Limitation Principle Of Gdpr Law Professional PDF
This slide conveys the GDPR laws storage limitation principle, which prohibits you from holding personal data for longer than is required and requires you to justify your reasons for maintaining data. This is a information privacy it storage limitation principle of gdpr law professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like storage limitation principle of gdpr law. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Privacy IT Monitor And Detect Abnormal Activity On Sensitive Data Structure PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Presenting information privacy it monitor and detect abnormal activity on sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like monitor and detect abnormal activity on sensitive data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Purpose Limitation Principle Of Gdpr Law Topics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Presenting information privacy it purpose limitation principle of gdpr law topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like rpose limitation principle of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Analyzing The Impact Of Russia Ukraine Conflict On Gas Sector Russian Conflict Risk On Security Icons PDF
This slide showcases Russia invasion risk to security of Ukrainian gas transmission system GTS. It provides information about military intervention, instability zone, south stream project, etc. This is a analyzing the impact of russia ukraine conflict on gas sector russian conflict risk on security icons pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like russian conflict risk on security of ukrainian gas transportation system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Benefits Of Security As A Service Secaas Xaas Cloud Computing Models Ppt PowerPoint Presentation Show Slide Portrait PDF
This slide describes the benefits of security as a service, such as free up resources, most recent security updates and tools, cost savings, and improved agility and quick provisioning.This is a Benefits Of Security As A Service Secaas Xaas Cloud Computing Models Ppt PowerPoint Presentation Show Slide Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Dashboards, Security Handled, Effectively Outsourced. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF
This is a Table Of Contents For Risk Based Procedures To IT Security Wd Ppt PowerPoint Presentation File Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Global Market, IoT Products, Companies Digitization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
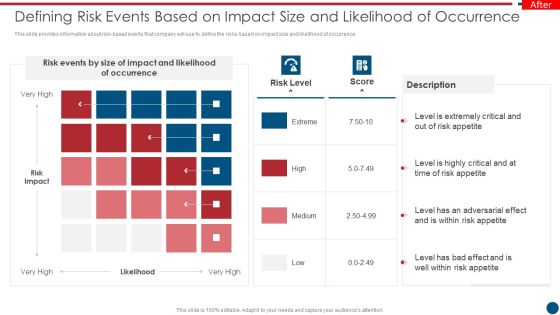
Risk Based Procedures To IT Security Defining Risk Events Based On Impact Size And Likelihood Summary PDF
This slide provides information about risk-based events that company will use to define the risks based on impact size and likelihood of occurrence. This is a Risk Based Procedures To IT Security Defining Risk Events Based On Impact Size And Likelihood Summary PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Events, Risk Impact, Risk Appetite. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Develop Corporate Cyber Security Risk Mitigation 30 60 90 Days Plan For Organization Cyber Protection Proposal Mockup PDF
This is a develop corporate cyber security risk mitigation 30 60 90 days plan for organization cyber protection proposal mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF
This slide covers plan related to cyber security awareness. It includes timeline pertaining to preparation, detection, analysis, eradication, recover and post incident of a security lapse. Presenting Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Post Inside, Eradicate and Recover, Detection, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
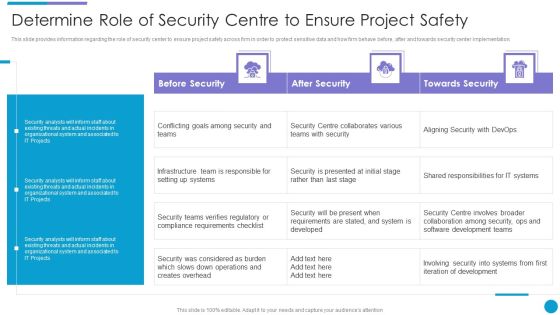
Major Techniques For Project Safety IT Determine Role Of Security Centre To Ensure Project Safety Download PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative major techniques for project safety it determine role of security centre to ensure project safety download pdf bundle. Topics like before security, after security, towards security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
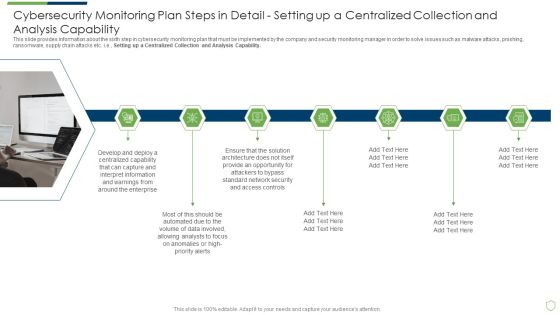
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
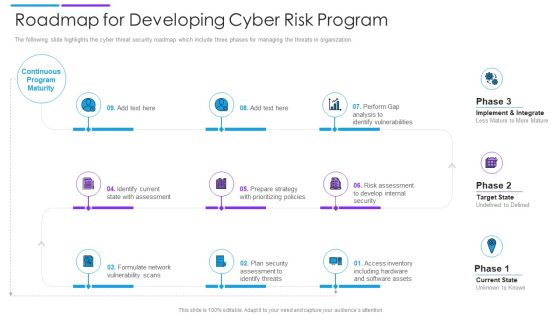
Roadmap For Developing Cyber Risk Program Download PDF
The following slide highlights the cyber threat security roadmap which include three phases for managing the threats in organization. Persuade your audience using this roadmap for developing cyber risk program download pdf. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including internal security, software assets, identify threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Everything As A Service Xaas For Cloud Computing IT Security As A Service Secaas Overview Portrait PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service. Presenting everything as a service xaas for cloud computing it security as a service secaas overview portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like expenses, security, organization, services, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
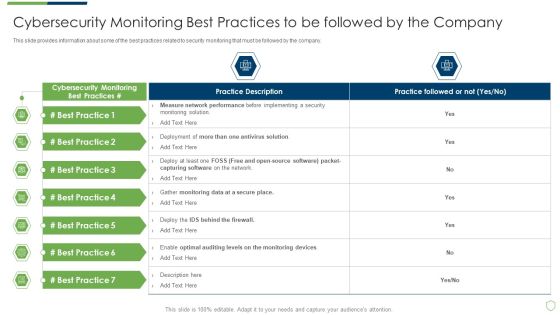
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Policy And Why You Should Embrace It Cloud Computing Security IT Ppt Infographics Gridlines PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a zero trust policy and why you should embrace it cloud computing security it ppt infographics gridlines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication, device validation, restrict access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Measures And Ways To Mitigate Rules PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach measures and ways to mitigate rules pdf. Use them to share invaluable insights on measures and ways to mitigate security monitoring challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
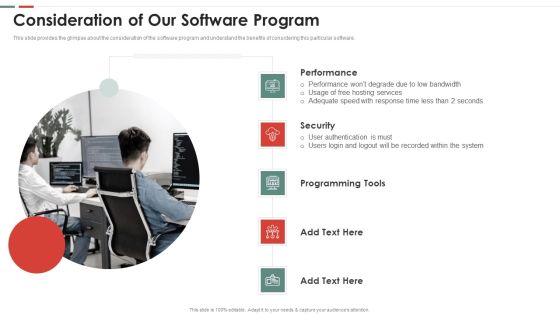
Feasibility Analysis Template Different Projects Consideration Of Our Software Program Infographics PDF
This slide provides the glimpse about the consideration of the software program and understand the benefits of considering this particular software. This is a feasibility analysis template different projects consideration of our software program infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performance, security, programming tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Presenting 1G To 5G Wireless Communication System IT What Security Features Does 5G 5Th Generation Technology Include Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Cryptographic Evidence, Domestic, Via Network Slicing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Develop Corporate Cyber Security Risk Mitigation Plan Next Steps For Organization Cyber Protection Services Topics PDF Themes PDF
Presenting develop corporate cyber security risk mitigation plan next steps for organization cyber protection services topics pdf themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like desired changes, initial payment, organization, cyber protection services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

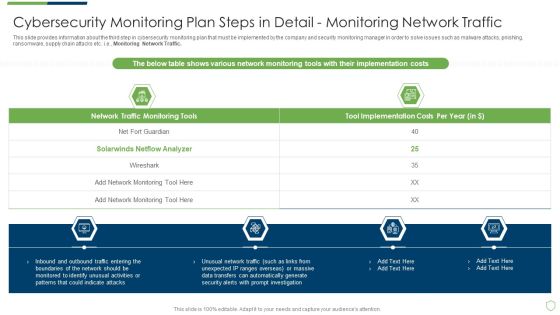
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Building An IT Strategy Plan For Business Expansion Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. There are so many reasons you need a Building An IT Strategy Plan For Business Expansion Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
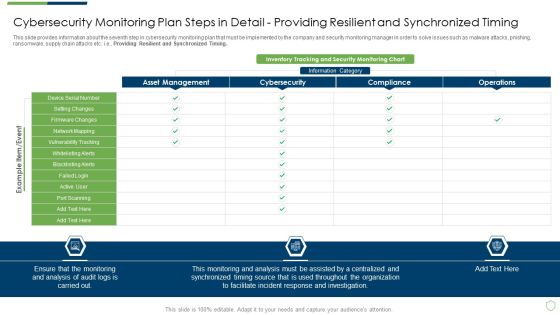
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
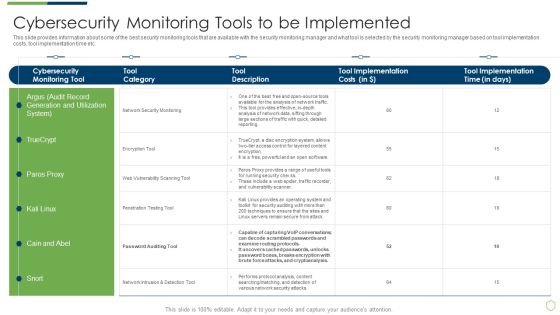
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Boost your pitch with our creative IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF
This slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map. Showcasing this set of slides titled Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF. The topics addressed in these templates are Risk Heat Map, Action Plan Breakdown, Risk Rating Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF bundle. Topics like Virtualization Threats, Information Interception, Unauthorized Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

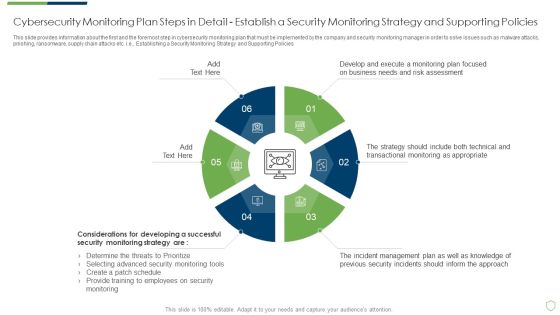
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks Ppt PowerPoint Presentation Complete Deck With Slides
This Implementing Cybersecurity Awareness Program To Prevent Attacks Ppt PowerPoint Presentation Complete Deck With Slides is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This seventy five slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.
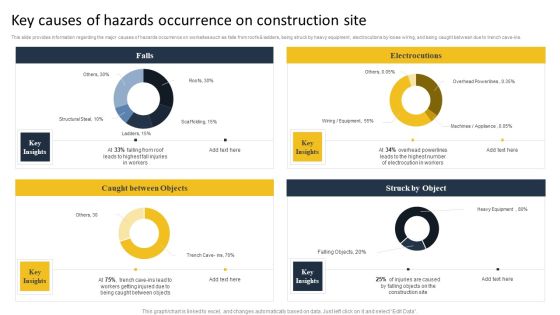
Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF
This slide provides information regarding the major causes of hazards occurrence on worksites such as falls from roofs AND ladders, being struck by heavy equipment, electrocutions by loose wiring, and being caught between due to trench cave-ins. Find a pre designed and impeccable Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for. Download the template from Slidegeeks today and give a unique touch to your presentation.

Building An IT Strategy Plan For Business Expansion How Management Enables Effective Corporate Security Governance Diagrams PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Slidegeeks is here to make your presentations a breeze with Building An IT Strategy Plan For Business Expansion How Management Enables Effective Corporate Security Governance Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cloud Intelligence Framework For Application Consumption Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like power management, building management, security management, security effectiveness, global supervision can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact IT Security IT Plan Can Reduce The Risk Of Data Breach In Organization Ppt Infographic Template Objects PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this detail impact it security it plan can reduce the risk of data breach in organization ppt infographic template objects pdf. Use them to share invaluable insights on detail impact it security it plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
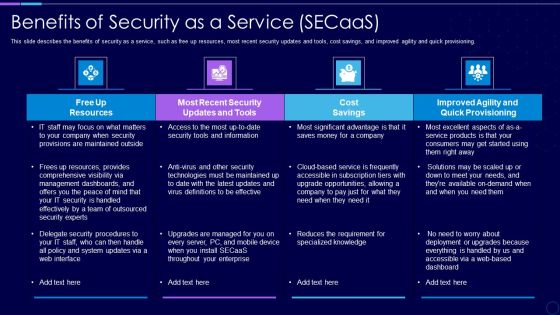
Everything As A Service Xaas For Cloud Computing IT Benefits Of Security As A Service Clipart PDF
This slide describes the benefits of security as a service, such as free up resources, most recent security updates and tools, cost savings, and improved agility and quick provisioning. Deliver an awe inspiring pitch with this creative everything as a service xaas for cloud computing it benefits of security as a service clipart pdf bundle. Topics like cost savings, security, resources, dashboards can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hotel Security Personnel Looking At Various CCTV Footage On Computers Ppt PowerPoint Presentation File Visual Aids PDF
Presenting hotel security personnel looking at various cctv footage on computers ppt powerpoint presentation file visual aids pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including hotel security personnel looking at various cctv footage on computers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

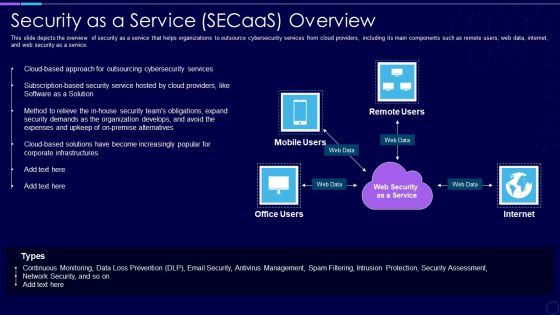
Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
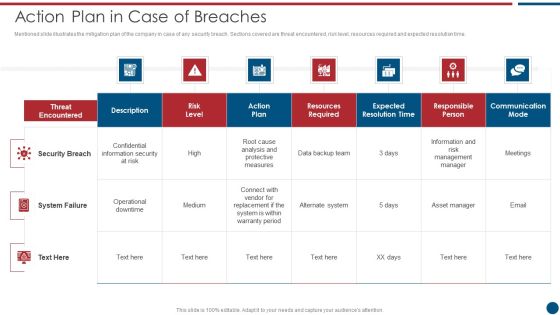
Risk Based Procedures To IT Security Action Plan In Case Of Breaches Ppt PowerPoint Presentation File Model PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Action Plan In Case Of Breaches Ppt PowerPoint Presentation File Model PDF bundle. Topics like Threat Encountered, Communication Mode, Security Breach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CRM Implementation Strategy CRM Training Program For Employees Infographics PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session.This is a CRM Implementation Strategy CRM Training Program For Employees Infographics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Session, Customization Session, Overview Training You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
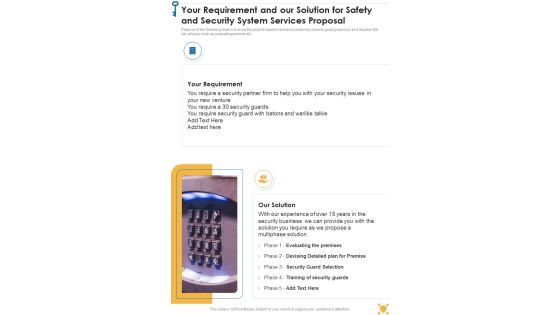
Your Requirement And Our Solution For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the project requirement and solution for security guard proposal, as it displays the key phases such as evaluating premise etc. Presenting you an exemplary Your Requirement And Our Solution For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Requirement And Our Solution For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

30 60 90 Days Plan For Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary 30 60 90 Days Plan For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this 30 60 90 Days Plan For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
Timeline For Safety And Security System Services Proposal One Pager Sample Example Document One Pager Sample Example Document
Presenting you an exemplary Timeline For Safety And Security System Services Proposal One Pager Sample Example Document One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline For Safety And Security System Services Proposal One Pager Sample Example Document One Pager Sample Example Document brilliant piece now.

Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF
This slide depicts the official announcement to avoid russias kaspersky antivirus tool by german officials as kaspersky has been accused of working for the russian government. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF today and make your presentation stand out from the rest.

Cloud Intelligence Framework For Application Consumption Financial Losses To The Organizations Due To Security Issues Mockup PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption financial losses to the organizations due to security issues mockup pdf bundle. Topics like security vulnerabilities, primary reasons for the growing, physical theft of a data-carrying device, 2016 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF
This slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc.Showcasing this set of slides titled Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF. The topics addressed in these templates are Management Failures, Irregular Penetration, Expense Borne. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
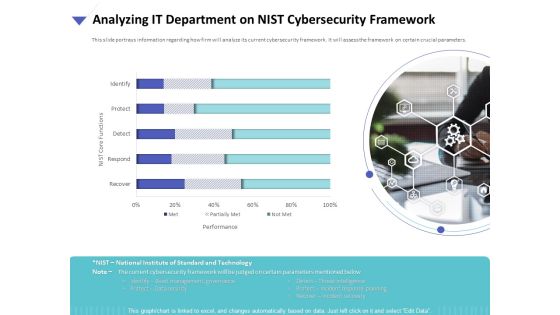
Strategies To Mitigate Cyber Security Risks Analyzing IT Department On NIST Cybersecurity Framework Ppt Slides Background Designs PDF
Presenting this set of slides with name strategies to mitigate cyber security risks analyzing it department on nist cybersecurity framework ppt slides background designs pdf. The topics discussed in these are performance, nist core functions, identify, protect, detect, recover, respond. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
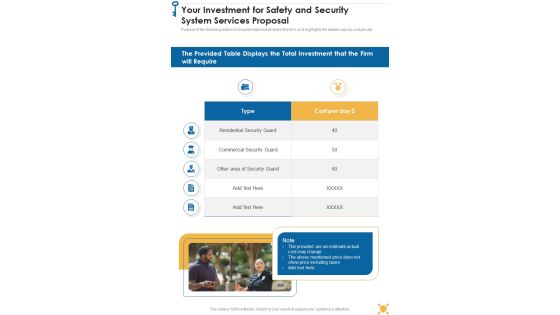
Your Investment For Safety And Security System Services Proposal One Pager Sample Example Document One Pager Sample Example Document
Purpose of the following slide is to show the total investment of the firm, as it highlights the details such as cost per day. Presenting you an exemplary Your Investment For Safety And Security System Services Proposal One Pager Sample Example Document One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Investment For Safety And Security System Services Proposal One Pager Sample Example Document One Pager Sample Example Document brilliant piece now.

Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
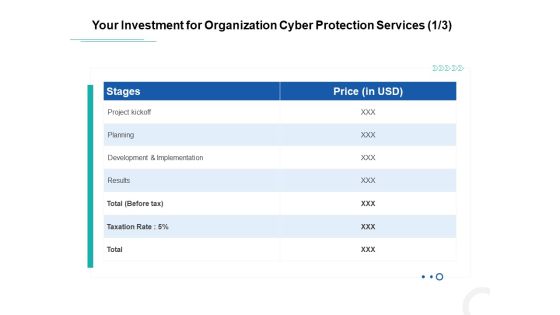
Develop Corporate Cyber Security Risk Mitigation Plan Your Investment For Organization Cyber Protection Services Planning Rules PDF
Deliver and pitch your topic in the best possible manner with this develop corporate cyber security risk mitigation plan your investment for organization cyber protection services planning rules pdf. Use them to share invaluable insights on project kickoff, planning, development and implementation, results and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Develop Corporate Cyber Security Risk Mitigation Plan Case Study For Organization Cyber Protection Services Themes PDF Sample PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan case study for organization cyber protection services themes pdf sample pdf bundle. Topics like problem, results, our solution, low cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home