Information Security Program

Digitization Of Security Systems KPI Dashboard Ppt Summary Portfolio PDF
The following slide highlights a comprehensive dashboard used to analyze the performance of digitization of security systems. It provides information about total automations performed, records created, time taken by each security analyst, incidents by different groups etc. Showcasing this set of slides titled Digitization Of Security Systems KPI Dashboard Ppt Summary Portfolio PDF. The topics addressed in these templates are Automations Performed, Records Created, Hours Saved. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF
This slide covers cyber security health status dashboard . It also includes audit and compliance, controls health, project status, incident response process, vulnerability patching schedule, investigation process and training compliance. Pitch your topic with ease and precision using this Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF. This layout presents information on Cyber Security, Vulnerability Patching Schedule, Compliance Investigation Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Computing Services Security Architecture Assessment Infographics PDF
The slideshows an assessment model of CSP cloud service security. It includes identification of existing warrant, verification of certificates and reports, evidence review and additional information collection about third party warrant and certificates. Showcasing this set of slides titled Cloud Computing Services Security Architecture Assessment Infographics PDF. The topics addressed in these templates are Cloud Control Profile, Administrative Need, Safety Security Needs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Smart Home Security Solutions Company Profile SWOT Analysis Rules PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. Presenting Smart Home Security Solutions Company Profile SWOT Analysis Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths Weaknesses Opportunities, Threats Market Technology, Home Security Devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Artificial Intelligence Security Issues And Solutions Analysis Topics PDF
The purpose of this template is to provide details of artificial intelligence AI security analysis based on the challenges faced and solutions available. It covers different applications used in AI for maintaining security and privacy. Pitch your topic with ease and precision using this Artificial Intelligence Security Issues And Solutions Analysis Topics PDF. This layout presents information on Applications, Autonomous Systems, Wireless. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

How Management Enables Effective Corporate Security Governance Topics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward How Management Enables Effective Corporate Security Governance Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal How Management Enables Effective Corporate Security Governance Topics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Manpower Corporate Security Business Profile Swot Analysis Introduction PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Swot Analysis Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weaknesses, Opportunities, Threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Data Security Software As A Service Saas Portrait PDF
This slide describes the software as a service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model. Presenting Cloud Data Security Software As A Service Saas Portrait PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Advantages, Disadvantages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
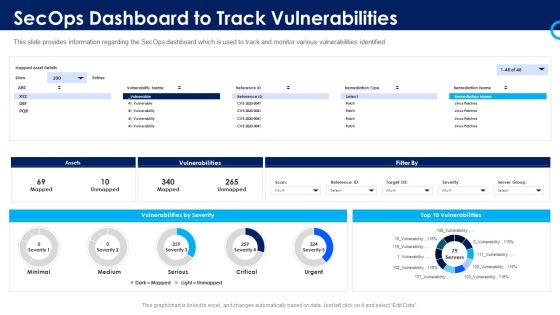
Organizational Security Solutions Secops Dashboard To Track Vulnerabilities Pictures PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this organizational security solutions secops dashboard to track vulnerabilities pictures pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
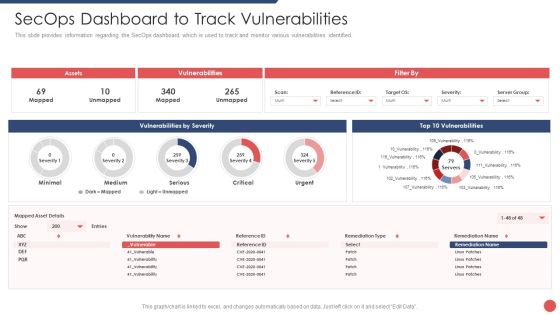
Security Functioning Centre Secops Dashboard To Track Vulnerabilities Portrait PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver an awe inspiring pitch with this creative security functioning centre secops dashboard to track vulnerabilities portrait pdf bundle. Topics like assets, vulnerabilities, vulnerabilities by severity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Risk Management Framework To Manage Security Threats Summary PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Retrieve professionally designed IT Risk Management Framework To Manage Security Threats Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
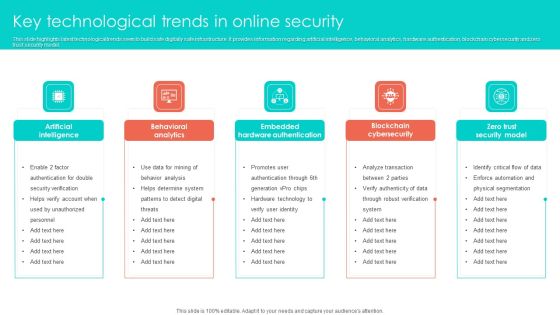
Key Technological Trends In Online Security Clipart PDF
This slide highlights latest technological trends seen to build safe digitally safe infrastructure. It provides information regarding artificial intelligence, behavioral analytics, hardware authentication, blockchain cybersecurity and zero trust security model. Persuade your audience using this Key Technological Trends In Online Security Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Behavioral Analytics, Artificial Intelligence, Embedded Hardware Authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Timeframe For Incident Management In Security Centre Portrait PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Timeframe For Incident Management In Security Centre Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Security Asset Risk Analysis Software Report Pictures PDF
This slide covers the risk identification status report for different cyber incidents. It includes malicious insider activity, confidential data loss, system failure and denial of service attacks. Pitch your topic with ease and precision using this Cyber Security Asset Risk Analysis Software Report Pictures PDF. This layout presents information on Cyber Security Asset Risk, Analysis Software Report. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
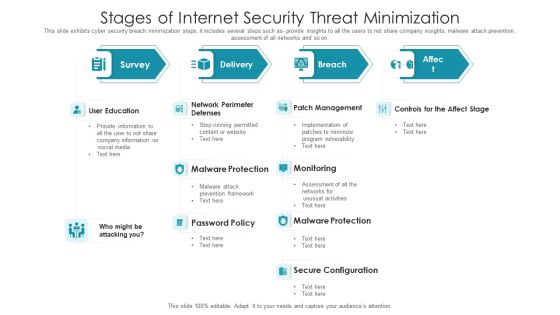
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

What Are The Downsides Of A Cloud Security Download PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting What Are The Downsides Of A Cloud Security Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Manage Security In Cloud Background PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting How To Manage Security In Cloud Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Firewalls, Access Controls, Data Recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
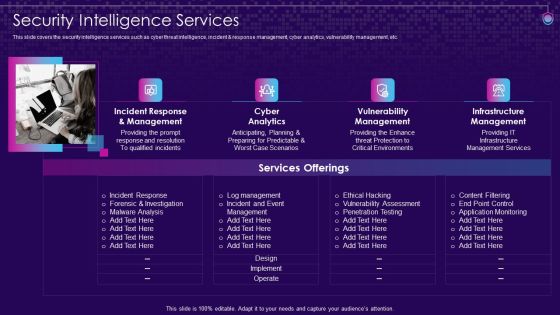
SIEM Services Security Intelligence Services Ppt Show Layouts PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem services security intelligence services ppt show layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management cyber, analytics vulnerability, management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Communication Plan To Assess Channel Effectiveness Themes PDF
This slide provides information about various channels to effectively communicate of cyber security incidents to respected department. It includes channels such as emails, alerts, collaborative tools, intranet, digitalscreen and newsfeeds. Showcasing this set of slides titled IT Security Communication Plan To Assess Channel Effectiveness Themes PDF. The topics addressed in these templates are Denial Service, Phishing, Password Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Safety Initiatives Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this data safety initiatives summary existing security management capabilities topics pdf. Use them to share invaluable insights on key enablers, rating scale, incident occurrence identification, asset management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Analysis Plan With Threats And Solutions Infographics PDF
This slide contains the information related to the plan made for the security analysis of the organization and its clients. It also includes the solutions for treating the threats and vulnerabilities. Showcasing this set of slides titled IT Security Analysis Plan With Threats And Solutions Infographics PDF. The topics addressed in these templates are Risk, Applications, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Determine Focus Areas To Implement Security Operations Centre Diagrams PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. Deliver an awe inspiring pitch with this creative determine focus areas to implement security operations centre diagrams pdf bundle. Topics like digital forensics and control, risk monitoring and management, system and network administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

3 Key Areas For Document Management Security Controls Ideas PDF
This slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Persuade your audience using this 3 Key Areas For Document Management Security Controls Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cryptography, Practice Guidelines, Attestations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Role of Tokenization in Advancing Data Security PPT Example
Use this Role of Tokenization in Advancing Data Security PPT Example to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in eighty three slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

How Management Enables Effective Corporate Security Governance Graphics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. This modern and well-arranged How Management Enables Effective Corporate Security Governance Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Target Market Assessment For Facility Security Corporation Brochure PDF
This slide covers the target audience analysis of company with facility security services. It includes analysis details such as key demographics, psychographics, challenges, preferred channels, and preferred content type. Pitch your topic with ease and precision using this Target Market Assessment For Facility Security Corporation Brochure PDF. This layout presents information on Key Demographics, Preferred Content Types, Preferred Channels. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Budget Analysis For Effective Security Management At Workplace Demonstration PDF
Firm has prepared a budget for managing security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Budget Analysis For Effective Security Management At Workplace Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
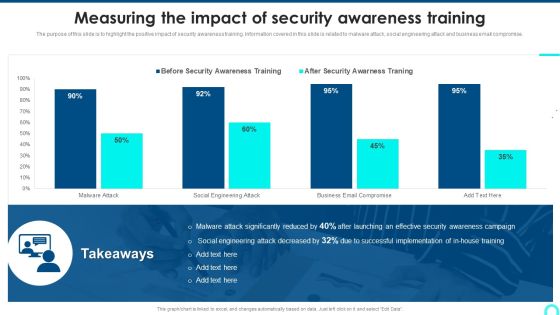
Measuring The Impact Of Security Awareness Training Structure PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Deliver and pitch your topic in the best possible manner with this Measuring The Impact Of Security Awareness Training Structure PDF. Use them to share invaluable insights on Attack Significantly, Awareness Campaign, Social Engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Scope For Security Camera Services One Pager Sample Example Document
This slide depicts the project scope providing information about the multiple activities to be performed by the bidding company for the client. Presenting you an exemplary Scope For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Security Camera Services One Pager Sample Example Document brilliant piece now.

Security Agency Business Profile Our Global Presence Themes PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. Presenting Security Agency Business Profile Our Global Presence Themes PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Developed Markets, Customers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Impact Of Cyber Security Breach Lost Revenue Portrait PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an awe inspiring pitch with this creative Impact Of Cyber Security Breach Lost Revenue Portrait PDF bundle. Topics like Social Engineering, Password Attack, Ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills

Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF
The purpose of this slide is to highlight the security gap analysis of the organization. Information covered in this slide is related to current vs desired state of the company, reasons identified, techniques to be used and the priority level.Deliver an awe inspiring pitch with this creative Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF bundle. Topics like Facing Ransomware, Reasons Identified, Organization Malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Qualitative Risk Analysis Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management. This is categorized as certain, likely, possible, unlikely, and rare. Pitch your topic with ease and precision using this Cyber Security Qualitative Risk Analysis Matrix Background PDF. This layout presents information on Risk Matrix, High Severity, Cyber Security Qualitative. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
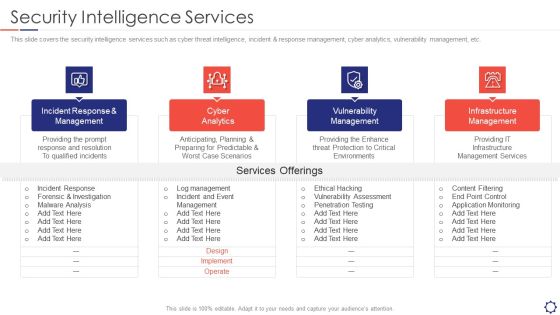
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
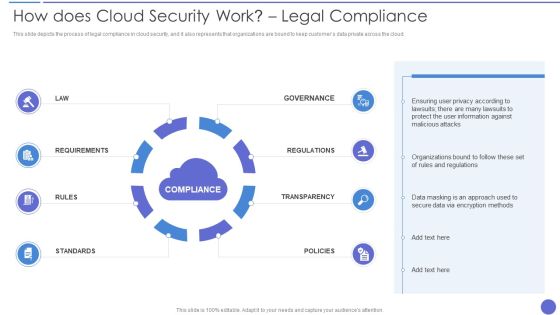
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Month IT Security Plan Timeline Pictures PDF
This slide 5 month cyber security strategy timeline illustrating product security, architecture security, people security, security compliance and resilience. Showcasing this set of slides titled 5 Month IT Security Plan Timeline Pictures PDF. The topics addressed in these templates are Architecture Security, People Security, Security Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
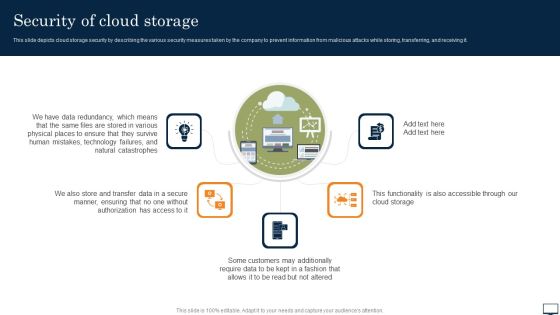
Security Of Cloud Storage Ppt PowerPoint Presentation File Styles PDF
This slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. Get a simple yet stunning designed Security Of Cloud Storage Ppt PowerPoint Presentation File Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Of Cloud Storage Ppt PowerPoint Presentation File Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
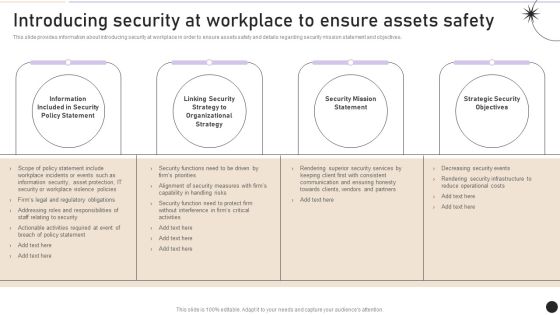
Introducing Security At Workplace To Ensure Assets Safety Graphics PDF
This slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introducing Security At Workplace To Ensure Assets Safety Graphics PDF can be your best option for delivering a presentation. Represent everything in detail using Introducing Security At Workplace To Ensure Assets Safety Graphics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Need For Cyber Security Awareness Training Ppt Gallery Template PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Welcome to our selection of the Need For Cyber Security Awareness Training Ppt Gallery Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
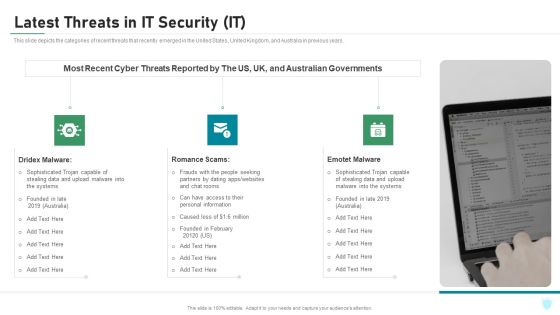
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Running Cyber Security Awareness Campaign For Employees Portrait PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. This modern and well-arranged Running Cyber Security Awareness Campaign For Employees Portrait PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Desktop Security Management Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting desktop security management assessment matrix of cyber risks infographics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like retail, systems, systems, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SDN Security Architecture Infrastructure Layer And Apis Professional PDF
This slide represents the infrastructure layer and Application programming interfaces of SDN architecture. The layer contains the physical switches and other devices that help redirect the network traffic, and APIs are used to interact between the three layers of the SDN architecture. Slidegeeks has constructed SDN Security Architecture Infrastructure Layer And Apis Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
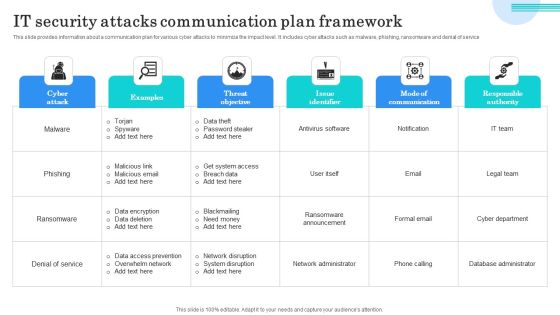
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Standard Compliances For Online Security Pictures PDF
This slide shows various standards that are established for digital safety and followed by organization to meet compliance regulations. It provides information for PCI DSS, SOC 2, NYDFS, NIST AND CCPA. Persuade your audience using this Major Standard Compliances For Online Security Pictures PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Digital Safety, Requirements For Financial, Regulate Risk Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

CYBER Security Breache Response Strategy Ppt PowerPoint Presentation Complete Deck
Whether it is for your individual use or business purpose, providing information in a clear format is often an added advantage, as this CYBER Security Breache Response Strategy Ppt PowerPoint Presentation Complete Deck does so wonderfully well. Incorporate this content-ready, versatile PowerPoint complete deck in sixty eight slides to significantly enhance your chances of success. It will help you talk about multiple components of business and be more efficient. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

Competitor Analysis Grid Of Security Software Inspiration PDF
This slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Pitch your topic with ease and precision using this Competitor Analysis Grid Of Security Software Inspiration PDF. This layout presents information on System Cleansing, Everyday Backup Option, Anti Spyware. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study 2 Banks Cyber Security Infrastructure Topics PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Presenting case study 2 banks cyber security infrastructure topics pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like implemented, integrated, our approach. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
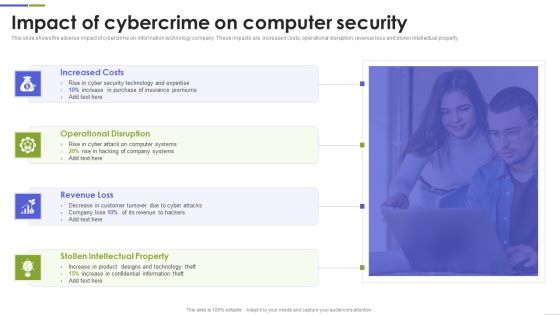
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. If you are looking for a format to display your unique thoughts, then the professionally designed Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
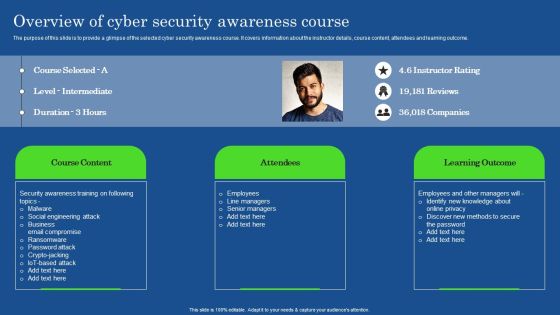
Overview Of Cyber Security Awareness Course Brochure PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Cyber Security Awareness Course Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Cyber Security Awareness Course Brochure PDF.
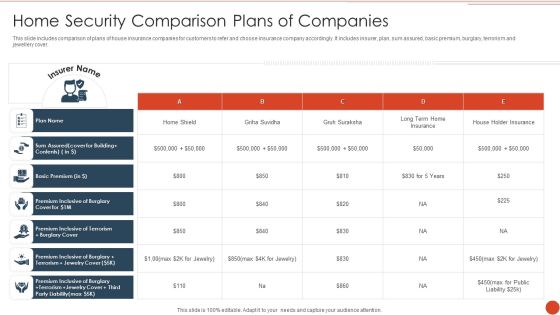
Home Security Comparison Plans Of Companies Formats PDF
This slide includes comparison of plans of house insurance companies for customers to refer and choose insurance company accordingly. It includes insurer, plan, sum assured, basic premium, burglary, terrorism and jewellery cover. Pitch your topic with ease and precision using this Home Security Comparison Plans Of Companies Formats PDF. This layout presents information on Basic Premium, Plan Name, House Holder Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Mobile Application Security Architecture For Clients Summary PDF
This slide represents the architecture designed to enable the mobile application safety to gain trust of clients. It includes details related to windows and web applications, smart card resource manager, Bluetooth smart card reader. Pitch your topic with ease and precision using this Mobile Application Security Architecture For Clients Summary PDF. This layout presents information on Windows Applications, Web Applications, Resource Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
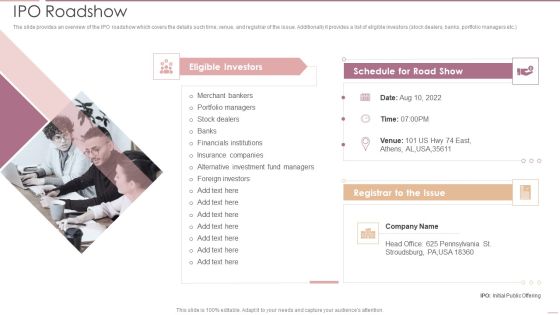
Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF
The slide provides an overview of the IPO roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc.Presenting Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Eligible Investors, Portfolio Managers, Alternative Investment In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Slidegeeks has constructed Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Investment Banking Security Underwriting Pitchbook Post IPO Plan Microsoft PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and selling, general, and administration expenses, operating income, and net income.Presenting Investment Banking Security Underwriting Pitchbook Post IPO Plan Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Market Capitalization, Fund Allocation, Business Expansion In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Phone Security Key Aspects For Growing Revenue Icons PDF
This slide shows every aspect of phone security model that should be considered while framing security policy for organization. It include aspects such as compliance security, product security and infrastructure security etc. Presenting Smart Phone Security Key Aspects For Growing Revenue Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Compliance Security, Product Security, Infrastructure Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Awareness Trends In 2022 Diagrams PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Presenting Cyber Security Awareness Trends In 2022 Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Malware Ransomware, Advanced Challenging, Malware Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Incident Response Process Flow Chart Download PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. This Cyber Security Incident Response Process Flow Chart Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF
The purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF can be your best option for delivering a presentation. Represent everything in detail using Organizing Security Awareness General Outlook Of Ransomware Attack Structure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Pricing Plan Of Security Awareness Packages Slides PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Pricing Plan Of Security Awareness Packages Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
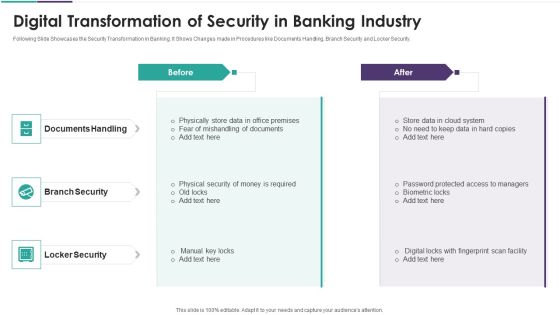
Digital Transformation Of Security In Banking Industry Elements PDF
Following Slide Showcases the Security Transformation in Banking. It Shows Changes made in Procedures like Documents Handling, Branch Security and Locker Security. Presenting digital transformation of security in banking industry elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including documents handling, branch security, locker security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Roles And Responsibilities Of Financial Security Team Sample PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Slidegeeks is here to make your presentations a breeze with Major Roles And Responsibilities Of Financial Security Team Sample PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
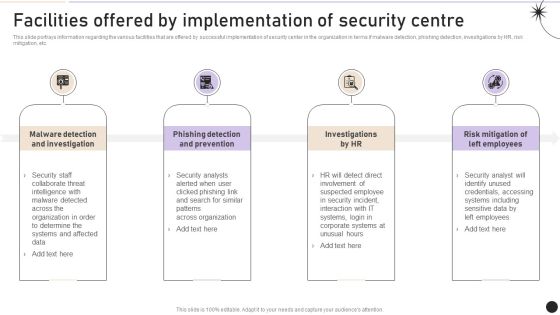
Facilities Offered By Implementation Of Security Centre Topics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Slidegeeks is here to make your presentations a breeze with Facilities Offered By Implementation Of Security Centre Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Levels Of Security Concerns In Cloud Network Download PDF
The slide showcases levels of security concerns that measure user and device authentication. The elements are virtual machine security , network security , interface security , privacy concerns etc. Presenting Levels Of Security Concerns In Cloud Network Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Virtual Machine Security, Interface Security, Network Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Analysis Icon With Magnifying Glass Introduction PDF
Presenting IT Security Analysis Icon With Magnifying Glass Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security Analysis Icon, Magnifying Glass. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Wall Virtual Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this security wall virtual ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
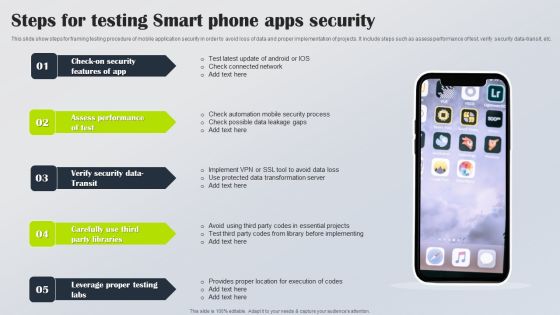
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Components Of Data Security Management Framework Pictures PDF
This slide showcases a framework highlighting key areas covered in data security governance to manage business information. It includes key components such as quality, knowledge, ownership, accessibility and security. Presenting Key Components Of Data Security Management Framework Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Ownership, Accessibility, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
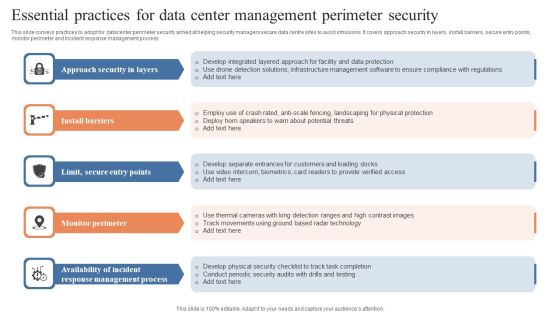
Essential Practices For Data Center Management Perimeter Security Guidelines PDF
This slide conveys practices to adopt for datacenter perimeter security aimed at helping security managers secure data centre sites to avoid intrusions. It covers approach security in layers, install barriers, secure entry points, monitor perimeter and incident response management process. Persuade your audience using this Essential Practices For Data Center Management Perimeter Security Guidelines PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Approach Security Layers, Install Barriers, Monitor Perimeter. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Road Traffic Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this road traffic security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
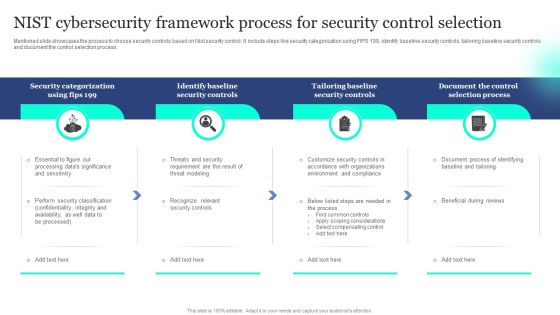
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Hacker Interview Schedule For New Professionals Portrait PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Interview Schedule For New Professionals Portrait PDF. Use them to share invaluable insights on Ethical Hacker, Security Consultant, Security Analyst and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
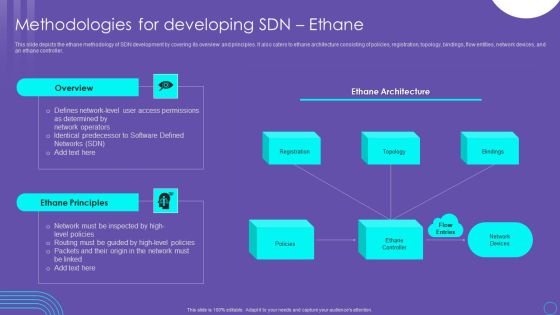
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Benefits Reaped Through Cloud Network Security Sample PDF
The slide showcases benefits of cloud security that continuously help monitor, identify, analyze and mitigate attacks. The elements are optimize security cost, automated security, response time , centralize security with easy management , reliability with easy access . Presenting Benefits Reaped Through Cloud Network Security Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Optimize Security Cost, Response Time, Future Considerations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
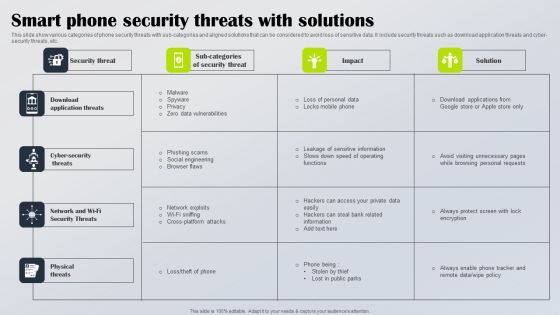
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Estimated Security Management Plan Critical Success Factors Infographics PDF
Deliver an awe inspiring pitch with this creative Estimated security management plan critical success factors infographics pdf bundle. Topics like security management, security incidents level, security implementation duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Common Data Security And Storage Environment Icon Ppt Inspiration PDF
Presenting Common Data Security And Storage Environment Icon Ppt Inspiration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Common Data, Security And Storage, Environment Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
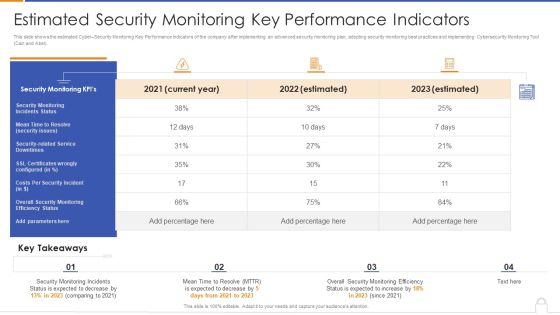
Estimated Security Monitoring Key Performance Indicators Diagrams PDF
Deliver and pitch your topic in the best possible manner with this estimated security monitoring key performance indicators diagrams pdf. Use them to share invaluable insights on security monitoring, security related service downtimes, overall security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
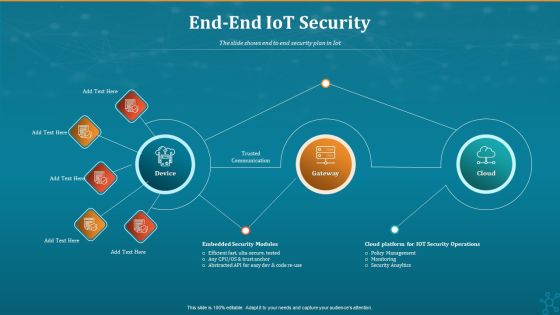
Machine To Machine Communication End End Iot Security Inspiration PDF
The slide shows end to end security plan in Iot.Deliver an awe-inspiring pitch with this creative machine to machine communication end end iot security inspiration pdf. bundle. Topics like trusted communication, gateway, embedded security modules, cloud platform for iot security operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current Security Monitoring Key Performance Indicators Formats PDF
Deliver and pitch your topic in the best possible manner with this current security monitoring key performance indicators formats pdf. Use them to share invaluable insights on security monitoring incidents, overall security monitoring, costs per security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
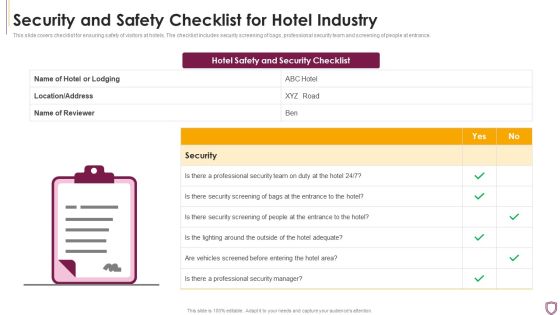
Security And Safety Checklist For Hotel Industry Summary PDF
This slide covers checklist for ensuring safety of visitors at hotels. The checklist includes security screening of bags, professional security team and screening of people at entrance.Showcasing this set of slides titled Security And Safety Checklist For Hotel Industry Summary PDF The topics addressed in these templates are Professional Security, Security Screening, Vehicles Screened All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Banking Security Technology PowerPoint Templates And PowerPoint Themes 1112
We present our Internet Banking Security Technology PowerPoint Templates And PowerPoint Themes 1112.Use our Money PowerPoint Templates because, Inform your team of your ideas using our illustrative slides. Use our Technology PowerPoint Templates because, Demonstrate how they contribute to the larger melting pot. Use our Signs PowerPoint Templates because, Now put it up there for all to see. Use our Finance PowerPoint Templates because, Anoint it with your really bright ideas. Use our Business PowerPoint Templates because,Now use this slide to bullet point your views.Use these PowerPoint slides for presentations relating to Internet banking, money, technology, signs, finance, business. The prominent colors used in the PowerPoint template are Blue, Pink, Black

Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Current Security Management Challenges The Company Is Facing Microsoft PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers. Deliver an awe inspiring pitch with this creative current security management challenges the company is facing microsoft pdf bundle. Topics like environments, security risk , information, design, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Data Encryption Security Management Technology Ideas PDF
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting Business Data Encryption Security Management Technology Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authentication, Privacy, Regulatory Compliance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
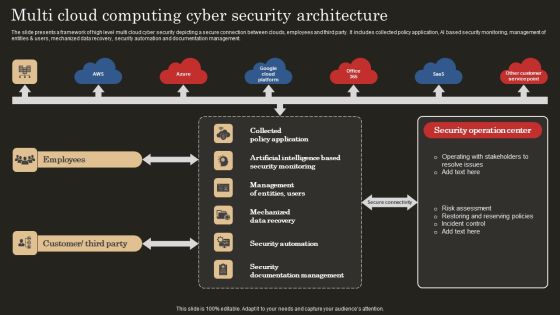
Multi Cloud Computing Cyber Security Architecture Microsoft PDF
The slide presents a framework of high level multi cloud cyber security depicting a secure connection between clouds, employees and third party. It includes collected policy application, AI based security monitoring, management of entities and users, mechanized data recovery, security automation and documentation management. Showcasing this set of slides titled Multi Cloud Computing Cyber Security Architecture Microsoft PDF. The topics addressed in these templates are Mechanized Data Recovery, Security Automation, Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Security Management Technology Framework Elements PDF
This slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Persuade your audience using this Cloud Computing Security Management Technology Framework Elements PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including User Access Management, Data Security, Hardware And Software, Network Security, Monitoring, Governance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Complete IT Security IT Implementation Checklist Ppt Diagrams PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Deliver an awe inspiring pitch with this creative complete it security it implementation checklist ppt diagrams pdf bundle. Topics like training, antivirus software, secure communications, access control measures, device security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
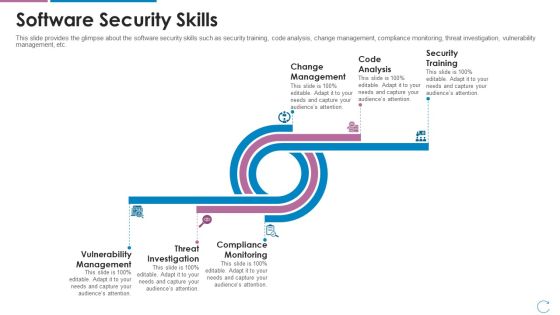
Devops Team Capabilities IT Software Security Skills Ppt Deck PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Deliver an awe inspiring pitch with this creative devops team capabilities it software security skills ppt deck pdf bundle. Topics like change management, code analysis, security training, vulnerability management, threat investigation, compliance monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Data IT Security Analysis Icon With Shield Download PDF
Presenting Business Data IT Security Analysis Icon With Shield Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Business Data IT Security, Analysis Icon With Shield. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Desktop Security Management Cont Ideas PDF
Deliver an awe inspiring pitch with this creative table of contents for desktop security management cont ideas pdf bundle. Topics like security implementation, security budget, dashboards, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Techniques For Digital Terrorism Icon Elements PDF
Persuade your audience using this Security Techniques For Digital Terrorism Icon Elements PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Digital Terrorism Icon, Security Techniques. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Breach Prevention Recognition Organization Cyber Security Dashboard Demonstration PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization cyber security dashboard demonstration pdf. Use them to share invaluable insights on cyber security, key performance, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

It Security Ppt PowerPoint Presentation Complete Deck With Slides
This is a . This is a one stage process it security ppt powerpoint presentation complete deck with slides. The stages in this process are it security, business, management, planning, strategy.
It Security Risk Management Ppt Powerpoint Presentation Outline Guidelines Cpb
This is a it security risk management ppt powerpoint presentation outline guidelines cpb. This is a five stage process. The stages in this process are it security risk management.

Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Detection And Prevention Of Management Security Controls Structure PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Create an editable Detection And Prevention Of Management Security Controls Structure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Detection And Prevention Of Management Security Controls Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Measuring Security Awareness Campaign Results With Kpis Template PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self reported incidents, security breaches, cost of security breach and campaign participation rateDeliver an awe inspiring pitch with this creative Measuring Security Awareness Campaign Results With Kpis Template PDF bundle. Topics like Security Breaches, Cost Of Security, Campaign Participation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mobile Application Security Management Technology Icon Structure PDF
Presenting Mobile Application Security Management Technology Icon Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Mobile Application Security, Management Technology Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Latest Trends For Mobile Smart Phone Security Icons PDF
This slide shows current trends for securing mobile phone against potential cyber attacks and loss of sensitive data. It include trends such as rise in security automation, increasing threat modelling and SAST-DAST integration etc qPresenting Latest Trends For Mobile Smart Phone Security Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increasing Security, SAST DAST Integration, Increasing Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Business Driven Security Architecture Introduction PDF
The slide shows a security framework of business driven services. It highlight cloud computing services such as SaaS, PaaS and IaaS and security services such as data security management, software and service assertion, technical service control, risk management infrastructure management, etc. Showcasing this set of slides titled Cloud Computing Business Driven Security Architecture Introduction PDF. The topics addressed in these templates are Strategies, Delegation Authority, Service Goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF
Showcasing this set of slides titled Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF. The topics addressed in these templates are Data Warehouse, Security Mechanism, Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Users Password IT Security Analysis Dashboard Elements PDF
This slide displays the analysis of the users password security in an organization to make sure that the users confidential details are safe. It includes security gains, password evaluation, active users data, activities of password, etc. Showcasing this set of slides titled Users Password IT Security Analysis Dashboard Elements PDF. The topics addressed in these templates are Password Evaluation Score, Security Gains. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
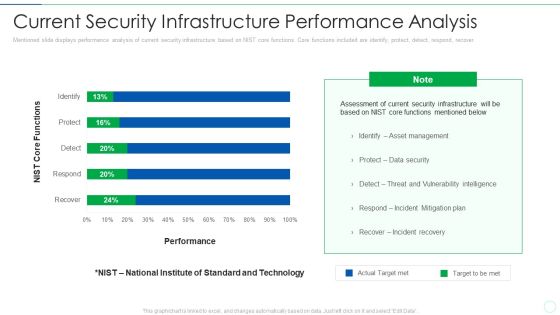
Effective IT Risk Management Process Current Security Infrastructure Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative effective it risk management process current security infrastructure clipart pdf bundle. Topics like asset management, data security, plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home