Information Security Ppt

Developing IT Security Strategy Analysing The Impact On Assets Due To Information Breach Sample PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Analysing The Impact On Assets Due To Information Breach Sample PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Information And Technology Security Operations Analysing Various Threats Faced By Firm Microsoft PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative information and technology security operations analysing various threats faced by firm microsoft pdf bundle. Topics like threats, negligent, occurrence, compromised, malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
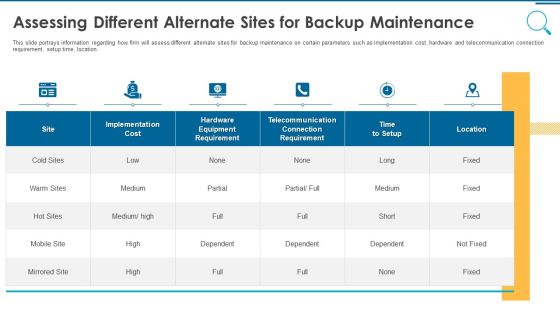
Information And Technology Security Operations Assessing Different Alternate Sites For Backup Maintenance Rules PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this information and technology security operations assessing different alternate sites for backup maintenance rules pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.This is a Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Encrypted Data, Sensitive Information You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
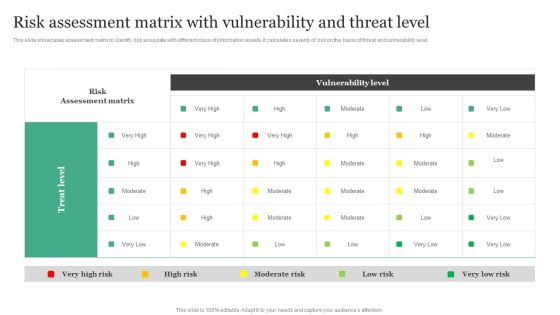
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF. Use them to share invaluable insights on Vulnerability Severity, Unprotected Storage, Unprotected Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Secops Staff Training Plan With Cost Introduction PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative information and technology security operations secops staff training plan with cost introduction pdf bundle. Topics like management, vulnerability, business, training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Selecting Data Centre Management Solution Workplace Security Management Program Information PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Selecting Data Centre Management Solution Workplace Security Management Program Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Security Agency Business Profile Additional Security Services Download PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. This is a Security Agency Business Profile Additional Security Services Download PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Safety Escort Service, Executive Protection, Special Event Security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF. Use them to share invaluable insights on Unpatched Servers, Attacks Including, Awareness Trainings and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Threat Management Action Plan Level Information PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
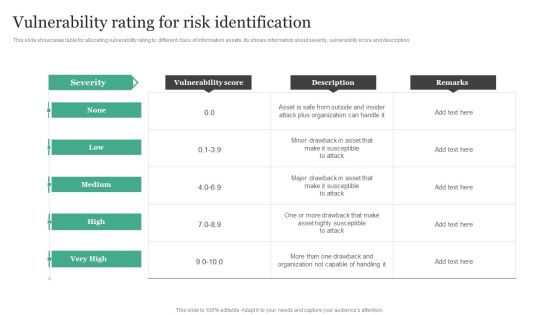
Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF
Retrieve professionally designed Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating. This modern and well-arranged Developing IT Security Strategy Assigning Criticality Rating To Information Assets Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Slidegeeks has constructed Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Desktop Security Management Best Practices For Cloud Security Topics PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. This is a desktop security management best practices for cloud security topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, management, measures, planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Checklist Networking Formats PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks.This is a Cloud Security Assessment Cloud Security Checklist Networking Formats PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gateway To Protect, Injecting Malicious, Precautions To Protect You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How To Manage Cloud Security Inspiration PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures.This is a Cloud Security Assessment How To Manage Cloud Security Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compliance Is Effective, Business Procedures, Manage Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system.This is a Cloud Security Assessment What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Convenience Over, Accessed Remotely, Threats Of Accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How Does Cloud Security Work Formats PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Security Assessment How Does Cloud Security Work Formats PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Information Against, Transparency, Regulations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.This is a Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Administrative Rights, Privileged Credentials, Legitimate Users You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Presenting Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Visibility And Consistency, Network Security, Identity Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Complete Computer Security Implementation Checklist Demonstration PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting desktop security management complete computer security implementation checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, organizations, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Security Framework In Cloud Computing Demonstration PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a desktop security management security framework in cloud computing demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, detect, respond, recover, identify. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Main Steps Of Operational Security Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting desktop security management main steps of operational security inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, determine, analyze, systems, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions.Presenting Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Categorization Of Services, Access Control, Data Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Security Patches And Updates Summary PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting Cloud Security Checklist Security Patches And Updates Summary PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security Patches, Measures, Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment What Is Cloud Security Elements PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers.Presenting Cloud Security Assessment What Is Cloud Security Elements PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Computing Systems, Business Coherence, Parties Involved. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs.Presenting Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Compliance Violations, Access Control, Daniel Of Service In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on.Presenting Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Compliance Violations In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. This is a Risk Management Model For Data Security Roles And Responsibilities For Managing Information Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Role, Position, Responsibility, Chief Information Officer, Information Management Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Technology Team Data Security And Communication Plan Icon Graphics PDF
Presenting Information Technology Team Data Security And Communication Plan Icon Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Technology, Team Data Security, Communication Plan Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Device Icon To Improve Information Technology Security Communication Plan Infographics PDF
Presenting Digital Device Icon To Improve Information Technology Security Communication Plan Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Digital Device Icon, Improve Information Technology, Security Communication Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
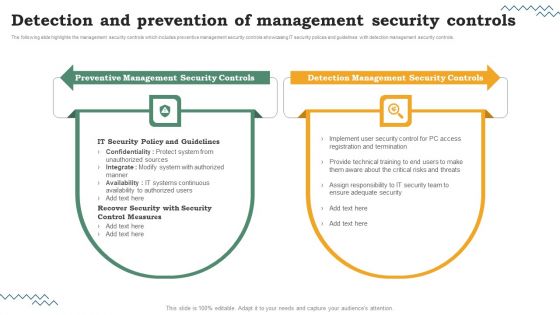
Risk Evaluation Of Information Technology Systems Detection And Prevention Of Management Security Controls Microsoft PDF
Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Risk Evaluation Of Information Technology Systems The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Detection And Prevention Of Management Security Controls Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Risk Evaluation Of Information Technology Systems Detection And Prevention Of Management Security Controls Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
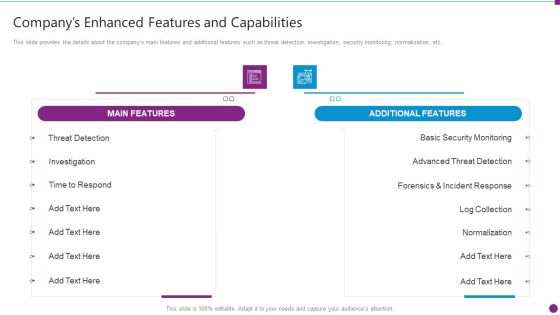
Security Information And Event Management Strategies For Financial Audit And Compliance Companys Enhanced Features Portrait PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance companys enhanced features portrait pdf bundle. Topics like main features, additional features, security monitoring, advanced threat detection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Scorecard Information Security Risk Rating Scorecard With Customer Order Slides PDF
This is a cybersecurity risk scorecard information security risk rating scorecard with customer order slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security risk rating scorecard with customer order. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
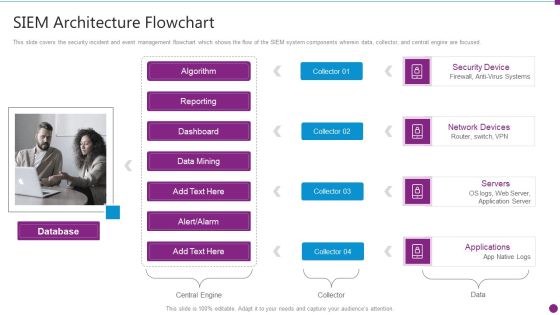
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Flowchart Microsoft PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a security information and event management strategies for financial audit and compliance siem architecture flowchart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda Of Security Information And Event Management Strategies For Financial Audit And Compliance Infographics PDF
This is a agenda of security information and event management strategies for financial audit and compliance infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like customers, security intelligence, log management and compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Convergence Strategy Information Two Way Interactions Between Safety Security Rules PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment. Presenting Convergence Strategy Information Two Way Interactions Between Safety Security Rules PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Servers, Engineer Station, Cyber Intelligence Center, Cyber Intelligence Station. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Technology Security Operations Prerequisites For Effective Secops Implementation Designs PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a information and technology security operations prerequisites for effective secops implementation designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
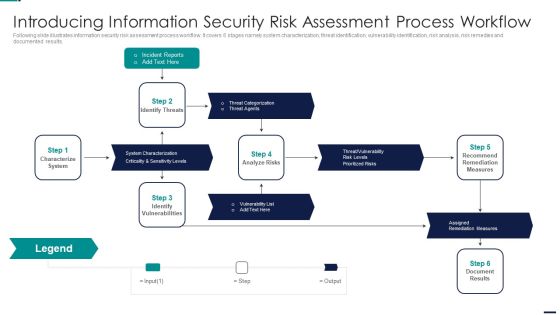
Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
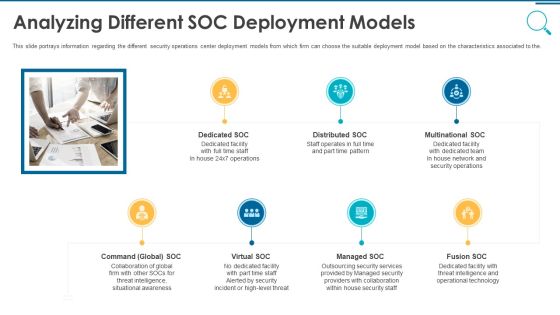
Information And Technology Security Operations Analyzing Different SOC Deployment Models Rules PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a information and technology security operations analyzing different soc deployment models rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information Running Cyber Security Awareness Campaign For Employees Brochure PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Create an editable Prevention Of Information Running Cyber Security Awareness Campaign For Employees Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Prevention Of Information Running Cyber Security Awareness Campaign For Employees Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF
This is a Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Bestinformation Technology Security And Data Security Practices Slides PDF
The following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi-layer authentication etc. Persuade your audience using this Bestinformation Technology Security And Data Security Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Adopt Strong Password Policy, Make Regular Backups, Resource Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Software Engineering Technology, Network Security, Telecommunications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

30 60 90 Days Plan To Implement Cloud Security In Business Information PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 Days Plan To Implement Cloud Security In Business Information PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze, Cloud Services Provided , Control Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF
Find highly impressive Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Security Operations Icon To Prevent Security Breaches Ideas PDF
Persuade your audience using this Security Operations Icon To Prevent Security Breaches Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Icon, Prevent Security Breaches. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Get a simple yet stunning designed Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Strategies We Will Implement To Make Security Awareness Ideas PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

IT Policies And Procedures Information Security Policy For Employees Download PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Policies And Procedures Information Security Policy For Employees Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Policies And Procedures Information Security Policy For Employees Download PDF.

Security Information And Event Management Strategies For Financial Audit And Compliance Table Of Contents Diagrams PDF
This is a security information and event management strategies for financial audit and compliance table of contents diagrams pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like company overview, challenges and solutions, services offered, features and benefits, siem architecture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Prevention Of Information Key Benefits Of Cyber Security Awareness Training Inspiration PDF

 Home
Home