AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Information Security Ppt
Information Security Ppt

Organizing Security Awareness Tracking Sheet To Monitor The Performance Of Employees Elements PDF
Get a simple yet stunning designed Organizing Security Awareness Tracking Sheet To Monitor The Performance Of Employees Elements PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Organizing Security Awareness Tracking Sheet To Monitor The Performance Of Employees Elements PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
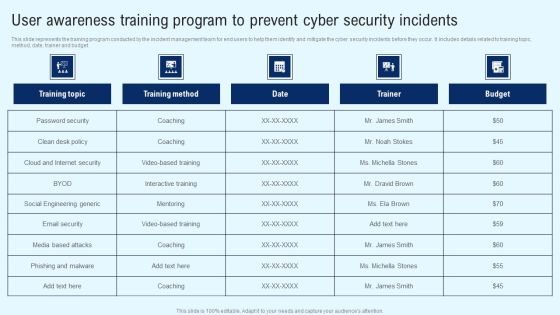
Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cyber Physical System To Enhance Cps Security And Privacy Life Cycle Portrait PDF
This slide depicts the cyber-physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cyber Physical System To Enhance Cps Security And Privacy Life Cycle Portrait PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cyber Physical System To Enhance Cps Security And Privacy Life Cycle Portrait PDF today and make your presentation stand out from the rest.

Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF Use them to share invaluable insights on Authentication Process, Access Standards, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF today and make your presentation stand out from the rest.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Checklist For Work From Home Data Security Improving Cybersecurity With Incident Structure PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Work From Home Data Security Improving Cybersecurity With Incident Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Security Control Techniques For Real Estate Project Construction Site Safety Department Objectives Structure PDF
This Security Control Techniques For Real Estate Project Construction Site Safety Department Objectives Structure PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Control Techniques For Real Estate Project Construction Site Safety Department Objectives Structure PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, donot wait, grab the presentation templates today

Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Want to ace your presentation in front of a live audience Our Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Intelligent Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Weekly Timeline With Task Name Hacking Prevention Awareness Training For IT Security Download PDF
Deliver an awe inspiring pitch with this creative weekly timeline with task name hacking prevention awareness training for it security download pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF. Use them to share invaluable insights on Threat Encountered, Risk Level, Mitigation Plan, Resources Required and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
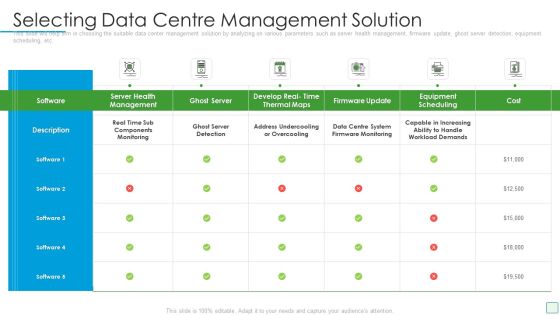
Developing Firm Security Strategy Plan Selecting Data Centre Management Solution Pictures PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan selecting data centre management solution pictures pdf. Use them to share invaluable insights on monitoring, management, develop, ghost server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF. Use them to share invaluable insights on Impact Rating On Business, Criticality Rating, Failure Cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
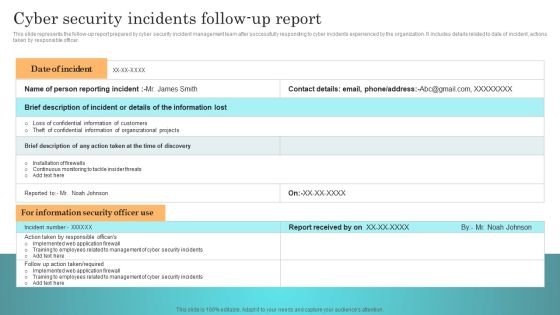
Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. The Incident Response Techniques Deployement Cyber Security Incidents Follow Up Report Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
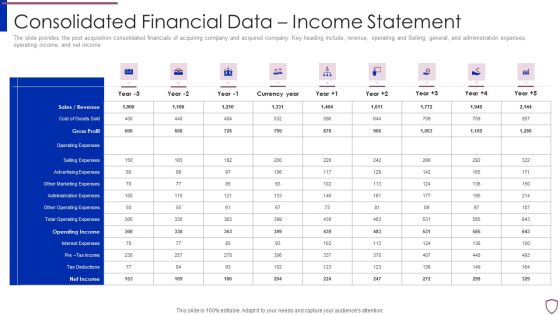
Financing Catalogue For Security Underwriting Agreement Consolidated Financial Data Income Statement Template PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and Selling, general, and administration expenses, operating income, and net income. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement consolidated financial data income statement template pdf. Use them to share invaluable insights on sales or revenue, cost of goods sold, gross profit, operating expenses, selling expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
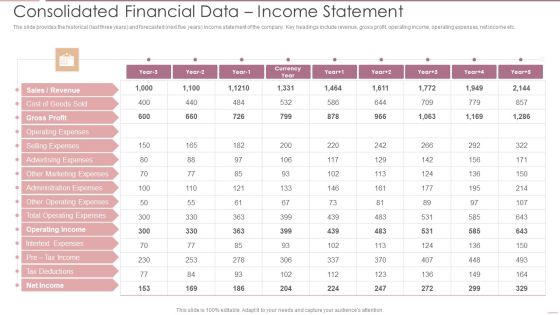
Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF
The slide provides the historical last three years and forecasted next five years income statement of the company. Key headings include revenue, gross profit, operating income, operating expenses, net income etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF Use them to share invaluable insights on Gross Profit, Operating Expenses, Advertising Expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Comparative Assessment Of Various Threat Agents Slides PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management comparative assessment of various threat agents slides pdf. Use them to share invaluable insights on comparative assessment of various threat agents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives Eliminating Manual Security Processes Through Automation Topics PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a data safety initiatives eliminating manual security processes through automation topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like manual vulnerability, scanning and resolution, vulnerability scanning, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF
This slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
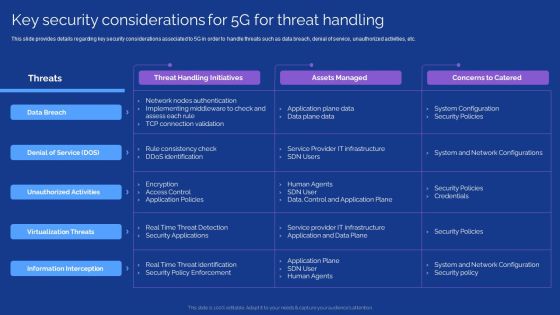
Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. This modern and well arranged Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Major Reasons For Poor Security Management In The Company Professional PDF
Deliver and pitch your topic in the best possible manner with this Major reasons for poor security management in the company professional pdf. Use them to share invaluable insights on evolving software, lack of recovery, improper protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Major Reasons For Poor Security Management In The Company Rules PDF
Deliver and pitch your topic in the best possible manner with this major reasons for poor security management in the company rules pdf. Use them to share invaluable insights on outdated software, lack of proper protection, lack of recovery and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
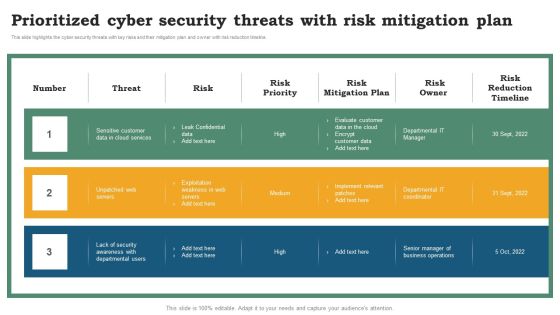
Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Explore a selection of the finest Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Developing Firm Security Strategy Plan Weekly Timeline With Task Name Clipart PDF
Deliver an awe inspiring pitch with this creative developing firm security strategy plan weekly timeline with task name clipart pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF

Cloud Intelligence Framework For Application Consumption Case Study 2 Banks Cyber Security Infrastructure Microsoft PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges. This is a cloud intelligence framework for application consumption case study 2 banks cyber security infrastructure microsoft pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process workflows, industry standard security metrics, implemented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF
This slide covers objectives challenges catalysts and benefits of the security in IT or OT convergence and reduce systems cyberattack surface. This is a Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Problem Faced By The Organization Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a problem faced by the organization hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, cybersecurity, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Home Security Solutions Company Profile Business Development Strategy Elements PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings. This is a Smart Home Security Solutions Company Profile Business Development Strategy Elements PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Multifamily Professional, Channels Instore Lead, Generation Provide Demo, Customer Target Builders. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
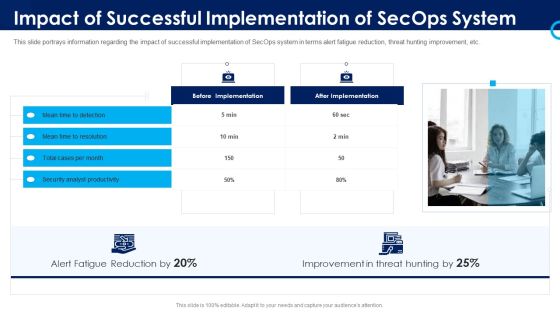
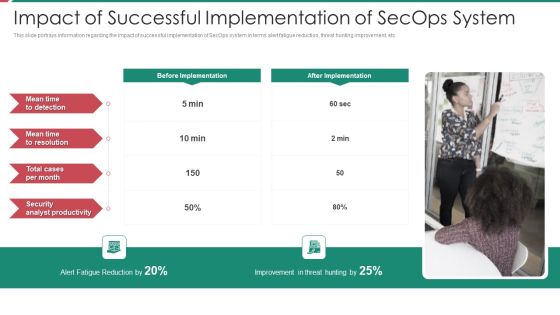
Organizational Security Solutions Impact Of Successful Implementation Of Secops System Designs PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting organizational security solutions impact of successful implementation of secops system designs pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security And Process Integration Impact Of Successful Implementation Of Secops System Diagrams PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting security and process integration impact of successful implementation of secops system diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
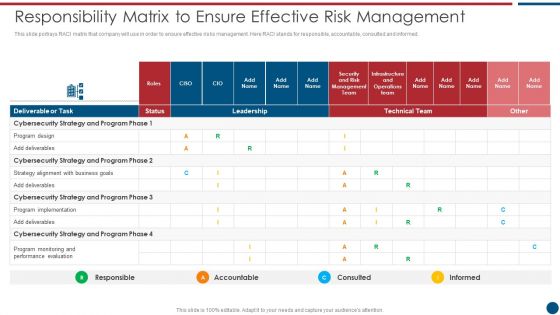
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

New Website Launch Strategy Website Security Management Action Plan Portrait PDF
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Slidegeeks is here to make your presentations a breeze with New Website Launch Strategy Website Security Management Action Plan Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Retrieve professionally designed Organizations Risk Management And IT Security Technical Security Control Model With Supporting Function Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
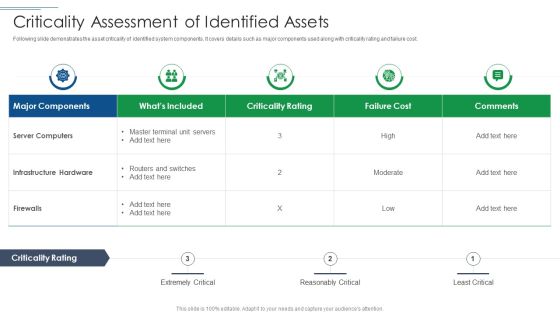
IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF bundle. Topics like Server Computers, Infrastructure Hardware, Failure Cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security And Performance Digital Marketing Interestbased And Safety Net Of Prospecting Diagrams PDF
This template depicts that majority of prospective audiences are lookalikes. If any target customer falls between the gap of the sales funnel, then they will be captured in the broad interest based audience. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Interestbased And Safety Net Of Prospecting Diagrams PDF. Use them to share invaluable insights on Browsing Information, Purchasing Devices, Prospective Audiences and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
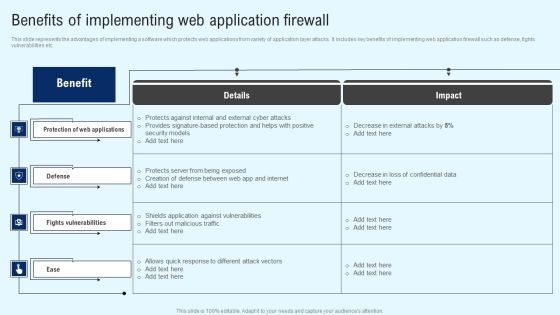
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Physical System To Enhance Steps For Cps Security Strategy Plan Elements PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Physical System To Enhance Steps For Cps Security Strategy Plan Elements PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Developing Firm Security Strategy Plan Elevating Brand Protection Strategy Mockup PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. This is a developing firm security strategy plan elevating brand protection strategy mockup pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like overt security features, covert security features, serialization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Slidegeeks has constructed Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Information Technology Consulting And Support Needs Ppt Powerpoint Templates
This is a information technology consulting and support needs ppt powerpoint templates. This is a nine stage process. The stages in this process are it outsourcing, project management, it strategic planning, problem resolution, business process, it assessment, security, help desk, network, services.

Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
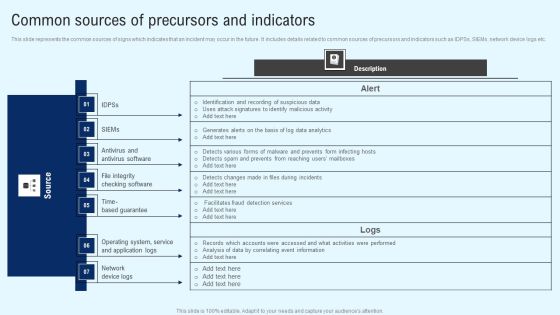
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF
This template covers guidelines to build ad sets and ad placements for Facebook, Instagram, messenger and audience network etc. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Building Ad Sets And Ads Placements Professional PDF. Use them to share invaluable insights on Column Marketplace, Presented Various, Choose Particular and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
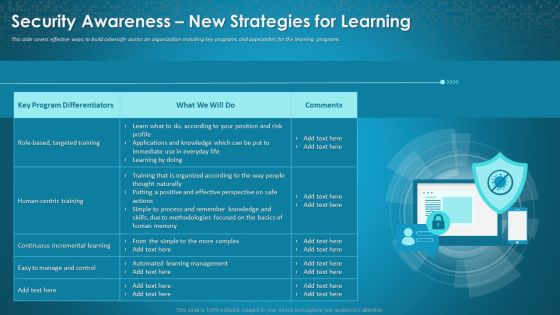
Organizational Network Staff Learning Security Awareness New Strategies For Learning Rules PDF
This slide cover effective way to build cybersafe across on organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness new strategies for learning rules pdf bundle. Topics like human centric training, manage and control, targeted training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
