Information Security Gap Analysis

IT Security Hardware And Software Update In Company Ppt Infographics Ideas PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a it security hardware and software update in company ppt infographics ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, security, operating systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF bundle. Topics like Organizational System, Security Analysts, Collaborate With Operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
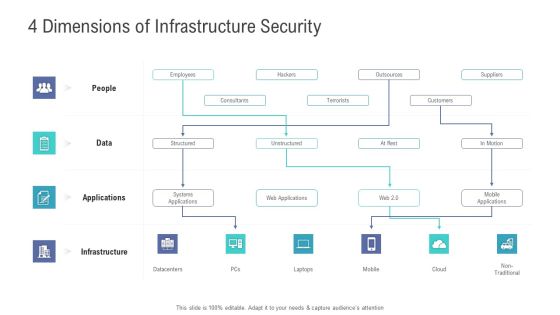
Financial Functional Assessment 4 Dimensions Of Infrastructure Security Ppt Professional Ideas PDF
This is a financial functional assessment 4 dimensions of infrastructure security ppt professional ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, applications, data, people. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF
The flowing slide highlights managed security service framework. It provides information about components such as clients issues and key operations to be performed by service provider such as antivirus offerings, data loss prevention etc. Presenting Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Framework Significance, Business Security Users, Major Bottlenecks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
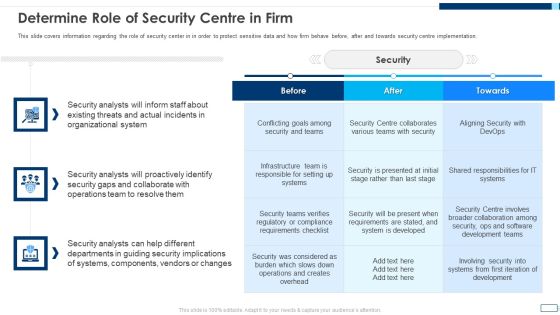
Evolving BI Infrastructure Determine Role Of Security Centre In Firm Summary PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative evolving bi infrastructure determine role of security centre in firm summary pdf bundle. Topics like organizational, security analysts, collaborate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
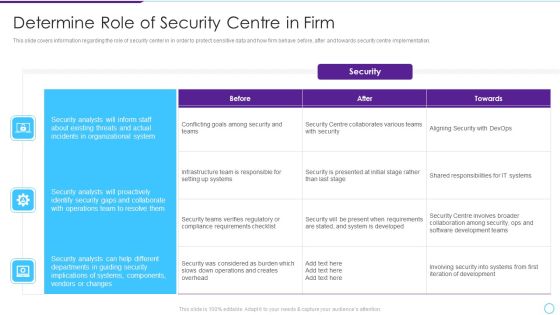
Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF bundle. Topics like Security, Organizational System, Operations Team, Conflicting Goals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
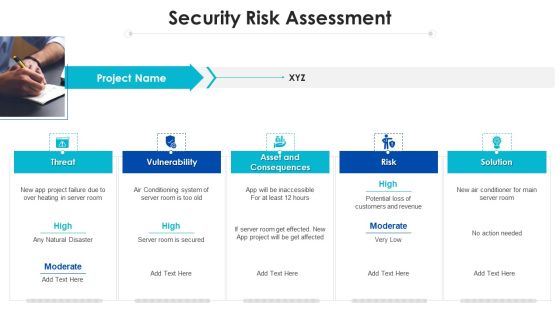
Project Assessment Templates Bundle Security Risk Assessment Ppt Infographic Template Guide PDF
This is a Project Assessment Templates Bundle Security Risk Assessment Ppt Infographic Template Guide PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Threat, Asset Consequences, Risk Solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Various Food Quality Management Tools Food Security Excellence Ppt Inspiration Example PDF
This slide provides information regarding various quality tools that can be used by firm in checking food and process quality such as scatter diagrams, histogram, process flow charts, pareto charts. This is a addressing various food quality management tools food security excellence ppt inspiration example pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like scatter diagrams, histogram, process flow charts, pareto chart. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF
This slide shows timeline depicting insider threat user logs. It contains information about archived activities, user event, policy violation trigger, capture continuation, etc. Pitch your topic with ease and precision using this Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF. This layout presents information on User Event, Policy Violation Trigger, Archived Logs. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF
The following slide outlines a comprehensive training plan for managed security service and awareness for employees. It provides information about the training subject, trainer name, training hours, status and learning outcome. Pitch your topic with ease and precision using this Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF. This layout presents information on Training Plan, Managed Cyber Security, Solutions Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
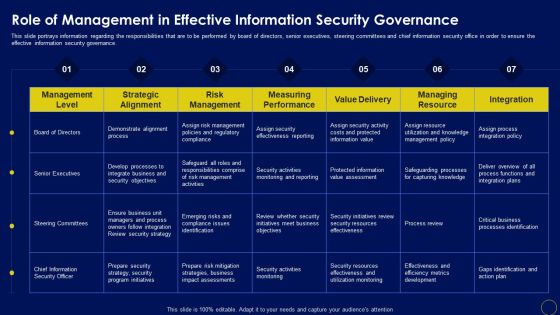
Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Guards In Music Concert For People Safety Ppt PowerPoint Presentation Outline Guide PDF
Pitch your topic with ease and precision using this security guards in music concert for people safety ppt powerpoint presentation outline guide pdf. This layout presents information on security guards in music concert for people safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF
Pitch your topic with ease and precision using this Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF. This layout presents information on Virus Cyber Security, Attack Warning, Web Browser Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Security Problem And Threat Management Ppt PowerPoint Presentation Model Gridlines PDF
Pitch your topic with ease and precision using this business security problem and threat management ppt powerpoint presentation model gridlines pdf. This layout presents information on business security problem and threat management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Guard On Surveillance Duty At Mall Ppt PowerPoint Presentation Summary Introduction PDF
Pitch your topic with ease and precision using this security guard on surveillance duty at mall ppt powerpoint presentation summary introduction pdf. This layout presents information on security guard on surveillance duty at mall. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Feature In Internet Modem Vector Icon Ppt PowerPoint Presentation File Professional PDF
Pitch your topic with ease and precision using this security feature in internet modem vector icon ppt powerpoint presentation file professional pdf. This layout presents information on security feature in internet modem vector icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
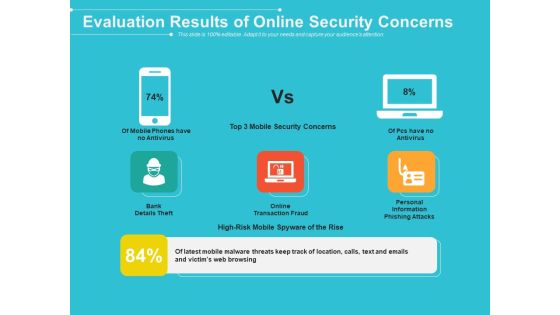
Evaluation Results Of Online Security Concerns Ppt PowerPoint Presentation File Summary PDF
Pitch your topic with ease and precision using this evaluation results of online security concerns ppt powerpoint presentation file summary pdf. This layout presents information on evaluation results of online security concerns. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
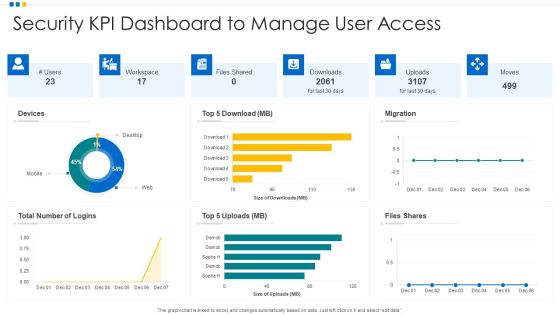
Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF
Pitch your topic with ease and precision using this Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF. This layout presents information on Devices, Security KPI Dashboard, Workspace. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Upgrading Total Project Safety IT Determine Role Of Security Centre To Ensure Project Safety Download PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative upgrading total project safety it determine role of security centre to ensure project safety download pdf bundle. Topics like before security, after security, towards security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Hardware And Software Update In Company Portrait PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a desktop security management hardware and software update in company portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, servers, devices, network, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Table Of Contents Structure PDF
Presenting techniques and strategies to reduce security management risks table of contents structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF Use them to share invaluable insights on Assessing Information Security, Safeguarding Valuable, Vulnerability Intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

30 60 90 Days Plan To Implement Cloud Security In Business Formats PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval.This is a 30 60 90 Days Plan To Implement Cloud Security In Business Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze Different, Provided By Vendors, Categorized Data You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Our Organization SIEM Log Flow Topics PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a real time assessment of security threats our organization siem log flow topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF
This This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting 6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prioritize, Evaluate, Analyse, Treat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF
This slide covers cyber security incident response KPI dashboard. It involves details such as intent alarm, event trend sources, event trend, sensor activity, major operating systems and asset information. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF. This layout presents information on Top Alarms Method, Alarms Intent, Timely Event Trend. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Security Solutions Various Metrics To Measure Secops System Performance Portrait PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting organizational security solutions various metrics to measure secops system performance portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
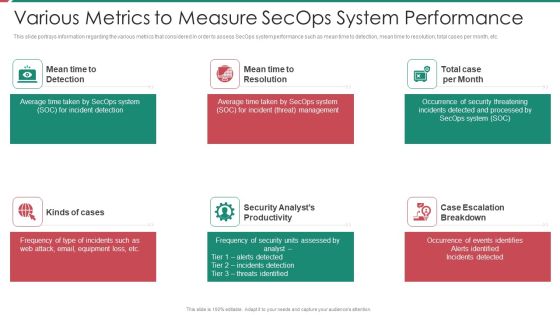
Security And Process Integration Various Metrics To Measure Secops System Performance Introduction PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting security and process integration various metrics to measure secops system performance introduction pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Enhanced Protection Corporate Event Administration Determine Focus Areas To Implement Security Operations Centre Icons PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a enhanced protection corporate event administration determine focus areas to implement security operations centre icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
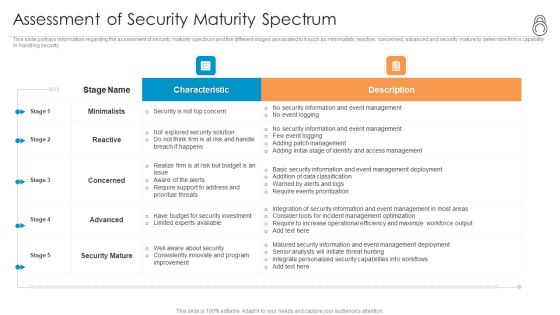
Enhanced Protection Corporate Event Administration Assessment Of Security Maturity Spectrum Background PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration assessment of security maturity spectrum background pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Security Risk Assessment Report For Business Ppt PowerPoint Presentation Gallery Graphics Example PDF
Pitch your topic with ease and precision using this internet security risk assessment report for business ppt powerpoint presentation gallery graphics example pdf. This layout presents information on process, unit, risk level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Internet Security Risk Assessment Report With Vulnerability And Impact Ppt PowerPoint Presentation Icon Backgrounds PDF
Pitch your topic with ease and precision using this internet security risk assessment report with vulnerability and impact ppt powerpoint presentation icon backgrounds pdf. This layout presents information on vulnerability, asset, impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Internet Security Threat Management For People Process And Technology Ppt PowerPoint Presentation File Inspiration PDF
Pitch your topic with ease and precision using this business internet security threat management for people process and technology ppt powerpoint presentation file inspiration pdf. This layout presents information on people, process, technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Pre And Post Process Results Of Cyber Security Process Changes Sample PDF
This slide shows reduction in threats percentage after adopting cyber security. It includes computer virus, data breach, DOS and phishing. Pitch your topic with ease and precision using this Pre And Post Process Results Of Cyber Security Process Changes Sample PDF. This layout presents information on Process Results, Process Changes, Key Insights. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
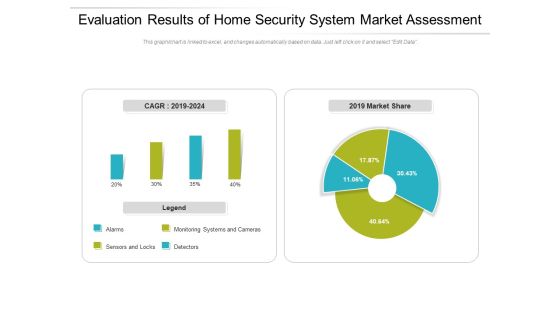
Evaluation Results Of Home Security System Market Assessment Ppt PowerPoint Presentation Gallery Deck PDF
Pitch your topic with ease and precision using this evaluation results of home security system market assessment ppt powerpoint presentation gallery deck pdf. This layout presents information on monitoring, market, detectors. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Assessment Of Security Problem Management Tools Ppt Model Influencers PDF
Pitch your topic with ease and precision using this Comparative Assessment Of Security Problem Management Tools Ppt Model Influencers PDF. This layout presents information on Customized Workflows, Threat Intelligence Integration, Real Time Alerts. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Intelligence With Data Governance And Security Ppt PowerPoint Presentation Infographics Example PDF
Pitch your topic with ease and precision using this business intelligence with data governance and security ppt powerpoint presentation infographics example pdf. This layout presents information on data governance, data discovery, data quality management, connected clouds, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Big Data Security Model With Identity And Access Management Ppt PowerPoint Presentation Inspiration Good PDF
Pitch your topic with ease and precision using this big data security model with identity and access management ppt powerpoint presentation inspiration good pdf. This layout presents information on identity and access management, data protection and privacy, infrastructure security and integrity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
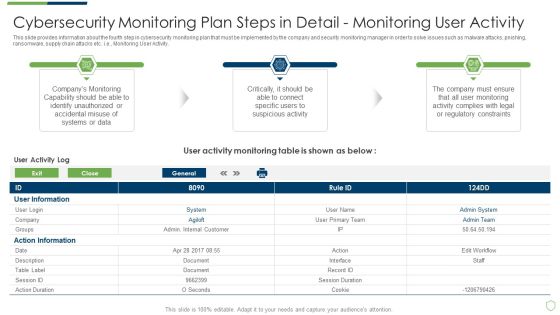
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
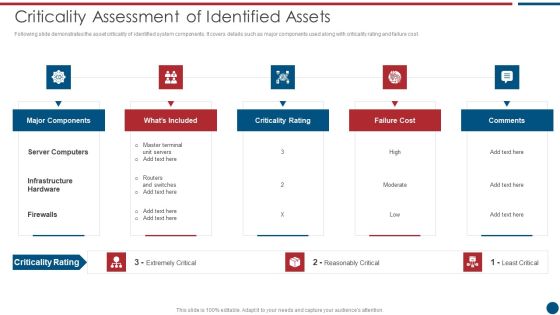
Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

United States Marine Officers Port Security Officers On Patrol 01 Ppt PowerPoint Presentation Model Good PDF
Pitch your topic with ease and precision using this united states marine officers port security officers on patrol 01 ppt powerpoint presentation model good pdf. This layout presents information on united states marine officers port security officers on patrol 01. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
United States Marine Officers Security Escort Holding Weapon On Boat Ppt PowerPoint Presentation Outline Icon PDF
Pitch your topic with ease and precision using this united states marine officers security escort holding weapon on boat ppt powerpoint presentation outline icon pdf. This layout presents information on united states marine officers security escort holding weapon on boat. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Enhanced Protection Corporate Event Administration Determine Security Risks Dashboard Summary PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration determine security risks dashboard summary pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF bundle. Topics like Information Interception, Virtualization Threats, Denial Of Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Risk Assessment Matrix With Severity And Likelihood Portrait PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. This is a developing firm security strategy plan risk assessment matrix with severity and likelihood portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment matrix with severity and likelihood. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
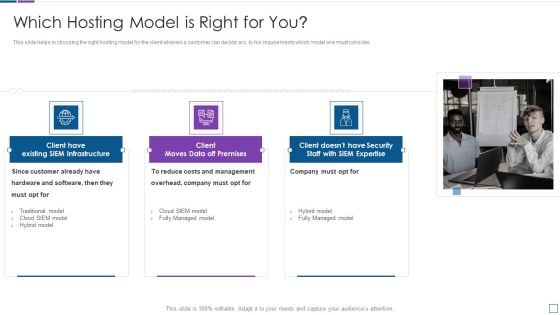
Real Time Assessment Of Security Threats Which Hosting Model Is Right For You Clipart PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. This is a real time assessment of security threats which hosting model is right for you clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs and management, company, hardware and software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
 Home
Home