Information Security Gap Analysis
Playbook For Content Advertising Interest Based And Safety Net Of Prospecting Icons PDF
This template depicts that majority of prospective audiences are lookalikes. If any target customer falls between the gap of the sales funnel, then they will be captured in the broad interest-based audience. Deliver and pitch your topic in the best possible manner with this Playbook For Content Advertising Interest Based And Safety Net Of Prospecting Icons PDF. Use them to share invaluable insights on Target Audience, Purchasing Devices, Shopping Behavior and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Infographics Option Banner With Umbrella Powerpoint Templates
Who doesn?t want to have a secure life? Be it financial security, safety of your child or safe environment at home and at work place. Well we hope for that but we can definitely save you from making ugly PowerPoint presentations. Above is the slide which is of umbrella with four options and along with it are four icons. This slide is one of our most downloaded PowerPoint slides and can be used to depict safety and security of any kind. The umbrella here can be used to indicate the safety, security, protection so you can choose this slide to show why it is safe to be associated with your company, or with your business, with your school, how your money is safe and secured in your bank or how it is safe if you pay online and much more. It is a multipurpose slide and can easily be modified as you want. Choose this slide to make your PowerPoint presentation look even more fantastic.

Cyber And Data Safety Risk Management Framework Designs PDF
Mentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Showcasing this set of slides titled cyber and data safety risk management framework designs pdf. The topics addressed in these templates are service design, development, service operationalization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Assessment Of Cloud And Traditional Project Management Microsoft PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc.There are so many reasons you need a Comparative Assessment Of Cloud And Traditional Project Management Microsoft PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Comparative Assessment Of Cloud And Traditional Integrating Cloud Computing To Enhance Projects Effectiveness Mockup PDF
The following slide showcases comparative analysis of cloud and traditional project management. It provides information about capital expenditure, scalability, efficiency, real time information, security, fixes, etc. There are so many reasons you need a Comparative Assessment Of Cloud And Traditional Integrating Cloud Computing To Enhance Projects Effectiveness Mockup PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Retail Store Risk Management Assessment To Minimize Risks Rules PDF
The slide showcases convenience store safety evaluation. The purpose of this slide is to present potential hazards and actions that can be taken to control them. It include several risk such as lifting heavy stocks, fire, theft along with actions taken responsible person, and dat. Pitch your topic with ease and precision using this Retail Store Risk Management Assessment To Minimize Risks Rules PDF. This layout presents information on Security Measures, Regular Evaluation, Control Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Impact Of Data Safety Risk Management On Company Guidelines PDF
Mentioned slide graphically depicts before and after impact of information security risk management on a company. The various points covered in the slide are increased costs, operational disruption, reputational damage, improved company credentials, faster recovery time etc. Showcasing this set of slides titled impact of data safety risk management on company guidelines pdf. The topics addressed in these templates are impact of data safety risk management on company. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Safety Incident Management Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative cyber safety incident management current potential implications faced by firm as threats clipart pdf bundle. Topics like issues related to employees, data breaches and records exposed, reported financial losses due to increase security threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Governance IT Why Is Data Stewardship Important Formats PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Are you searching for a Data Governance IT Why Is Data Stewardship Important Formats PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Data Governance IT Why Is Data Stewardship Important Formats PDF from Slidegeeks today.

Cyber Terrorism Assault Confidential Data Should Be Backup Brochure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
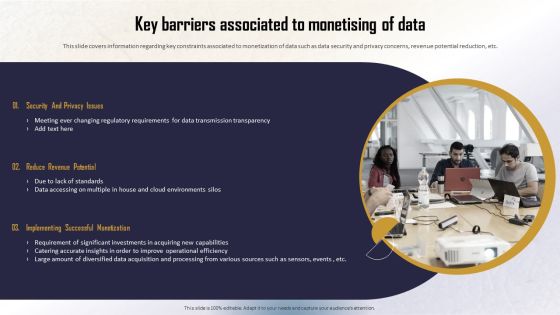
Identifying Direct And Indirect Key Barriers Associated To Monetising Of Data Sample PDF
This slide covers information regarding key constraints associated to monetization of data such as data security and privacy concerns, revenue potential reduction, etc. Welcome to our selection of the Identifying Direct And Indirect Key Barriers Associated To Monetising Of Data Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
Risk Associated With Team Working Environment In Workplace Ppt Icon Examples PDF
This slide represents risk associated with collaborative working environment in workplace. It covers risk such as wasting time, poor project management poor strategy execution, negative impact n employee morale and security risk. Pitch your topic with ease and precision using this Risk Associated With Team Working Environment In Workplace Ppt Icon Examples PDF. This layout presents information on Risk, Strategy Execution, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF
This slide showcases statistics indicating changing landscape of business risk which can be referred by executives and managers to make decisions regarding their upcoming strategies and opportunities for risks. It includes information about cybersecurity breaches, business interruption, new technologies, climatic change, Persuade your audience using this Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Breaches, Business Interruption, New Technologies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technology Facility Maintenance And Provider IT Service Maintenance Checklist Ppt Model Background Image PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this technology facility maintenance and provider IT service maintenance checklist ppt model background image pdf. Use them to share invaluable insights on planning meeting, preventive maintenance, security patches executive reporting, activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Distributor Assessment Scorecard To Improve Performance Pictures PDF
This slide provides vendor assessment scorecard for IT company which helps analyzing supplier performance. It provides details regarding quality, lifecycle requirements, design and coding, security and change management.Pitch your topic with ease and precision using this IT Distributor Assessment Scorecard To Improve Performance Pictures PDF. This layout presents information on Department Separation, Functional Requirements, Documentation Standards. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Risk Assessment Management Dashboard With Geographical Distribution Clipart PDF
The following slide highlights the cyber security risk management dashboard with dashboard with geographical distribution depicting incident volume by severity, open incidents, root cause details, divisional details and geographical distribution of risks. Pitch your topic with ease and precision using this Digital Risk Assessment Management Dashboard With Geographical Distribution Clipart PDF. This layout presents information on Geographical Distribution, Root Cause Details, Divisional Details, Social Engineering. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Cost Reduction Strategiesi Mpact Of Effective Cios IT Cost Reduction Strategies Structure PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit IT Cost Reduction Strategiesi Mpact Of Effective Cios IT Cost Reduction Strategies Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

SIEM Services What Sets Us Apart Ppt Infographic Template Backgrounds PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting siem services what sets us apart ppt infographic template backgrounds pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, ownership, dynamic business, improvement it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mobile Device Management For Improving IT Operations Determining Firm Current Capabilities Template PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Explore a selection of the finest Mobile Device Management For Improving IT Operations Determining Firm Current Capabilities Template PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mobile Device Management For Improving IT Operations Determining Firm Current Capabilities Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Multi Cloud Infrastructure Management Types Of Services Offered By Consulting Firm Download PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi-cloud services, manged security services. This Multi Cloud Infrastructure Management Types Of Services Offered By Consulting Firm Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF
This slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Pitch your topic with ease and precision using this Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Possibility It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Assessment Test To Measure Effectiveness Of Training Plan Professional PDF
purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Presenting Assessment Test To Measure Effectiveness Of Training Plan Professional PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Collecting Sensitive, Performing Unauthorized, Hurting Statement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
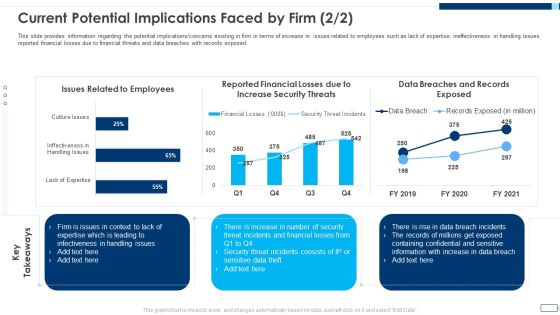
Evolving BI Infrastructure Current Potential Implications Faced By Firm Threats Portrait PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative evolving bi infrastructure current potential implications faced by firm threats portrait pdf bundle. Topics like issues related to employees, reported financial losses due to increase security threats, data breaches and records exposed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
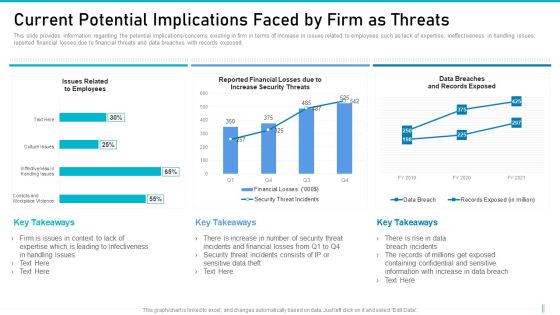
Risk Management For Organization Essential Assets Current Potential Implications Faced Graphics PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative risk management for organization essential assets current potential implications faced graphics pdf bundle. Topics like issues related to employees, reported financial losses due to increase security threats, data breaches and records exposed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current Potential Implications Faced By Firm Intelligent Infrastructure Rules PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative Current Potential Implications Faced By Firm Intelligent Infrastructure Rules PDF bundle. Topics like Issues Related To Employees, Reported Financial Losses, Due To Increase Security Threats, Data Breaches And can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
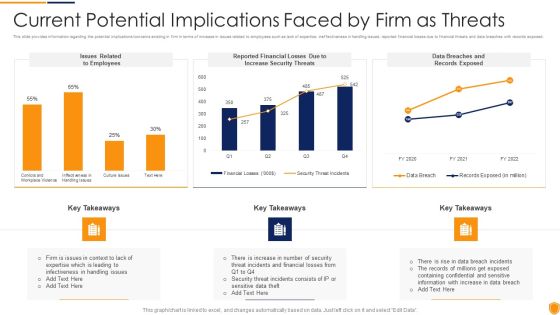
Mitigating Cybersecurity Threats And Vulnerabilities Current Potential Implications Formats PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities current potential implications formats pdf bundle. Topics like employees, increase security threats, data breaches and records exposed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
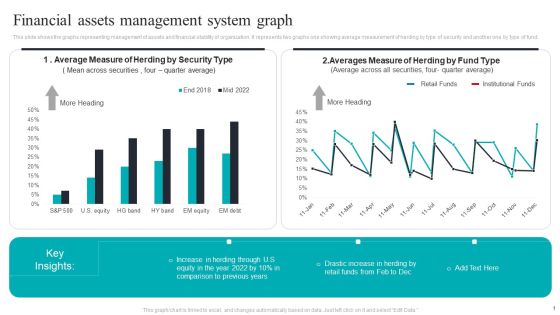
Financial Assets Management System Graph Structure PDF
This slide shows the graphs representing management of assets and financial stability of organization. It represents two graphs one showing average measurement of herding by type of security and another one by type of fund. Pitch your topic with ease and precision using this Financial Assets Management System Graph Structure PDF. This layout presents information on Financial Assets, Management System Graph. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

ESO System Incident Management KPI Dashboard Ppt PowerPoint Presentation File Graphic Images PDF
This slide covers enterprise security operation incident management kpi dashboard. It involves details such as average resolution time, new incidents, incident status and new incidents by category. Pitch your topic with ease and precision using this ESO System Incident Management KPI Dashboard Ppt PowerPoint Presentation File Graphic Images PDF. This layout presents information on Average Resolution Time, Incident Status, New Incidents. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Devops Quality Assurance And Testing To Improve Speed And Quality IT Impact Of Effective Testing Clipart PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Deliver an awe inspiring pitch with this creative devops quality assurance and testing to improve speed and quality it impact of effective testing clipart pdf bundle. Topics like mean lead time to changes, quality test pass rate, product failure rate, mean time to resolution can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
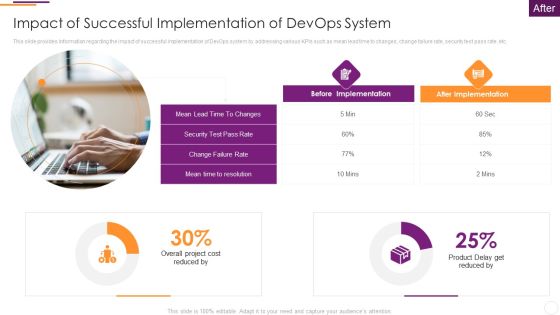
Key Parameters To Establish Overall Devops Value IT Impact Of Successful Implementation Of Devops System Summary PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Deliver an awe inspiring pitch with this creative key parameters to establish overall devops value it impact of successful implementation of devops system summary pdf bundle. Topics like impact of successful implementation of devops system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

VID Managing End User Computing In The Company Infographics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting VID Managing End User Computing In The Company Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Implications, Application Performance, Endeavor And Metrics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer Virtualization Managing End User Computing In The Company Topics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting Computer Virtualization Managing End User Computing In The Company Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security Implications, Storage Consumption, Experience Server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cybersecurity Employee Training Status With Completion Status Structure PDF
This slide exhibits a security awareness training checklist to educate employees and protect the company from malware attacks. It includes categories for training such as password protection, browsers, devices, and network connection. Pitch your topic with ease and precision using this Cybersecurity Employee Training Status With Completion Status Structure PDF. This layout presents information on Training Status Completion Status, Cybersecurity Employee. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
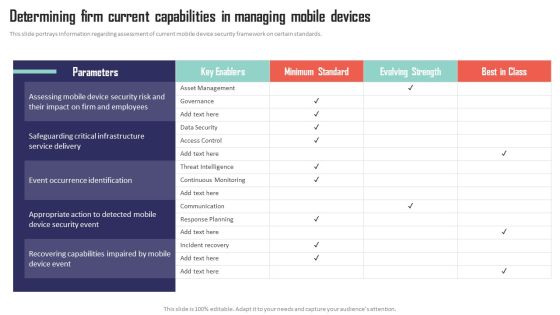
Mobile Device Management Determining Firm Current Capabilities In Managing Mobile Devices Structure PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Create an editable Mobile Device Management Determining Firm Current Capabilities In Managing Mobile Devices Structure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Mobile Device Management Determining Firm Current Capabilities In Managing Mobile Devices Structure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

In House Training Schedule We Will Implement Icons PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack.Deliver and pitch your topic in the best possible manner with this In House Training Schedule We Will Implement Icons PDF. Use them to share invaluable insights on Social Engineering, Ransomware, Password Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Apple Emotional Marketing Strategy Brand Storytelling Overview Elements Statistics Professional PDF
This slide showcases general overview of brand storytelling strategy with elements and key statistics. It provides details about plot points, neural activity, stats, information, marketers, content marketing, service and product value, authentic, relatable, user generated content, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Apple Emotional Marketing Strategy Brand Storytelling Overview Elements Statistics Professional PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Apple Emotional Marketing Strategy Brand Storytelling Overview Elements Statistics Professional PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Elastic NLB 30 60 90 Days Plan For NLB Implementation Download PDF
This slide depicts the 30 60 90 days plan for network load balancer implementation, including tasks that would be performed at each months interval. Boost your pitch with our creative Elastic NLB 30 60 90 Days Plan For NLB Implementation Download PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
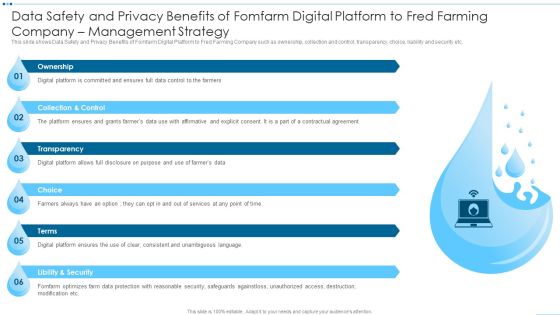
Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF
This slide shows Data Safety and Privacy Benefits of Fomfarm Digital Platform to Fred Farming Company such as ownership, collection and control, transparency, choice, liability and security etc. Deliver an awe inspiring pitch with this creative Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF bundle. Topics like Ownership, Collection And Control, Transparency, Choice can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps Of Vulnerabilities And Risk Mitigation Process Icons PDF
The following slide showcases some steps to mitigate risk for eliminating future expenses. It includes key elements such as find, prioritize, fix and monitor. Presenting Steps Of Vulnerabilities And Risk Mitigation Process Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Security Risks, Deploy Automated Tool, Resolve Risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financial Transformation Key Success Metrics Assessment Digital Transformation Toolkit Accounting Finance Introduction PDF
In this slide we have showcased financial transformation effectiveness graph with key success metrics lincluding data management, IT system efficiency and cyber security Deliver an awe inspiring pitch with this creative financial transformation key success metrics assessment digital transformation toolkit accounting finance introduction pdf bundle. Topics like financial transformation key success metrics assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing System Technology Confidential Computing Market Driven By Cloud Professional PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Dashboard For Threat Tracking Topics PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cyber exploitation it dashboard for threat tracking topics pdf bundle. Topics like dashboard for threat tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
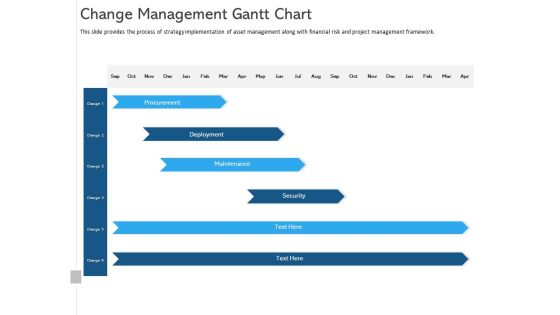
ALM Optimizing The Profit Generated By Your Assets Change Management Gantt Chart Themes PDF
This slide provides the process of strategy implementation of asset management along with financial risk and project management framework. Deliver and pitch your topic in the best possible manner with this alm optimizing the profit generated by your assets change management gantt chart themes pdf. Use them to share invaluable insights on procurement, deployment, maintenance, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Assessing Contribution Of 5G To Global Economy Pictures PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc.Deliver an awe inspiring pitch with this creative Assessing Contribution Of 5G To Global Economy Pictures PDF bundle. Topics like Telecommunication Networks, Across Digital Systems, Manage Digitalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
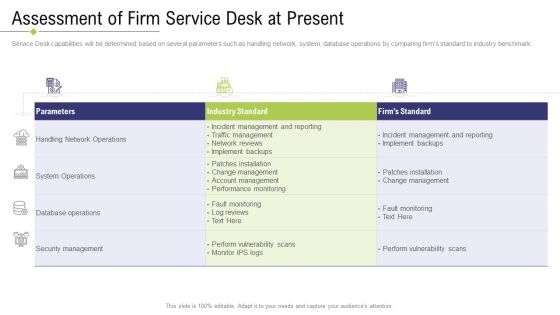
Technology Facility Maintenance And Provider Assessment Of Firm Service Desk At Present Brochure PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver an awe inspiring pitch with this creative technology facility maintenance and provider assessment of firm service desk at present brochure pdf bundle. Topics like system operations, security management, performance monitoring, network reviews, database operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Assessing Contribution Of 5G To Global Economy Icons PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver and pitch your topic in the best possible manner with this Assessing Contribution Of 5G To Global Economy Icons PDF. Use them to share invaluable insights on Financial, Economic Value Developed, Digital Systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Project Gantt Chart For Assessing Department Progress Brochure PDF
This slide represents the project Gantt chart that enables monitoring the progress status of departments. It covers the website team, mobile team, and marketing team. Showcasing this set of slides titled Project Gantt Chart For Assessing Department Progress Brochure PDF. The topics addressed in these templates are Third Party Integration, New Admin Console, Security Upgrade. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Banking Operations Management Change In Customer Preference Towards E Banking Icons PDF
This slide highlights the consumer preference for retail branch banking in bar graph format, which showcases the interest of consumers for digital or in person transaction with bank. Deliver an awe inspiring pitch with this creative Banking Operations Management Change In Customer Preference Towards E Banking Icons PDF bundle. Topics like Digital Transactions, Customers, Security Concerns can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparison Assessment Of ESO System Tools Ppt PowerPoint Presentation File Graphics Template PDF
This slide covers comparison assessment of enterprise security operations tools. It involves features such as vulnerability management, penetration testing and privacy standard compliance. Showcasing this set of slides titled Comparison Assessment Of ESO System Tools Ppt PowerPoint Presentation File Graphics Template PDF. The topics addressed in these templates are Cost Involved, Vulnerability Management, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Assessment Of Firm Service Desk At Present Ppt Professional Files PDF
Service Desk capabilities will be determined based on several parameters such as handling network, system, database operations by comparing firms standard to industry benchmark. Deliver and pitch your topic in the best possible manner with this assessment of firm service desk at present ppt professional files pdf. Use them to share invaluable insights on database operations, security management, network operations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Protection And Privacy Risk In Internet Of Things Topics PDF
The following slide showcases some major security and privacy issues associated with internet of things iot to achieve customer trust. It includes elements such as inadequate password safety, lack of secure interface, abundance of data etc. Presenting Protection And Privacy Risk In Internet Of Things Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Abundance Of Data, Eavesdropping, Unwanted Public Exposure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
 Home
Home