Information Security Gap Analysis
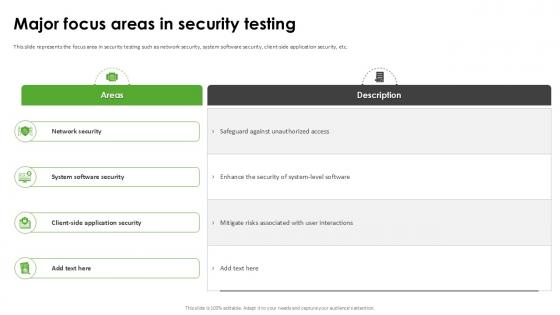
Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example
This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Top Firewall As A Service Technology Trends Network Security Mockup Pdf
This slide outlines the top Firewall-as-a-Service trends. The purpose of this slide is to briefly explain the top current FWaaS trends. These include firewalls remain important, zero trust in the cloud, isolation of security from the underlying infrastructure, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Firewall As A Service Technology Trends Network Security Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Firewall As A Service Technology Trends Network Security Mockup Pdf today and make your presentation stand out from the rest

Cyber Security Risk Assessment And Management Ppt Powerpoint Presentation File Example File Pdf
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the Cyber Security Risk Assessment And Management Ppt Powerpoint Presentation File Example File Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template
This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
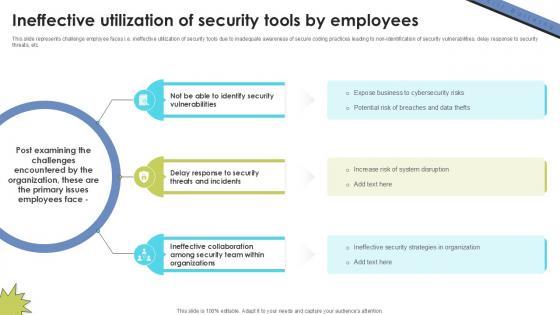
Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V
This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Wireless Network Security System Smart Lock Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this wireless network security system smart lock ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Get a simple yet stunning designed Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
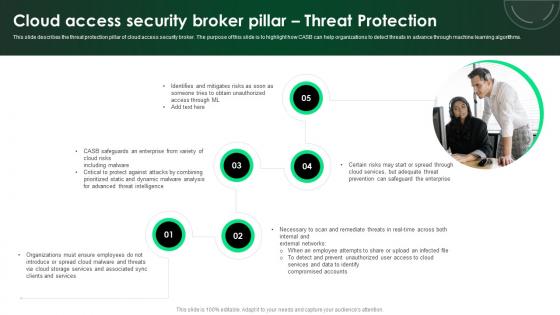
CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Retrieve professionally designed CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Mesh Computing Safety Icon Cloud Computing Cloud Security Ppt PowerPoint Presentation Complete Deck
Share a great deal of information on the topic by deploying this mesh computing safety icon cloud computing cloud security ppt powerpoint presentation complete deck. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
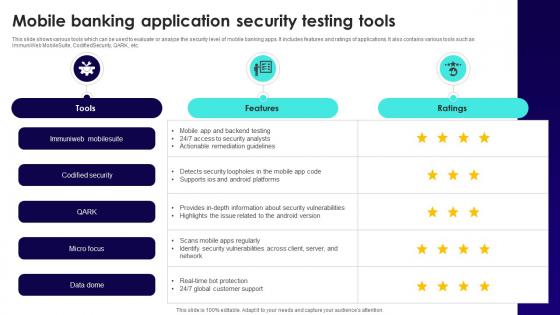
Wireless Banking To Improve Mobile Banking Application Security Testing Tools Fin SS V
This slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Get a simple yet stunning designed Wireless Banking To Improve Mobile Banking Application Security Testing Tools Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Wireless Banking To Improve Mobile Banking Application Security Testing Tools Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Software Architecture Security Scalability Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this software architecture security scalability ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example
This slide showcases the principles of security testing such as confidentiality, integrity, authentication, authorization, availability, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. If you are looking for a format to display your unique thoughts, then the professionally designed Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Internet Security Assessment By Computer Forensics Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting internet security assessment by computer forensics ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including internet security assessment by computer forensics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Icons Slide For Network Security Using Firewall As A Service Clipart Pdf
Introducing our well designed Icons Slide For Network Security Using Firewall As A Service Clipart Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Managing Technical And Non Different Security Threats To Be Managed By Web Developers
Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Managing Technical And Non Different Security Threats To Be Managed By Web Developers to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Managing Cyber Security Incident Response Lifecycle Ppt Styles Example Topics PDF
This slide covers cyber security incident response lifecycle. It involves four phases such as preparation, detection, containment and post incident activity. Presenting Managing Cyber Security Incident Response Lifecycle Ppt Styles Example Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Preparation, Post Incident Activity, Detection And Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
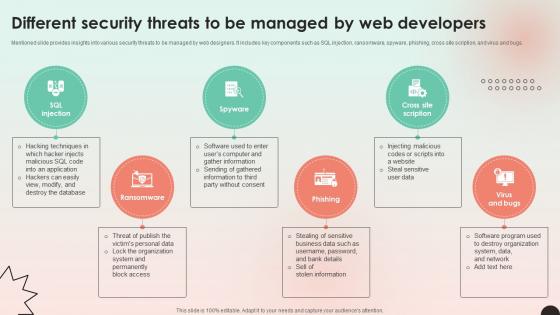
Web Consulting Business Different Security Threats To Be Managed By Web
Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs. This modern and well-arranged Web Consulting Business Different Security Threats To Be Managed By Web provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Mobile Banking Application Security Testing Tools Comprehensive Smartphone Banking Icons Pdf
This slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc.Create an editable Mobile Banking Application Security Testing Tools Comprehensive Smartphone Banking Icons Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Mobile Banking Application Security Testing Tools Comprehensive Smartphone Banking Icons Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint
This slide highlights the overview of security testing such as discovering and securing vulnerabilities, ensuring a threat-free software environment, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
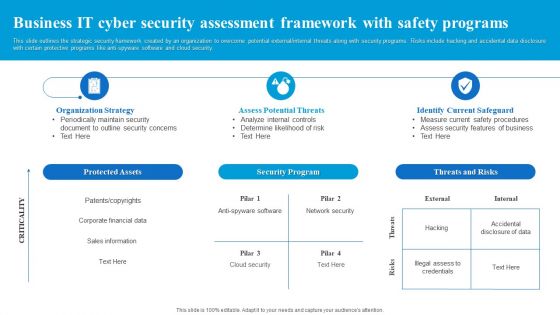
Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF
This slide outlines the strategic security framework created by an organization to overcome potential external or internal threats along with security programs. Risks include hacking and accidental data disclosure with certain protective programs like anti-spyware software and cloud security. Presenting Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Program, Threats And Risks, Protected Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icons Slide For Exploring Investment Opportunities With Security Token Offerings Infographics Pdf
Introducing our well designed Icons Slide For Exploring Investment Opportunities With Security Token Offerings Infographics Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf
Introducing our well designed Icons Slide For Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Global Security Industry Report PPT Slide IR SS V
Introducing our well designed Icons Slide For Global Security Industry Report PPT Slide IR SS V set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Tracking Mobile Device Activities At Workplace Business Mobile Device Security Management Icons PDF
This slide covers information regarding the tracking mobile device activities at workplace with details about MDM managed mobile summary, MDM users, vulnerabilities and severity summary. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Tracking Mobile Device Activities At Workplace Business Mobile Device Security Management Icons PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Addressing Mobile Device Management Business Mobile Device Security Management And Mitigation Background PDF
This slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU that can be selected by vendor based on requirement. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Addressing Mobile Device Management Business Mobile Device Security Management And Mitigation Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
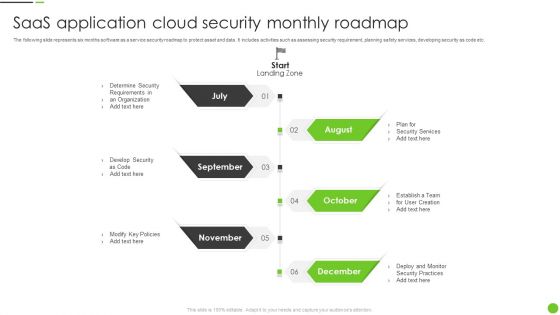
Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF
The following slide represents six months software as a service security roadmap to protect asset and data. It includes activities such as assessing security requirement, planning safety services, developing security as code etc. Presenting Saas Application Cloud Security Monthly Roadmap Ppt PowerPoint Presentation File Format PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Determine Security, Develop Security, Modify Key Policies. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
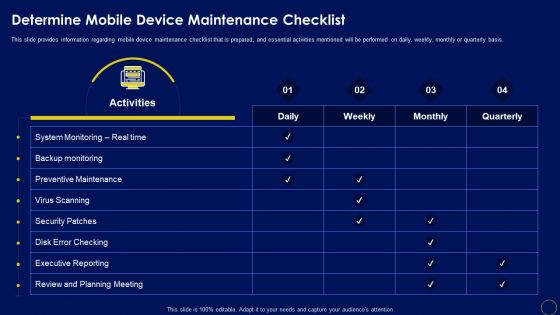
Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Retrieve professionally designed Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
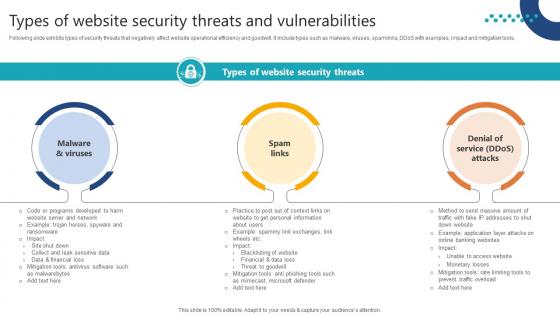
Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Building Trust With IoT Security IoT Based Edge Computing Three Layer Architecture IoT SS V
This slide showcases edge computing architecture that helps in improving performance and reduce latency through real time data processing. It includes three layers such as cloud layer, edge layer, and device layer. Welcome to our selection of the Building Trust With IoT Security IoT Based Edge Computing Three Layer Architecture IoT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Global Cyber Terrorism Incidents On The Rise IT IT Infrastructure Cyber Security Budget Pictures PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it it infrastructure cyber security budget pictures pdf bundle. Topics like data security, infrastructure protections, access management, security service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Practices For Effectively Managing Cyber Security Ppt Powerpoint Presentation File Model Pdf
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as train staff on cyber incident management process If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Best Practices For Effectively Managing Cyber Security Ppt Powerpoint Presentation File Model Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
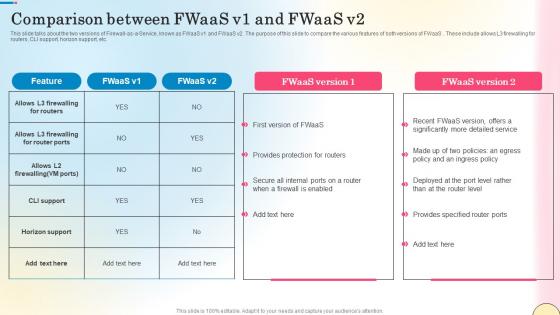
Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf
This slide talks about the two versions of Firewall-as-a-Service, known as FWaaS v1 and FWaaS v2. The purpose of this slide to compare the various features of both versions of FWaaS . These include allows L3 firewalling for routers, CLI support, horizon support, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Insider Attacker Method And Behaviour Assessment Information PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver an awe inspiring pitch with this creative insider attacker method and behaviour assessment information pdf bundle. Topics like logging in at odd hours, first time accessing system, copying large amount of information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Website Security Management Strategic Plan Step By Step Guide Slides PDF
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Website Security Management Strategic Plan Step By Step Guide Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Website Security Management Strategic Plan Step By Step Guide Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Global Market Size Of Security Harnessing The World Of Ethical Ppt Slide
This slide represents the global market size of security testing based on different storage such as on-premises and cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Global Market Size Of Security Harnessing The World Of Ethical Ppt Slide can be your best option for delivering a presentation. Represent everything in detail using Global Market Size Of Security Harnessing The World Of Ethical Ppt Slide and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
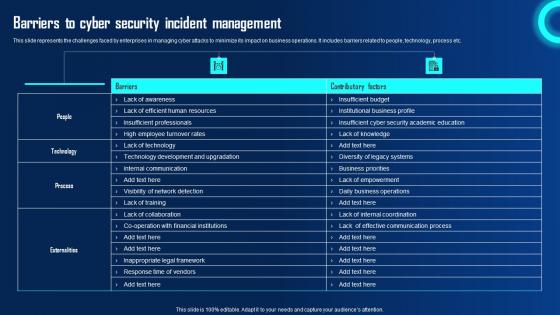
Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
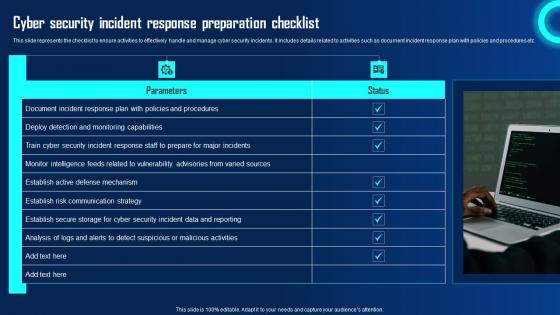
Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
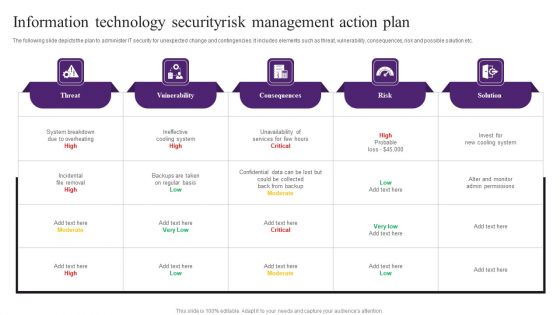
Information Technology Securityrisk Management Action Plan Themes PDF
The following slide depicts the plan to administer IT security for unexpected change and contingencies. It includes elements such as threat, vulnerability, consequences, risk and possible solution etc. Showcasing this set of slides titled Information Technology Securityrisk Management Action Plan Themes PDF. The topics addressed in these templates are Consequences, Vuinerability, System Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
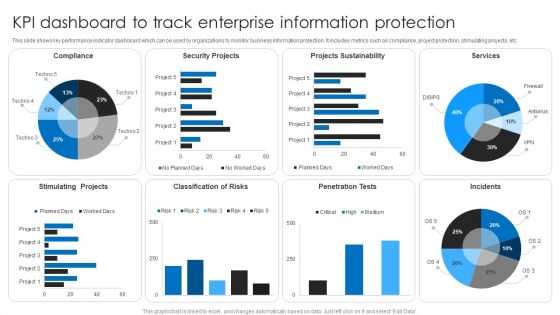
KPI Dashboard To Track Enterprise Information Protection Topics PDF
This slide shows key performance indicator dashboard which can be used by organizations to monitor business information protection. It includes metrics such as compliance, project protection, stimulating projects, etc. Showcasing this set of slides titled KPI Dashboard To Track Enterprise Information Protection Topics PDF. The topics addressed in these templates are Security Projects, Projects Sustainability, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
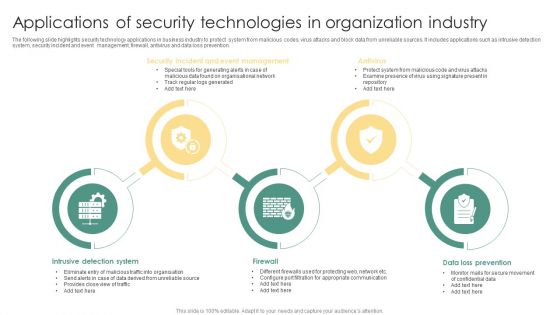
Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF
The following slide highlights security technology applications in business industry to protect system from malicious codes, virus attacks and block data from unreliable sources. It includes applications such as intrusive detection system, security incident and event management, firewall, antivirus and data loss prevention. Presenting Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Incident, Event Management, Antivirus, Firewall. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
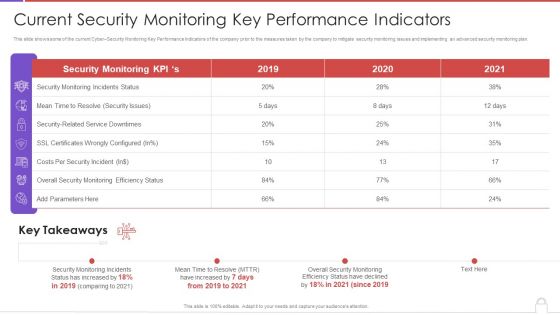
Methods To Develop Advanced Current Security Monitoring Key Performance Indicators Formats PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative methods to develop advanced current security monitoring key performance indicators formats pdf bundle. Topics like monitoring incidents status, security issues, costs per security incident, 2019 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF bundle. Topics like Security Awareness, Current Assessment, Security Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Center Kpis With Security And User Assessment Ppt Infographics Deck PDF
Showcasing this set of slides titled Data Center Kpis With Security And User Assessment Ppt Infographics Deck PDF. The topics addressed in these templates are Data Center, Data Discovery, Security Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
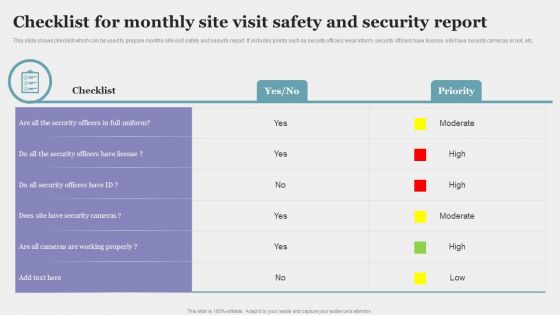
Checklist For Monthly Site Visit Safety And Security Report Guidelines PDF
This slide shows checklist which can be used to prepare monthly site visit safety and security report. It includes points such as security officers wear inform, security officers have license, site have security cameras or not, etc. Showcasing this set of slides titled Checklist For Monthly Site Visit Safety And Security Report Guidelines PDF. The topics addressed in these templates are Security Officers, Monthly Site, Visit Safety. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Risk Assessment Icon With Magnifying Glass Ppt PowerPoint Presentation File Templates PDF
Presenting this set of slides with name security risk assessment icon with magnifying glass ppt powerpoint presentation file templates pdf. This is a three stage process. The stages in this process are security risk assessment icon with magnifying glass. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Step By Step Guide To Security Testing Harnessing The World Of Ethical Ppt Template
This slide showcases the steps to follow for security testing such as creating a functional test case, adding a security test, running the test, creating the reports, etc. Slidegeeks has constructed Step By Step Guide To Security Testing Harnessing The World Of Ethical Ppt Template after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

IT Security Awareness Topics To Considered For Effective Training Program Brochure PDF
This slide covers cybersecurity awareness topics to considered for effective training. It involves topics such as removable media, cloud security, public wi-fi and physical security. Presenting IT Security Awareness Topics To Considered For Effective Training Program Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Removable Media, Cloud Security, Physical Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF
The following slide highlights multiple solutions to prevent security risks and issues. It also includes elements such as risk evaluation, security awareness, checklist, policies and regulation, recovery plan etc. Presenting Key Solutions To Manage Saas Cloud Security Issues Ppt PowerPoint Presentation Gallery Visuals PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Risk Evaluation, Security Awareness, Security Checklist, Policies And Regulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global And Regional Market Performance Global Security Industry PPT Slide IR SS V
The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If you are looking for a format to display your unique thoughts, then the professionally designed Global And Regional Market Performance Global Security Industry PPT Slide IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global And Regional Market Performance Global Security Industry PPT Slide IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Key Objectives Of People Centric Work Culture Security System Infographics PDF
The following slide highlights the main reasons to develop human centric security system for better security features. It mainly includes activities such as establishing secure perimeter, comprehending cause behind user actions, optimizing remote security operations etc. Presenting Key Objectives Of People Centric Work Culture Security System Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Establish Secure Perimeter, Acknowledges Potential Threats, Employee Roles. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF
This slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Challenges And Solutions Of Security Operations Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
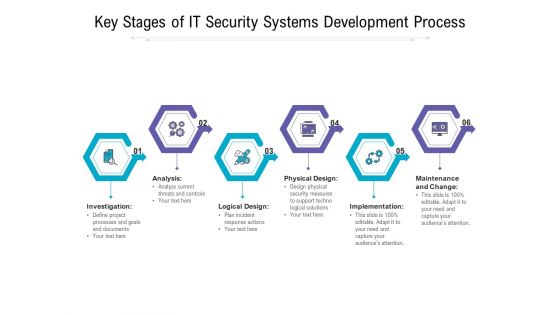
Key Stages Of IT Security Systems Development Process Ppt PowerPoint Presentation Slides Display PDF
Presenting key stages of it security systems development process ppt powerpoint presentation slides display pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including investigation, analysis, logical design, physical design, implementation, maintenance and change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf
The following slide showcases various milestones that an open source virtual assistant platform providing company achieves. It outlines milestones such as the release of new versions and new launches. Slidegeeks has constructed Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
IT Security Risk Management Icon Showcasing Risk Assessment Checklist Graphics PDF
Presenting IT Security Risk Management Icon Showcasing Risk Assessment Checklist Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security Risk Management, Icon Showcasing Risk, Assessment Checklist. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
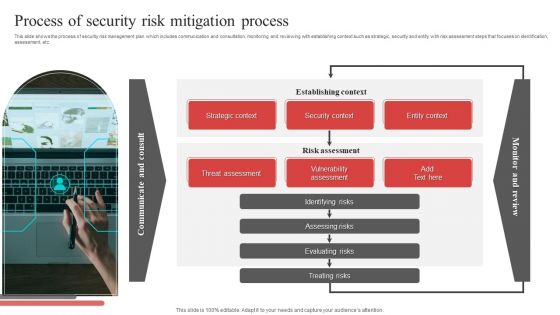
Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide shows the process of security risk management plan which includes communication and consultation, monitoring and reviewing with establishing context such as strategic, security and entity with risk assessment steps that focuses on identification, assessment, etc. Presenting Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Strategic Context, Security Context, Entity Context, Establishing Context. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS. Retrieve professionally designed Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide illustrates the SaaS security to meet business needs and ensure data management. It includes four major elements such as vendor management, cloud security, business engagement, communicate proactively etc. Presenting Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vendor Management, Cloud Security, Business Engagement, Communicate Proactively. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

3 Groups Slide For Cloud Native Security Assessments Ppt PowerPoint Presentation File Professional PDF
Presenting 3 groups slide for cloud native security assessments ppt powerpoint presentation file professional pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including 3 groups slide for cloud native security assessments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF
The following slide highlights a comprehensive checklist for digitization of security systems. The checklist covers key points such as deciding the budget, selecting the right tools, deciding the tasks for automation etc. Presenting Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security Automation, Checklist, Security Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
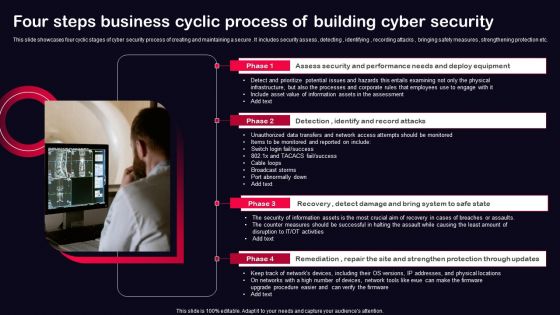
Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
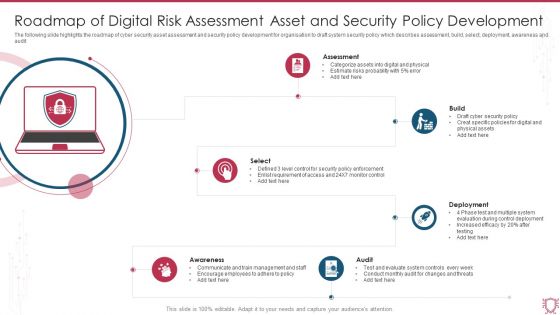
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
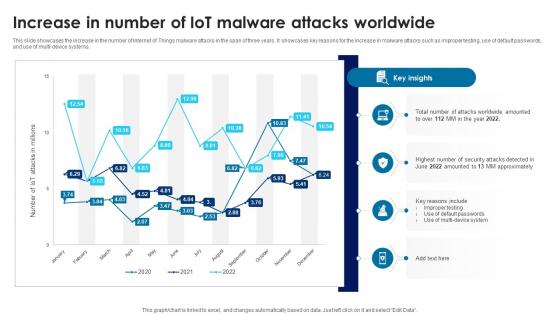
Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V
This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Kpis To Measure Phishing Scams And Attacks Topics PDF
Mentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Showcasing this set of slides titled cyber security kpis to measure phishing scams and attacks topics pdf. The topics addressed in these templates are cyber security kpis to measure phishing scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
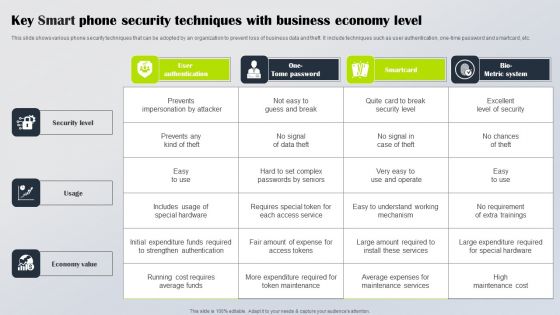
Key Smart Phone Security Techniques With Business Economy Level Brochure PDF
This slide shows various phone security techniques that can be adopted by an organization to prevent loss of business data and theft. It include techniques such as user authentication, one-time password and smartcard, etc. Showcasing this set of slides titled Key Smart Phone Security Techniques With Business Economy Level Brochure PDF. The topics addressed in these templates are Security Level, Usage, Economy Value. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
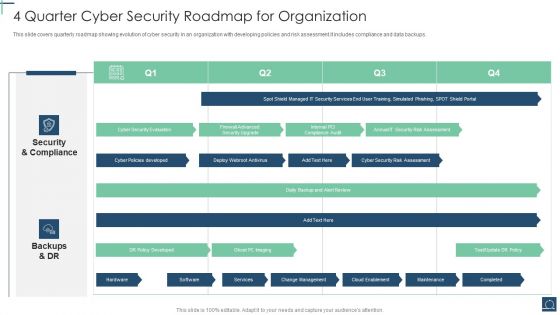
4 Quarter Cyber Security Roadmap For Organization Ppt PowerPoint Presentation File Example Topics PDF
This slide covers quarterly roadmap showing evolution of cyber security in an organization with developing policies and risk assessment.It includes compliance and data backups. Showcasing this set of slides titled 4 Quarter Cyber Security Roadmap For Organization Ppt PowerPoint Presentation File Example Topics PDF. The topics addressed in these templates are Security And Compliance, Backups And DR, DR Policy Developed. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
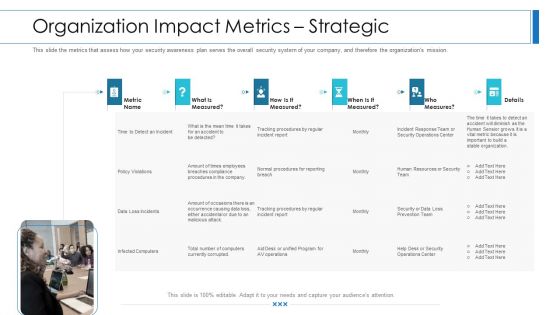
Workforce Security Realization Coaching Plan Organization Impact Metrics Strategic Infographics PDF
This slide the metrics that assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan organization impact metrics strategic infographics pdf. Use them to share invaluable insights on organization impact metrics strategicand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
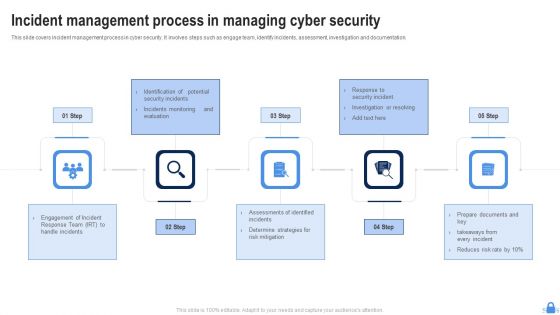
Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF
This slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Determine Strategies, Risk Mitigation, Engagement Incident. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Our Services For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the key services that the organization offers , these services can be personal bodyguard services , cyber security services and security guard service. Presenting you an exemplary Our Services For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Our Services Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the key services that the organization offers , these services can be personal bodyguard services , cyber security services and security guard service. Presenting you an exemplary Our Services Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
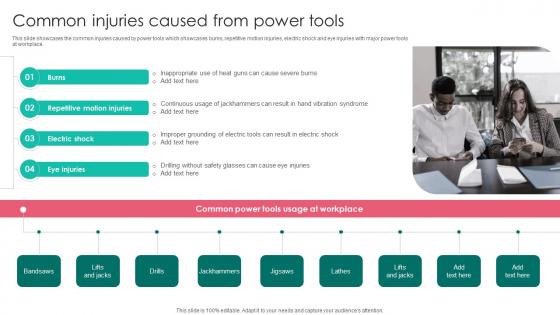
Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf
This slide showcases the common injuries caused by power tools which showcases burns, repetitive motion injuries, electric shock and eye injuries with major power tools at workplace. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
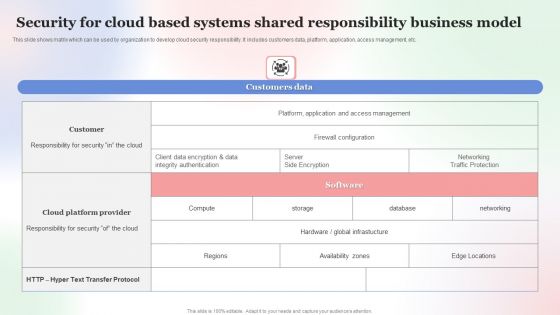
Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF
This slide shows matrix which can be used by organization to develop cloud security responsibility. It includes customers data, platform, application, access management, etc. Showcasing this set of slides titled Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF. The topics addressed in these templates are Security For Cloud Based, Systems Shared Responsibility, Business Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

RPA Operating Model With Security And Compliance Ppt PowerPoint Presentation Model Styles PDF
Presenting rpa operating model with security and compliance ppt powerpoint presentation model styles pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including strategy leadership and organizational fit, organizational enablement and change, deployment and operations, security and compliance, technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF
This side showcase the checklist of working condition and firewall security of smart home to know updates of standard devices and their benchmarks. It includes status of devices such as garage locks, remote access, data sharing, door openers, policies of devices and update cycle. Presenting Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Devices Firewall, Working Condition, Access Points. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Management Model For Data Security Impact Assessment Matrix Formats PDF
Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Assessment Matrix Formats PDF bundle. Topics like Financial, Reputation, Regulatory, Operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Governance Plan Framework With Security And Auditing Ppt PowerPoint Presentation File Template PDF
Presenting data governance plan framework with security and auditing ppt powerpoint presentation file template pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data architecture, data quality, change management and deployment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
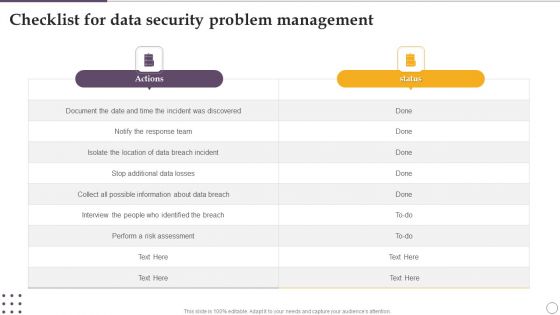
Checklist For Data Security Problem Management Ppt Visual Aids Deck PDF
Showcasing this set of slides titled Checklist For Data Security Problem Management Ppt Visual Aids Deck PDF. The topics addressed in these templates are Actions, Risk Assessment, About Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF
This slide outlines safety measures for various hotels across hospitality sector. It involves measures such as surveillance cameras, cybersecurity, mobile room keys and providing staff training.Presenting Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cybersecurity, Security And Ensure, Staff Training This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty eight slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Table Of Contents Organizations Risk Management And IT Security Formats PDF
Find highly impressive Table Of Contents Organizations Risk Management And IT Security Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Organizations Risk Management And IT Security Formats PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

IT System Risk Management Guide Table Of Contents Security Background PDF
Are you searching for a IT System Risk Management Guide Table Of Contents Security Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT System Risk Management Guide Table Of Contents Security Background PDF from Slidegeeks today.
Icons Slide For Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Clipart PDF
Introducing our well designed icons slide for modern security observation plan to eradicate cybersecurity risk and data breach clipart pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
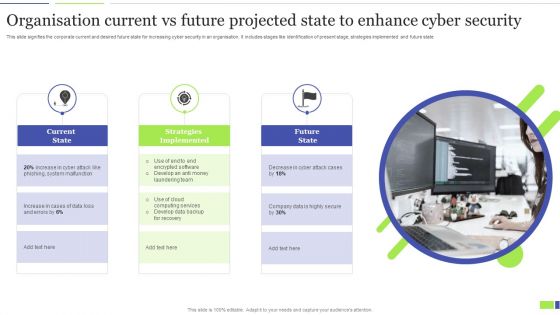
Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF
This slide signifies the corporate current and desired future state for increasing cyber security in an organisation. It includes stages like identification of present stage, strategies implemented and future state. Presenting Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Current State, Strategies Implemented, Future State. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
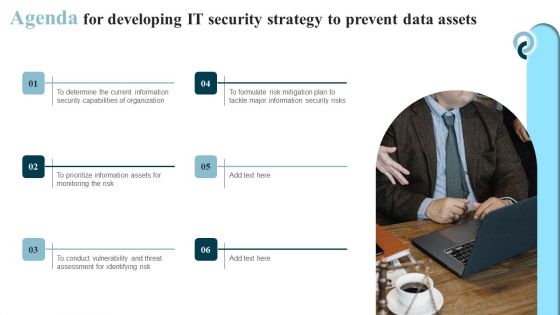
Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
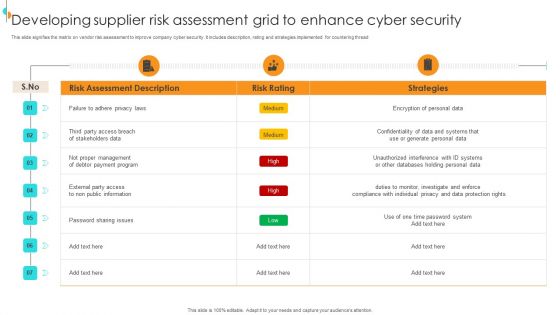
Developing Supplier Risk Assessment Grid To Enhance Cyber Security Structure PDF

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
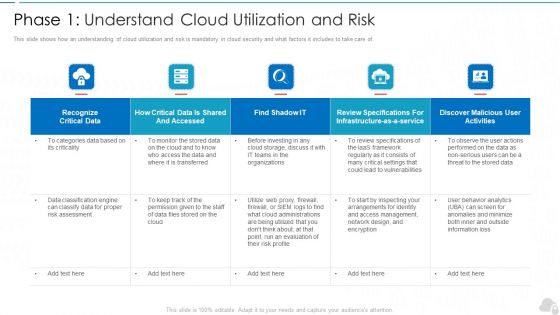
Phase 1 Understand Cloud Utilization And Risk Cloud Computing Security IT Ppt Summary Smartart PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this phase 1 understand cloud utilization and risk cloud computing security it ppt summary smartart pdf. Use them to share invaluable insights on recognize critical data, infrastructure, evaluation, vulnerabilities, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
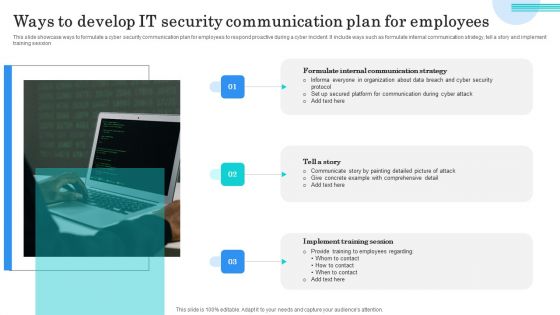
Ways To Develop IT Security Communication Plan For Employees Elements PDF
This slide showcase ways to formulate a cyber security communication plan for employees to respond proactive during a cyber incident. It include ways such as formulate internal communication strategy, tell a story and implement training session. Presenting Ways To Develop IT Security Communication Plan For Employees Elements PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Formulate Internal Communication, Tell Story, Implement Training Session. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
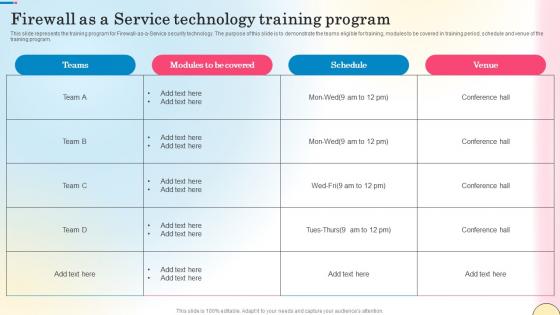
Firewall As A Service Technology Training Program Network Security Brochure Pdf
This slide represents the training program for Firewall-as-a-Service security technology. The purpose of this slide is to demonstrate the teams eligible for training, modules to be covered in training period, schedule and venue of the training program. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Firewall As A Service Technology Training Program Network Security Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Firewall As A Service Technology Training Program Network Security Brochure Pdf
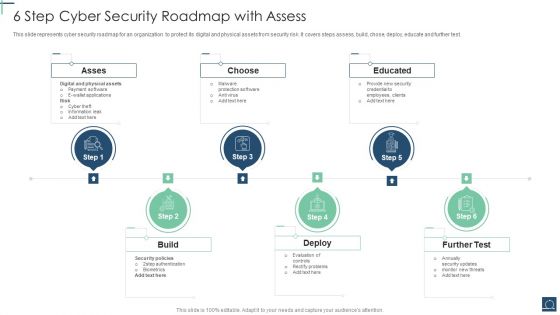
6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF
This slide represents cyber security roadmap for an organization to protect its digital and physical assets from security risk .It covers steps assess, build, chose, deploy, educate and further test. Persuade your audience using this 6 Step Cyber Security Roadmap With Assess Ppt PowerPoint Presentation File Objects PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Asses, Choose, Educated, Build. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
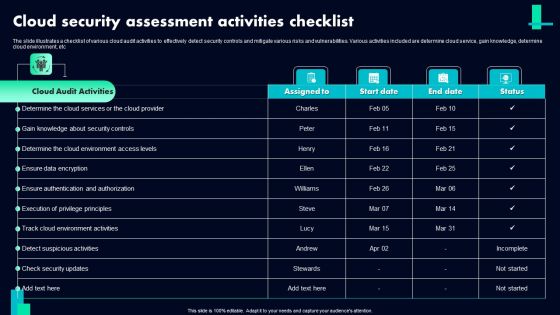
Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF
The following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. This Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cover Letter For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the security guard service proposal , as it highlights the key issues being faced by the organization and a brief background about the company. Presenting you an exemplary Cover Letter For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Next Step For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be team meeting ,on-site visit etc. Presenting you an exemplary Next Step For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Effective IT Risk Management Process Impact On Security Infrastructure Structure PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this effective it risk management process impact on security infrastructure structure pdf. Use them to share invaluable insights on target, risk, performance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
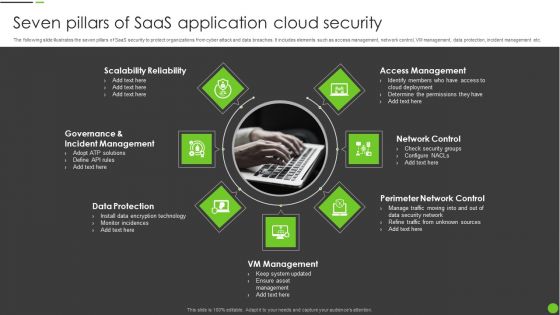
Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF
The following slide illustrates the seven pillars of SaaS security to protect organizations from cyber attack and data breaches. It includes elements such as access management, network control, VM management, data protection, incident management etc. Presenting Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including VM Management, Data Protection, Network Control, Perimeter Network Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cover Letter Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the security guard service proposal , as it highlights the key issues being faced by the organization and a brief background about the company. Presenting you an exemplary Cover Letter Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF
This slide outlines strategies to minimize security failure in RPA projects. Some of the best practices such as maintain accountability for BOT actions, prevent fraud and abuse, preserve log integrity, and authorize secure RPA development. Presenting Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Maintain Accountability, Prevent Fraud And Abuse, Preserve Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Next Step Proposal For Security Guard Services One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be team meeting, on-site visit etc. Presenting you an exemplary Next Step Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

Challenge And Solutions 2 Cloud Threats And Security Ppt Inspiration Slideshow PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver and pitch your topic in the best possible manner with this challenge and solutions 2 cloud threats and security ppt inspiration slideshow pdf. Use them to share invaluable insights on security, risks, encryption methods, echniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
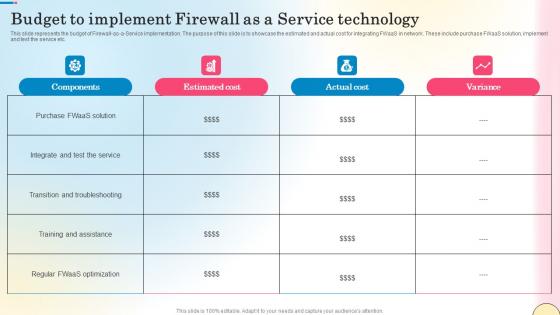
Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf
This slide represents the budget of Firewall-as-a-Service implementation. The purpose of this slide is to showcase the estimated and actual cost for integrating FWaaS in network. These include purchase FWaaS solution, implement and test the service etc. Get a simple yet stunning designed Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget To Implement Firewall As A Service Technology Network Security Diagrams Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.

Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck
Landing corporate business deals can be a huge achievement, both in terms of reputation and finance. This highlights the importance of drafting a comprehensive plan for this business segment that this Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck does perfectly for you. Given below is a perfectly curated service proposal in Seventy slides that is sure to give your presentation the desired edge. It will display all the details enabling the company to analyze standout components and make an informed decision. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.
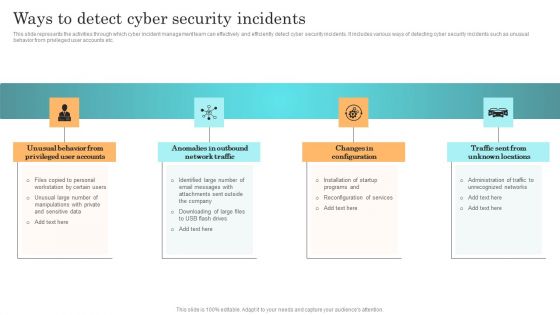
Incident Response Techniques Deployement Ways To Detect Cyber Security Incidents Infographics PDF

Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document brilliant piece now.

Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

 Home
Home