Hacking Phases
The Roi Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Icons PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this the roi of security awareness training hacking prevention awareness training for it security icons pdf. Use them to share invaluable insights on organizations, training, security, costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
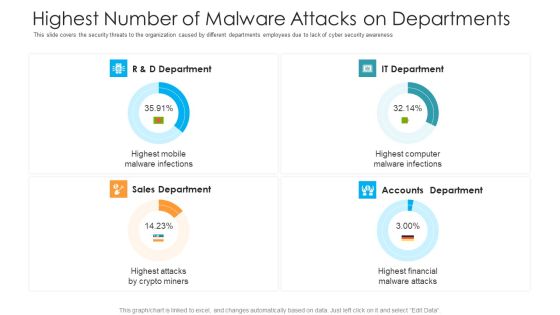
Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
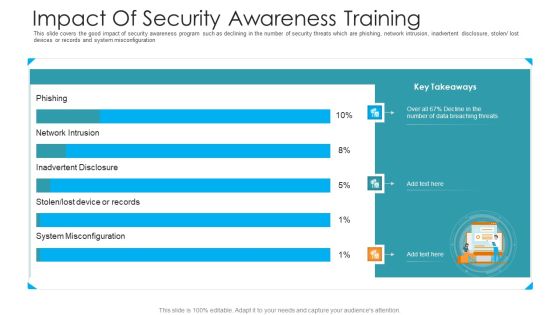
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Where Is The Gap In Security Programs Hacking Prevention Awareness Training For IT Security Diagrams PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a where is the gap in security programs hacking prevention awareness training for it security diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF
This slide depicts the hacking groups such as the anonymous hacker group, conti ransomware gang, threat actors in belarus launching cyber proxy war over ukraine attacks by russia. Find highly impressive Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Effect After Implementing Cyber Risk Security Awareness Program Hacking Prevention Awareness Training For IT Security Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative effect after implementing cyber risk security awareness program hacking prevention awareness training for it security information pdf bundle. Topics like accounts department, sales department, it department, r and d department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Person Working To Hack Confidential Data Ppt PowerPoint Presentation File Images PDF
Presenting person working to hack confidential data ppt powerpoint presentation file images pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including person working to hack confidential data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Role Of Project Management In Product Life Cycle Phases Infographics PDF
This slide showcase management roles at every phase of product lifecycle manager to reduce or ramp up product in market and includes shortening product development. It include elements such as subject expert, growth hacker, retention strategist and solution seeker. Pitch your topic with ease and precision using this Role Of Project Management In Product Life Cycle Phases Infographics PDF. This layout presents information on Goals, Developing Product, Faster Growth. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

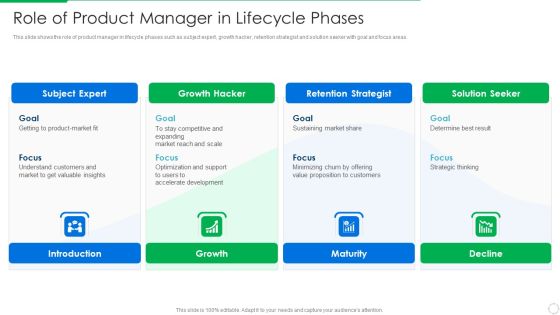
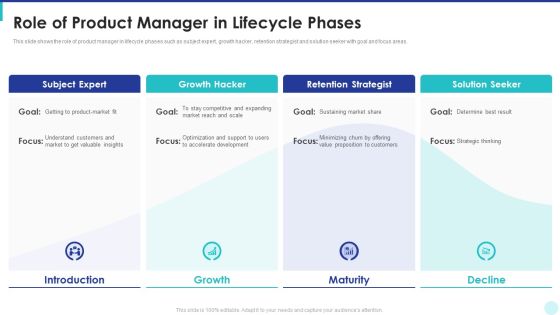
Product Lifecycle Management IT Role Of Product Manager In Lifecycle Phases Themes PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. This is a product lifecycle management it role of product manager in lifecycle phases themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like subject expert, growth hacker, retention strategist, solution seeker . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agile Product Life Process Management Role Of Product Manager In Lifecycle Phases Clipart PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. This is a agile product life process management role of product manager in lifecycle phases clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like retention strategist, growth hacker, subject expert, solution seeker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
PLM Execution In Company Role Of Product Manager In Lifecycle Phases Sample PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. This is a plm execution in company role of product manager in lifecycle phases sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like subject expert, growth hacker, retention strategist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Optimization Of Product Development Life Cycle Role Of Product Manager In Lifecycle Phases Demonstration PDF
This slide shows the role of product manager in lifecycle phases such as subject expert, growth hacker, retention strategist and solution seeker with goal and focus areas. Presenting optimization of product development life cycle role of product manager in lifecycle phases demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like introduction, growth, maturity, decline. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
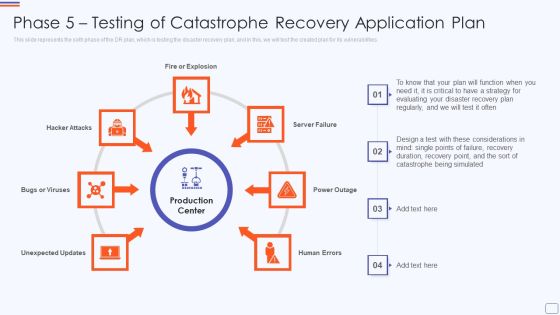
Phase 5 Testing Of Catastrophe Recovery Application Plan Mockup PDF
This slide represents the sixth phase of the DR plan, which is testing the disaster recovery plan, and in this, we will test the created plan for its vulnerabilities. Presenting phase 5 testing of catastrophe recovery application plan mockup pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like fire or explosion, hacker attacks, server failure, power outage, human errors. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Vector Illustration Of Hacked Data Server Icon Ppt PowerPoint Presentation Professional Designs Download PDF
Showcasing this set of slides titled vector illustration of hacked data server icon ppt powerpoint presentation professional designs download pdf. The topics addressed in these templates are vector illustration of hacked data server icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Growth Hacks For Small Business Goal Setting And Budget Ppt PowerPoint Presentation Icon Design Templates
Presenting this set of slides with name growth hacks for small business goal setting and budget ppt powerpoint presentation icon design templates. This is a four stage process. The stages in this process are small company, goal setting and budget, content marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Appvirality Capital Financing Elevator Pitch Deck Growth Hacks And Selecting Social Diagrams PDF
Following slide provides information about the various social actions that can be selected by the businesses as per their requirement. Deliver and pitch your topic in the best possible manner with this Appvirality Capital Financing Elevator Pitch Deck Growth Hacks And Selecting Social Diagrams PDF. Use them to share invaluable insights on Launching Page, Advanced Customization, Configuring Coupons and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Diagram Three Circles With Lock For Safety Presentation Template
Three air balloons with text boxes are used to craft this power point template slide. This PPT slide contains the concept of business text representation. This slide is usable for business and marketing related presentations.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
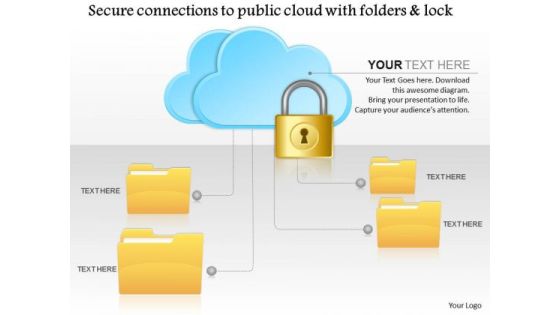
Business Diagram Secure Connections To The Public Cloud With Folders And Lock Ppt Slide
This technical slide has been designed with graphic of folders and cloud with lock. This PPT slide depicts the concept of secure connections. It focuses on the data safety in cloud technology. Use this diagram for data safety related presentations.

Competitive Analysis Of ABS Healthcare Company For 2021 Themes PDF
This slide shows the competitive analysis of ABS Healthcare Company with other similar line of competitors on the based of certain parameters such as Sales, Stole Personal Records, Hacking Incidents, Total Cybersecurity Cases etc. Deliver an awe inspiring pitch with this creative competitive analysis of abs healthcare company for 2021 themes pdf bundle. Topics like personal records stolen, hacking incidents, cybersecurity cases can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Costs Of Repairing Damages Themes PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money. Deliver an awe inspiring pitch with this creative cyber exploitation it costs of repairing damages themes pdf bundle. Topics like social network account, servers, network equipment, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Russian Cyber Attacks On Ukraine IT Global Uprising Of Grassroots Microsoft PDF
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an awe inspiring pitch with this creative russian cyber attacks on ukraine it global uprising of grassroots microsoft pdf bundle. Topics like internet, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Security Threat Analysis With Tactics And Victims Ppt PowerPoint Presentation Infographic Template Format Ideas PDF
Showcasing this set of slides titled internet security threat analysis with tactics and victims ppt powerpoint presentation infographic template format ideas pdf. The topics addressed in these templates are fake installation, hack the bidding models, hack the identity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF
This slide outlines the strategic security framework created by an organization to overcome potential external or internal threats along with security programs. Risks include hacking and accidental data disclosure with certain protective programs like anti-spyware software and cloud security. Presenting Business IT Cyber Security Assessment Framework With Safety Programs Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Program, Threats And Risks, Protected Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Dashboard For ABS Healthcare Company Ppt Themes PDF
This slide shows a cybersecurity dashboard with KPIs such as total cybersecurity cases in company in 2021, total records stoles, malware cases resolved, operational efficiency, mean time to resolve threats etc. Presentingcybersecurity dashboard for abs healthcare company ppt themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like phishing attacks 2021, records stolen 2021, malware cases resolved 2021, malware attacks 2021, hacking incidents 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
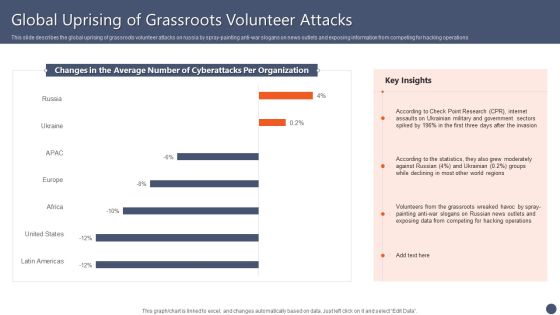
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Technology Framework Risk Assessment And Management Diagrams PDF
This slide highlights the potential threat related to IT services used by enterprises and provide techniques to mitigate them. Key components of risk are Cybersecurity, compliance, automation and data privacy. Showcasing this set of slides titled Information Technology Framework Risk Assessment And Management Diagrams PDF. The topics addressed in these templates are Malware Attacks, Phishing Emails Asking Bank, Website Hacking Third. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Russian Cyber Attacks On Ukraine IT Threat Actors Supporting Russia And Ukraine Icons PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. Presenting russian cyber attacks on ukraine it threat actors supporting russia and ukraine icons pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like organization, systems, servers, planned, analyzing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Global Uprising Of Grassroots Volunteer Attacks Background PDF
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray-painting anti war slogans on news outlets and exposing information from competing for hacking operations.Deliver an awe inspiring pitch with this creative data wiper spyware attack global uprising of grassroots volunteer attacks background pdf bundle. Topics like according to the statistics, moderately against russian, volunteers from the grassroots can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF
This slide illustrates steps to save devices from botnet hacking attacks. It includes measures such as build secure passwords, allow trusted parties only, implement ingress and egress filtering, etc. Presenting Preventive Measures To Protect Devices From Botnet Attack Demonstration PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Build Secure Passwords, Allow Trusted Party Only, Implement Ingress. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
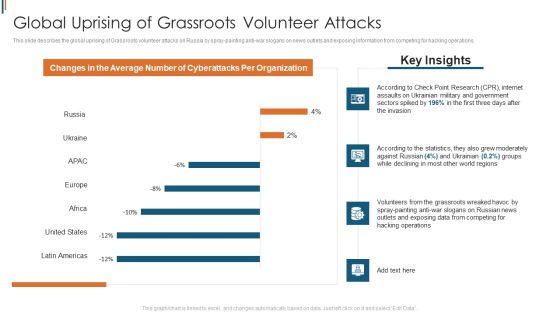
Ukraine Cyberwarfare Global Uprising Of Grassroots Volunteer Attacks Rules Pdf
This slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an awe inspiring pitch with this creative ukraine cyberwarfare global uprising of grassroots volunteer attacks rules pdf bundle. Topics like according to check point research cpr, internet assaults on ukrainian military, government sectors spiked by 196 percentage in the first three days after the invasion, according to the statistics, they also grew moderately against russian 4 percent, ukrainian 0.2 percent groups while declining in most other world regions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Signs For Various Digital Terrorism Attacks Brochure PDF
This slide shows various cyber terrorism attacks along with signs associated with each cyber attack. It include various cyber terrorism attacks such as Blackmailing Email Demand, Social Accounts Hacked etc. Presenting Signs For Various Digital Terrorism Attacks Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Attacked Network, Fraudulent Financial Transaction, Social Accounts Hacked. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Creating Transaction Monitoring Real Time ATM Fraud And Crime Detection Icons PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Slidegeeks has constructed Creating Transaction Monitoring Real Time ATM Fraud And Crime Detection Icons PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Enhancing CX Strategy Social Media Strategies For Customer Retention Pictures PDF
This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts. Retrieve professionally designed Enhancing CX Strategy Social Media Strategies For Customer Retention Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Deploying Banking Transaction Real Time Atm Fraud And Crime Detection Download PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Retrieve professionally designed Deploying Banking Transaction Real Time Atm Fraud And Crime Detection Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Actual Time Transaction Monitoring Software And Strategies Real Time ATM Fraud And Crime Detection Elements PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Retrieve professionally designed Actual Time Transaction Monitoring Software And Strategies Real Time ATM Fraud And Crime Detection Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF
This slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing, Malware, Blackmail Hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Exploitation IT Interview Schedule For New Professionals Icons PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking. Deliver and pitch your topic in the best possible manner with this cyber exploitation it interview schedule for new professionals icons pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Disaster Resilience Plan Current Situation Of The Client Company Designs PDF
This slide depicts the current situation of the client company by displaying the total number of breaches due to hacking, the number of errors, the percentage of social attacks, and so on.Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan Current Situation Of The Client Company Designs PDF bundle. Topics like Disaster Recovery, Facilities Management, Collaboration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. There are so many reasons you need a Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
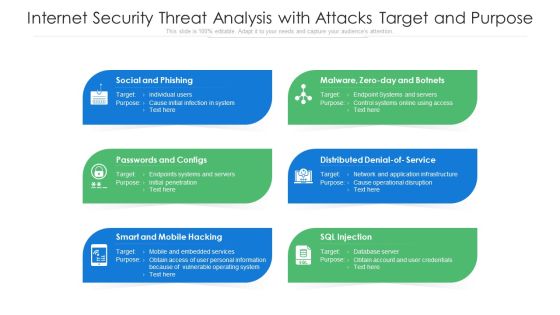
Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
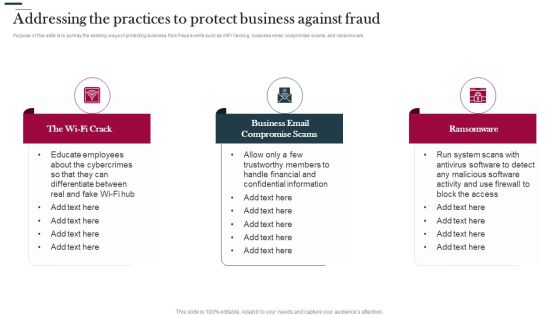
Various Strategies To Prevent Business Addressing The Practices To Protect Business Against Fraud Graphics PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Presenting Various Strategies To Prevent Business Addressing The Practices To Protect Business Against Fraud Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Business Email, Compromise Scams, Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Technology Disaster Recovery Plan Current Situation Of The Client Company Icons PDF
This slide depicts the current situation of the client company by displaying the total number of breaches due to hacking, the number of errors, the percentage of social attacks, and so on. Deliver and pitch your topic in the best possible manner with this Technology Disaster Recovery Plan Current Situation Of The Client Company Icons PDF. Use them to share invaluable insights on Organized, Social and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
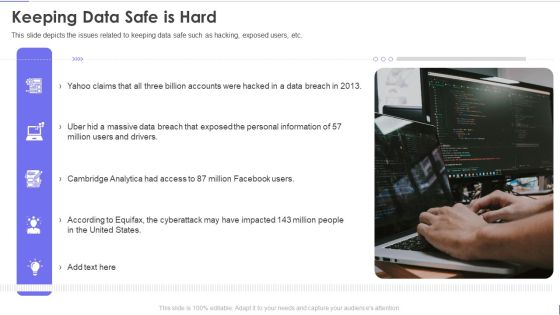
Evervault Capital Investment Elevator Pitch Deck Keeping Data Safe Is Hard Themes PDF
This slide depicts the issues related to keeping data safe such as hacking, exposed users, etc. This is a evervault capital investment elevator pitch deck keeping data safe is hard themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like keeping data safe is hard. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Scam Inquiry And Response Playbook Addressing The Practices To Protect Business Against Fraud Themes PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware. Make sure to capture your audiences attention in your business displays with our gratis customizable NAMEEEEEEEEEEEScam Inquiry And Response Playbook Addressing The Practices To Protect Business Against Fraud Themes PDFEEEEEEEEEEEEEEEE. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Process Flow Of Botnet Malware Attack Icons PDF
This slide illustrates flowchart of attack through botnet malware hacking. It includes transmitting specific string to C and C, C and C authorizes bot connection, etc. Persuade your audience using this Process Flow Of Botnet Malware Attack Icons PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware In Victim, Hacker Launches, Malware Reads. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
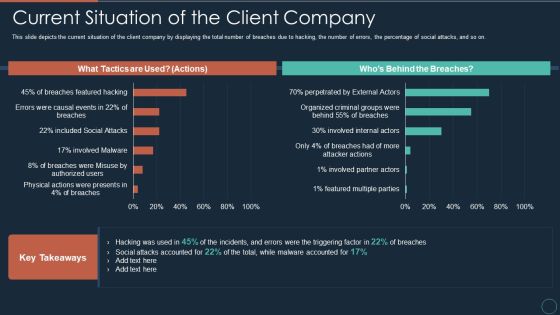
Implementing DRP IT Current Situation Of The Client Company Ppt PowerPoint Presentation Inspiration Deck PDF
This slide depicts the current situation of the client company by displaying the total number of breaches due to hacking, the number of errors, the percentage of social attacks, and so on.Deliver and pitch your topic in the best possible manner with this implementing drp it current situation of the client company ppt powerpoint presentation inspiration deck pdf Use them to share invaluable insights on featured multiple parties, involved partner actors, organized criminal groups and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Situation Of The Client Company Catastrophe Recovery Application Plan Guidelines PDF
This slide depicts the current situation of the client company by displaying the total number of breaches due to hacking, the number of errors, the percentage of social attacks, and so on. Deliver and pitch your topic in the best possible manner with this current situation of the client company catastrophe recovery application plan guidelines pdf. Use them to share invaluable insights on current situation of the client company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
AI And ML Driving Monetary Value For Organization Required Manpower Skills Set Data Icons PDF
Following slide shows details about required manpower skills set. Skills set covered are domain knowledge, machine learning, data visualization and hacking. Deliver and pitch your topic in the best possible manner with this ai and ml driving monetary value for organization required manpower skills set data icons pdf. Use them to share invaluable insights on data engineer, data scientist, devops engineer, data visualization, machine learning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

 Home
Home