Gap Analysis Of Security

Information Systems Security And Risk Management Plan Process For Information Security Risk Assessment Formats PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. This modern and well arranged Information Systems Security And Risk Management Plan Process For Information Security Risk Assessment Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Desktop Security Management Dashboard For Threat Tracking In Computer Security Guidelines PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative desktop security management dashboard for threat tracking in computer security guidelines pdf bundle. Topics like threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Kpis To Measure Information Security Risk Management Brochure PDF bundle. Topics like Between Failures, Times Attackers, Management Programme can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats Benchmarking With Security Operations Maturity Model Infographics PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting real time assessment of security threats benchmarking with security operations maturity model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like centralized forensic visibility, mean time to detect, mean time to respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Difference Between Cloud Security Solutions And Traditional IT Solutions Portrait PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses.Presenting Cloud Security Assessment Difference Between Cloud Security Solutions And Traditional IT Solutions Portrait PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Reduced Infrastructure, Resource Utilization, Diminished Opportunity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls.This is a Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Streamlining Employee Verification Process To Ensure People Security Microsoft PDF
This slide provides information about streamlining employee verification process at workplace to ensure people security by performing pre and post employee verification. This is a developing firm security strategy plan streamlining employee verification process to ensure people security microsoft pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like importance of employee verification process, pre and post employment verifications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
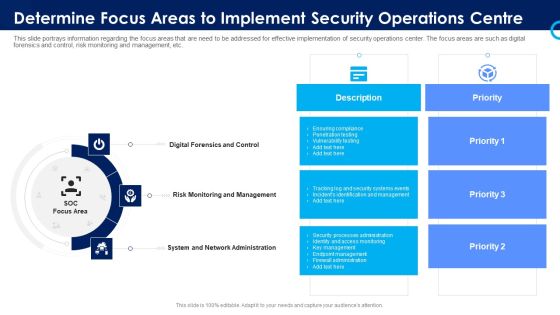
Organizational Security Solutions Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a organizational security solutions determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
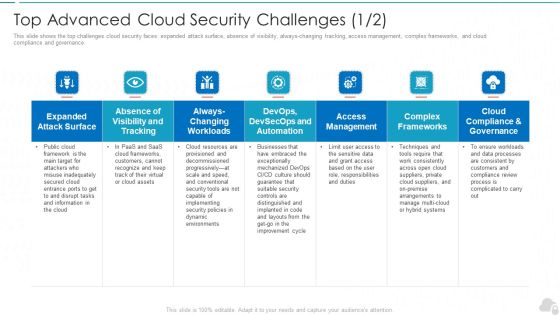
Top Advanced Cloud Security Challenges Cloud Computing Security IT Ppt Slides Clipart Images PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver and pitch your topic in the best possible manner with this top advanced cloud security challenges cloud computing security it ppt slides clipart images pdf. Use them to share invaluable insights on cloud compliance and governance, access management, complex frameworks, visibility and tracking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Presenting Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Expanded Attack, Access Management, Complex Frameworks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Developing IT Security Strategy Kpis To Measure Information Security Risk Management Graphics PDF today and make your presentation stand out from the rest.

Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF
This slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present like a pro with Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
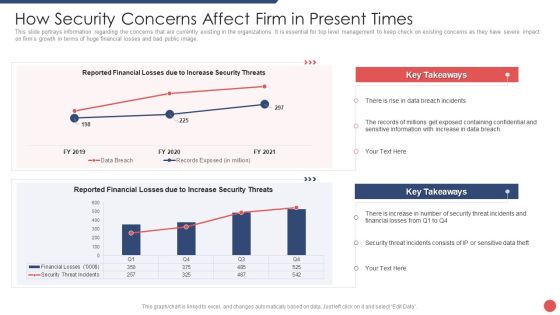
Security Functioning Centre How Security Concerns Affect Firm In Present Times Ideas PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver and pitch your topic in the best possible manner with this security functioning centre how security concerns affect firm in present times ideas pdf. Use them to share invaluable insights on financial, security threat, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. This Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Smart Home Security Solutions Company Profile Security Company Business Model Infographics PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Security Company Business Model Infographics PDF bundle. Topics like Target Market Revenue, Stream Cost Structure, Customer Relationship Products, Customer Segments Key can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
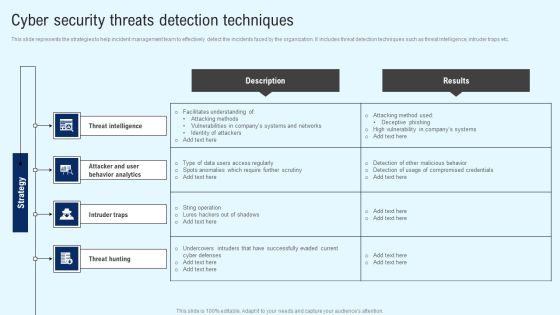
Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.

Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Best Data Security Software Next Steps For Company Online Database Security Infographics PDF
Presenting this set of slides with name best data security software next steps for company online database security infographics pdf. This is a two stage process. The stages in this process are discuss the desired changes, accept the proposal, once we get the notification of your proposal acceptance, we will send you the separate copy of the signed contract for your record. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Security And Human Resource Services Business Profile Corporate And Industrial Security Formats PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Present like a pro with Security And Human Resource Services Business Profile Corporate And Industrial Security Formats PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
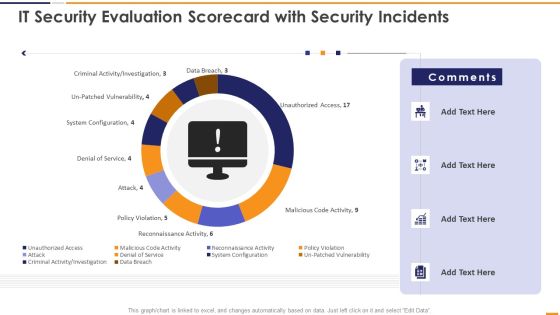
IT Security Evaluation Scorecard With Security Incidents Ppt Pictures Vector PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Security Incidents Ppt Pictures Vector PDF. Use them to share invaluable insights on Unauthorized Access Sales, Malicious Code Activity, Reconnaissance Activity Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Are you searching for a Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF from Slidegeeks today.

Information Systems Security And Risk Management Plan Timeline For Information Security Risk Management Training Inspiration PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Present like a pro with Information Systems Security And Risk Management Plan Timeline For Information Security Risk Management Training Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Information Systems Security And Risk Management Plan Reporting Structure For Information Security Risk Management Demonstration PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. This Information Systems Security And Risk Management Plan Reporting Structure For Information Security Risk Management Demonstration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Information Systems Security And Risk Management Plan Kpis To Measure Information Security Risk Management Template PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Kpis To Measure Information Security Risk Management Template PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
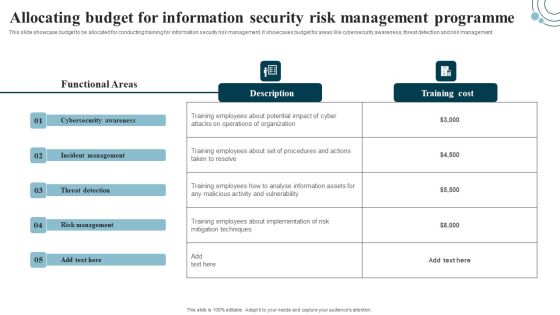
Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Allocating Budget For Information Security Risk Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
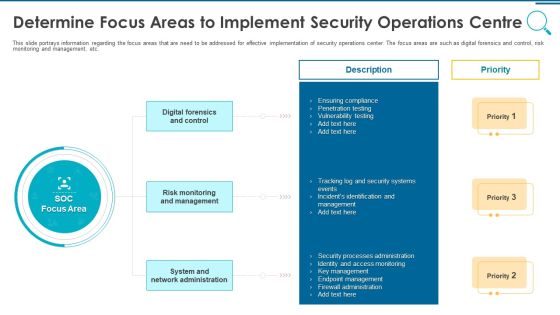
Information And Technology Security Operations Determine Focus Areas To Implement Security Operations Centre Download PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a information and technology security operations determine focus areas to implement security operations centre download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
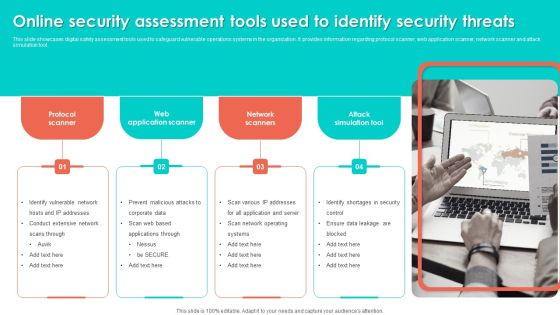
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
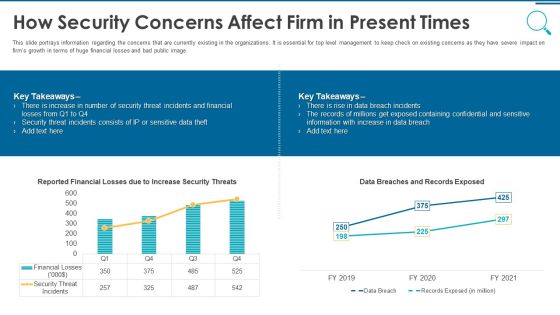
Information And Technology Security Operations How Security Concerns Affect Firm In Present Times Rules PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative information and technology security operations how security concerns affect firm in present times rules pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
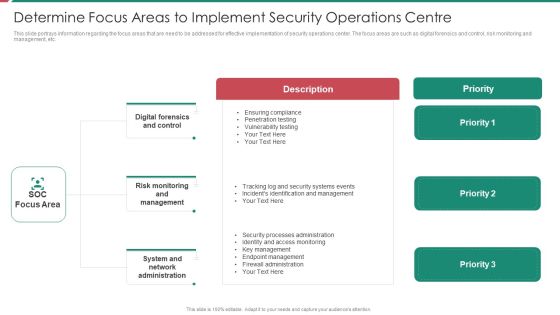
Security And Process Integration Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security and process integration determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.This Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Presenting Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Partners, Contract Breaches, Against The Organization In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Security Training Program Frameworks Contd Rules PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks contd rules pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
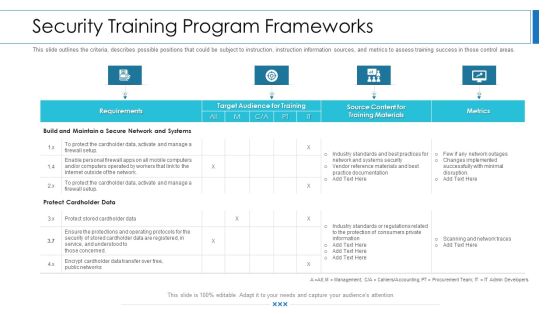
Workforce Security Realization Coaching Plan Security Training Program Frameworks Brochure PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan security training program frameworks brochure pdf. Use them to share invaluable insights on requirements, target audience for training, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

CYBER Security Breache Response Strategy Cyber Security Incident Communication Strategy Topics PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Present like a pro with CYBER Security Breache Response Strategy Cyber Security Incident Communication Strategy Topics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Retrieve professionally designed Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
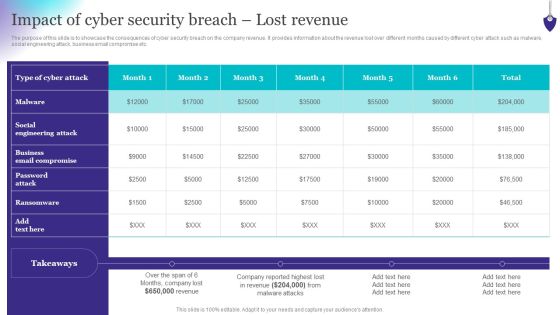
Organizing Security Awareness Impact Of Cyber Security Breach Lost Revenue Topics PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Organizing Security Awareness Impact Of Cyber Security Breach Lost Revenue Topics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Organizational Security Solutions How Security Concerns Affect Firm In Present Times Structure PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative organizational security solutions how security concerns affect firm in present times structure pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
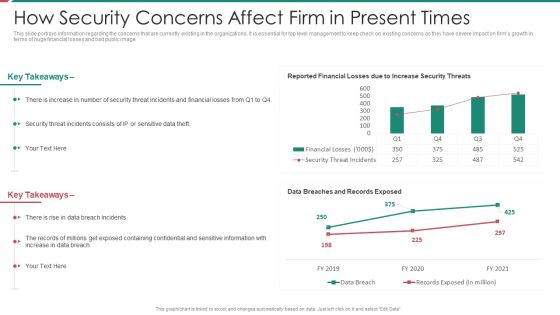
Security And Process Integration How Security Concerns Affect Firm In Present Times Microsoft PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative security and process integration how security concerns affect firm in present times microsoft pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Information Security Loss On Organization Information Security Risk Administration Infographics PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Impact Of Information Security Loss On Organization Information Security Risk Administration Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
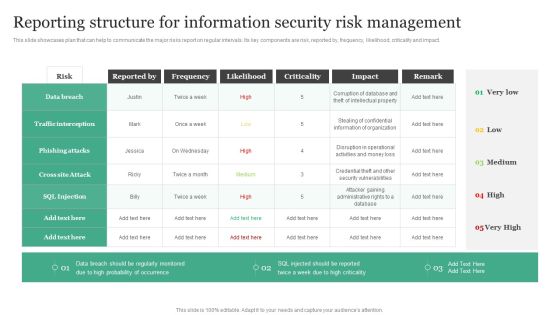
Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Do you know about Slidesgeeks Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.This modern and well-arranged Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Developing IT Security Strategy Reporting Structure For Information Security Risk Sample PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Reporting Structure For Information Security Risk Sample PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Safety Lock Cyber Security Global Security Ppt PowerPoint Presentation Complete Deck
Boost your confidence and team morale with this well-structured safety lock cyber security global security ppt powerpoint presentation complete deck. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of fourteen slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

Security Administration Strategy Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this security administration strategy security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Target Market Assessment For Facility Security Corporation Brochure PDF
This slide covers the target audience analysis of company with facility security services. It includes analysis details such as key demographics, psychographics, challenges, preferred channels, and preferred content type. Pitch your topic with ease and precision using this Target Market Assessment For Facility Security Corporation Brochure PDF. This layout presents information on Key Demographics, Preferred Content Types, Preferred Channels. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Overview Of Security Risk Management Process Formats PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative overview of security risk management process formats pdf bundle. Topics like strategic context, vulnerability assessment, security context, risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
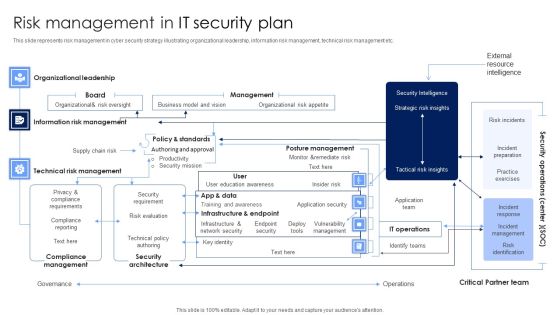
Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Private Security Service Provider Company Summary Report Clipart PDF
This slide provide information of firm providing security services to safeguards life of human beings who are facing threats. It includes elements such as about, category, services, company stats, packages, our service benefits. Pitch your topic with ease and precision using this Private Security Service Provider Company Summary Report Clipart PDF. This layout presents information on Provide World, Security Guard, Security Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
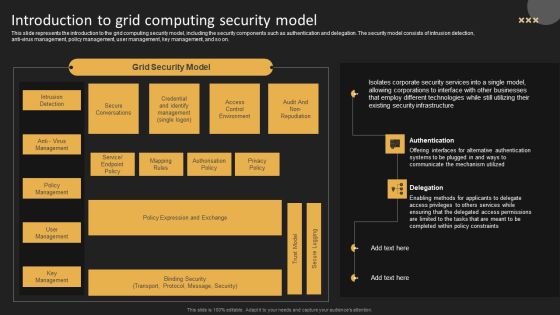
Introduction To Grid Computing Security Model Template PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti virus management, policy management, user management, key management, and so on. Get a simple yet stunning designed Introduction To Grid Computing Security Model Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Introduction To Grid Computing Security Model Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Computing Services Security Architecture Assessment Infographics PDF
The slideshows an assessment model of CSP cloud service security. It includes identification of existing warrant, verification of certificates and reports, evidence review and additional information collection about third party warrant and certificates. Showcasing this set of slides titled Cloud Computing Services Security Architecture Assessment Infographics PDF. The topics addressed in these templates are Cloud Control Profile, Administrative Need, Safety Security Needs. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Assessment Platform As A Service Paas Ideas PDF
This slide defines the platform as a service model of cloud security and the various advantages and disadvantages of the PaaS model.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Platform As A Service Paas Ideas PDF bundle. Topics like Customers Empowering, Specialists Collaborate, Adaptable In Structure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home