Gap Analysis Of Security

Cyber Security For Your Organization Risk Assessment Matrix Ppt Ideas PDF
Presenting this set of slides with name cyber security for your organization risk assessment matrix ppt ideas pdf. This is a one stage process. The stages in this process are insignificant, minor, severity, risk, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Risk Assessment Matrix Ppt Show Design Ideas PDF
Presenting this set of slides with name computer security incident handling risk assessment matrix ppt show design ideas pdf. This is a four stage process. The stages in this process are minor, significant, serious, catastrophic, insignificant. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Risk Assessment Matrix Ppt Visuals PDF
Presenting this set of slides with name strategies to mitigate cyber security risks risk assessment matrix ppt visuals pdf. This is a four stage process. The stages in this process are insignificant, minor significant, serious, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security Risk Evaluation Risk Assessment Matrix With Vulnerability And Threat Level Mockup PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Risk Assessment Matrix With Vulnerability And Threat Level Mockup PDF bundle. Topics like Risk Assessment, Vulnerability Level, Treat Level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Alert On Computer Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Computer PowerPoint Templates because they pinpoint the core values of your organisation. Use our Technology PowerPoint Templates because these ideas abound in the strong branches of your brain. Download our Signs PowerPoint Templates because health of the determines the quality of our lives. Present our Business PowerPoint Templates because your fledgling career is in the chrysallis stage. Nurture it and watch it grow into a beautiful butterfly. Download and present our Triangles PowerPoint Templates because it unravels each one for your audience while setting key timelines as you go along.Use these PowerPoint slides for presentations relating to Alert button on a black computer keyboard, computer, technology, signs, business, triangles. The prominent colors used in the PowerPoint template are Red, Black, Yellow. We assure you our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Customers tell us our keyboard PowerPoint templates and PPT Slides are Classic. You can be sure our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Beautiful. People tell us our a PowerPoint templates and PPT Slides are Splendid. Presenters tell us our Alert On Computer Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Adorable. People tell us our technology PowerPoint templates and PPT Slides are Efficient.

1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Welcome to our selection of the 1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Cyber Security Process Steps With Icons Ppt PowerPoint Presentation Summary Slide
Presenting this set of slides with name cyber security process steps with icons ppt powerpoint presentation summary slide. This is a four stage process. The stages in this process are assess, evaluate, build, execute. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
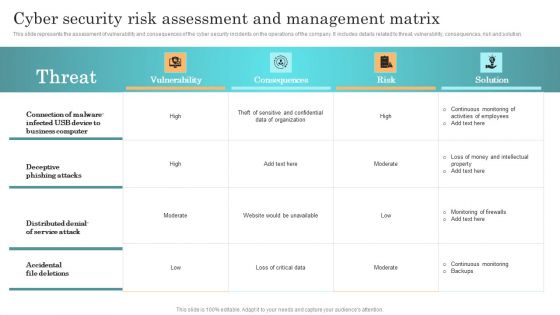
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF. Use them to share invaluable insights on Current Assessment, Determining Actors, Understanding Frequency and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Three Staged Security Process Infographic Ppt PowerPoint Presentation File Infographic Template PDF
Presenting this set of slides with name three staged security process infographic ppt powerpoint presentation file infographic template pdf. This is a three stage process. The stages in this process are assess and learn, strategize and plan, implement and support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Key To Money Savings Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Money PowerPoint Templates because they will help you to organise the logic of your views. Download our Finance PowerPoint Templates because you envisage some areas of difficulty in the near future. The overall financial situation could be a source of worry. Download our Business PowerPoint Templates because it will demonstrate the strength of character under severe stress. Shine the torch ahead and bring the light to shine on all. Download our Services PowerPoint Templates because you understand the illness and its causes. Download our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities.Use these PowerPoint slides for presentations relating to Financial money saveing security, money, business, marketing, services, finance . The prominent colors used in the PowerPoint template are Blue, Blue light, Yellow. We assure you our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Wonderful. Customers tell us our marketing PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. You can be sure our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212 are designed by a team of presentation professionals. People tell us our money PowerPoint templates and PPT Slides will get their audience's attention. Presenters tell us our Key To Money Savings Security PowerPoint Templates PPT Backgrounds For Slides 1212 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our services PowerPoint templates and PPT Slides are Amazing.
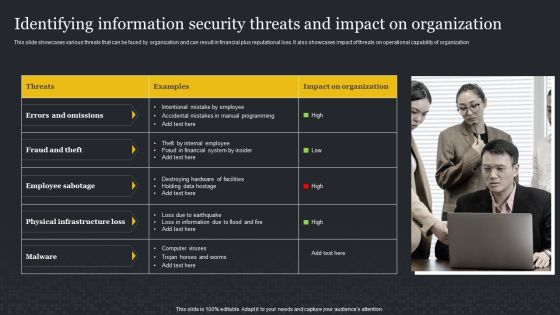
Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Retrieve professionally designed Organizations Risk Management And IT Security Technical Security Control Model With Supporting Function Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Slidegeeks has constructed Financial Impact Of Information Security Attacks Cybersecurity Risk Assessment Template PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Addressing Quality Check Schedule Food Security Excellence Ppt Pictures Background PDF
Quality check will be done regular intervals. These checks can be on daily, weekly, monthly, quarterly basis by reviewing product on several parameters. Deliver an awe inspiring pitch with this creative addressing quality check schedule food security excellence ppt pictures background pdf bundle. Topics like analyzers, maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

New Website Launch Strategy Website Security Management Action Plan Portrait PDF
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Slidegeeks is here to make your presentations a breeze with New Website Launch Strategy Website Security Management Action Plan Portrait PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Effective IT Risk Management Process Information Security Risk Assessment Formats PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this NAMEEEEEE. Use them to share invaluable insights on system failure, potential, vulnerability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Security Assessment Matrix Of Cyber Risks Ppt PowerPoint Presentation Icon Styles PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative info security assessment matrix of cyber risks ppt powerpoint presentation icon styles pdf bundle. Topics like employee devices, webserver network, cloud, retail, data center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

IT Security Assessment Matrix Of IT Risks Ppt Slides Visual Aids PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative information technology security assessment matrix of it risks ppt outline objects pdf bundle. Topics like assessment matrix of it risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Comparative Assessment Of Various Threat Agents Slides PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management comparative assessment of various threat agents slides pdf. Use them to share invaluable insights on comparative assessment of various threat agents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
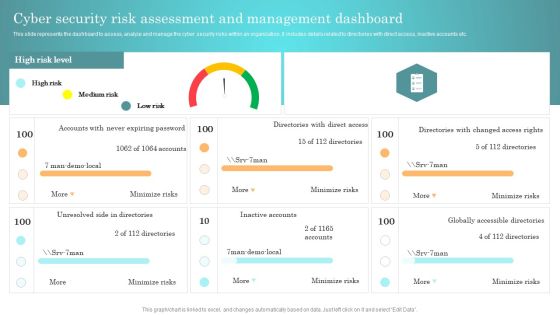
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF bundle. Topics like Spend Vs Budget, Return On Investment, IT Department Revenue, IT Costs Vs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
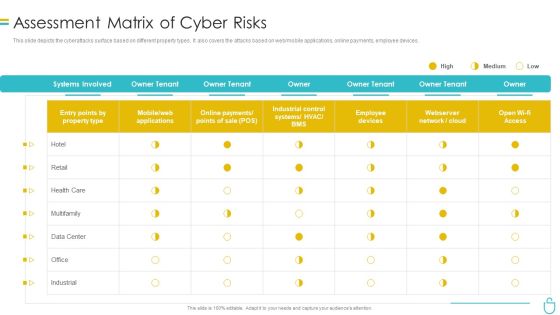
Information Security Assessment Matrix Of Cyber Risks Ppt Infographics Sample PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative information security assessment matrix of cyber risks ppt infographics sample pdf bundle. Topics like employee devices, retail, industrial, owner can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
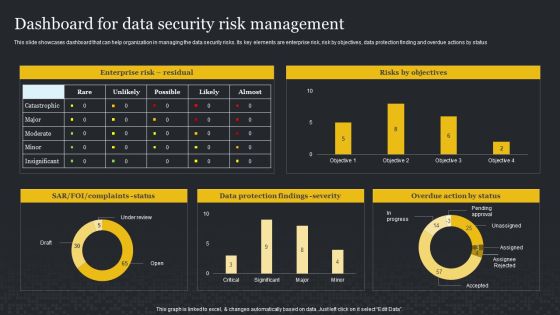
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
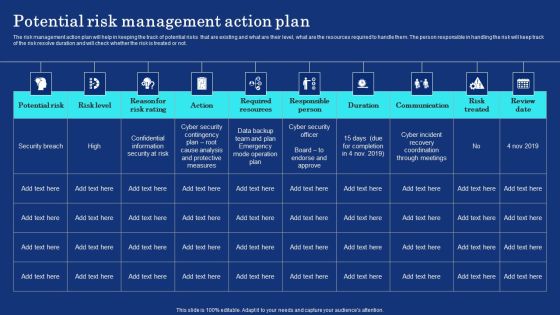
Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF can be your best option for delivering a presentation. Represent everything in detail using Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Companys Data Safety Recognition Security Training Program Frameworks Contd Infographics PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this companys data safety recognition security training program frameworks contd infographics pdf. Use them to share invaluable insights on requirements, target audience, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Risk Management Approach Introduction Encountered Risks Summary And Their Impact Assessment Professional PDF
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Encountered Risks Summary And Their Impact Assessment Professional PDF. Use them to share invaluable insights on Moderate Inherent Risk, Risks By Category, Financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF
The following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Take your projects to the next level with our ultimate collection of Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Are you searching for a Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF from Slidegeeks today.

Table Of Contents For Security Control Techniques For Real Estate Project Download PDF
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Security Control Techniques For Real Estate Project Download PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Data Breach Prevention Recognition Security Training Program Frameworks Contd Template PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security training program frameworks contd template pdf bundle. Topics like measures, instruction information sources, target audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
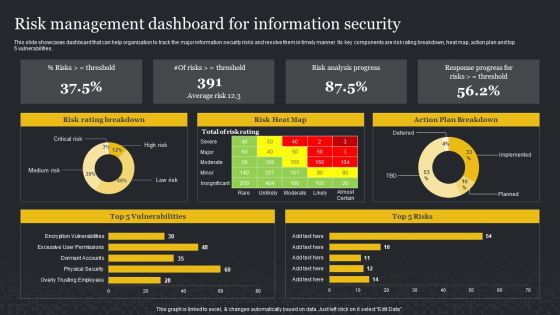
Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Business Mobile Device Security Management And Mitigation Tips Pictures PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Implementing Cyber Security Incident Management Guidelines PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Corporate Security And Risk Management Addressing Natural Calamities Posing Threat Information PDF
This slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing natural calamities posing threat information pdf bundle. Topics like addressing natural calamities posing threat to organization infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.

Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF
The following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Slidegeeks has constructed Impact Of Cyber Safety Security Measures Ppt PowerPoint Presentation File Layouts PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
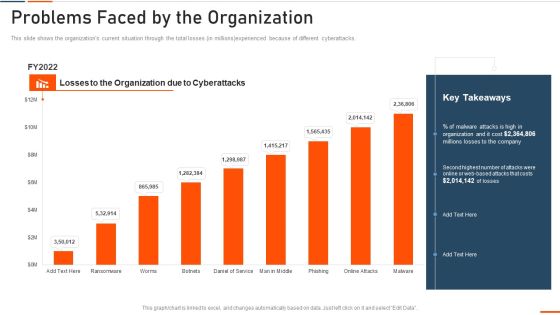
Information Technology Security Problems Faced By The Organization Ppt Ideas Visuals PDF
This slide shows the organizations current situation through the total losses ins millionsexperienced because of different cyberattacks. Deliver an awe inspiring pitch with this creative information technology security problems faced by the organization ppt ideas visuals pdf bundle. Topics like problems faced by the organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Present like a pro with Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF
This slide shows that information privacy laws are beneficial for both social media platforms and their users, as it protects companies from any unnecessary penalties while providing users the required data protection. Get a simple yet stunning designed Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Assessing Cost Of Information Breach In Different Countries Guidelines PDF.

Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information And Technology Security Operations Secops Dashboard To Track Vulnerabilities Information PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations secops dashboard to track vulnerabilities information pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
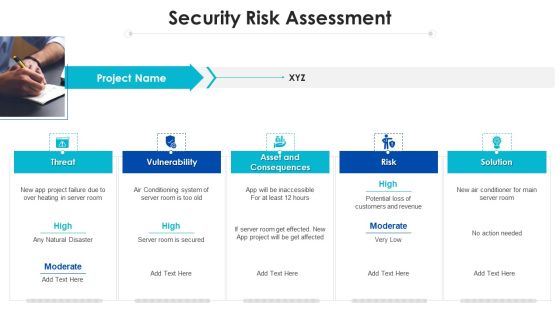
Project Assessment Templates Bundle Security Risk Assessment Ppt Infographic Template Guide PDF
This is a Project Assessment Templates Bundle Security Risk Assessment Ppt Infographic Template Guide PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Threat, Asset Consequences, Risk Solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Enhanced Protection Corporate Event Administration Determine Focus Areas To Implement Security Operations Centre Icons PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a enhanced protection corporate event administration determine focus areas to implement security operations centre icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
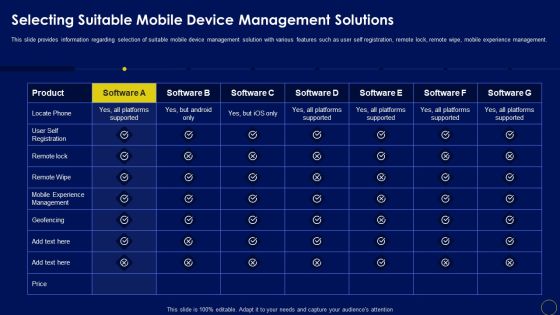
Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.

How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

 Home
Home