Executive Summary Security

Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
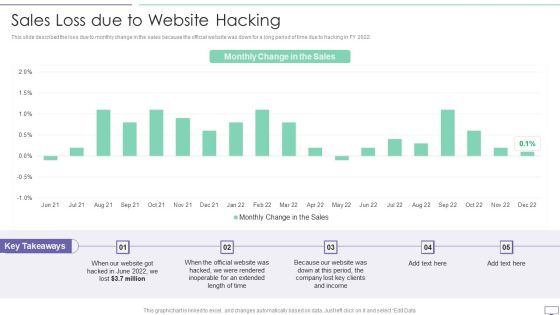
IT Security Hacker Sales Loss Due To Website Hacking Introduction PDF
This slide described the loss due to monthly change in the sales because the official website was down for a long period of time due to hacking in FY 2022.Deliver an awe inspiring pitch with this creative IT Security Hacker Sales Loss Due To Website Hacking Introduction PDF bundle. Topics like Inoperable, Extended, Clients Income can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Do you know about Slidesgeeks Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
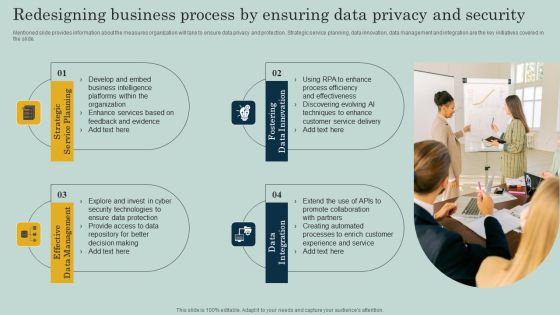
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Create an editable Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides
Using this ready-made PowerPoint slide, you can incorporate your own data to make an impact with your business innovation and clarity of goals. Use this brilliantly designed Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides to showcase how ultimately all business concepts are related. This presentation template can also be used to record resource allocation in a visual form. The twenty one Slide Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides is suitable for all your business needs, where you need to make sure that all bases are covered. Download this PPT template now to start a journey on your chosen business, with customer satisfaction the key aim.

Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
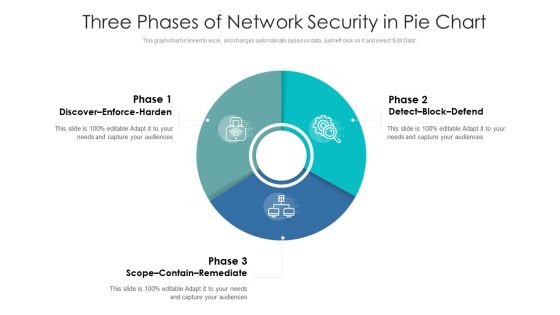
Three Phases Of Network Security In Pie Chart Ppt PowerPoint Presentation Gallery Graphics Download PDF
Pitch your topic with ease and precision using this three phases of network security in pie chart ppt powerpoint presentation gallery graphics download pdf. This layout presents information on discover enforce harden, detect block defend, scope contain remediate. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
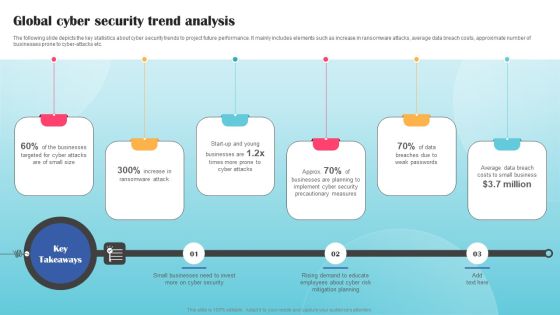
Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. The Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
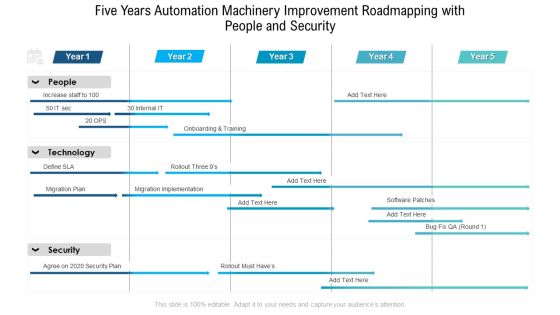
Five Years Automation Machinery Improvement Roadmapping With People And Security Download
Presenting our innovatively structured five years automation machinery improvement roadmapping with people and security download Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

IT Risk Management Process Organizations Risk Management And IT Security Slides PDF
This slide highlights the information technology risk management process which includes risks scope, risks assessment, risk treatment and risk communication along with operations and product procedure. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Risk Management Process Organizations Risk Management And IT Security Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Risk Management Process Organizations Risk Management And IT Security Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Create an editable Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Security Awareness Checklist To Ensure It Asset Protection Ppt Model Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Slidegeeks is here to make your presentations a breeze with Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Incident Response Techniques Deployement Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. This Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF
This slide represents the seven principles of GDPR law, including lawfulness and transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, accountability. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Info Security Implementation Of Strong Password Policy Ppt PowerPoint Presentation File Slide Download PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Deliver an awe inspiring pitch with this creative info security implementation of strong password policy ppt powerpoint presentation file slide download pdf bundle. Topics like implementation strong, password policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
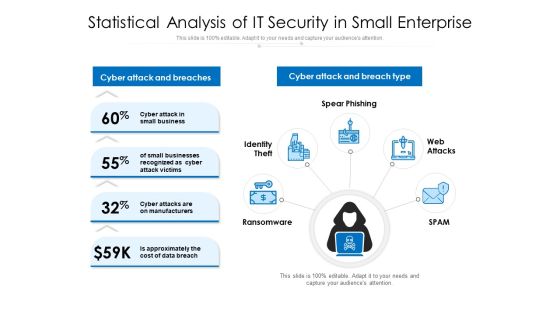
Statistical Analysis Of IT Security In Small Enterprise Ppt PowerPoint Presentation Ideas Design Inspiration PDF
Persuade your audience using this statistical analysis of it security in small enterprise ppt powerpoint presentation ideas design inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber attack and breaches, cyber attack and breach type, spear phishing, web attacks, spam, ransomware, identity theft. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Information Systems Security And Risk Management Plan Our Mission Infographics PDF
The Information Systems Security And Risk Management Plan Our Mission Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Three Seps Of Enterprise Network Security With Icons Ppt PowerPoint Presentation Icon Slide Portrait PDF
Presenting three seps of enterprise network security with icons ppt powerpoint presentation icon slide portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, scope contain remediate, detect block defend. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
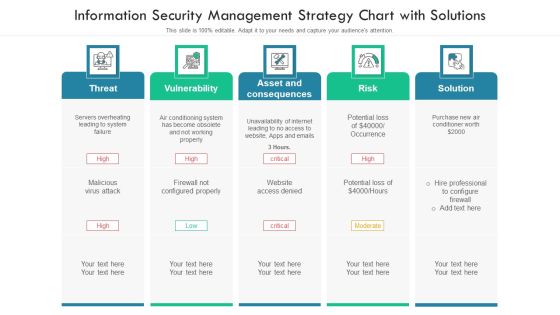
Information Security Management Strategy Chart With Solutions Ppt PowerPoint Presentation File Slides PDF
Persuade your audience using this information security management strategy chart with solutions ppt powerpoint presentation file slides pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including threat, vulnerability, risk, solution. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack.Welcome to our selection of the Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
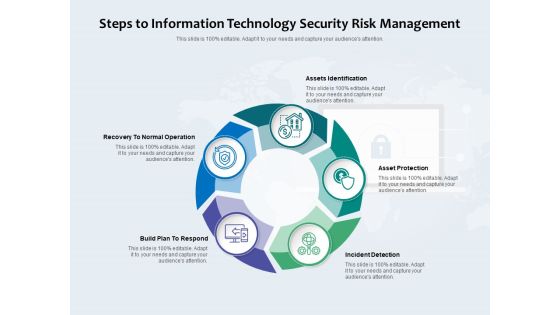
Steps To Information Technology Security Risk Management Ppt PowerPoint Presentation Gallery Example File PDF
Presenting steps to information technology security risk management ppt powerpoint presentation gallery example file pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including assets identification, asset protection, incident detection, build plan to respond, recovery to normal operation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
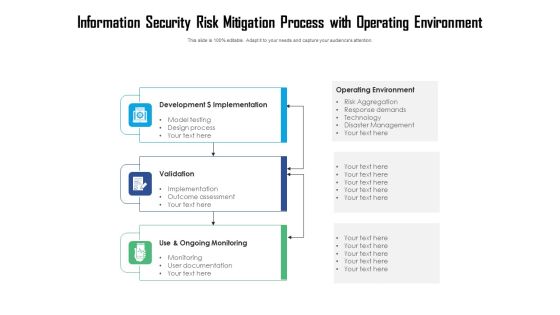
Information Security Risk Mitigation Process With Operating Environment Ppt PowerPoint Presentation File Templates PDF
Persuade your audience using this information security risk mitigation process with operating environment ppt powerpoint presentation file templates pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including development dollar implementation, validation, use and ongoing monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. Find highly impressive Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Information Systems Security And Risk Management Plan Vulnerability Rating For Risk Identification Slides PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
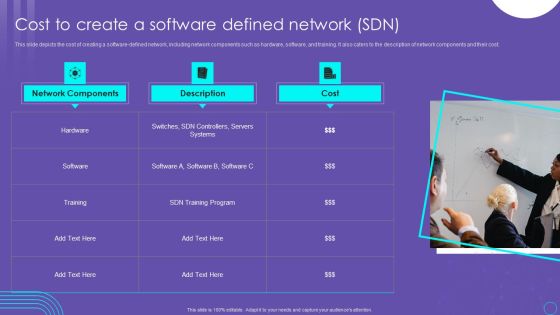
SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF
This slide depicts the cost of creating a software defined network, including network components such as hardware, software, and training. It also caters to the description of network components and their cost. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into SDN Security Architecture Cost To Create A Software Defined Network SDN Slides PDF
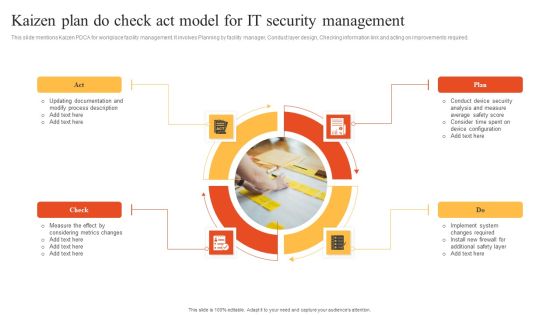
Kaizen Plan Do Check Act Model For IT Security Management Information PDF
This slide mentions Kaizen PDCA for workplace facility management. It involves Planning by facility manager, Conduct layer design, Checking information link and acting on improvements required. Presenting Kaizen Plan Do Check Act Model For IT Security Management Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Check, Plan, Act. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Advantages For IT Security In Business Ppt PowerPoint Presentation Infographic Template Microsoft PDF
Presenting advantages for it security in business ppt powerpoint presentation infographic template microsoft pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including valuable information protection, evade loss of crucial data, risk mitigation, privacy of customer and employee is ensured, recovery time is improved. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.This Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF.

Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF
This slide shows that information privacy laws are beneficial for both social media platforms and their users, as it protects companies from any unnecessary penalties while providing users the required data protection. Get a simple yet stunning designed Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
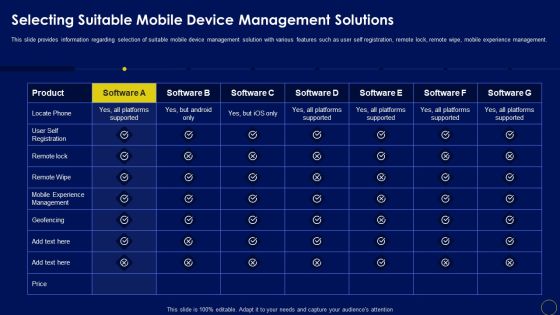
Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.

Information Security Prepare Data Backup For Sensitive Information Ppt Introduction PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information security prepare data backup for sensitive information ppt introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, manipulation, services, natural disasters, secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
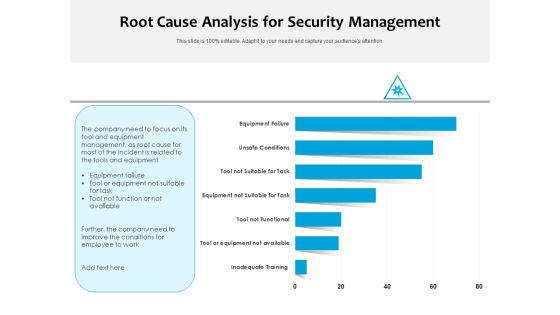
Root Cause Analysis For Security Management Ppt PowerPoint Presentation Slides Grid PDF
Pitch your topic with ease and precision using this root cause analysis for security management ppt powerpoint presentation slides grid pdf. This layout presents information on inadequate training, tool or equipment not available, tool not functional, equipment not suitable for task, tool not suitable for task, unsafe conditions, equipment failure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Security Data Audit Report With Description Ppt PowerPoint Presentation Inspiration Example PDF
Showcasing this set of slides titled security data audit report with description ppt powerpoint presentation inspiration example pdf. The topics addressed in these templates are attribute, description, audit status, comments, data backup, data and application management, data disaster recovery system integration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Compliance Framework With Individual Rights Ppt PowerPoint Presentation Infographics Graphics Pictures
Presenting this set of slides with name cyber security compliance framework with individual rights ppt powerpoint presentation infographics graphics pictures. This is a twelve stage process. The stages in this process are raise awareness, information held, communicating privacy, individual rights, subject access requests, legalities of processing personal data, consent, protecting childrens data, data breaches, data protection by design, data protection officers, international work. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
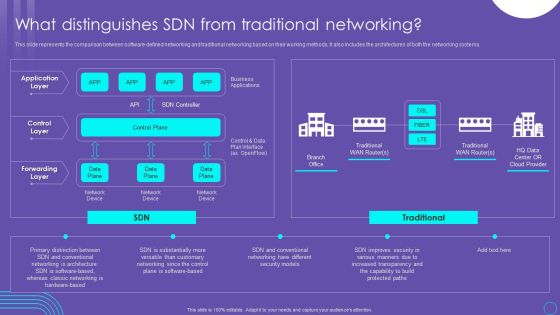
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Based Email Security Market Report Table Of Contents Ppt Inspiration Vector PDF
Presenting cloud based email security market report table of contents ppt inspiration vector pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like market introduction, market dynamics, issues faced by companies, kpi dashboard, market by segments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety Dominos Business Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Business PowerPoint Templates because it helps you to project your enthusiasm and single mindedness to your colleagues. Download our Finance PowerPoint Templates because it helps you to satiate the brains of your team with a taste of the final product. Present our Future PowerPoint Templates because this PPt Enlighten others on your team with your views. Use our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download and present our Shapes PowerPoint Templates because you have an idea of which you are sure.Use these PowerPoint slides for presentations relating to Domino effect and business, business, finance, future, marketing, shapes. The prominent colors used in the PowerPoint template are Green, Yellow, Gray. We assure you our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Efficacious. Customers tell us our business PowerPoint templates and PPT Slides are Gorgeous. You can be sure our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 will help you be quick off the draw. Just enter your specific text and see your points hit home. People tell us our and PowerPoint templates and PPT Slides are Pretty. Presenters tell us our Safety Dominos Business Security PowerPoint Templates PPT Backgrounds For Slides 1212 will make the presenter look like a pro even if they are not computer savvy. People tell us our shapes PowerPoint templates and PPT Slides are One-of-a-kind.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Image Of Internet Security Virus PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Present our Arrows PowerPoint Templates because You can Bind your ideas with our PowerPoint Templates and Slides. They will add great value to the worth of your package. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use our Finance PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Use our Success PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level.Use these PowerPoint slides for presentations relating to Internet Virus, technology, arrows, signs, finance, success. The prominent colors used in the PowerPoint template are Yellow, Black, White. Professionals tell us our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. You can be sure our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. We assure you our Image Of Internet Security Virus PowerPoint Templates PPT Backgrounds For Slides 0113 will make you look like a winner. PowerPoint presentation experts tell us our arrows PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words.

Security Management Plan Steps In Detail Adopting Access Controls Demonstration PDF
Presenting security management plan steps in detail adopting access controls demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like logical access controls, control implementation, physical access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home