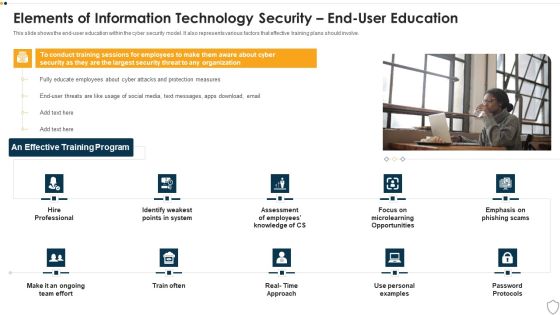
IT Security Elements Of Information Technology Security End User Education Ppt Show Maker PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a it security elements of information technology security end user education ppt show maker pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of information technology security end user education. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security What Are The Benefits Of Information Technology Security Ppt Layouts Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a it security what are the benefits of information technology security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, process, potential threats, security devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
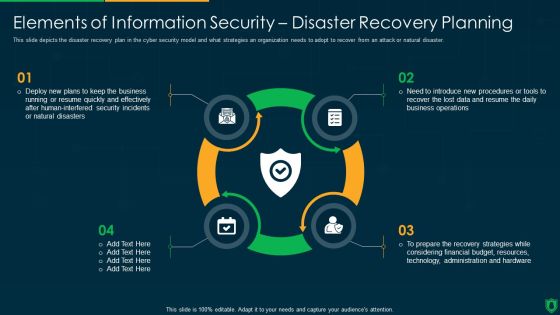
Info Security Elements Of Information Security Disaster Recovery Planning Ppt PowerPoint Presentation Gallery Designs PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a info security elements of information security disaster recovery planning ppt powerpoint presentation gallery designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deploy new plans, quickly and effectively, security incidents, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Roadmap For Information Security Training Ppt PowerPoint Presentation File Inspiration PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a info security roadmap for information security training ppt powerpoint presentation file inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, personal information, safe and computing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Exploitation IT Budget For IT Spending By The Company Professional PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
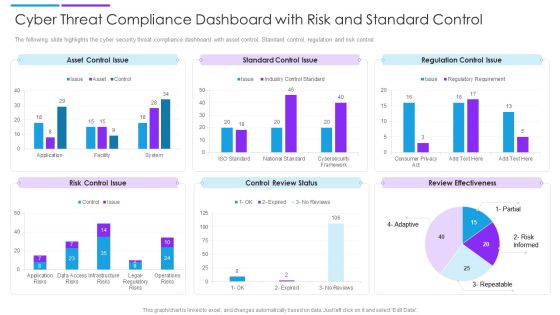
Cyber Threat Compliance Dashboard With Risk And Standard Control Sample PDF
The following slide highlights the cyber security threat compliance dashboard with asset control. Standard control, regulation and risk control. Showcasing this set of slides titled cyber threat compliance dashboard with risk and standard control sample pdf. The topics addressed in these templates are asset control issue, standard control issue, regulation control issue. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Deliver an awe inspiring pitch with this creative Sensing Components Of Cyber Physical Systems Ppt Ideas Graphics Example PDF bundle. Topics like Processing Data, Information, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Revenue Losses Cloud Computing Security IT Ppt Ideas Rules PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. This is a cloud security threats revenue losses cloud computing security it ppt ideas rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cyber threats, revenue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Dashboard For Threat Tracking In Computer Security Guidelines PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative desktop security management dashboard for threat tracking in computer security guidelines pdf bundle. Topics like threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Common Methods Used To Threaten Computer Security Template PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a desktop security management common methods used to threaten computer security template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, services, network, database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Common Methods Used To Threaten Information Technology Security Ppt Layouts Graphics PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a it security common methods used to threaten information technology security ppt layouts graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
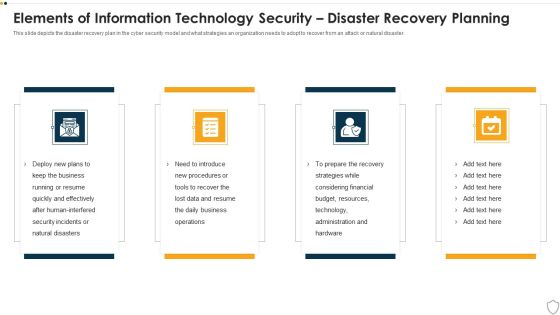
IT Security Elements Of Information Technology Security Disaster Recovery Planning Ppt Infographics Design Ideas PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting it security elements of information technology security disaster recovery planning ppt infographics design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, financial, budget, resources, effectively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security What Is Information Technology Security And How Does IT Work Ppt Icon Smartart
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Presenting it security what is information technology security and how does it work ppt icon smartart to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like techniques, servers, natural disasters. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Dashboard For Threat Tracking In Information Technology Security Ppt Inspiration Gallery PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative it security dashboard for threat tracking in information technology security ppt inspiration gallery pdf bundle. Topics like current risk status, threat report, risk by threats, threats based on role, threats by owners can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
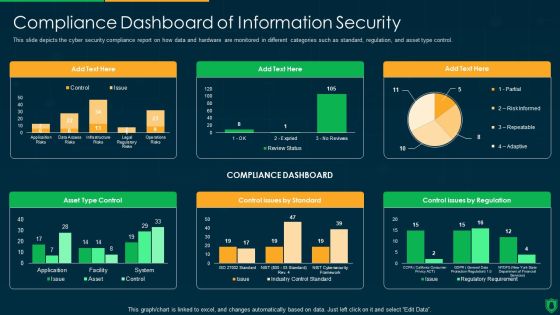
Info Security Compliance Dashboard Of Information Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative info security compliance dashboard of information security ppt powerpoint presentation file graphics download pdf bundle. Topics like compliance dashboard, asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Dashboard For Threat Tracking In Information Security Ppt PowerPoint Presentation File Example Introduction PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative info security dashboard for threat tracking in information security ppt powerpoint presentation file example introduction pdf bundle. Topics like threats by owners, risk by threats, threat report, monthly threat status, current risk status, threats based on role can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
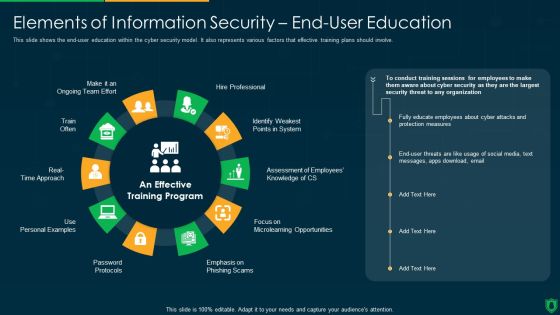
Info Security Elements Of Information Security End User Education Ppt PowerPoint Presentation File Example File PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Presenting info security elements of information security end user education ppt powerpoint presentation file example file pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like hire professional, emphasis on phishing scam, password protocols, train often. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Checklist Backup And Data Recovery Ppt Layouts Infographic Template PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting Cloud Information Security Cloud Security Checklist Backup And Data Recovery Ppt Layouts Infographic Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Plan, Cyber Attacks, Plans Timely. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cyber Threats, Organizations Could, Drastic Decrease. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Organizing Security Awareness Pricing Plan Of Security Awareness Packages Diagrams PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Take your projects to the next level with our ultimate collection of Organizing Security Awareness Pricing Plan Of Security Awareness Packages Diagrams PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Boost your pitch with our creative Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Security How Is Automation Used In Data Security Ppt Model Graphics Template PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting information security how is automation used in data security ppt model graphics template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security How Is Automation Used In Information Technology Security Ppt Diagram Lists PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting it security how is automation used in information technology security ppt diagram lists pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Security How Is Automation Used In Information security Ppt PowerPoint Presentation Gallery Samples PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting info security how is automation used in information security ppt powerpoint presentation gallery samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Security Latest Threats In Information Security Ppt PowerPoint Presentation Gallery Shapes PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a info security latest threats in information security ppt powerpoint presentation gallery shapes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like most recent, cyber threats reported, dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF
This slide showcases software that can help organization to monitor and manage the risk. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc .Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Selecting Suitable Software For Information Security Risk Management Introduction PDF. Use them to share invaluable insights on Vulnerability Management, Centralized Repository, Intelligent Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Selecting Suitable Software For Information Security Risk Management Information Security Risk Administration Sample PDF
This slide showcases software that can help organization to monitor and manage the risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. Want to ace your presentation in front of a live audience Our Selecting Suitable Software For Information Security Risk Management Information Security Risk Administration Sample PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Key Safety Audits To Stop Cyber Attacks Ppt PowerPoint Presentation File Example Topics PDF
Persuade your audience using this key safety audits to stop cyber attacks ppt powerpoint presentation file example topics pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including inventory, secure configurations, continuous vulnerability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda Of E Business And Cyber Risk Management Ppt Outline Vector PDF
This is a agenda of e business and cyber risk management ppt outline vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, information, program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Best Mockup PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring best mockup pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT Implement Strong IT Guidelines Pictures PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it implement strong it guidelines pictures pdf bundle. Topics like implement strong it guidelines in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
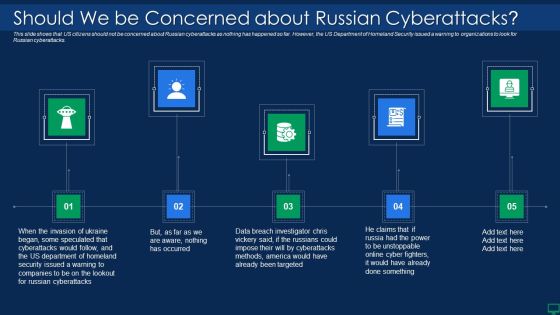
Russian Cyber Attacks On Ukraine IT Should We Be Concerned Slides PDF
Presenting russian cyber attacks on ukraine it should we be concerned slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like targeted, methods, security, cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhancing Cyber Safety With Vulnerability Administration SIEM Competitive Advantage Designs PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration siem competitive advantage designs pdf bundle. Topics like detection, management, deployment, value can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
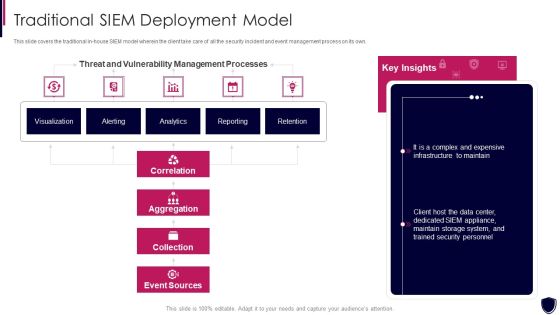
Enhancing Cyber Safety With Vulnerability Administration Traditional SIEM Deployment Designs PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration traditional siem deployment designs pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
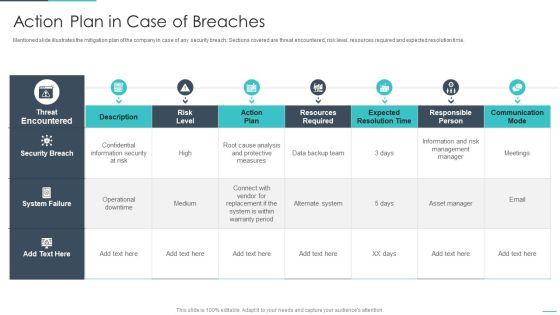
Handling Cyber Threats Digital Era Action Plan In Case Of Breaches Ppt Styles Objects PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative handling cyber threats digital era action plan in case of breaches ppt styles objects pdf bundle. Topics like action plan in case of breaches can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Updating Hardware And Software In Company Infographics PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems.Deliver an awe inspiring pitch with this creative cyber terrorism assault updating hardware and software in company infographics pdf bundle. Topics like peripheral devices, security necessitates, traditional ways to data transport can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5 Month IT Security Plan Timeline Pictures PDF
This slide 5 month cyber security strategy timeline illustrating product security, architecture security, people security, security compliance and resilience. Showcasing this set of slides titled 5 Month IT Security Plan Timeline Pictures PDF. The topics addressed in these templates are Architecture Security, People Security, Security Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Smart Venture Digitial Transformation Two Way Interactions Between Safety Security Template PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment. This is a Smart Venture Digitial Transformation Two Way Interactions Between Safety Security Template PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like SCADA Station Servers, Engineer Station, Cyber Intelligence Center. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
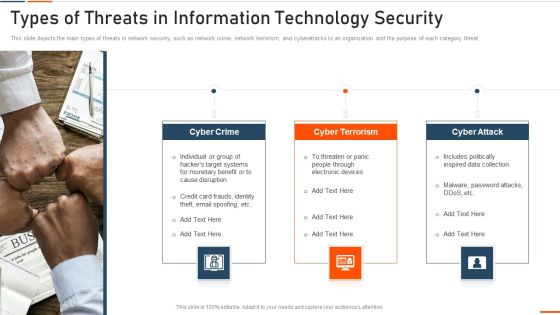
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
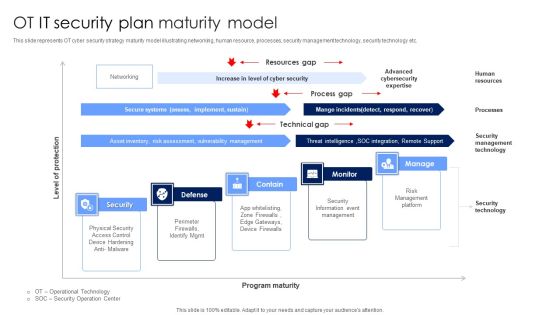
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT teams etc. Presenting Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Cyber Risk, Process Of Evaluating. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Venture Digitial Transformation Launch Of Cyber IT OT Strategy Ppt Icon Slides PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Smart Venture Digitial Transformation Launch Of Cyber IT OT Strategy Ppt Icon Slides PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like OT Strategy, Cyber IT, Process Evaluating. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF
This slide covers IT OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategy, Launch Of Cyber, Business Programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF
The following slide highlights some kpas of cyber security incidents to evaluate and monitor threats. It includes elements such as open incidents, warnings by severity, average response time, warnings pending for inspection etc. Showcasing this set of slides titled Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF. The topics addressed in these templates are Cyber Protection Incident, Privacy Analysis, KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Awareness System For Online Security Improvement Ppt PowerPoint Presentation Show Samples PDF
Presenting this set of slides with name awareness system for online security improvement ppt powerpoint presentation show samples pdf. This is a three stage process. The stages in this process are cyber focus, planning, 2020, build security policy, security architecture, cyber disaster management, evaluate supply chain security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organizational Network Staff Learning Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
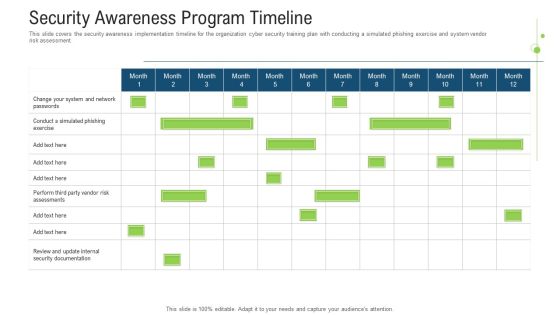
Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
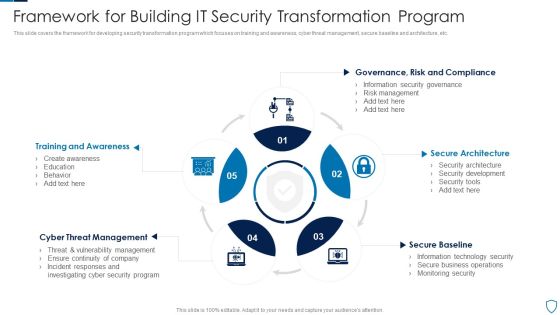
Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Cyber Terrorism Incidents On The Rise IT Strategies To Keep Company Safes Portrait PDF
This slide describes the checklist to deal with cyber-terrorism threats and counter it such as go after the perpetrators and prosecute them. This is a global cyber terrorism incidents on the rise it strategies to keep company safes portrait pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implemented, organization, technology, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Cyber Safety Tips Protection Against Cyberattacks Ppt Styles Gallery PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a cybersecurity cyber safety tips protection against cyberattacks ppt styles gallery pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT Are There International Mockup PDF
This slide describes the establishment of cyber policies by international laws, including the Budapest Convention on Cybercrime and the United Nations Group of Governmental Experts. This is a russian cyber attacks on ukraine it are there international mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, strategic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
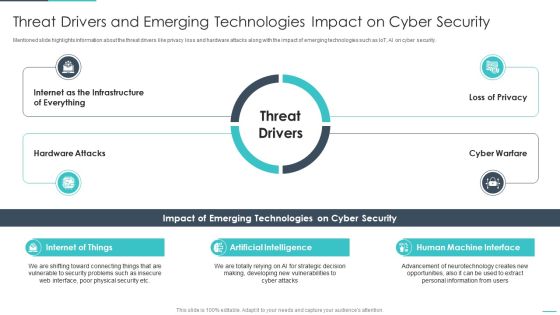
Handling Cyber Threats Digital Era Threat Drivers And Emerging Technologies Ppt Styles Ideas PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era threat drivers and emerging technologies ppt styles ideas pdf. Use them to share invaluable insights on internet of things, artificial intelligence, human machine interface and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
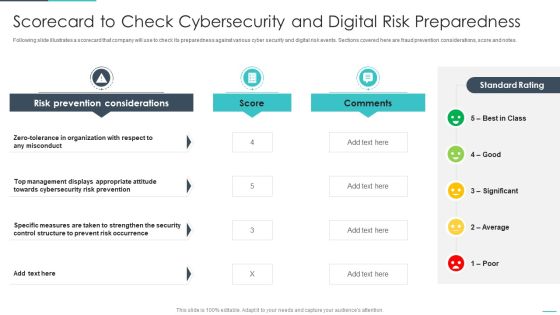
Handling Cyber Threats Digital Era Scorecard To Check Cybersecurity Ppt Model Information PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative dling cyber threats digital era scorecard to check cybersecurity ppt model information pdf bundle. Topics like scorecard to check cybersecurity and digital risk preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Wiper Spyware Attack Hacking Groups Launching Cyber Proxy War Against Russia Portrait PDF
This slide depicts the hacking groups such as the Anonymous hacker group, Conti ransomware gang, threat actors in Belarus launching cyber proxy war over Ukraine attacks by Russia.This is a data wiper spyware attack hacking groups launching cyber proxy war against russia portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure security, superpowers fought, conflicts through proxy You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home