Email Security

Competitive Analysis Of Major Players Existing Across Marketplace Demonstration PDF
This slide provides information regarding comparative analysis of potential players existing across marketplace. The points of differentiation include financial parameters, critical success factors such as product variety, customer services, email marketing, etc. There are so many reasons you need a Competitive Analysis Of Major Players Existing Across Marketplace Demonstration PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Marketing Department Detail Report One Pager Documents
This one pager marketing department report template covers detailed marketing highlights for search engine optimization and email marketing. Presenting you a fantastic Marketing Department Detail Report One Pager Documents. This piece is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this Marketing Department Detail Report One Pager Documents A4 One-pager now.

Contact Details For IP Telephony Services One Pager Sample Example Document
This template covers contact info for VoIP services company including email ids, address etc. Presenting you an exemplary Contact Details For IP Telephony Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Contact Details For IP Telephony Services One Pager Sample Example Document brilliant piece now.

Cafe Franchise Proposal Contact Us One Pager Sample Example Document
This slide shows the contact details of the company covering the address, email id and phone number. Presenting you an exemplary Cafe Franchise Proposal Contact Us One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cafe Franchise Proposal Contact Us One Pager Sample Example Document brilliant piece now.

Whitewash Services Proposal Contact Us One Pager Sample Example Document
This slide shows the contact details of the company covering the address, email id and phone number. Presenting you an exemplary Whitewash Services Proposal Contact Us One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Whitewash Services Proposal Contact Us One Pager Sample Example Document brilliant piece now.

Contact Details For Loan Settlement One Pager Sample Example Document
This template covers contact info for loan settlement company including email ids, address etc. Presenting you an exemplary Contact Details For Loan Settlement One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Contact Details For Loan Settlement One Pager Sample Example Document brilliant piece now.

Identifying And Increasing Brand Awareness Dashboard Depicting Website Data Insights Rules PDF
This slide shows the dashboard that depicts website data insights which covers channels such as display, social and email with total sessions, pages, average session duration, bounce rate, goal completion. There are so many reasons you need a Identifying And Increasing Brand Awareness Dashboard Depicting Website Data Insights Rules PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
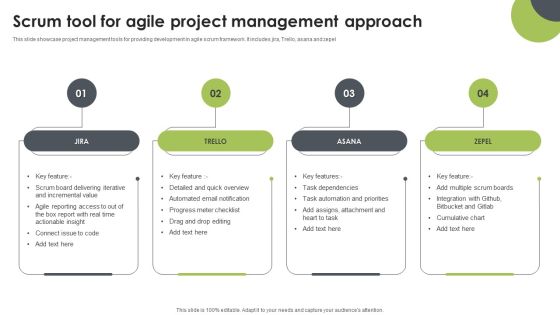
Scrum Tool For Agile Project Management Approach Topics PDF
This slide showcase project management tools for providing development in agile scrum framework. It includes jira, Trello, asana and zepel. Presenting Scrum Tool For Agile Project Management Approach Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Scrum Board Delivering Iterative, Detailed Quick Overview, Automated Email Notification. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Contact Details For Debt Settlement One Pager Sample Example Document
This template covers contact info for debt settlement company including email ids, address etc. Presenting you an exemplary Contact Details For Debt Settlement One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Contact Details For Debt Settlement One Pager Sample Example Document brilliant piece now.

Five Months Marketing Timeline Ppt Inspiration Portrait PDF
This is five months marketing timeline which includes SEO, paid searches, social media, email marketing, display ads and site UX or UI. There are so many reasons you need a Five Months Marketing Timeline Ppt Inspiration Portrait PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Constructive Destructive Customer Feedback Dashboard Designs PDF
This slide shows statistics about weekly number of favorable and unfavorable customer responses with overall email sentiment score. It further includes details about daily deals, special discounts, newsletter and renewal reminders. Showcasing this set of slides titled Constructive Destructive Customer Feedback Dashboard Designs PDF. The topics addressed in these templates are Previous Week, Current Week, Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorism 60 Days Plan Professional PDF
This slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it managing cyber terrorism 60 days plan professional pdf bundle. Topics like time to detect an incident, policy violations, data loss incidents, infected computers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Physical System To Enhance Sensing Components Of Cyber Physical Systems Pictures PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Physical System To Enhance Sensing Components Of Cyber Physical Systems Pictures PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Ways To Control Cyber Protection And Privacy Issues Diagrams PDF
The following slide illustrates some ways to monitor cybersecurity and privacy issues. It includes activities such as protecting CRM platform, keeping security system updated, modifying passwords regularly etc. Persuade your audience using this Ways To Control Cyber Protection And Privacy Issues Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Regularly, Regular Backups, Protect CRM Platform. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information And Cyber Data Safety Risk Management Plan Summary PDF
Mentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Showcasing this set of slides titled information and cyber data safety risk management plan summary pdf. The topics addressed in these templates are information and cyber data safety risk management plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Safety Awareness Training Program Ppt Layouts Infographic Template PDF
This slide covers training program based on cyber security in an organization. It includes elements such as department, training topics, certifications involved and learning methods to be used and total training hours required. Showcasing this set of slides titled Cyber Safety Awareness Training Program Ppt Layouts Infographic Template PDF. The topics addressed in these templates are Department, Training, Certifications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber And Data Safety Risk Management Framework Designs PDF
Mentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Showcasing this set of slides titled cyber and data safety risk management framework designs pdf. The topics addressed in these templates are service design, development, service operationalization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
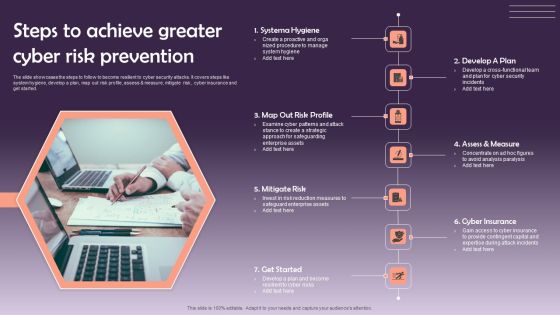
Steps To Achieve Greater Cyber Risk Prevention Infographics PDF
The slide showcases the steps to follow to become resilient to cyber security attacks. It covers steps like system hygiene, develop a plan, map out risk profile, assess and measure, mitigate risk, cyber insurance and get started. Presenting Steps To Achieve Greater Cyber Risk Prevention Infographics PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Systema Hygiene, Develop A Plan, Mitigate Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Confidential Data Should Be Backup Brochure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF
This slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Pitch your topic with ease and precision using this Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Possibility It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Step Procedure Of Cyber Threat Hunting Introduction PDF
This slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Persuade your audience using this Five Step Procedure Of Cyber Threat Hunting Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare Detailed, Management Software, Management Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Exploitation IT Regaining Reputation Of Our Company Demonstration PDF
This slide describes the regaining companys reputation through regaining customers trust by showcasing the companys new security policies and strategies. This is a cyber exploitation it regaining reputation of our company demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like regaining reputation of our company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF
The following slide highlights some kpas of cyber security incidents to evaluate and monitor threats. It includes elements such as open incidents, warnings by severity, average response time, warnings pending for inspection etc. Showcasing this set of slides titled Cyber Protection Incident And Privacy Analysis With KPI Dashboard Ideas PDF. The topics addressed in these templates are Cyber Protection Incident, Privacy Analysis, KPI Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Cyber Safety Tips Protection Against Cyberattacks Ppt Styles Gallery PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a cybersecurity cyber safety tips protection against cyberattacks ppt styles gallery pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF
This slide covers frequency of training to be provided as per prescribed format. It includes elements such as clicking suspicious links, use of simple passwords, workstation security management, public network management, etc. as per multiple time duration. Showcasing this set of slides titled Training Frequency For Cyber Safety Awareness Program Ppt Pictures Graphics PDF. The topics addressed in these templates are Training Included, Once Per Month, Frequency Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SIEM Competitive Advantage Enhancing Cyber Safety With Vulnerability Administration Introduction PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Deliver and pitch your topic in the best possible manner with this siem competitive advantage enhancing cyber safety with vulnerability administration introduction pdf. Use them to share invaluable insights on security information and event management, application performance monitoring, digital experience management, service health check and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative cyber safety incident management current potential implications faced by firm as threats clipart pdf bundle. Topics like issues related to employees, data breaches and records exposed, reported financial losses due to increase security threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhancing Cyber Safety With Vulnerability Administration Which Hosting Model Is Right Ideas PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. Presenting enhancing cyber safety with vulnerability administration which hosting model is right ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like client have existing siem infrastructure, client moves data off premises, client doesnt have security staff with siem expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
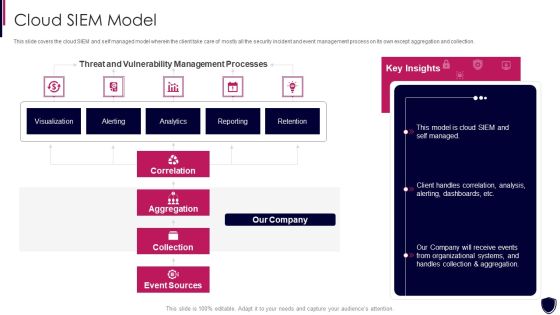
Enhancing Cyber Safety With Vulnerability Administration Cloud SIEM Model Clipart PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration cloud siem model clipart pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimating Total Cost Of Ownership Enhancing Cyber Safety With Vulnerability Administration Inspiration PDF
This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver and pitch your topic in the best possible manner with this estimating total cost of ownership enhancing cyber safety with vulnerability administration inspiration pdf. Use them to share invaluable insights on annual and ongoing expenses, cost breakdown, siem solution, security engineering costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhancing Cyber Safety With Vulnerability Administration Our Organization SIEM Log Flow Inspiration PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. Presenting enhancing cyber safety with vulnerability administration our organization siem log flow inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like index, analyz, correlate, threshold, capture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
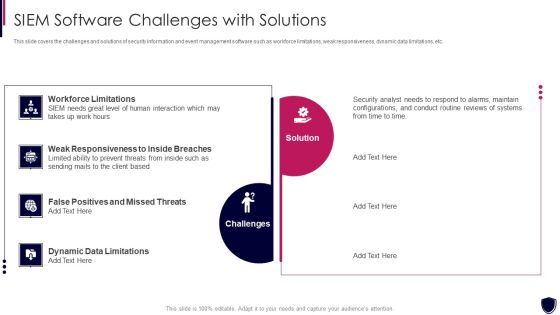
Enhancing Cyber Safety With Vulnerability Administration SIEM Software Challenges Slides PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a enhancing cyber safety with vulnerability administration siem software challenges slides pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like workforce limitations, challenges, solution, weak responsiveness to inside breaches, dynamic data limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Cyber Data Safety Risk Management Maturity Levels Elements PDF
Mentioned slide showcase maturity stages of information security risk management, which will assist company to develop comprehensive cybersecurity strategy. The maturity stages could be Partial informed repetitive and adaptive. Presenting information and cyber data safety risk management maturity levels elements pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including partial, informed, repetitive, adaptive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT teams etc. Presenting Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Cyber Risk, Process Of Evaluating. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Smart Venture Digitial Transformation Launch Of Cyber IT OT Strategy Ppt Icon Slides PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Smart Venture Digitial Transformation Launch Of Cyber IT OT Strategy Ppt Icon Slides PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like OT Strategy, Cyber IT, Process Evaluating. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF
This slide covers IT OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategy, Launch Of Cyber, Business Programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
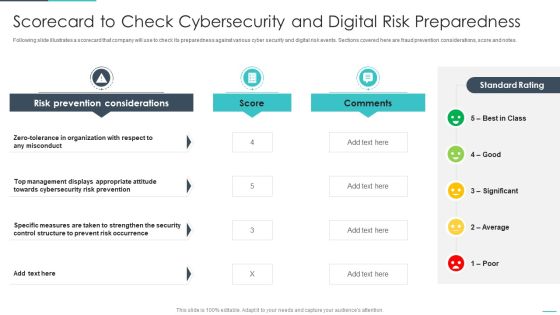
Handling Cyber Threats Digital Era Scorecard To Check Cybersecurity Ppt Model Information PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative dling cyber threats digital era scorecard to check cybersecurity ppt model information pdf bundle. Topics like scorecard to check cybersecurity and digital risk preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Wiper Spyware Attack Weaknesses Of Russian Cyber Cell Microsoft PDF
This slide represents the weaknesses of Russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials.Presenting data wiper spyware attack weaknesses of russian cyber cell microsoft pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like lack of skilled professionals, corruption, security agencies In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Audit Demanded, Enable Collaboration, Industrialize Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Causes Of Cyber Crimes And Attacks Ppt PowerPoint Presentation File Outline PDF
The following slide highlights the key reasons of cyber-attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Find a pre designed and impeccable Major Causes Of Cyber Crimes And Attacks Ppt PowerPoint Presentation File Outline PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
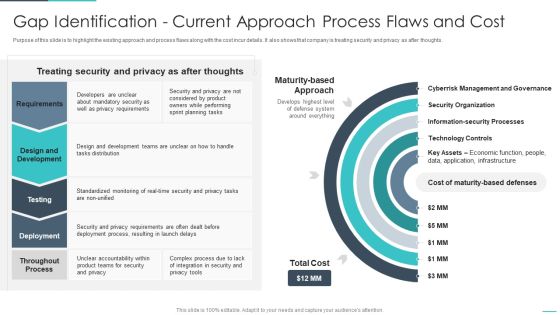
Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
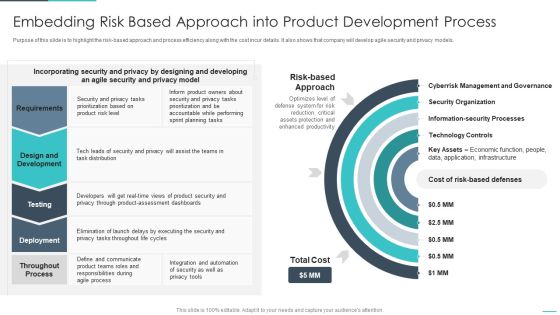
Handling Cyber Threats Digital Era Embedding Risk Based Approach Into Product Ppt Gallery Designs PDF
Purpose of this slide is to highlight the risk-based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative handling cyber threats digital era embedding risk based approach into product ppt gallery designs pdf bundle. Topics like embedding risk based approach into product development process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Handling Cyber Threats Digital Era Categorization Worksheet For Assets Ppt Icon Outline PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting handling cyber threats digital era categorization worksheet for assets ppt icon outline pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like server computer, system location, system accessibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Cyber Officials Urge Agencies To Armor Download PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines.Presenting data wiper spyware attack cyber officials urge agencies to armor download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like warning government, corporations to be cautious, russian cyberattacks In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Officials Urge Agencies To Armor Up For Potential Russian Attacks Background PDF
This slide represents that officials from the department of homeland security have urged agencies to prepare for possible russian cyberattacks, and CISA has amended its shields up guidelines. Boost your pitch with our creative Cyber Officials Urge Agencies To Armor Up For Potential Russian Attacks Background PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Global Cyber Terrorism Incidents On The Rise IT How To Prevent Ddos Attacks In The Company Designs PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Presenting global cyber terrorism incidents on the rise it how to prevent ddos attacks in the company designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mitigation technologies, service, traffic irregularities, network monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Planning Process For Digital Terrorism Graphics PDF
This slide shows steps of planning process to tackle cyber terrorism for preventing cyber attacks and data leakage. It include steps such as identifying threats, setting framework, documenting program etc. Presenting Organizational Planning Process For Digital Terrorism Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cyber Program, Determine Improvement Programs, Document Cyber Security Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Terrorism Attack Trends On USA Ideas PDF
This slide shows cyber terrorism attack trends on USA organizations for decade to highlight importance of cyber security systems. It includes valuation of losses, categories of cyber attacks and victim companies etc. Showcasing this set of slides titled Digital Terrorism Attack Trends On USA Ideas PDF. The topics addressed in these templates are Key Insights, Internet, Digital Terrorism Attack Trends. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Safety Risk Management Challenges And Solutions Clipart PDF
Mentioned slide showcases various challenges and solutions of information security risk management. The challenges mentioned in the slide are continuously cyber risk measurement, risk of cyber-adversaries, tracking sensitive data flows. Showcasing this set of slides titled y risk management challenges and solutions clipart pdf. The topics addressed in these templates are data safety risk management challenges and solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Impact On Organization After Implementing Ppt Summary Influencers PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Presenting cybersecurity impact on organization after implementing ppt summary influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network intrusion, inadvertent disclosure, system misconfiguration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Technology Trends Impacting Digital Loans Ppt Summary Model PDF
This slide shows the impacts of technology trends on digital lending to enhance the customer service and simplify the process. It includes credit decision automation, personalized products, focus on cyber attacks, etc. Persuade your audience using this Technology Trends Impacting Digital Loans Ppt Summary Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Credit Decision Automation, Personalized Products, Focus Cyber Security . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home