Email Communication
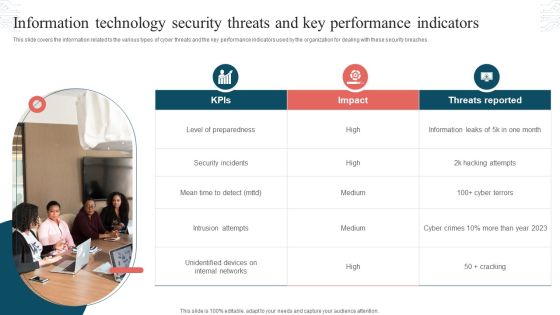
Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Training Program Challenges Ppt Styles Clipart PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Security Awareness Training Program Challenges Ppt Styles Clipart PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Secure Access Service Edge Importance Ppt Outline Graphics Example PDF
This slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. This modern and well arranged Secure Access Service Edge Importance Ppt Outline Graphics Example PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Global Cyber Terrorism Incidents On The Rise IT How To Prevent Ddos Attacks In The Company Designs PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Presenting global cyber terrorism incidents on the rise it how to prevent ddos attacks in the company designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like mitigation technologies, service, traffic irregularities, network monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Roadmap For IT Security IT Training Ppt Slides Format Ideas PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting roadmap for it security it training ppt slides format ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, privacy, safe and computing, ensuring physical security, mobile and remote. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
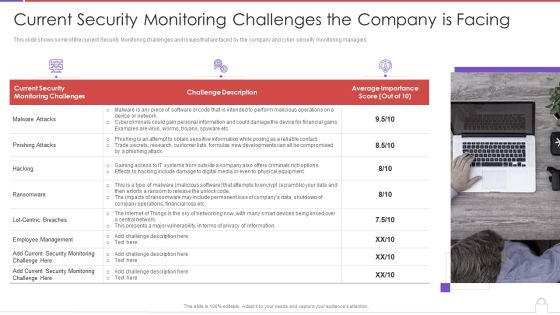
Methods To Develop Advanced Current Security Monitoring Challenges The Company Is Facing Professional PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a methods to develop advanced current security monitoring challenges the company is facing professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like current security, monitoring challenges, challenge description, average importance score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Hardware And Software Update In Company IT Security IT Ppt Model Infographics PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting hardware and software update in company it security it ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technology, security, data across. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hardware And Software Update In Company Ppt Infographics Ideas PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a it security hardware and software update in company ppt infographics ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, security, operating systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Hardware And Software Update In Company Ppt Outline Graphics Pictures PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a information security hardware and software update in company ppt outline graphics pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, technology, devices, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Hardware And Software Update In Company Portrait PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a desktop security management hardware and software update in company portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, servers, devices, network, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Info Security Minimize Administrative And Staff Privileges Ppt PowerPoint Presentation Icon Files PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting info security minimize administrative and staff privileges ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like employees, prevent cyber attacks, administrative staff. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Team Performance Improvement Functional Optimization Through Agile Methodologies Prioritizing Agile Software Development Tasks Sample PDF
This slide shows some important tasks that need to be done on priority basis in order to implement Agile Technique in the team such as focusing on individual, enhance product features, quickly responding to change, collaborating with the customer for efficient task completion etc. This is a team performance improvement functional optimization through agile methodologies prioritizing agile software development tasks sample pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project deliverables, enhancing team communication, customer collaboration, minimize cyber security risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Prevention Of Information Security Awareness Packages Offered By Third Party Information PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Prevention Of Information Security Awareness Packages Offered By Third Party Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
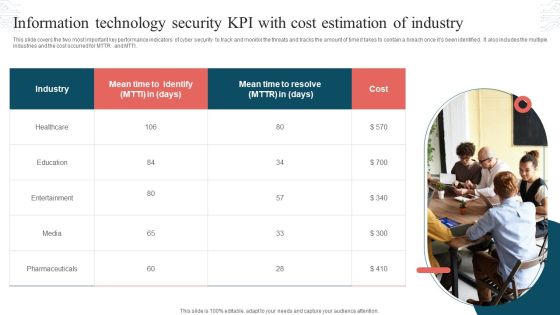
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Practices To Improve Security Awareness Level Amongst Download PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Take your projects to the next level with our ultimate collection of Prevention Of Information Practices To Improve Security Awareness Level Amongst Download PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest

Lead Scoring AI Model Gathering Information For Lead Qualifying Process Ppt Guidelines PDF
The firm will generate lead crucial information through webinar by collecting the relevant data from prospective leads such as job title, phone number, name, email address, etc. Presenting lead scoring ai model gathering information for lead qualifying process ppt guidelines pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like marketing, campaign, timeframe, business, communicating. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF
The following slide showcases various courses associated with cyber security training to aware workforce with latest security threats. It includes elements such as course name, features, cost, duration etc. Presenting Enterprise Cybersecurity Training Plan Courses For Employee Development Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Introduction To Cybersecurity, Cyber Online, IT And Cybersecurity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risks And Frauds In Electronic E Procurement System And Purchasing Designs PDF
The following slide showcases risks involved in e procurement that can disrupt smooth functioning of organization. The risks covered are poor internal system, cyber security risk and conflict of interest. Presenting Risks And Frauds In Electronic E Procurement System And Purchasing Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security Risk, Conflict Of Interest, Poor Internal System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
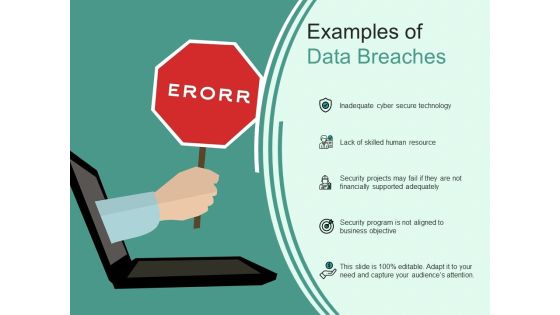
Examples Of Data Breaches Ppt PowerPoint Presentation Summary Portrait PDF
Presenting this set of slides with name examples of data breaches ppt powerpoint presentation summary portrait pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
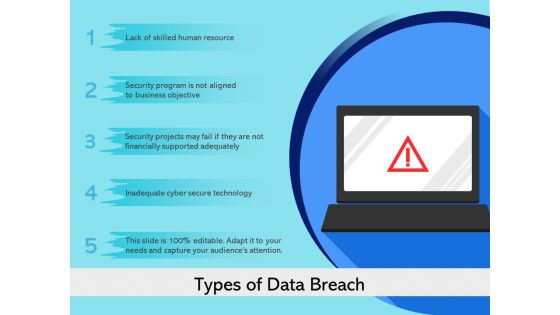
Types Of Data Breach Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name types of data breach ppt powerpoint presentation inspiration ideas pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
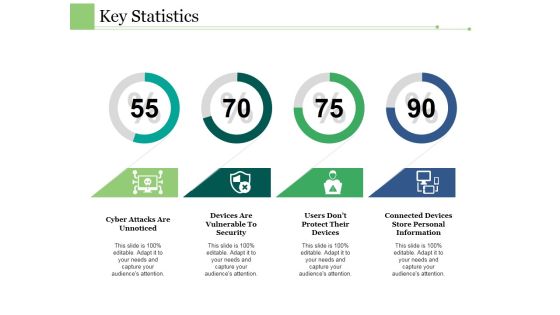
Key Statistics Ppt PowerPoint Presentation Show Sample
This is a key statistics ppt powerpoint presentation show sample. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users do not protect their devices, connected devices store personal information.

Incident Response Techniques Deployement Impact Of Cybersecurity Incidents On Organization Clipart PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Digital Technology Adoption In Banking Industry Case Competition Emerging Technological Infographics PDF
This slide shows the latest technological trends which should be adopted by the ABC Bank which includes cyber security, upgraded ATMs, Chatbot, Artificial Intelligence etc.Presenting Digital Technology Adoption In Banking Industry Case Competition Emerging Technological Infographics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Cyber Security, Artificial Intelligence, Cloud Computing In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Managed Services Pricing Guide Service Features Comparison Ppt Gallery Infographic Template PDF
Presenting this set of slides with name cloud managed services pricing guide service features comparison ppt gallery infographic template pdf. This is a three stage process. The stages in this process are service, cyber security, analytics, monitoring, disaster recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Support And Monitoring Services Pricing Agenda For IT Support And Monitoring Services Pricing Elements PDF
Presenting this set of slides with name it support and monitoring services pricing agenda for it support and monitoring services pricing elements pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF
The following slide showcases evolution of cybersecurity infrastructure with developments in communication strategy. It presents information related to unawareness, reactive, proactive, etc. Presenting Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unaware, Reactive, Proactive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Technology Transformation Seven Basic Goals Ppt PowerPoint Presentation Ideas Images PDF
Persuade your audience using this technology transformation seven basic goals ppt powerpoint presentation ideas images pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including safeguarding digital resources cyber threats, technology optimization to push faster and respond to changes, technology optimization more productive, secure, track and react to conditions real time, optimizing investment protection to reduce resources and administration, ensuring threats handled and fully complied security, build modern business plan grabbing new opportunities. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
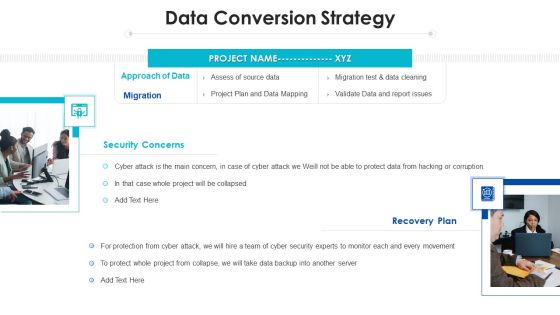
Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF
Presenting Project Assessment Templates Bundle Data Conversion Strategy Ppt Inspiration Background Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Approach Data, Recovery Plan, Cyber Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
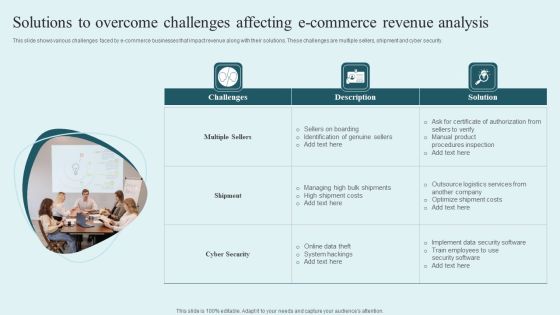
Solutions To Overcome Challenges Affecting E Commerce Revenue Analysis Summary PDF
This slide shows various challenges faced by e-commerce businesses that impact revenue along with their solutions. These challenges are multiple sellers, shipment and cyber security. Presenting Solutions To Overcome Challenges Affecting E Commerce Revenue Analysis Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Challenges, Solution, Multiple Sellers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Hardware And Software Update In Company Ppt Inspiration Rules PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a cybersecurity hardware and software update in company ppt inspiration rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, secure, network, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Reverse Proxy Server IT Why To Use Reverse Proxy Server Ppt Gallery Good PDF
This slide depicts why to use reverse proxy servers, including control over cyber loafing, bandwidth saving, privacy benefits, security, and access to blocked resources. Presenting reverse proxy server it why to use reverse proxy server ppt gallery good pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like employees, privacy benefits, advanced security, access to blocked, resources and websites. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Playbook For Enterprise Transformation Administration Digital Transformation Trends We Can Adopt Professional PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyper automation, cyber security tools, usage of AI etc. This is a Playbook For Enterprise Transformation Administration Digital Transformation Trends We Can Adopt Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Deconstruction, Security Tools, Organizations Operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. This is a Smart Venture Digitial Transformation IT OT Organizational Structure Based On Target Download PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise CIO, Product Heads, Crisis Management, IT Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Slidegeeks is here to make your presentations a breeze with Forecast Analysis Technique IT Outliers Model For Predictive Modeling Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Assessment Test To Measure Effectiveness Of Training Plan Professional PDF
purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Presenting Assessment Test To Measure Effectiveness Of Training Plan Professional PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Collecting Sensitive, Performing Unauthorized, Hurting Statement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Trends On Effective Information Technology Service Excellence Themes PDF
This slide signifies the effective information technology recent and future trends. It includes stages like artificial intelligence, block chain, cyber security and customer data platform. Persuade your audience using this Key Trends On Effective Information Technology Service Excellence Themes PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analytics, Distributed Enterprise, Enterprise Service Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Assessment Test To Measure Effectiveness Of Training Plan Ppt Pictures Templates PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Find a pre-designed and impeccable Assessment Test To Measure Effectiveness Of Training Plan Ppt Pictures Templates PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Program Budget Setting Approaches For Digital Terrorism Background PDF
This slide shows various approaches to set budget for security plans against cyber terrorism for preventing data fraudulent. It include approaches such as Reactive Approach, Proactive Approach, Benchmarking approach etc. Presenting Program Budget Setting Approaches For Digital Terrorism Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benchmarking Approach, Risk Based Approach, Proactive Approach. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Presenting How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Transform Cybersecurity, Complex Business, Accelerate Autonomous Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Charity Fundraising Marketing Plan Best Practices Adopted By Nonprofit Organizations Themes PDF
This slide provides an overview of the practices to be followed by marketers. Major practices covered are store insightful data, trigger email series, segment supporters, schedule and automate posts. Create an editable Charity Fundraising Marketing Plan Best Practices Adopted By Nonprofit Organizations Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Charity Fundraising Marketing Plan Best Practices Adopted By Nonprofit Organizations Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
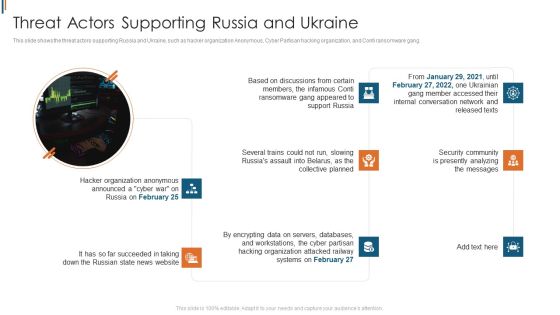
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Processing Services Delivery The Next Generation Operating Model After Implementing Ai Pictures PDF
This slide represents the next generation operating model after implementing AI in the organization and how it would increase the productivity and profit. This is a Data Processing Services Delivery The Next Generation Operating Model After Implementing Ai Pictures PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Sales Reports, Cyber Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why To Use Reverse Proxy Server Reverse Proxy For Load Balancing Clipart PDF
This slide depicts why to use reverse proxy servers, including control over cyber loafing, bandwidth saving, privacy benefits, security, and access to blocked resources.Presenting Why To Use Reverse Proxy Server Reverse Proxy For Load Balancing Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Provide Load, Application Firewalls, Delivery Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Company Transformation Strategies And Its Implementation On Project Ppt File Designs Download PDF
This slide contains the information related to the best implementation of the strategies used for the transformations in the business. It includes improving cyber security for financial technologies , create digital solutions , increase budget for RandD and developing user friendly systems. Persuade your audience using this Company Transformation Strategies And Its Implementation On Project Ppt File Designs Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Change Passwords Monthly, Digital Solutions, Digital Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Incident Response Techniques Deployement Gap Analysis Representing Current Situation Of Cybersecurity Designs PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. There are so many reasons you need a Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

 Home
Home