Data Security
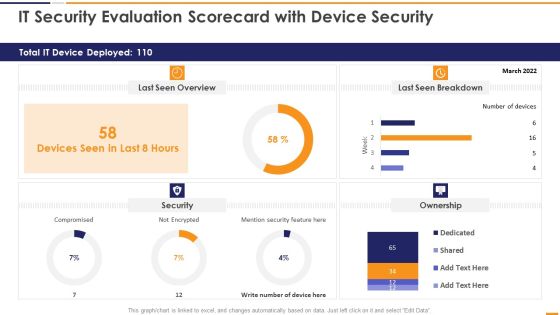
IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF bundle. Topics like Total IT Device, Last Seen Overview, Last Seen Breakdown, Mention Security Feature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
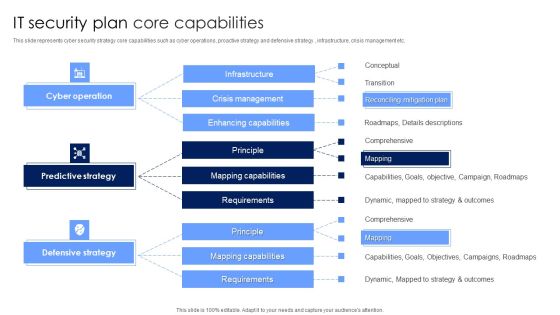
IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Native Application Security PPT Template
This Cloud Native Application Security PPT Template is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This seventy two slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Safety And Security Icon Infographics PDF
Persuade your audience using this Computer Safety And Security Icon Infographics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Computer Safety, Security Icon Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

KPI Dashboard Metrics Security Icon Download PDF
Persuade your audience using this KPI Dashboard Metrics Security Icon Download PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Kpi Dashboard, Metrics Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Roadmap Of Cloud Security Implementation Infographics PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Presenting Roadmap Of Cloud Security Implementation Infographics PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Applications Services Management, Cloud Services Monitoring, Network Security December. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
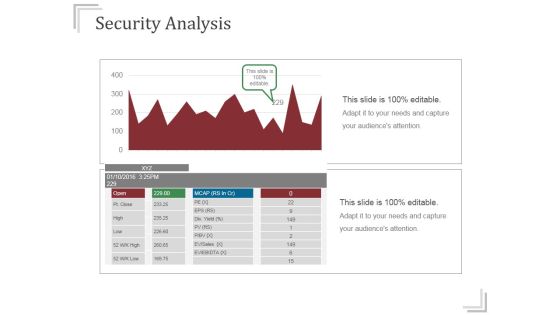
Security Analysis Ppt PowerPoint Presentation Infographics
This is a security analysis ppt powerpoint presentation infographics. This is a two stage process. The stages in this process are business, finance, growth, analysis, success.

Security Analysis Ppt PowerPoint Presentation Background Image
This is a security analysis ppt powerpoint presentation background image. This is a two stage process. The stages in this process are business, analysis, strategic, finance, management.
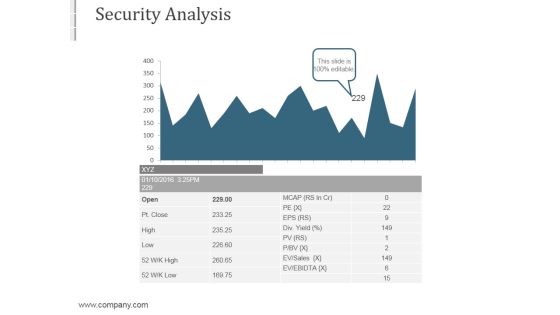
Security Analysis Ppt PowerPoint Presentation Guidelines
This is a security analysis ppt powerpoint presentation guidelines. This is a one stage process. The stages in this process are high risk, low risk.

Security Analysis Ppt PowerPoint Presentation Slides
This is a security analysis ppt powerpoint presentation slides. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.

Security Analysis Ppt PowerPoint Presentation Layout
This is a security analysis ppt powerpoint presentation layout. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, success.

Security Analysis Ppt PowerPoint Presentation Deck
This is a security analysis ppt powerpoint presentation deck. This is a one stage process. The stages in this process are business, strategy, marketing, analysis, growth.

Security Analysis Ppt PowerPoint Presentation File Inspiration
This is a security analysis ppt powerpoint presentation file inspiration. This is a two stage process. The stages in this process are business, growth, analysis, strategy, management.

Security Analysis Bar Graph Ppt Slides
This is a security analysis bar chart ppt slides. This is a one stage process. The stages in this process are business, finance, marketing.
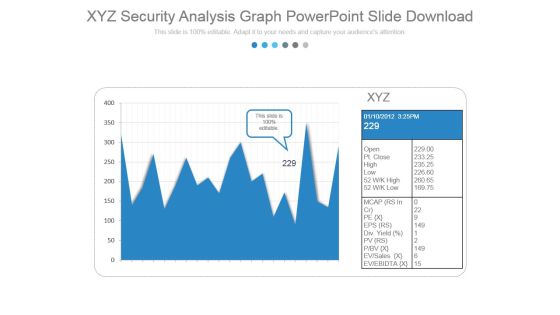
Xyz Security Analysis Graph Powerpoint Slide Download
This is a xyz security analysis graph powerpoint slide download. This is a two stage process. The stages in this process are business, marketing, growth, graph.

Security Analysis Ppt PowerPoint Presentation Show
This is a security analysis ppt powerpoint presentation show. This is a one stage process. The stages in this process are open, high, low, business, marketing.

Security Analysis Ppt Powerpoint Presentation File Tips
This is a security analysis ppt powerpoint presentation file tips. This is a one stage process. The stages in this process are graph, marketing, business, growth, finance.
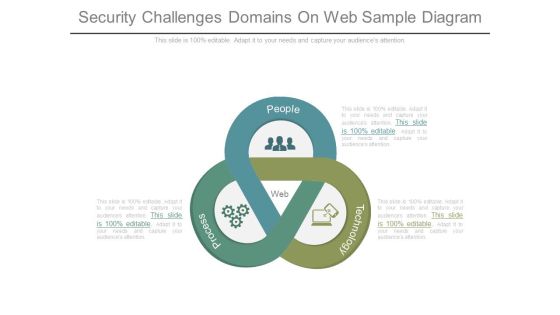
Security Challenges Domains On Web Sample Diagram
This is a security challenges domains on web sample diagram. This is a three stage process. The stages in this process are web, process, people, technology.

Cyber Security Incident Handling Checklist Information PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Welcome to our selection of the Cyber Security Incident Handling Checklist Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Security Patch Management Template Presentation Images
This is a security patch management template presentation images. This is a six stage process. The stages in this process are testing, architecture, quality assurance, analysis, design, synthesis.

Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
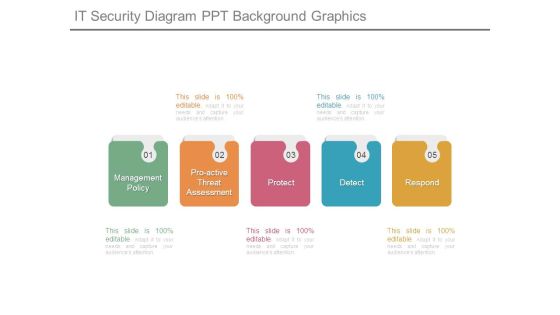
It Security Diagram Ppt Background Graphics
This is a it security diagram ppt background graphics. This is a five stage process. The stages in this process are management policy, proactive threat assessment, protect, detect, respond.

Security Initiatives Protecting Recruitment Process Elements PDF
This slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Slidegeeks is here to make your presentations a breeze with Security Initiatives Protecting Recruitment Process Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
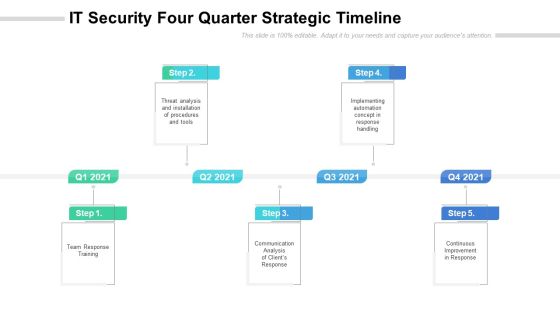
IT Security Four Quarter Strategic Timeline Slides
Presenting our innovatively structured it security four quarter strategic timeline slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Quarterly IT Security Recognition Program Roadmap Infographics
Presenting our innovatively-structured quarterly it security recognition program roadmap infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
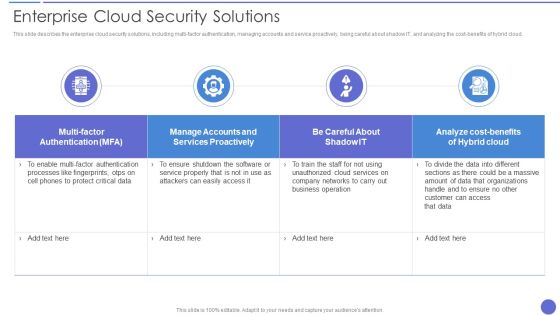
Enterprise Cloud Security Solutions Professional PDF
This slide describes the enterprise cloud security solutions, including multi factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost benefits of hybrid cloud. Deliver an awe inspiring pitch with this creative Enterprise Cloud Security Solutions Professional PDF bundle. Topics like Services Proactively, Analyze Cost Benefits, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
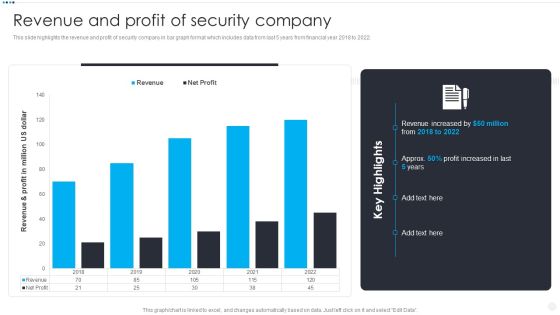
Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF. Use them to share invaluable insights on Revenue And Profit, Million US Dollar, Revenue Increased Profit and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF. Use them to share invaluable insights on Revenue Increased, Increased In Last, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Encryption Ppt PowerPoint Presentation Layouts Cpb
Presenting this set of slides with name security encryption ppt powerpoint presentation layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like security encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
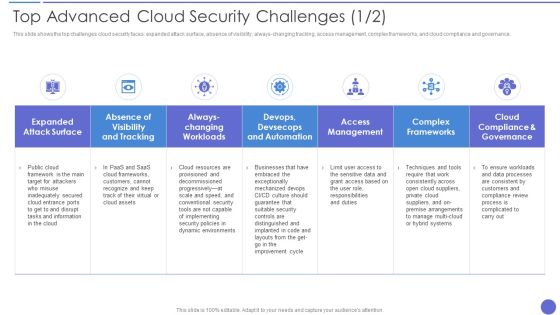
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Management Technology Framework Themes PDF
This slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Persuade your audience using this Cyber Security Management Technology Framework Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Protect, Identify, Detect, Respond, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Incident Handling Checklist Elements PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Take your projects to the next level with our ultimate collection of Cyber Security Incident Handling Checklist Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Cloud Security Risks Or Threats Brochure PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Security Risks Or Threats Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Malware Attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
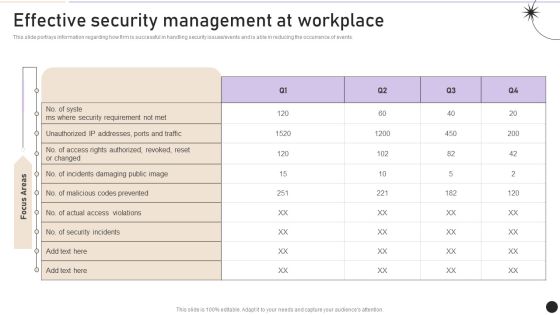
Effective Security Management At Workplace Designs PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present like a pro with Effective Security Management At Workplace Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
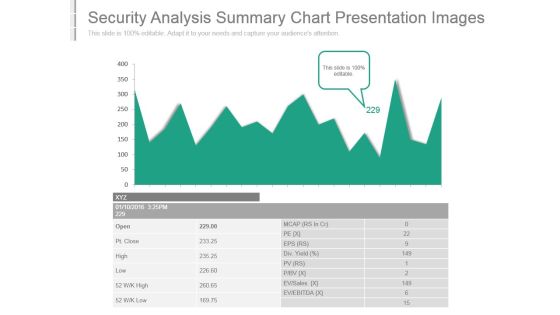
Security Analysis Summary Chart Presentation Images
This is a security analysis summary chart presentation images. This is a one stage process. The stages in this process are ev ebitda, ev sales, div yield, open, pt close, high, low, mcap, eps.
Security Strategic Four Quarter Functional Timeline Icons
Presenting our innovatively structured security strategic four quarter functional timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Security Of Supply Project Assessment Ppt Slides
This is a security of supply project assessment ppt slides. This is a four stage process. The stages in this process are project assessment, technical resilience, technical aspects, losses variation.
IT Security Five Years Strategic Timeline Icons
We present our it security five years strategic timeline icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched it security five years strategic timeline icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Organizational Security Solutions Quotes Ppt Model PDF
Deliver an awe inspiring pitch with this creative organizational security solutions quotes ppt model pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Organizational Security Solutions Financial Icons PDF
Presenting organizational security solutions financial icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like euro, dollar, pound. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
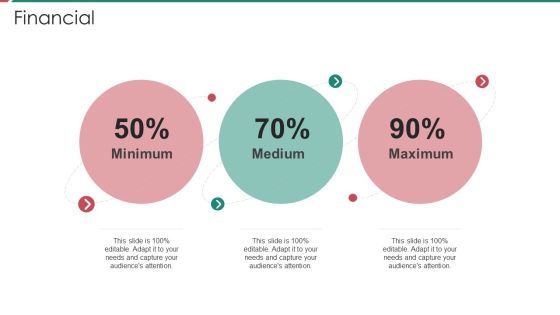
Security And Process Integration Financial Formats PDF
Presenting security and process integration financial formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Cloud Security Assessment Infographics PDF
Presenting Agenda For Cloud Security Assessment Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For IT Security Designs PDF
Download our innovative and attention grabbing icons slide for it security designs pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Cyber Security Five Year Strategic Timeline Demonstration
We present our cyber security five year strategic timeline demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security five year strategic timeline demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Strategic Five Year Functional Timeline Graphics
We present our security strategic five year functional timeline graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched security strategic five year functional timeline graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Security Incident Response Lifecycle Diagrams PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Incident Response Lifecycle Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Get a simple yet stunning designed IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

IT Security Half Yearly Strategic Timeline Diagrams
Introducing our it security half yearly strategic timeline diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

IT Security Three Months Strategic Timeline Portrait
Presenting our jaw dropping it security three months strategic timeline portrait. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Are you searching for a Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF from Slidegeeks today.

Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
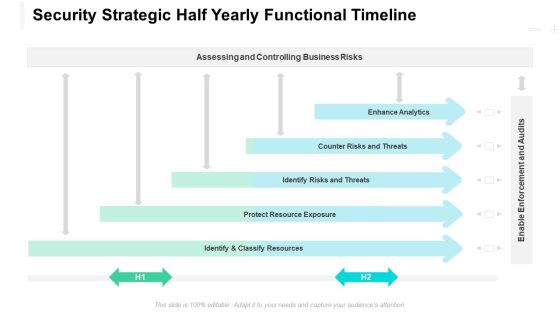
Security Strategic Half Yearly Functional Timeline Designs
Introducing our security strategic half yearly functional timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Half Yearly Strategic Timeline Icons
Presenting our innovatively structured cyber security half yearly strategic timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
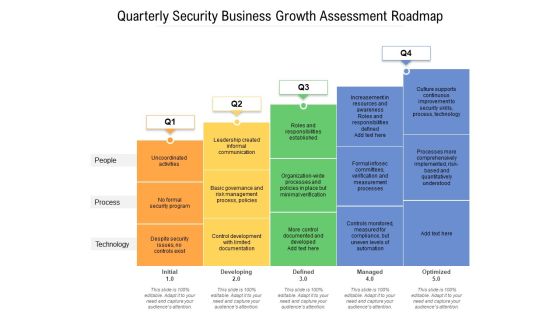
Quarterly Security Business Growth Assessment Roadmap Infographics
Presenting our jaw-dropping quarterly security business growth assessment roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

IT Security Six Months Strategic Timeline Portrait
Presenting the it security six months strategic timeline portrait. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Computer Security Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this Computer Security Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Security Strategic Six Months Functional Timeline Clipart
Presenting the security strategic six months functional timeline clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Model Business PowerPoint Templates Security Plan Slides
We present our model business powerpoint templates security plan Slides.Download our Marketing PowerPoint Templates because you should Experience excellence with our PowerPoint Templates and Slides. They will take your breath away. Download our Circle Charts PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Download our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download and present our Business PowerPoint Templates because It will get your audience in sync. Download and present our Shapes PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown.Use these PowerPoint slides for presentations relating to arrow, blue, chart, chevron, circle, circular, diagram, graphic, green, hub, icon, illustration, isometric, pie, pieces, process, purple, red, round, set, slices, stages, vector, wheel, yellow. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
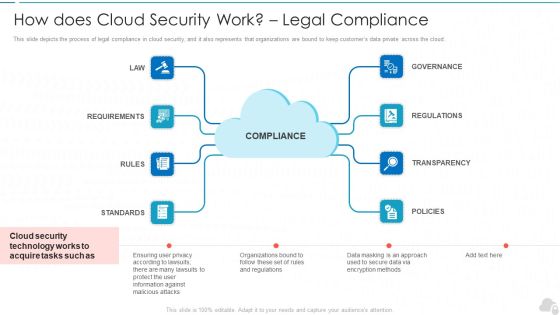
How Does Cloud Security Work Legal Compliance Cloud Computing Security IT Ppt Model Maker PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a how does cloud security work legal compliance cloud computing security it ppt model maker pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance, regulations, transparency, policies, rules. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Retrieve professionally designed Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
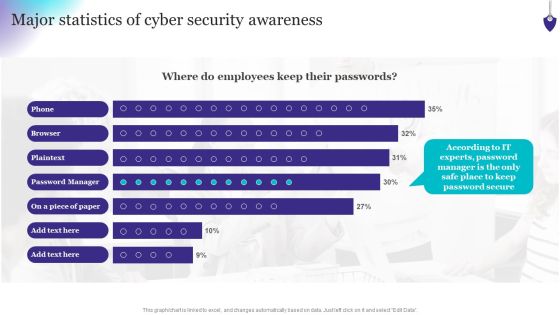
Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Welcome to our selection of the Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

IT Security Ppt PowerPoint Presentation Complete Deck
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty one slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Laptop Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with rendered illustration of a laptop with chains and lock around screen

Weakest Link Security PowerPoint Template 0510
weakest link in the chain on a white background

Identity Theft Security PowerPoint Template 1110
Hand punching through the image grabbing documents

Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
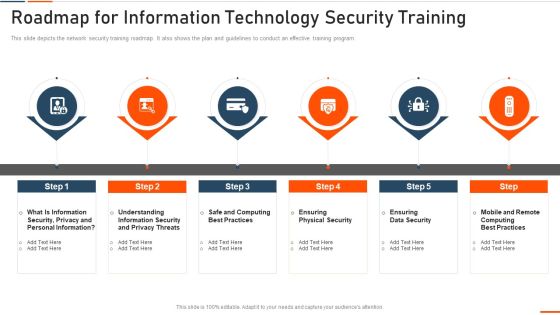
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Web Development What Is The Cyber Security Designs PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Web Development What Is The Cyber Security Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Categories Of Cyber, Operational Security, Includes Network Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Computing Business Driven Security Architecture Introduction PDF
The slide shows a security framework of business driven services. It highlight cloud computing services such as SaaS, PaaS and IaaS and security services such as data security management, software and service assertion, technical service control, risk management infrastructure management, etc. Showcasing this set of slides titled Cloud Computing Business Driven Security Architecture Introduction PDF. The topics addressed in these templates are Strategies, Delegation Authority, Service Goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Bring Your Own Device Security Policy Checklist Graphics PDF
This slide showcases checklist for bring your own device policy to map and understand of information network. It also includes check points related to back up, data security, companys protocol, etc. Presenting Bring Your Own Device Security Policy Checklist Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Check Points, Checklist, Device. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Implementation Approach Conceptual Structure Professional PDF
Following slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Presenting Cyber Security Implementation Approach Conceptual Structure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State, Evaluation, Target State . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Effective Online Security Risk Assessment Process Inspiration PDF
This slide showcases digital safety risk assessment process which helps identify potential cyber vulnerabilities. It provides steps such as asset prioritization, identify threat, analyze controls, assess impact and recommend controls. Persuade your audience using this Effective Online Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Card Data Security, Cross Border Transactions, Payment Methods. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
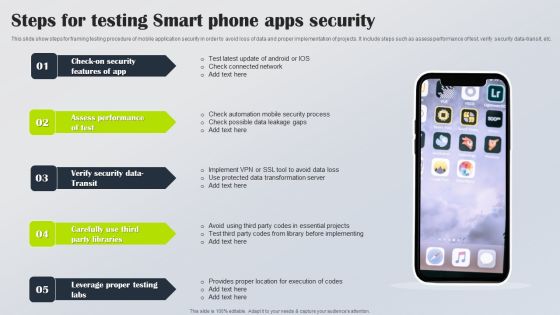
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Security Architecture Shared Responsibilities Brochure PDF
The slide shows cloud security shared responsibilities for users and service providers. It includes client data protection and supervision, data and information security, application level security and platform and infrastructure security. Showcasing this set of slides titled Cloud Computing Security Architecture Shared Responsibilities Brochure PDF. The topics addressed in these templates are Client Data Protection, Data Information Security, Application Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Information And Event Management Services Mockup PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting security information and event management services mockup pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Transformation Trends In It And Cyber Security Designs PDF
This slide signifies digital transformation in Information technology and cyber security. It includes trends like securing assets, cloud computing, data analytics, security and automation. Persuade your audience using this digital transformation trends in it and cyber security designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including securing digital assets, cloud computing, data analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
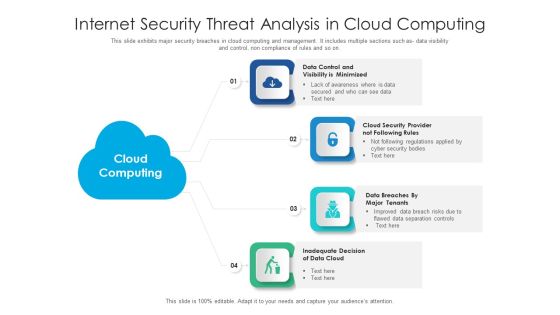
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

6 Step Process To Implement Information Availability Security Icons PDF
This slide represents 6 step process to implement data availability security illustrating simplified recording, on site maintenance and online security, training, record disposal and plan. Presenting 6 step process to implement information availability security icons pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including required, develop, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Database Access Security Measures For Businesses Portrait PDF
This slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data-centric security plan, deploying a multi-factor authentication policy, etc. Pitch your topic with ease and precision using this Database Access Security Measures For Businesses Portrait PDF. This layout presents information on Methods, Benefits, Actions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
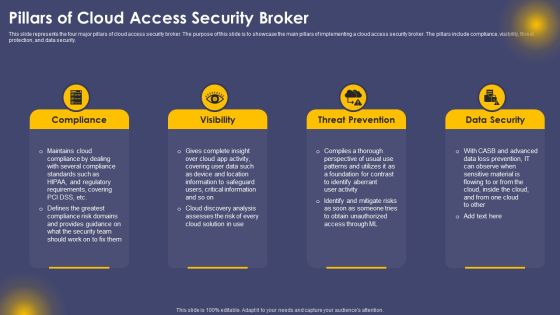
Pillars Of Cloud Access Security Broker Ppt Show Background PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Pillars Of Cloud Access Security Broker Ppt Show Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Pillars Of Cloud Access Security Broker Ppt Show Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Information And Event Management Dashboard Events Ideas PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative security information and event management dashboard events ideas pdf bundle. Topics like security events, data source, event categories can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Secure Internet Connection Security PowerPoint Templates And PowerPoint Themes 0712
Secure Internet Connection Security PowerPoint Templates And PowerPoint Themes 0712-Microsoft Powerpoint Templates and Background with secure internet connection

Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF. Use them to share invaluable insights on Efficient Recovery, Hardware Required, Efficient Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Main Principle Of Information Security Ppt PowerPoint Presentation File Background Designs PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative info security main principle of information security ppt powerpoint presentation file background designs pdf bundle. Topics like integrity, confidentiality, availability, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
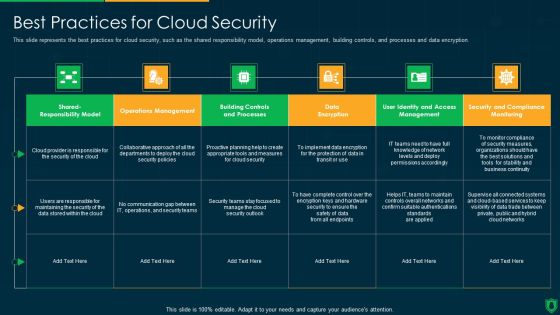
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. This Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
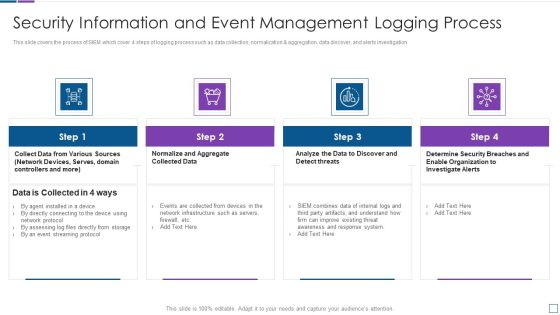
Real Time Assessment Of Security Threats Security Information And Event Management Logging Process Demonstration PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a real time assessment of security threats security information and event management logging process demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Main Principle Of Information Security Ppt Model Designs Download PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative information technology security main principle of information security ppt infographic template information pdf bundle. Topics like main principle of information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Presenting Security Officer Service Company Profile Additional Security Services Ppt PowerPoint Presentation Gallery Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Safety Escort Service, Executive Protection, Special Event Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Best Practices For Cloud Security Ppt Gallery Visuals PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this information technology security best practices for cloud security ppt inspiration example file pdf. Use them to share invaluable insights on best practices for cloud security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Main Steps Of Operational Security Ppt Inspiration Show PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting information security main steps of operational security ppt inspiration show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like sensitive information, potential threats, analyze security, assessment of risks, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Network Security Awareness Staff Learning Organization Cyber Security Dashboard Elements PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization cyber security dashboard elements pdf. Use them to share invaluable insights on organization cyber security dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Managing Information Technology Security 60 Days Plan Professional PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative it security managing information technology security 60 days plan professional pdf bundle. Topics like time to detect an incident, policy violations, data loss incidents, infected computers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security IT Main Principle Of Information Security Ppt Show Example Topics PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative it security it main principle of information security ppt show example topics pdf bundle. Topics like confidentiality, integrity, availability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
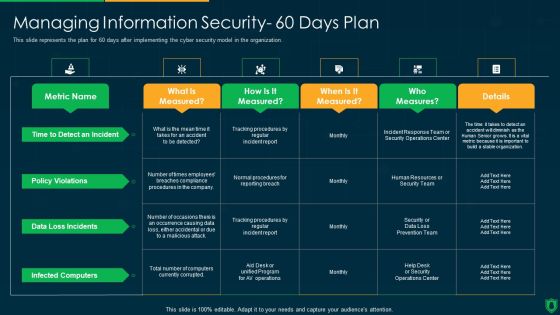
Info Security Managing Information Security 60 Days Plan Ppt PowerPoint Presentation File Graphics Example PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this info security managing information security 60 days plan ppt powerpoint presentation file graphics example pdf. Use them to share invaluable insights on policy violations, data loss incidents, infected computers, time to detect an incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF bundle. Topics like Automation, Individual Insight, Gather Data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
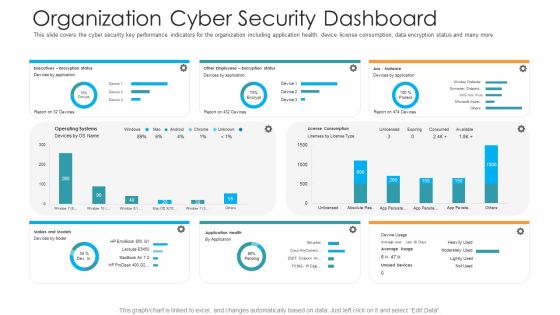
Organization Cyber Security Dashboard Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on executives, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

IT Security Complete IT Security Implementation Checklist Ppt Layouts Graphics PDF
This slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Presenting complete information technology security implementation checklist ppt file introduction pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like secure communications, device security, access control measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Owner Ship, Accessibility Knowledge, Data Governance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Main Principle Of Information Security Ppt Infographics Example Topics PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. This is a it security main principle of information security ppt infographics example topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, integrity, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home