Data Security
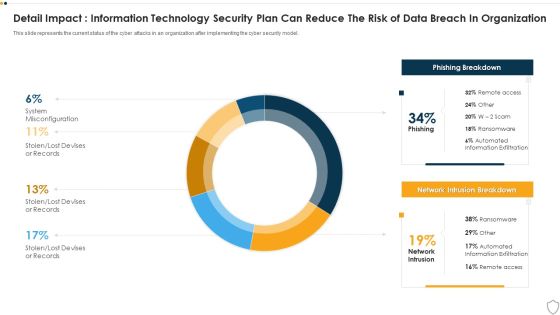
IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Administration Powerpoint Shapes
This is a security administration powerpoint shapes. This is a three stage process. The stages in this process are storage management, directory service administration, security administration.

Security Methodology Diagram Powerpoint Topics
This is a security methodology diagram powerpoint topics. This is a six stage process. The stages in this process are device protection, data separation, security operation, security organization, leak protection, sharing protection.

Security Solutions Powerpoint Templates
This is a security solutions powerpoint templates. This is a four stage process. The stages in this process are site preparation, networking solutions, security solutions, it system integration.

Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF bundle. Topics like Security And Monitoring, Recognize Services, Supporting Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Why Cloud Security Is Important Pictures PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Why Cloud Security Is Important Pictures PDF bundle. Topics like Centralized Security, Cost Effective, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Key Cloud Security Use Cases Diagrams PDF Use them to share invaluable insights on Account Access, Data Exfiltration, Network Connections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Best Practices For Cloud Security Topics PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. This is a desktop security management best practices for cloud security topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, management, measures, planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How To Manage Cloud Security Inspiration PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures.This is a Cloud Security Assessment How To Manage Cloud Security Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compliance Is Effective, Business Procedures, Manage Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Cloud Security Checklist Networking Formats PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks.This is a Cloud Security Assessment Cloud Security Checklist Networking Formats PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gateway To Protect, Injecting Malicious, Precautions To Protect You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How Does Cloud Security Work Formats PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Security Assessment How Does Cloud Security Work Formats PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Information Against, Transparency, Regulations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF. Use them to share invaluable insights on Cloud Frameworks, Information Division, Cautious Scaling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.This is a Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Administrative Rights, Privileged Credentials, Legitimate Users You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss.This is a Cloud Security Assessment Pillars Of Cloud Security Identity Security Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Devices To Accomplish, Service Permissions, Information Applications You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF
This slide outlines the main attributes of blockchain network security. The purpose of this slide is to highlight the security attributes of blockchain technology, including transaction integrity, tamper resistance, consistency, access to network and data, confidentiality of transactions, and so on. The Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cloud Information Security Pillars Of Cloud Security Identity Security Ppt Layouts Graphics Example PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. This is a Cloud Information Security Pillars Of Cloud Security Identity Security Ppt Layouts Graphics Example PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Advanced Authentication, Cloud Access, Eliminate Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pillars Of Cloud Security Identity Security Cloud Computing Security IT Ppt Model Slides PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. This is a pillars of cloud security identity security cloud computing security it ppt model slides pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like pillars of cloud security identity security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Operations Cyber Security Protection Icon Rules PDF
Persuade your audience using this Security Operations Cyber Security Protection Icon Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Protection Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.

Security Operations Cyber Security Icon With Lock Clipart PDF
Persuade your audience using this Security Operations Cyber Security Icon With Lock Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Cyber, Security Icon With Lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
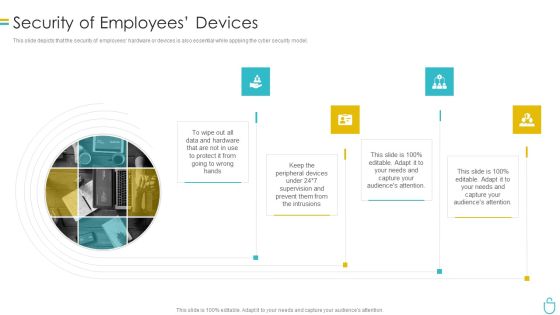
Information Security Security Of Employees Devices Ppt Model Infographics PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting information security security of employees devices ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Pillars Of Cloud Security Identity Security Diagrams PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. Deliver an awe inspiring pitch with this creative Pillars Of Cloud Security Identity Security Diagrams PDF bundle. Topics like Service Permissions, Application, Required can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Main Principle Of Information Security Introduction PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver and pitch your topic in the best possible manner with this desktop security management main principle of information security introduction pdf. Use them to share invaluable insights on availability, integrity, confidentiality and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions.Presenting Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Categorization Of Services, Access Control, Data Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Complete Computer Security Implementation Checklist Demonstration PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting desktop security management complete computer security implementation checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, organizations, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. This is a Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
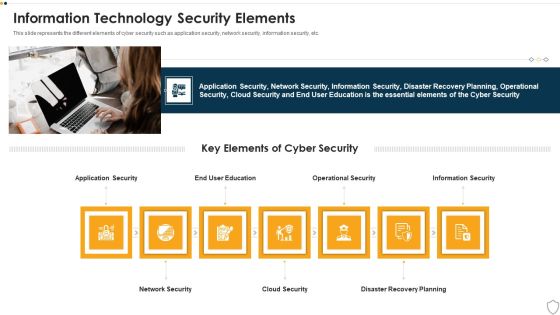
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pillars Of Cloud Security Network Security Rules PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. This is a Pillars Of Cloud Security Network Security Rules PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure, Network, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Roadmap For Computer Security Training Graphics PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting desktop security management roadmap for computer security training graphics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Security Patches And Updates Summary PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting Cloud Security Checklist Security Patches And Updates Summary PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security Patches, Measures, Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Confidential Files Security Template 1010
illustration of confidential files security in computer generated image

Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF
The following slide highlights the quarterly roadmap to plan strategically and achieve goals. It constitutes of activities such as optimizing website, establishing governance team, setting security standards, organizing training and awareness etc. Presenting Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Optimize Website, Information Management, Organize Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Functioning Centre Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security functioning centre assessment of security maturity spectrum slides pdf bundle. Topics like security mature, operational efficiency, security capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative organizational security solutions impact of effective security management information pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Good Ppt Example
This is a security management good ppt example. This is a thirteen stage process. The stages in this process are logical security, access control, digital video , asset management, alarm, management, multi tenant property management, fire alarm integration.

Security Agency Business Profile Additional Security Services Download PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. This is a Security Agency Business Profile Additional Security Services Download PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Safety Escort Service, Executive Protection, Special Event Security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Presenting Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Visibility And Consistency, Network Security, Identity Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Pillars Of Cloud Security Process Based Security Information PDF
This slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Pillars Of Cloud Security Process Based Security Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Application, Security Requires. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
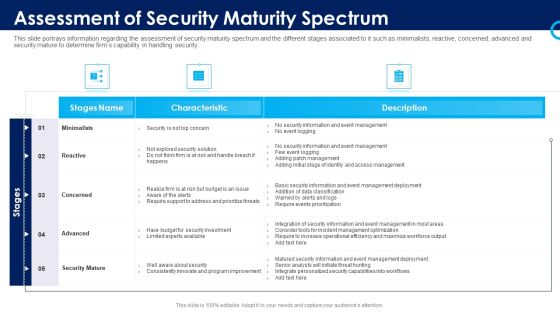
Organizational Security Solutions Assessment Of Security Maturity Spectrum Rules PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative organizational security solutions assessment of security maturity spectrum rules pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Use Of Security Programs Professional PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks.Presenting IT Security Hacker Use Of Security Programs Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Technology Requires, Monthly Membership, Elimination Of Malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
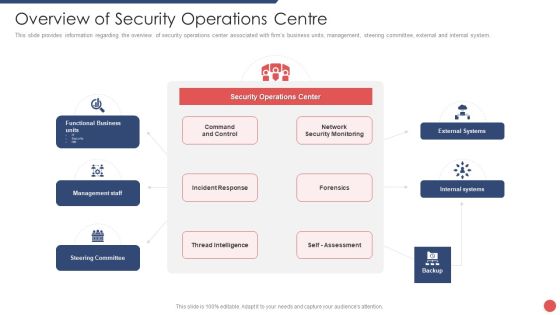
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
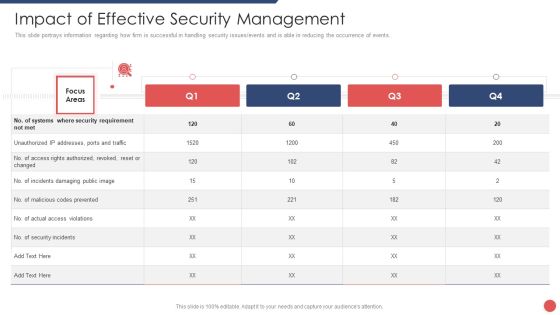
Security Functioning Centre Impact Of Effective Security Management Brochure PDF
This slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative security functioning centre impact of effective security management brochure pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Additional Security Services Formats PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Additional Security Services Formats PDF bundle. Topics like Safety Escort Service, Executive Protection, Safety Escort Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Operations Framework To Monitor Security Threats Demonstration PDF
This slide display security operations threat detection and eradication process in order to increase security at all stages of development. It includes new security incident, response to threat, root cause analysis, etc. Pitch your topic with ease and precision using this Security Operations Framework To Monitor Security Threats Demonstration PDF. This layout presents information on Execute Mitigation, Develop, Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Desktop Security Management Security Of Employees Devices Microsoft PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Deliver an awe inspiring pitch with this creative desktop security management security of employees devices microsoft pdf bundle. Topics like security of employees devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Uniformed Security Security Guard Services Proposal Specializing In Icons PDF
This is a uniformed security security guard services proposal specializing in icons pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like environments, security, investigations, communication, entertainment facilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role Of Security Operations Centre In Security Operations Structure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. This is a role of security operations centre in security operations structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like operations team is responsible, compliance requirements checklist, security will be present. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system.This is a Cloud Security Assessment What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Convenience Over, Accessed Remotely, Threats Of Accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Operations Icon To Prevent Security Breaches Ideas PDF
Persuade your audience using this Security Operations Icon To Prevent Security Breaches Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Operations Icon, Prevent Security Breaches. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizational Security Solutions Security Operations Implementation Timeline Activity Background PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative organizational security solutions security operations implementation timeline activity background pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Security Operations Implementation Timeline Staff Brochure PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this organizational security solutions security operations implementation timeline staff brochure pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home