Data Security

Addressing Timeframe For Incident Management At Mobile Device Mobile Device Security Management Microsoft PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this Addressing Timeframe For Incident Management At Mobile Device Mobile Device Security Management Microsoft PDF. Use them to share invaluable insights on Incident Categorization, Incident Prioritization, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Determine Mobile Device Maintenance Checklist Mobile Device Security Management Graphics PDF
This slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver an awe inspiring pitch with this creative Determine Mobile Device Maintenance Checklist Mobile Device Security Management Graphics PDF bundle. Topics like Preventive Maintenance, Executive Reporting, Planning Meeting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF
This slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy.This is a Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Best Example, Authentication, Implement Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
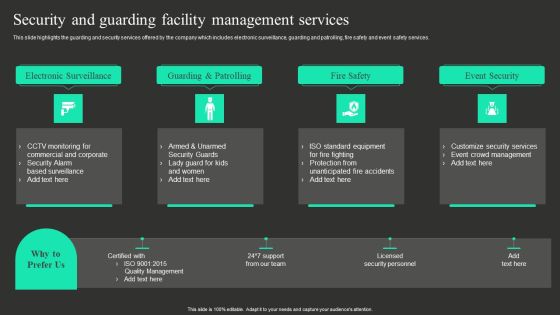
Workplace Facility Management Services Company Security And Guarding Facility Management Services Portrait PDF
This slide highlights the guarding and security services offered by the company which includes electronic surveillance, guarding and patrolling, fire safety and event safety services. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Workplace Facility Management Services Company Security And Guarding Facility Management Services Portrait PDF can be your best option for delivering a presentation. Represent everything in detail using Workplace Facility Management Services Company Security And Guarding Facility Management Services Portrait PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Use this Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cyber Security Administration In Organization Threat Management Action Plan Level Information PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Human Resource Services Business Profile Our Global Presence Graphics PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. This Security And Human Resource Services Business Profile Our Global Presence Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security And Human Resource Services Business Profile Our Global Presence Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Cyber Security Operations Center With Log And Event Aggregation Ppt Infographic Template Tips PDF
Showcasing this set of slides titled cyber security operations center with log and event aggregation ppt infographic template tips pdf. The topics addressed in these templates are operational, technology, business. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
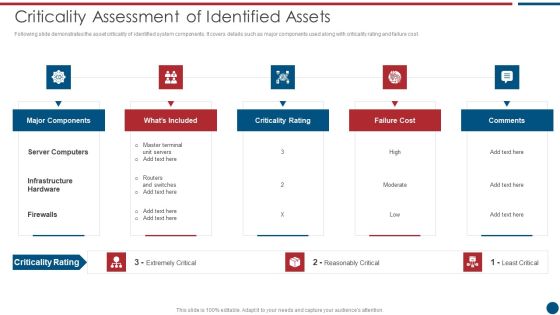
Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Global Cyber Terrorism Incidents On The Rise IT Roadmap To Implement Cyber Security Icons PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. This is a global cyber terrorism incidents on the rise it roadmap to implement cyber security icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like keep the hardware and software updated, awareness training for employees, creating personal accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Roles And Responsibilities To Ensure Work Environment With Employee Safety Pictures PDF
This slide provides information regarding roles and responsibilities assigned to ensure minimum violence work environment. Presenting project security administration it roles and responsibilities to ensure work environment with employee safety pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee responsibilities, unit supervisor or manager responsibilities, internal investigations unit responsibilities, human resources responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Awareness Program Capability Maturity Model Ppt PowerPoint Presentation File Portfolio PDF
The following slide showcases five stages of security awareness maturity model. Non-existent, compliance focused, promoting awareness, cultural change and metrics framework are the key stages through which an organization can build robust security awareness program. Persuade your audience using this security awareness program capability maturity model ppt powerpoint presentation file portfolio pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including non existent, compliance focused, promoting awareness and behavior change, long term sustainment and culture change, metrics framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF
The purpose of this slide is to outline a multistep process that can assist IT managers in drafting a cyber security awareness roadmap. The various steps are assessing, building, choosing, deploying, educating employees, and retesting. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Five Step Process To Create Cyber Security Awareness Roadmap Microsoft PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF
This slide describes the cyclops blink cyber attack held by russia on official ukrainian websites created by the sandworm organization to replace the VPN filters. Get a simple yet stunning designed Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Retrieve professionally designed O RAN Architecture Role Of Security In Open RAN Standards Ppt Infographics Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
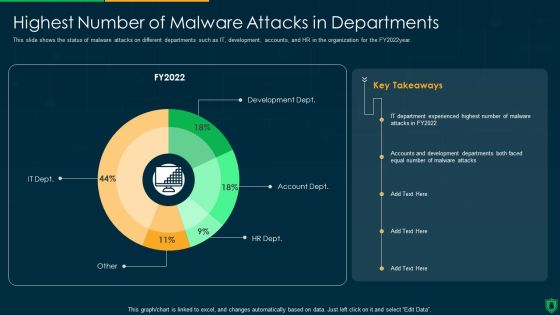
Info Security Highest Number Of Malware Attacks In Departments Ppt PowerPoint Presentation Gallery Format PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022year. Deliver an awe inspiring pitch with this creative info security highest number of malware attacks in departments ppt powerpoint presentation gallery format pdf bundle. Topics like development dept, account dept, hr dept, it dept can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Retrieve professionally designed Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Get a simple yet stunning designed Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. rom laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Developing Firm Security Strategy Plan Determine Staff Training Schedule For Skills Enhancement Infographics PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting developing firm security strategy plan determine staff training schedule for skills enhancement infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Determine Staff Training Schedule For Skills Enhancement Inspiration PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting corporate security and risk management determine staff training schedule for skills enhancement inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced software training, advanced skills training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Different Kinds Of Insider Digital Threats Themes PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Presenting corporate security and risk management different kinds of insider digital threats themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like malicious insider, negligent or careless insider, third party insider . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Threat Management Action Plan Risk Portrait PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting corporate security and risk management threat management action plan risk portrait pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
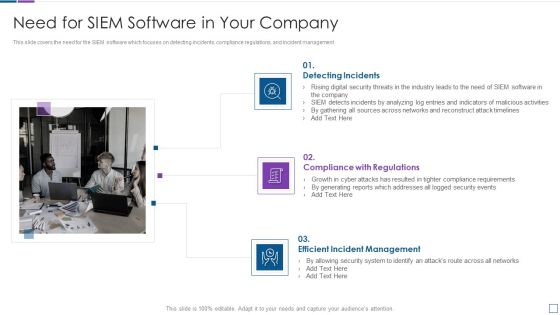
Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF today and make your presentation stand out from the rest.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF today and make your presentation stand out from the rest.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
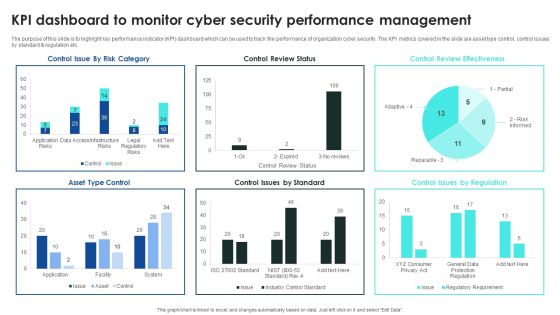
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Get a simple yet stunning designed Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF Use them to share invaluable insights on Authentication Process, Access Standards, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Packages Offered By Third Party Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Info Security Problems Faced By The Organization Ppt PowerPoint Presentation File Slide PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this info security problems faced by the organization ppt powerpoint presentation file slide pdf. Use them to share invaluable insights on losses organization, due cyberattacks, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Statistics Highlighting Lack Of Cyber Security Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
IT Security Strategies To Manage Cyber Risks Ppt Icon Gallery PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting it security strategies to manage cyber risks ppt icon gallery pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like conduct awareness sessions, prioritize cyber risk as strategic issue, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document
This slide illustrates the cover letter for the business proposal providing a brief overview of the clients wants and a brief introduction to the project. Presenting you an exemplary Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document brilliant piece now.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting project security administration it various ways to manage project safety by managing threats designs pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like track baseline behavior, networks and individuals, inform end user, periodic risk assessment, render least amount of privilege. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
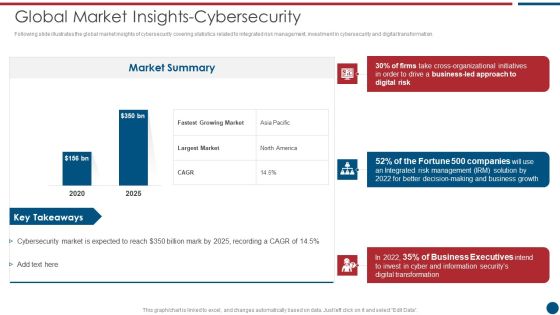
Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF bundle. Topics like Market Summary, Largest Market, Business Led can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
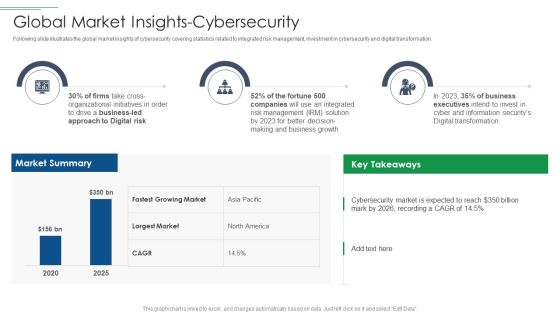
IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF bundle. Topics like Business Growth, Risk Management, Organizational Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
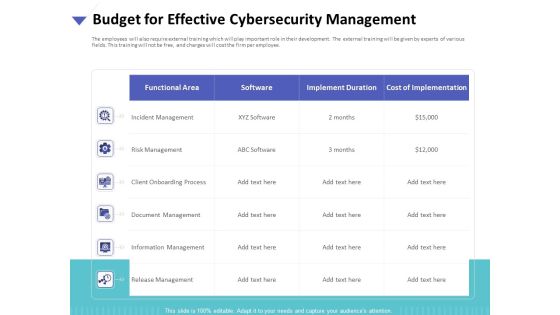
Strategies To Mitigate Cyber Security Risks Budget For Effective Cybersecurity Management Ppt Infographic Template Styles PDF
Presenting this set of slides with name strategies to mitigate cyber security risks budget for effective cybersecurity management ppt infographic template styles pdf. The topics discussed in these slides are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Develop Corporate Cyber Security Risk Mitigation Plan Organization Mission And Vision Statement Download PDF
Presenting develop corporate cyber security risk mitigation plan organization mission and vision statement download pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like vision, mission. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Compare Elements PDF
Presenting case competition overpower the obstacle of cyber security in medicare compare elements pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like male, female. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Mission Vision And Core Values Microsoft PDF
Presenting Security Agency Business Profile Mission Vision And Core Values Microsoft PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Mission Vision, Core Values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
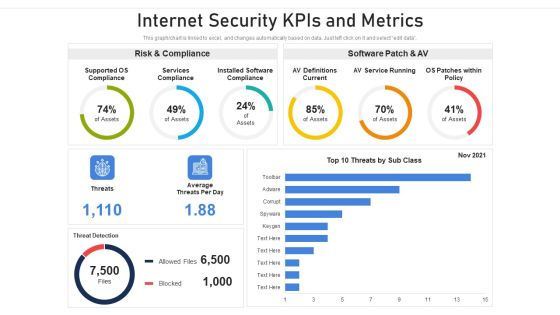
Internet Security Kpis And Metrics Ppt PowerPoint Presentation Gallery Outline PDF
Showcasing this set of slides titled internet security kpis and metrics ppt powerpoint presentation gallery outline pdf. The topics addressed in these templates are threat detection, risk and compliance, services compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Risk Scorecard 8 Essential Information Security Risk Scorecard For Organization Elements PDF
Presenting cybersecurity risk scorecard 8 essential information security risk scorecard for organization elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF
Get a simple yet stunning designed Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.

Your Specialized Packages For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the specialized package of custom services it includes cost of each phase along with key notes. Presenting you an exemplary Your Specialized Packages For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Specialized Packages For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Client Testimonial For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the client testimonials that has been provided by multiple clients to the origination. It also displays the name and designation of client. Presenting you an exemplary Client Testimonial For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Client Testimonial For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
 Home
Home